A Lightweight Mutual Authentication Protocol for IoT
2022-06-29BrouBernardEhuiYiranHanHuaGuoJianweiLiu
Brou Bernard Ehui,Yiran Han,Hua Guo,Jianwei Liu
Abstract—Due to the resource-constrained of Internet of things (IoT) devices,the traditional cryptography protocols are not suitable for IoT environments.When they can be implemented,their performances often are not acceptable.As a result,a lightweight protocol is required to cope with these challenges.To address security challenges in IoT networks,we present a lightweight mutual authentication protocol for IoT.The protocol aims to provide a secure mutual authentication mechanisms between the sensor node and gateway using a lightweight cryptography algorithms.The protocol is relied on two main shared secret keys,a permanent key (kp) used for encrypting messages during the mutual authentication phase and an update key(ku)used for the communication session.The session key is constantly updated after a pre-defined session time (sesstimei) by using the previous session information.We used a lightweight cryptography mechanisms that includes symmetric-key cryptography,hash-based message authentication code (HMAC),and hash function to design the protocol.We analyze the protocol using the Barrows-Abadi-Needham (BAN)-logic method and the results show that the proposed scheme has good security and performance compared to existing related protocols.It can provide a secure mutual authentication mechanism in the IoT environment.
Keywords—Internet of things,security,authentication,attacks,sensors,gateway
I.INTRODUCTION
Internet of things(IoT)has become one of the dynamic and exciting developments in communication technology.With the advent of IoT,a large number of devices are connected to the network.These have included smart TV,vehicles,medical devices,electric meters and controls,street lights,traffics controls,house appliances,etc.IoT technology has assigned digital labels to all people,things,and devices.Today from vehicles to drones,from robots to farm animals,and from surveillance facilities in cities to power grids,all things are gaining the ability to sense through the power of data[1].Huawei forecasts that by 2025 there will be over 100 billion connected devices around the world and 200 million vehicles connected to fifth generation(5G)[1].This will drive us to an intelligent world where all objects sense,things are related,and items are intelligent.This IoT scenario will increase also the quantities of data generated per year.According to Ref.[1],by 2025,180 billion TB of data will be generated every year.
With the advent of IoT,wireless sensor network (WSN)has become more popular.It is composed of smaller-sized sensors that aim to collect data from the physical environment to central locations such as servers or cloud.It works in conjunction with IoT technology where sensors are able to sense data,make collaboration,and transfer information to the end-users.It is deployed in every working place around the world including smart cities,smart agriculture,home automation,health-care,transport,etc.The sensors deployed in the WSN are typically resource-constrained devices in terms of memory,battery capacity,energy consumption,and computational power(low central processing unit(CPU)power).Additional characteristics of IoT-enabled WSN include mobility,bandwidth,heterogeneity of the IoT network,and scalability.These sensors are generally composed of a micro-controller(CPU),a memory unit(random access memory(RAM),readonly memory(ROM)),communication devices,actuators,and a power supply unit.Furthermore,sensors are mobile nodes deployed in a random location in the environment.Usually,the central node is required to connect WSN to the Internet using IP protocol.Also,it transfers the aggregated data to the cloud server.This central node can be remotely accessible and manageable.
However,using sensors to collect data from the physical world to the cloud can increase potential security vulnerability.As we increasingly connect objects to the Internet,we need to be aware that every poorly secured device connected to the Internet can serve as an entry point for cyberattacks.Poorly designed protocols can also expose end-user data to theft by leaving data streams inadequate protected[2].When devices are failing or malfunctioning,they can represent security vulnerabilities for another Internet user.For this reason,IoT security needs to be a major challenge in this digital world and should be considered a critical issue.Manufacturers and IoT security protocol designers may provide authentication and secure communication mechanism in WSN for exchanging confidential information.
Moreover,due to the resource-constrained of IoT devices,the traditional cryptography protocols are not suitable for IoT environments.When they can be implemented,their performances often are not acceptable.As a result,lightweight cryptography is required to cope with these challenges.It aims to provide a solution for resource-constrained devices by reducing the key size,cycle rate,throughput rate,power consumption,and area.Lightweight cryptography algorithms have been extensively studied for the last few years because of security requirements in resource-constrained devices such as radio-frequency identification(RFID)and smart cards.There is a significant amount of work done by researchers related to lightweight cryptography including efficient implementation of traditional cryptography algorithms and the design of new lightweight algorithms and protocols.Furthermore,many academic communities and international organizations such as the Internet Engineering Task Force(IETF),European Telecommunications Standards Institute (ETSI),and Institute of Electrical and Electronics Engineers (IEEE) have provided a noteworthy contribution in terms of normalizing and developing IoT security standards.Some of these standards are IEEE802.15.4[3,4],ZigBee[5],WirelessHART[6,7],ISA100.11[8,9],6LoWPAN[10],and Bluetooth Low Energy[11,12].In Refs.[13-18],authors have proposed a lightweight authentication protocol and key management for IoT systems.
To address security challenges in IoT networks,we present a lightweight mutual authentication protocol for IoT.The primary motivation for designing this protocol is to provide secure communication mechanisms between the sensor node and gateway using lightweight cryptography algorithms.as shown in Fig.1,a simple gateway is used to connect heterogeneous IoT devices,and each device can communicate with another device through the gateway.Thus,IoT device needs to trust the gateway.That means before starting to share data;the IoT device needs to authenticate the gateway and viceversa.Mutual authentication means that only an authenticated and authorized device can communicate with the gateway.An intruder will not be able to eavesdrop on the authentication process and performs a reply attack or other attacks.The proposed protocol enhances the security robustness of IoT technology.The main contributions of this work are as follows:(i) the protocol provides a secure and fast mutual authentication mechanism between the IoT device and gateway.It also offers low communication overhead and reduces energy consumption;(ii) The proposed protocol uses a lightweight cryptography mechanisms;(iii)The protocol is based on two shared secret keys and is not dependent on a trusted third party(TTP).The proposed protocol is safe and robust against multiple attack types.
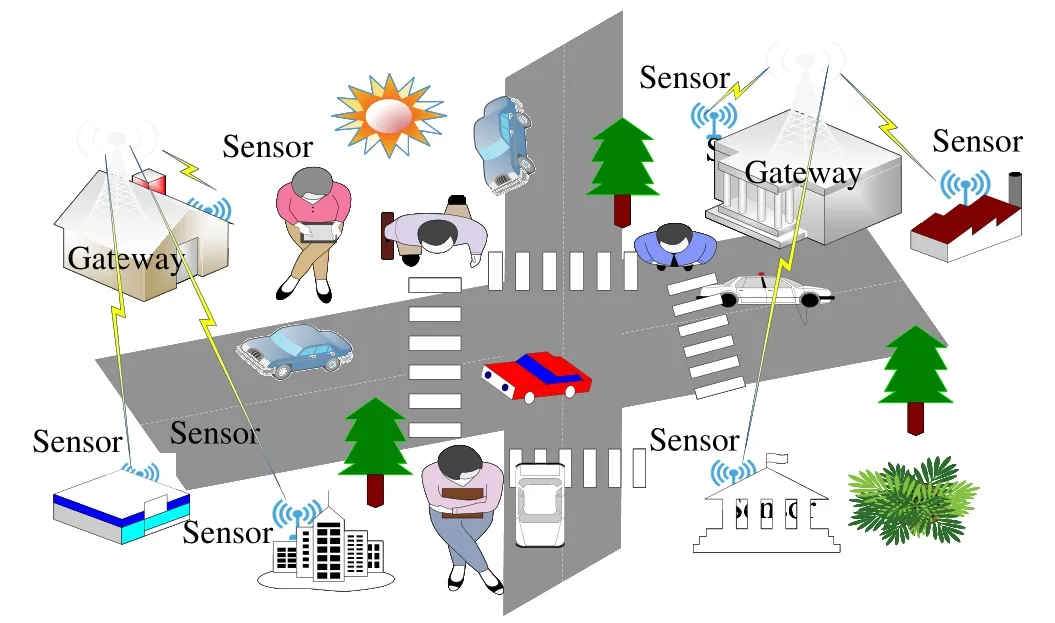
Fig.1 Network topology
The rest of the paper is organized as follows:Section II presents related works.Section III describes the IoT environment considered in this work;it includes network topology and attack scenarios.The proposed protocol is discussed in detail in section IV.Section V describes the security analysis,and we conclude in section VI.
II.RELATED WORKS
Since the first use of the term Internet of things in 1999 by Kevin Ashton to describe a system in which objects in the physical world could be connected to the Internet by sensors[2].Researchers have proposed many protocol designs to enhance the security robustness in the IoT environment.In Refs.[19-21],the authors give a comprehensive understanding of IoT technology and present a survey of IoT security,framework,and architecture.In addition,a high-level overview of the basics of IoT and some of the critical issues and questions about IoT technology is described by Ref.[2]to help the IoT society community navigate the dialogue surrounding IoT technology.Authors in Ref.[13] propose a lightweight authentication and key exchange protocol for IoT using an approach similar to ours.However,the threshold,a maximum number of frames exchanged in each session to update the session key,makes it vulnerable to cyberattacks such as denial of service (DOS).In addition,some variables parameters like the sensor’s identification(ID)and gateway’s ID used in this protocol are not encrypted.It exposes the devices to impersonate attacks.Other lightweight authentication protocols are developed by Refs.[14,15] based on physical unclonable function (PUF).These proposed protocols are very efficient in terms of memory,computation,energy,and communication overhead.It can also provide low-cost device authentication and secure communication.However,it presents an implementation limit,as PUF is still not yet widely used in IoT technology.Therefore,we need to look for other alternatives.Authors in Ref.[22]developed lightweight two-level session key management for IoT users in wireless sensor networks.
III.IOT ENVIRONMENT AND SECURITY REQUIREMENT
This section presents the IoT environment and the different security requirements needed to design the proposed protocol.
A.IoT Environment
The network topology that we consider in this work is shown in Fig.1.As we can see,multiple IoT devices (sensors) are connected to a single intermediary gateway.Each device can communicate with other nodes only through the gateway by using a wireless communication channel.IoT devices in this topology are small-sized and have limited energy,as they depend on batteries.IoT devices and gateway need to operate in a disconnected environment.It means that IoT devices and gateway are not connected to a central device or are not dependent on a trusted third-party(TTP).In addition,we assume that IoT devices have limited memory and manual configuration is feasible.The administrator can manually set up the shared secret key into the IoT device and gateway.To store the shared private key and the hash of the sensor’s ID and gateway’s ID in the apparatus,non-volatile memory like electrically erasable programmable read-only memory(EEPROM) is required.A few megabytes (MB) of RAM is also necessary to perform communication between the device and gateway.RAM is used to store all the information shared during the previous communication session,as it will be used to update the session key.We finally assume that the proposed protocol network topology is set up in a secure area where attackers have no physical access to the devices.Thus,they cannot discover the configured secret keys that are stored on the devices.
B.Security Requirements
As the number of IoT devices connected to the Internet grows exponentially,new opportunities to exploit potential security vulnerabilities also increase.Every unsecured device connected to the Internet could serve as an entry point for cyberattacks.User’s data can be exposed to theft if IoT security protocols are poorly designed.Security in IoT devices needs to be considered a top priority.Moreover,IoT device manufacturers need to provide a security mechanism that can guarantee the security and privacy of Internet users.Enabling the users to have a high degree of trust in the Internet,its applications,and the devices linked to it,is secure enough to protect their online activity[2].IoT products and services can cause real problems if users do not believe that their connected devices and information are secure from cyberattacks.As result,we need to design a new IoT protocol to address these security challenges and provide unquestionable authentication message integrity and confidentiality.The proposed protocol is designed to deal with these issues.
1) Mutual Authentication:This section presents a brief description of the mutual authentication phase;more details are presented in section IV.A.As we can see in Fig.2,mutual authentication is required before the two devices establish a typical communication process.Sensors first contact the gateway by sending an encrypted mutual authentication message including the hash of the sensor’s ID and challenge.To provide the integrity and authenticity of the message,sensors calculate the message authentication code (MAC)[23]for the whole message.Once the gateway receives the mutual authentication message from the sensors,it first decrypts the message and compares the received hash with the stored hash of the sensor’s ID.Suppose the two hashes are equal.It continues the authentication process by calculating the MAC of the whole message.Otherwise,the authentication process fails.Suppose the calculated MAC matches the received MAC.In that case,the gateway authenticates the sensors and sends an encrypted reply message including a hash of his ID,a new challenge,the set of random sequence numbers,the session time,and the MAC of the whole message to the sensors.
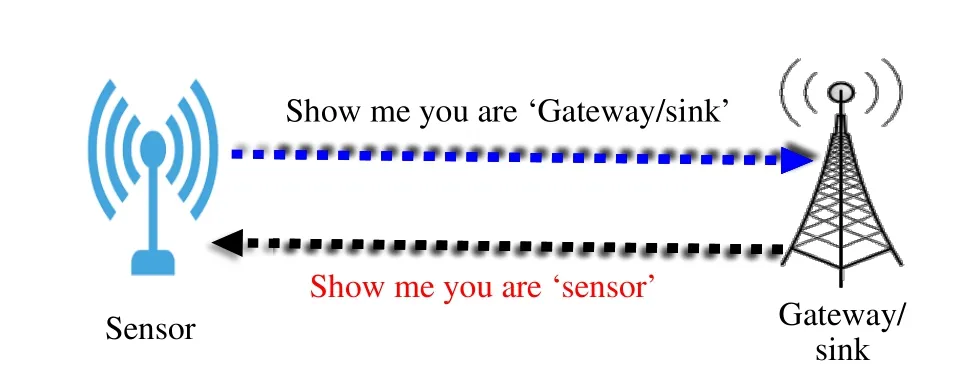
Fig.2 Mutual authentication
The sensor decrypts the message and compares the received hash of the gateway’s ID with the stored hash.If the two hashes match,the authentication process continues by verifying the received MAC with his calculated MAC.If the two MACs are identical,then the sensor authenticates the gateway.Otherwise,the authentication fails.Once the mutual authentication step is successfully done,secure regular communication can start.Attackers cannot intercept the data during the normal communication process.All the authentication credentials are encrypted and hashed using a secret pair key manually inserted in the devices by the administrator.
2) Key Exchange:The secret key exchange phase is shown in Fig.3.As we can see in this figure,sensors and gateway share a secret key to establish secure communication.We consider two main shared secret keys.A permanent key(kp)is used to encrypt the authentication messages and an update key(ku)is used for encrypting and hashing communication during sessions.An initial update key (kik) is necessary for hashing authenticated messages between devices and gateway.The permanent key and the initial update key are inserted into all the devices in non-volatile memory,such as EEPROM.kuis generated by using hash key derivation function(HKDF)[24,25]for the next session.After a pre-defined session time,kuis updated by using the previous session information.More details about thekuupdate process are presented in section IV.C.All the keys used in this proposed protocol are not shared through the network.
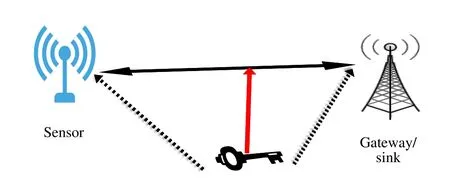
Fig.3 Key exchange
3) Attacks Scenarios:By considering the network topology described in the previous section,we want to present the attack scenarios that attackers can launch to exploit vulnerabilities in the proposed protocol.As described in the previous section,IoT devices are connected to a gateway through a wireless channel.The use of wireless channels can be an easy way for an attacker to eavesdrop and launch an attack,exposing the network to many cyber-attacks.An attacker can use brute force attack methods to discover the secret key on the key exchange traffic.They can also perform a man-in-themiddle[24]attack to have unauthorized access to the confidential message and modify them.
IV.LIGHTWEIGHT MUTUAL AUTHENTICATION PROTOCOL FOR IOT
Internet of things has become a more and more popular topic recently.Many industry sectors,including healthcare,automotive,home,smart transport,smart city manufacturing,and consumer electronics,have adopted the idea of incorporating IoT technology into their products,services,and operations.It allows interconnecting of more and smaller devices.At present,it is increasingly difficult to purchase some devices that are not Internet-connected[2].In addition,IoT devices play an important role in every working area.For example,in the healthcare area,IoT devices monitor a patient’s health status.They can collect data from patients and share it with the doctor.Such data need to be shared in a secure and authenticated manner as it contains patient’s confidential information and their privacy needs to be protected.For this reason,we propose a lightweight mutual authentication protocol to provide authenticated and secure communication for the IoT environment using a lightweight cryptography mechanisms.
The designed protocol provides a secure mutual authentication mechanism between the sensor and the gateway.It enhances the security robustness of IoT network.The network topology adopted in this work is a disconnected network.It means that the network is not connected to any central device or a cloud.Nevertheless,a simple gateway is used to connect IoT devices,and each device can communicate with another device through the gateway.Before starting to share data;the IoT device needs to authenticate the gateway and vice-versa.The proposed protocol has the following features.(i)The protocol provides secure mutual authentication between the IoT devices and intermediary gateway.(ii)This protocol depends on two main shared secret keyskpused for encrypting messages during the mutual authentication phase,andkuused for communication sessions.The session key is constantly updated after a pre-defined session time using the information exchanged in the previous session.Bothkikand permanent keys are inserted into the sensor and the gateway during configuration time,and they are never shared in the network.(iii)The proposed protocol used a lightweight mechanism that includes symmetric-key cryptography[25],hash-based message authentication code (HMAC)[26],and hash function[27].The key derivation function based on the HKDF[28,29]is used to generate the session key after a pre-defined interval time.To enhance the security robustness of authentication,we have inserted the hash of the sensor’s ID (h(Sid)) and gateway’s ID(h(Gid))into the device and the gateway during configuration time.Thus,the different IDs will not be shared in plaintext and cannot be modified by the attacker even if the message is captured during the mutual authentication phase.Hence,it provides a high-security level as the received ID hash is compared with the stored hash during the mutual authentication process.If the received hash matches the stored hash,the device is authenticated,and the mutual authentication process can continue.Otherwise,the mutual authentication fails.(iv)The protocol is implemented in a disconnected environment and does not depend on a TTP.This provides a secure and fast authentication mechanism.It also reduces energy consumption and minimizes message exchange during mutual authentication and data transmission process.The different notations used in this work are presented in Tab.1.Mutual authentication,normal communication,session key update are the three main parts of this section and they are described as follows.
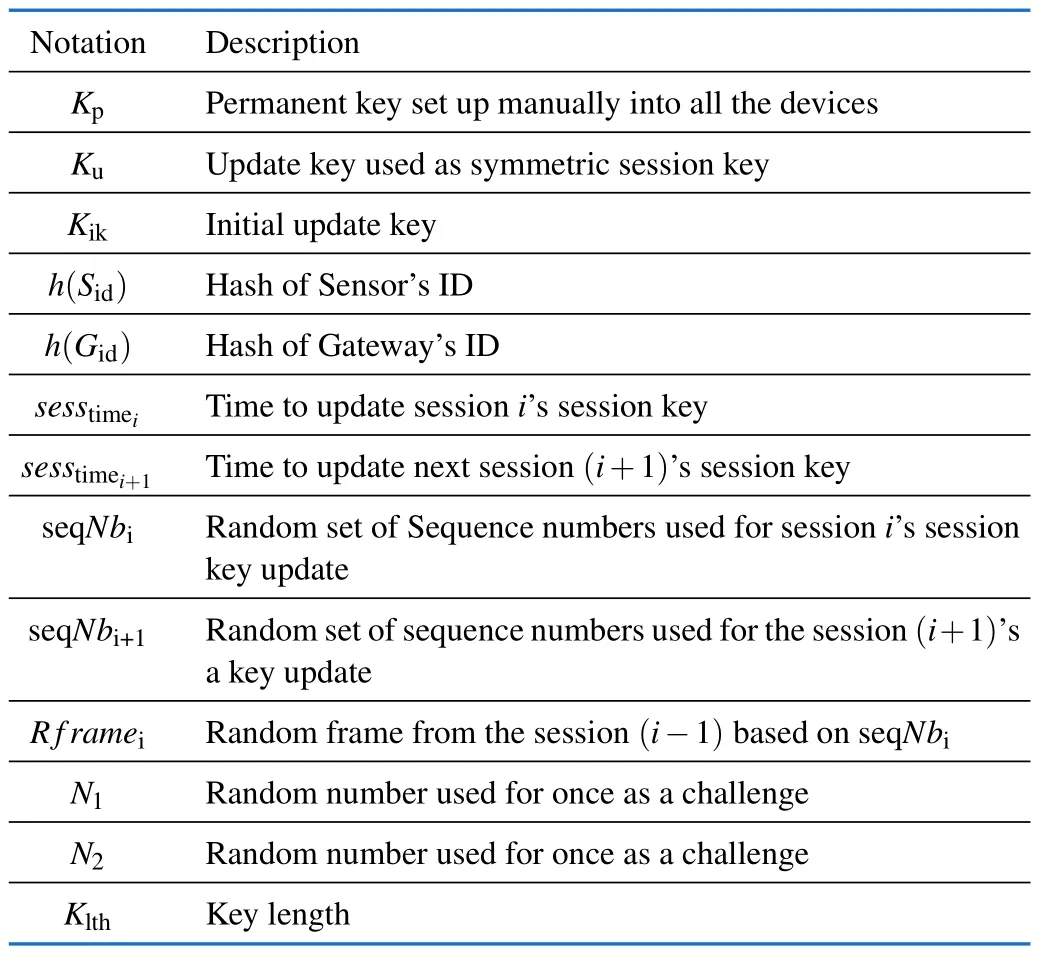
Tab.1 Notations
A.Mutual Authentication Phase
The mutual authentication process is shown in Fig.4.The different steps are described as follows.
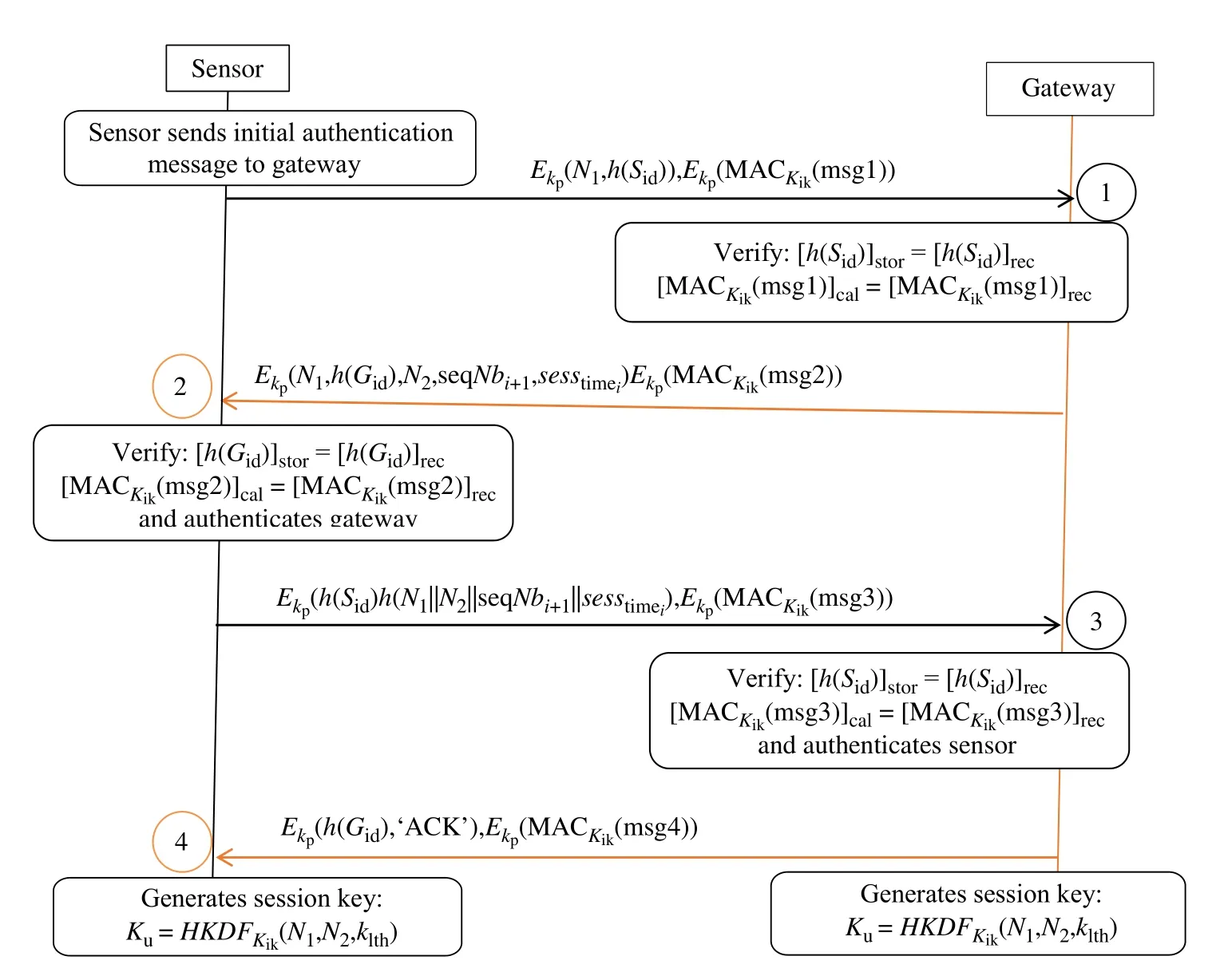
Fig.4 Mutual authentication
step 1:Sensor-→Gateway
The IoT device(sensor)initiates the mutual authentication process by sending the hash of its ID (h(Sid)) and randomly generated challengeN1to the gateway.This initial authentication message is encrypted with a permanent key (kp).To provide integrity and authenticity of the message,the sensor calculates the MAC for the whole message(msg1))by using the initial update key(kik)
step 2:Gateway-→Sensor
Once the gateway receives the mutual authentication message from the sensor,it first decrypts the message and compares the received hash of the sensor’s ID with the stored hash([h(Sid)]stor[h(Sid)]rec).If the two hashes are equal;it continues the authentication process by calculating the MAC for the whole message.Otherwise,the authentication process fails.If the calculated MAC matches the received MAC(msg1)]cal(msg1)]rec),then the gateway authenticates the sensors.Otherwise,the authentication process fails.It selects a set of sequence numbers(seqNbi+1)that will be used to update the session key,the new generated challengeN2,the pre-defined session timeN1and the hash of its ID(h(Gid)all encrypted with(kp),it also calculates(msg2)by usingkikand sends it to the IoT device.
step 3:Sensor-→Gateway
When the sensor receives the message from the Gateway.It first decrypts the message and compares the received hash of the gateway’s ID with the stored hash ([h(Gid)]stor[h(Gid)]rec).If the two hashes match then,it continues the authentication process by verifying the received MAC with his calculated MAC(msg2)]cal(msg2)]rec).If the two MACs are identical,then the sensor authenticates the gateway and confirms that the gateway has the correct initial session key and has receivedN1from the first message.Otherwise,the authentication fails.To confirm that it has successfully receivedN2andfrom the previous message(message 2),the sensor calculates the hash ofN2,seqNbi+1,(h(N1‖N2‖seqNbi+1‖)) and the MAC for the whole message(msg3))all encrypted withkpand sends it to the gateway.
step 4:Gateway-→Sensor
Once the gateway receives message 3 from the sensor,it first decrypts the message and verifies that [h(Sid)]stor=[h(Sid)]recare equal.If not valid,authentication fails.Otherwise,it calculates the MAC for the received message and compares it with the received MAC(msg3)]cal=(msg3)]rec) .If the two MACs match,the gateway authenticates the sensor,as it knows that the sensor has correctly receivedN2,seqNbi+1,From message 2.The gateway then sends the encryption of the hash of its ID,an acknowledgment(ACK),and(msg4)to the sensor.The permanent key(kp)is used as the secret key.By this,the gateway confirms that it has correctly received message 3 from the sensor.
When the sensor receives message 4 from a gateway,it decrypts the message and verifiesh(Gid)and(msg4).If valid,it confirms that the gateway has successfully received message 3,and the mutual authentication process is completed.Once the mutual authentication is finished,the sensor and gateway generate the session key(ku)by using HKDF function andN1,N2as an input salt,the length of the key is determined byKlthandkikis used as an HKDF key.The session key is used for encrypting and hashing until the predefined session time is reached.After the pre-defined session time,the session key is updated by using the previous session information.
B.Normal Communication Between IoT Device and Gateway
As we can see in Fig.5,during normal communication between sensor and gateway,the sensor sends encrypted and hashed normal session frames using a session key.When the gateway receives the message from the sensor,it first decrypts it and calculates the MAC for the whole message.If the received MAC matches the calculated MAC,the gateway authenticates the sensor,knowing that the sensor has the correct session key.Then the gateway sends an encrypted and hashed acknowledgement message to the sensor,confirming that the previous message has been correctly received.Once the sensor receives the acknowledgement message from the gateway,it confirms that the gateway has correctly received the previous message and has the correct session key.Now,it sends the next frames to the gateway,and the same process is repeated until the pre-defined session time is reached.After that,the next phase for session key update can start.The sensor and gateway secretly keep all the information used for the next session key update phase during this phase.
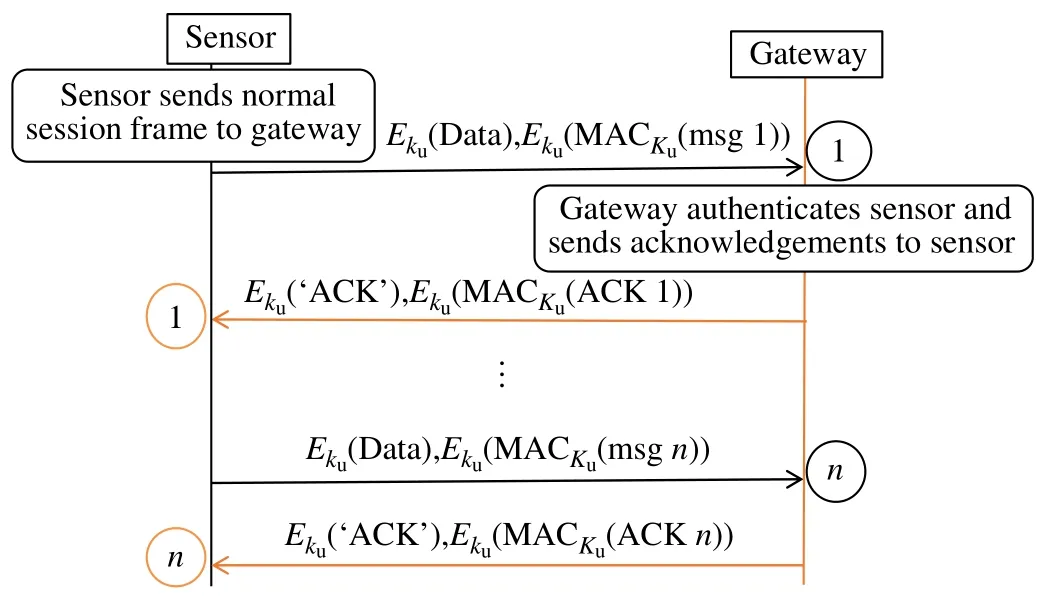
Fig.5 Normal communication phase
C.Session Key Update Phase
The session key update process is shown in Fig.6.The different steps are described as follows.
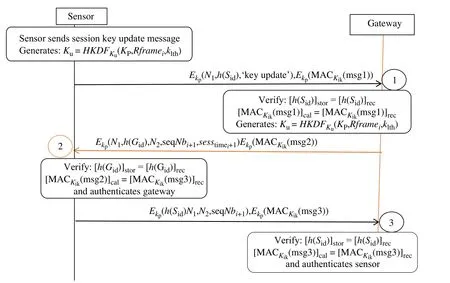
Fig.6 Session key update phase
step 1:Sensor-→Gateway
Once the pre-defined session time is reached,the IoT device calculates the new session key (ku) by using HKDF ofRframeias input information andkpas a salt input,currentkuis used as an HKDF key.The IoT device sendsh(Sid)and’key update’ command (to notify the gateway about the key update process),a new challengeN1and(msg1) all encrypted withkpto the gateway.
step 2:Gateway-→Sensor
When the gateway receives the key update message,it decrypts it and verifies if the pre-defined session time is reached.Then,it calculates the next session key by using HKDF ofR frameias an information input andkpuses as input salt.The current session key is used as HKDF Key.The gateway sends the encryption ofh(Gid),N1,N2,seqNbi+1,by usingkpto the IoT device.
step 3:Sensor-→Gateway
When the IoT device gets the message from the gateway,it decrypts the message and calculates the MAC.If the received MAC matches the calculated MAC,then it authenticates the gateway.It sendsh(Sid),N1,N2,seqNbi+1,and(msg3) usingkpto the gateway.When the gateway receives the message,it calculates the MAC.If it matches the received MAC,then it authenticates the IoT device.This completes the update key process,and the new communication session can start.
V.SECURITY ANALYSIS OF THE PROPOSED PROTOCOL
A.Theoretical Security Analysis
In this section,we present a theoretical security analysis to evaluate the security robustness of the protocol.We believe that by providing two secret keys,we enhance the robustness of the proposed protocol,as it is difficult for the attacker to discover them.Knowing one key is not enough to violate confidentiality and message integrity.The security analysis shows that the designed protocol can support various security proprieties including resist man-in-the-middle attack,data integrity,data confidentiality,mutual authentication,replay attack,brute force attack,and impersonate attack.
Man-in-the-middle attack:Man-in-the-middle attack is a type of cryptographic attack over a communication channel where an active attacker secretly takes over a confidential communication channel between two parties.Attackers can intercept,read,modify,and replace the communication traffic between victims[26].In this proposed protocol,if the attacker intercepts the communication traffic between sensor and gateway,he needs to know both permanent keys(kp)and session key(ku)before decrypting and modifying data.Even if an attacker knowskphe cannot calculateskuas it depends on the previous session key and the previous random session number.Furthermore,the intruder cannot obtainkubecause the keys are never exchanged over the network.If we assume thatkpcan be discovered in the mutual authentication phase,manin-the attack still cannot succeed,as the attacker needs to learn the initial session key to prove his identity.In consequence,an attacker is not able to decrypt and modify data.Therefore,the protocol can resist man-in-the-middle-attack.
Data integrity:Data integrity guarantees that messages are received as sent with no duplication,insertion,modification,or reordering.We used the HMAC function to provide data integrity.Before sending messages,both sensor and gateway calculate the MAC for whole messages.If the received MAC matches the calculated MAC,they know that messages are not modified during transmission.If an attacker wants to tamper with transmission messages,he must knowkuused as encryption and hash key during a session.In mutual authentication,the attacker needs to knowkpandkikbefore tampering with messages,and this allows us to confirm that the protocol can guarantee data integrity.
Data confidentiality:Confidentiality is the protection of transmitted data between communication nodes.It ensures that only the sender and the receiver can read or modify the message.We used two secret keys to provide data confidentiality.Traffic from the sensor and gateway are encrypted with the secret key,which is never shared over the network.It makes it difficult for the attacker to know the secret key.Therefore,we can confirm that the protocol can achieve data confidentiality.
Mutual authentication:As mentioned in section III.B.1),secure mutual authentication is required between the two devices before establishing a normal communication process.Once the mutual authentication step is successfully done,secure normal communication can start.Attackers cannot intercept the data during the normal communication process.The authentication credentials are encrypted and hashed using a pair of secret keys manually inserted into the devices by the administrator.Therefore the protocol can achieve secure mutual authentication.
Replay attack:A replay attack is a form of cyber-attack where an attacker eavesdrop on valid messages exchanged during an authentication phase and replays these captured messages later to impersonate a legitimate party to establish an authentication session.In this proposed protocol,the use ofh(Sid),N1,N2,h(Gid)guarantees replay attack prevention.The receiver first verifies the validity of all this informationbefore authenticating the sender.Furthermore,once the mutual authentication is established between sensor and gateway,all the previous information is invalid and cannot be used later to manage an authentication process.If an attacker tries to perform a replay attack,the gateway and the sensor can detect that these messages are invalid and authentication fails.Therefore we can confirm that the proposed protocol resist replay attack.
Brute force attack:a brute force attack is a form of a cyber-security attack in which an attacker tries to guess the password or the secret key to decrypt the message.In this proposed protocol,the attacker cannot perform a brute force attack for three main reasons.Firstly,the length of the secret keys is so long that it makes it difficult to perform a brute force attack to discover them.Secondly,the secret keys are inserted into the sensor and gateway in a no-volatile memory(EEPROM),and they are never exchanged over the network.This makes it difficult to discover them.Lastly,the attacker does not have any information about the secret keys.Therefore,it will be very difficult to guess them.In addition,the attacker will not be able to initiate mutual authentication to log in sensor or gateway,as he cannot provide all the mutual authentication process information.Hence,the protocol can resist brute force attacks.
Impersonation attack:in this attack type attacker tries to masquerade as a valid user node.If the attacker wants to masquerade sensor or gateway,he needs to learnh(Sid),N1,N2,h(Gid) before impersonation attack can succeed.However,not all this information can be discovered without knowing the secret keys.Therefore,we can confirm that the protocol can resist impersonation attacks.
B.Attacks and Security Proprieties Comparison
Tab.2 summarizes and compares the attacks and security proprieties of the proposed protocol compared with other related works.As we can see in this table,the proposed protocol can resist all attacks compared to the related protocols.The existing proposed schemes cannot resist various attacks such as man-in-the-middle attacks,brute force attacks,and replay attacks.Moreover,most of these protocols cannot achieve mutual authentication and anonymity.For these reasons,we can confirm that the proposed protocol provides better security features than the other existing related protocols.

Tab.2 Attacks and security proprieties comparison with other related protocols1
C.Communication Cost Comparison
We analyze the communication cost of the proposed protocol and make a comparison with other related protocols.To analyze the communication cost,we assume the different encryption and hash digest values presented in Tab.3.In this work,all the authentication credentials are hashed and encrypted before transmitting to the receiver.By making these assumptions,we aim to calculate the number of bits transmitted during the authentication phase.Based on Fig.4 and Tab.3,the communication cost during the authentication phase can be calculated as follows.
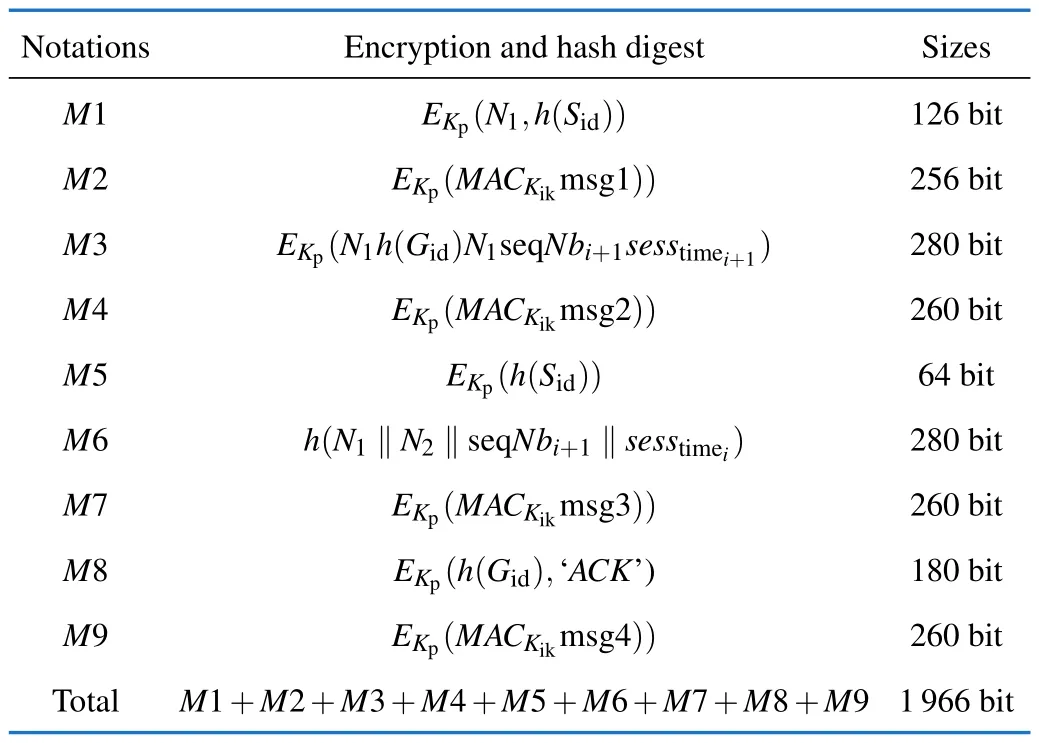
Tab.3 Communication cost
step 1:{M1,M2},{126+256382 bit}
step 2:{M3,M4},{280+260540 bit}
step 3:{M5,M6,M7},{64+280+260604 bit}
step 4:{M8,M9},{180+260440 bit}
The total bits after the 4 steps are:{382+540+604+4401966 bit}.
The total communication cost during the authentication phase is 1 966 bit.By comparing this value with the existing related protocol described in Tab.4,we found that the proposed protocol requires low communication cost than Ref.[32],Ref.[35],and Ref.[36].The proposed scheme has a higher communication cost compared to Ref.[33],Ref.[34],and Ref.[38].However,the difference is acceptable.Therefore,from the perspective of resource-constrained propriety,the proposed protocol is suitable for wireless sensor networks.
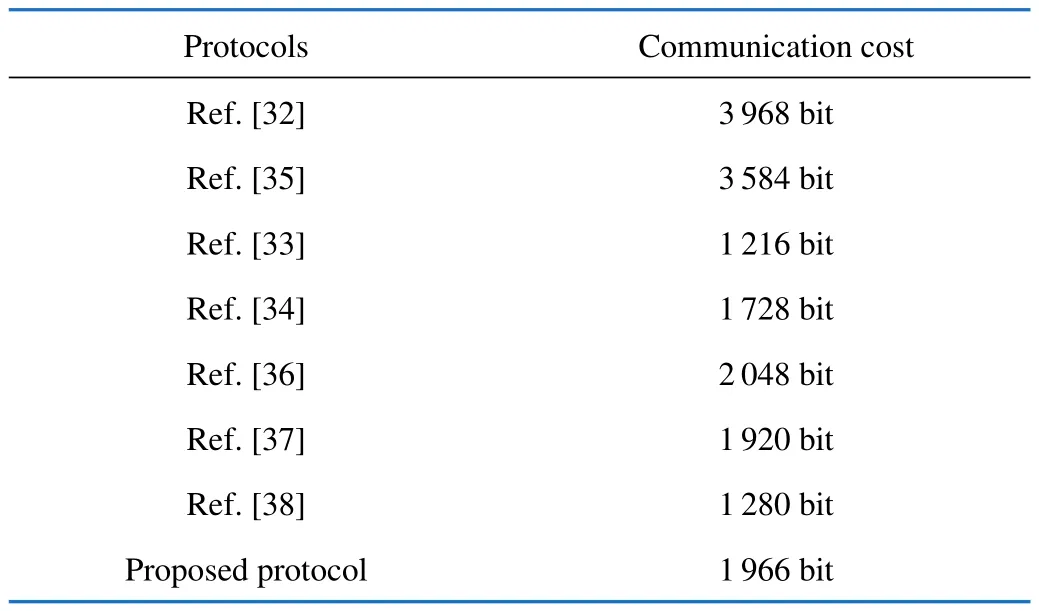
Tab.4 Communication cost comparison
D.BAN-Logic Security Proof
To validate the protocol,we used the Barrows-Abadi-Needham (BAN)-logic method to analyze and prove the se-curity robustness of the proposed protocol.The BAN-logic,designed by Burrows,Abadi,and Needham is a set of rules for defining and analyzing information exchange protocols.It helps protocol designers to prove the security of the protocol by determining whether exchanged information is trustworthy,and secured against attacks[39].The BAN-logic is a widely-used protocol analysis method to verify the robustness and correctness of an authentication protocol.It is also a robust validation logic method used to prove the mutual authentication of an authentication protocol.We start the BAN-logic analysis in this work by defining the different goals(4 goals).Then,we set the idealized form of the transmitted messages and the assumptions of BAN-logic proof.After that,we perform the security proof of the proposed protocol step by step based on BAN-logic rules.We achieved the previous defining goals after 16 steps.Showing that the proposed protocol has good security and performance.The proposed scheme is robust and efficient and can be applied in an IoT environment.It is also suitable for resource-constrained networks.The different notations of BAN-logic used in this work are presented in Tab.5.The BAN-logic analysis process is described below.
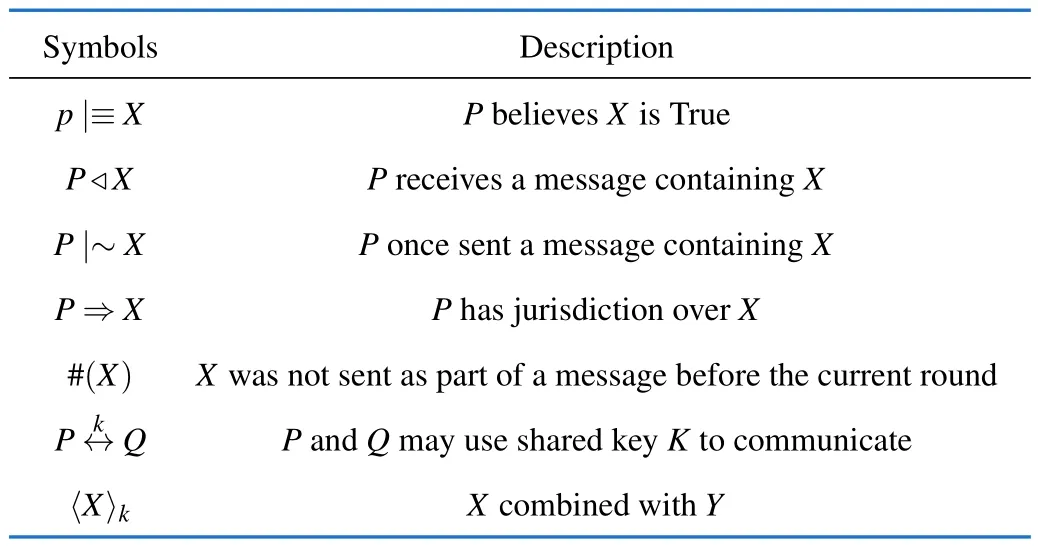
Tab.5 BAN-logic notations
1)BAN Logic Formulas:the BAN-logic formulas considered in this work are defined as follows.
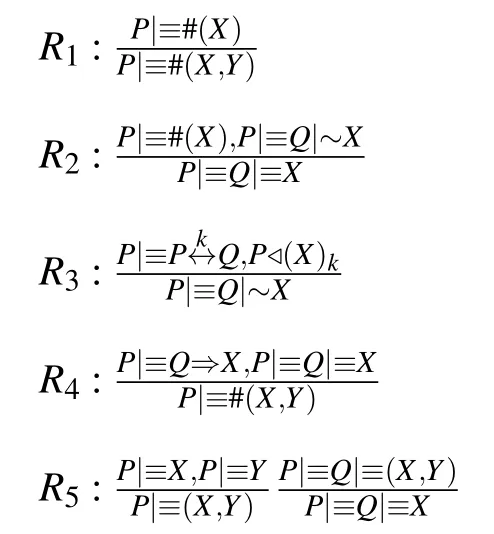
2)Security Goals:Ku
KikandKlthhave been negotiated in advance.So we aim at satisfying the following security goals.3) The Idealized Form:The idealized form of the message exchange is presented as follows.

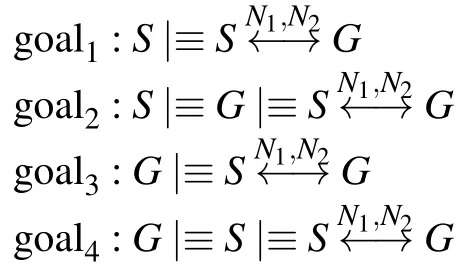
4) The Assumptions:We make assumptions about the initialization as follows.
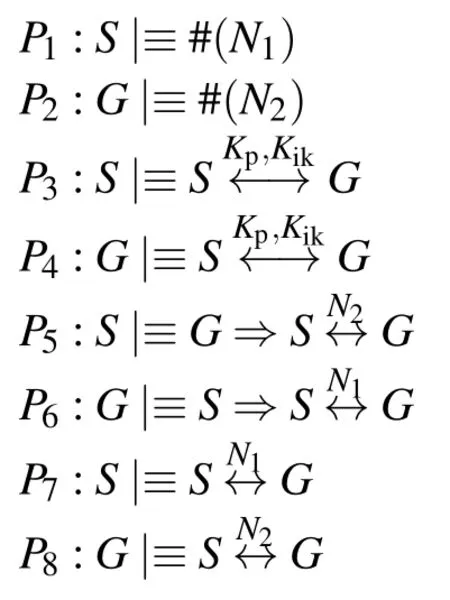
5) The BANLogic Proving Process:The BANlogic proving process is described as follows.

VI.CONCLUSION
This paper presented a lightweight mutual authentication protocol for IoT.A lightweight cryptography mechanism that includes symmetric-key cryptography,HMAC,and hash function are used to design the protocol.The proposed scheme is based on two main shared secret keys,a permanent key(kp) used for encrypting messages during the mutual authentication phase and an update key (ku) used for the communication session.The session key is constantly updated after a pre-defined session timeby using the previous session information.Mutual authentication,normal communication,and session key update are the three main parts of this protocol.At each part,a security mechanism is provided to guarantee secure communication between the sensor node and the gateway.We analyze the protocol using the BAN-logic method and the results show that the proposed scheme has good security and performance.It can provide a secure mutual authentication mechanism in the IoT environment.Consequently,the protocol is efficient and suitable for resource-constrained networks.The theoretical security analysis also shows that the protocol can support various security properties,and the confidentiality and message integrity cannot be violated by knowing only one key.The protocol can contribute to increase energy efficiency and reduce economic costs in the wireless sensor network.We will enhance the protocol by using the physical unclonable function(PUF)algorithm for future work.It will avoid inserting a secret key into the device,making the protocol more secure.
杂志排行
Journal of Communications and Information Networks的其它文章
- Channel Estimation for One-Bit Massive MIMO Based on Improved CGAN
- DOA Estimation Based on Root Sparse Bayesian Learning Under Gain and Phase Error
- Multi-UAV Trajectory Design and Power Control Based on Deep Reinforcement Learning
- Local Observations-Based Energy-Efficient Multi-Cell Beamforming via Multi-Agent Reinforcement Learning
- Rethinking Data Center Networks:Machine Learning Enables Network Intelligence
- RIS-Assisted Over-the-Air Federated Learning in Millimeter Wave MIMO Networks
