A Novel Dynamic Watermarking-Based EKF Detection Method for FDIAs in Smart Grid
2022-07-18XueLiZiyiWangChangdaZhangDajunDuandMinruiFei
Xue Li, Ziyi Wang, Changda Zhang, Dajun Du, and Minrui Fei
Dear editor,
The existing bad data detection (BDD) cannot effectively detect false data injection attacks (FDIAs) in smart grid. The objectiveness of this letter is to investigate a novel dynamic watermarking (DW)-based extendedKalmanfilter (EKF)detectionmethodto detect FDIAs.Firstly,securityweaknessof traditionalχ2detector is analyzed, and a novel DW-based EKF detection method is proposed for FDIAs. Secondly, the detection effectiveness and security property of the proposed method are analyzed theoretically, where not only the positive correlation between the detection performance and DW signal intensity but also zero impact of FDIAs not being detected on smart grid (SG) are revealed. Finally, the effectiveness of the proposed method is confirmed by experimental results.
Related work:With the rapid development of information and new energy technologies, the traditional power system is gradually migrating to SG [1], [2], where wired/wireless communication networks are employed to support the operation and running of SG [3],[4]. However, these communication networks make SG vulnerable to cyber attacks. For cyber attacks in SG, some issues such as attack detection, recovery after attack, security control and so on have been reported [5]. Specially, attack detection methods of rapidly discovering cyber attacks have attracted wide attention from academic and engineering field.
FDIAs are a kind of typical cyber attacks. A successful FDIAs on supervisory control and data acquisition (SCADA) will bring untrue measuring data, which will make state estimator produce wrong data to the operator, affecting seriously safe running of SG [6]. Therefore,it is of great significance to study the detection of FDIAs. When cyber attack signals obey Gaussian distribution, Kalman filter-based χ2detection method is usually employed for detection [7]. A datadriven learning-based algorithm is also proposed to detect FDIAs in SG [8].
However, the attacker always tries to bypass attack detection and destroys the stability and economy of SG. Recently, dynamic watermarking [9] has been employed to support attack detection and secure control. Therefore, inspired by the idea of DW, this letter will investigate new DW-based attack detection method for FDIAs, but there exist the following challenges: How to design a new DW-based detection method against FDIAs? What are detection effectiveness and security property of the proposed new detection method?
To solve these challenges, this letter proposes a new DW-based EKF detection method for FDIAs in SG. Compared with the existing methods in the literatures, comparative analysis is listed in Table 1. It can be clearly seen that security weakness of traditional χ2-based detector is analyzed while detection performance and security property of the proposed new DW-based EKF detection method are proved.
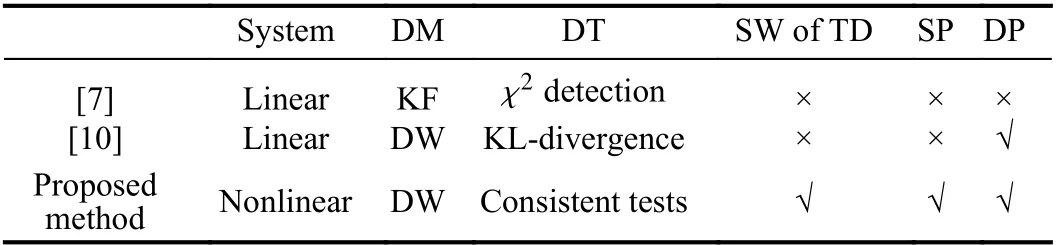
Table 1.Comparative Analysis Between the Proposed Method and Existing Methods
Problem statement:
1) AC model of SG: The dynamic operation of AC power grid can be described approximately by a continuous state-space model,which includes the following state and measurement equations:
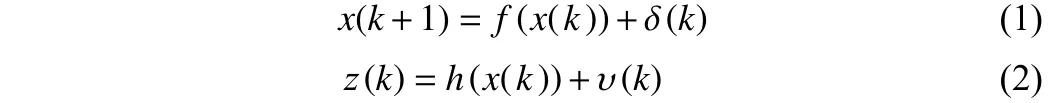
wherex(k)∈Rnare system state including voltage magnitudeVand voltage angleθ,z(k)∈Rmare system measurements including node active injection powerPi, node reactive injection powerQi, branch active power flowPij, branch reactive power flowQij,f(x(k)) andh(x(k))are nonlinear state transfer function and nonlinear measurement function based on Ohm’s and Kirchhoff’s laws,δ(k)∈Rnand υ(k)∈Rmare independent identically distributed(i.i.d.) zero mean white Gaussian with covariance matrices Σδand Συ, respectively.
Remark 1: Since it is difficult to obtain the concrete form off(x(k))[11 ], the popular Holt’s two parameter exponential smoothing method are used to identifyf(x(k)). With Kirchhoff’s voltage law and other circuit theorems,h(x(k)) can be expressed as
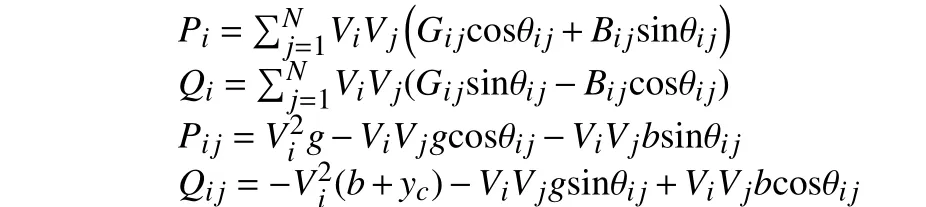
whereiandjare the serial number of nodes, θij=θi−θjrepresents the voltage phase difference,GijandBijrepresent the conductance and susceptance,g,bandycrepresent line conductance, line susceptance and line to ground admittance of the branch, respectively.
2) EKF under FDIAs andχ2detector: Since SG under normal conditions is known as quasi-stationary regime, i.e., the system experiences change smoothly and slowly [12], it can be linearized at about an operating point in the framework of EKF with high accuracy. Thus, using parameter identification and Taylor expansion,(1) and (2) can be linearized as
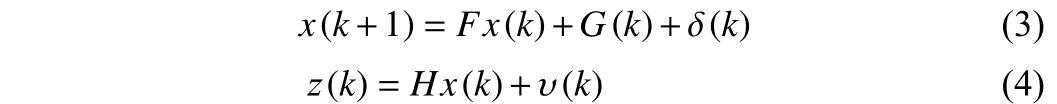
whereFis state transition matrix,G(k) is state vector,H∈Rm×nrepresents Jacobian matrix ofh(x(k)).
Remark 2: The Holt’s two parameter exponential smoothing method can be used to calculateFandG(k) in (3), and it follows that
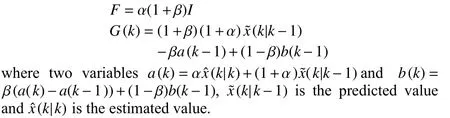
Whenz(k) is attacked by FDIAs, the typical FDIAs commonly adopt scaling, injection, replacement, and so forth [13]. Here, we consider the FDIA with scaling and injection, i.e.,
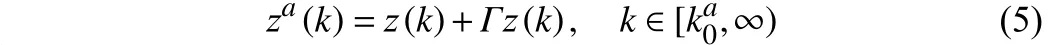

New dynamic watermarking-based EKF detection method for FDIAs in smart grid:To overcome security weakness of the traditional χ2detector, DW is used to protect the measurement fed back to state estimator [10]. Thus, a new DW-based EKF detection method is proposed for SG under FDIAs. Meanwhile, the detection performance and security property of the detector will also be discussed.
1) A new DW-based EKF detection method for FDIAs: The framework of new DW-based EKF detection method for FDIAs in SG is shown in Fig.1. The measurementz(k) is firstly sampled,which is then encrypted by watermarking signalw(k) (i.e., as a key),becoming(k). If(k) is attacked and becomesza(k), it is decrypted withw(k) and saved as(k). Furthermore, using(k),w(k) andk|k−1), attack detector can check whether or not(k) is attacked.
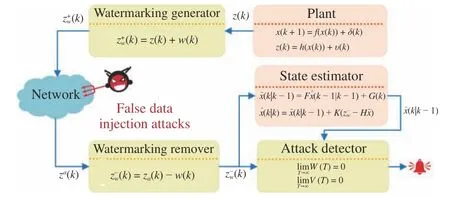
Fig. 1. DW-based EKF detection for FDIAs in smart grid.
For (3) and (4), to guarantee data security,z(k) is encrypted by watermarking, i.e.,
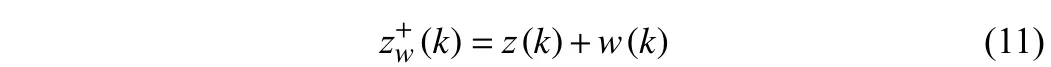
wherew(k) is DW signal (i.e., an i.i.d. Gaussian random variable with zero mean and covariance Σw) , and it is independent ofz(k).

To detect FDIAs, Tests 1 and 2 must be converted to the statistical tests ρ1(k)=|trWk(T)| a nd ρ2(k)=||Vk(T)|| for practical applications, whereWk(T) andVk(T) areW(T) andV(T) within the current time window {k−T+1,k−T+2,...,k}, respectively.Furthermore, let ζ1and ζ2be the preset thresholds and if(k) is attacked, ρ1≥ζ1or ρ2≥ζ2is expected. An online detection procedure is given by the following Algorithm 1.
Remark 3: Note that to prevent measurement noise and disturbance input being regarded as bad data (i.e., causing false alarm), the thresholds ζ1and ζ2should be selected bigger than maximal attackfree tests ρ1and ρ2, respectively.
Algorithm 1Online Detection Algorithm for FDIAs
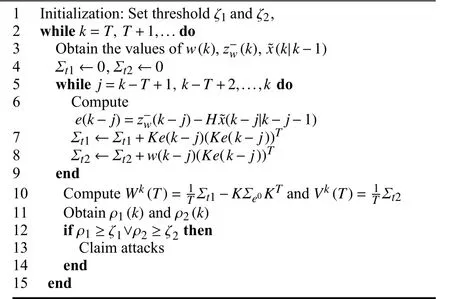
2) Detection effectiveness analysis of new DW-based EKF detection method for FDIAs: The detection performance of the proposed detection method will be presented by the following Theorem 1.
Theorem 1: For the system in (3), (4) and (11)–(15), FDIAs will result in
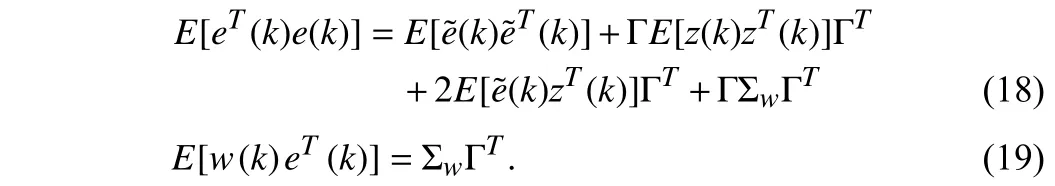
Proof: Due to the existence ofw(k),e(k) can be re-written ase(k)=(1+Γ)z(k)−H(k|k−1)+Γw(k). With the help of the above formula, the covariance ofe(k) can be obtained in (18). Taking the covariance ofe(k) andw(k) and consideringw(k)⊥(k|k−1) andw(k)⊥z(k)leads to (19). ■
Remark 4: When no attack occurs (Γ is zero matrix), the last three terms of (18) and the right side of (19) are 0, and DW tests are satisfied. When FDIAs occur, the above does not hold, DW tests are not satisfied, FDIAs are detected. Even Γ is small, different from χ2detector, Σwcan be increased to ensure that DW-based EKF detector can detect FDIAs. Moreover, the positive correlation between the detection effectiveness of DW-based EKF detector and the watermarking intensity is also revealed by (18) and (19). With the increasing of watermarking intensity Σw, cross covariance of watermarking and the residuals and auto-covariance of the residuals increase, which meansW(T) andV(T) enlarge. Thus, it improves the detection effectiveness of DW-based EKF detector.
3) Security property analysis of new DW-based EKF detection method for FDIAs: The detection effectiveness of DW-based EKF detection method has been analyzed. When the attacks bypass the detector, security performance is then analyzed. To quantify the additional distortion caused by FDIAs, it is defined as

It means that when the FDIAs (12) bypass Tests 1 and 2, the additionaldistortionpower ofthesystemislimitedto0.
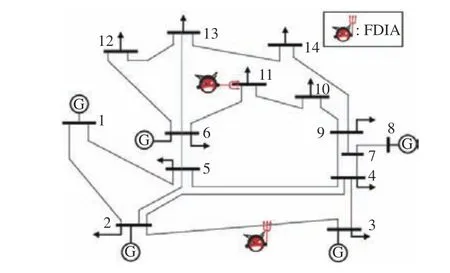
Fig. 2. Schematic diagram of IEEE 14-bus system under FDIAs.
According to (6) and (7), the residual of the attack-free system can be given by system state with the help of the first two time samples (i.e.,k=0 andk=1) derived from power flow (PF) calculations, and the parameters are set as α=0.8 and β=0.5. Then, state estimation based on EKF is operated fromk=2 . Diagonal elements ofF0andP0are set as 1 .0 and 1 ×10−6, respectively.
FDIAs in (5) emerge atk≥3 and

Fig. 3 shows the detection results of χ2detector and DW-based EKF detector under the same FDIAs. Obviously, χ2detector cannot detect FDIAs at all. The strong robustness of SG ensures the stable operation of SG will not be affected by short-term FDIAs. However,as FDIAs continue to destroy measurement data, the stability of SG is destroyed. The influence of FDIAs on data is marked and amplified by DW, which ensures that DW-based EKF detector can detect FDIAs quickly and sensitively. Moreover, when DW signal is too weak to mark attacked data effectively, FDIAs possibly bypass DW-based EKF detector, resulting in misdetection. Due to page limit, the corresponding results are not presented. Therefore, DWbased EKF detector also need to choose appropriate DW signal.
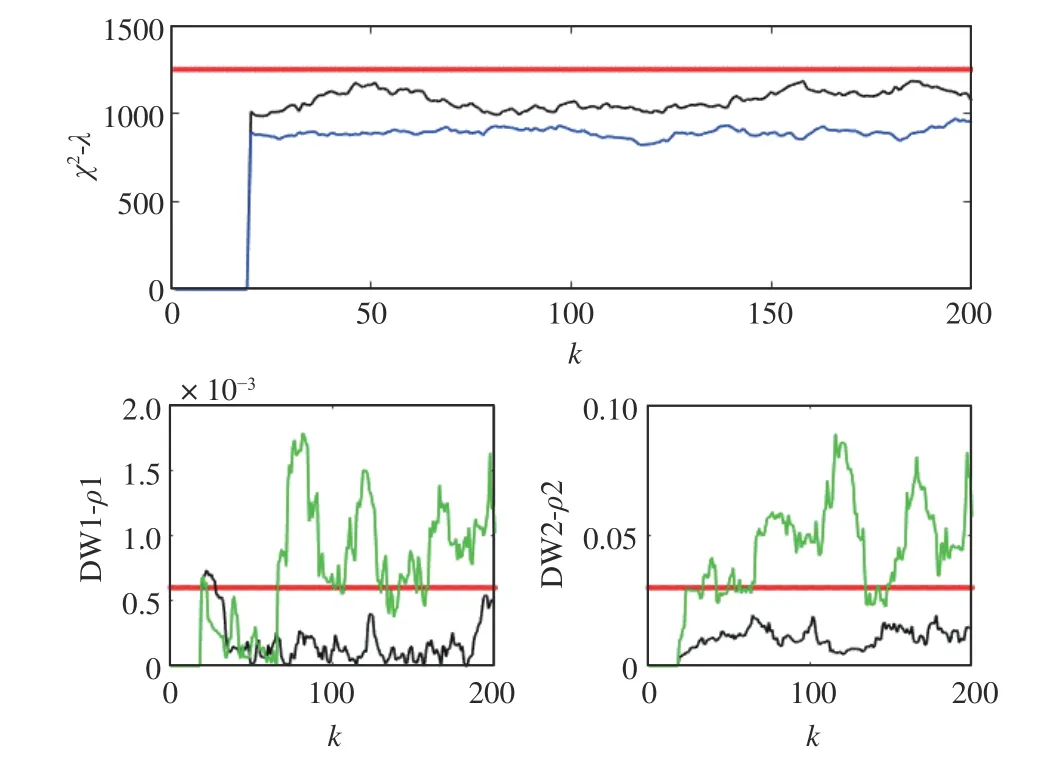
Fig. 3. Comparison of detection results between χ 2 detector and the proposed DW-based EKF method. Black line: Normal system. Blue line: System under the FDIAs without watermarking. Green line: System under the FDIAs with watermarking. Red line: Detection threshold. The detection threshold of χ2 detector is ζ 3=1250, which is based on the principle of ensuring no false detection without attack.
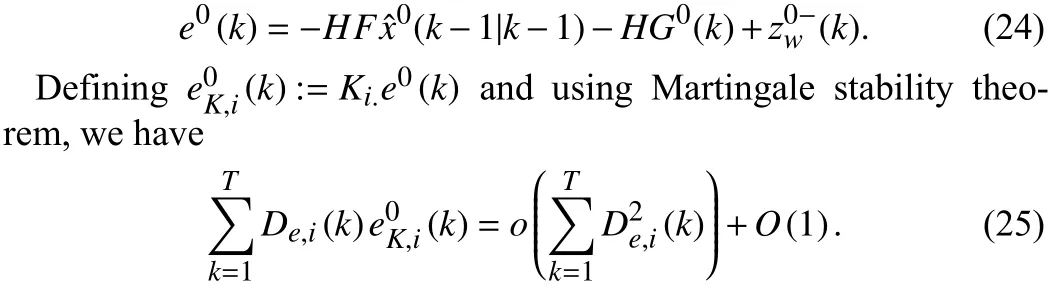
Substituting (25) into (22) yields

Experiments:IEEE 14-bus system is employed to validate the proposed method, as shown in Fig. 2. Holt’s technique initializes
Additional distortion power of SG under different attack intensities is shown in Fig. 4. With the increase of attack intensityγ, the system additive distortion power increases gradually. When the attack intensityis onlyγ=−0.2,the additive distortionpower ofthe system isveryclose tothatof the attack-free system(i.e., γ=0).It also means that DW-based EKF detector cannot detect the FDIAs with this intensity.
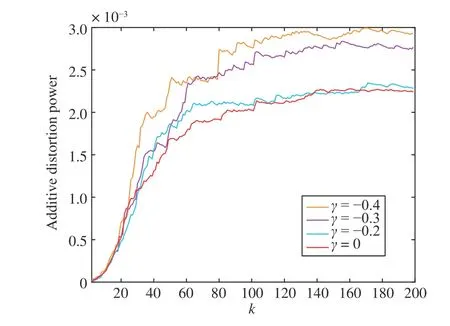
Fig. 4. Additive distortion power under different intensity attacks.
To analyze the impact of FDIAs on SG at attack intensity γ=−0.2, considering that the system operates close to the upper power limit of transmission line, the upper power limits of 1–3 transmission lines are 100 MW, 50 MW and 50 MW, respectively,and the upper power limits of other transmission lines are 40 MW.
Table 2 shows the optimal power flow (OPF) calculation results before and after FDIAs. Compared with the original optimal power flow calculation results, it shows that there is little change of the optimal power flow operation cost of the system before and after FDIAs with γ=−0.2, and the system is not affected in general.However, the state estimation results after FDIAs change load distribution and power flow of the system, which finally leads to the adjustment of power generation distribution.
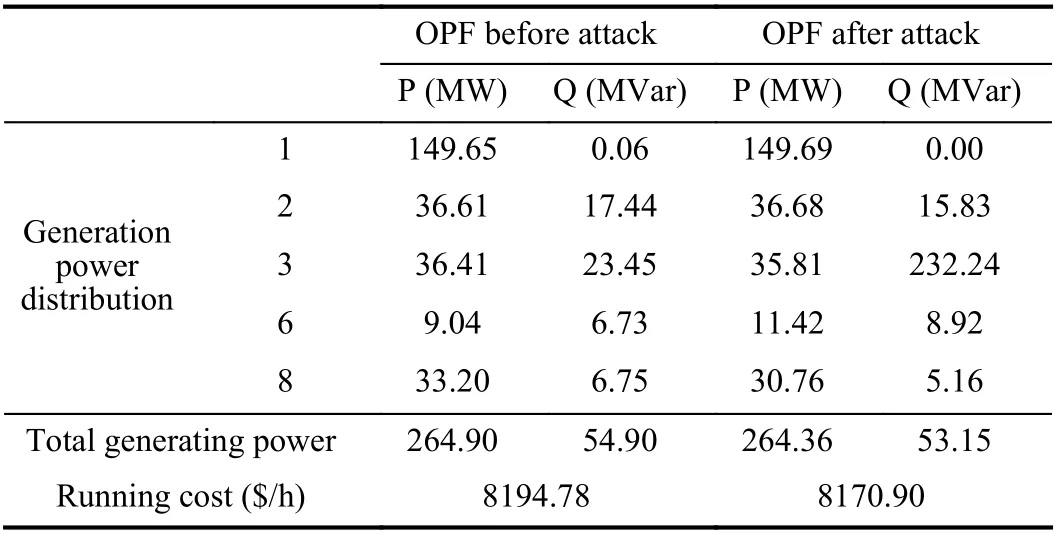
Table 2.Optimal Power Flow Results Before and After Attacks
According to power flow calculation of the system, Table 3 shows the power flow calculation results before and after FDIAs of some corresponding transmission branches. Since there are many transmission branches, only 5 transmission branches that are more prone to overload are analyzed including transmission branches 1-2,1-5, 2-3, 2-4 and 4-5. In comparison with the power flow results before and after FDIAs in Table 3, it is not difficult to see that FDIAs with γ=−0.2 has little impact on SG power flow, but it will still lead to the adjustment of branch power flow.
Conclusions:This letter has proposed a new DW-based EKF detection method for FDIAs in SG. Security weaknesses ofχ2detector is firstly analyzed and a new DW-based EKF detection method for FDIAs is presented by integrating the watermarking as symmetric-key encryption and DW tests. Using cross covariance of watermarking and the residuals and auto-covariance of the residuals,the positive correlation between the detection effectiveness of FDIAs and the watermarking intensity has then been proved. Furthermore,additional distortion power of the system has been provided todemonstrate security property of the proposed method. Finally, the effectiveness of the proposed method is confirmed on IEEE 14-bus system. However, according to the proposed DW-based EKF detection results, the recovery and security control of SG under FDIAs are interesting future research direction.
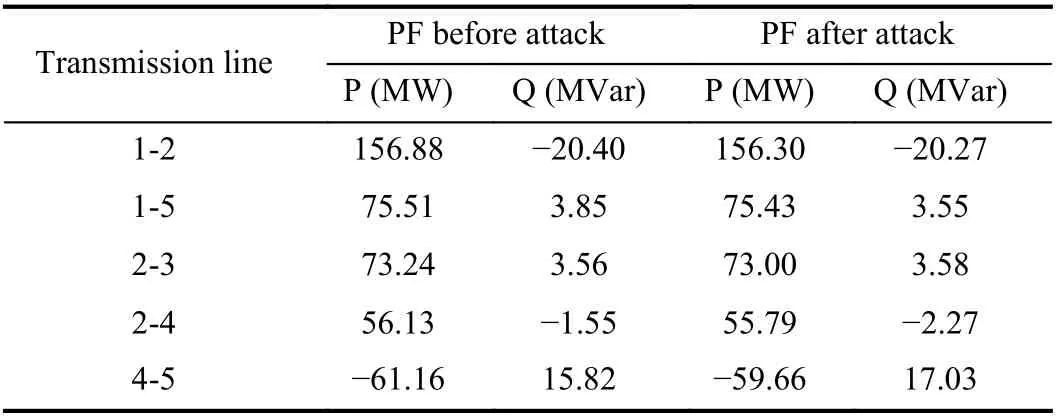
Table 3.Power Flow Results Before and After Attacks
Acknowledgments:The work was supported in part by the National Science Foundation of China (92067106, 61773253, 61803252,61833011), and Project of Science and Technology Commission of Shanghai Municipality (20JC1414000, 19510750300, 21190780300).
杂志排行
IEEE/CAA Journal of Automatica Sinica的其它文章
- An Overview and Experimental Study of Learning-Based Optimization Algorithms for the Vehicle Routing Problem
- Towards Long Lifetime Battery: AI-Based Manufacturing and Management
- Disagreement and Antagonism in Signed Networks: A Survey
- Finite-Time Distributed Identification for Nonlinear Interconnected Systems
- SwinFusion: Cross-domain Long-range Learning for General Image Fusion via Swin Transformer
- Real-Time Iterative Compensation Framework for Precision Mechatronic Motion Control Systems
