Joint utility optimization algorithm for secure hybrid spectrum sharing①
2022-02-11WANGYiHUANGRongXUYaohuaJIANGFangBAINaTANGTaoHUYanjun
WANG Yi(王 翊),HUANG Rong,XU Yaohua,JIANG Fang,BAI Na,TANG Tao,HU Yanjun
(Key Laboratory of Intelligent Computing & Signal Processing,Ministry of Education,Anhui University,Hefei 230601,P.R.China)
Abstract
Key words:spectrum sharing,power control,joint utility,blockchain
0 Introduction
With the increasing demand for fifth-generation wireless communication networks,the development of key capabilities such as large-scale connectivity,high reliability and guaranteed low latency of wireless communication networks are in the process of being standardised.The new requirements mentioned in the 6G Drivers and Visioninclude the need to provide global coverage,higher spectrum/energy/cost efficiency,more intelligence and higher security[1].The issues of spectrum,energy and free access are increasingly prominent in current communication scenarios[2].Radio spectrum resources are not efficiently utilized,and there are problems such as shortages of spectrum resources,inefficient resource management modes,uneven distribution of available spectrum resources,etc.In terms of the deployment of the mobile communication network,it is necessary to effectively use all available spectrum resources considering costs,demands and service experience[3].Therefore,it is urgent to find new solutions to improve the spectrum management and allocation efficiency in wireless communication networks.
Cognitive radio(CR)technology is a feasible solution for alleviating the spectrum resource shortage and under-utilization problem.Cognitive radio is defined as an intelligent wireless communication system with two main features:cognitive capability and reconfiguration capability.In addition,primary users(PUs)can share their licenced spectrum with secondary users(SUs)to improve spectrum utilization[4].
Cognitive capabilities enable radio systems to capture or sense information from the wireless environment in which they operate so that they can identify unused spectrum resources in the given time and space for the most appropriate spectrum and operating parameters.Energy consumption during spectrum sensing is modelled in Ref.[5],which investigates the factors that influence the energy efficiency of spectrum sensing and signal transmission.During sensing,individual secondary users are vulnerable to the effects of factors such as multipath fading and shadow effects.Cooperative spectrum sensing can be used to share important user information and send the sensed information to the fusion centre(FC)for fusion decisions,which is superior to the single node method and ensures the accuracy of the sensing result[6].Through cooperative spectrum sensing,the fading problem is effectively improved,the false probability is reduced and the probability of correct decisions was increased in Ref.[7].The impact of incomplete knowledge of false alarm probabilities and detection probabilities on fusion results was investigated in Ref.[8].The detection probability increases as the sensing time increases,and the transmission time is inversely proportional to the sensing time.Furthermore,the transmission energy consumption will decrease as the transmission time decreases,which affects the energy efficiency of the system.Therefore,under certain interference constraints,the trade-off between the detection rate and the energy efficiency of the SU is an important problem.
The kernel thought of the reconfiguration capability provides reliable communication services using the free spectrum of the authorized system without causing harmful interference for authorized users.Once a band is used by a PU,two methods,switching to other free bands for communication or changing the transmission frequency or modulation scheme to avoid harmful interference for the PU,are used.The throughputs of primary and secondary users with dynamic spectrum sharing were studied in Refs[9-11].The spectrum and energy efficiency in spectrum sharing are further optimized by improving the sensing performance.Considering the constraints of the maximum transmission power,user quality of service requirements,interference limitations and primary user protection,the joint optimization of the spectrum sensing time and secondary user system power to improve the energy efficiency of cognitive networks is proposed in Ref.[12].An energy efficiency model based on the hybrid spectrum sharing mode is constructed by combining opportunistic spectrum access and underlay spectrum sharing to optimize the sensing time,the number of secondary users engaging in sensing and the transmission power to maximize the energy efficiency in Ref.[13].
Regarding the spectrum management and allocation security,there should be a platform for the current spectrum sharing approaches to connect the secondary users who borrowed spectrum and the primary users who lease spectrum.However,the platform is also vulnerable to attacks and requires considerable human resources for maintenance,which will lead to additional costs for both sides of the transaction.In addition,users’privacy may be compromised.To address these security threats,a degree of trust for both parties in a transaction process,which can ensure that both parties obtain the maximum utility and effectively improve the spectrum utilization,is set in Ref.[14].However,the amount of data is large,and the computational complexity is high.In contrast,the blockchain,which is a shared and immutable ledger that can provide a trusted channel for exchanging information and value,has many advantages.The spectrum transaction can be safely and securely stored in the block without relying on a third-party platform[15].In addition,a model to improve spectrum sharing in a decentralized manner through the blockchain and smart contracts without centralized methods for operations was proposed in Ref.[16].A spectrum sharing algorithm based on the blockchain and game theory to improve spectrum utilization,which has the advantages of decentralization and high-level trust was proposed in Ref.[17].Therefore,blockchain technology will be used in this paper as a platform for efficient and secure spectrum sharing transactions.
In summary,the relevant factors currently engaged in cognitive radio networks include the user profit,the throughput and energy consumption of SUs,etc.However,most related studies consider the ratio of SU throughput to energy consumption or independently consider the gain of SUs and PUs.It is necessary to study throughput in combination with energy consumption and transaction cost issues.Furthermore,the above mentioned literature only considers SUs that access PU spectrum resources through sensing.However,the spectrum resources of convenient and stable mobile network operators(MNOs)can also be used to ensure the transmission efficiency of secondary users.Based on the above problems,an optimization algorithm of the joint utility for secure hybrid spectrum sharing(JUSH)to improve the utility of cognitive radio networks is proposed in this paper.The main work is summarized as follows.
(1)A new cooperative spectrum sharing model in which an SU can use the spectrum resources of PUs and an MNO in a comprehensive manner to ensure a certain transmission rate is proposed.Considering the actual performance,a joint utility model with spectrum sensing and opportunity spectrum access is constructed.
(2)The proposed joint utility model is a nonconvex problem,and the model solution is split into two sublayer optimization problems.The upper layer uses the exhaustive method to solve for the optimal sensing time and the number of users engaged in sensing,and the lower layer uses the Dinkelbach and Lagrange multiplier method to solve for the optimal power allocation.
(3)Evaluate the joint utility performance of the secure hybrid spectrum sharing system proposed in this paper through simulations,and the results show that the proposed algorithm can achieve higher joint utility under various system settings.
The remainder of the paper is organized as follows.Section 1 introduces the system model proposed in this paper.The joint utility representation and the solution to the optimization problem are presented in Section 2.Simulation results are provided and analyzed in Section 3.Finally,conclusions are obtained in Section 4.
1 System model
1.1 Network model
Consider a network scenario in which there is a MNO,multiple PUs with licenced spectrum andNSUs without licenced spectrum that requires spectrum resources in a certain range of area,as shown in Fig.1.The MNO has sufficient spectrum bandwidth resources,and the SUs need to lease spectra for data transmission from the MNO or PUs.If SUs choose to use the PUs’free spectrum by spectrum sensing,they need to consume energy for spectrum sensing and information transmission.In return,SUs need to pay the PU the corresponding fee.If an SU leases the use of spectrum from the MNO,the required transaction cost is higher and thus less cost-efficient.SUs can choose to lease the spectrum resources of the MNO or the idle spectrum of a PU according to the needs of the current task and its own cost considerations.PUs are willing to lease free spectrum to form a consortium chain,which is jointly maintained by the PUs engaging in the formed blockchain,to ensure fair leasing.The rental records of PUs and the revenue of each PU are kept in the blockchain.
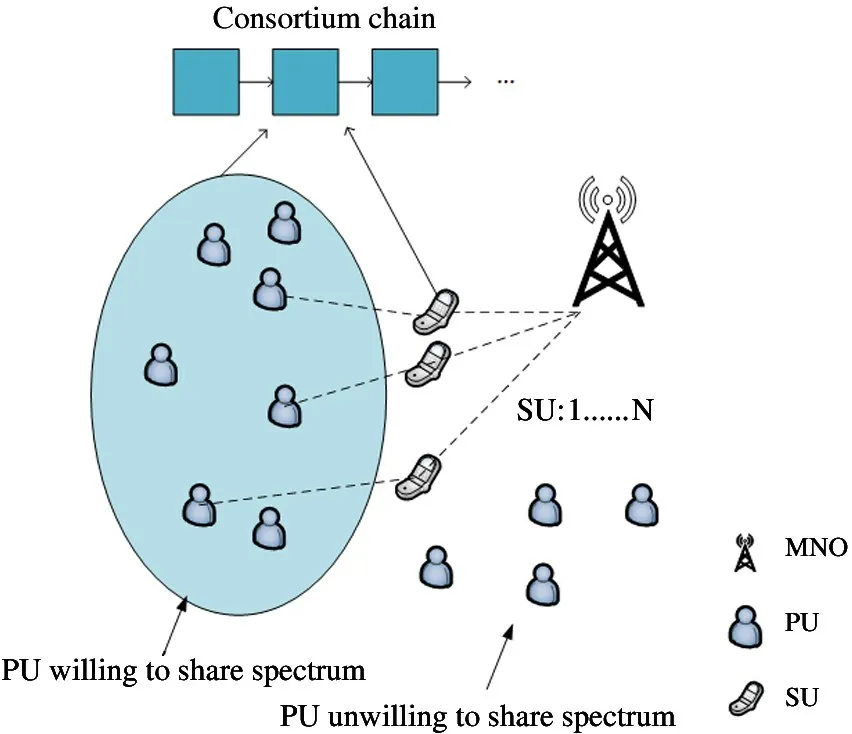
Fig.1 Network model
1.2 Spectrum sharing-based blockchain
A blockchain is a peer-to-peer decentralized ledger designed to efficiently record transactions between participants in a verifiable and permanent manner without relying on a trusted hub.Blockchain technology enables spectrum transactions to be executed in a distributed,transparent and secure marketplace environment.Consortium chains are not only an important application area for blockchain but also a new attempt at spectrum sharing methods.Users who want to engage in the consortium chain need to obtain a licence that is usually only open to members.By comparison,everyone can engage in transactions,as in the case of Bitcoin.The consortium chain raises the barriers to entry and improves security and privacy to address threats in the spectrum sharing process,including three possible threats.(1)malicious spectrum providers that occupy and interfere with other users’transmissions during leasing;(2)SUs that refuse to deliver the corresponding fees after a transaction is completed;(3)malicious trusted third parties that may leak users’private information,etc.
The transaction process for PUs with authorized spectra and SUs without authorized spectra is as follows.
(1)Transaction starts with the blockchain login of users who are the PUs willing to rent the free spectrum and SUs.Both users will obtain the information that has been authenticated on the consortium chain,including the price per quantity of the spectrum and the time of their rental.
(2)SUs obtain PUs’idle spectrum information through sensing.
(3)SUs apply to PUs for spectrum leasing,including the bands to be leased and the time required.
(4)Both parties make a transaction and record a list including the band information,amount of spectrum,cost and time of the traded spectrum.
(5)The PUs encrypt the transaction list and broadcast it to the entire network.
All transactions based on the blockchain will be verified by broadcasting instead of direct transactions between parties.The secure spectrum transaction environment can be established,and thereby the security and privacy protection of transactions can be ensured.
1.3 Hybrid spectrum sharing with spectrum sensing
Each time slot is represented asT,which is composed of sensing timeτ,reporting timeTrand data transmission timeTtr.The time frame structure is shown in Fig.2.The sensing time in a working cycle isτ,and the reporting time of each SU isTr.In the sensing stage,all SUs perform spectrum sensing at the same time.Then,the SUs report the local sensing information to the FC through a common channel.Furthermore,in the transmission stage,the SU decides whether to access a PU’s authorized spectrum according to the FC’s decision result.
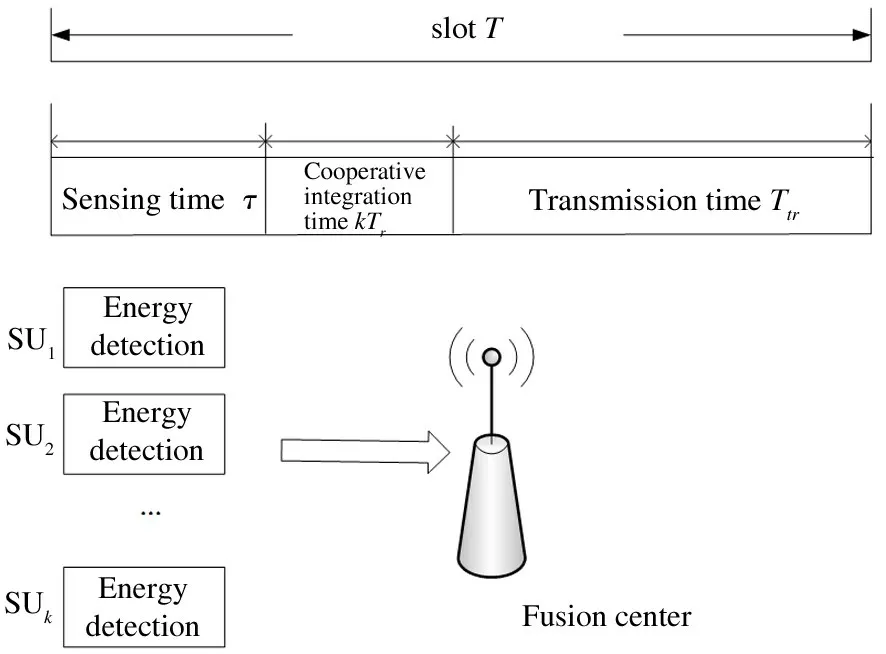
Fig.2 Time frame structure
The transmission time is denoted asTtr=T-τkTr.During the sensing time,each SU senses the state of the PUs,makes a local decision,and then sends the decision result to the FC through a dedicated reporting channel in accordance with TDMA(time division multiple access).
The PUs’state is sensed by energy detection[18],and the statistics are as follows.
H0:a PU is not occupied,and the channel is idle.
H1:a PU is occupied,and the channel is busy.
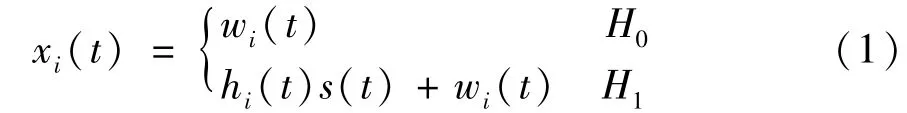
whereirepresents theith cognitive user,xi(t)is the received signal,s(t)is the primary user signal,wi(t)is the additive white Gaussian noise(AWGN),andhi(t)denotes the gain of the channel.hi(t)is considered time-invariant and can be denoted ashisince the coherence time is considered to be longer than the sensing time.
Energy detection is considered a good method for spectrum sensing without prior knowledge.The false alarm probability and detection probability for theith user on the AWGN channel are calculated as follows[19].
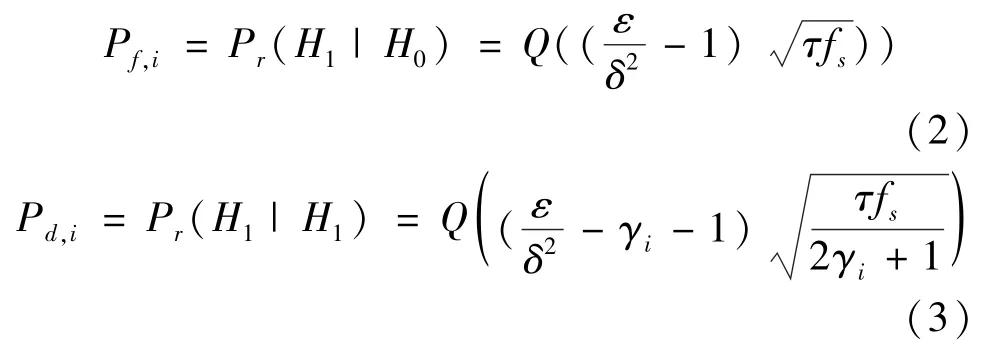
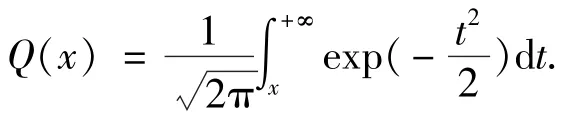
s∈{0,1}denotes the real state of a PU,where 0 indicates that the PU is idle and 1 indicates that the PU is busy.Furthermore,cs∈{0,1}denotes a PU’s perceived state,where 0 indicates that the SU perceives that the PU is idle and 1 indicates that the PU is perceived as busy.The false alarm probability is expressed asQf=Pr{cs=1|s=0},and the global detection probability is expressed asQd=Pr{cs=1|s=1}.All SUs report the local decision information to the FC,which makes the final decision according to the‘K-out-of-N’rule,withkbeing the FC decision threshold.Therefore,the false alarm probabilityQfand the detection probabilityQdof cooperative spectrum sensing(CSS)are expressed as follows[18].

In this paper,not only the throughput of the SUs but also the energy and transaction costs should be considered.The SUs sense the idle spectrum of a PU and then decide how to use the spectrum resources.DefineP(H0)=Pr(s=0)andP(H1)=Pr(s=1)to denote the probabilities that a PU is idle and busy,respectively.There are four different possible results through the perception of SUs.
(1)The FC correctly makes the decision that the real state of the PU is busy,and the probability of this occurrence is expressed asq1=Pr{cs=1|s=1}=P(H1)Qd.At this time,the PU’s state is sensed to be busy.Then,an SU chooses to use the spectrum of an MNO instead of the spectrum resources of a PU,i.e.,it completely uses the spectrum of the MNO.Furthermore,the SU transmits data with powerPM,the throughput of the SU is as follows.
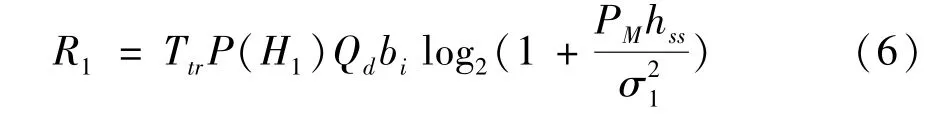
The energy consumption and transaction costs are denoted asE1=TtrP(H1)QdPMandC1=TtrP(H1)Qdbiμ1,respectively,wherebiis the amount of spectrum bandwidth required by the SU,hssis the channel power gain between the FC and the SU,σ21denotes the noise variance,andμ1denotes the price per unit of time per unit of bandwidth of the spectrum resources of an MNO.
(2)The FC incorrectly makes the decision that the state of the PU is busy,and the probability of this occurrence is expressed asq2=Pr{cs=1|s=0}=P(H0)Qf.At this time,the SU still transmits with powerPM.The throughputR2is calculated as
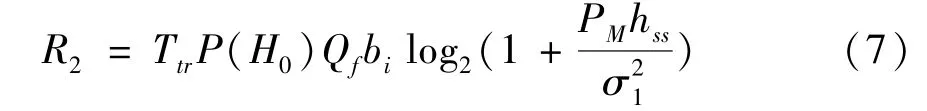
The energy consumption and transaction costs are denoted asE2=TtrP(H0)QfPMandC2=TtrP(H0)Qfbiμ1,respectively.
(3)The FC correctly makes the decision that the real state of a PU is idle,so the spectrum of the PU is also considered.The used spectrum of a PU is expressed asθbi,and the spectrum resources of an MNO are(1-θ)bi.At this time,the probability of this occurrence isq3=Pr{cs=0|s=0}=P(H0)(1-Qf),and an SU uses the spectrum resources of an MNO for data transmission with powerPMand the resources of a PU for data transmission with powerPP.The throughputR3is calculated as
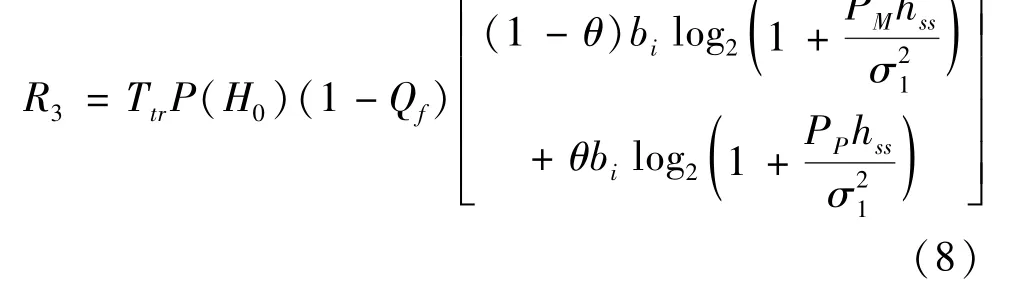
The energy consumption and transaction costs are denoted asE3=TtrP(H0)(1-Qf)[PM+PP]andC3=TtrP(H0)(1-Qf)[(1-θ)biμ1+θbiμ2],respectively.
(4)The FC incorrectly makes the decision that the state of a PU is idle,soq4=Pr{cs=0|s=1}=P(H1)(1-Qd).Then,an SU will use the spectrum resources of both an MNO and a PU,and the throughput is
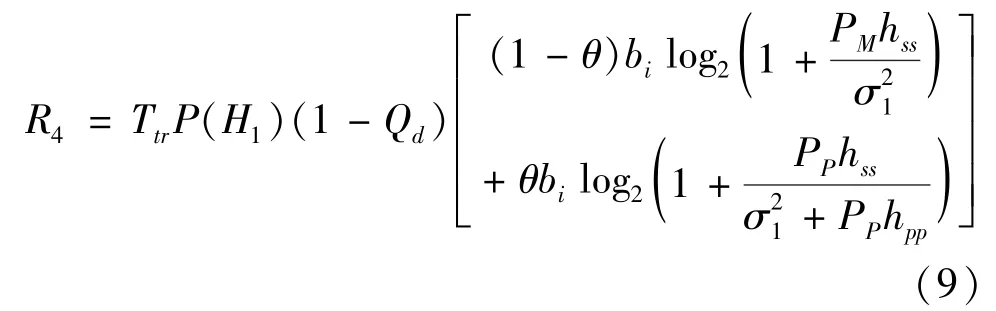
wherehpprepresents the channel gain when the master user makes the transmission,andPPhpprepresents the noise from the PU when the SU makes the transmission.
The energy consumption and transaction costs are denoted asE4=TtrP(H1)(1-Qd)[PM+PP]andC4=TtrP(H1)(1-Qd)[(1-θ)biμ1+θbiμ2],respectively.
2 Joint utility optimization for hybrid spectrum sharing
2.1 Joint utility function for hybrid spectrum sharing
Based on the above model analysis,the joint utility of the system,which is expressed as the ratio of the throughput to the energy consumption and transaction costs,is studied in this section.Among the components,the throughput of an SU can be expressed as

The normalized throughput is expressed as

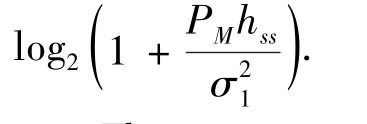
The energy consumed by the secondary user’s systemETmainly includes the sensing consumptionEs,the consumption of reporting the results to the FCER,the transmission consumption(E1+E2+E3+E4),and the base consumption energyEe,which can be expressed as
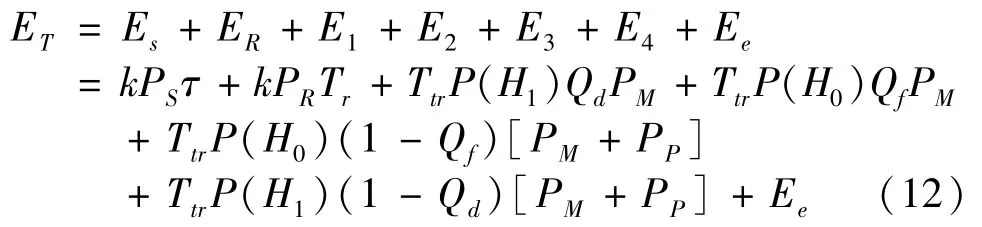
Furthermore,the total transaction costsCTconsumed by an SU can be expressed as
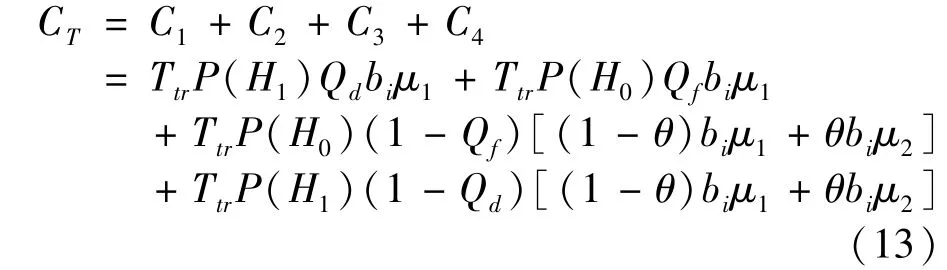
The energy consumption and transaction costs are jointly expressed asZ.
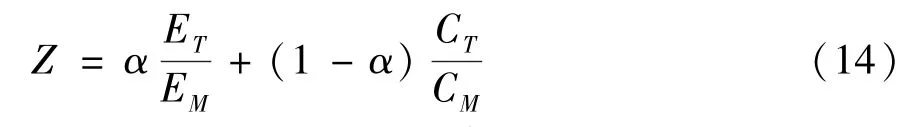
whereαis a weighting factor(0≤α≤1),and users can change the value ofαaccording to their needs.EMrepresents the maximum possible energy consumption,that is,the energy consumption generated when the entire time slot is completely used for data transmission with the maximum transmission power,namely,EM=PmaxT+Ee.Furthermore,Pmaxis the maximum transmission power of an SU;andCMis the maximum possible transaction costs,i.e.,when the entire time slot is fully used for data transmission using the MNO’s spectrum,CM=Tbiμ1.
To maximize the joint utility for secure hybrid spectrum sharing,the problem is transformed into an optimization problem with sensing timeτ,the number of SUs engaged in sensingk,and the optimal power allocation.Furthermore,the optimization problem should satisfy the constraints of the system minimum throughput,the SU maximum transmission power and the PU maximum interference.Considering that joint utility is defined as the ratio of the throughput to the energy consumption and transaction costs per unit of time,the problem is modelled as
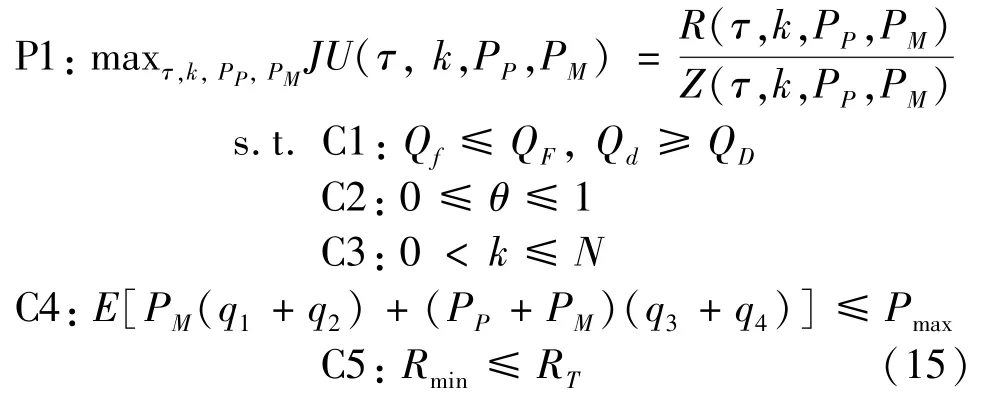
where C1 denotes the upper limit of the false alarm probability and the lower limit of detection probability,C2 denotes the proportion of hybrid spectrum in which SUs select an MNO or a PU,C3 denotes the range of the numbers of secondary users engaging in spectrum sensing,C4 denotes the maximum transmission power of SUs andRminis the minimum throughput of SUs in C5.
2.2 Problem analysis and solution
Considering that P1 is a nonconvex function,the sensing time and the number of SUs engaging in the sensing will be fixed to facilitate the calculation,and the transmission powersPPandPMof the SUs will be allocated.

The numerator and denominator of P2 are both positive continuous functions.The optimization problem is divided into two sublayer optimization problems using a two-layer optimization algorithm.The upper layer is the optimization of the sensing time and the number of SUs engaged in spectrum sensing,and the lower layer is for optimizing the transmission power at a given sensing time.According to Dinkelbach’s theory,the fractional problem can be transformed into an equational parametric optimization problem,i.e.,P3:
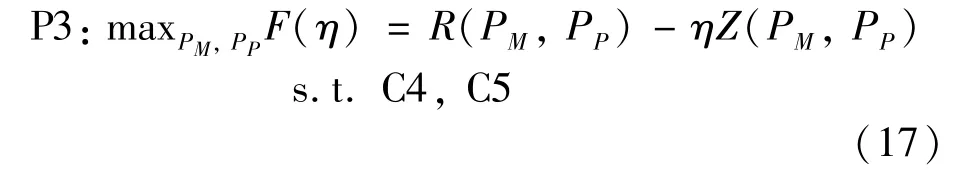
whereηis a nonnegative parameter,and Conclusion 1 describes the relationship between P1 and P3.
Conclusion 1:η*is the optimal joint utility andPandPare the optimal power allocation when and only whenη*,P,andPsatisfy the following equation.
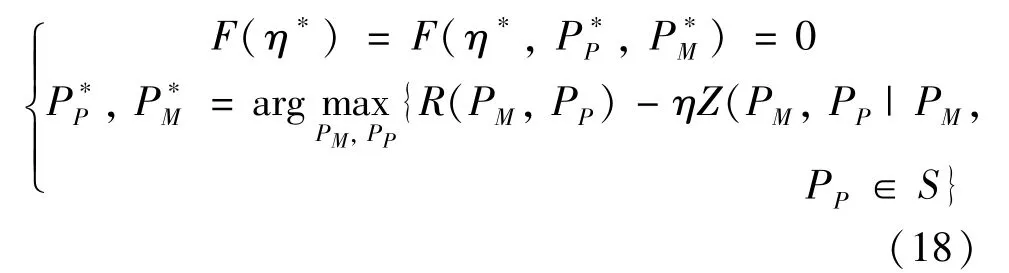
whereSis the feasible region ofPMandPP.F(η)is a convex function ofPMandPP,andηis fixed.According to Dinkelbach’s theory,the optimal solution of problem P3 is the optimal solution of problem P2;and P3 is a convex function,which can be solved by the Lagrange multiplier method.
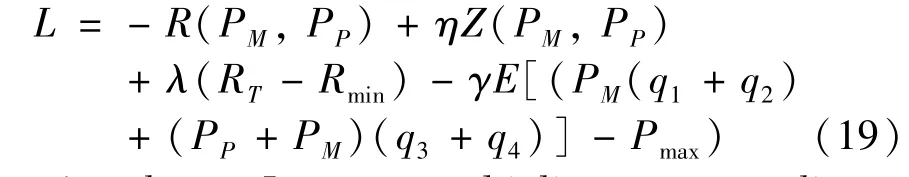
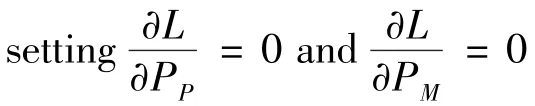
To obtain the optimalλandγ,the gradient descent method is used to iteratively updateλandγ:
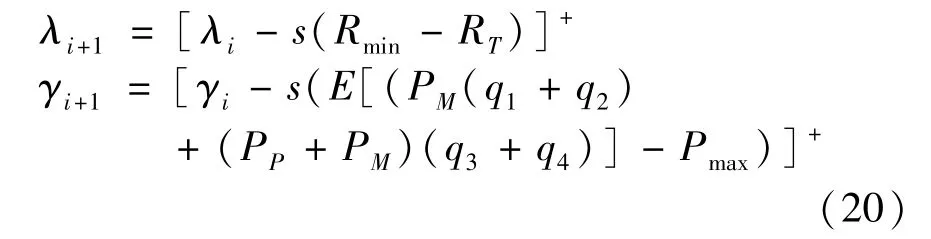
wheresandidenote the step size and number of iterations,respectively.By iterating Eq.(20)until the updatedPandPmake Eq.(18)satisfyF(η*)≤ε1,the optimal solution at this time is obtained,whereε1denotes a very small number.
The algorithm steps are as follows.
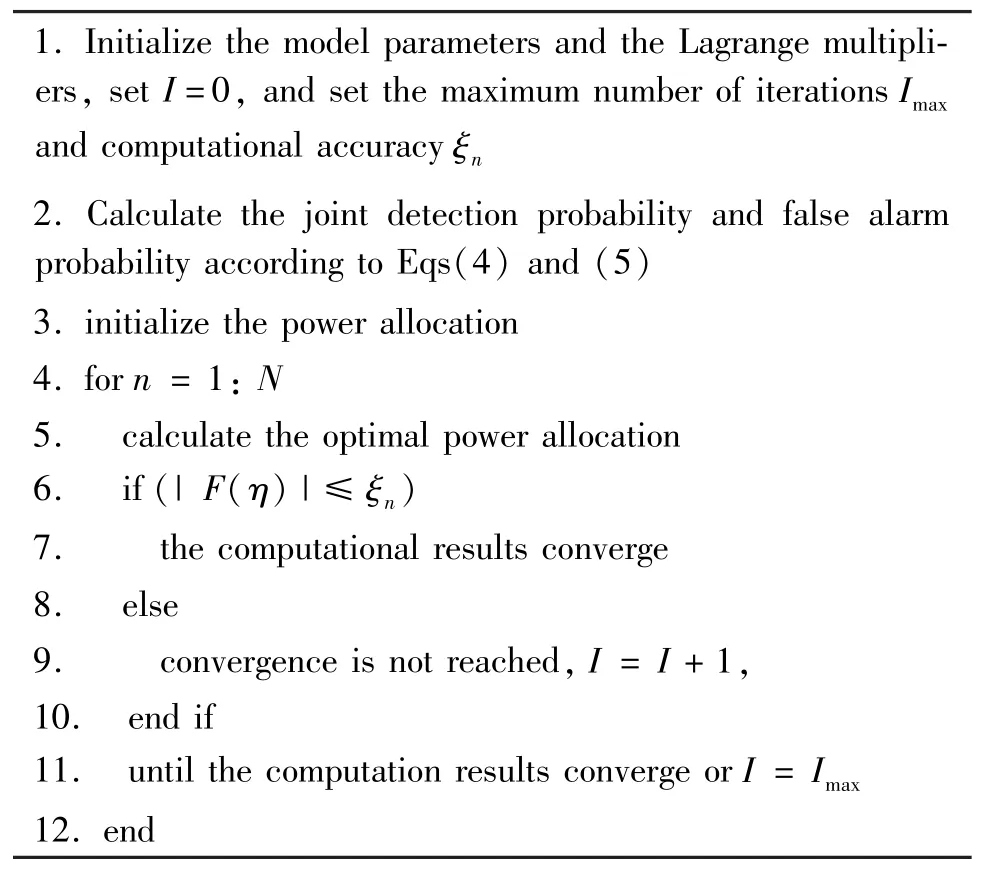
1.Initialize the model parameters and the Lagrange multipliers,set I=0,and set the maximum number of iterations Imax and computational accuracyξn 2.Calculate the joint detection probability and false alarm probability according to Eqs(4)and(5)3.initialize the power allocation 4.for n=1:N 5. calculate the optimal power allocation 6. if(|F(η)|≤ξn)7. the computational results converge 8. else 9. convergence is not reached,I=I+1,10. end if 11. until the computation results converge or I=Imax 12.end
The optimal power allocation problem can be solved quickly by an iterative procedure,which is described by the above algorithm.Approximately,the optimal sensing time can be found by a one-dimensional exhaustive search.In this paper,the optimal power is obtained by the above algorithm.
3 Simulation analysis
This section will conduct data simulations for the above algorithm.The joint utility optimization problem of the SU is considered in a certain area,including an MNO,a PU with licenced spectrum,and SUs.The algorithm proposed in this paper is also compared with three different methods,namely,no hybrid spectrum sharing,fixed sensing time,and single node sensing.No hybrid spectrum sharing means only using the free spectrum of PUs through cooperative spectrum sensing,not using the spectrum resources of an MNO,and taking the joint utility obtained by the best sensing time.The joint utility of the fixed sensing time is based on the method mentioned in this article.The single node sensing approach means that no cooperative spectrum sensing is used and only the sensing result of a single node is taken as the basis of whether an SU uses a PU’s spectrum for data transmission,and the joint utility is obtained by using the hybrid spectrum sharing method proposed in this paper.The parameters are shown in Table 1.
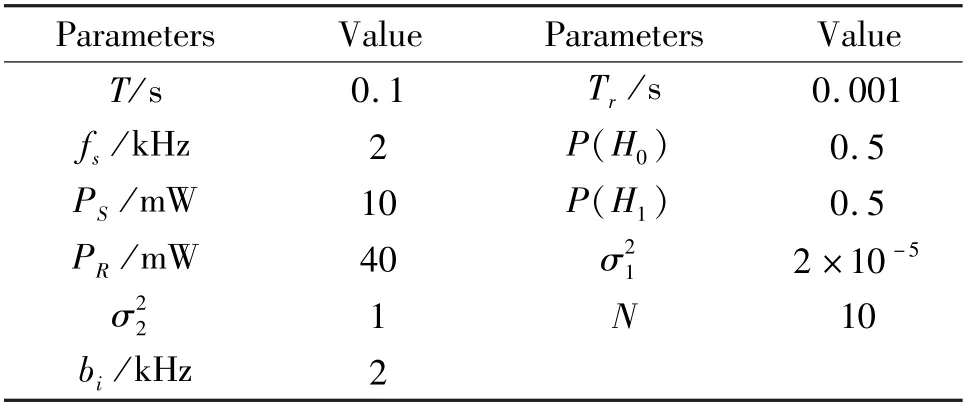
Table 1 The values of the variables involved in the simulation
First,the security and energy efficiency of using spectrum blockchain is analysed.Additionally,the JUSH optimization algorithm used in this paper is compared with two other methods:the joint utility for spectrum sharing based on a third-party platform(JUTP)optimization algorithm and the joint utility for spectrum sharing based on third-party with setting the degree of trust(JUTD)optimization algorithm for both parties of the transaction.The JUSH optimization algorithm records the transaction information through the blockchain when the primary and secondary users perform spectrum sharing.In addition,under the JUTP optimization algorithm,the transaction parties only perform transactions on a third-party platform.This is more costly to maintain and creates an extra cost for both parties to the transaction.The JUTD optimization algorithm sets a trust degree for both transaction parties when the primary and secondary users engage in spectrum sharing on a third-party platform.Where there is dishonest behaviour,the trust degree can affect the success rate of the next transaction.For instance,the PU will maliciously occupy the frequency band used by the SU during the transaction.As the SU does not bear the corresponding cost[17],this improves the SU’s transmission rate and increases its throughput.
Fig.3 represents the relationship between the sensing time and an SU’s joint utility from spectrum transactions by primary and secondary users based on different methods,wherek=5 and weighting factorα=0.5 are used for cooperative spectrum sensing with hybrid spectrum sharing.As the Fig.3 shows,JUSH can achieve higher joint utility.Due to blockchain features,such as openness and transparency,through which the information and transaction records of both parties to a transaction are public,the probability of dishonest behaviour to a transaction can be effectively reduced,thus effectively increasing the throughput of SU.In addition,neither side of the transaction has to pay higher costs to maintain the third-party platform,thus achieving higher joint utility.Although setting the trust degree of both sides of the transaction on the third-party trading platform can also effectively reduce the probability of dishonest behaviour between both sides of the transaction,a higher cost nevertheless incurs to maintain the third-party platform.As a result,JUSH’s performance far exceeds spectrum sharing trading methods that do not utilize blockchain.
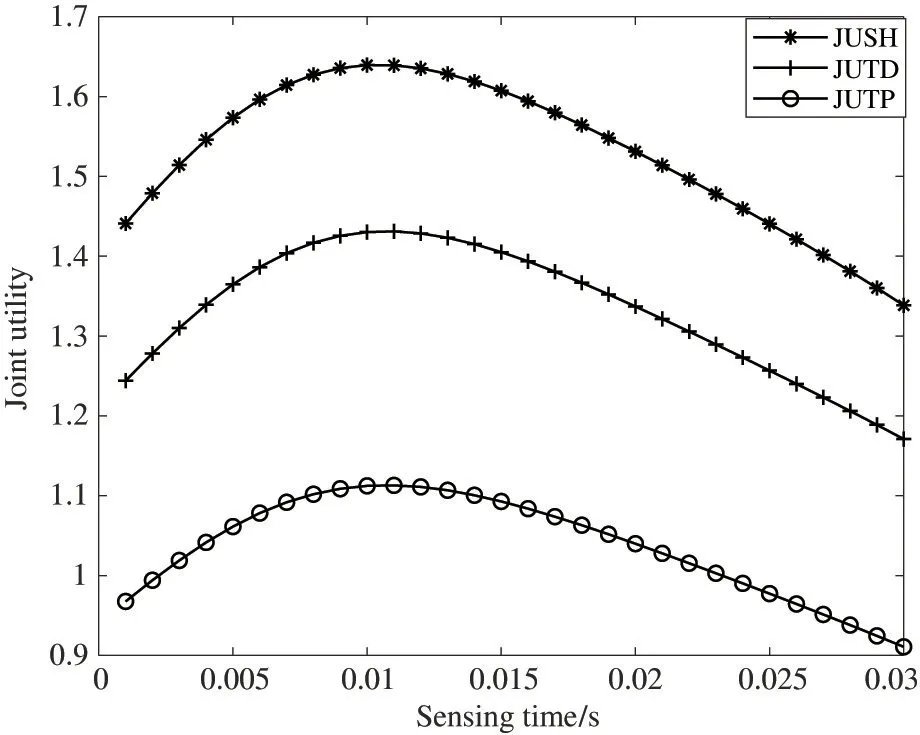
Fig.3 Joint utility versus sensing time for spectrum sharing based on different methods
Fig.4 shows the joint utility versus sensing time for different numbers of cooperative sensing users,and the number of users engaged in cooperative spectrum sensing is set tok=4,k=5,k=6,k=7,andk=8.The weighting factorα=0.5.The figure shows that the joint utility of the system can reach the highest value atτ=0.11 s whenk=5.This is because the detection probability and false alarm probability converge at different times when different numbers of sensing users are engaged in sensing;and as the number of cooperative users engaged in sensing increases,the false alarm rate decreases and the detection rate increases,thereby improving the transmission success rate of the system.Whenk>5,the joint utility of the system decreases askincreases.In the sensing model,the false alarm rate and detection rate of the system stabilize when the number of cooperative users engaged in sensing reaches a certain number,and the energy consumption for sensing and sending sensing messages increases at this time,thus leading to a decrease in the joint utility of the system.It can also be seen in Fig.4 that although the maximum joint utility is achieved atk=5 andτ=0.11 s,the joint utility atk=5 is lower than that atk=4 whenτ<0.07 s.This is because when the number of SUs involved in sensing is low,the SUs can more readily achieve a higher detection rate,thereby realizing a higher joint utility more quickly.However,the false alarm rate is also higher during this time,leading the sensing time to increase.Subsequently,the false alarm rate and detection rate are gradually optimized and a higher overall joint utility is attained atk=5.
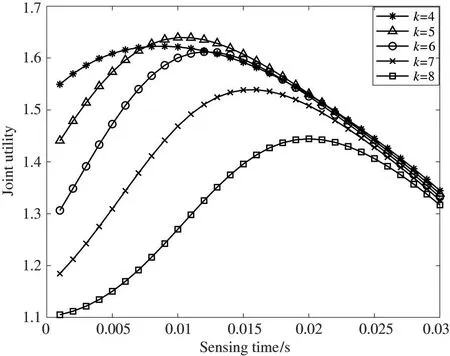
Fig.4 joint utility versus sensing time for different numbers of cooperative sensing users
Fig.5 shows the utilities of different algorithms for different maximum transmission powers of SUs,where the number of engaged cooperative spectrum sensing usersk=5,the weighting factorα=0.5 and the fixed sensing timeτ=0.1 s.The algorithm proposed in this paper is compared with the fixed sensing time method,the single node sensing method and the no hybrid spectrum sharing method;and the results show that the proposed algorithm obtains the maximum transmission power for users based on the joint utility of the system.The proposed algorithm adopts hybrid spectrum sharing,which can guarantee the throughput and reduce the transmission energy consumption;therefore,the proposed algorithm can achieve the highest joint utility.No hybrid spectrum sharing means that when no free spectrum of a PU is sensed,an SU adopts the spectrum of an MNO;conversely,when free spectrum is sensed,the spectrum of a PU is fully adopted,so the throughput is slightly reduced.In the single node sensing process,the detection probability and the false alarm rate are higher when the spectrum of an MNO accounts for a larger proportion,which results in high energy consumption and transaction costs and low joint utility.
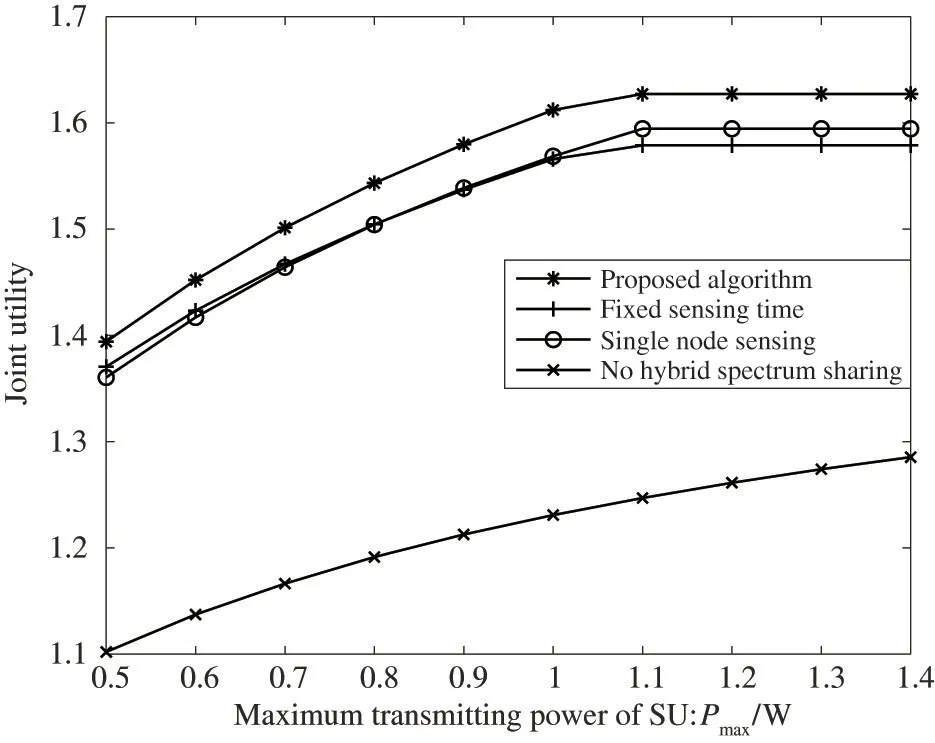
Fig.5 Average joint utility versus sensing time for different values of Pmax
Fig.6 shows the relationship between the number of SU engaged in cooperative spectrum sensing and the joint utility in the case of the optimal solution of the proposed algorithm.The horizontal coordinate is the number of SU,k=1,2,4,6,8,10,respectively,and the vertical coordinate is corresponding joint utility maximum,as comparisons are the spectrum sharing method based on a third-party platform and the spectrum sharing method that sets the degree of trust for both parties of the transaction.As can be seen from Fig.6,the joint utility obtained by the optimal solution of the proposed method in differentk-values is higher than that of the two comparison algorithms.Because the proposed algorithm is based on the blockchain platform,it reduces the probability of SU occupancy and reduces the cost of maintaining the third-party platform,so the proposed algorithm can achieve higher joint utility.
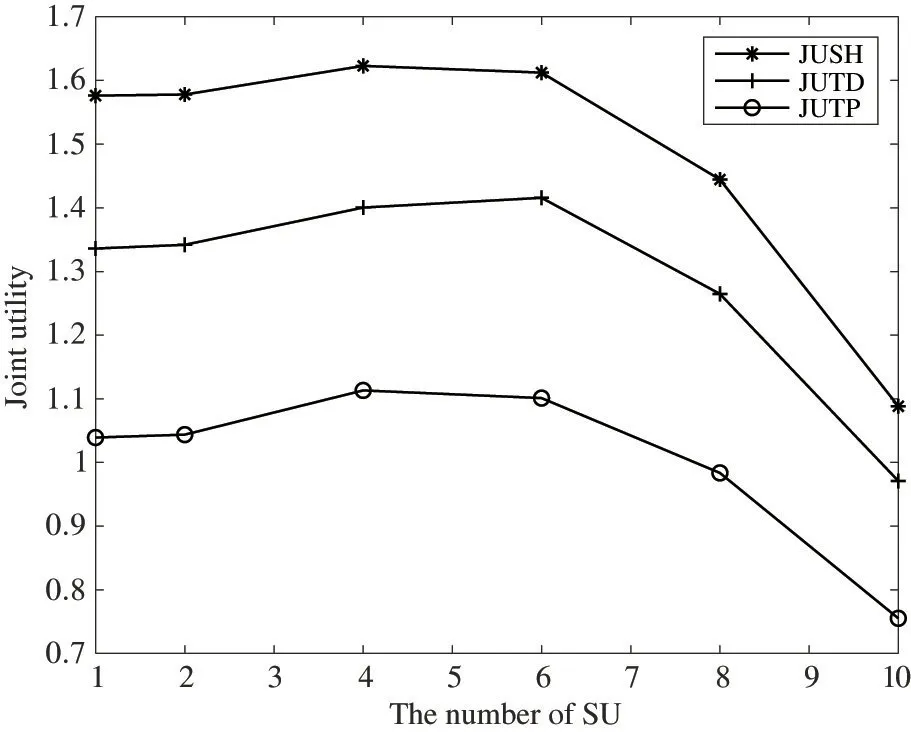
Fig.6 Joint utility versus the number of SU under the optimal solution
Fig.7 shows the variation of the joint utility of different spectrum sensing methods under different minimum throughput constraints,where the number of cooperative spectrum sensing usersk=5,the weight factorα=0.5,andPmax=1.In the proposed algorithm,when the sensing time increases,Qdincreases andQfdecreases,and the growth rate of the throughput is higher than the growth rate of the energy consumption and transaction costs;thus,the joint utility increases.QdandQftend towards stability whenτ>0.11 s,the throughput gain from sensing performance no longer increases,and the energy consumption increases;therefore,the joint utility decreases.QfandQdvary slightly during single node sensing,and the growth rate of the throughput is lower than the growth of energy consumption and transaction costs;therefore,the joint utility gradually decreases.However,when the minimum throughput constraint is larger,the maximum joint utility achieved by the proposed method shows less improvement than that attained through the single-node sensing method.The reason for this is that,in the single-node perception spectrum sharing algorithm,the time spent by the user on sensing and collaborative fusion time is shorter.Therefore,single-node sensing methods can also achieve high joint utility when the perception time is short.However,as sensing time increases,the joint utility of the single-node sensing method gradually decreases.
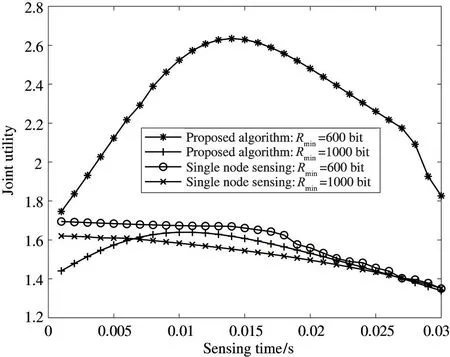
Fig.7 Joint utility versus sensing time under different minimum throughput constraints
Fig.8 shows the relationship between the maximum transmission power and the throughput for different spectrum sharing methods,where the number of engaged cooperative spectrum sensing usersk=5 and the weighting factorα=0.5.It can be observed that the throughput of different methods gradually increases as the maximum transmission power increases,and the maximum throughput can be achieved by single node sensing.During the single node sensing process,the number of SUs engaged in cooperative sensing is small.Then,less energy is consumed for the sensing and fusion process,and a large amount of time is spent in transmitting data.The algorithm in this paper with hybrid spectrum sharing achieves a greater throughput.The throughput of no hybrid spectrum sharing is lower because only the available free spectrum of the PU can be used.
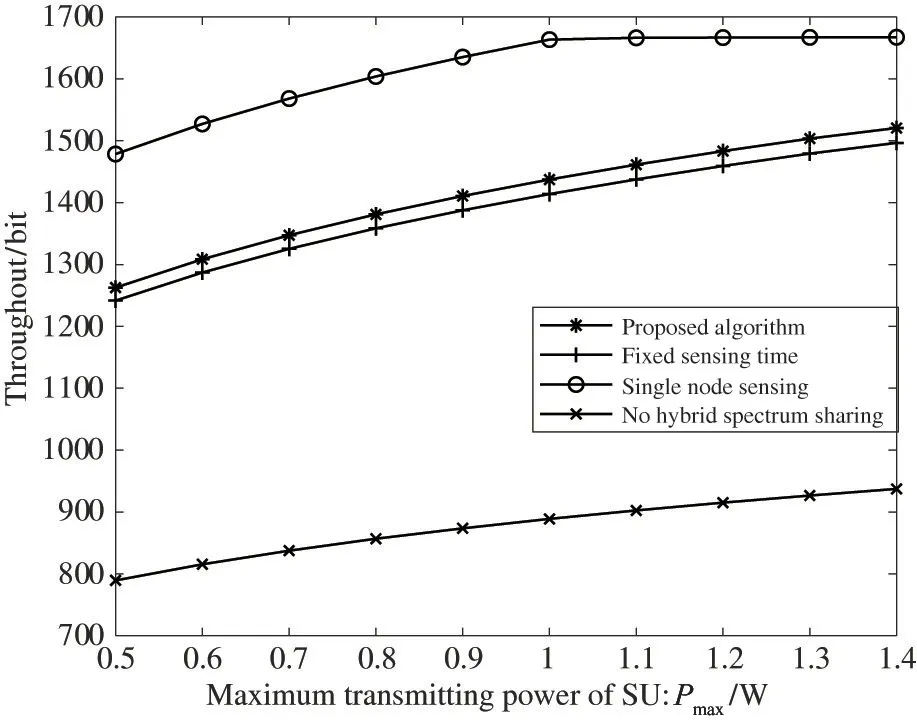
Fig.8 Maximum transmission power versus throughput for different spectrum sharing methods
Fig.9 gives the joint utility function of the system versus the sensing time for different weighting factors,where the number of cooperative spectrum sensing usersk=5,andPmax=1.Whenα=0,the utility function of the system behaves as the ratio of the throughput to transaction costs.Whenα=1,the utility function of the system behaves as the ratio of the throughput to energy consumption.When 0<α<1,the utility function is converted into joint utility,and the value ofαcan be changed according to the importance of transaction costs and energy.Fig.9 shows that the trend of the utility changes under three different weights first increases and then decreases.The best sensing time is approximately 0.12 s when the false alarm rate and detection probability are regionally stable,and the sensing efficiency is the highest;therefore,the utility will also reach the maximum.
4 Conclusion
To improve the spectrum efficiency,cost efficiency and security,a joint utility optimization algorithm that combines the free spectrum of authorized users and the leased spectrum of mobile network operators is proposed.The joint utility function is optimized by considering the throughput,energy consumption and cost issues of subscribers.The nonconvex problem is transformed into a convex optimization problem using the Dinkelbach method,and the Lagrange multiplier method is used to optimize the sensing time,the number of users engaged in collaborative sensing,and the transmission power of secondary users.Compared with other algorithms,the algorithm proposed in this paper can achieve higher joint utility under the constraints of the minimum throughput and maximum transmission power.
杂志排行
High Technology Letters的其它文章
- Design and implementation of near-memory computing array architecture based on shared buffer①
- Adaptive cubature Kalman filter based on variational Bayesian inference under measurement uncertainty①
- Design and experimental study of active balancing actuator driven by ultrasonic motor①
- Trajectory tracking control of characteristic model for nonplanar hex-rotor UAV①
- The adaptive distributed learning based on homomorphic encryption and blockchain①
- HOPE:a heterogeneity-oriented parallel execution engine for inference on mobiles①
