Airborne GNSS-Receiver Threat Detection in No-Fading Environments
2023-01-07OmidSharifiTehrani
Omid Sharifi-Tehrani
Abstract: Jamming and spoofing detection of global navigation satellite systems (GNSS) is of great importance. Civil and military aerial platforms use GNSS as main navigation systems and these systems are main target of threat attacks. In this paper a simple method based on different empirical probability density functions of successive received signal powers and goodness of fit technique is proposed for airborne platforms such as unmanned aerial vehicle (UAV), in no fading environment. The two different paths between UAV-satellite and UAV-threat, experience different empirical probability density functions which can be used to distinguish between authentic and threat signals. Simulation results including detection and false alarm probabilities show good performance of proposed method as well as low computational burden.
Keywords: detection; global navigation satellite systems (GNSS); jamming; spoofing; unmanned aerial vehicle
1 Introduction
Jamming, interference and spoofing immunity is one part of the most important issues in global navigation satellite systems (GNSS) [1].Demands for resistance of GNSS against jamming and spoofing in aerial platforms have been increased in recent decades. Unmanned aerial vehicles (UAV), helicopters, fighters and commercial aircrafts use GNSS as primary navigation system.
Also other alternative avionic systems like inertial navigation system (INS), Gyro, magnetic compass, very-high-frequency omnidirectional range with distance-measuring equipment(VOR/DME) and tactical air navigation(TACAN) are used as auxiliary navigation aids,but primary systems that are responsible for navigation are global positioning system (GPS),GLONASS, GALILEO and other GNSS. Due to weak signals of GNSS satellites received by aerial and ground-based platforms, intentional and unintentional interferences can easily disrupt GNSS services partially or completely [2]. Thus,early detection of jamming and spoofing as modern threats can help users to make decision and do preemptive or defensive actions. Different algorithms and methods have been developed in detection domain. Some methods are based on transfer domain such as fast Fourier transform(FFT), short-time Fourier transform (STFT)and spectrogram [3]. Eigenvalue and eigenvector analysis in conjunction with Wigner-Ville and Marcenko-Pastur laws are another methods [4, 5].Space-time adaptive processing (STAP) by using antenna array is one of the most powerful methods in detection and mitigation of unwanted signals but they have high computational complexity and hardware burden [6-11]. Some algorithms are based on normality tests and have blind spots [12-14]. The monitoring of possible distortions in the received signal correlation, can be used for spoofing detection. This method is called ratio-metric [15]. The disadvantage of this method is the need for post-correlation calculations. In [16] the pseudo-range differences method is proposed for a single receiver, capable of detecting simplistic and intermediate spoofing threats. This method also requires post-correlation calculations. Signal quality monitoring(SQM) technique is another method for spoofing detection which is spoofing detection effectiveness utilizing a single SQM metric, and is conditional and limited based on the signal extracted features [17]. Obviously the computational burden of this method is not low. The strategy of combining several metrics can improve the performance of the defense, in terms of detection and false alarm probabilities. Several methods have been introduced in this regard including combination of SQM, carrier-to-noise moving variance, moving average, signal distortion, etc.Although the performance gets better through metrics combination, the complexity increases as well [18-21]. Using signal power measurements is one of the simple methods to detect GNSS spoofing attack [22, 23]. Although it has low computational complexity, the performance is lower than other newer methods. Its performance could deteriorate if the spoofer is smart enough to handle the power of the threat signal. Other methods such as artificial neural networks (ANN) and wavelet transform have also been used in this regard [24-27]. Apart from which method to use,simplicity and computational complexity are two important parameters when hardware implementation and real-time performance matter. Most of aforementioned algorithms have high computational complexity. In this paper, a new method based on empirical probability density function comparison is introduced for utilization in unmanned aerial vehicles, as well as other aerial platforms, which has low computational complexity and can be used as early detection and warning. The proposed method takes advantage of aerial platform movement and uses successive received signal powers. Some of the existing methods for spoofing detection that are based on the power measurements, simply compare the received signal power with an known average power and if it is greater than the average threshold, it is concluded that the signal is spoofing and not authentic. But the performance will get worse if the spoofer is smart enough to control the transmitted power accordingly. The proposed method in this paper is based on the distribution of the power which means the two different paths between UAV-satellite and UAVthreat, experience different empirical probability density functions and thus no function of the average received power threshold. Hence it can be assumed stand-alone. This paper is organized as follows. In section 2 and 3 the problem and scenario assumptions are stated. In section 4 the proposed algorithm is described and finally, simulation results and conclusion are provided.
2 Problem Statement
We can model the received signal from theith satellite as [5, 28]
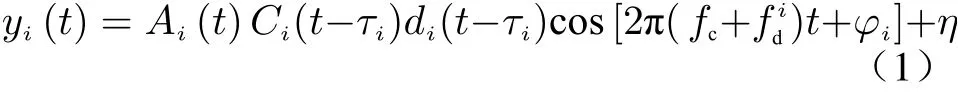
whereAi(t) is the signal amplitude which is related to theith satellite power amplifier (PA),is theith GPS signal Doppler frequency,φiis the random phase of signal,fcis the carrier frequency,Ci(t) is the unique spreading code of theith satellite,di(t) is the navigation message,τiis the channel delay,ηis the receiver noise, andtis the index of time. The product ofAi(t)Ci(t)di(t)can be assumed like a modulation factor for the cosine base signal. The received GNSS radio frequency (RF) signal from theith satellite, in the receiver is modeled as
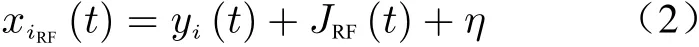
whereJRF(t)=AJcos(2πfJt+φ0) is the jammer signal,fJis the jammer frequency,AJis the jammer signal amplitude,φ0is the jammer initial signal phase andηis receiver additive white Gaussian noise. Jamming (J) to noise (N) ratio isJ/N=A2J/2ηand jamming to signal (S) ratio isJ/S=A2/A2. There are three necessary observa-Jitions for GPS which are pseudo-range, Doppler and carrier phase measurements.
3 Scenario Assumptions
The aerial platform flies with nearly fixed altitude which is called cruise altitude. Maximum altitude of UAV is known and is approximately 40 000 feet. The minimum and maximum speeds are known which are 120 km/h to 300 km/h with nominal cruise speed between 150 km/h to 200 km/h. The operational radius of threat source is known and limited. Threat source is a static ground-based / maritime single-spot narrowband one. UAV is at the distance of 10 km away from threat and ground threat power is such that in the distance of 10 km (UAV position) is equal to authentic GPS signal power received by UAV from GNSS satellite (carrier to threat ratio is 0 dB). UAV velocity is fixed and equal to 180 km/h which is equal to 262.5 Hz Doppler relative to ground threat and its motion is toward the threat source. The assumed scenario is shown in Fig. 1.
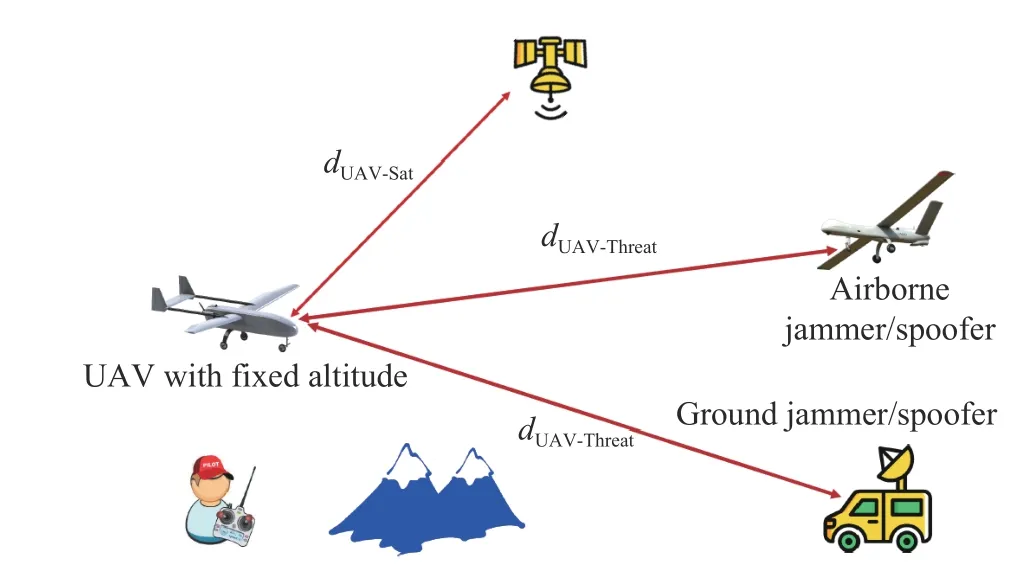
Fig. 1 Assumed scenario in no fading environment
4 Algorithm Description
Because of fixed velocity UAV motion to threat zone, the distance between UAV and groundbased jammer/spoofer could be considered as a uniform random variabledUAV-Threat~U(a,b).Therefore by utilizing received signal power relation in logarithm domain we have
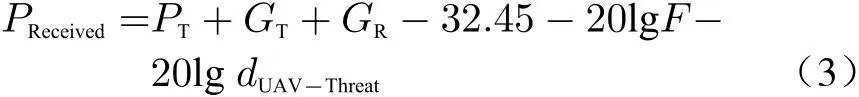
wherePT,GTandGRare transmit signal power,transmit antenna gain and received antenna gain respectively and are considered as constant values in decibel,Fis the frequency of the signal,andPReceivedis the received power. Hence we can approximately say
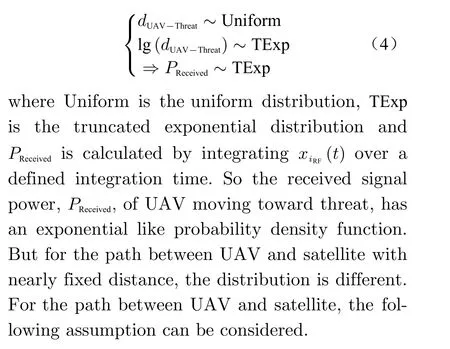
4.1 Normality Assumption for UAV Altitude Changes
Because in the cruise profile operation of UAV,the altitude is not usually fixed and has few changes including increasing and decreasing as pseudo random, so the distance random variable between UAV and satellite is considered as a normal random variable in which the mean is equal to UAV cruise flight altitude and variance is equal to few changes in altitude. So we can approximately say

wheredUAV-SATmeans the distance between UAV and SAT,μUAV-SATmeans the mean value, andσUAV-SATmeans the standard deviation. Because the logarithm of this random variable is used, it is necessary to study its logarithm behavior. For simplicity we assume that the random variable is standard normal.
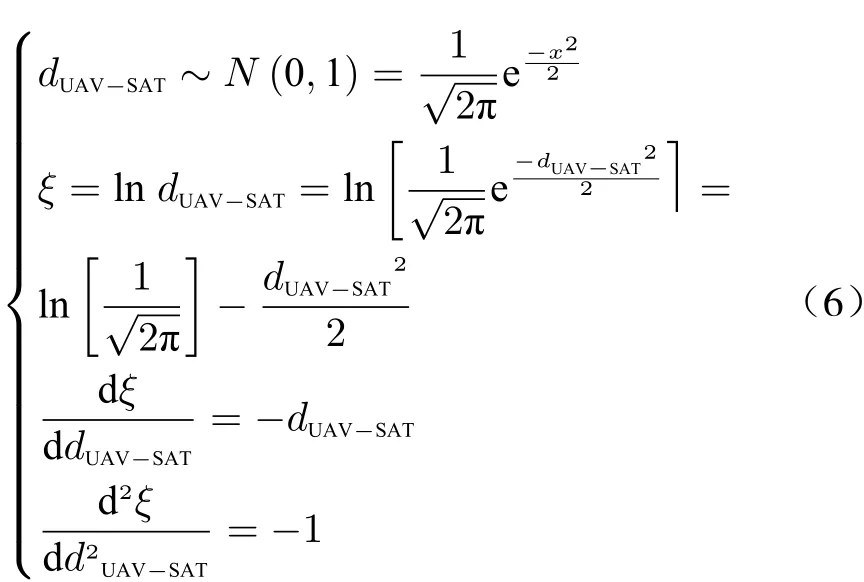
Thus, the probability density function (PDF)has log-concavity feature and is a log-concave function. Prekopa [29-31] proved that log-concavity feature of functions is also transferred to their integrals.
1) Theorem 1
Suppose thatgis a probability density function with support (a,b) andGis its cumulative distribution. Ifgis continuously differentiable and has log-concavity feature over (a,b), thenGis also log-concave over (a,b) [29, 30].
2) Theorem 2
AssumeGis a function with positive values,twice differentiable with support (a,b).Tis a uniform function and twice differentiable from(a′,b′)to (a,b)=(T(a′),T(b′)). FunctionG︿with support (a′,b′) is defined such that for allx ∈(a′,b′)we haveG︿(x)=G(T(x)). In this case ifGhas log-concavity feature andTtransform is a concave function, thenG︿will be log-concave as well.
3) Proof


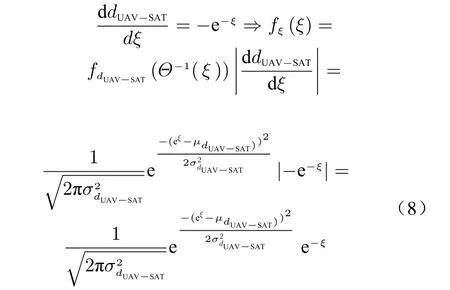
wherefξis the PDF andfdUAV-SATis PDF ofdUAV-SAT.So the UAV successive received signal powers from satellite have a different probability density function. Now by utilizing different empirical probability density functions, detection of threat is done.
4.2 PLGoF Proposed Method
In this method, we use empirical probability density function comparison and their differences.Goodness of fit (GoF) method based on mean squared error (MSE) function explores whether a sample dataset comes from a set with specific distribution or not. So the hypothesis test can be written as

wherePReferencemeans the reference probability to compare with. GoF relation based on MSE cost function is

whereNis the sample size,xis observed values from histogram binning process of received signal powers andxReferenceis expected values form histogram binning process of received signal powers in learning phase. Fit output value has different values for authentic and threat signal empirical cumulative distribution functions (CDF). Adequate threshold level is selected based on Monte Carlo (MC) simulation trials. Path-loss goodness of fit (PLGoF) algorithm steps are depicted in Fig. 2.

Fig. 2 Entity relationship diagram: (a) proposed method steps; (b) learning phase
4.3 Learning Phase
In the proposed method, GNSS authentic signal features are used as reference. Thus these features should be obtained in clear environment.This phase is learning phase and is depicted in Fig. 2.
PLGoF algorithm steps are summarized in Tab. 1.

Tab. 1 PLGoF algorithm steps summary
5 Simulation Results Utilizing Real GPS Signal Dataset
In this section by using real GPS signal dataset,performance of the proposed Algorithm is evaluated and compared with some other methods(Anderson-Darling (AD), Jarque-Bera (JB) and Lilliefors (LILLIE)). Sampling frequency is 6.4 MHz, central frequency is 1.575 42 GHz, 5 MHz span and the number of the recorded samples is 16 383 488 which are captured by Tektronix RSA3408A Real-Time Spectrum Analyzer, Rojone A-GPSA95NS antenna, Rojone AMA-061B amplifier and direct current (DC) block [32].Simulations are based on the MC with 1 000 trials. The α-significance level is set to be 5%. The spoofing signal is generated as GPS signal recorddelay-broadcast scenario. Simulation results based on detection and false alarm probabilities are depicted in Fig. 3 and Fig. 4 in the presence of jammer and spoofer threat. As shown, based on assumed scenario and setting, the proposed method provides better detection probability in longer distances than other compared methods.Also, it provides false alarm probability below 10% as others which nearly confirms the preset α-significance level. In Fig. 5, typical MC simulations for different selected threshold levels are provided. A comparison between different algorithm features in the scope of this article application is done in Tab. 2.
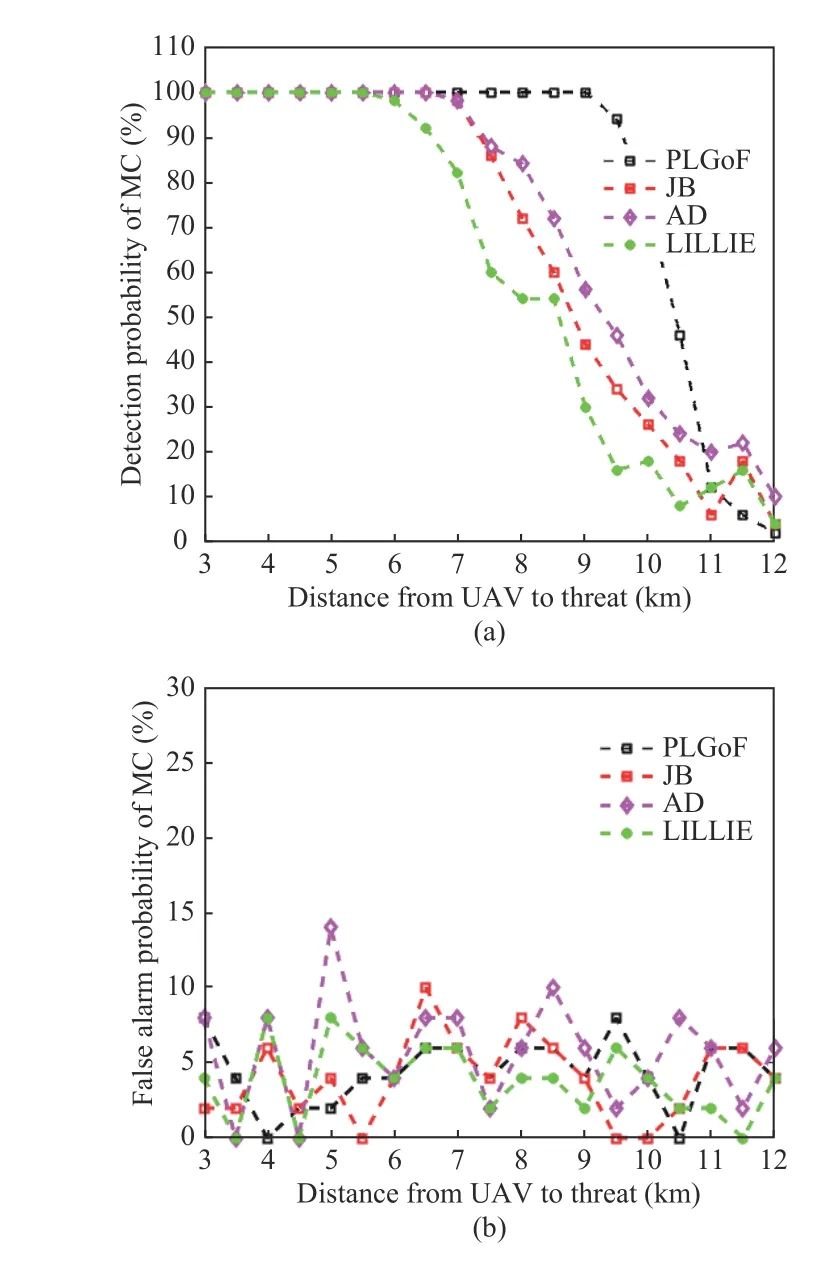
Fig. 3 Simulation results in the presence of jammer: (a) detection probabilities; (b) false alarm probabilities
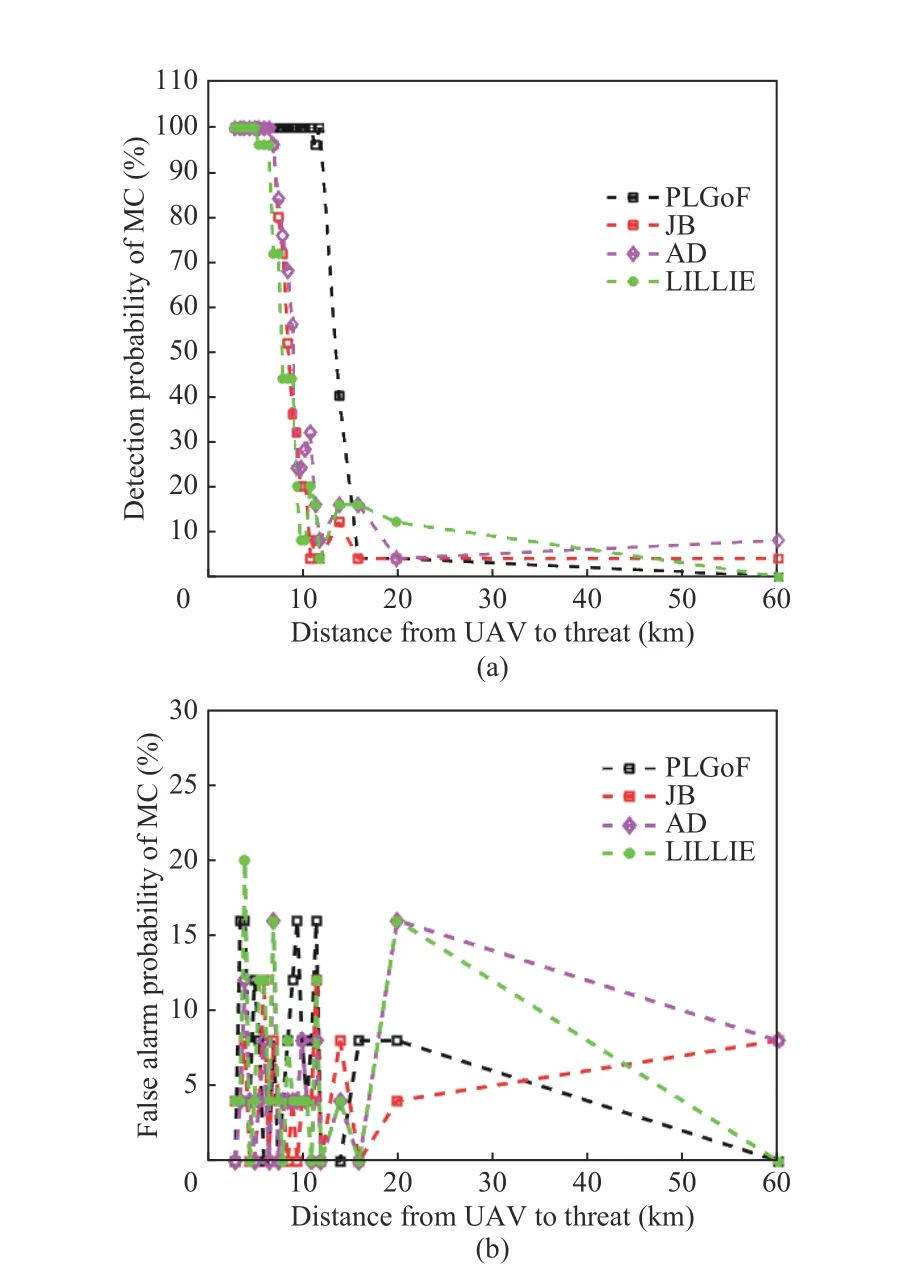
Fig. 4 Simulation results in the presence of spoofer: (a) detection probabilities; (b) false alarm probabilities
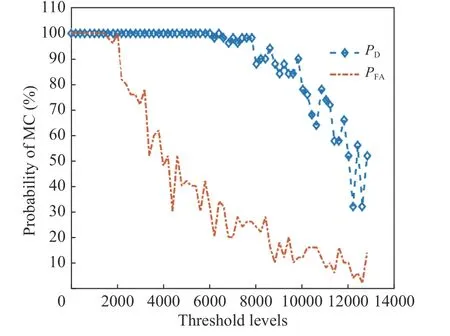
Fig. 5 Detection and false alarm probabilities based on different threshold levels (detection probability (PD) , false alarm probability (PFA))
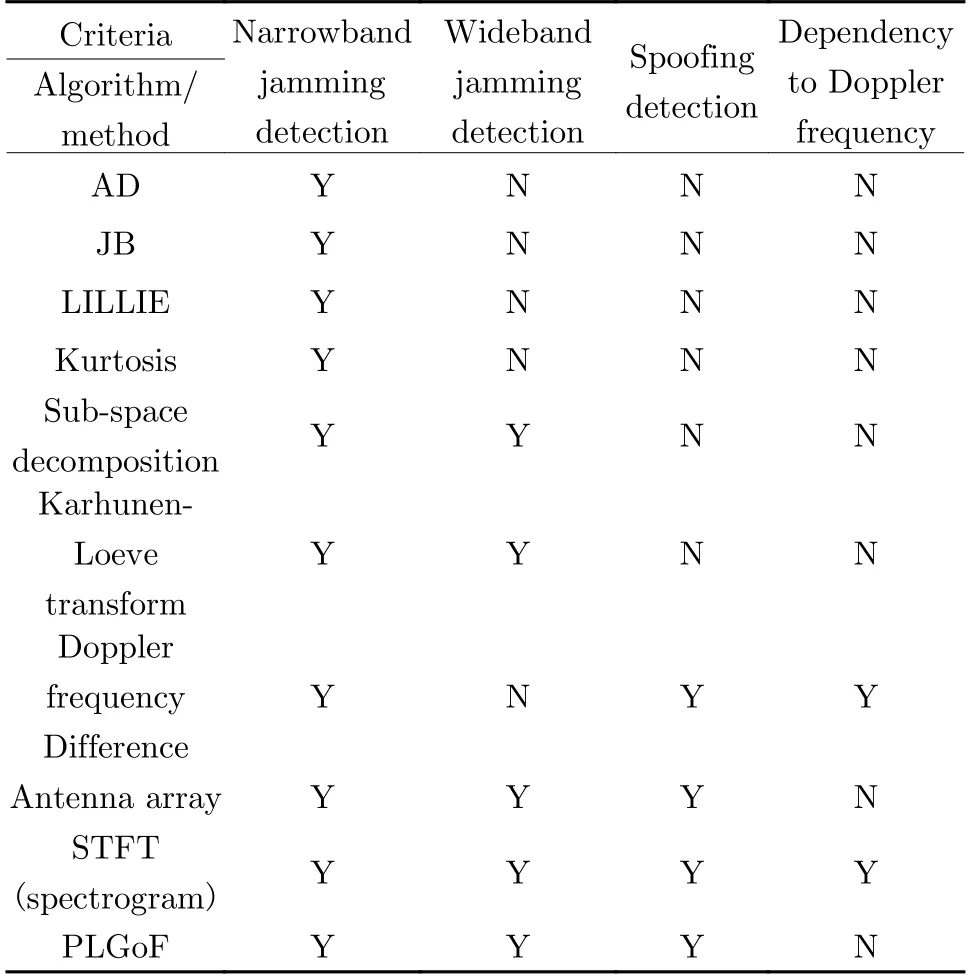
Tab. 2 Comparison between different algorithm features in the scope of this article application
As is evident from the simulation results, the proposed method shows better behavior in detection and false alarm probabilities. This is due to the utilization of goodness-of-fit criteria with empirical PDFs as well as learning phase performance.
6 Conclusion
A simple algorithm based on different empirical probability density functions (EPDF) of successive received signal powers and goodness of fit(GoF) technique was developed for aerial platforms such as UAV in no fading environment.The two different paths between UAV-satellite and UAV-threat experience different empirical probability density functions that were used to distinguish between authentic (GNSS) and threat (jamming or spoofing) signals. Simulation results containing detection and false alarm probabilities demonstrated good performance of proposed algorithm as well as low logical computational burden.
杂志排行
Journal of Beijing Institute of Technology的其它文章
- Distributed Privacy-Preserving Fusion Estimation Using Homomorphic Encryption
- Sub-Regional Infrared-Visible Image Fusion Using Multi-Scale Transformation
- Adaptive Sampling for Near Space Hypersonic Gliding Target Tracking
- Distributed Radar Target Tracking with Low Communication Cost
- Power Plant Indicator Light Detection System Based on Improved YOLOv5
- Model Predictive Control Based Defensive Guidance Law in Three-Body Engagement
