Computing Paradigms in Emerging Vehicular Environments: A Review
2021-04-16LionSilvaNaercioMagaiaBrenoSousaAnnaKobusiskaAntnioCasimiroConstandinosMavromoustakisSeniorMemberIEEEGeorgeMastorakisandVictorHugodeAlbuquerqueSeniorMemberIEEE
Lion Silva, Naercio Magaia, Breno Sousa, Anna Kobusińska, António Casimiro, Constandinos X. Mavromoustakis,Senior Member, IEEE, George Mastorakis, and Victor Hugo C. de Albuquerque, Senior Member, IEEE
Abstract—Determining how to structure vehicular network environments can be done in various ways. Here, we highlight vehicle networks’ evolution from vehicular ad-hoc networks(VANET) to the internet of vehicles (IoVs), listing their benefits and limitations. We also highlight the reasons in adopting wireless technologies, in particular, IEEE 802.11p and 5G vehicle-toeverything, as well as the use of paradigms able to store and analyze a vast amount of data to produce intelligence and their applications in vehicular environments. We also correlate the use of each of these paradigms with the desire to meet existing intelligent transportation systems’ requirements. The presentation of each paradigm is given from a historical and logical standpoint.In particular, vehicular fog computing improves on the deficiences of vehicular cloud computing, so both are not exclusive from the application point of view. We also emphasize some security issues that are linked to the characteristics of these paradigms and vehicular networks, showing that they complement each other and share problems and limitations. As these networks still have many opportunities to grow in both concept and application, we finally discuss concepts and technologies that we believe are beneficial. Throughout this work,we emphasize the crucial role of these concepts for the well-being of humanity.
I. INTRODUCTION
IN this work, we introduce fundamental concepts of computing paradigms and their use in emerging vehicular environments and later analyze those that may be more promising in the near future. Usually, these paradigms have much in common in terms of the need for proper functioning,particularly in such environments.
Specifically, an efficient, fast, and integrated network is necessary for different forms of wireless connectivity. We chose to adopt a logical instead of physical perspective regarding the paradigm layers in question.
Regarding vehicular networks, we recall the need to provide safer traffic, and therefore protect human life, whether in large cities, on highways, or in rural areas.
Intelligent transportation systems (ITS) is a concept that covers both connected vehicle networks, and any other means that involves the cooperative, efficient, intelligent, safe, and economical transportation of people and goods with the construction of an infrastructure that is integrated with the means of transportation in question. Hence, there is a flow of data that, when transformed into information, allows drivers and managers to make the best decisions in perspective and real-time.
A vehicular ad-hoc network (VANET) is a specific type of mobile ad-hoc network (MANET) where network nodes (i.e.,vehicles) self-organize themselves to provide some simple but essential set of services. The internet of vehicle (IoV) is a novel vehicular environment with more powerful infrastructural elements (i.e., 4G/5G and Wi-Fi-enable OBUs,Access Points to the Internet, connection to the cloud, among others). In conjunction, these elements bring a novel set of applications and services not only fulfilling ITS but also commercial ones requirements.
VANET still has its value as it has been in stable development for 30 years. Its distributed and simple architecture is well suited to safety applications between nearby vehicles and pedestrians. Furthermore, it can provide simple, informative, and local services to the driver, such as nearby gas stations or traffic warnings in nearer electronic road signs.
Vehicular computing paradigms are an essential evolution of cloud and edge computing in vehicular environments.Using the newest communication technologies, and specific protocol techniques, these two paradigms provide a more robust and efficient network, in which cars can act such as cloud servers whenever the situation permits (i.e., in parking lots, traffic-congested roads). Furthermore, they can act as fog nodes where real-time services can benefit local drivers,pedestrians, business and citizens (if integrated into an interconnected, smart-sensor-fueled environment called smart city [1]).
Nowadays, security requirements such as confidentiality,integrity, availability, authenticity, authorization and access control, non-repudiation, reliability, and privacy are also crucial in vehicular environments, given the latest wave of cyberattacks.
There are also some inherent limitations of self-organized networks, such as the lack of cooperation among nodes, which pose additional challenges to integrating computing paradigms.
Zhao et al. [2] analyze deployable vehicle communication technologies, comparing them on their technical and nontechnical aspects, and summarizing their limitations. Huang et al. [3] propose a vehicular fog computing architecture and present several use cases. They also briefly discuss security challenges and potential solutions.
Our contributions, which is different from previous works,are as follows:
1) We provide a roadmap, starting from a historical and logical point of view, and give small panorama of the intersection between both subjects, namely computing paradigms and emerging vehicular environments.
2) We emphasize key security issues that are linked to the characteristics of computing paradigms and vehicular networks, verifying that because of what they are, they complement each other and share problems and limitations.
3) We present our view and hope of what we would consider reasonable for their materialization in the upcoming years when most commercial applications of the concepts discussed here are practical.
The remainder of this work is as follows: Section II presents a historical and conceptual perspective on vehicular communications. Section III presents emerging vehicular environments. Section IV presents computing paradigms. In Section V, limitations and challenges are presented, and Section VI presents security issues. Section VII presents future directions. Finally, Section VIII presents concluding remarks.
II. VEHICULAR COMMUNICATIONS
Both mobile networks and Wi-Fi are expected to receive new generations in 2020, with 5G for the former and 802.11ax for the latter [4], [5]. While 5G networks are expected to help make a leap in vehicle-to-everything (V2X) communications,another Wi-Fi-based vehicle-to-vehicle (V2V) communication standard, i.e., IEEE 802.11p, has been established since 2004.Both will operate in the 5.9 GHz band. IEEE 802.11p is part of the layers of a broader standard, IEEE 1609, which deals with Dedicated Short-Range Communications (DSRC).Among its objectives is communication between stations and access points (APs) in a model where the stations are highly dynamic such as vehicles [6].
The U.S. Federal Communication Commission (FCC),which is the regulator for radio, television, cable, and satellite communications, has decided to separate a 75 MHz band within the 5.9 GHz spectrum to be used for V2V and vehicleto-infrastructure (V2I) communications. The goal was to allow applications that would save lives and promote safety and fluidity in transit [7]. Theoretically, DSRC and IEEE 802.11a are similar, with the former being a version with less overhead than the latter and operating at 10 MHz of channel width, half the width of the latter.
In 2004, DSRC radio technology was standardized by the IEEE and gave rise to IEEE 802.11p wireless access in vehicular environments (WAVE) Standard. In Europe, the equivalent standard is called ITS-G5 and was officially adopted on 17 April 2019 [8].
On the other hand, there are the C-V2X networks, which have emerged as an alternative and extend mobile networks’capabilities to meet the needs of communication between vehicles, roadside units (RSUs), and even pedestrians. In these, the most significant proponent is the next-generation of mobile networks (i.e., 5G) [9], [10].
5G networks will resolve a set of challenges proposed by the Mobile and Wireless Communications Enablers for the Twenty-twenty Information Society (METIS). Specifically,most mobile devices have numerous purposes for communicating both with the internet and with each other, thus requiring low latencies, higher reliability, throughput, and more scalable algorithms. Moreover, the International Telecommunications Union (ITU) has defined requirements for this new generation that meet low-latency, in the order of 1 ms,and have data transfer rates between 100 Mbps and 1 Gbps,with a peak of 10 Gbps [4].
On the one hand, METIS has proposed that such a network should be extremely fast, reliable, and multi-purpose. Hence,it would allow a multitude of connected devices and would offer a good experience to mobile users, consequently mitigating most of the current common problems. On the other hand, the ITU has proposed that such a network could offer low latency and high reliability, allow multimedia services in new areas beyond entertainment, be prepared for IoT, and provide greater adaptability in new applications.Also, it would provide great efficiency in applications that are location-based, beyond those specified previously by METIS.Both METIS and ITU do not aim to present protocols to address these challenges, but only to list them given the human needs and world trends of this particular time.
As previously presented, communications in vehicular environments can be separated into V2V, V2I, and, ultimately,V2X, where the exchange is done both with infrastructure and with other vehicles. If 5G networks are utilized, we can take into account the following benefits [11], in contrast to IEEE 802.11p:
1) Millimeter-Wave (mmWave): There will be high throughput and bandwidth, and this is essential for fast communications between vehicles and things in a constantly changing topology scenario by nature.
2) Non-Orthogonal Multiple Access (NOMA): Multiple users can share time or frequency resources by multiplexing power or using encoding, where NOMA would give V2X the ability to cancel interference.
3) Multiple Radio Access Technology (Multi-RATS): 5G networks could benefit V2I or vehicle-to-network (V2N)communications (i.e., when the vehicle communicates directly to a server or cloud using cellular infrastructure) either by increasing network capacity and throughput. Alternatively,they can increase redundancy to increase performance in some remote driving use cases.
4) Antenna Design: Using multiple input multiple output(MIMO) and other techniques so that overall system capacity would be higher and therefore support more V2X activities.
5) In-Band Full-Duplex (FD): Throughput would be doubled by using the same band frequency to receive and send data, and
6) Mobile Edge Computing (MEC): Would enable performing real-time situational awareness, creating local maps in high definition, and analyzing in real-time the data being exchanged from multiple sources.
Both U.S. and Europe have adopted IEEE 802.11p and DSRC as the current acceptable standard for V2I and V2V communications; another part of the industry (the so-called 5G Automotive Association) believes that the future of V2X communications will be realized by the advantages of 5G networks [12].
According to the 5G Automotive Association, tests have shown that 5G networks can outperform 802.11p networks[13]. From the industry side, the following brands are adopting 5G: Daimler, Ford, Huawei, Intel, Qualcomm, and Samsung. On the other hand, some adopted DSRC: General Motors, NXP, Toyota, Volkswagen, and Volvo [14].
According to both ITU and METIS, 5G networks promise to be ubiquitous once deployed. However, their initial costs may be higher than those of Wi-Fi networks, with the later being around for over ten years [15].
Both technologies have their implementation difficulties,yet they share similar problems as mobile wireless technologies, such as topology dynamics and physical or radio interference from other sources. Nonetheless, the result of adoptions will only be known in the future. Perhaps neither standard will be dominant in the market or as the predominant form of communication in vehicular environments.
III. EMERGING VEHICULAR ENVIRONMENTS
In 1994 the first world conference known as world congress on intelligent transport systems (WCITS) was held in Paris,where the idea was to promote ITS globally was introduced[16]. This congress was the culmination of effort that began in the 19th century with the first traffic light [17]. Today, in full development, it involves millions of devices and sensors in highways, vehicles (e.g., utility, emergency or commercial vehicles, and public transportation ones), and adjacent structures (traffic lights, CCTV systems, weather stations,event detections).
A. Intelligent Transportation Systems
An ITS is defined as advanced information, communication,and electronic technology system that unites users, highways,and means of transportation in order to increase safety,convenience, efficiency, logistics, the productivity of any process involving the transport of people or things [18].Additionally, these systems aim to reduce the emission of pollutants into the air.
ITS systems require three general elements: communication,location, and mapping [19], [20]. From this need, these systems are composed of positioning, communication,mapping, network, and sensor technologies. Furthermore, they need a human-machine interface integrated into vehicles, in particular car navigation systems, so that even basic users are proficient enough, to be able to define a journey, route, or destination [19].
There are six major categories of ITS, namely advanced traffic management systems, advanced travelers information systems, commercial vehicles operation, advanced public transportation systems, advanced vehicles control systems,and advanced rural transports systems [18].
Also, there are three main types of ITS architectures:framework ITS architecture, which analyzes and summarizes user needs (functional and practical); mandated ITS architecture, which is the implementation of the previous part,and hence is a set of physical and logical, and communication layers; and service ITS architecture, which, starting from the previous architecture, adds services [21].
Following the development of ITS, vehicles had to communicate with each other in some way. The set of communications, usually wireless, between vehicles is called a vehicular network, and it can be delineated by, among other things, what types of entities communicate with each other.More formally, vehicular networks are wireless networks that are used by vehicles. They are dynamic, heterogeneous,changeable, and must meet the requirements of speed,reliability, and integrity to be considered trustworthy in a nonfixed topology [22].
B. Vehicular Ad-Hoc Networks
The simplest type of vehicular network is one that is between vehicles and uses V2V communications. A more advanced version adds devices fixed on the roads that we travel using V2I communications. The union of these two communications and their technologies forms the so-called VANET, whose main objective is to optimize traffic and reduce emissions, mostly of gases that pollute the environment [23]. A VANET is a subset of a broader set of networks with mobile nodes, also known as MANET [24].
VANETs can still be divided into three categories according to how the communication is being made: i) WAVE, if the IEEE 802.11p protocol is used and vehicles not only communicate only amongst themselves, but also between themselves and RSUs; ii) Ad-Hoc, if the communication is only between the vehicles (and there are no services or connection with the Internet); or iii) Hybrid if both are implemented concomitantly. RSUs and vehicles are the basic units of a VANET. In this architectural model proposed by the car 2 car communication consortium (C2C-CC), each vehicle has an on-board unit (OBU) and at least one application unit(AU). The former deals with the connection between vehicles or between vehicles and RSUs or Hot Spots (to connect to the Internet directly). Meanwhile, the latter serves to realize a set of services/applications and is also connected to the OBU[22]. The OBU does not necessarily have to use Wi-Fi technology as there are other alternatives such as 4G, 5G,WiMAX [24]. RSUs are stationary and linked together in a certain location where they are installed. They will be connected to the internet forming the infrastructure, where data coming from vehicles and themselves will be the basis for various services aiming at achieving some ITS objectives such as safe driving [24].

Fig.1. VANET architecture.
A complete version (see Fig.1) can consider the separation of RSU functions without the use of sensors. Therefore, there are four types of communication: V2V, V2I (being the infrastructure of mobile networks, e.g., cellular base stations,or Wi-Fi AP), vehicle-to-sensor (V2S) (which is in the vehicle itself, gathering on-board data from its own operations), and vehicle-to-RSUs (V2R) (where RSUs can be, for example, in traffic lights, and vehicle-to-pedestrian (V2P), among others[25]).
From the infrastructure side, there must be a trusted authority (TA) whose job is to manage the entire VANET network by registering RSUs, OBUs, and perhaps vehicle users. This management also includes user and OBU authentication. Ultimately, a TA could act as a substantial network intrusion detection system (NIDS), collecting information on suspicious activities from a particular vehicle or possibly identifying an ongoing attack [26].
Regarding standards organizations, VANETs have been appreciated by the IEEE for using 802.11p (and other related protocols), C2C-CC, ETSI, TC ITS, and the International Organization for Standardization (ISO). Their main objective is to connect the vehicular network in a continuous and unlimited way with a continuous air-interface, long, and medium range (CALM) [22].
ITS problems and challenges are also in VANETs.Specifically,
1) In a heterogeneous network with so many nodes, density spikes can happen relatively frequently. In these scenarios,scalability needs to be improved.
2) Securing applications and devices ensures that their communications are implemented concurrently with the overall development of VANETs. Security is necessary.
3) Quality of service (QoS) and traffic characterization in VANETs are more difficult because, in addition to the heterogeneity of the protocols of each V2X, applications will also have different QoS requirements.
4) Nodes’ cooperation is based on the fact that each member of the network, i.e., node, is working, sharing, and legitimately receiving information, and is willing to cooperate with other network nodes so that the services are available and reliable to all.
The union of all vehicle-to-something creates the V2X network. However, these networks do not have sufficient global information management power. Usually, they do not analyze, process, or evaluate information collected from vehicles globally [27].
Thus, they are an intermediate step to what the future vehicular networks will be, that is, the IoV, which is a specialization of the internet of things (IoT), as VANET is of MANET.
C. Internet of Vehicles

Fig.2. IoV architectures. a) 5-layers; b) 7-layers.
The IoV is defined as a network of the future in which integration between devices, vehicles, and users will be unlimited and universal, overcoming the heterogeneity of systems, services, applications, and devices. It also brings intelligence to the network, i.e., the information is distributed,shared, valued, in a way that is meaningful to both the user and vehicular systems, authorities, and service providers [28],[29].
Being a recent idea, different authors have been proposing architectures that differ in certain aspects. For example,Kaiwartya et al. [28] proposed an architecture (Fig.2(a)) in five layers.
1) Business: The outermost layer, for service sectors to add commercial value to the network.
2) Application: The service layer itself, where the intelligence will reside and give the user the feeling of total integration.
3) Artificial Intelligence: A second layer of intelligence, but focused on analyzing all information that is being exchanged voluntarily and globally. This is the layer at which computational paradigms will be located.
4) Coordination: Which is the core that already existed in a VANET, where one defines how and with which technology information will be exchanged (i.e., WAVE, LTE, 5G, among others). This layer, united with Perception, can apply the computing paradigm, such as Fog computing, which will also be discussed later.
5) Perception: Also already present in VANETs, will deal with sensors, RSUs, personal devices (e.g., AUs). It is at this layer that the information is collected correctly, scanned, and transmitted.
Golestan et al. [30] proposed a 7-layer architecture (Fig.2(b)),similar to the previous one, but containing: a data acquisition layer, similar to perception, which collects intra-vehicle, intervehicle, and inter-objects data; a filtering and pre-processing layer, which chooses what and to whom to transmit what is collected; a communication layer, which would be responsible for the integration between network technologies (i.e., Wi-Fi,DSRC, LTE, 5G, among others.); a control and management layer, which would serve to control the integration of information traffic and policies applied to the network; a global processing layer that would integrate various types of cloud (i.e., public, private, or enterprise); and finally, the last two layers, which are between the vehicle and the user with audiovisual interfaces (that is, the user interface layer), and security (that is, security management), which would cover authentication, privacy, trust, authorization, accounting.
Kaiwartya et al. [28] presented a qualitative comparison between IoV and VANETs, showing some perspectives where the former is more advantageous than the latter. For example,reliable internet services are available continuously on IoVs.Meanwhile, on VANETs, whose architecture does not have to be collaborative, internet service is not available. The processing capacity of the network will be much higher since it is integrated to services in the cloud, as opposed to VANETs, which, in principle, are a network by themselves,not integrated to any cloud. The IoVs will, by default, be integrated between VANETs, Wi-Fi, 5G, and others, making it scalable by splitting and extending services and data transfer across diverse networks. Simultaneously, VANETs, because they are not collaborative, have only the local extension of themselves.
Ultimately, IoV can be viewed either as a collection of novel network technologies to provide the layered architecture discussed above. The intelligence is built and somewhat independent of VANET (as if working parallel to it or in its complete absence), or it can use a VANET established network for some layers (like coordination). That is because VANET not only is simpler and can take care of such a layer,but also already has emergency channels, in which priority messages can be passed faster.
D. The Importance of Novel Vehicular Environments
Human life is the central element of any technological evolution and revolution. When these changes happen,suddenly, there is an enrichment that brings comfort to those who can enjoy them.
In the 1980s, the first computers were marketed to families,businesses, and schools as a new way of relating to information. Later, with the commercial success of the internet,and especially broadband, the world became connected and agile. In fact, there were more means by which to expand the internet with the devices that could connect it. With the advent of smartphones, people are much more quickly and continuously connected. For example, it was estimated that in 2018 there were 3.5 billion people connected to mobile networks [31], [32].
New smart services were being made, such as those of socalled shared economies, in which a user could make certain goods available to others. In addition, integration services such as GPS, social networks, virtual credit cards could be used all at once, forming a virtual user that could: find the good, obtain information about the owner of that good, and pay for the service entirely through the internet. These types of services that bring a virtual user all the information necessary was one of the innovations of the last ten years. The next step to be taken is to make connected and intelligent a critical element in the lives of millions of people, i.e., their vehicles.
In general, vehicles still have not widely adopted the connections that in the last 30 years have been established globally such as Wi-Fi, 3G, 4G networks. Connected vehicles,which contain the technology to be considered smart devices,have the potential to increase road safety and driver wellbeing. For example, in the U.S., in 2017, there was a cost of$433.8 billion related to accidents involving motor vehicles with 40 231 fatalities [33]. In the E.U., in 2016, 25 600 lives were lost in traffic accidents, in addition to 1.4 million people injured [34]. Therefore, road safety is the central element of any process involving the integration of vehicles into an intelligent network.
ETSI ITS defines around 32 use cases to ensure different safety elements between pedestrians, vehicles and other elements [20]. In the basic set of applications, there is, for example, ITS systems that can enable driver assistance including road hazard warnings, emergency electronic brake lights, wrong-way driving warnings, traffic condition warnings, among others.
These use cases can be more or less divided into categories where they fit VANET or IoV networks, which implies both network importance and differences.
On the one hand, IoV is better for services that share some intelligence, i.e., higher-level services that use more expensive computation or data storage to provide a context of the many factors involving the network and users. They can also be used to establish efficient carpooling schemes [35] and artificial intelligence (AI) [36], [37]. For example, can be used to provide information about traffic jams provide advertisements based on user location and personal preferences, or avoid accidents. AI is one of the critical technologies for IoV applications.
On the other hand, we have VANET that was primarily conceived to inform drivers about harsh conditions or emergencies that could be happening nearby. This includes messages passed by nearby vehicles when facing an unexpected situation where drivers must brake, where other drivers would benefit from being alerted. RSUs can also send messages either to vehicles directly or, after some data computation, to outdoors installed along the road, where they provide almost real-time information.
In short, VANET is essential to road safety situations, and IoV will provide higher-level services, enabling regular programmers to build services too.
The expected benefits of vehicular networks for safer traffic include fewer accidents (mainly fatal ones), more timely responses in their occurrences, less congestion and less pollution, safer social and entertainment dynamism in the use of vehicles, and better-informed users of the road, traffic, and route conditions. More computational power will allow for the the realization of these networks, in the long run, we will be able to see the different types of intelligent services that emerge.
Therefore, the use of emerging vehicle networks is welcome in the sense that they have the potential to prevent various types of traffic accidents by reducing the loss of human lives.
IV. COMPUTING PARADIGMS
As previously mentioned, the implementation of vehicular networks is planned in several different ways aspects depending on the adopted architecture. Mainly, there are two aspects to consider depending on the type of wireless communication: either V2X or IEEE 802.11p. VANETs were also considered somewhat archaic networks, and consequently, the need to introduce “intelligence” in the network motivated the appearance of the IoV concept. There are also other essential aspects to consider. For example, we must consider how heterogeneous we want the network to be, that is, how many different types of services and devices can participate in it. Furthermore, we must determine how can we distribute the analysis of the collected data in a way such that the most important data has low latency in their distribution and/or collection or are readily available where they are most needed. It is also necessary to define the data that is not of immediate need, and where they will be kept. For example,this could include information about the number of times that there was a traffic jam on a certain road during a certain month of the year. This can be processed to generate statistics or build relevant information for users, authorities, and service providers.
A paradigm is a specific way of seeing or understanding a particular thing. In the context of vehicular networks, one way to solve the problem of data availability where it is most needed, especially when there are real-time requirements, and when the stakeholders are network elements close to the vehicles or their users, is using a computing paradigms.Moreover, one way to be able to store and analyze a vast amount of data to produce relevant information after collection is also through computing paradigms.
A. Cloud Computing
According to NIST [38], cloud computing is “a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g.,networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction”. It became common in the literature to use NIST’s definition. Nonetheless, it is interesting to note that ten years ago, when cloud computing was in its early days, there were so many definitions that some authors decided to bring them together in the search for the striking and common features [39].
An important feature of cloud computing is that its services and means of provision can be sub-categorized. Thus, the cloud is composed of characteristics that will concretize its proposal as defined above, and characteristics that will be used for the cloud to behave in a certain way, defining the service model. Finally, those characteristics will determine who is responsible for its management. Depending on the latter, there are three basic models and a hybrid model [40]that unites them:
1) Private cloud, where the manager is a private entity,typically a technology company.
2) Community cloud, where the manager(es) has(ve) some policy requirements that are shared and involve the use of the cloud, whether these policies are common concerns of managers and users or even some common mission to achieve.
3) Public cloud, where the manager may be a government,academic, or even private entity, but the use of the cloud is open to any user. The purpose can be varied.
4) Hybrid cloud, in which the manager uses both previous models, noting that the way they are interconnected is by some technology that still distinguishes each cloud as a distinct entity.
Despite these being the base models, there are others such as the Inter-Cloud [41], [42], and its main variants: Multi-Cloud, Federation Cloud, Micro-Clouds and Cloudlets, Ad-Hoc Clouds, and Heterogeneous Clouds.
Inter-Cloud allows for different clouds to collaborate in order to ensure greater availability of services for users (e.g.,for vehicular networks, monitoring, and vehicle maintenance services) [43] as well as the gain of computational resources[44]. One of the reasons Inter-Cloud is recommended is because while cloud computing providers are concerned with configuring their data centers in different geographic regions,they have a limitation in creating policies that ensure optimal load balancing between different data centers, as well as ensuring optimal QoS [45]. In [43], a framework was developed using business models based on platform production services (PPS), IoT, and Inter-Cloud computing aiming at convenience, efficiency, and safety in vehicular networking applications (VNA). In this framework, VNA stands out in the use of cloud services for scalability of the computing level and an Inter-Cloud architecture that supports telematics applications and scenarios.
Multi-Cloud computing [46], [47] refers to the relation between different service models of cloud computing (i.e.,infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS), and software-as-a-service (SaaS)), being this motivated by the variety of implementations and administrative domains of cloud computing.
Federation Clouds [48] are those where a service is offered with shared resources between public and private providers that rationalize the use of their clouds and mutually increase computing power, avoiding service disruption. Implementation is difficult because the best way to define integration rules is still diverse, although efforts in this direction have been made for a long time [49].
As for the components of services that the cloud can offer,three basic types may have sub-categories to the extent that innovation allows [38]:
1) IaaS: In the scale of services, this is the “lowest level”offered in the sense that the user hires a subset of computational resources (whole operating systems, storage, processing, and main memory) in which he can operate in any way he wants. He will have no control over the cloud infrastructure itself, nor the entire network.
2) PaaS: In the scale of services, this model is intermediate,in which the user no longer has the control he had in IaaS.However, he can have control of some host settings so that applications made in languages and libraries supported by the provider run as desired. These applications can be made, and usually are, by the user.
3) SaaS: In the scale of services, this model is the “highest level”. In it, the services are made by the provider, and the user buys the right to use them in the cloud but cannot modify the application or any underlying aspect of the infrastructure that runs it.
Other examples of the “as-a-service” collection include backend-as-a-service (BaaS), storage-as-a-service (STaaS),cooperation-as-a-service (CaaS), traffic-information-as-aservice (TIaaS), vehicle-witnesses-as-a-service (VWaaS),mobile-backend-as-a-service (MBaaS) [50], database-as-aservice (DBaS) (i.e., Relational Cloud) [51], network-as-aservice (NaaS) [52], and function-as-a-service (FaaS) [53].
In order to implement a cloud architecture in the general case, it will be necessary to use a collection of data centers providing different kinds of services that including storing large amounts of data as well as performing demanding computation tasks. Also, since the cloud is thought of as a seamless computing resource that a user can use but not possesses, the services are accessed by network infrastructure.
The machines used need to have virtualization technology where virtual layer can be used to provide transparency of the services as a whole and protection for each individual machine, in which virtualization emulates specific operating systems and configurations for final users.
The services can be distributed between cloud data centers,but, in general, one can view this as a centralized paradigm since all users need to be served from a particular cloud most of the time in a client-server model. As previously stated, the nature of the cloud and services can vary.
Finally, an efficient cloud implementation requires algorithms for energy spending, task distribution, and efficient revenue maximization, as the complexity of offering such services often does not provide the best way to manage the cloud’s resources.
In this respect, Bi et al. [54] and Yuan et al. [55] give optimization methods for different parts of the cloud’s management process. They, among others, indirectly target the economy in and around cloud computing and directly target resource provisioning because many external cloud services are allocated to its environment.
In the first work, the allocation of heterogeneous resources from virtual machines to Virtualized Cloud Data Centers is addressed. In conclusion, several Service Level Agreements are met more cheaply and efficiently. In the second, an algorithm (i.e., temporal task scheduling algorithm (TTSA)) distributes tasks in a Hybrid Cloud environment that unites a Private Cloud (i.e., a restricted resource cloud), and Public Clouds (i.e., an unrestricted resource cloud) so that the former is not overloaded, which manages to decrease the underlying operating costs.
B. Fog Computing
Fog computing [56] is defined as a way to extend cloud services to the edge of the network. It is based on the philosophy that data should be processed where it is collected[57], [58].
The edge consists of two sets of devices. The first ones are devices that will consume or send data on the network;however, as users of one or more services made possible by the network itself, without contributing to its infra-structural functioning. End devices can be smartphones, IoT devices,vehicles, sensors, or others, and simply have the necessary hardware to connect. The second set of edge devices are those that are part of the network infrastructure and provide intermediate access to services, either by managing the data that passes through them, or by providing access to the services, or by serving as a data storage point.
Fog computing aims at solving problems that arise when the number of devices to access the network is so high that QoS metrics such as latency, response time, among other performance metrics, fall below the minimum defined for the well-being of the user and the requirements of the services provided. Ultimately, it can be a paradigm to extend network scalability, given the innovations to be leveraged with smart devices.
Dastjerdi et al. [56] proposed a possible architecture for fog computing consisting of three main layers: cloud, edge devices, and the network between them. Between the cloud and edge devices, there will be a layer of software that enables the infrastructure. This layer does not explicitly deal with enduser services or network protocols but with managers and performance monitors orchestrating the operation of cloud and fog services. In the outermost layer lies the services themselves, that is, the innovations that providers can offer or that will be created by third parties.
According to Xu et al. [59], the following tiers should be considered to implement a fog architecture:
1) User-Tier: The implementation will be based on diverse types of sensors, smart devices, vehicles using Wi-Fi,Bluetooth, LTE, 5G, or other wireless technologies to communicate between each other and with the Fog-Tier.
2) Fog-Tier: The implementation will be based on different nodes, namely switches, routers, access points, and dedicated fog servers.
3) Cloud-Tier: The highest tier contains multi-purpose data centers to operate in a fog context for services that are not in real-time.
The User-Tier will be served by real-time services provided by fog nodes since they were designed mostly for this type of service. Services that can build a context awareness from a more prominent view can be built in the Cloud-Tier. The latter will be presented back to the lower tiers in the form of better distribution of fog nodes and fog layer abstraction software,and provide users with a better experience.
The Fog-Tier will distribute data and perform computational offloading so that the services can be experienced both at the location they are being provided or in a decentralized manner,protecting the lower layer from slow responses and poor QoS.
The Cloud-Tier will be used to gather data that is not immediately used by the User-Tier in a real-time context.Then, some computation can be performed to obtain statistics,AI, and other knowledge-based services, in addition to other computationally demanding services. Please note that more information can be found in [60].
C. Other Computing Paradigms
Other paradigms are close to cloud and fog computing.Specifically, edge computing [60], which does not connect to the network, and the infrastructure and service is between end devices and edge devices. Mobile cloud computing (MCC) is similar to cloud computing, where moderation of use is considered due to limited energy capabilities, and can pose a problem for computing-intensive services. Moreover, mobile edge computing (MEC), which, similarly to fog computing,aims to be used between users with mobile devices and the mobile network [61].
Besides these, there is dew computing [62], [63] that is located at the floor level of the cloud and fog computing environment. It involves the microservices concept (in which its computing is vertically distributed) rather than solely storage/networking. Mist Computing [64] is similar to fog computing but lighter and closer to endpoints than the fog itself. It is performed by using microcomputers and microcontrollers. These specialized and near peripherals are the helpful counterpart to more powerful fog nodes. Mist nodes can help IoT devices have self-awareness and selforganization capacities. Finally, cloudlets [65], [66] are a lighter version of cloud services and infrastructure. They are put near mobile devices, where the intent is to provide access to the Internet, storage, and powerful computing. They are usually small data centers powered with virtualization technologies in such a way that mobile devices can offload their computation to them.
D. Computing Paradigms in Vehicular Environments
Here, we revisit the definition of concepts such as fog,cloud, and edge computing in vehicular environments as follows:
1) Vehicular Cloud Computing (VCC): VCC [67] is the case where vehicles will be functioning as a cloud, i.e., when together, they form a kind of computational “cluster” with the processing power equivalent to that required for certain “large services”, and possibly will be used as temporary storage of large volumes of data. Optionally, there will be vehicles using cloud (VuC) [68], where the cloud will be an external entity to the vehicle network, but connected to it, probably far away,from a service provider that does not necessarily own or manage the vehicle network in some way.
2) Vehicular Fog Computing (VFC): In a vehicularenvironment where services, processes, data, policies whose execution time, transmission latency, and availability need to be measured in real-time, each vehicle can be restructured as a dynamic part of that network by offering the computational power for those sets of operations provided within the network in order to decrease the overhead of “large services”or simply eliminate them when it is possible to solve network needs locally [69]. A fog vehicular computing (or vehicular using fog computing) [70] network will be a vehicular environment whose fog nodes are RSUs, or any other geographically distributed equipment to meet the needs of the VFC without necessarily having any vehicle as a fog node.
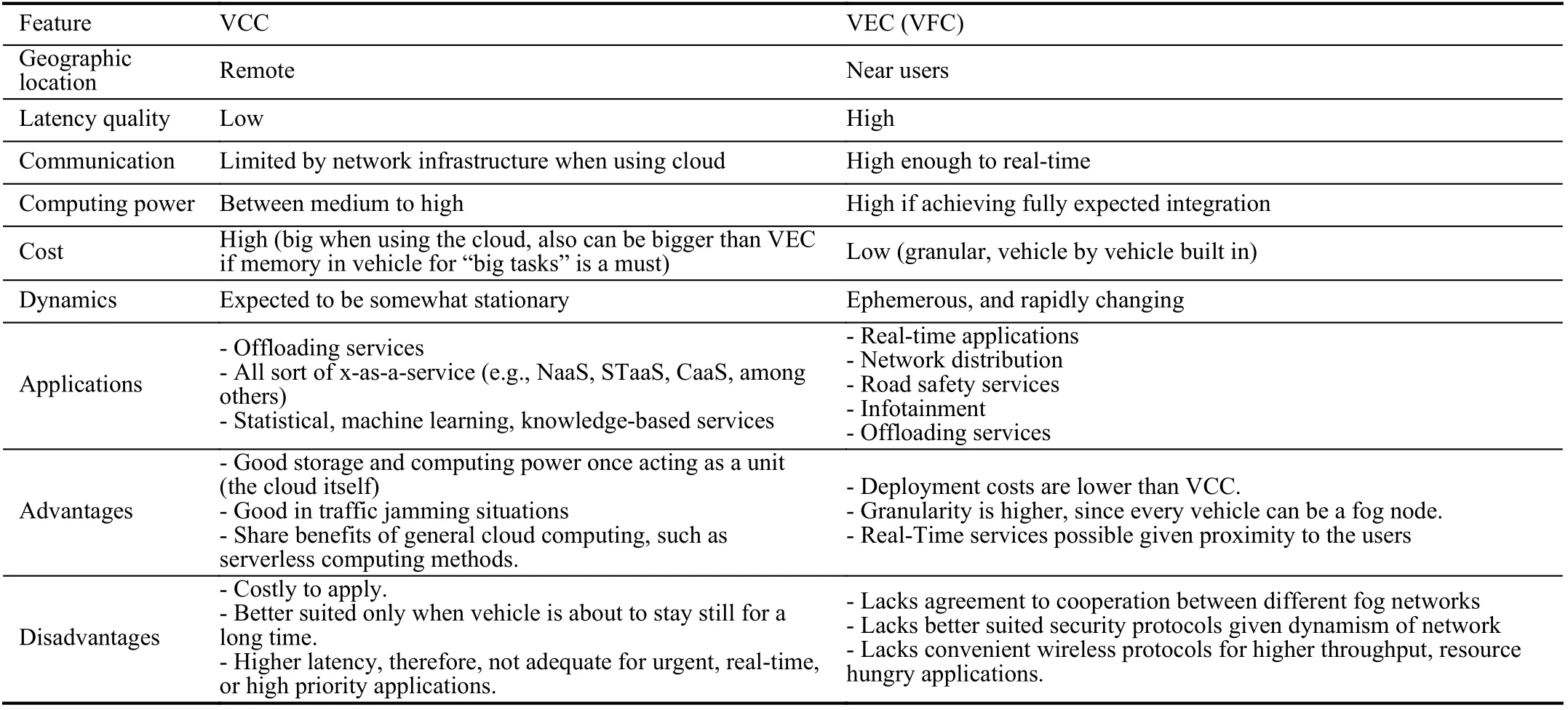
TABLE I VCC VS VEC COMPARISON
3) Vehicular Edge Computing (VEC): The term VEC can be seen as a generalization/variant of VFC, just as fog computing can be seen as a variant or implementation of edge computing[71]. Furthermore, as MCC is the paradigm that encompasses VCC, MEC is the paradigm that will encompass VEC (and VFC) [72]. Therefore, we take this perspective only with the difference that edge nodes are vehicles, and then, if edge computing is used, RSUs will be edge nodes.
Table I summarizes what is consensual about VCC and VEC paradigms. Please note that some advantages or disadvantages mentioned are simply because of current technological limitations, instead of general architectural faults.
Depending on the infrastructure of each of these types of vehicular networks, we choose to summarize in two figures all paradigms as we describe them in a way that is in line with the literature. In Fig.3, we emphasize the global vision. It should be noted that the way services implemented and distributed should not strictly follow this organization. However, it is expected that the implementations take advantage of the architectures presented. Besides, the expectation that the cloud is distant, and therefore denoted in Fig.3, is valid since most cities will most likely not have a large computing center from service providers such as Google or Amazon. However,nothing prevents other types of clouds from being more locally stored, by intermediate or even large service providers or by merely solving local storage and data analysis needs.
Other essential aspects are:
1) The use of 4G, 5G, as well as IEEE 802.11p is critical to achieving the level of ubiquity that METIS ITS standards require.
2) Both VCC and VFC would divide the intermediate layers, redirecting the data according to the type of service provided and their priority.
3) A VCC does not necessarily need to be connected to the internet (Fig.3), but a VuC does.
4) An RSU does not need to be a fog server if vehicles are already a distributed fog server or nodes. However, in order to increase the granularity of the network and to guarantee that in specific geographical points there will always be a fog node available, excluding eventual failures, RSUs can pack a server as a minimum computational power and storage that may be considered necessary for the most basic services that the vehicular network offers at that point.
5) In principle, the Vehicular Cloud can be used in places of high concentration of parked vehicles for a long time. In such cases, this cloud may eventually serve clients other than those of the enterprise in which they are parked. This will depend on the interest of various involved parties (i.e., users and managers).
6) If both paradigms are available, and if vehicles have more than one way to connect wirelessly, it may be interesting to separate the paradigms for each type of connection, such as real-time data passing through 4G, 5G to VFC, and data for later analysis and intelligence building through IEEE 802.11p to Base Stations. Thus, if a group of vehicles is facing congestion that is predicted to last for a long time (e.g., one hour or more), the vehicles may decide to form a cloud while performing fog node functions at the same time using different types of wireless communications.
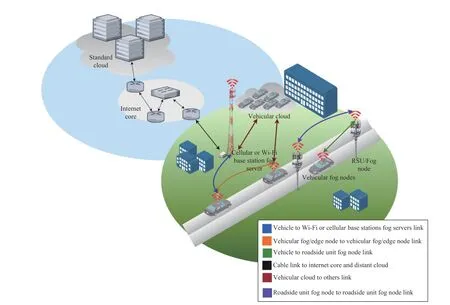
Fig.3. Interactions between vehicular cloud and fog (or edge) paradigms.
V. LIMITATIONS AND CHALLENGES
A. Limitations
Up until now, we ha ve described and even discussed some limitations of each of the paradigms as well as the associated vehicular networks. Here, we extend this discussion even further.
In IoVs, the following factors, although necessary for their proper functioning [73], still present some limitations: i)Interoperability of network architectures: there is a need for the development of communication protocols to ensure better transmission of a large volume of data as well as interoperability, meeting IoV requirements; ii) Intelligent routing and route planning: the constant modifications of network topology, due to high vehicles’ mobility makes it necessary for IoV to take measures to define routes in the communication layer as well as ensure that autonomous vehicles are able, for example, to find routes with the shortest distance and lowest cost; iii) Sensors and AI: the use of AI can reduce the effort to process data collected by various sensors scattered on highways, and assisting in decision-making; and iv) Real-time massive data processing: combining sequential and parallel processing is essential to optimize processing limitations since it is necessary to integrate parallel data acquisition, data processing and big data analytics in IoV.
The following possible limitations have been identified in VANETs: RSUs communication, cooperation with other networks, standards, and complexity and technological infrastructure [24], [25], [74].
Specifically, concerning the first point: i) the number of RSUs available on the road: vehicles need to send and receive data from the network, where the lack of Internet signal (a signal that in this scenario comes from RSUs) will directly influence communication with the cloud; ii) limited communication range: in addition to the previous limitation,the communication range is a fundamental requirement due to the nature of vehicles themselves, i.e., they are constantly moving away from the physical positioning of RSUs; iii) lowquality communication links: data transmission failures may occur due to low signal quality, making it necessary to find alternatives for sending and receiving data.
Regarding the second point, VANETs are focused on safety,that is, focused on current traffic situations, and not particularly on entertainment (or similar). Therefore, they do not integrate, a priori, the Internet, and reduce costs; the option is to use WAVE or 5G, but not necessarily both. In addition, they do not integrate other types of networks such as IoT, as VANET’s data is produced and disseminated by vehicles, RSUs, and Base Stations.
Concerning the third, communication standards already exist in VANETs, and they deal with general aspects such as how a node enters or leaves the network. However, it is thought that it might be better to produce more refined standards for cyber-physical systems involved, for example,vehicles, motorcycles, buses, ambulances, among others, as we have seen before in the architectural components of an ITS. Besides, having a global coupling standard between VANETs will be necessary as they grow, and different providers and public agents realize that their networks will be meeting geographically.
Relating to the last, one of the factors that make the popularization of VANETs more difficult is that the implementation costs are still high given the interest that people have in possessing a vehicle with connection capabilities to participate in them. Moreover, an RSU is an expensive device [75]. It also involves a physical structuring of space, with structural changes in cities, highways. Thus, it is complex in terms of strategy and management, and in the interests of public and private agents.
Acceptance, resource management, and suitable technologies are some of the limitations of Vehicular Clouds [76].Specifically, acceptance is practical and not technical. The owner of a vehicle must have reasons to want to participate in a VCC, as it implies sharing its resources, and there must be a benefit for him to be interested. Commonly, vehicles do not automatically participate in a VCC, nor are they obliged to do so. Then, it is necessary to make choices regarding load balancing, data dissemination, and resource allocation. That is, it is still necessary to deal with algorithms that distribute resources efficiently from an energetic and computational point of view so as not to overload the vehicles. Therefore, the idea is not to generate expenses higher than those required for those who ask for them (in the same way as a Cloud Service Provider would charge for using the cloud, the vehicle owner may also charge). Lastly, VCC networks lack the central element that will make them possible, i.e., a medium or a set of wireless communication means that are fast enough for the massive demand for data traffic that is expected. WAVE or 5G can be used, but network saturation, even for these two types of communication, might be achieved relatively quickly,increasing the cost of implementation and use.
For Vehicular Fog, there are the same questions given above for VCC and besides others, namely network topology and mobility model, and privacy [77], [78]. On the one hand,with Vehicular Clouds, it is not always necessary to worry about network dynamics, but in the case of VFC, it is mandatory. One of the assumptions is that nodes are incredibly dynamic and fast (i.e., they are moving vehicles).The mobility model should predict which vehicle enters and exits or which sub-part of the network it is headed to in realtime. Furthermore, currently, there are neither protocols nor ways to integrate this network in the ubiquitous way that one so desires, mainly because VFC is presently a growing topic.
On the other hand, it will be necessary to keep fog nodes private and, at the same time, known on the network. The differentiation of what can be shared and kept secret is still a limitation under study. For example, to mitigate part of the network topology problem, fog nodes could be willing to disclose their location in real-time, and that the network could know the route of any GPRS device they used. However, this possibly constitutes a privacy breach.
It is also necessary to consider big data as previously stated,the volume of data expected today and in the upcoming years is in the order of zettabytes. Furthermore, this data may be used to understand the usage patterns of certain services, i.e.,general network behavior, and QoS.
Xu et al. [79] describes both topics, i.e., IoV and big data,that we highlight below:
1) Wireless Condition: It suffers from various blocking elements, such as buildings, other cars, and networks. From the vehicle’s perspective, these obstacles are amplified due to their constant movement. Thus, the topology dynamism is a crucial factor. Big data applications and services will suffer as any other since this is a global problem.
2) Spectrum Resource Shortage: Considering an IoV implementation, the number of applications that will follow will be enormous. However, contrarily, the spectrum allocated by some countries for wireless communication seems to be insufficient to supply such a rich range of applications. For instance, the FCC only allocated 75 MHz of licensed spectrum for DSRC, which is insufficient for big data applications.
3) High Mobility and Dynamic Density: Mobility and density dynamism are among the core differences between IoV and VANETs with other common networks. A highway can lead to a “smoother” network since cars are moving along the road at an expected maximum speed, and, usually,highways are built to be easy to drive on. Nevertheless, in cities, the opposite is expected as traffic jams are widespread.As a global challenge, all applications and services will suffer if this issue is not addressed.
Other specific problems can arise in the big data era in emerging vehicular environments. For example, to mitigate problems related to data and computationally hungry applications and services, computing paradigms could adopt an offloading layer. The offloading idea relies on the transfer of storage or computation to capable network elements, in a particular moment, which can fulfill more efficiently such duties, either because they were previously in the idle state compared to other elements or are merely more powerful to do so [80]. This, however, does not mean that total mitigation of the problem is achieved because there is still a lack of ubiquitous networks and powerful enough nodes. Please note that more information can be found in [81]-[83].
B. Challenges
As previously mentioned, the dynamism of the network topology is the first big challenge. Protocols that provide security while considering the unstable network structure must be specially tailored for vehicular environments [84], [85].This is valid for both IoV and VANET. The latter networks still lack a set of standards for their various layers.
Nowadays’ adoption of 5G and WAVE only solves part of the whole set of features for vehicular environments. The socalled best practices for the development of services and applications also do not exist yet. The primary impulse to solve them will come when these networks start to be widely used in everyday life worldwide, particularly IoV.
Recent works aim to use big data, AI, blockchain, and software defined networks (SDN) to address some challenges of vehicular networks. For instance, big data’s use can be as valuable as saving more lives by anticipating congestions and accidents, a challenge for ITS and VANET [86]. Zhou et al.[87] address content distribution challenges with a heuristicscheme using big data and coalition game behavior for VANETs.

TABLE II VANET CHARACTERISTICS AND POSSIBLE SECURITY ISSUES
AI can be used for a variety of reasons in vehicular environments ranging from network to driver benefits [88].For example, if we are using big data services, it is necessary to distribute the computing the network can perform with data reliably. Ning et al. [89] try to solve the latter using deep reinforcement learning together with 5G to offload big data traffic.
On the top layer of IoV, multimedia services and applications usually need QoS, a way to quantify how nearer to an ideal or expected scenario the network delivers these services. Sodhro et al. [90] use AI to provide optimization in QoS for IoV communications. Sodhro et al. [91] propose a self-adaptative, reliable, intelligent, and mobility-aware intravehicular mobility management algorithm for vehicular fog networks to avoid interference so that the network provides seamless connection. Moreover, Tang et al. [92] discuss the possible applications and challenges future vehicular networks will have using 6G and artificial intelligence.
Regarding blockchain, the authors in [93] and [94] focus on vehicular environments’ challenges related to strong,traceable, and reliable data sharing, and dissemination, and scalable secure protocols. Also, authentication schemes that guarantee network participants’ security is a fundamental challenging aspect [95].
Zhuang et al. [96] discuss SDN’s ability to address the challenges IoV services have, namely offloading tasks, mobility-aware computation, caching deployment and dissemination, and more.
In the next section, we will talk about security issues. They are, to some extent, linked to the limitations and challenges presented here, and hence fundamental to tackle.
VI. SECURITY ISSUES
With the possibility of using different types of services and the ability to exchange information with different entities that integrate the vehicular networks, the need to improve security solutions is mandatory for the proper functioning of the network. The increase of such services means more data exchange that, ultimately, is correlated to each of the participants, and therefore, considered sensitive.
Wang et al. [97], [98] address privacy issues for messages exchanged in the network in a specific case, i.e., vehicular social networks (VSN - a new paradigm centered in the social properties of vehicular networks to improve their performance), and a much broader sense. Magaia et al. [99], [100]proposed privacy-preserving routing protocols to conceal routing metrics necessary in such networks.
Despite all VSN characteristics, data dissemination, attacks,and the possible mitigations, when talking about privacy, the following issues exist:
1) Location and Trace Privacy: There are roughly two layers of location-based services: the first one is for safety applications, thus thought of as a service provided by the control channel. It will be developed in secure protocols.However, the second one is more general-purpose, i.e., when a driver wants to know where the nearest place with a gas station is. Here, the location providers cannot provide adequate protocols to maintain driver’s privacy, as it is an open question if they will share it or not with third parties,similarly to what happens on the internet.
2) Personal and Common Interest Privacy: Despite the roads being a common path in which people of different interests go along to reach several different places, while traveling, they tend to share interests in order to maintain a safe state. These interests can be categorized in such a way,that for a vehicular network, they can help to shape traffic.However, there is also the common interest of privacy which should be considered by vehicular network protocols.
3) Community Privacy: This more general privacy requirement prevents a malicious user from tracing other user’s personal information based on what virtual communities they are in. As an example, a wealthy community user can be exposed and targeted if the VSN is not able to keep private the places that the user goes.
For both VSN, social IoV, and big data content exchange(i.e., a novel concept briefly discussed in the previous section), security issues are still open.
There are general and specific security requirements to a particular technology, application, or service. The three fundamental security requirements are confidentiality,integrity, and availability (CIA) [101], [102]. Furthermore,there are authentication, non-repudiation, privacy and anonymity, traceability and revocability, data verification, and access control, which are relevant in the context of VANETs[103], for example.
For specific security issues, we know that security is also something directly related to the design of what is being analyzed; hence it is common to list characteristics and possible associated security problems.
Tables II-V gather characteristics and possible security issues surveyed from the most recent literature of VANETs[103], IoVs [104], cloud [105]-[108], and fog computing[109]-[113].

TABLE III IOV CHARACTERISTICS AND POSSIBLE SECURITY ISSUES

TABLE IV VCC CHARACTERISTICS AND POSSIBLE SECURITY ISSUES

TABLE V VFC CHARACTERISTICS AND POSSIBLE SECURITY ISSUES
Please note that instead of listing VCC and VFC issues, we could have mentioned cloud and fog computing issues, as they share similar problems, differing only in the cyber-physical elements that compose them.
For example, in a traditional cloud, there is a set of geographically distributed computers offering services, and in the case of the VCC, this set is formed by vehicles.
For both VANET and IoV, plenty of communication attacks can happen not only because these networks are still in development but their actual implementation, commercially speaking, are not guaranteed to bring the security countermeasures that are researched/proposed [114]-[116].
Like any network, VANET and IoV could suffer from signal jamming, man-in-the-middle attacks, eavesdropping,spoofing, flooding, spamming, DoS, and DDoS attacks. One can even try to tamper OBUs or access the vehicle internals through the network interface there could be a link to the underlying OS [117].
These problems escalate when in an IoV network, as vehicle sensors and engines, user peripherals, and devices are supposed to act together to deliver a pleasant and unified experience for vehicle users or owners. Each of these devices brings their issues, and their expected “organic” communication opens the door to how much an attacker can go hopping from point to point inside the IoV structure.
For VFC and VCC, the same myriad of problems as above happens, but also each vehicle, and each infrastructure element, as a node, can behave in such a way that it is designated rogue node because it either exhaustively uses VFC or VCC computing power to some malicious intent, or can tamper with and scavenge data passing through.Ultimately, attackers will modify their vehicle to use it as a malicious weapon as much they now create as fake access points in coffee shops.
Table VI presents common attacks and possible solutions in vehicular networks.
It is out of this work’s scope to present an exhaustive coverage of the security problems and solutions in vehicular environments since they are already available in the literature[118].
It is also vital to highlight tradeoffs as using a technology or paradigm implies being susceptible to all the risks of its logical and implementation failures. However, it also allows using those very technologies or paradigms to mitigate other problems.
The following examples present the use of VANETs, IoV,VCC, and VFC and their security benefits. Bousselham et al.[119], and Erskine and Elleithy [120] suggest methods in how to use fog computing to enhance VCC and VANETs security,respectively. In Hussain and Oh [121], cooperation-as-aservice and VANET Clouds are used for security in the VANETs themselves. Additionally, in Hussain et al. [122],5G is used with VANETS to increase network security following a top-down approach. Xue et al. [123] present anarchitecture incrementing privacy and data-sharing in VCCs using a fog-to-cloud scheme.
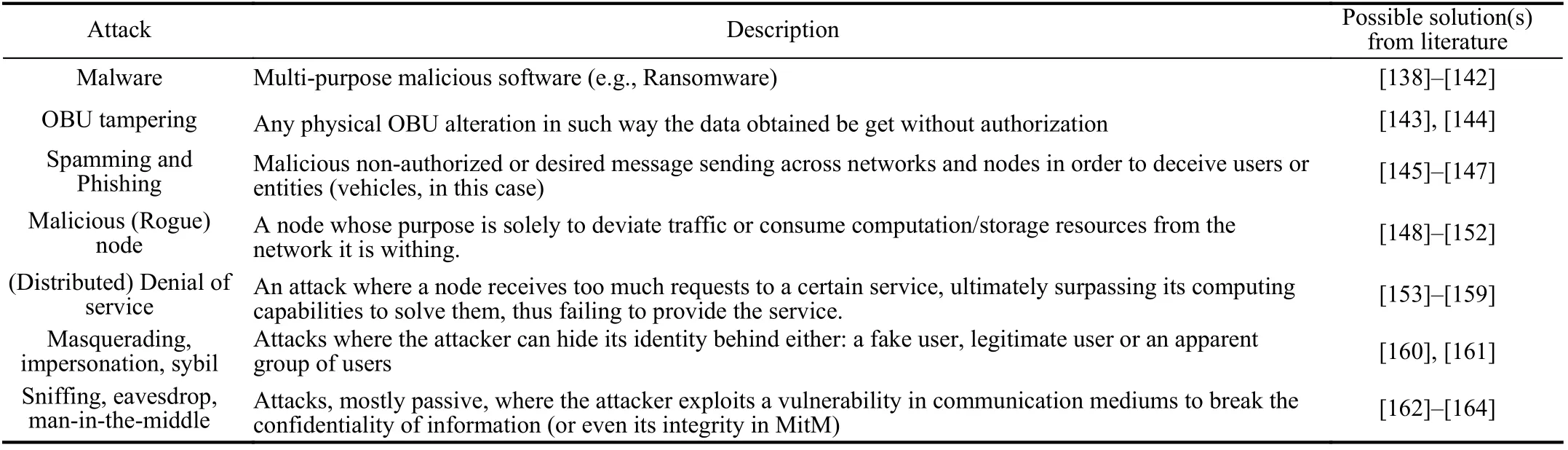
TABLE VI COMMON ATTACKS AND POSSIBLE SOLUTION(S) IN VEHICULAR NETWORKS
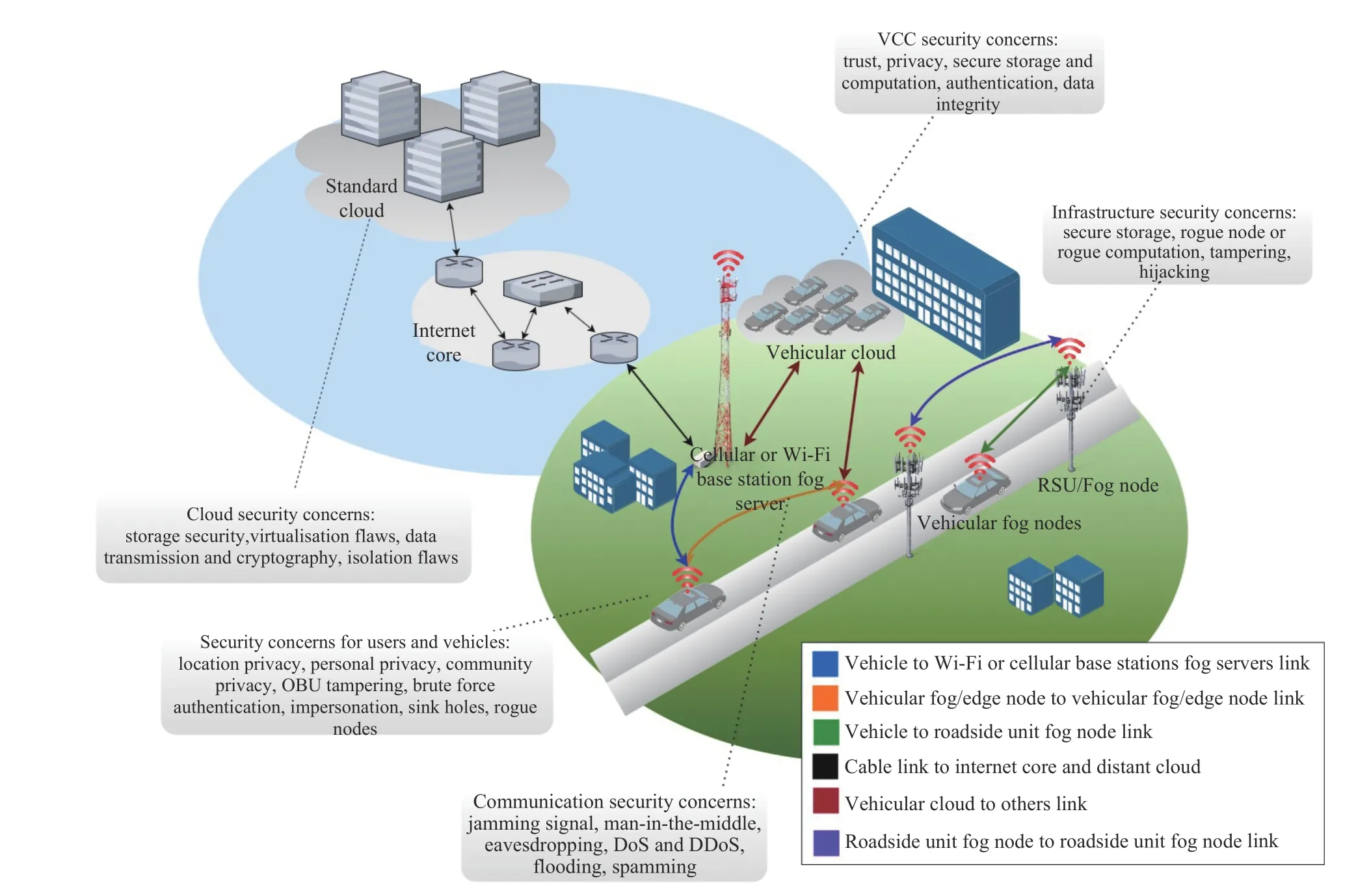
Fig.4. Security concerns in vehicular environment architectures.
Fig.4 presents security concerns in vehicular environment architectures.
VII. FUTURE DIRECTIONS
The implementation of computing paradigms in vehicular environments such as VCC and VFC (or VEC) is still in development, in contrast to cloud computing, whose concept dates back to the 1960s [124], [125]. In the last ten years, we have seen computers being used as a source of services with the “illusion” of an infinite amount of resources; meanwhile,fog computing is quite a recent concept [61].
Currently, vehicular networks, in particular, IoVs, are not popular. Even the commercialization of 5G networks is no widespread and they are expected to be implemented in 2020[4]. Although there are already VANET, which realize some ITS use cases, they do not exist in the same order of magnitude as IoT or the adoption of smartphones, where there are already around 20.8 billion devices [126].
In computing, it is common for there to be a stage of development of the physical layer. The following layers and logical abstractions come to make the infrastructure available in an almost transparent way so that even people who know little or nothing about that infrastructure can create services and applications. This departure from the structural layer to the highest level often allows the construction of what is called the Intelligence of something, which is when“ordinary” people have the opportunity to develop their services, and innovations happen.
Therefore, we present what we believe will help achieve the“ubiquitous” status desired for vehicular networks and networks in general.
Below, we present the following three required elements:
1) Software-Defined Networking (SDN) [127]: SDNs are a way of seeing and, therefore, of structuring the network so that its programmability is enhanced by separating the data and control planes. This flexibility makes, for example, a device with SDN capability capable of functioning as a switch, firewall, or router using, for instance, OpenFlow or P4[128]. SDNs are used for multiple purposes, such as in data centers. Yuan et al. [129] give an example of how data centers and VCC can benefit from SDNs. They considered the inherent latency of virtual machines and formulated the workload-aware multi-application (WARM) method to optimize the distribution of data and tasks to virtual machines through optimal paths for each. The result of load balancing is effectively better with a decrease of the round-trip time (RTT)compared to other know methods. Vehicles’ OBUs will need to have intelligence capabilities, a high transmission rate, and,most probably, SDN functionalities. The latter will enable vehicles, whether participating in the cloud or as fog nodes, to shape the network more flexibly, participating in it more effectively by behaving as components not only of the network edge but also of its core. An architecture can be found in [130].
2) 6th Generation Mobile Networks [131], [132]: Each generation of cellular technology has a forecast of application creation between 10 and 20 years. Although 5G networks are already being deployed worldwide, their maturation is expected by 2025/26 and the complete adoption by the year 2030, which will coincide with the beginning of 6G networks[128]. Such networks are promised to have peak data-rates as high a 1 Tbps and enable user-experience data rates as high as 1 to 10 Gbps. Moreover, they promise latency less than 1 ms,with expected device positioning precision as low as 10 cm indoors and 1 m outdoors. 6G networks are aimed to be efficient, targeting green cities and computing [131],[133]-[135], with an expected energy efficiency around 100 times higher, spectrum efficiency at least 5 to 10 times higher,and traffic capacity around 1000 times higher than 4G,respectively.
3) Serverless Computing [136]: In this type of computing,which is directed to the cloud (and possibly fog), there is a drastic change in the way services are performed. In the traditional model, known as serverfull, the cloud services are offered in several forms, i.e., IaaS, PaaS, SaaS. However, a user pays for up to a certain amount for resources and cannot surpass it unless he pays more (an upgrade). In the serverless model, functions are executed once at a time from an eventdriven perspective. There are three primary characteristics: i)decoupled computation and storage, and both will possibly be placed in different parts of the cloud or clouds in order to climb in different ways. Therefore, each is charged and priced according to use, and the computing will then be stateless(which will increase virtualization and isolation); ii) code without resource allocation, where not only are computation and storage separated, but also the user does not need to define how many resources should be allocated. The cloud will automatically take care of this for each time a function that is triggered; iii) proportional payment by use, not allocation, where the user delivers his code, and the cloud executes it by automatically configuring everything necessary without the user having to specify any information. Then,there is the amount to pay for the time the code needs to run.In short, serverless computing will enable content, service or application producers to offer their ideas in such a way to form a new economy around cloud computing, and consequently VCC, and also will give cloud providers much more flexibility to charge for cloud services.
We envision a future in which billions of devices will form an internet-of-everything (IoE) even before 2050. IoE will include vehicles, smartphones, home appliances, smart houses, smart cities, ITS, wearables (internal and external),among others. We also foresee the realization of energy savings through green computing and network processes[131], [133] applied to smart cities [135] and the cloud [137],in order to adapt computing to the immense amount of data that will be on the go continuously feeding real-time systems,and high-quality and faithful video and audio streams.
For the next decade, we realize that in due course, 6G and IoV will possibly have commercial applications. It will also be the time when serverless computing will come into operation.It is therefore crucial that researches start uniting VCC, VFC,serverless computing, SDNs, and, possibly, 6G as soon as the enabling technologies become commercially viable, thus decreasing latency to the order of pico-seconds meanwhile increasing transmission rates to the order of Terabits per second [132]. It is essential that the serverless computing is applied to vehicular networks due to the need for an abstraction between physical elements and their components,which will allow users to create their services. In addition,pricing, whether for users “lending” their vehicles or using others, will be more appropriate, based on time of use and not by the package, something that would be necessarily inappropriate in a dynamic network such as one that is vehicular.
The union of these technologies and paradigms seems to us as the natural way to overcome these obstacles, and in the coming years, should solve the difficulties of integrating vehicular networks and make them more user-friendly for programmers who want to develop applications and services.Specifically, it is our prediction that they will mitigate challenges, i.e., 6G will enable complete ubiquitous network across heterogeneous devices (vehicles, sensors, IoT,unmannered aerial vehicles - UAVs, wearables, among others) at high speeds and very low latency; serverless computing will provide sufficient decoupling from the cloud infrastructure so that services can be charged on a different and easier basis; finally, SDN-enabled network elements will easy to combine and will complement various computing paradigms in vehicular networks.
VIII. CONCLUSIONS
We presented a unifying perspective of technologies,architectures, and nomenclatures concerning computing paradigms in vehicular environments. We believe that the future of vehicular communications will benefit from 5G networks for the next decade, and from 6G after that, in addition to Wi-Fi technology. IoVs are considered an evolution of VANET, without disregarding the latter technology’s instrumental role from a safety point of view and the former technology’s role in providing various services even outside the scope of vehicular environments, in addition to massive amounts of data analytics in the long run. Even if IoVs are still under research and not being seen recurrently in cities, their deployment will happen soon. Future safer driving is imperative, and every technological advance is expected to bring more quality of life to people, in addition to saving lives.
杂志排行
IEEE/CAA Journal of Automatica Sinica的其它文章
- Deep Learning in Sheet Metal Bending With a Novel Theory-Guided Deep Neural Network
- Nonsingular Terminal Sliding Mode Control With Ultra-Local Model and Single Input Interval Type-2 Fuzzy Logic Control for Pitch Control of Wind Turbines
- Deep Learning for EMG-based Human-Machine Interaction: A Review
- Distributed Secondary Control of AC Microgrids With External Disturbances and Directed Communication Topologies: A Full-Order Sliding-Mode Approach
- Adaptive Backstepping Control Design for Semi-Active Suspension of Half-Vehicle With Magnetorheological Damper
- Autonomous Control Strategy of a Swarm System Under Attack Based on Projected View and Light Transmittance
