Event-triggered finite-time command-filtered tracking control for nonlinear time-delay cyber physical systems against cyber attacks∗
2024-03-01YajingMAYuanWANGZhanjieLIXiangpengXIE
Yajing MA,Yuan WANG,Zhanjie LI‡,Xiangpeng XIE,
1School of Internet of Things, Nanjing University of Posts and Telecommunications, Nanjing 210003, China
2Institute of Advanced Technology for Carbon Neutrality, Nanjing University of Posts and Telecommunications,Nanjing 210023, China
Abstract: This article addresses the secure finite-time tracking problem via event-triggered command-filtered control for nonlinear time-delay cyber physical systems(CPSs)subject to cyber attacks.Under the attack circumstance,the output and state information of CPSs is unavailable for the feedback design,and the classical coordinate conversion of the iterative process is incompetent in relation to the tracking task.To solve this,a new coordinate conversion is proposed by considering the attack gains and the reference signal simultaneously.By employing the transformed variables,a modified fractional-order command-filtered signal is incorporated to overcome the complexity explosion issue,and the Nussbaum function is used to tackle the varying attack gains.By systematically constructing the Lyapunov–Krasovskii functional,an adaptive event-triggered mechanism is presented in detail,with which the communication resources are greatly saved,and the finite-time tracking of CPSs under cyber attacks is guaranteed.Finally,an example demonstrates the effectiveness.
Key words: Cyber physical systems;Finite-time tracking;Event-triggered;Command-filtered control;Attacks
1 Introduction
In recent years,physical systems have been tightly integrated with cyber components via network communication channels.These systems are denominated as cyber physical systems (CPSs)(Wang YN et al.,2016;Ge XH et al.,2023a).While considering the fact that CPSs are vulnerable to cyber attacks,the security problem is recognized to be one of the main concerns (Ding et al.,2021;Wang R et al.,2021;Xie et al.,2023).Among the various attacks,deception attacks are characterized by the injection of false data into sensors or actuators to change the authenticity of transmitted signals and system data,which will seriously threaten the security of CPSs(Guan and Ge,2018;Xiao et al.,2022).To deal with the deception attacks,a novel detection strategy was presented in Ge XH et al.(2019)for a discrete system subject to data deception attacks on sensor communication links and the system dynamics.In Chen WD et al.(2022),a coordinate conversion was proposed to achieve the tracking task of CPSs with deception attacks by considering the attack gain.
It is known that in the network environment,the continuous transmission of data results in the generation of a lot of redundant data,thereby causing the imposition of unnecessary load upon network communication (Samy et al.,2023;Yang SH et al.,2023;Zhang et al.,2023).Thus,the eventtriggered mechanism has been established to reduce the communication rate,and many important results have been received (Ju et al.,2022;Liu et al.,2022;Yang D et al.,2022;Ge XH et al.,2023b;Hu et al.,2023).For example,Xu and Guo (2022) proposed an event-triggered scheme to handle the multiple network attacks and obtained the length rate and the upper bound of attack frequency.With the use of a sampled-data model,Zhang et al.(2020)introduced a logic processor to receive sampled data and designed resilient controllers for systems under denialof-service attacks.Based on the dead zone operator,Wang YC et al.(2022) designed an event-triggered adaptive controller to ensure boundedness of the tracking error in the mean square in the sense of attacks.It needs to be noted that while,on one hand,the above mentioned results focus on the asymptotic performance corresponding to time approaching infinity,on the other hand,it is always a key objective in practice to reach the steady performance within a limited period of time under the given operating conditions (Wei et al.,2021;Chen WB et al.,2022;Ning et al.,2023).Through a command-filtered inversion technique,faster and more accurate control was obtained in Song et al.(2022b).In Kazemi et al.(2022),a finite-time state estimator was introduced for CPSs with unknown inputs and sensor attacks to estimate the state of the CPS in a predefined finite time.One approach for achieving finite-time performance that needs to be particularly emphasized is the deployment of the coordinate conversion technique,which was introduced in Kazemi et al.(2022)and Song et al.(2022b) for continuing the iterative control.However,since the system output and state data are corroded by attackers,and only the compromised data are available for feedback design,the classical coordinate conversion cannot be directly applied to the controlled systems.Ascertainment of the means to address the mismatching output signal is difficult when solving the finite-time tracking issue of CPSs under the attacks.
On the other hand,the foregoing important results involve repeated differentiation of virtual control,which results in a complexity explosion issue(Li ZJ and Zhao,2021).The use of the dynamic surface method and command-filtered technology can help avoid this problem(Choi and Yoo,2020).Considering the influences of time delays,Li M et al.(2022)used the Lyapunov–Krasovskii (LK) functional to incorporate time delays and designed an adaptive event-triggered controller based on a command filter.In Wang X et al.(2023),an event-based dynamic surface control method was adopted to deal with the influence of deception attacks and time delays.Compared with the common integer-order (IO) filter used in the abovementioned research,fractionalorder(FO)control is characterized by the unique advantage of historical memory,and can thus provide another option for the improvement of the system performance.Song et al.(2022a)incorporated coordinate conversion and an improved fractional-order command filtering (FOCF) technique to deal with deception attacks,and overcame the computational complexity difficulty.It is stressed that although many FO design methods characterized by a combination of FO properties and IO techniques have been reported in the literature,to our knowledge,studies reporting results pertaining to the finite-time command-filtered tracking issue for nonlinear timedelay CPSs via event-triggered mechanism with cyber attacks are rare.
With the above mentioned rationale serving as a motivation,the present research aims to solve the event-triggered finite-time tracking problem for the nonlinear time-delay CPSs against unknown cyber attacks.By proposing a new coordinate conversion technique,and combining fractional calculus with the command-filtered methods,all signals of the closed-loop system are bounded and the output of CPSs tracks the desired reference signal in a finite time.
1.The systematical design procedure,encompassing the introduction of the FO command filter,the construction of the LK functional,the utilization of the Nussbaum function,and the design of the adaptive event-triggered mechanism,is presented in detail.Based on the above mentioned strategies,the finite-time tracking of CPSs under cyber attacks is guaranteed with limited network communication resources.
2.A new coordinate conversion is proposed to cope with the coupling effects between the reference signal and the cyber attacks.By embodying the reference signal and the compromised variables simultaneously,the transformed state is used as the available data for the tracking design.Compared with the approaches adopted in Chen WD et al.(2022) and Song et al.(2022b),the new coordinate transformation method is suitable for more general time-delay CPSs with non-strict feedback structures.
3.An improved FO command filter is proposed using FO calculus.It realizes the finite-time tracking of time-delay CPSs,overcomes the complexity explosion problem,and improves the filtering performance.
2 Problem description and preliminaries
2.1 Problem description
Consider a nonlinear time-delay CPS given by
wherei=2,3,...,n,λ1(t) is the first attack ofx1,λi(t)is the attack ofxi,andis the available system state after attack.
Assumption 1The deception attacks are expressed asλ1(t)=ϖ1(t)x1(t),λi(t)=ϖ(t)xi(t),where the weightϖ1(t) is known,ϖ(t) is unknown,and 1+ϖ1(t)≠0,1+ϖ(t)≠0.We suppose that the unknown positive constantsandare the upper bounds of|ϖ(t)|and|(t)|,respectively.
Remark 1Assumption 1 is a standard and common requirement used in the existing results;see,for example,Kazemi et al.(2022) and Song et al.(2022b).According to (2),we can obtain=(1 +ϖ1)x1and=(1 +ϖ)xi.If 1 +ϖ1=0 and 1+ϖ=0,the available compromised states will vanish.In this particular case,there are no available signals that can be used for the control design to guarantee the security of CPSs.Furthermore,to ensure the tracking task against the attacked output,it is necessary to suppose that the attack weight of the first step differs from that in other steps.
The objective of the research is to ensure eventtriggered finite-time tracking control of system (1)under attacks(2).
2.2 Preliminaries
The functionFi(Δi) is a continuous one within a compact setΩΔ.Then,it can be approximated by neural networks(NNs)satisfying
withlbeing the neuron number,andbilandσilthe corresponding width and center respectively.
Assumption 2Ξiandoisatisfy the relationship‖Ξi‖ ≤iand|oi|≤withandbeing the unknown constants.
Lemma1 (Li ZJ and Zhao,2021) For an NN withΔ=(x1,x2,...,xn)TandΠ(Δ)=being its input vector and basis function vector respectively,the following inequality holds:
whereΔp=(x1,x2,...,xp)with 1≤p ≤n.
Definition 1(Song et al.,2022a) Let us define a function,0<α<1.For a functionf(t),the fractional derivative of orderαwith Caputo’s definition is given by
Definition 2(Kazemi et al.,2022) A continuous even function is called a Nussbaum-type function if
Lemma 2(Chen WD et al.,2022) We consider a smooth Nussbaum-type functionN(ξ),and the smooth functionsV(t)andξ(·)defined on[0,ts)andV(t)≥0,∀t ∈[0,ts).If
holds∀t ∈[0,ts),with two constantsm1>0,m2>0,and(·) being a time-varying parameter taking values in a non-trivial closed intervalI=[l-,l+],thenξ(t),V(t),and,t ∈[0,ts) are bounded.
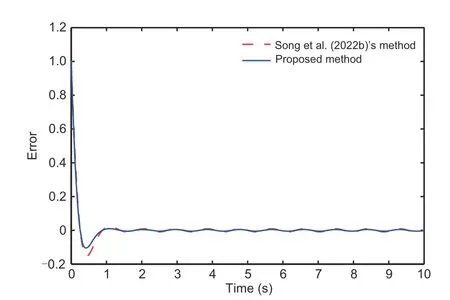
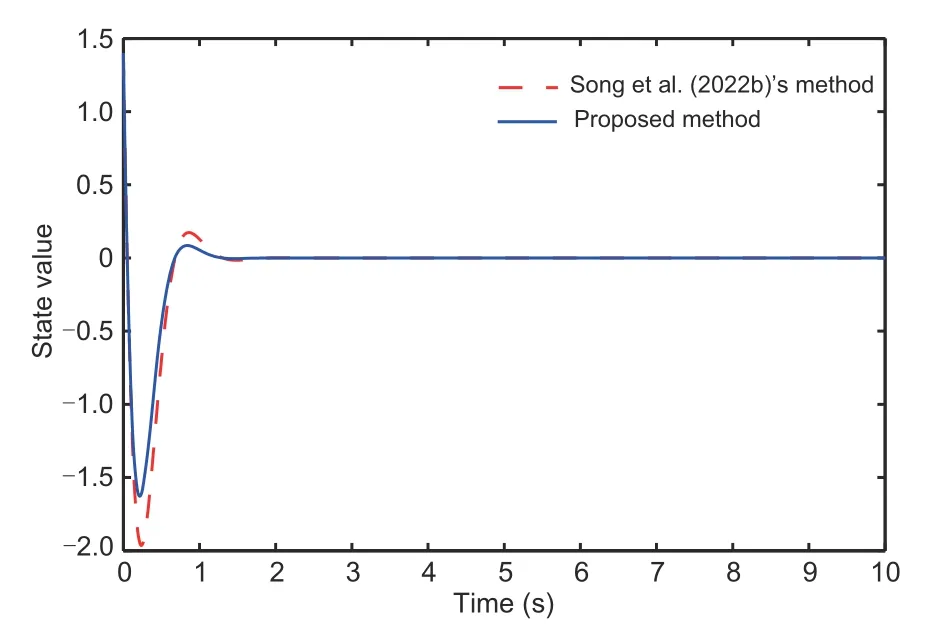
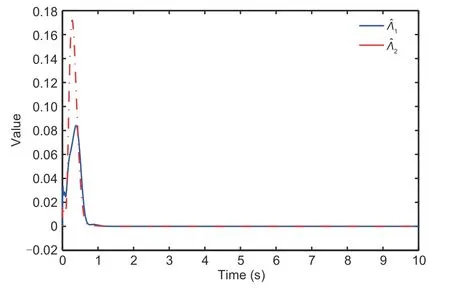
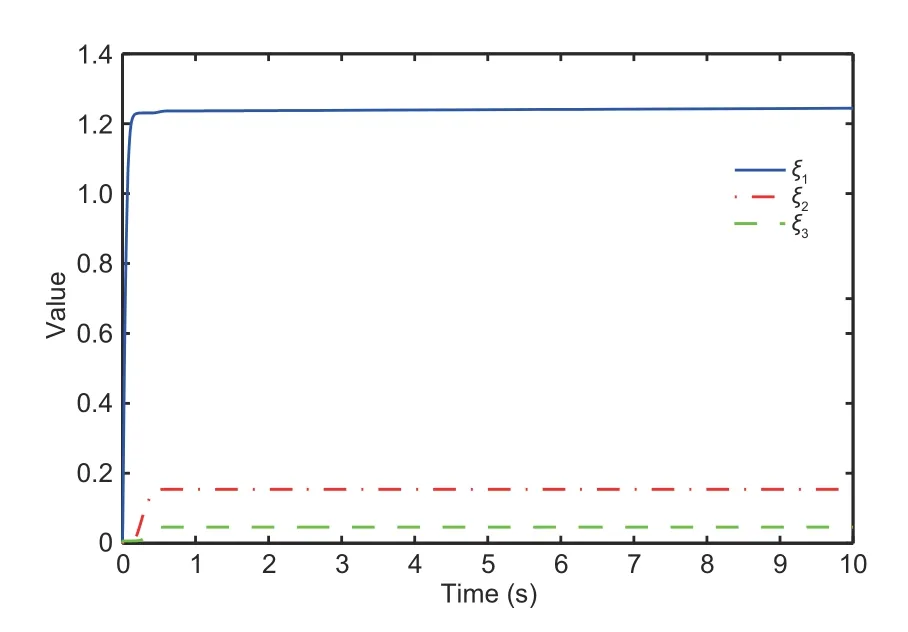
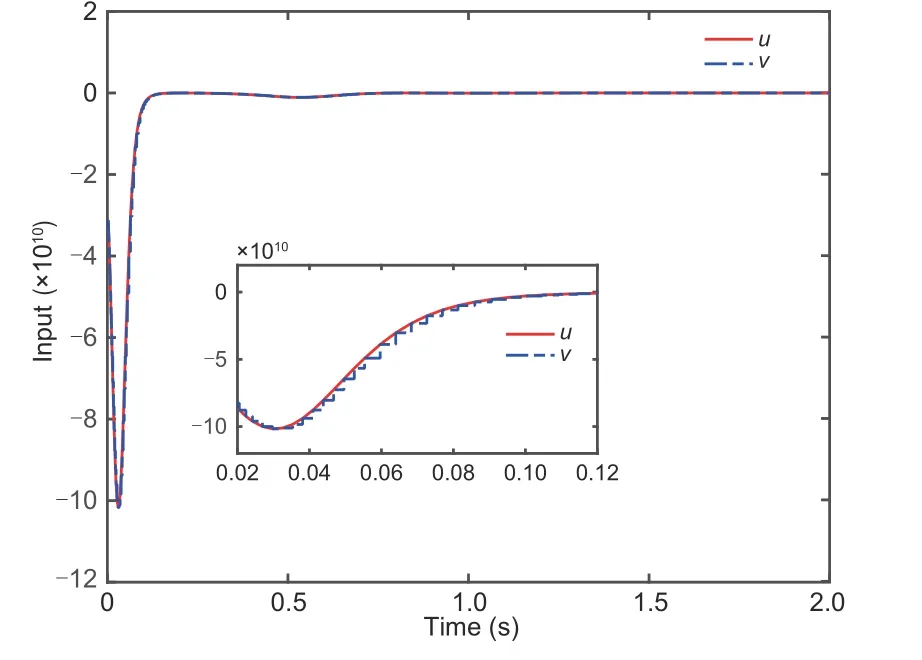
Lemma 3(Ge SS and Tee,2007) For any real numbersμ1,μ2>0,0 Lemma 4(Li M et al.,2022) Letπ1∈Rn,π2∈Rm,andg:Rn×RmR be a continuous function.There are smooth scalar functionsC(π1)≥0 andD(π2)≥0 such that By using Lemma 4,for the termsgj(j,τ(t)),one can deduce wherexs,τs(t)=xs(t-τs(t)) andΘj,s(·) are continuous functions. Lemma 5(Song et al.,2022b) Forz ∈R and a positive constantϖ,it holds that Lemma 6(Song et al.,2022a) For any real variabless1ands2and any positive numbersς1,ς2,andϱ,it holds that From the attacks(2),one has whereγ1=(1 +ϖ1)-1,γ=(1 +ϖ)-1.From Assumption 1,one obtains thatγis bounded byγm≤|γ|≤γM,whereγmandγMare some positive constants.We propose the following new coordinate conversion to construct a controller under deception attacks: whereydis the reference signal,θi-1(i=2,3,...,n)are filtered signals of the virtual control law ħi-1(i=2,3,...,n),and ħi-1will be designed below. Remark 2In traditional tracking control,the output signal is not attacked,and thus the output signal and the tracking signal are matched.In CPSs under deception attacks,the matched condition is no longer available for the attacked output signal.To realize the tracking control for the attacked system,it is assumed that,unlike the case with other steps,the attack signal for the first step is known.We propose a new coordinate conversion,including the reference signal and the attack signal simultaneously,to ensure the tracking task for the CPSs under attacks. From(15),one can deduce where the filtered signalθi-1is calculated with the FO filter: where 0<β1<1,β2>1,0<β3<1,α1,i-1>0,α2,i-1>0,α3,i-1>0 are some constants,andDαdefined in (6) is the fractional operator.The orderαtakes its value in (0,1).The input of the filter is virtual control law ħi-1,and the outputs areθi-1=λ1,i-1andDαθi-1=Γ1,i-1. Remark 3Compared with IO control,the unique aspect of FO control is its historical memory behavior,which enables the system to obtain better precision and a greater degree of design freedom.FOCF is used to obtain the filtered signal of the virtual control law.This method can improve the filtering performance by reducing the filtering error,and also can overcome the computational pressure brought by the traditional iterative method. We define the filter error∊i=θi-ħi.Then,the signals that compensate for the filtering errors would be as follows: Step 1: According to system (1),coordinate transformations (15),and the definition of the filter error∊i=θi-ħi,one can deduce the time derivative ofz1as The Lyapunov function is chosen as follows: Let us denote for simplicity.Following the definition ofW1provided above,one can obtain the derivative ofW1as By adding and subtracting the two terms tanh2(z1/l1)φ1/z1and,it follows from Lemma 6 and(19)that Since the termF1(X,γ1) is unknown,the NNs are used to approximate this uncertain term,and the following equality can be obtained: whereΔ1=(X,γ1),ando1is the approximation error.It is noted thatΔ1is the attacked state and cannot be used for the feedback design.To continue the design process,Δ1is replaced by the system state=(,γ1),and(23)is rewritten as Recalling Assumptions 1 and 2,one can infer that|Ψ1|≤with>0 being a constant.Therefore,it holds that wherec1is a positive constant.Besides,it follows from Lemmas 1,5,and 6 that The adaptive laws and virtual controller are given by Similarly,one can obtain Substituting (30)–(32)into(29),one can deduce Stepi(i=2,3,...,n-1): From (1) and (15),and the definition of the filter error∊i=θi-ħi,one calculates The Lyapunov function is chosen as follows: Similar to (22),one deduces Using (11),one can derive Invoking(37)–(39)yields The adaptive laws and virtual controller are given by Substituting(18),(41),and(42)into(40)yields Stepn: According to(1)and(15),one calculates The triggering event condition is described as wheree(t)=v(t)-u(t),and,mare designed parameters satisfying 0<ϕ1k<1,m>0. With the help of (46),one has|v(t)-u(t)|≤|u(t)|+m,∀t>t0.Ifu(t)≥0,it follows that By (47),it is known that for some time-varying parameterϕ(t),|ϕ(t)|≤1,one has Ifu(t)<0,in a similar way one has Considering(48)and(49),one can derive whereϕ1=ϕ2=ϕifu(t)>0,and otherwiseϕ1=ϕ,ϕ2=-ϕ. From(45)and(50),it is calculated that The Lyapunov function is chosen as Using (11),one can derive Invoking(53)–(55)yields The adaptive laws and virtual controller are given by Substituting (18)and(57)–(59)into (56)yields The adaptive laws and virtual controller are given by By selecting the design parameters,(62)can be expressed as Now,we can summarize the main result. Theorem 1Consider the nonlinear time-delay CPS(1)with deception attacks(2).The control law(61),including the event-triggered mechanism (46),the FO filter (17),and the adaptive laws (28),(42),and(59)can guarantee that: (1) All signals of the closed-loop systems are practically finite-time stable. (2) The tracking error converges to a small neighborhood of the origin within timeTfas With the help of Lemma 3 in Ge SS and Tee(2007),it follows from(63)and (65)that The inequality above implies that all signals of the closed-loop system are practically finite-time stable. On the other hand,by using (67),it can be deduced that whereasatisfies 0 Considering the definition ofVn,it is deduced that with the finite timeTf.Therefore,the tracking error eventually tends to a small region of the origin in a finite timeTf. Remark 4In Song et al.(2022b),FO command filtering was introduced to achieve finite-time boundedness of closed-loop signals.In our context,by considering both the reference signal and the attack gains,the finite-time tracking task is guaranteed.Compared with the tracking result(Chen WD et al.,2022),the coordinate transformation is embedded into fractional-order command filtering to obtain the virtual control law and overcome the complexity explosion issue.Apart from this point,unlike the approach adopted in Chen WD et al.(2022) and Song et al.(2022b),the proposed method is suitable for more general CPSs with time-delay and non-strict feedback structures. This section demonstrates the effectiveness of the designed method for the chemical reactor system(Song et al.,2022b).By considering time delays,the model dynamics are given as where the values of the parametersιi(i=1,2,3,4,5)can be taken from Song et al.(2022b). The event-triggered command-filtered tracking control scheme can be obtained using the design process elucidated in Section 3.In the example,a comparison is proposed with the result achieved in Song et al.(2022b)without considering the tracking task.We choose the attacksλi=(-0.3-0.25 sint)xi,i=1,2,3,and the tracking referenceyd=0.1 sin(2πt).k1=5,k2=3.5,c1=0.005,c2=0.01,ρi,j=2,i=1,2,j=1,2,α1,1=α1,2=2,α=0.9,x1(0)=1,x2(0)=1.4,and the other initial values are zero. Figs.1–6 show the example results.Fig.1 shows the tracking error under the proposed method and Song et al.(2022b)’s method.In Song et al.(2022b),the classical coordinate conversion was constructed without considering tracking control.Fig.1 shows that the proposed method guarantees a good finitetime tracking behavior with a smaller tracking error than that in Song et al.(2022b).Fig.2 indicates the system states bounded in a finite time.Figs.3 and 4 show the adaptive laws that offset the influences of the uncertain functions and attack signals.Fig.5 depicts the evolution of the parameter variables in Nussbaum-type functions,which are used to handle the time-delay attack weight.It is clear that these variables are all bounded.Fig.6 presents the control input efforts,and the proposed method can greatly save communication resources. Fig.1 Tracking error Fig.2 System state x2 Fig.3 Adaptive laws and Fig.4 Adaptive laws and Fig.5 Parameter variables ξ1, ξ2,and ξ3 Fig.6 Inputs u and v This article has addressed the problem of finitetime tracking control for the event-triggered nonlinear time-delayed CPSs with deception attacks.A new coordinate conversion technique is proposed to deal with the influence of attack gain.The modified FOCF backstepping recursive process and the Nussbaum gain function are introduced to address the complexity explosion issue and deal with the time-varying weight.In future research,the proposed scheme can be extended to a class of CPSs with mismatched disturbance and a stochastic phenomenon. Contributors Yajing MA and Zhanjie LI designed the research.Yajing MA and Yuan WANG processed the data.Yajing MA and Zhanjie LI drafted the paper.Yuan WANG helped organize the paper.Zhanjie LI and Xiangpeng XIE revised and finalized the paper. Compliance with ethics guidelines Yajing MA,Yuan WANG,Zhanjie LI,and Xiangpeng XIE declare that they have no conflict of interest. Data availability The data that support the findings of this study are available from the corresponding author upon reasonable request.3 Main results
4 Simulations

5 Conclusions
杂志排行
Frontiers of Information Technology & Electronic Engineering的其它文章
- Towards resilient average consensus in multi-agent systems:a detection and compensation approach∗&#
- Modified dynamic event-triggered scaled formation control for multi-agent systems via a sparrow search algorithm based co-design algorithm∗
- Event-triggered distributed optimization for model-free multi-agent systems∗#
- Outlier-resistant distributed fusion filtering for nonlinear discrete-time singular systems under a dynamic event-triggered scheme∗
- Recursive filtering of multi-rate cyber-physical systems with unknown inputs under adaptive event-triggered mechanisms∗#
- Estimation of Hammerstein nonlinear systems with noises using filtering and recursive approaches for industrial control*
