Jamming Monitoring Technology of the Space Situational Awareness Facilities:A Comprehensive Survey
2022-04-29SitianLiuChunliZhuChenYangLiyangChenKunFangKuoLiXingHeZhipengWangLihengBian
Sitian Liu, Chunli Zhu, Chen Yang, Liyang Chen, Kun Fang,Kuo Li, Xing He, Zhipeng Wang, Liheng Bian
Abstract: Complicated electromagnetic environments of the space situational awareness facilities(i.e., satellite navigation systems, radar) would significantly impact normal operations. Effective monitoring and the corresponding diagnosis of the jamming signals are essential to normal operations and the innovations in anti-jamming equipment. This paper demonstrates a comprehensive survey on jamming monitoring algorithms and applications. The methods in dealing with jamming signals are summarized primarily. Subsequently, the jamming detection, identification, and direction finding techniques are addressed separately. Based on the established studies, we also provide some potential trends of the demonstrated jamming monitoring issues.
Keywords: space situational awareness facilities; jamming monitoring; deep learning; jamming detection; jamming identification; jamming direction finding
1 Introduction
The space situational awareness facilities (i.e.,satellite navigation systems, radar) are among the critical components to enable space offensive and defensive capabilities, as well as provide high-precision, full-time, all-weather navigation and positioning services for human-centric economic society[1, 2]. However, the increasingly complex electromagnetic environment and various jamming signals are challenging the reliability of the space situational awareness facilities[3–5]. In Tab. 1, some classic examples are demonstrated, in which signal jamming is crucial for both military and civilian applications [6–8]. In such circumstances, this paper conducts a comprehensive survey on the jamming monitoring technology from the methodology and application scenarios, which would be a reference for the subsequent studies.
The comprehensive review on jamming monitoring of the space situational awareness facilities includes the following contents: 1) types of jamming signals; 2) jamming monitoring methods; 3) jamming monitoring applications. They respectively constitute Section 2, Section 3, and Section 4. The discussions are addressed in Section 5.
2 Types of Jamming Signals
As stated before, jamming signals would be masking the real signals or transmitting the misleading information[9, 10]. In this section, we briefly summarized the typical types of jamming signals.
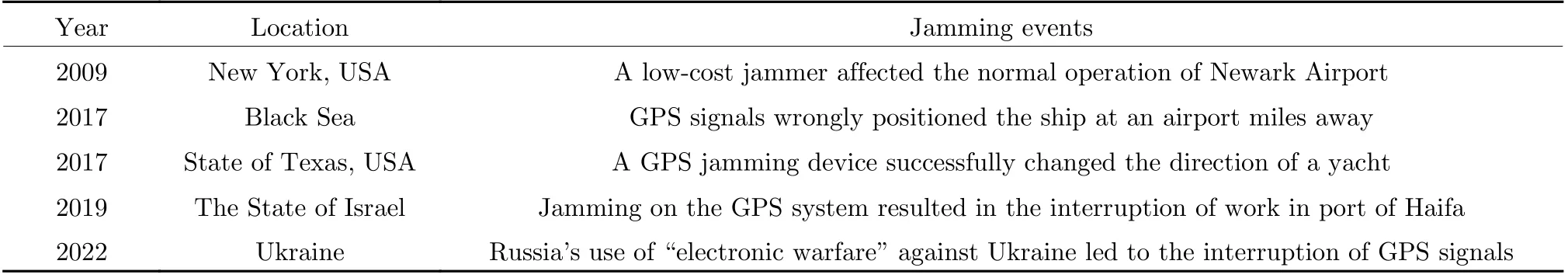
Tab. 1 Some typical jamming events
2.1 Malicious Jamming
Malicious jamming refers to an artificially generated signal that intentionally affects the routine operations of the facilities, in which suppressive jamming and deceptive jamming are among the two main types[11, 12].

Fig. 1 Types of malicious jamming signals
Suppressive jamming is the jamming that overloads the receiving equipment with highpower noise jamming or masks the working signal with other signals[13, 14]. The kind of jamming would continuously reduce the facilities’ operational accuracy by maliciously decreasing the signal-to-noise ratio (SNR) of the input signal.Suppressive jamming is extremely common for its low cost and simple principles. Representative suppressive jamming types are shown in Fig. 1,including targeted jamming, semi-target jamming, blocking jamming, and sweep jamming.Common suppressive jamming includes surplus continuous wave jamming (SCWJ), pulse jamming (PJ), chirp jamming (CJ), etc.
Deceptive jamming is generally designed for specific facilities or target signals with sufficient knowledge, which aims to induce the false judgment[15, 16]. The deceptive jamming signal is analogous to the target signal to a certain degree,which is solid concealment and difficult to be detected. The formation mechanism of deceptive jamming naturally leads to high design costs. In addition, the impacts of deceptive jamming would not only disrupt the system operation but also completely control the system. Under this circumstance, deceptive jamming is even more destructive than suppressive jamming. Representative deceptive jamming types are shown in Fig. 1, including false target, intensive false targets, and distance gate drag. Common deceptive jamming contains noise product jamming (NPJ),dense false target jamming (DFTJ), and distance deception jamming (DDJ), etc.
2.2 Non-malicious Jamming
Non-malicious originates from complicated and variable electromagnetic environments, for example, under weather events such as storms,ionospheric scintillation in the atmosphere, or radio frequency interference in electromagnetic space[17–19]. For not artificially generated disruptions, non-malicious jamming is beyond the scope of this review.
3 Jamming Monitoring Methods
We discussed the feasible jamming monitoring methods separately from the perspectives of traditional algorithms and machine learning.
3.1 Traditional Algorithms
Traditional algorithms, such as fuzzy C-means(FCM) method, wavelet transform, maximum likelihood method, and subspace-based methods rely significantly on domain knowledge. Moreover, the attributes of the input feature are often extracted manually and adjusted according to the realistic scenarios.
Wavelet transform is a classical denoising method, which is widely used in signal analysis,image processing, seismic exploration data processing, etc.[20]. Wavelet transform provides a time-frequency window that varies with frequency and is an ideal tool for signal time-frequency analysis and processing[21]. It replaces infinite-length trigonometric bases with finitelength decaying wavelet bases, which realizes high-frequency time-subdividing and low-frequency frequency-subdividing. However, wavelet domain denoising is effective in processing low-dimensional data, but not applicable for high-dimensional data.
FCM is a clustering algorithm based on the function optimization, which uses fuzzy logic to solve the optimal cost function[22]. FCM assigns weights to each object and clusters that indicate the degree of its affiliation. However, FCM strongly depends on the quality of initialized data and is easy to fall into local minima. FCM has been effectively applied in large-scale data analysis, vector quantization, pattern recognition,etc.[23].
Maximum Likelihood is also a well-known model-based method in signal processing[24].This method deduces parameter values from samples and selects the optimal solution with the smallest variance among all unbiased estimates.Maximum Likelihood has better significance sample accuracy and does not require the signal to be Gaussian. However, it involves a highly nonlinear and multi-dimensional optimization procedure, which leads to higher computational costs[25].
The subspace-based method relies on specific geometrical properties of the assumed data model, which is usually implemented by eigenvalue decomposition (EVD) and singular value decomposition (SVD)[26]. Compared with maximum likelihood, the subspace-based method exhibits excellent super-resolution and high-precision signal identification behavior. However, it is still computationally intensive and prone to spacial leakage due to difficulty inaccurately distinguishing between the signal and noise subspace at low SNR. Subspace-based method is commonly applied to source localization in radar and sonar systems[27].
3.2 Machine Learning
Common machine learning methods, such as support vector machine (SVM), decision tree, and artificial neural network (ANN), are research hotspots in the artificial intelligence and pattern recognition [28, 29]. As an important branch of machine learning, deep learning mainly uses multi-layer nonlinear processing units for feature extraction and transformation, including convolutional neural network and recurrent neural network[30, 31].
SVM is a linear classifier for binary classification of data[32], which is achieved by finding the hyperplane with the maximum distance between two categories. This classification method could reduce the impact of local disturbance and has robust classification results and competitive generalization ability. It is worth mentioning that SVM is a method dealing with small sample, nonlinear, and high-dimensional model.SVM is generally used in pattern recognition problems in various fields, such as portrait recognition and text classification[33].
Decision tree implements the classification process by judging different characteristics of data[34]. In a tree structure, each node represents a feature, each branch represents a test result, and each end leaf node represents a category.Benefiting from the simple structure of the decision tree, the computational complexity is relatively low, therefore suitable for solving the classification problems of large data volume. However,the decision tree would be overfitting easily and have poor generalization performance[34].
In addition, other machine learning algorithms, such as logistic regression (LR), Knearest neighbor (KNN) and random forest(RF), are also being utilized[35– 37]. The researchers have improved the shortcomings of the above machine learning algorithms and promoted the model’s performance. For example, the RF algorithm consists of many decision trees,which enhances the decision tree algorithm through the accumulation of decision tree and avoids over fitting[38].
ANN simulates how neurons send signals to one another, inspired by the human brain [39].The characteristics of the network structure make it capable of self-learning and associative memory storage. However, due to the complexity of the framework, the running time is often consumed, and the black-box effect makes the learning process invisible. ANN has achieved excellent results in different fields such as image processing, signal processing, and wireless communication[40].
Convolutional neural network (CNN) is a feedforward neural network with deep structure including convolutional computations, which is universally applied in image recognition, target detection, malfunction detection, etc.[41, 42].CNN consists of convolutional layers, pooling layers, and fully connected layers, which has larger parameter size and powerful learning ability.CNN could automatically extract features and reduce subjective bias in manual feature extraction methods. However, CNN is prone to gradient disappearance if the model is too deep. With the improvement of computer computing power,CNN began to develop expeditiously. Among them the popular CNN mainly includes LeNet in 1986, AlexNet in 2012, GoogleNet in 2014, VGG in 2014, and ResNet in 2015[43–46].
Recurrent neural network (RNN) is a recurrent neural network with short-term memory capability, which is suitable for dealing with timing-related problems such as video, speech, text,etc.[47– 49]. Compared with CNN, RNN performs better in processing sequence features.However, RNN requires many parameters to train and is prone to gradient dissipation or gradient explosion. To solve the gradient disappearance overtime, the researchers developed a long-short-term memory unit (LSTM), which maintains memory over time by switching between gates[50].
4 Jamming Monitoring Applications Overview
The development of software-defined radio technology and open-source simulation software stimulates the signal jamming applications, which is frequently occur worldwide[51]. According to the type of the applications, this section includes jamming detection, jamming recognition, and jamming direction finding.
4.1 Jamming Detection
Jamming detection is the first step of the monitoring system, and its detection accuracy concerns the effectiveness of the following response strategies[52, 53].
Some studies used the traditional strategic algorithms to solve jamming detection problems such as fuzzy mean algorithms, wavelet transform, etc.[54, 55]. In [56], A. Javad et al. could effectively reduce the variance of predicted values by using improved Doppler frequency shift estimation and FCM algorithm. In [57], X. Yan et al. measured the signal complexity by the approximate entropy (ApEn) method and obtained mutation point by moving-cut data approximate entropy (Mc-ApEn). The results showed that ApEn and Mc-ApEn are more robust than the wavelet transform in detecting deceptive jamming under noisy conditions. In [58],Q. Quiros et al. designed wavelet-based estimators and jamming detectors. They could effectively predict the start and finish time of the pulse jamming. In [59], X. Duan et al. combined the weighted least square algorithm and Chisquare test to determine the existence of RGPO.
The traditional algorithms for jamming detection are improved accordingly, with signal processing and mathematical analysis techniques[60, 61]. In [62], Y. Xu et al. investigated the jamming signal detection from high dimensional spectral data based on truncated singular value decomposition (TSVD). The method could ensure both high precision and recall rate, and the accuracy rates exceed 97%.
Machine learning is widely used in jamming detection because of its ability to represent hidden features in historical big data. In [63], J. A.Jahanshahi et al. realized jamming detection based on SVM through modeling of Terrestrial Trunked Radio (TETRA ) analog base station receiver, which effectively reduced the hardware complexity. The results showed that the accuracy of the proposed method could reach more than 90% at low Doppler frequency shift, and more than 70% at high Doppler frequency shift.In [64], H. Xu et al. introduced the method of spectral components clustering of multi-period signals into jamming detection, where the magnitude of the normalized mean square error is below 10−4.
ANN could be applied for jamming detection due to its adaptive and self-organizing capabilities[65, 66]. In [67], R. Mohsen et al.provided a performance comparison of machine learning-based methods for detecting ADS-B receiver jamming attacks, including LR, ANN,SVM, and KNN algorithms. Results showed that when the ANN has two hidden layers and fifteen neurons in each hidden layer, the detection accuracy would reach 81%. In [68], A. Youness et al. compared the efficiency of several machine learning methods in detecting jamming signals in the field of wireless communications, and the results showed some superiority of RF-based methods on accuracy and computational cost.
As to the specific area of deep learning, CNN and RNN are the most widely used in dealing with jamming detection. In [69], J. Yu et al. designed the improved VGG16 according to the statistical characteristics of synthetic aperture radar (SAR), to detect whether signals in the dataset are contaminated by the barrage jamming. In [70], after using the nearest neighbor interpolation (NNI) and the short-time Fourier transform (STFT) to analyze the signal, J. Qian et al. applied VGG16 and AlexNet to detect the presence of jamming within the time-frequency(TF) range. The work showed that AlexNet was superior to VGG16 in generalization and recognition time.
In addition, LSTM could directly process the time or spectrum sequence of the signal in signal detection damain without extracting time-frequency images (TFI), thus reducing the computation cost and running time[71]. In [72], combined with the LSTM designed by C. Robert et al., they used the predictability of Doppler characteristics of received signals to determine the presence of malicious attackers. In [73], M. Liu et al. utilized the LSTM network to detect satellite communication jamming, and combined with numurous filtering fast algorithms to suppress the alpha-stable noise. The algorithm could reduce the complexity of infinite filtering by iteratively approximating the estimated value.
The preprocessing procedures and the algorithm structures used for jamming detection are summarized in Tab. 2.
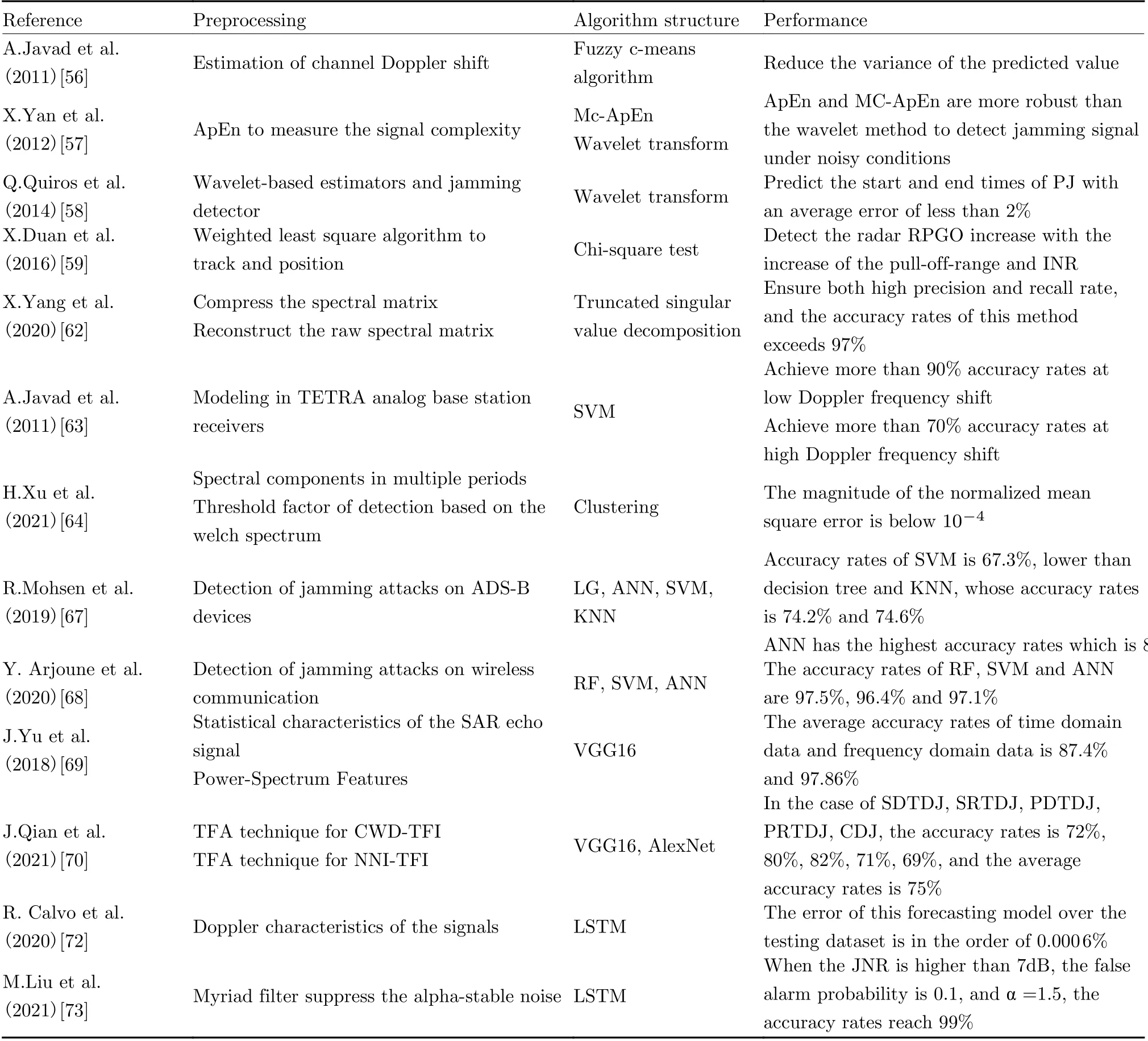
Tab. 2 Overview of the jamming detection algorithms
4.2 Jamming Recognition
Identifying jamming signals accurately in the complicated electromagnetic environment is the basis of effectively taking anti-jamming measures.To cope with the jamming, it is necessary to collect various jamming samples, analyze their different signal characteristics, establish a jamming database, and quickly identify the jamming signals[74, 75].
Signal likelihood estimation is usually used in traditional jamming identification algorithms.In [76], J. Wang et al. designed appropriate wavelets to recognize BPSK signals. In [77], H.Wu et al. extracted high order cumulants for frequency analysis (FA), combined with wavelet transform to perform denoising, and then achieved jamming recognition based on signal features. In [78], Y. Niu et al. exploited LZ complexity and box dimension as features and exponential fuzzy membership function to identify jamming patterns.
Machine learning algorithms were also widely used in jamming identification, such as SVM, decision tree, and ANN. In [79], Y. Wen et al. considered signal’s high order cumulants as feature vectors after separating the mixed jamming signal by the blind signal separation (BSS)algorithm. Then they realized the recognition of four jamming signals by using SVM as classifiers.In [80], G. Wang et al. established signal feature space based on signal models expressions and signal space theory, and then realized binarization and multi-class classification by SVM. In [81], D.Su et al. extracted a set of FA and time analysis(TA) characteristic parameters with small computation and strong robustness, and then identified six jamming signals through decision tree. In[82], Y. Wei et al. recognized six radar jamming signals by decision tree based on fuzzy clustering Xie-Beni index and information gain.
In recent year, jamming recognition based on deep learning has been popular. The general recognition process is as follows: a) Extracting the TFI features of signals; b) Input the TFI into the constructed DNN for training; c) Input the signal to be recognized into the trained network to determine jamming type.
In addition, some studies extracted the TFI of the signals and extracted the features via the TA technique or FA technique to increase the recognition accuracy of the network. The researchers tend to use time-frequency analysis(TFA) to extract TFI, such as Choi-William distribution(CWD), Cohen’s time-frequency distribution(CTFD), Wigner Ville distribution (WVD),Smooth Pseudo Wigner-Ville distribution (SPWD), and STFT[83].
Besides TFA, TA or FA is also utilized separately to extract the signal features. In [84],G.Shao et al. extracted the real part and the imaginary part of the time domain of the jamming signals in the preprocessing and then input the features into two 1D-CNNs with different structures for identification. In [85, 86], the jamming data are preprocessed with the FA technique. In [85], Q. Qu et al. input the 1-D power spectrum of the signal to the improved ResNet18,where the residual block is improved into an asymmetric convolution block. In [86], J. Ma et al. extracted the frequency features of the jamming signals, and the licensed frequency of the jamming is also determined in the preprocessing stage. If its frequency is not the licensed frequency, this broadcasting signal would be recognized as unauthorized broadcasting directly, and the preprocessed features would be determined.Then they applied a complex LSTM network for recognition.
In [87–89], feature extraction is conducted via the classic CWD-TFI in TFA during the preprocessing stage. In [87], T. Huynh-The et al. accomplished the recognition by inputting the CWD-TFI into an improved CNN consisting mainly of three sophisticated modules. In [88], S.Zhang et al. utilized an atomic norm-based method and a sparsity-based reconstruction technique to obtain a high-resolution time-frequency distribution of the jamming signals and realized recognition via an 8-layer CNN. In [89], S. Kong et al.used sample averaging technology(SAT) to preprocess and efficiently reduce the high computational cost, in which a 6-layer CNN was then recognized. In [90], CTFD-TFI was used to extract TFI, combined with image resize and amplitude normalization to preprocess TFI. After that, they used a convolutional denoising autoencoder (CDAE) to denoise and repair TFI and then employed an improved Google Net with inception structures to recognition.
The computational complexity of frequent utilized CWD cannot be ignored. Therefore, some studies use other TFA techniques for TFI extraction. In [91], C. Wang et al. used WVD-TFI as a substitute to extract TFI in the preprocessing,followed by an 8-layer CNN. However, WVD has severe cross-terms while reducing the amount of computation, which is not conducive to characterizing the jamming. In [92], SPWVD was applied to preprocess TFI, which could significantly reduce the cross term of WVD but followed by the increase of calculation cost. They resized, grayscaled, and enhanced the images,which is handled with an improved CNN squeeze net consisting of squeeze and expansion modules.STFT is a linear transformation that does not generate cross-terms and requires less computation. In [93], the jamming parameters are measured based on the ordered statistics constant false alarm rate (OS-CFAR)algorithm, and then they adopted STFT to obtain the TFI and proposed a 9-layer CNN. In [94], P. Wang et al.combined frequency features and STFT-TFI in the preprocessing, and then a 1D-CNN and an improved ResNet are introduced to extract the deep features of the two prepossessing inputs, respectively.
Furthermore, when utilizing the deep learning algorithms to identify the jamming signals,one could input the jamming signals into the DNN directly without preprocessing, such as extracting the multi-domain features. For example,in [95], the jamming signal was directly input the signal into the 9-layer CNN and combined it with multidimensional scale analysis for identification.
Many different types of conscious jamming have been utilized to test the performance of various CNN structures. Some papers mainly identify suppressive jamming[76, 80], while others focus on identifying deceptive jamming[90,91]. In [94, 95],authors identify not only single jamming but also complex jamming. Although the performance of various CNNs is noncomparable because of the input difference, the recognition accuracy is higher than 90% when JNR is 0 dB in [85, 95]. By comparing the experimental results, the method based on deep learning has better recognition accuracy than machine learning and traditional methods, especially at low JNR. Some other parameters of the dataset would influence the recognition accuracy besides JNR, such as bandwith, carrier frequency,sampling frequency, etc.
The preprocessing procedures, the algorithm structures and recognized jamming signals used for jamming recognition are summarized in Tab. 3.
4.3 Jamming Direction Finding
Jamming direction finding and direction of arrival(DOA) estimation are often recognized as a particular spectral estimation[96–99]. The research content of DOA estimation is to estimate the orientation of signal from the background noise, namely, detecting which transmitter is working and the transmitter’s direction.
The research of DOA estimation has gone through a long development process. Through the characteristics of the received data of the array and the steering matrix, a large number of excellent techniques have been developed to improve the DOA estimation performance. The traditional algorithms mainly include the maximum likelihood and subspace-based method and improved algorithms on these two methods.
Maximum likelihood is the most
fundamental method proposed for the DOA estimation problem. M. Pesavento et al. proposed new closed-form expressions and a more general noise model that could detect multiple sources from nonuniform white noise[100]. C. Chen et al.derived the stochastic maximum likelihood based on an iterative procedure to improve detection performance further[101]. The stochastic maximum likelihood provides better properties with nonuniform white noise, but its complexity is a few times higher than the conventional maximum likelihood.

Tab. 3 Overview of the jamming recognition algorithms
To improve the performance of SBM at low SNR, J. Xin et al. proposed a subspace-based method without eigen decomposition to reduce the computational complexity[102]. This method has low computational cost and superiority in solving spaced coherent signals with few snapshots and low SNR. J. Wen et al. used spatial smoothing techniques for constant white noise to mitigate the effect of noise nonuniformity, which makes better performance with coherent signals[103]. M. Cao et al. used the forward-backward averaging[104] based on tensor, which further improves the performance with coherent signals. K. Xu et al. refined the signal subspace and get better performance in lower SNR[105].
Some studies concentrated on reducing the computation amount. H. Xu et al. improved the sample covariance matrix via linear shrinkage to eliminate the negative effect of mutual coupling.It also suits large-scale uniform linear arrays[106].X. Yang et al. reconstructed the covariance matrix with diagonal loading and achieved better performance with few snapshots and low computational complexity[107].
However, existing direction finding algorithms, such as estimation based on Maximum Likelihood and the subspace-based method, are computationally expensive and difficult to meet real-time requirements. To solve the problem, researchers propose using of a neural network for direction finding. In[108], X. Chen et al. utilized multilayer perception (MLP) neural networks to detect the presence of a source in a sub-area and applied radial basis function (RBF) neural networks for position estimation. The results show that the MLP-RBF method has the same performance as the traditional algorithm with lower computational intensity, beneficial to real-time direction finding. In [109], W. Liu et al. used ResGAN to deal with DOA problem and could achieve higher resolution and better generalization with random signal numbers and SNR. In[110], Y. Ma et al. proposed a deep learningbased super-resolution DOA estimator, enabling higher resolution and more POR. The preprocessing procedures and performance of jamming direction finding are summarized in Tab. 4.
5 Discussion
In this work, we conducted a comprehensive survey of traditional and emerging algorithms and discussed the application of these techniques in jamming monitoring of space aware facilities.Traditional algorithms based on mathematical theories were usually used for jamming monitoring, but plenty of prior and expert knowledge was often required. With the development of artificial intelligence, researchers utilize machine learning for jamming monitoring, which could achieve higher accuracy than traditional ones,but more computing resources than the traditional methods.
Challenges in jamming monitoring are shown as follows. 1) The performance of jamming monitoring under low SNR requires to be improved.2) The amount of iterations and its correspondence calculation time for the deep learning approach are of significant large, especially when extracting the signal’s two-dimensional time-frequency features. 3) The requirement of receiver's real-time application approach is not easy to be guaranteed for the large amount of simulations.
The potential direction in jamming monitorning are summarized as follows. 1) In the cur-rent design of jamming monitoring system, the monitoring algorithms of suppressive and deceptive jamming are independent of each other. How to effectively combine those two types, and accurately determine the type of jamming is the direction of future development. 2) With the development of artificial intelligence technology,space perception equipment is becoming more and more complicated and diversity. How to construct jamming monitoring network through artificial intelligence technology, accurately detect jamming, determine the type of jamming, and test the direction of jamming is the research direction that requires further investigations.

Tab. 4 Overview of the jamming direction finding algorithms
杂志排行
Journal of Beijing Institute of Technology的其它文章
- Objective Quantification of Small Motor Sound Quality Based on Psychoacoustic Metrics
- ISAR Imaging and Cross-Range Scaling Based on Image Rotation Correlation
- Fast Rail Defect Inspection Based on Half-Cycle Power Demodulation Method and FPGA Implementation
- Restoring Polarization Angle Map for High-Fidelity Underwater Imaging
- Jamming Recognition Based on Feature Fusion and Convolutional Neural Network
- Unmanned Technology-Based Civil-Military Intelligent Logistics System : From Construction to Integration
