Statistical Analysis of a Class of Secure Relay Assisted Cognitive Radio Networks
2018-12-26MonaShokairWaleedSaadShadyIbraheem
Mona Shokair, Waleed Saad,3, Shady M. Ibraheem,2
1 Electronic and Electrical Comm. Dep., Faculty of Electronic Engineering, Menofia University, Egypt
2 Telecom Egypt, Egypt
3 Electrical Engineering Department, College of Engineering, Shaqra University, Dawadmi, Ar Riyadh, Kingdom of Saudi Arabia
Abstract: In this paper, the problem of communication security in an underlay wiretap cognitive radio network is addressed and statistically investigated. We rely on a simple dual-hop communication model of decode and forward relay assisted network. Regarding the interference from primary users, interference power and maximum transmit power constraints; this network is subjected to multiple eavesdropping attacks which employ a specific interception strategy. To confound this eavesdropping, proposed selection schemes are exploited that aim at maximizing the minimum of the dual secrecy rates in order to strengthen the physical layer security. Moreover, exact and asymptotic closed form expressions are derived for specific performance metrics over independent and identically distributed Rayleigh fading channels. At high signal to interference noise ratio (SINR), tangential system bounds are also derived and discussed.Monte Carlo simulation results emphasize our assumption. It is found out that at the full diversity of the system, any additional node that enters the cooperative eavesdropping system becomes significantly of no effect.
Keywords: relay selection; non-colluding or colluding eavesdroppers; outage probability;secrecy rate; power constraints.
I. INTRODUCTION
Cognitive radio networks have been widely utilized as an effective approach to exploit the available portion of the spectrum opportunistically by enabling the unlicensed secondary users to transmit simultaneously with the licensed primary users on the same bandwidth via employing overlay (interweave) and underlay mechanisms [1]. Among these mechanisms, the underlay cognitive radio network is preferable due to its low implementation complexity in the dense areas where the secondary users are allowed to utilize the licensed spectrum if the interference to the primary users is below a given threshold [2].
Meanwhile, cognitive relay assisted networks were used to overcome the problem of extending the coverage of wireless networks[3]. Specifically, cooperative schemes had been proposed to obtain a diversity gain and enhance the performance [4-14]. However,due to the natural wireless broadcasting, the physical layer security is vulnerable to illegitimate benefits. Securing and protecting issue of the physical layer against eavesdroppers had been extensively investigated for non-cognitive radio networks [15-22].
In [15] the authors analyzed the essence of physical layer security from the information theory viewpoint. This can be achieved by improving statistically the source to destination channel while corrupting all wiretap channels.Two methods of maximizing the secrecy rate under the total power constraints or minimizing the total power under the secrecy rate constraints were proposed in [16] where the cooperative relays transmit a weighted source signal to the destination. Ref. [17] investigated how to place the cooperative relays in order to achieve the best performance. A more generalized model with single and multiple relay selection schemes had been considered in [18]
where the principle of cooperative diversity order was discussed. In [19] closed form expressions of some performance metrics, i.e.,outage probability and secrecy outage probability, were derived for multicasting system in the presence of multiple eavesdroppers. In[20] the case of unknown channel state information CSI about the attackers (sub-optimal relay selection) was assumed. The case of regenerative multi relay system was introduced in [21].
In the context of cognitive radio networks,literature review on physical layer security has been further investigated in [23-32] and references therein. More specifically, due to the power constraint at the primary network and the impact of large scale fading, the performance of the secondary network will be substantially limited. Promising relay protocols had been studied and used to forward the secondary source message in a cognitive radio system to the destination. In [23] a relay selection scheme was proposed for security-reliability constraints in a cognitive radio network with a single eavesdropper under the best knowledge of the statistical properties of the channels. However, the maximum interference power constraint was only considered at the secondary source. In [24] single and multi relay selection schemes were investigated
where security and reliability trade-off issues were examined. Nevertheless, the interference from the primary transmitter was not taken into account, where the coexistence of the primary and secondary networks in the same frequency band may cause mutual interference to each other. Furthermore, the secondary network can utilize the interference of the primary transmission as an active jamming signal to enhance the security. A similar work was applied to the general case of wireless network by using single-relay and multi-relay selection schemes [25].
This paper investigates a statistical analysis for a class of underlay cognitive radio network. For secure and reliable transmission,optimal relay selection schemes were proposed in the presence of non-colluding or colluding eavesdroppers.
Ref. [26] studied the performance of a twohop underlay cognitive relay network with a decode and forward relay by assuming the combination of direct and relayed signals at the destination and the eavesdropper without considering the interference of the primary transmitter. The performance of a single-input multiple-output (SIMO) cognitive radio network was investigated in [27] under joint constraint of the interference and security of the primary network. However, it did not consider distant transmitters and receivers that may be assisted by a set of intermediate relay nodes and no specific relay selection scheme was proposed. Ref. [28] discussed security versus reliability for multi-eavesdropping cooperation without including in a cognitive radio network. A beamforming vector for single multi-antenna relay was designed in [29] to maximize the secrecy rate by extra forwarding a jamming signal. However, the interference from the primary network was also ignored.
In [30] proposed selecting a secondary relay and a secondary destination to improve the security performance and neglected the impact of primary interference. Ref. [31] investigated the problem of selecting a secondary user to transmit a jamming signal that can confuse the interception of the eavesdropping system and maintain a secrete communication for the secondary network. Unfortunately, the mutual interference power and maximum transmit power constraints were ignored which is not reasonable for cognitive radio networks. Besides, the primary interference can be relied upon as a jamming signal to confound eavesdropping. A similar proposed model characterized the physical layer security in cognitive radio networks in the presence of multiple primary users and multiple eavesdroppers was analyzed in [32] without considering the interference constraints of the primary network.
In spite of these investigations, an integrated model that analyzes the physical layer security in underlay cognitive relay networks regarding the primary/secondary mutual interference constraints has not been introduced in any open literature which motivates our simple work.
In this paper, a statistical analysis of a class of wiretap cognitive relay networks is performed where a simple model of a dual-hop underlay cognitive relay network is assumed.Decode and forward relays are employed to support the communication in the presence of non-colluding or colluding eavesdropping systems. Different from our earlier work [35], independent and identical distribution iid channels are assumed which simplify the analysis.Besides, it is further assumed that signal to interference noise ratios at all nodes are much greater than one. Although the considered system model is simple, it can be recognized as a simple generalized cognitive radio network model where all of its nodes are subjected to all possible communications’ constraints while taking into account the mutual communications between nodes with the expected and applicable SINR at the end of each node. To the best of the authors’ knowledge, this model has not been considered before and it can be easily included in many applications of the field. The contributions of this paper can be summarized as follows:
● We propose relay selection schemes for each individual hop and the dual-hop communications to improve the physical layer security under the primary/secondary mutual interference constraints.
● The secrecy performance is evaluated and new closed form expressions for achievable secrecy rate, outage probability and asymptotic outage probability are derived.
● Thereafter, system inner and outer bounds are also analyzed which give appointments on the steady state performance of the network. Those bounds become tight at high transmitted signal to interference noise ratio(SINR) in the considered system.
● The impact of the number of relays and eavesdroppers in the cooperative system is studied and simulated.
The rest of the paper is organized as follows. In Section II we investigate the system analysis and the optimum relay selection conditions. In Section III we evaluate the performance metrics. Simulation results, discussion and future works are depicted in Section IV.Section V concludes the paper.
II. SYSTEM MODEL AND ANALYSIS
A wiretap underlay cognitive radio network model is considered here. It is indeed a dual-hop decode and forward relay assisted network. It consists of the following nodes;one secondary user source, S, set of N decode and forward relays, (Ri,1 ≤ i ≤ N), one secondary user destination, D, one primary user transmitter, PTx, one primary user receiver, PRx,and multiple M eavesdroppers, (Ej,1 ≤ j ≤ M).All nodes are equipped with a single antenna where the secondary source transmitter transmits a confidential information to the secondary receiver in the presence of non-colluding or colluding eavesdroppers with the aid of N trusted decode and forward relays, while the eavesdroppers try to overhear and attack all of the communication paths between the secondary source, S, and destination, D.
As shown in figure 1 a primary network is in co-existence with the secondary network.An interference power constraint condition guarantees that the transmitted power of the secondary source and relays will not exceed a threshold limit, i.e., TPSand TPR, respectively. It is further assumed that all of the legal receiving nodes are confirmed to know global channel state information (CSI) and instantaneous information about eavesdroppers is available,as in [5], [10], [19] and references therein1This assumption is reasonable when the well known user represents a legitimate user for some applications and an eavesdropper for others, at the end of the secondary user source, S. Furthermore, the secondary user destination, D,and relays are subjected to interference signals from the primary transmitter, PTx. All communication channels are quasi-static, flat fading and error free estimated Rayleigh channels.No additional external interference is considered, No direct path from S to D is found due to deep path fading conditions and the spectrum sharing network is assumed with a half duplex mode communication.
The secondary network communication procedure takes place in two phases; In the first phase, S transmits a power constraint signal while the relays listen, types of non-colluding (e.g., max. of eavesdroppers) or colluding eavesdroppers (cooperative eavesdroppers)2It is nonsense considering a collision system as it reduces the opportunity to occupy a legitimate channel.,try to overhear through wiretap channels. In the second phase, the relays listen in a cooperative scheme. Then, one potential relay node from the set of successfully decodes the source message is selected to forward the re-encoded messages toward the destination such that this relay satisfies a certain optimization condition.However, the eavesdroppers’ system tries to again overhear the second path through another dedicated wiretap channel.
A cooperative communication method based on an optimum selection scheme is proposed to select the relay that has the best maximum dual-hop secrecy rate of S−Riand Ri− D paths (i.e., (maxi({S − Ri} ,{ Ri−D})),i ={1,….N}, to forward the source message to the destination.
In the following, we derive formulas for the cumulative and probability density functions(CDF and PDF) of the SINR of the two communication phases, considering the optimum selection scheme. Then, we use them to obtain closed form expressions for some important metrics such as the non-zero achievable secrecy rate and the outage probability.
The secrecy rate is defined as in [33],
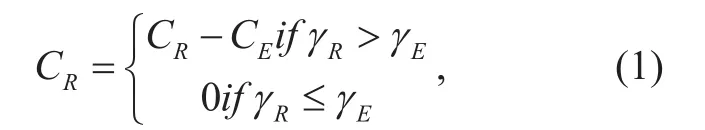
where CR, CE, γRand γEare the capacity of the main channel, the capacity of the wiretap channel, the SINR of the main channel and the SINR of the wiretap channel, respectively.
It is remarkable that model looks like a cell cluster where sources and destinations are located at the edge of the cell and relays are located well within the cell. We will begin with the individual hop relay selection scheme. It is notable that this scheme of secrecy analysis may dominate, if the eavesdroppers locate within one of the two communication phases.
2.1 The first communication phase
In this phase, due to Rayleigh fading channels assumed, S sends its message signal to Riwith average power,

where Psis the constraint source average power, hs,pis the S−P channel fading coefficient and PSpis the constraint average power at the PRxend.
In the vicinity of Ri, the received signal can be expressed as,

where hs,iis the S−Richannel fading coefficient and siis the transmitted source symbol of the S−Rilink with average power Ps, hp,iis the channel fading coefficient of the the PTx− Riinterference signal, piis the corresponding transmitted interference symbol with average power(where the superscript i belongs to relay i ) and ni~ CN (0,N0) is an additive white Gaussian noise (AWGN) signal.

Fig. 1. A class of wiretap underlay cognitive radio networks.
The received signal by eavesdropper j is given as,
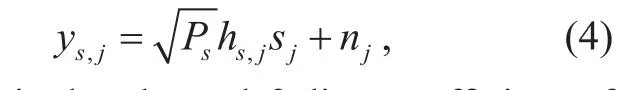
where hs,jis the channel fading coefficient of the overheard source message and sjis the overheard source symbol of the S−Ejlink and nj~ CN (0,N0) is an AWGN with respect to the j th eavesdropper end.
From (2), (3) and (4), the signal to interference noise ratio (SINR) at the i th relay can be expressed as,

At the j th eavesdropper, it can be obtained by,
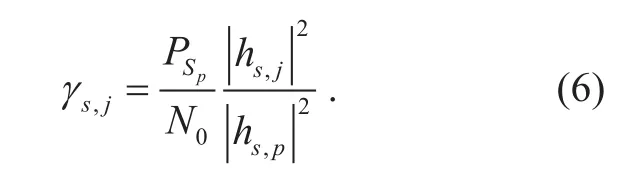
The achievable maximum rate for data transmission of the S−Richannel (channel capacity) is given by,
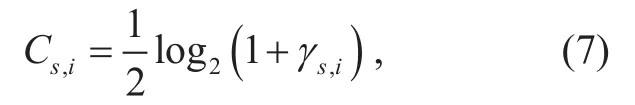

The achievable secrecy rate (secrecy capacity) at relay Rican be computed as,

where Cs,Jrepresents the capacity of the eavesdropping system which performs the underlined interception strategies andrepresents the SINR of the source signal at the eavesdropping system. Thus, Riof the optimal secrecy rate for the first phase can be extracted from the following relation,
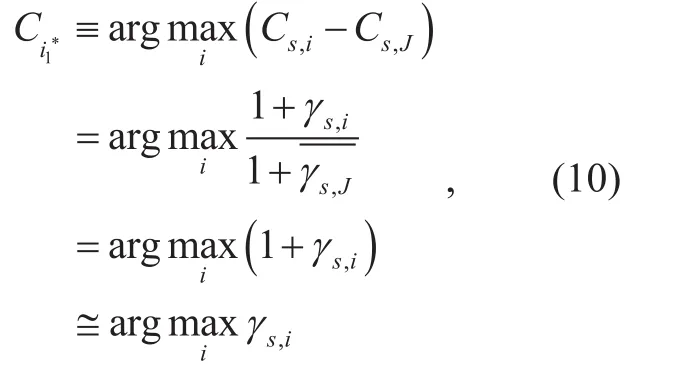
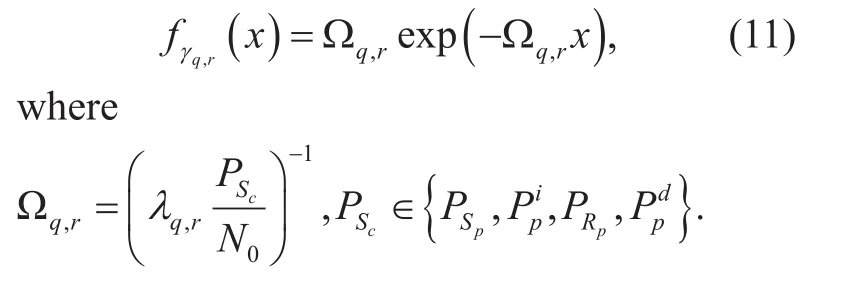
For simplicity, we compute the joint conditional statistics on. Then, averaging over the PDF ofas follows;


Substituting (13) and (15) into (17) and taking the equivalent SINR limits of integration from one to infinity, this yields,

Finally, the CDF of γs,iis obtained by averaging over the PDF ofusing
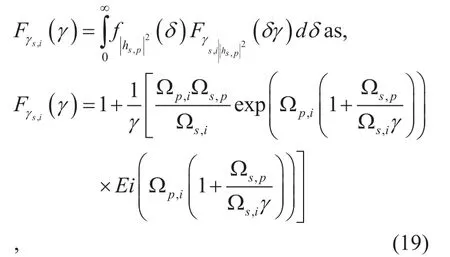
where Ei(.) is the exponential integral defined by [34, Eq. (3.352.4)] and the PDF ofgiven by,
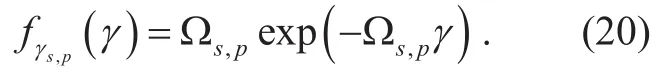
In the first phase, the relay selection rule is denoted according to (10). Therefore, the CDF at the optimum relay Ri*is given such that i satisfies,
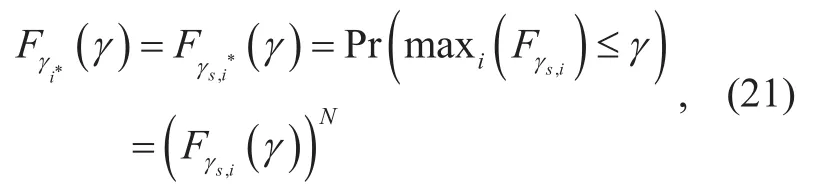
where γs,i, i∈ {1 ,2,… N} are independent and identical distributed random variables (without loss of generality) and Fγs,i(γ) is given by (19)by replacing i by i*.From the previous analysis, we can conclude that in the first communication phase,the optimal selection is abbreviated by a conventional selection scheme.
2.2 The second communication phase
As assumed for the first phase, Riforwards its message signal to D after successful decoding3Assuming high SINR, it is supposed that Ri∈D where=N is the set of all relay nodes that can decode the source message correctly with a cardinality of=N.By considering that this intended set can pass a predefined threshold, a relay is selected to decode and retransmit information to the destination [5].with average power that is given by,

where PRiis the constraint relay, Ri, average power, hi,pis the Ri− P channel fading coefficient and PRpis the constraint average power at the PRx, end, where relays of equally transmitted powers is assumed.
The received signal at D can be expressed as,

where hi,dis the Ri− D channel fading coefficient and riis the transmitted relay, Ri, symbol of the Ri− D link with average power PRi, hp,dis the channel fading coefficient of the PTx−D interference signal, Pdis the corresponding transmitted interference symbol with average power(where the superscript d belongs to D) and nd~ CN (0,N0) is an additive white Gaussian noise (AWGN) signal.
The received signal by eavesdropper j is given by,

where hi,jis the channel fading coefficient of the overheard relay, Ri, message and ri,jis the overheard relay, Ri, symbol of the Ri− Ejlink and nj~ CN (0,N0) is an AWGN with respect to the j th eavesdropper end.
From (22), (23) and (24), the signal to interference noise ratio (SINR) at D is denoted by,

At the j th eavesdropper the equation can be expressed by,

Applying the same concept for the second phase, the achievable secrecy capacity can be obtained by the form,
where Ci,drepresents the capacity of the relayed signal at D, Ci,Jrepresents the capacity at the eavesdropping system.γi,Jand subscript i2represent the SINR of the i th relayed signal at that eavesdropping system and the relay index of the second communication phase, respectively.
The maximum achievable secrecy rate(maximum secrecy capacity) from the optimum relay Ri, i=i*can be computed for the second phase as,
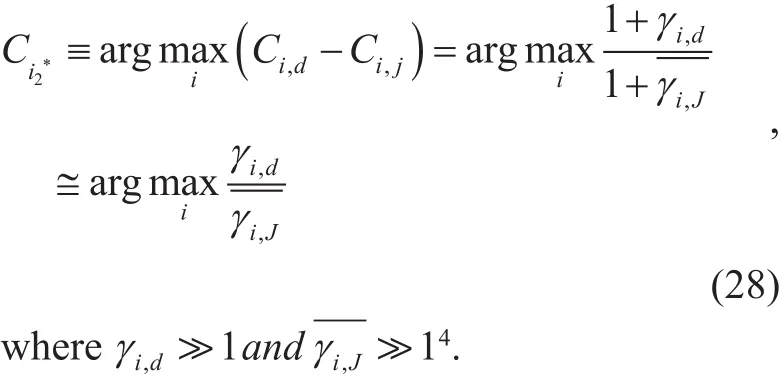
Following similar steps and assumptions,a similar formula as (18) is obtained for the CDF of the R.V. γi,dconditioned onas,

From (26) the PDF of the R.V.for the j th eavesdropper can be expressed directly as,

Two interception strategies of eavesdropping are adopted which are greatly confined on the cooperative nodes. This will be discussed in the following:
−Case 1: Non-colluding eavesdroppers(Maximum of the eavesdroppers):
In this case, the strongest attacker is picked up. Therefore, the group SINR is considered by the one that has the highest SINR and is given by,

where Ωi,J= Ωi,jf or all i,j, the PDF of the R.V.γi,Jconditioned onhi,p2is determined directly by differentiating the expansion of(33) by γ as follows,
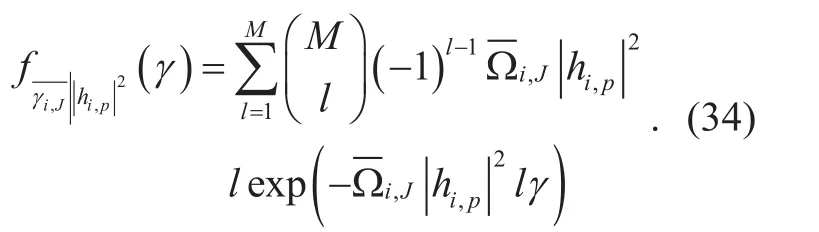
From (29), (34) and by using a similar integration as (17), the CDF of the R.V.is given by,

where Alis given by,
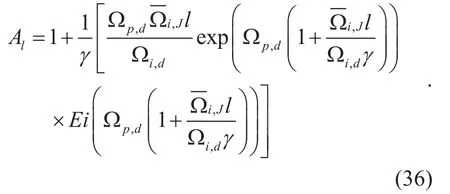
It is obvious that the CDF of the R.V. γiis independent of. This is because any node exposes itself as a legitimate user will pick up the same amount of the restricted relay power. The final result is obtained by averaging over the PDF ofusing
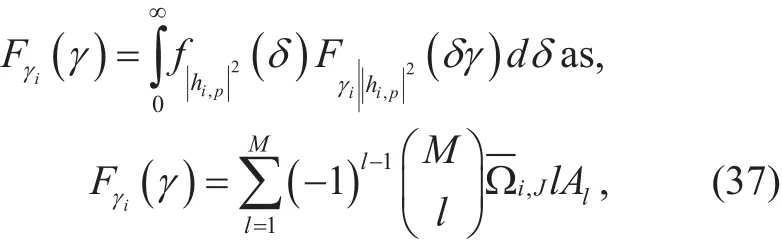
where Alis given by (36) under the assumption that,
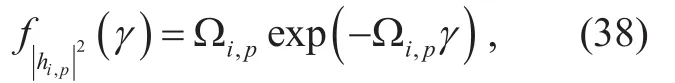
where Ωi,pis the weighted mean of the R.V.and Ei(.) is the exponential integral defined by [34, Eq. (3.352.4)].
In the second phase, the relay selection rule is given according to (28). Therefore, the CDF at the optimum relay Ri*is
given such that i satisfies,
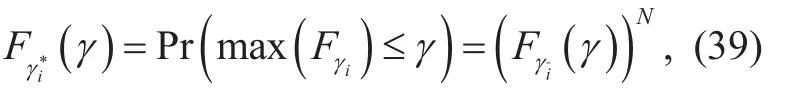
where Fγi(γ) is given by (37) by replacing i by i and considering that γi, i ∈{1,… … N},are iid R.V. s.
−Case 2: Colluding eavesdroppers (Cooperative eavesdroppers):
In this case, all eavesdroppers can perform joint processing, the group SINR is given by combination as,

where the eavesdroppers apply the maximal ratio combining MRC reception procedure“MRC with independent and identical distributions iid”. Thus, the CDF of the R.V.γi,Jconditioned on hi,p2is given by,

By applying recursive calculus, we get,

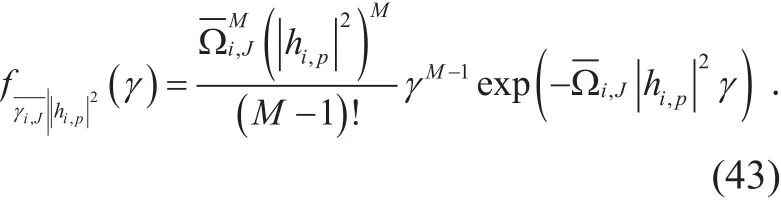
From (29), (43) and using a similar integration as (17), the CDF of the R.V.γi= γi,d/ γi,Jconditioned onis given by equ.
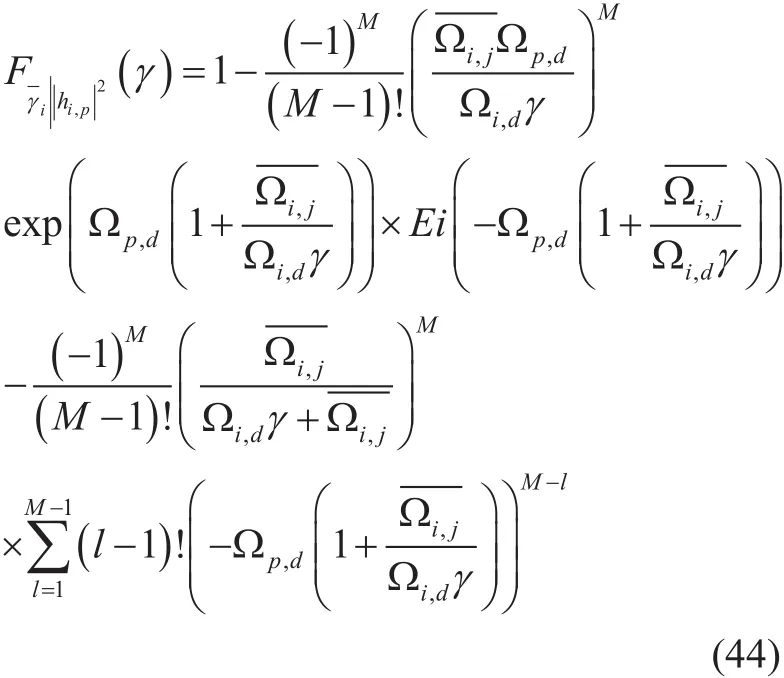
(44) on the top of the page. By averaging over the PDF of, this will be resulted in,
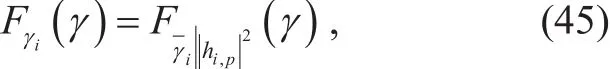
The relay selection rule is applied according to (28). Therefore, the CDF at the optimum relay Ri*is given such that i satisfies,
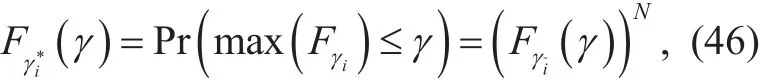
where Fγi(γ) is given by (44) by replacing i by i and considering that γi, i∈{1,…N}, are independent and identical distribution R.V. s.
2.3 The optimal selection
In the previous analysis, we in part state the statistical selection conditions for each communication phase, separately. However, the relay selected to achieve maximum secrecy rate at one hop, can severely interrupt the reception security at the other.
Thus, in order to guarantee that neither of the separate secrecy rates falls down to a low level (i.e. which implies a security degradation), a low complexity overall relay selection scheme is adopted to select a relay the cooperative system that maximizes the minimum of the dual secrecy rates as follows;
Let Ci1andCi2denote to the achievable secrecy rate of the first and the second communication phases, respectively. For the same relay selection we have, i1=i2=i. Then, the optimal relay Ri*maximizes the relation,
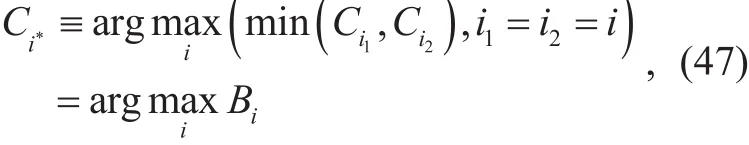
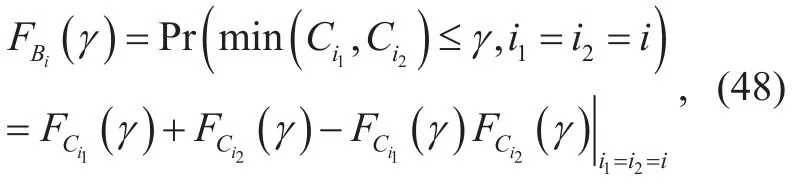

III. PERFORMANCE METRICS
In this section, we are going to derive expressions for some useful performance metrics such as secrecy outage probability, non-zero achievable secrecy rate and asymptotic secrecy outage probability.
In the concerned system, one feasible method to ensure a confidential data security
The secrecy outage probability is defined as the probability that the secrecy capacity (e.g.correspondingly SINR) falls below a desired secrecy rate (e.g. correspondingly a desired level).
For a certain relay Ri, i∈ {1,… .,N }, letrepresent the SINR γiat the first and the second phases, respectively, with a desired level at the first phase γout1and at the second phase γout2. The secrecy outage probability may be computed equivalently as,and reliability against eavesdropping is to transmit the data with a rate that is less than its dedicated channel capacity (i.e. from the source to destination) while maintaining that the difference between the transmitted and the confidential data rates larger than the channel capacity of the eavesdropping system. This guarantees that any transmitted data rate will become beyond the reliable illegal interception.
3.1 The exact secrecy outage probability

where α indicates the joint probability of the dual secure communication, i.e., from the secondary source to destination, and the last two terms follow from the fact that they are two disjoint events. A special case from the above equation occurs, for the two phases, when the communication channel requires one desired or predefined SINR level e.g. γout. In such case, Poutiis given by,
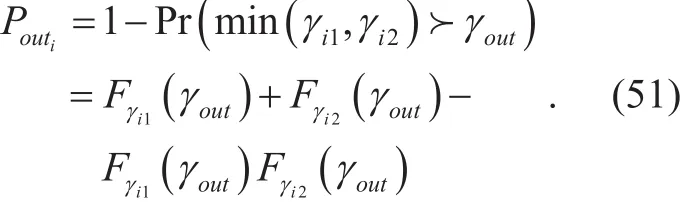
The reminder question is how to evaluate the CDF Fγil(γout), l ∈{1,2} of the two
phases. Actually, this can be processed by deriving the distributions of the terms under the log operation in (9) and (27), respectively. Indeed, Fγi2(γout) is obtained by (37) or (44) for a certain eavesdropping scheme. Furthermore, Fγi1(γout) can be derived in a similar way as Fγi2(γout) by replacingand Ωp,dby Ωp,irespectively. Three sub-metrics owed on them will be evaluated as follows:
1) Optimal secrecy outage probability: It follows likely from (51) for a certain selected optimal relay, i.e., i=i*, as
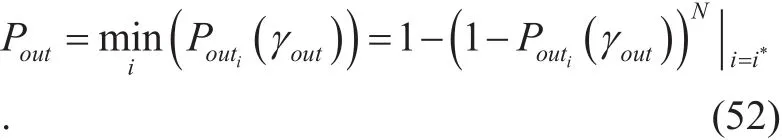
2) The non-zero achievable secrecy rate: By employing the fact that, it is obtained in the following form

3) Inner and outer bounds for the secrecy outage probability
In this subsection, we define the inner bound as the secrecy outage probability that appears when the minimum secrecy rate of a dual-hop communication itself for a certain selected relay is indeed the minimum rate amongst the entire relays, namely,

where Biis given by (47). Furthermore, the outer bound is defined by,

3.2 The asymptotic outage probability
Exact expressions are too complicated to interpret conceptually the impact of interference and eavesdropping for high SINR regime.This represents a main agent that identifies and controls the network behavior. In the following, we exhibit the effect of increasing the SINR statistically on all network parameters and random variables. If the transmitted SINR is abruptly increased in order to enhance the system performance within the secondary network. Then, the CDF in (11) can be approximated to its first order term, namely,
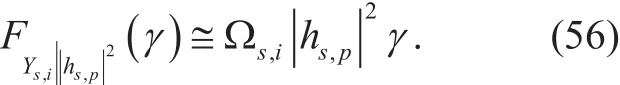
This yields a significant simplicity for the system analysis and gives an appointment on the steady state behavior, as well. Upon this fact, let the other transaction parameters and R.V. s be dependently unchanged. Then, by applying similar statistical analysis, a generalized form for the CDF of the SINR of Rican be rewritten as,

where the impact of diversity gain is not basically emphasized here5The diversity gain can be improved to approach N in this simple model by utilizing partial relay selection or optimal combining., e.g. it can be enhanced by using relays with distinguishable parameters, and ψiis defined as the coding gain parameter and derived as follows,
3.2.1 1stCommunication phase

3.2.2 2ndCommunication phase
–case of maximum of eavesdroppers
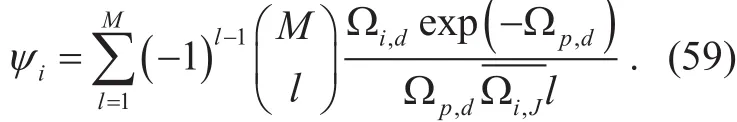
3.2.3 3rd phase
–case of cooperative eavesdroppers
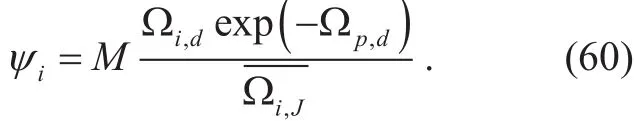
IV. SIMULATION RESULTS AND FUTURE WORK
4.1 Simulation results
This sub-section is devoted to verify the fact that the analytical derivation will coincide with the system simulation and to study the impact of the system parameters on the security performance. This is confirmed by performing Monte Carlo simulations with 106experimental trials.
From the previous analysis, one can find that the impact of relay interference is more severe with respect to the primary network than the source and destination. Consequently,it becomes dominant. Here, we are not interested in the impact of diversity gain that can be enhanced to approach N ≜numberofrelays for optimal relay selection. It should be noted that the diversity order expressed by the number of optimal collected relays out of N relays is beyond our interest.
Without loss of generality, a proper coordination is used to justify the simulation results where all the fading parameters are modeled aswhere δ is the path loss exponent and dq,ris the normalized distance between nodes. In the two-dimensional (2D) network topology, dq,rcan be calculated aswhere q has the coordinate (xq,yq) and r has the coordinate (xr,yr). Hence, the nodes are deployed in a 2D unit square area, the locations of S, D, PTxand PRxare fixed at distinct locations as (0.1, 0.5), (0.8,0.5), (7.25,1) and(2.25,1), respectively. The source power, i th relay power are fixed at, Ps= PRi=10 d BW and primary transmit power is 8 dBW while the noise power is, N0=−4 dBW. In the following three cases, each has distinct considerations of the number and the locations of relays and eavesdroppers.
Figure 2 illustrates the relation between the secrecy outage probability and the actual transmitted power, i.e. relay transmitters are the dominant interfere sources of power, with different number of cooperative relays. The relays are fixed at(0.5,0.36),(0 .5,0.4),(0 .5,0.44),(0 .5,0.48),(0.5,0.52),(0 .5,0.56),(0 .5,0.6),(0 .5,0.64),(0.5,0.68)}, while the eavesdroppers are fixed(0.8,0)}. This figure indicates a local minimum value of outage which represents the optimal adjustment of the encoding power of the relay system. Moreover, this figure also compares our exposed eavesdropping models. It is obvious that the cooperative eavesdropping exhibits worse performance than the case of maximum of eavesdroppers due to its robust overhearing procedure. Increasing the number of relays adds a little degree of freedom that improves the system performance marginally.There exists a successful agreement between the theoretical and simulation results which justifies our derivations. For low transmitted power, the outage probability begins to deteriorate until it reaches its minimum value.Then, it again begins to increase by increasing the transmitted power due to primary network constraints.
In figure 3 a global CSI knowledge about the primary network i.e. Ωp,i, Ωi,p, Ωs,pa nd Ωp,dis considered where constraint sources of power are maintained. The relays are fixed at {(0.5,0.5)} or {(0.5,0.4), (0 .5,0.6)} or{(0.5,0.4), (0 .5,0.5), (0 .5,0.6)}, while the eavesdroppers are fixed as in figure26. The performance of the secrecy outage probability against the increasing in SINR is highlighted.Moreover, the impact of increasing the number of relays, the inner and outer bounds are included in this figure. It is cleared that the case of non-colluding eavesdroppers outperforms the case of colluding eavesdroppers. It is notable that the outage probability drops down when the SINR increases. The asymptotic re-sponses represent the floor values of the exact curves. Additionally, the bounds approximate the exact curves. This can be realized to the extent that asymptotic outer bound and exact curves are tightly compromised at high SINR.Finally, parallel slops for different values of N ≡ number of re lays reflect the equality of the diversity gain.
An illustration for the maximum achievable capacity versus SINR γiis shown in figure 4.The distribution of the relays and the eavesdroppers are {(0.5,0.4), (0 .5,0.5), (0 .5,0.6)}and {(0.4,0),(0 .5,0),(0 .7,0),(0 .8,0)},respectively. Using the proposed optimal selection and constraint power sources, one can observe that there is a limited maximum capacity values “upper floor” [23] after which the secrecy rate will collapse unless the constraints are preserved. This means that at high SINR the secrecy rate is approximately fixed.It is noted that the horizontal lines represent the asymptotic curves of both the case of non-colluding eavesdroppers and the case of colluding eavesdroppers which are fully characterized by (59) and (60) where their fixed values, i.e., “1.904356783339800e+00” and“1.847668876613300e+00”, are evaluated by considering the parameters used in the simulation and denote the maximum achievable secrecy rates under a target secrecy rate of 0.8 bits/s/Hz.

Fig. 2. Secrecy outage probability vs. relay system transmitted power for target secrecy rate of 0.8, with N=1,2,1 0.

Fig. 3. Secrecy outage probability versus SINR for relaxed target secrecy rate of 0.5.
Increasing the number of eavesdroppers leads to a significant degradation in the secrecy rate. As depicted in figure 5, the secrecy rate decreases when the overhearing resources “M” increase where the eavesdroppers are located as(0.46,0),(0 .48,0),(0 .5,0),(0 .65,0),(0 .7,0),(0.75,0),(0.8,0)}. For M≫1, the performance curve over the colluding eavesdroppers or non-colluding eavesdroppers schemes is asymptotically the same. We use the same parameters as in figure 4 with one relay centered at {(0.5,0.5)}, then, we deposit the eavesdropping nodes one by one and examine the secrecy rates. It can be observed that the secrecy rates begin to deteriorate from values very close to the values “1.904356783339800e+00”and “1.847668876613300e+00” for the case of one eavesdropper, i.e., where the colluding eavesdroppers or non-colluding eavesdroppers schemes exhibit the same performance, to reach a “lower floor” value where the secrecy rate is preserved regarding our simulation parameters. Noticeably, a non-zero secrecy rate can be achieved by adjusting the key network parameters despite increasing the eavesdropping nodes, i.e., M≫1.
4.2 Future work
While our proposed model represents an applicable case of DF relay assisted cognitive radio networks, it can be extended to include the other relaying protocols (i.e., amplify and forward (AF), compress and forward (CF)and etc.) under the same conditions and constraints. For example, the use of AF relaying protocol can be considered for analysis in our proposed model, if the effect of error propagation in the DF relays outperforms the noise amplification of the AF relays under the same channel conditions and interference limitations.
We advocate the extending of our analysis to the AF and CF relaying protocols, if the wireless communications are supported by unintended relays, i.e., known as untrusted relays, which are not allowed to overhear the confidential information between the source and the intended destination. An example of such a scenario is in the heterogeneous networks where different types of nodes are colocated in the same geographical zone and the communications between homogeneous nodes can be supported by relaying nodes which may be considered untrusted. At this extent, AF and CF relaying protocols can achieve positive secrecy rates by leveraging the jamming signal which does not hold for DF relaying [36].
Another extension of our work can be revealed when it is desired to exploit the available degree of freedom of the cooperative relay channels by utilizing the multiple relay selection protocol [37]. Through an exhaustive search multiple relays can be selected to achieve an optimal secrecy rate under the considered constraints. However, there is a tradeoff between the achievable secrecy rate and the computational complexity which increases exponential with number of relays.
Through these models, we can deduce and derive many expressions that can be applied in our model according to network topology and conditions.
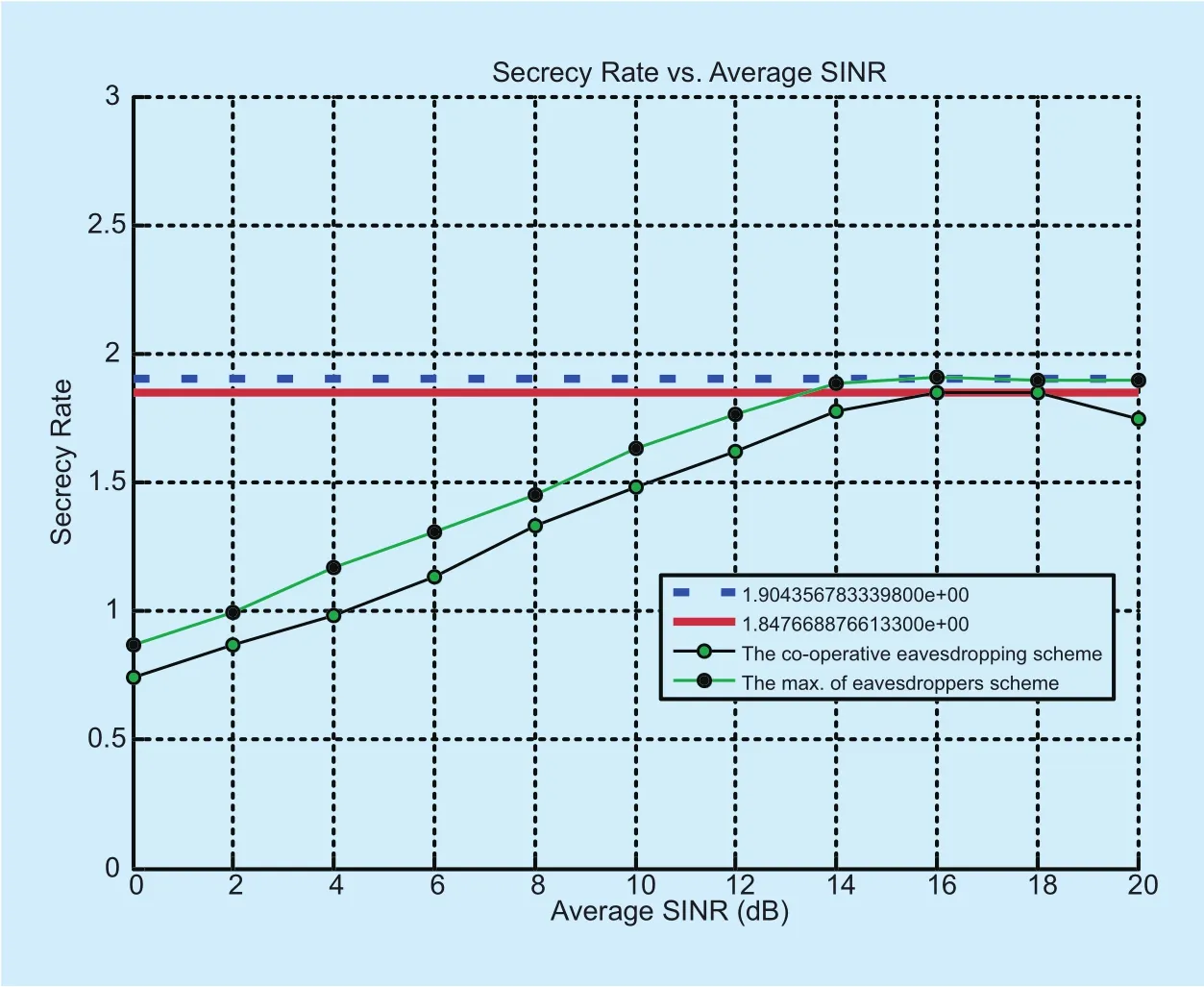
Fig. 4. Achievable secrecy capacity vs. SINR γi .
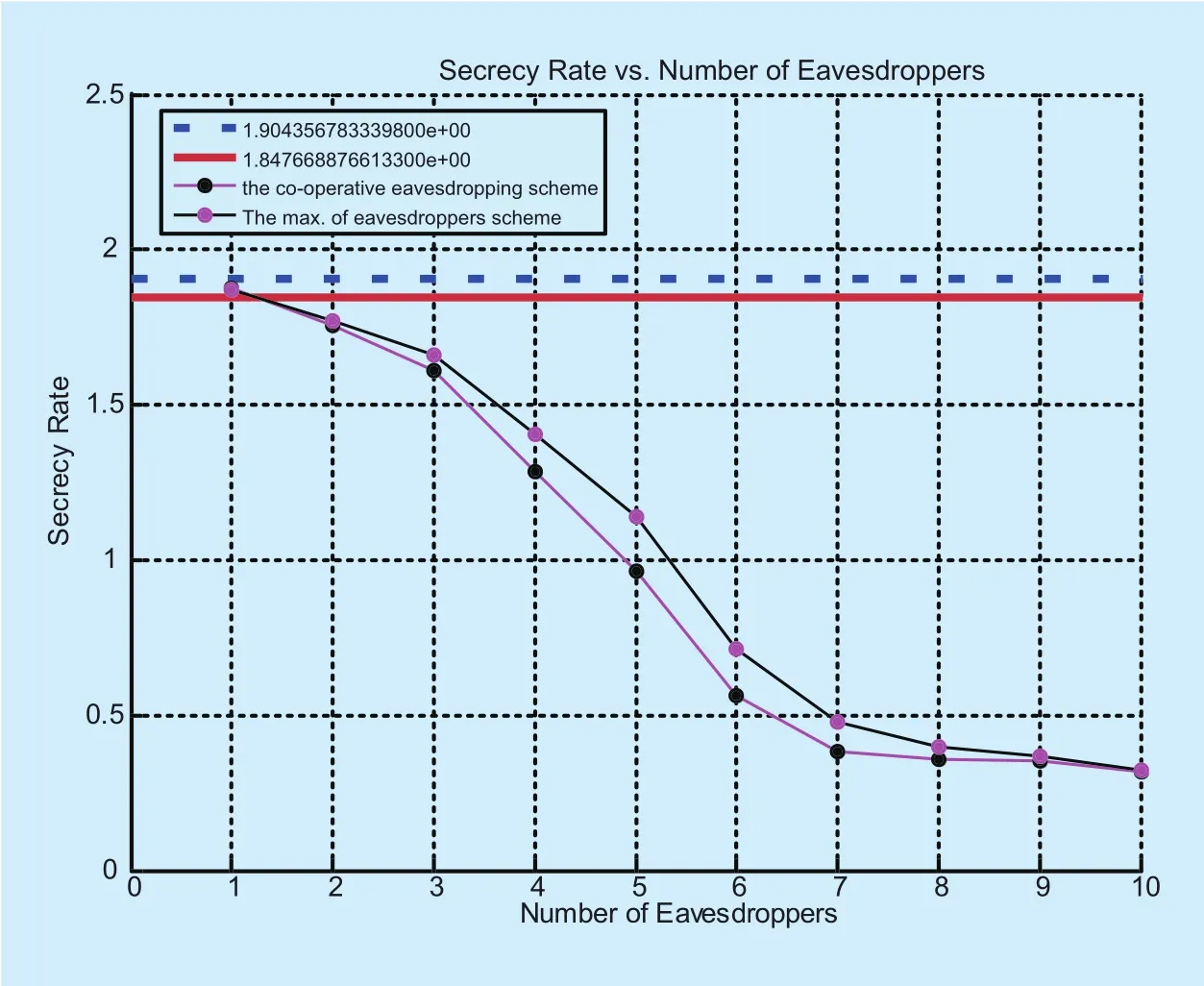
Fig. 5. The impact of number of eavesdroppers on the secrecy rate.
V. CONCLUSIONS
This paper investigates a statistical analysis for a class of underlay cognitive radio network.For secure and reliable transmission, optimal relay selection schemes were proposed in the presence of non-colluding or colluding eavesdroppers. Analytical expressions were derived for some basic performance metrics upon the exposed models to verify how to design and adjust the sources of power in order to optimize the communication quality. The proposed selection schemes were compared with the traditional selection ones. It was shown that the proposed schemes outperform the traditional schemes as the number of relays increase at full cooperative diversity of the system. Specifically, the achievable secrecy rate is not significantly related to the number of eavesdroppers. In addition, system bounds were also derived. Simulation results were in accordance with the analytical ones.
杂志排行
China Communications的其它文章
- Pedestrian Attributes Recognition in Surveillance Scenarios with Hierarchical Multi-Task CNN Models
- Cost-Aware Multi-Domain Virtual Data Center Embedding
- Moving Personal-Cell Network: Characteristics and Performance Evaluation
- A Novel 3D Non-Stationary UAV-MIMO Channel Model and Its Statistical Properties
- Mode Selection for CoMP Transmission with Nonideal Synchronization
- Illegal Radio Station Localization with UAV-Based Q-Learning
