A Trust Assessment-Based Distributed Localization Algorithm for Sensor Networks Under Deception Attacks
2022-10-26YaWangXinmingChenLeiShiYuhuaChengandHoujunWang
Ya Wang, Xinming Chen, Lei Shi, Yuhua Cheng, and Houjun Wang
Dear Editor,
This letter is concerned with the distributed localization issue for wireless sensor networks subject to deception attacks. It is assumed that malicious nodes randomly launch attacks to tamper the ranging information between sensors. In order to accommodate the effects of deception attacks, a trust assessment-based distributed localization algorithm is proposed. Combined with data fusion of barycentric coordinates, our algorithm can achieve accurate localization. Finally,numerical simulations are given to validate the effectiveness of the proposed localization algorithm.
The localization of sensor networks, which aims at obtaining the locations of sensors to achieve the monitoring of networks, is of great significance in various fields of military and industry [1], [2]. In order to achieve exact localization, numerous algorithms have been developed for wireless sensor networks [3]–[6]. For instance, in the presence of uncertainties, a semi-definite programming algorithm was introduced for node localization [3]. A second-order cone programming relaxation of localization was proposed to achieve faster speed than the semi-definite programming algorithm [4]. A gradientbased target localization algorithm was developed for robotic sensor networks by utilizing statistical techniques to estimate the location[5]. A gradient-based fingerprinting system for indoor localization was introduced [6]. However, it should be pointed out that most of existing localization algorithms have certain shortcomings such that they cannot achieve both accurate localization and global convergence. Thus, it is desirable for sensor networks to design an exquisite algorithm with both of the excellent characteristics. To address this issue, a fully distributed iterative localization (DILOC) algorithm on the basis of barycentric coordinates representation was utilized in [7],[8], which can globally converge to the sensors’ accurate locations.
Actually, communication channels in sensor networks are quite vulnerable to cyber attacks due to the nature of wireless communication [9]. Deception attacks, as one of the most typical cyber attacks, may ruin the integrity of data by tampering the information transmitted through communication networks, and eventually lead to undesirable consequences such as malicious manipulation or even system breakdown [10]. To alleviate the negative influence resulted from deception attacks, a number of secure control schemes have been studied [11]–[15]. For example, by designing a pinning strategy-based impulsive controller, the problem of synchronization under deception attacks in multi-agent systems was investigated in[11]. A consensus protocol of multiagent systems under sparse linear injection attacks was designed and the relevant optimization problem was solved efficiently by the means of alternating direction method of multipliers [12]. Moreover, a distributed set-membership filtering algorithm along with two recovery mechanisms for a vehicle platooning system was introduced to identify and resist attacks in [13]. A Lyapunov-based nonlinear control scheme based on a multiagent system was presented in [14] to defend real-time false-data-injection attacks. Based on the notion of network robustness, resilient consensus problem of networked control systems under F-local deception attacks was considered [15]. Although there have been some initial works on secure control under deception attacks, most of them focus on multiagent systems. To the best of the authors’ knowledge, there is a paucity of related results on the localization of wireless sensor networks. Therefore, it is interesting yet challenging to develop a localization algorithm for wireless sensor networks subject to deception attacks.
Motivated by the above observers, this letter aims to solve the localization issue of sensor networks in the presence of deception attacks. Its contributions are twofold: 1) A universal model of deception attacks under which the ranging information based on received signal strength indicator (RSSI) is tampered by injecting false data is considered; 2) A distributed iterative localization algorithm combined with the techniques of trust assessment and data fusion is developed, and it can effectively achieve the accurate localization of sensor networks.
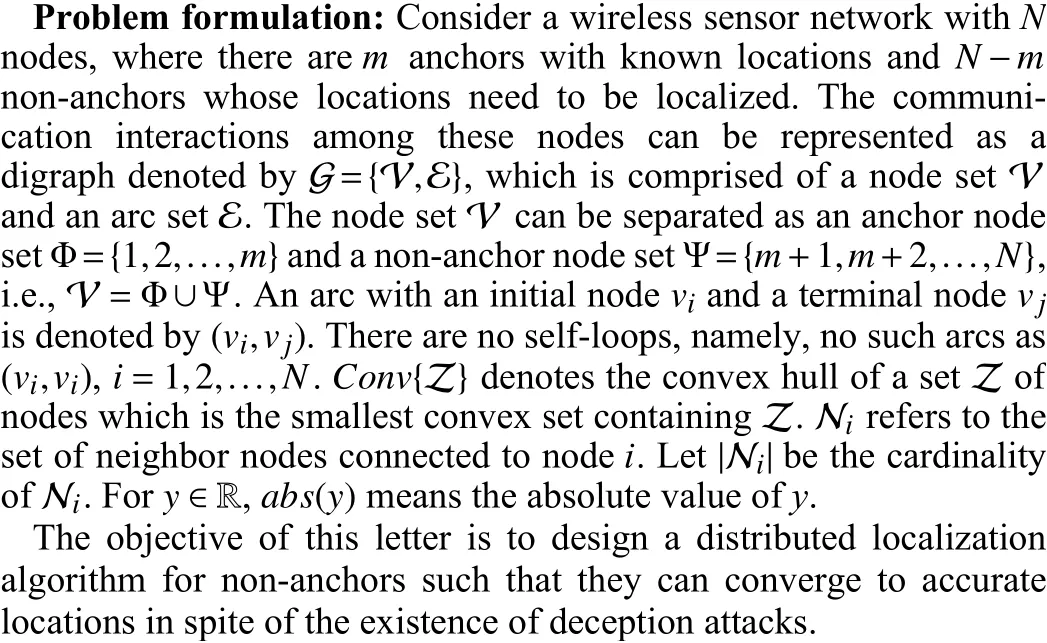
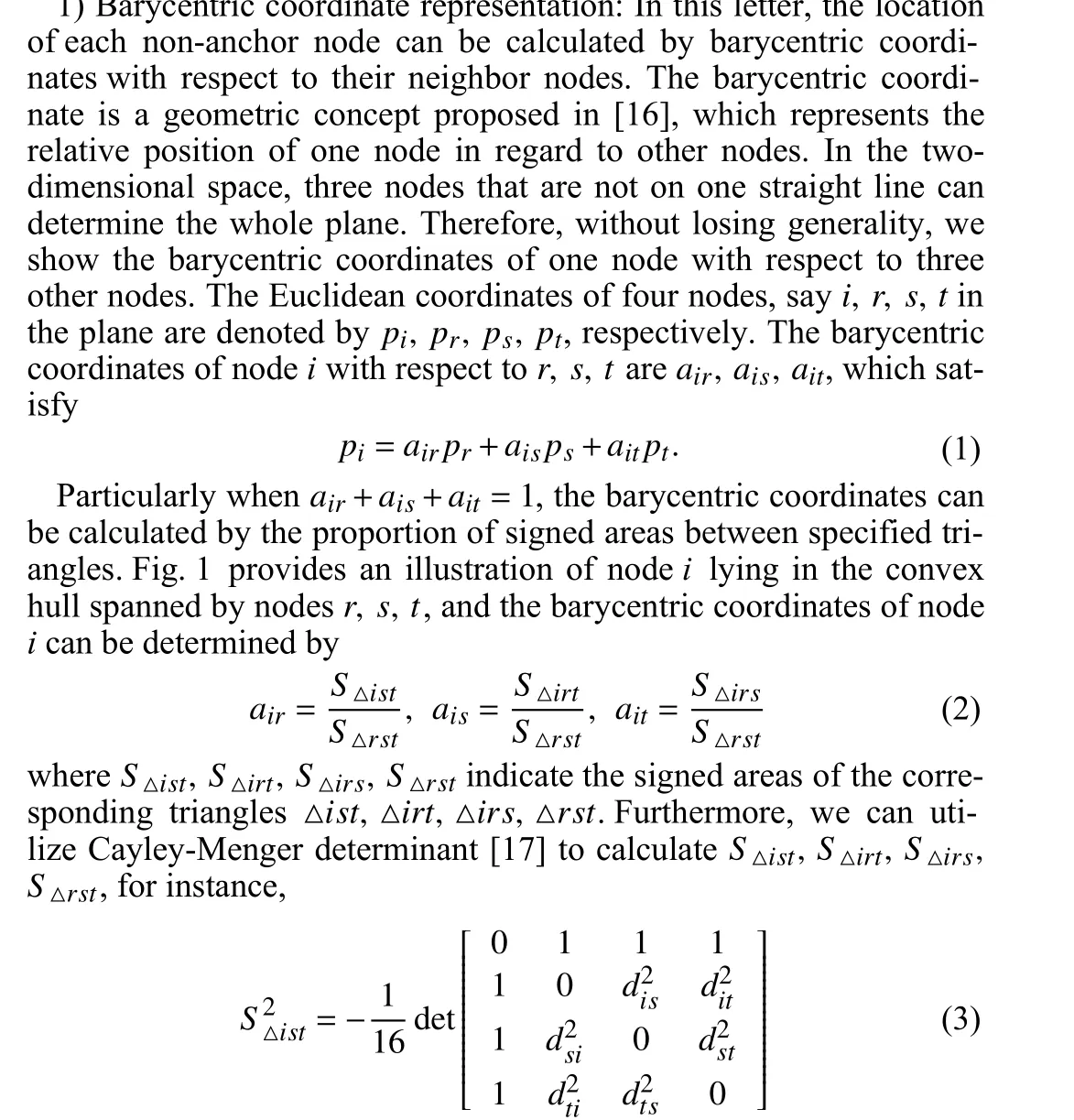
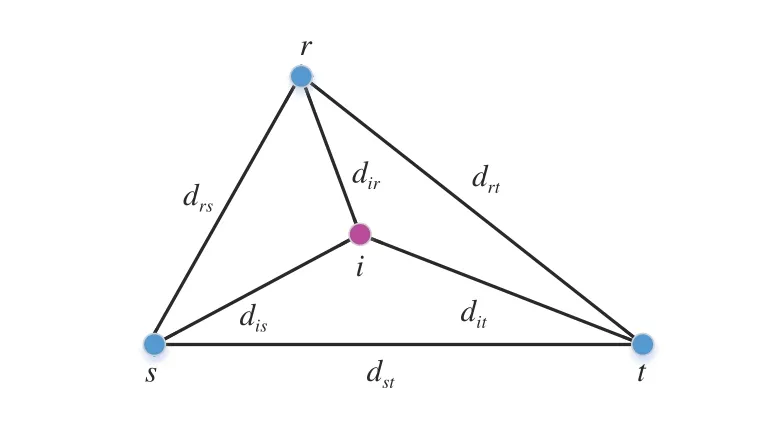
Fig. 1. Illustration of a node lying in the convex hull of its adjacent nodes.
2) Deception attack model: In this letter, it is assumed that malicious nodes are randomly distributed throughout the wireless sensor network which occasionally launch deception attacks on the nearest node, leading to the disintegrity of data transmitted among some of neighbor nodes. As depicted in Fig. 2, the nodes in green refer to sensors in the network, whereas the nodes in red stand for deception attack launchers, and the circles of red dotted line indicate the attack range of malicious nodes. Deception attacks aim to reduce the positioning accuracy or even make the whole sensor network unstable by modifying the data transmitted in the communication channels. In the scenario of this letter, the distances between sensors are measured based on RSSI. Therefore, the packet sent by a node, sayrnot only includes the location informationpr(t) at the current iteration timetbut also contains its transmitted signal power. With the same radio signal transmitting power, the distance between one node and its adjacent node is inversely proportional to the received signal power from the neighbor node, which as follows:and replay attacks. Compared with other attacks, false data injection attacks which can bypass the surveillance of attack detection mechanism silently, are more destructive to the system. Furthermore, in this letter, the tampering of distance measurement can be well modeled through the false data injection model. Therefore, we set up the m daotadel that the distance valuesdir(t) are tampered by injecting false

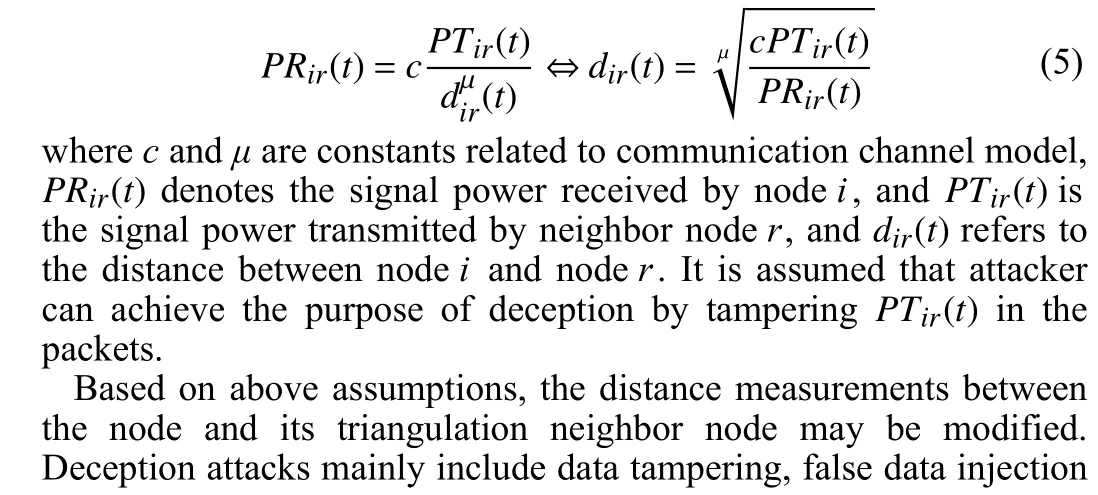
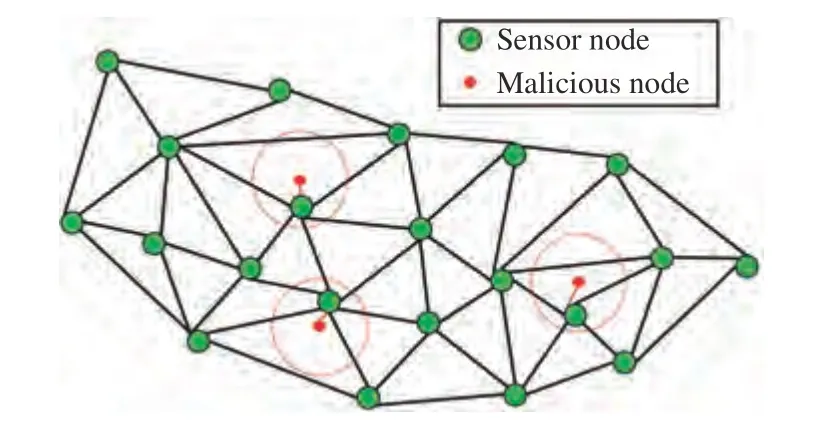
Fig. 2. Illustration of deception attack model.
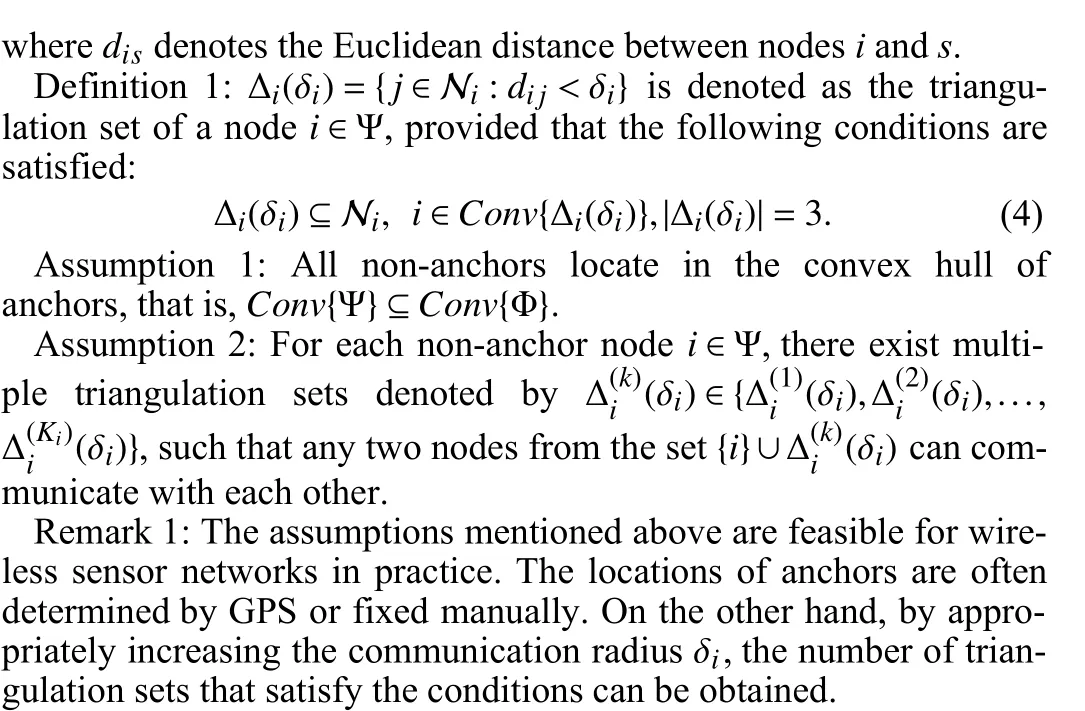
Assumption 3: For each non-anchori, there is at least one credible triangulation set in which each node is immune to deception attacks during the entire process of localization.
Remark 2: Due to the randomness of deception attacks launched and limited resources for stealth of malicious nodes, as well as the diversity of the triangulation sets of non-anchors, Assumption 3 is reasonable.
Algorithm design: In this section, a trust assessment based distributed iterative localization algorithm is proposed to eliminate the influence of deception attacks. Here we first introduce an evaluation scheme based on statistical characteristics to assess the trustworthiness of triangulation sets of non-anchors, and then in the process of distributed iterative localization, the weights of the triangulation sets those are evaluated as untrustworthy are reduced.

Consequently, in the following stage of distributed iterative localization, the degree of unreliable triangulation sets to influence the positioning process will be decreased to alleviate the negative impacts of deception attacks on the wireless sensor networks.
2) Distributed iterative localization: In this letter, we adopt a data fusion method of barycentric coordinates combined with trust assessment, on the basis of the DILOC algorithm [7] to resist deception attacks.
According to Assumption 2, the position of non-anchorican be determined by its triangulation sets, thus the location of nodeican be represented in the following iterative form:
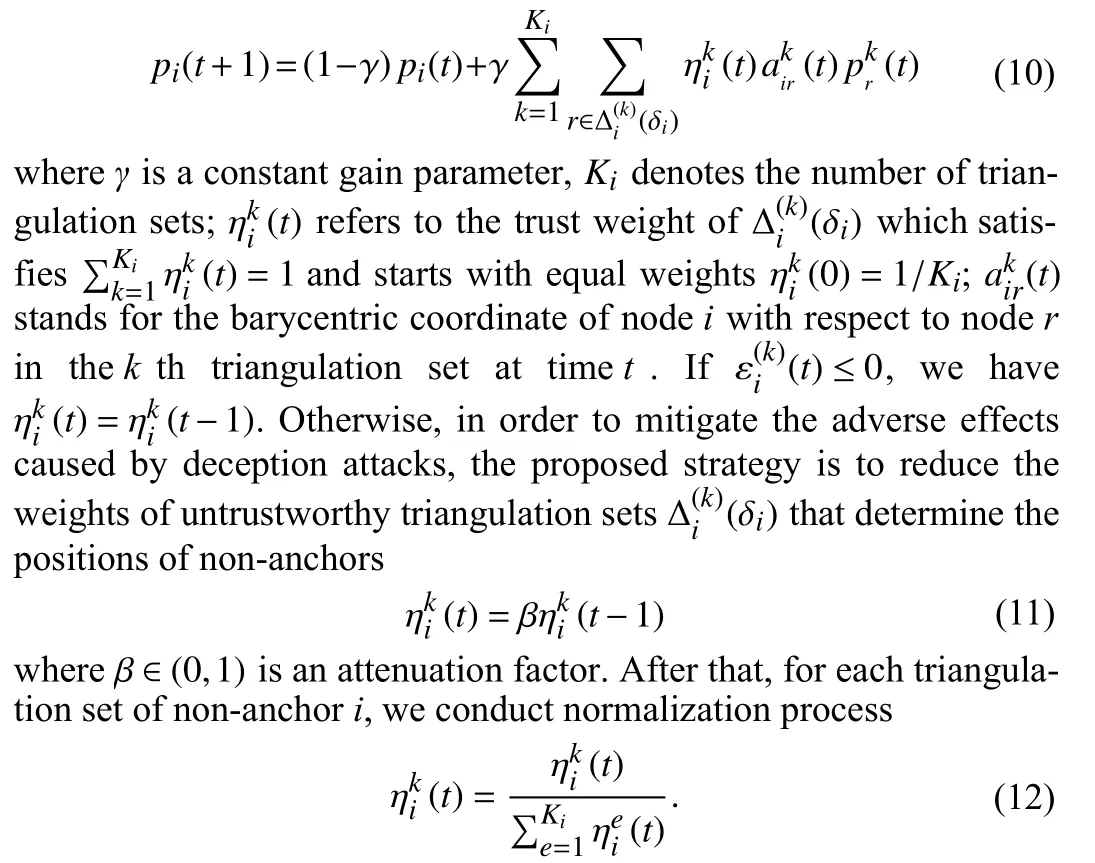
Next, we integrate the trust evaluation scheme into the process of distributed iterative localization. The detailed realization is given in Algorithm 1.
Remark 3: Note that when there are not any untrusted nodes and the number of trigulation sets for every non-anchor is only one,Algorithm 1 is reduced to the case of the DILOC algorithm in [7].
As shown in Fig. 3, nodes in black refer to anchors and nodes in red are non-anchors to be localized. The communication interactions among sensors are indicated by directional arrows.
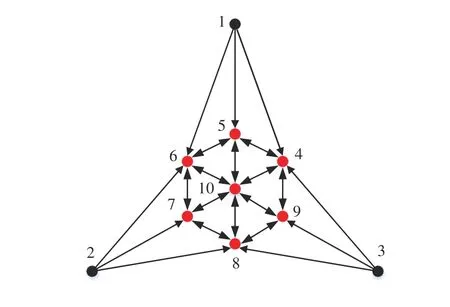
Fig. 3. Interactive topology among sensors.
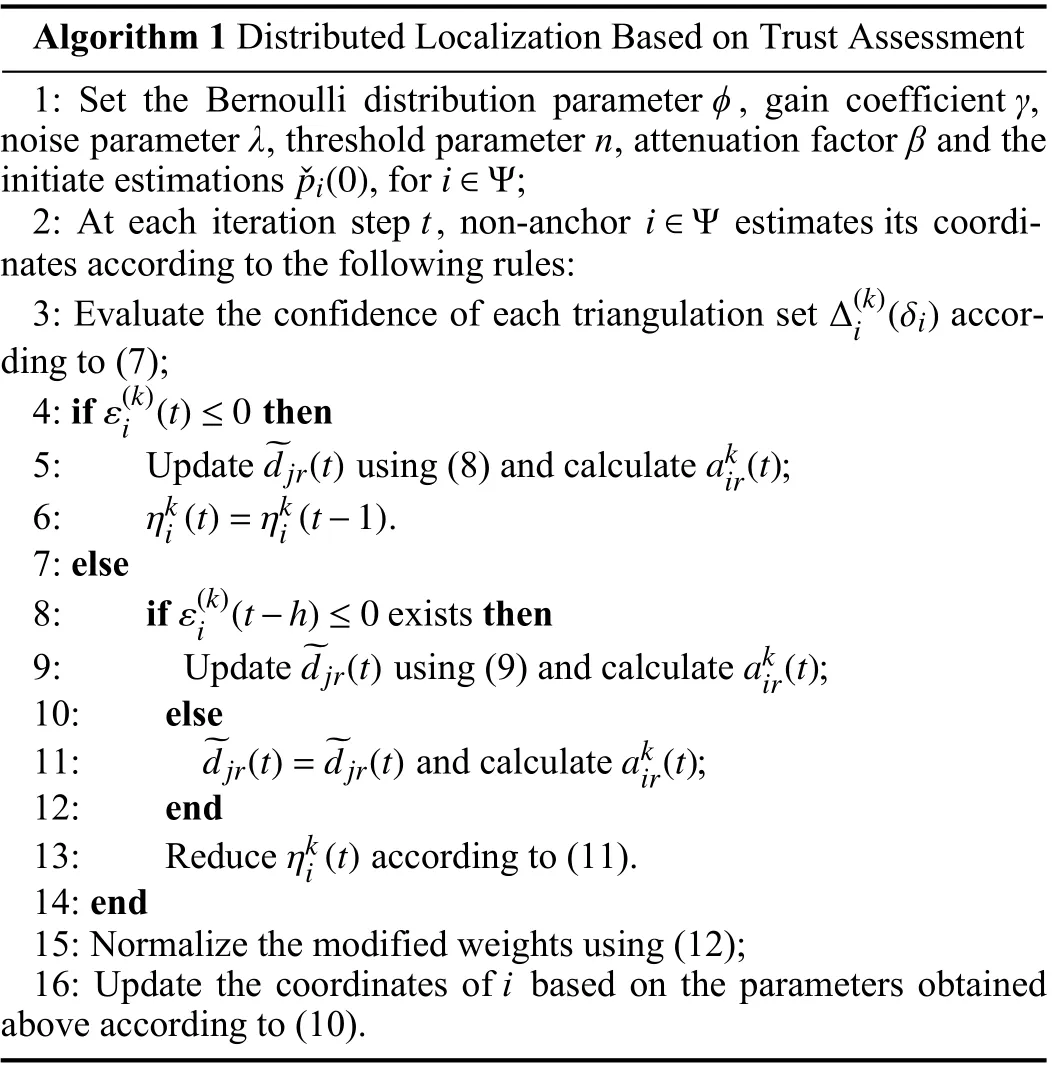
Algorithm 1 Distributed Localization Based on Trust Assessment 1: Set the Bernoulli distribution parameter φ, gain coefficient γ,noise parameter λ, threshold parameter n, attenuation factor β and the initiate estimations , for ;i ∈Ψ ˇpi(0) i ∈Ψ 2: At each iteration step t, non-anchor estimates its coordinates according to the following rules:Δ(k)i (δi)3: Evaluate the confidence of each triangulation set according to (7);ε(k)i (t)≤0 4: if then~djr(t) akir(t)5: Update using (8) and calculate ;ηki (t)=ηki (t-1)6: .7: else ε(k)i (t-h)≤0 8: if exists then~djr(t) akir(t)9: Update using (9) and calculate ;10: else~djr(t)=~djr(t) akir(t)11: and calculate ;12: end ηki (t)13: Reduce according to (11).14: end 15: Normalize the modified weights using (12);16: Update the coordinates of i based on the parameters obtained above according to (10).
Moreover, Fig. 7 reveals that all the non-anchors cannot converge to the exact locations because the distance measurements obtained by some nodes are tampered, which illustrates the deficiency of DILOC[7] under deception attacks. In contrast, it can be proven from Fig. 8 that our proposed algorithm based on trust assessment is capable of achieving accurate localization while suffering from deception attacks. Therefore, the proposed localization algorithm has been numerically verified.
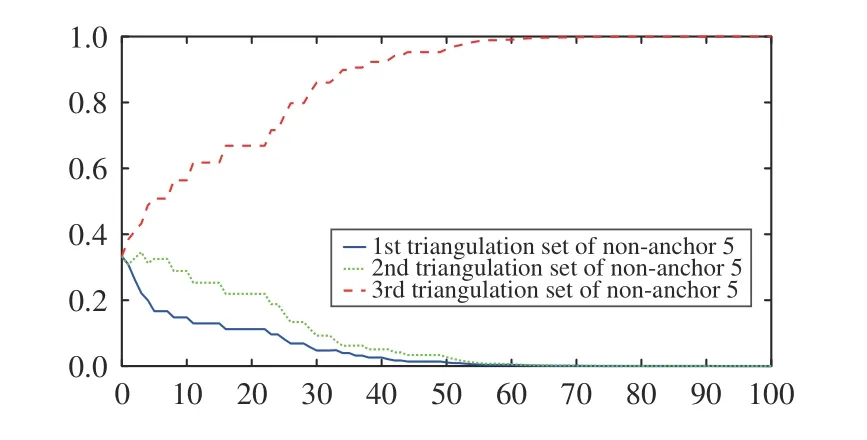
Fig. 4. Trust weight of the triangulation sets of non-anchor 5.
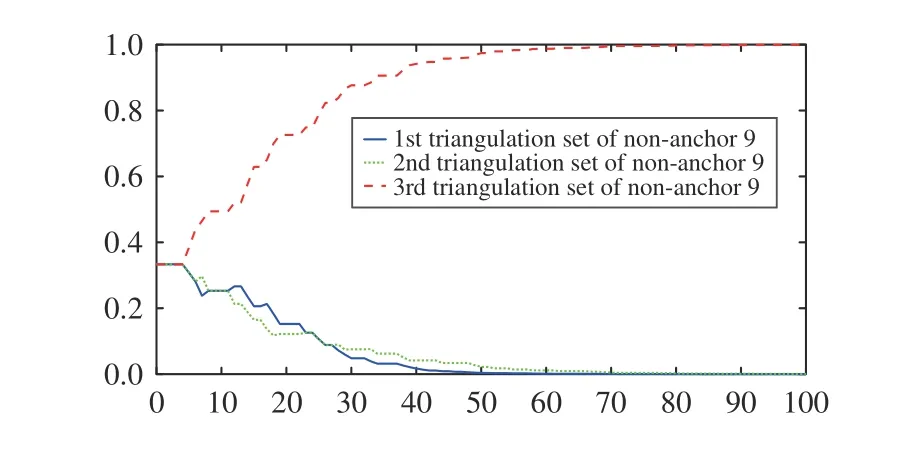
Fig. 5. Trust weight of the triangulation sets of non-anchor 9.
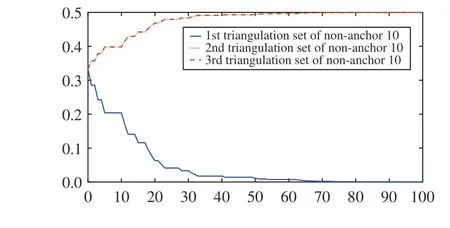
Fig. 6. Trust weight of the triangulation sets of non-anchor 10.
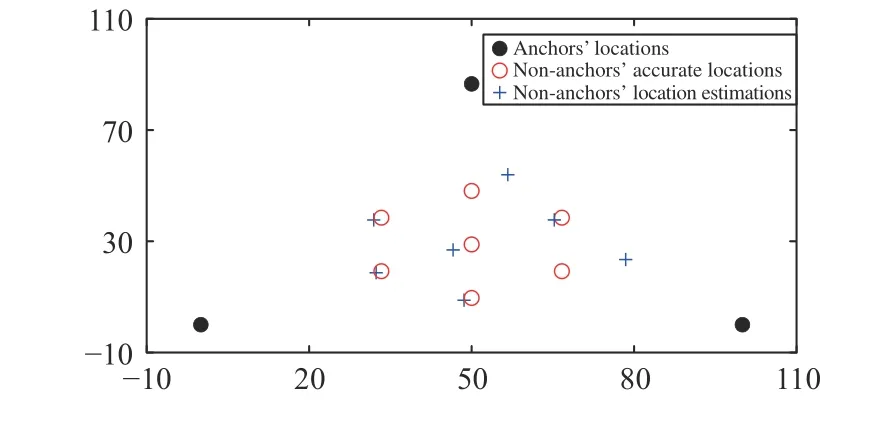
Fig. 7. Localization using DILOC [7] under deception attacks.
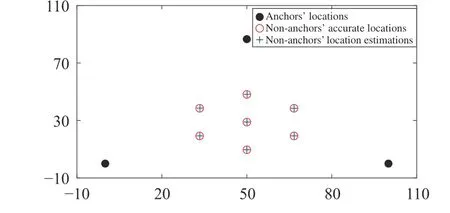
Fig. 8. Localization using our algorithm under deception attacks.
Conclusion: In this letter, the localization issue of wireless sensor networks under deception attacks has been investigated. A distributed iterative localization algorithm based on trust assessment has been presented for ensuring the accurate positioning of sensors subject to malicious tampering. By utilizing data fusion of barycentric coordinates combined with trust assessment model, the coordinates of non-anchors converge to their precise locations. Furthermore, the validity of the algorithm has been verified by numerical examples.
Acknowledgments: This work was supported in part by the National Natural Science Foundation of China (62103080), the Natural Science Foundation of Sichuan Province (2022NSFSC0878), the National Postdoctoral Program for Innovative Talents (BX2021056),the China Postdoctoral Science Foundation (2021M700696), and the Sichuan Science and Technology Program (2021YFH0042).
杂志排行
IEEE/CAA Journal of Automatica Sinica的其它文章
- Distributed Cooperative Learning for Discrete-Time Strict-Feedback Multi Agent Systems Over Directed Graphs
- An Adaptive Padding Correlation Filter With Group Feature Fusion for Robust Visual Tracking
- Interaction-Aware Cut-In Trajectory Prediction and Risk Assessment in Mixed Traffic
- Designing Discrete Predictor-Based Controllers for Networked Control Systems with Time-varying Delays: Application to A Visual Servo Inverted Pendulum System
- A New Noise-Tolerant Dual-Neural-Network Scheme for Robust Kinematic Control of Robotic Arms With Unknown Models
- A Fully Distributed Hybrid Control Framework For Non-Differentiable Multi-Agent Optimization
