System identification with binary-valued observations under both denial-of-service attacks and data tampering attacks:defense scheme and its optimality
2022-03-02JinGuoXuebinWangYanlingZhangWenchaoXueYanlongZhao
Jin Guo·Xuebin Wang·Yanling Zhang·Wenchao Xue·Yanlong Zhao
Abstract In this paper, we investigate the defense problem against the joint attacks of denial-of-service attacks and data tampering attacks in the framework of system identification with binary-valued observations.By estimating the key parameters of the joint attack and compensating them in the identification algorithm,a compensation-oriented defense scheme is proposed.Then the identification algorithm of system parameter is designed and is further proved to be consistent.The asymptotic normality of the algorithm is obtained,and on this basis,we propose the optimal defense scheme.Furthermore,the implementation of the optimal defense scheme is discussed.Finally,a simulation example is presented to verify the effectiveness of the main results.
Keywords System identification·Denial of service attack·Data tampering attack·Defense scheme
1 Introduction
Cyber physical systems (CPSs) composed of computing,network communication and physical environment have gradually become popular in the fields of infrastructure,aerospace,etc.[1–3].To meet the real-time requirement for the large amount of information exchange between subsystems, the CPSs have to use relatively open communication network,which brings hidden dangers for the system security[4–7].Therefore,it is of great significance to study the defense methods against network attacks for ensuring the safe and stable operation of CPSs.
The current research on CPSs security is mainly carried out from two aspects.On the one hand,it uses authentication protocols, encryption, access control and other methods to block attackers from entering [8–10]. To protect the sensitive data in the system,a layered encryption mechanism was designed based on hash chain technology that can provide key management [8]. For ensuring that only legal commands can be transmitted in the communication network,a scheme to sign control commands was proposed through a hash method [9], which can resist malicious command attacks, replay attacks, camouflage attacks, etc. An anonymous secure framework was presented for connected smart homes [10], which can ensure the anonymity and unlinkability of devices.On the other hand,methods such as traffic analysis and intrusion detection are used to realize real-time monitoring of attacks and judgment of malicious behaviors[11,12]. With developing and deploying smart modules in multiple layers of smart grids,a distributed intrusion detection system was given[11].By adopting a three-phase designstrategy, transfer entropy countermeasures were applied to anomaly detection and related problems in CPSs[12].
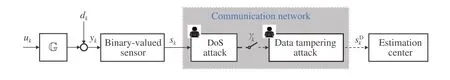
Fig.1 System configuration
From the point of view of hit effect,network attacks can be divided into DoS (denial-of-service) attacks that cause data packet loss,and data tampering attacks that cause data errors [13–18]. When these two kinds of attacks are performed simultaneously, the transmitting data may be lost and the data received may be incorrect. The coupling of the two brings great difficulties to the defense. As a result,there are relatively few effective defense schemes in literature.This paper is to introduce such a defense method against the joint attacks of DoS attacks and data tampering attacks in the framework of system identification with binary-valued observations, which is research area that has received wide attention in recent years[19–21].
We use the probabilistic models to describe DoS attacks and data tampering attacks.By estimating the key parameters of the joint attack and compensating them in the identification algorithm, a so-called compensation-oriented defense scheme is proposed, under which the identification algorithm of system parameter is designed. It is shown that the algorithm strongly converges to the true value. Then the asymptotic normality of the algorithm is obtained, and on this basis,we give the optimal defense scheme to minimize the the asymptotic variance of the estimation error.Furthermore,the implementation of the optimal defense scheme is discussed.
The rest of this paper is arranged as follows: Section 2 describes the defense problem under DoS attacks and data tampering attacks.Section 3 introduces the defense scheme.Section 4 discusses the asymptotic normality and optimality of the defense scheme. Section 5 gives the implementation method of the optimal defense scheme. Section 6 verifies the main conclusions via a simulation example. Section 7 summarizes the main findings and discusses possible future research directions.
2 Problem formulation
Consider a single-input single-output discrete-time system:yk= G(uk;θ)+dk,wheredkis the system noise;θis the unknown parameter;ukis the system input;ykis the system output measured by a binary-valued sensor with the thresholdC, which can be expressed by the following indicator function:

where{γk}is an independent random variable sequence,and its distribution is determined bysk,that is,
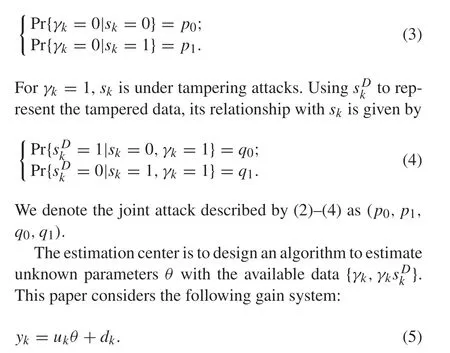
Assume thatuk≡1. For other multi-parameter systems such as linear finite impulse response systems and nonlinear Wiener systems, we can decoupled them into multiple gain systems by designing input[22].
Without network attacks, the optimal algorithm (in the sense of Cramér-Rao lower bound)to estimateθis
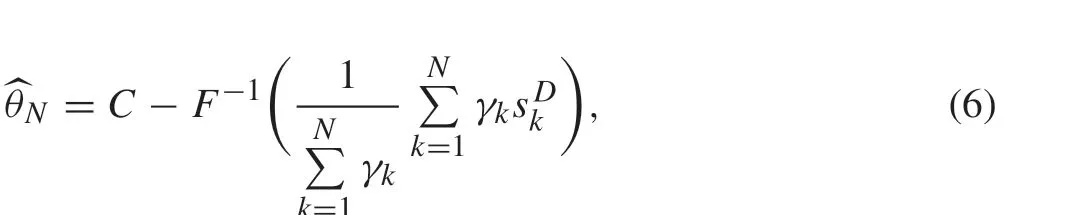
whereNrepresents the data length,θNis the estimated value of the unknown parameterθ,Cis the threshold in (1), andF-1(·)represents the inverse function ofF(·).
If the attack occur,then the consistency of algorithm(6)is bound to be destroyed. At this point, the first and core question is how should the estimation center design a defense scheme and redesign a consistent identification algorithm?This paper will solve this by introducing a compensationoriented defense scheme.
Assumption 1 The system noise{dk}is an independent and identical distribution (i.i.d) sequence of Gaussian random variables,where the distribution function is denoted asF(·)and the density function isf(·).
To facilitate the coming presentation,we give the following notation:
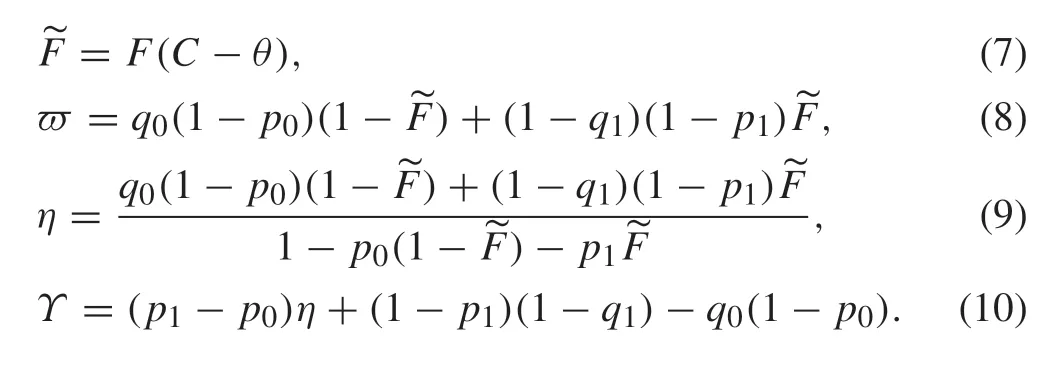
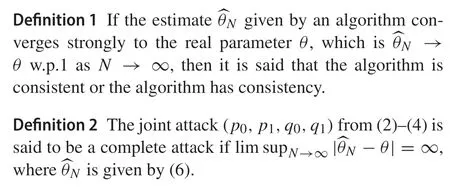
Remark 11)For multi-level quantized observation,one can view it as a vector-valued binary observation in which each vector component represents the output of one threshold.Then (6) can be improved by a method named the quasiconvexcombinationestimator(QCCE)proposedin[22].2)If thesysteminputisalsoquantized,oneeffectivewayistoclassify the regressor sequence into distinct patterns according to the values of the regressor vector.Then,one can combine the QCCE and the weighted least-squares optimization technique to design identification algorithms.See[23]for more details.
3 Design of defense scheme and identification algorithm
If the joint attack of DoS attacks and data tampering attacks are not limited by energy, it would be a complete attack,and the identification error will be infinite.In this case,it is very hard to compensate for the error through the design of identification algorithm. However, when the joint attack is constrained by energy and cannot achieve a complete attack,we may design a defense scheme and realize the compensation of identification error. The following considers the design of defense scheme and identification algorithm under incomplete attacks.
If(p0,p1,q0,q1)of the joint attack is known, one can design the compensation-type algorithm to ensure the consistency:
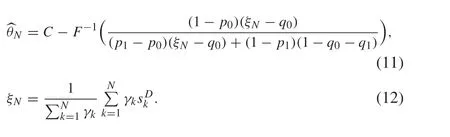
Theorem 1Consider the system (5) and the binary-valued observation (1). If Assumption 1 holds, then the algorithm(11)–(12)is consistent.
ProofAccording to Total Probability Theorem,we have

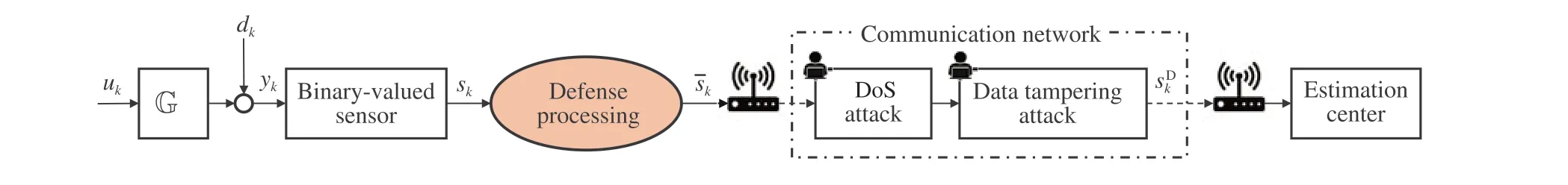
Fig.2 System configuration with defense
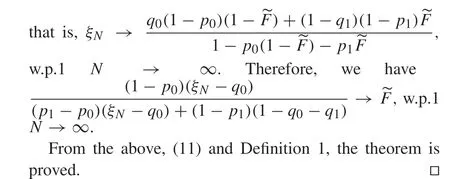
In practice,the estimation center does not know the attack strategy(p0,p1,q0,q1), and then the algorithm ((11) and(12)) does not work. One immediate idea is to estimate(p0,p1,q0,q1)and then replace the true value with its estimatedvaluein(11)and(12)toformanadaptiveidentification algorithm.

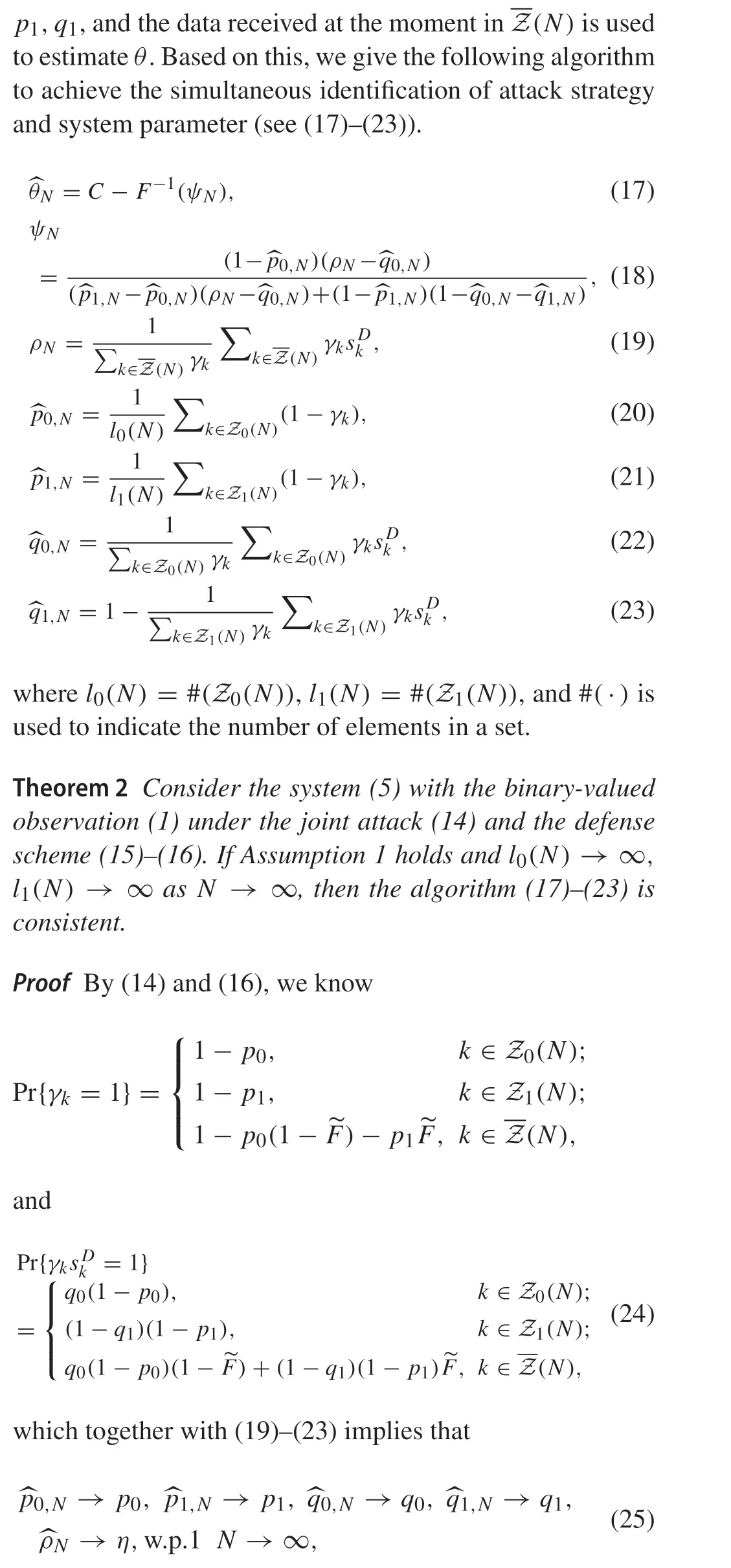
whereηis given by(9).By the above and(18),one can get
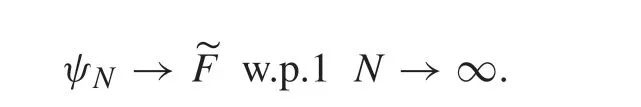
Then,the theorem is proved by(17)and Definition 1.■
Remark 2If the distribution function of the system noise is unknown,one can view it,system parameters and the attack strategy jointly as uncertainties,and extract the information about the noise distribution from the designed input and relevant output data of the system with a modified algorithm.The methodology of joint identification of the distribution function and the system parameter can be found in Chapter 8 of[22]and Section 7 in[23].
4 Optimality of defense scheme




Combing (35), (44), (45) and (46), the theorem is proved.■
From the above theorem, it can be seen that the smallerΣ2(β0,β1)means the smaller asymptotic variance of estimation error.Then,how to choose a defense scheme(β0,β1)to minimizeΣ2(β0,β1)?This can be described as the following optimization problem:

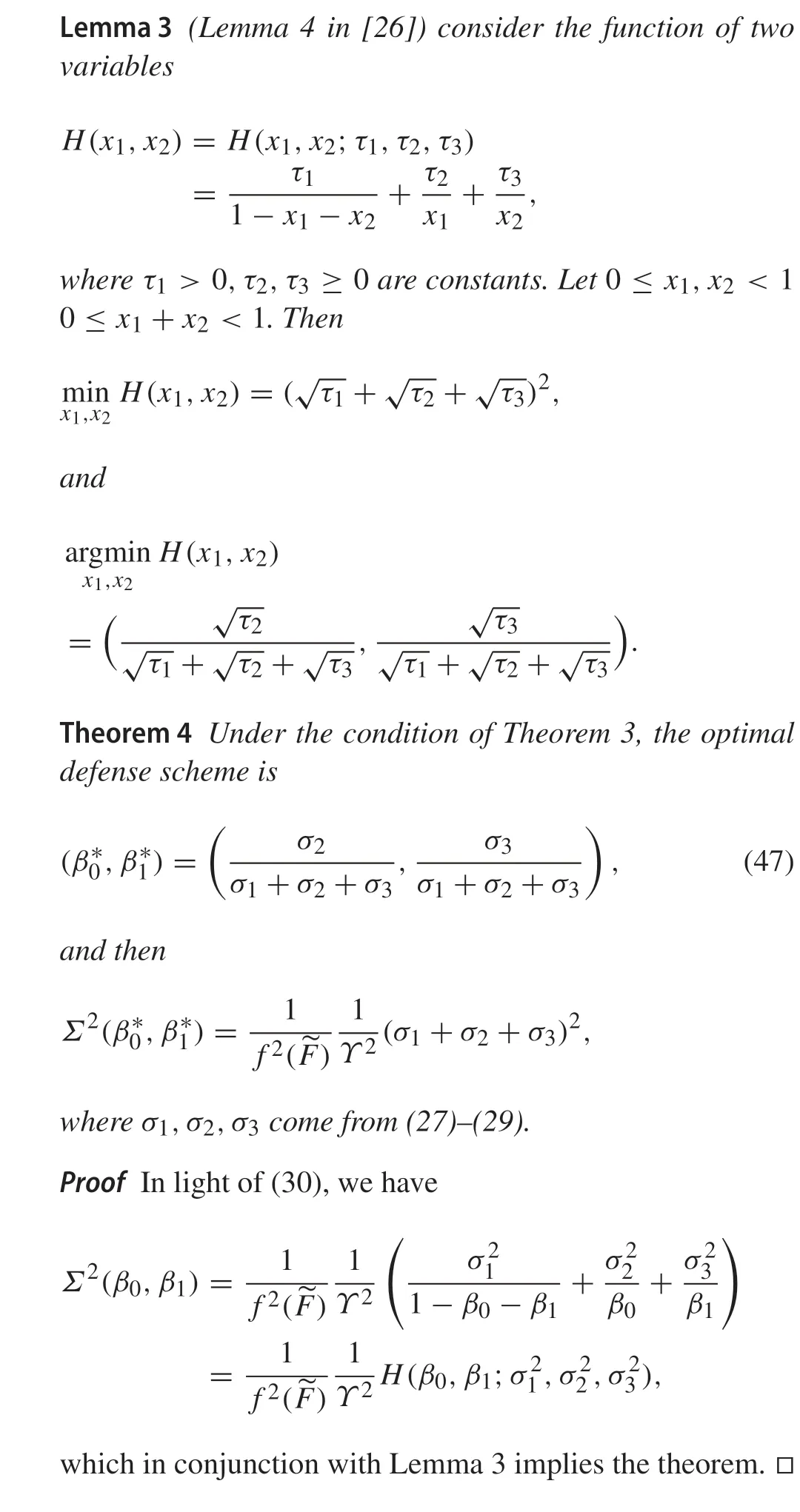
5 Implementation of the optimal defense scheme

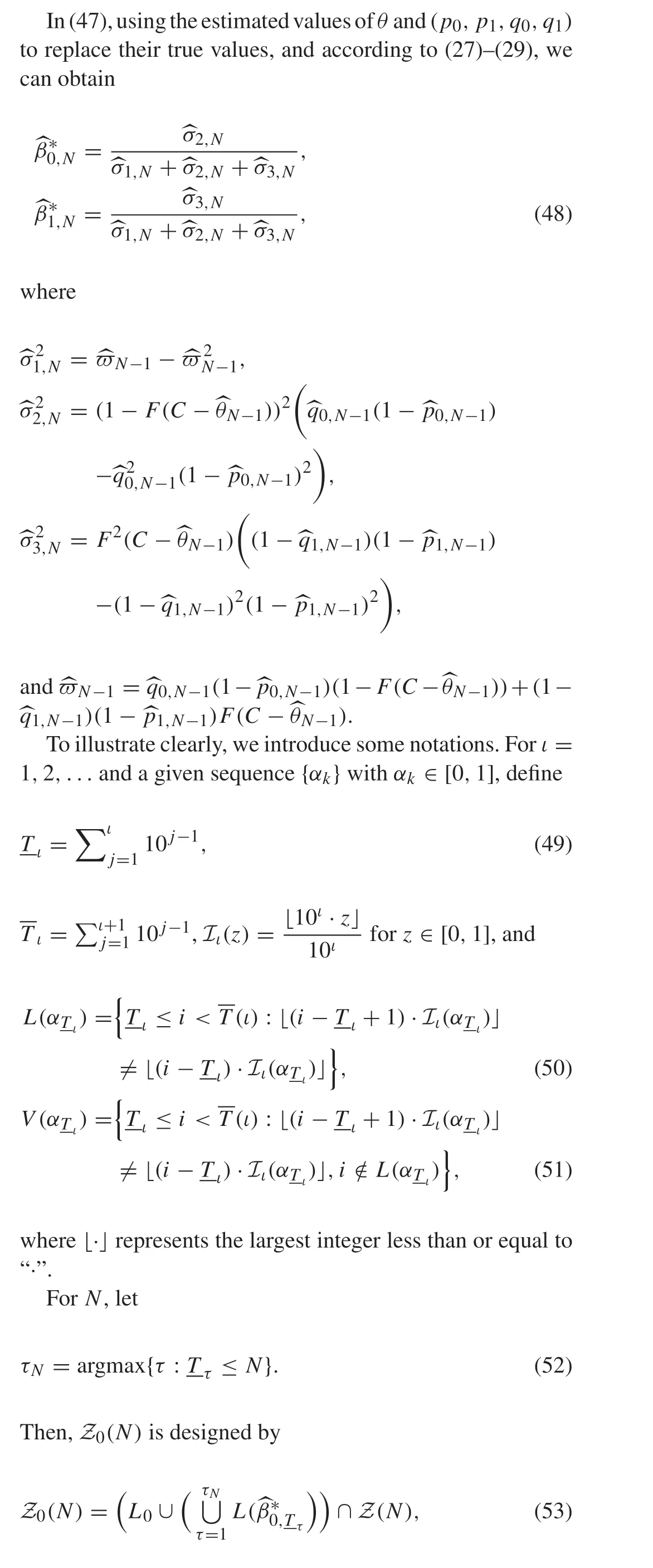




6 Numerical simulation
Consider the system
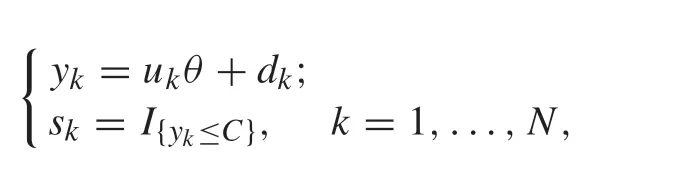
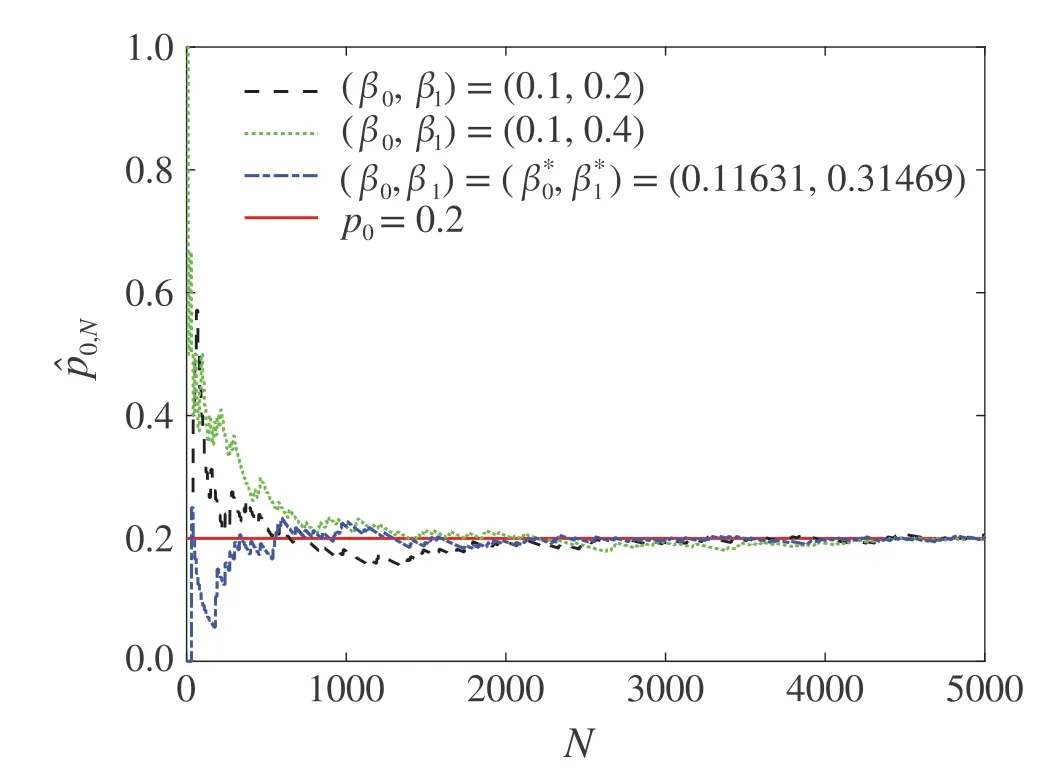
Fig.3 Convergence of the estimate of p0 using algorithm(17)–(23)
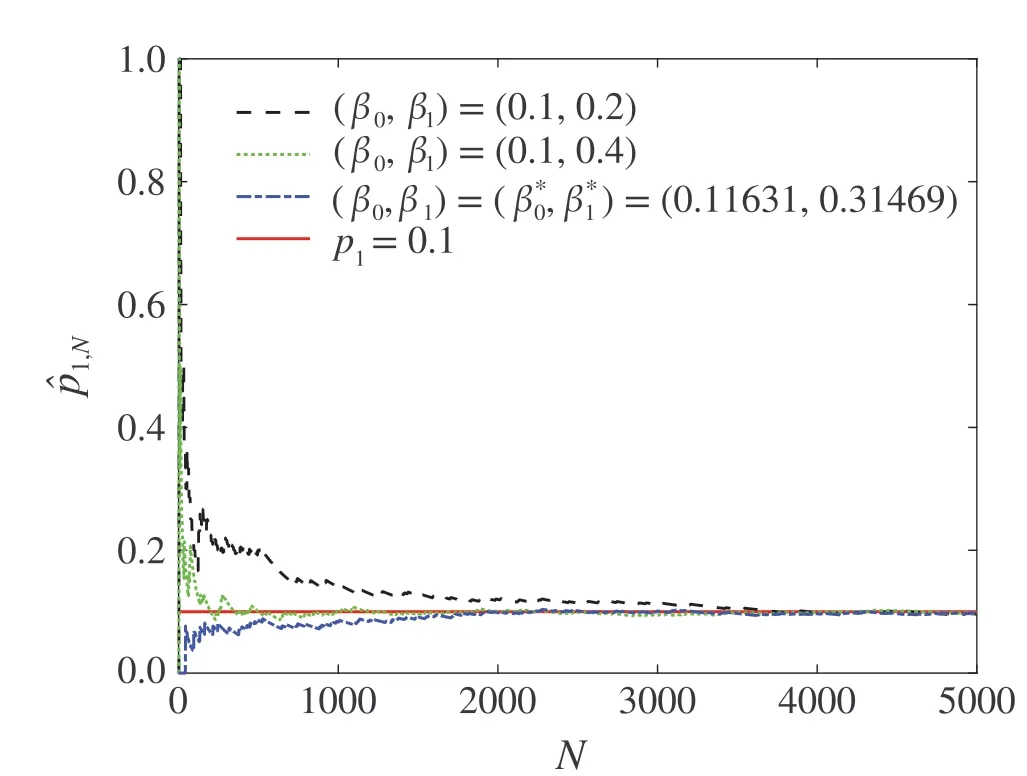
Fig.4 Convergence of the estimate of p1 using algorithm(17)–(23)
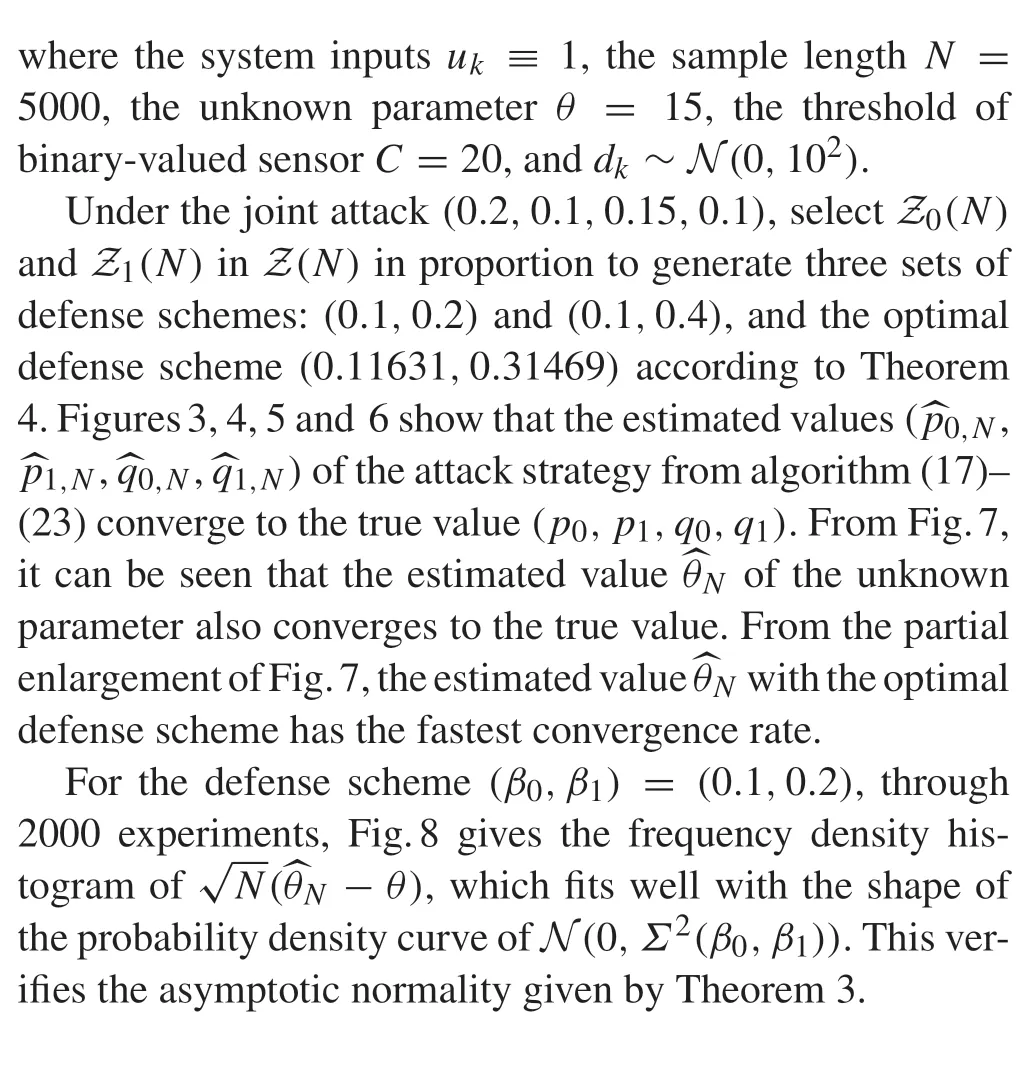
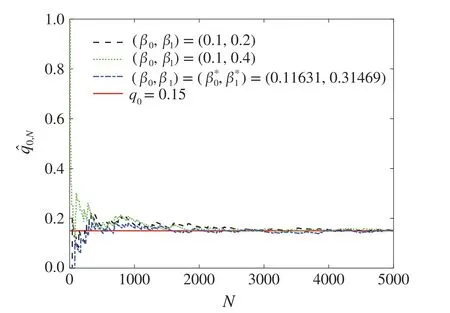
Fig.5 Convergence of the estimate of q0 using algorithm(17)–(23)
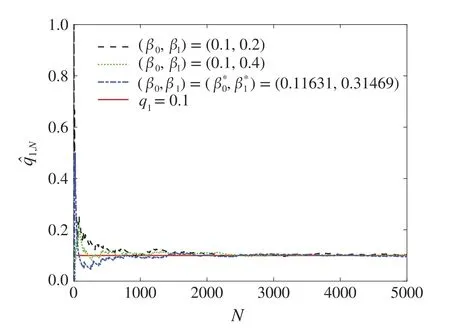
Fig.6 Convergence of the estimate of q1 using algorithm(17)–(23)
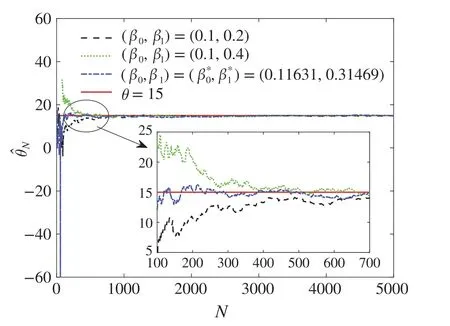
Fig.7 Convergence of the estimate of θ using algorithm(17)–(23)
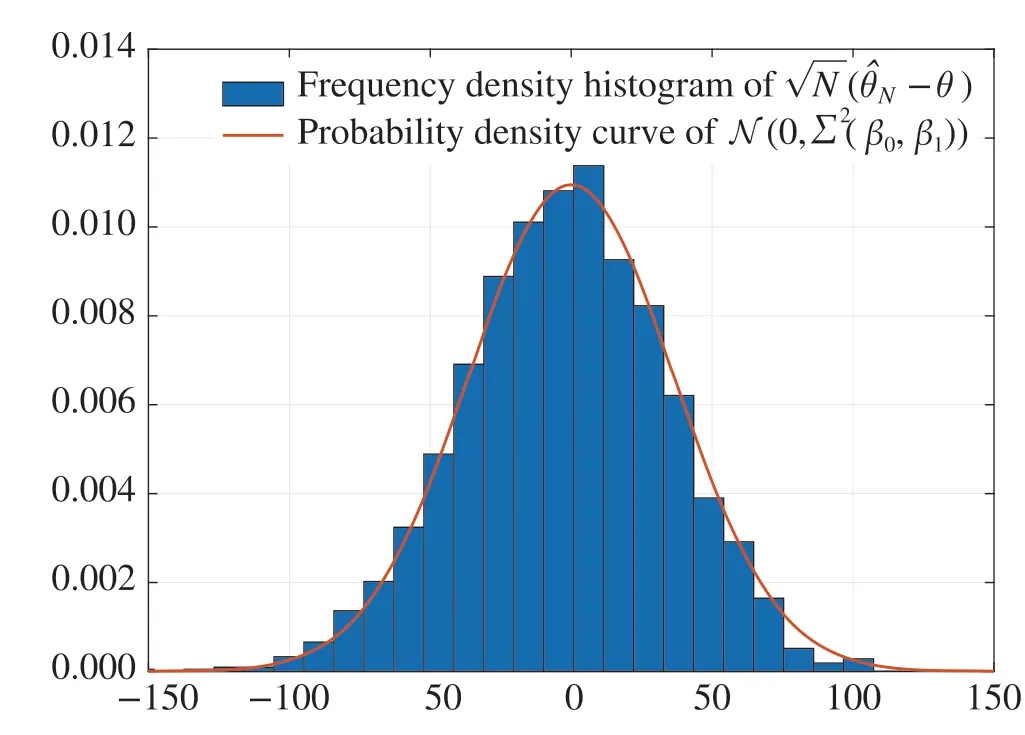
Fig.8 Asymptotic normality of algorithm(17)–(23)
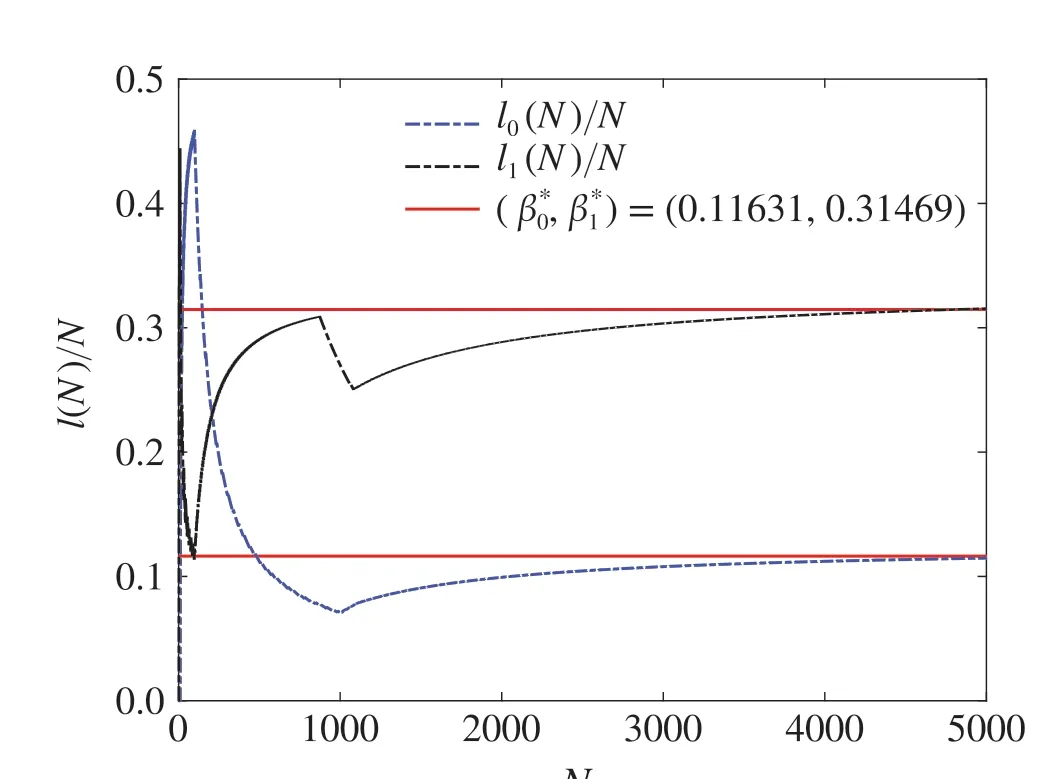
Fig.9 Convergence of andunder(53)and(57)

7 Concluding remarks
In the framework of system identification with binary-valued observations, this paper addressed the defense problem against the joint attacks of denial-of-service attacks and data tampering attacks. We proposed a compensation-oriented defense scheme. It was shown that the identification algorithm under such scheme was consistent and had asymptotic normality. Furthermore, the optimal defense scheme was obtained and its implementation was discussed.
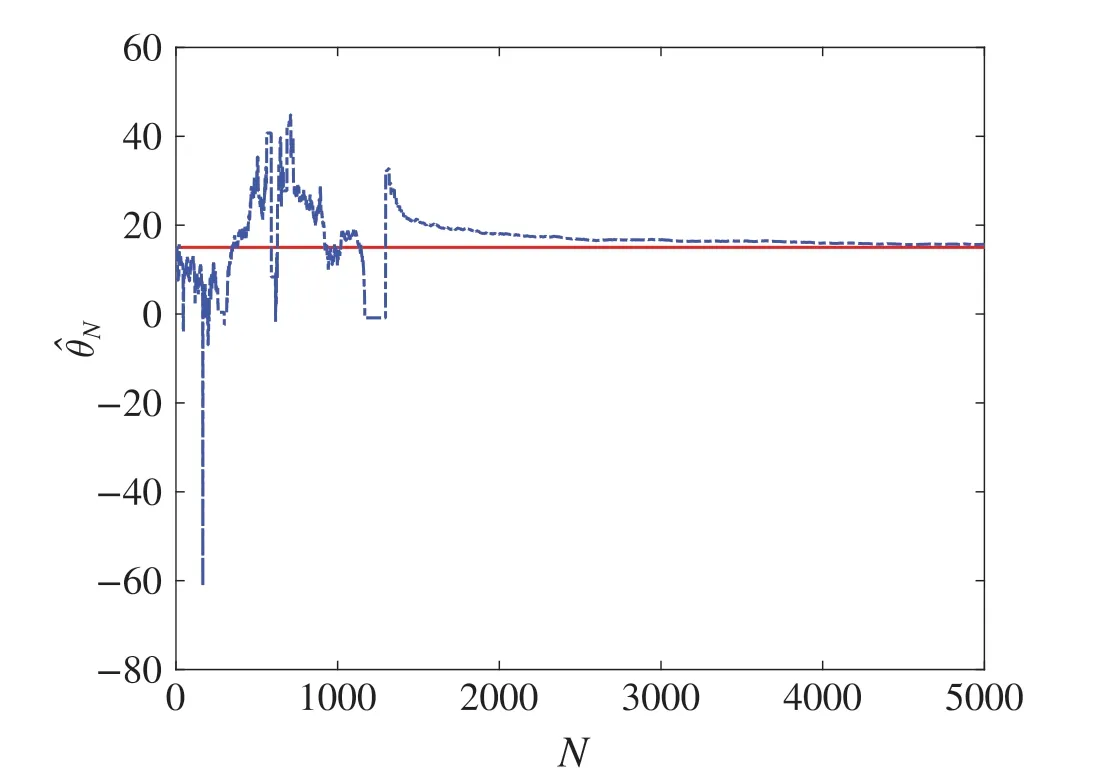
Fig.10 Convergence ofθN under(53)and(57)
Future research can explore new defense schemes and other application scenarios of the defense methods in this paper. The related results can be extended to the cases of colored noises,multi-level quantized observations,other parameterized attack models, multi-parameter systems and so on.
Acknowledgements This research was supported by the National Key Research and Development Program of China(2018YFA0703801),the National Natural Science Foundation of China(62173030,62033010).
杂志排行
Control Theory and Technology的其它文章
- Bearing fault diagnosis with cascaded space projection and a CNN
- Adaptive output regulation for cyber-physical systems under time-delay attacks
- Distributed robust MPC for nonholonomic robots with obstacle and collision avoidance
- Sparse parameter identification of stochastic dynamical systems
- Constrained nonlinear MPC for accelerated tracking piece-wise references and its applications to thermal systems
- Adaptive robust simultaneous stabilization of multiple n-degree-of-freedom robot systems
