HB-Protocol Based Advance Security System for PKES Using Multiple Antennas
2018-12-26AhmerKhanJadoonLichengWangMuhammadAzamZia
Ahmer Khan Jadoon, Licheng Wang,*, Muhammad Azam Zia,2
1 State key Laboratory of Networking and Switching Technology, Beijing University of Posts and Telecommunications,Beijing 100876, China
2 Department of Computer Science, University of Agriculture Faisalabad, Faisalabad 38000, Pakistan
Abstract: Modern cars are mostly computerized and equipped with passive keyless entry and start (PKES) system. PKES is based on Radio Frequency Identification (RFID) technology for authentication of the authorized drivers. RFID technology has replaced the conventional ways of identification and authorization in order to facilitate users while introducing new security challenges. In this article, we focused on verifying the presence of authorized key in the physical proximity of car by employing multiple antennas. Application of multiple antennas to the currently developed cryptographic algorithms opens a new approach for researchers to improve security of RFID based systems. We propose an advanced security system for PKES using multiple antennas wherein an authorized key passes through multiple vicinities to allow driver to access and start the car. Furthermore, we modified a light-weight cryptographic protocol named as HB (Hopper and Blum) protocol to integrate it with the proposed design based on multiple antennas. Simulation results show improvement in security functionality while keeping in view the efficiency constraints.
Keywords: passive keyless entry and start; radio frequency identification; hopper and blum protocol; multiple antennas; authorization
I. INTRODUCTION
RFID technology is being vastly studied and used since the last decade in most of the applications due to its advantages over the classical ways for identification and information handling. Modern cars are equipped with complex, safe and reliable electronic systems in order to facilitate the driver. Authorization of driver and access to the car has gained the interests of many manufacturers around the globe. Before the introduction of RFID technology, there were physical keys which would allow the driver to open the locks and ignites the engine by inserting the matched key into the slot. With the development of technology,remote keys were introduced which can remotely authorize driver by pressing fob on key to open the door of car.
RFID technology provides authentication and authorization to the driver even keys in their pocket. While manufactures named this technology as Passive Keyless entry and start(PKES) [1]. A user can open the car and starts its engine without inconvenience of searching for the keys. RFID reader is installed in the car and attached to a controller that manages door controlling circuit. As the user approaches towards the car, authorization is performed by the RFID reader and through subsequent authentication the locks are opened automatically. When user sits in car, ignitions switch authenticate the key automatically and starts the engine. Figure 1 shows the different vicinities inside and outside of the car. Whenever the authenticated key enters the respective vicinity, controller in the car automatically detects the key by the help of RFID reader, and sends a signal to open the door or start the engine.
Although PKES systems are working very efficiently while they are vulnerable to various attacks. We noted that, the main reason which makes it possible for an adversary to launch attacks is that; car only verifies weather it can communicate with the correct key to open and start the engine. Alternatively, car should verify that the authenticated key is present in its Physical proximity.
In order to overcome these vulnerabilities,we proposed a system based on multiple antennas that are generating diff erent proximity levels around the car.
1.1 Relay attack
Recently Security and privacy of modern cars have attracted attention of many researches since cars are equipped with computerized systems these days. Wireless systems in modern cars provides more flexible applications for the designers in order to facilitate users yet are more vulnerable to attacks.
Very popular attack described in the literature is relay attack [2] [3]. Message between two entities can be relayed using a communication medium to make them appear closer to each other. For instance relay attack can be used to attack credit card transactions, or it can be used to attack wireless sensor nodes etc. Similarly attacker uses it to relay the authentication message between key and the car.
When the loop antenna is placed close to the door handle (< 30 cm), it captures the car beacon signal as a local magnetic field. This field excites the first antenna of the relay,which creates an alternating signal at the output of the antenna by induction. This electric signal is then transmitted over the coaxial cable or air and reaches the second antenna via an optional amplifier. The need for an amplifier depends on several parameters such as the quality of the antennas, the length of the cable, the strength of the original signal and the proximity of the relaying antenna from the car’s antenna [4].
There are two types of relay attacks; wired relay attacks and wireless relay attacks. In wired relay attack, two loop antennas are used and LF signal can be relayed between these two antennas via cable connecting them.Amplifiers can be used in between the cable to amplify the signal. One antenna is placed near the car’s transmitter to catch the magnetic field and second loop antenna is placed near the key. First antenna converts this field into electrical signal that can be transmitted over the coaxial cable to the second antenna. The antenna is exited and produces magnetic field closer to the key and the signal can be successfully transmitted to the key [5].
Another type of relay attack uses air as a communication medium to pass on LF signal transmitted by car to the key with minimum delay [6].Wireless relay attack consists of an emitter and a transmitter. Emitter catches the low-frequency signal from the car, and up-converts it to high-frequency (2.5GHz),amplifies it and transmits it through the air.At the other end emitter receives the high-frequency signal, down-converts it to get the original low-frequency signal and pass it to loop antenna which re-produces the same LF signal as emitted by the car. Figure 2 shows the wireless relay attack over 2.5 GHz channel. We note that the communication between the car and key can be made even the key is present distant from the proximity of car.Once the car communicates with authenticated key, it assumes that key is present inside the defined vicinity and door locks are opened.

Fig. 1. Low frequency (130 KHz) coverage area inside and outside the car.
To achieve security against relay attacks,there is a need of multiple authentication process to detect tag at different locations. Few applications have been designed using multiple readers which can read the tag at different locations. Multi Reader Controller (MRC) [7]can work efficiently for anti-collision purpose but does not carry out the necessity to intercept attacks related to PKES. However, use of multiple antennas in a single RFID reader is a better choice to achieve essential security requirements.
Our main contributions in this article are as follows
(1) This is the first attempt, to consider an advanced security system using multiple antennas in a single RFID reader to intercept relay attack in modern cars.
(2) We propose an advanced security system for PKES using multiple antennas. Moreover, a light-weight HB algorithm is modified and synchronized with multiple proximities of antennas.
(3) We perform numerous experiments and comparative analysis shows that our proposed system provides the proof of correct key present in the physical proximity of car, which makes it more secure and reliable against relay attacks. A security system using multiple antennas and sharing different encryption keys for every antenna facilitate to detect any relay device placed inside the vicinity of car.

Fig. 2. Relay attack (130 KHz signals) over wireless (2.5GHz) channel.
Rest of the paper is organized as follows:Section 2 explain the literature on existing authentication protocols for RFIDs based security systems. We also presented a brief introduction to basic Hopper and Blum (HB)protocol in section 2, for the good understanding of modified version of HB protocol used in our proposed system. In section 3, advanced method which makes the PKES system more secure and reliable is explained. In Section 4 the system design and security verification of the proposed method is discussed and finally section 5 presents concluding remarks.
II. RELATED WORK
There are many scholars who proposed schemes for PKES system that are mostly based on RFID technology. So our concern about encryption and authentication mainly depends on the selection of best protocol being used in RFID systems.
2.1 Authentication protocols for RFID based PKES System
A brief assessment on existing protocols used in RFID systems is made to pick a feasible authentication protocol which can meet requirements of the proposed PKES system. The authentication protocols used for RFID systems can be classified in 4 different categories.
Class one includes full-fledged conventional cryptographic algorithms such as Public key cryptography, symmetric cryptographic ciphers and hash functions. Public key cryptography has been studied form very long time and researcher developed many advanced algorithms based on it such as Elliptic curves,deffie hellman key exchange, RSA etc. [8-10].Recently some advanced cryptographic algorithms based on public-key cryptography have been proposed that are very effective in terms of security such as short linearly homomorphic proxy signature scheme [11], an ID-based linearly homomorphic signature scheme [12],Significant permission identification [13].Symmetric cryptographic ciphers consist of DES, AES, and AES 3 etc. [14]. Cryptographic Hash functions include MDS, SHA1, SHA2,SHA3 etc. [15]. This class of cryptographic algorithms is complicated, requires a lot of calculations and costs large memory resources.
Second class is little simpler and consists of protocols that support one-way hashing function and random number generator placed on tags. Sarma et al in [16] introduced the hash-Lock scheme in which metaID=H(K)is used to hide the real ID of a tag. It uses K as the shared secret key between the backend server and the tag where H is a one-way hash function. Although a certain level of reliability is provided by this method even at low cost but the tag can be tracked by an adversary easily via its metaID and thus risks our privacy or transaction secret. Furthermore, it is easy for even a passive adversary to sniff the channel and later spoof the tag, since the secrete key shared by back-end server and tag is sent as a plaintext.
In [17] Henrici and muller proposed the hash based ID variation protocol similar to hash chain protocol. A random number is used in this protocol, which dynamically increases in every successful authentication. This improved protocol is more secure against replay attacks. The ID of tag is randomized in ever interrogation, so it resolves the location attack.Hash based ID variation protocol can restore data from the previous record which makes it reliable to prevent data loss. Unfortunately,this protocol is unable to resist against man-inthe-middle attacks.
Gao et al defined the de-synchronization attacks and position tracing attacks [18]. Zhou et al has also described the vulnerability of hash chain protocol [19], based on de-synchronization attacks. RIPTA-DA has been designed to overcome these attacks by using a stochastic dynamic multi key protocol for encryption of information. Noise disturbance technique is designed to prevent against de-synchronization attack but at the cost of large number of calculations.
Second class of protocols also include some recent techniques such as, Distance Metric Optimization [20], Secure Multiple Amplify-and-Forward Relaying [21] [22], DF relaying networks with randomly distributed interferers [23], Precoding-Based Blind Separation [24], Differentially Private Naive Bayes Learning [25], HybridORAM [26] etc. These techniques are very important in terms of efficiency and fast computation.
The third class of protocols includes a random number generator and simple functions referred as lightweight protocols. These protocols include mainly, Hopper and Blum abbreviated as HB, HB+, HB++ proposed by Blum et al. in [27], Juels and Weis [28], Bringer et al. [29] and Piramuthu [30] respectively. There are many developments put forward in this type of protocols by many researches to make them more secure against Man in middle Attack. All these protocols come under the family, which has used Learning Parity with Noise(LPN) to provide stronger security and fast functionality [31]. Protocol works on the challenge-response mechanism by the multiplication operator “dot” for the random number “a”and secrete key “s” and then adds noise “v”to the product. Duc et al presented a synchronization based communication protocol used for RFID [32]. The protocol is used to protect the EPC Global Class-1 Gen-2 RFID tags with only simple cryptographic primitives such as CRC and PRNG. The above mentioned protocol can prevent against malicious reader impersonating attack and also prevents to clone tags. Another advantage of this protocol is that each RFID tag emits different string of bits when receiving the reader query which provides privacy by tracking activities and personal preference of users.
The fourth class called ultra-lightweight encryption which is simpler and only uses simple bitwise operations for example AND,XOR, OR etc. with some built-in function on tags. This class of protocols is commonly used in low-cost RFID tags but they are less secure as compared to other cryptographic protocols.
Although full-fledged authentication protocols provide strong security but they cannot meet the requirements of low cost, fast speed and less power consuming RFID systems, so there is a need for trade off. For the proposed system, we have to choose a light-weight protocol which is more secure and needs to consume less power and time (as the tag present in the key needs to pass through multiple vicinities). The process must be fast and efficient with more security. Moreover, the protocol must have the ability to integrate with our multi-antenna design. Analysis shows that HB protocol is more effective and efficient to meet the requirements for proposed PKES system.
2.2 Overview on HB protocol
Processing power and memory constrains of the required implementation decides selection of best possible authentication protocol used to achieve required security and privacy. After analyzing the protocols used for RFID implementations, it’s clear that simple lightweight authentication protocols are more suitable and efficient for proposed PKES system.
Juels and Weis in [28] introduced two highly efficient, lightweight shared key authentication protocols for RFID identification, based on the work of Hopper and Blum [27]. HB and HB+ authentication protocols are both proven to be efficiently secure and works on the principle of learning parity with noise (LPN)problem [33], which only requires the same hardness as decoding a random linear code[34].
2.2.1 The LPN problem
The Learning Parity with Noise (LPN) prob-lem has recently found many applications in cryptography as the hardness assumption underlying the constructions of “provably secure” cryptographic schemes like encryption or authentication protocols. The basic principle of LPN problem is to search the secrete key by a round of iterations. Bits can either be 1 or 0, so the probability of correct guess is 0.5. As the number of bits in the secrete increase then the probability of guessing the right key is reduced. Being provably secure means that the scheme comes with a proof showing that the existence of an efficient adversary against the scheme implies that the underlying hardness assumption is wrong [35].
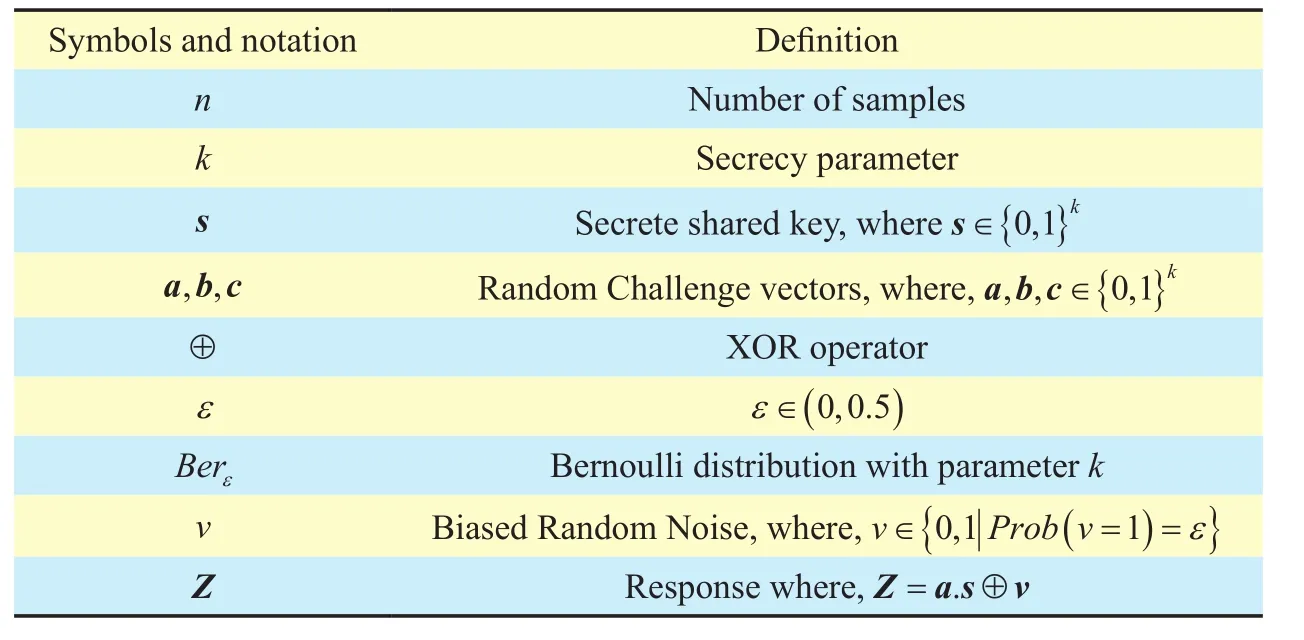
Table I. Symbols and notations for LPN Problem.
Following are the notations and symbols used to define learning parity with noise problem and employed in HB-Protocol
The learning parity with noise problem with parameters k(length of secrete), n(number of samples) and ε where ε∈(0,0.5) asks to find a random fixed k-bit secrete key s from n samples of the form a,〈 a,s〉 ⊕ v where a∈{0,1}kis a random vector and v ∈{0,1 Prob( v = 1)=ε}has a Bernoulli distribution with parameter ε and we represent this distribution as v ← Berεi-e. Pr[ v=1] =ε.
From the above notations, the hardness of LPN problem for ε, v and n with distribution D can be defined as

Where A represents the n×k binary matrix of random bits.
On the practical side, LPN based schemes are often extremely simple and efficient in terms of code-size as well as time and space requirements. This makes them prime candidates for light-weight devices like RFID tags, which are too weak to implement standard cryptographic primitives like the AES block-cipher.
2.2.2 Basic authentication step of HBProtocol
To analyze the basic authentication step of HB protocol for n=n(k) parallel iterations, we let k denotes security parameter. Reader R and tag T shares random secrete key i.e. s∈{0,1}k.In the basic authentication step, a reader sends a random bit stream a∈{0,1}kas a challenge to tag, and the tag replies with response i.e.Z = a,s ⊕ v, where v∈{0,1}k, correspond to a biased random noise with {Prob(v=1)=ε}for a fixed probability ε∈(0,0.5) and we represent it as v ← Berε. After receiving response from the tag, reader verifies weather Z = a,s ⊕v satisfies the challenge; if it satisfies then we say that the iteration is successful[28]. See Figure 3.
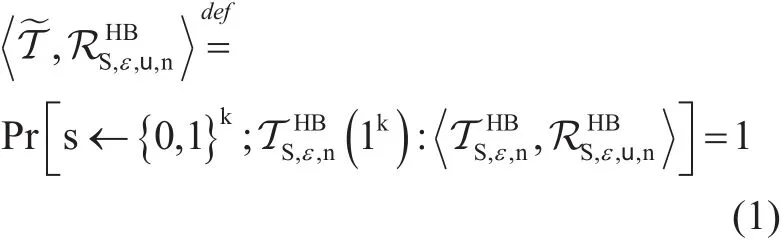
For a particular setting of ε, u=u(k) and n=n(k), we say that HB protocol is secure against passive attacks but for an active adversary, HB protocol has vulnerabilities. An active adversary can impersonate Reader R and sends the same bit-stream as a challenge vector repeatedly to the tag and then, learn the correct value of shared secrete key a.s. Juels and Weis in [28] proposed HB+ protocol,which is a modified version of HB protocol to achieve security against active attacks. In HB+ protocol Reader R and tag T shares two independent secrete keys; s1∈{0,1}kand s2∈{0,1}k. Based on the basic phenomena of LPN problem, there are many advance versions of HB family protocols. The proposed modification in the HB protocol can be applied to all the basic and advanced versions of HB family protocols to provide more security against active attacks related to low cost and limited resources systems.
III. METHODOLOGY
The proposed design consists of multiple antennas RFID reader which is applicable for PKES system used in modern cars. The proposed system provides additional security as it contains three antennas having different proximity ranges. Each proximity uses HB protocol challenge-response mechanism for authentication and shares different secrete encryption key for respective proximity. Every antenna creates circular vicinity around the car. We can vary the coverage area of every antenna to minimize the advantage for adversary to place relay devices inside vicinity of every antenna.
3.1 Modified HB protocol based on multiple antennas
We modified the basic HB protocol in such a way that both reader and the tag shares three different secrete keys s1, s2and s3for every round of authentication. Inside each round,the basic authentication steps are similar to the general HB protocol explained in section 2.2 (see Figure 3). Each round represents the respective proximity range around the car.
Fig. 3. Basic authentication step of HB protocol.
In Figure 4, Reader R and tag T shares three random secrete keys s1, s2and s3. In each authentication round, reader sends a random bit-stream as challenge. Tag replies with a response after multiplication of the random bit-stream with the shared key, and adds a random noise "v" to the response. Where "v"corresponds to a biased random noise with Pr[v=1]=ε for a fixed probability ε∈(0,0.5)and we represent it as v ← Berε. After applying LPN algorithm as illustrated in [31], reader verifies weather the response ⊕v, satisfies the challenge. If true then we say that the iteration is successful and tag is ready for next authentication round. Reader and tag both saves the value of random bit-stream a∈{0,1}kgenerated in round 1 and used it in the second round along with a new randomly generated bitstream b∈{0,1}kand so on. This mechanism makes every round dependent on the previous round which improves the security of the entire system. See Figure 4. Using more than one secrete keys and random challenge helps the system to achieve security against active attacks.

Fig. 4. Modified HB protocol based on multiple antennas.
Figure 4 shows the modified HB protocol for reader installed in the car and the tag present in the physical key. The protocol is modified in such a way that for every authentication round, different secrete keys are used in a synchronous way. For the first round, only one secrete key s1is used instead of all the security shared keys. For second authentication round,both s1and s2are used and similarly, third round uses s1, s2and s3. The process of second and third authentication does not continue unless first round is successfully completed. This mechanism makes the proposed system more secure against the relay attack and the message playback attack. The proposed modification of the basic HB protocol as shown in Figure 4 can be applied to HB+, HB++ and all the advanced versions of HB protocol family in a similar way but more cost involved in terms of resources utilization. All the improved versions of HB and HB+ protocols follow the same basic concept of Challenge-Response mechanism by using LPN problem with the addition of certain variables to improve the required security. For instance Munilla and peinado proposed HB-MP protocol in which a k-bit vector “b” such that b.x=Z is added.Combination of two secrete shared keys with rotations are used to make this protocol resistance to the man-in-middle attacks [36]. We can apply our proposed modifications to HBMP protocol in a similar way as performed on the basic HB protocol. A k-bit vector is added to each round of authentication. Based on HBMP protocol, we can combine two secrete shared key with rotations to make the protocol resistance to man-in-middle attacks. In this case the whole process involves six secrete keys plus the six random k-bit vector for three rounds of authentication. The main purpose of this example is to show that our modifications performed on the basic HB-protocol can be applied to recent and advanced versions of HB-family protocols that are found in literature [36-38].
Round 1
As user approaches towards the car; antenna with longest proximity (8m in our case)first detects the tag (present inside the authorized key) by ping mechanism and sends out the first random challenge a∈{0,1}k. After receiving a random k-bit stream, tag multiplies first secrete shared key s1with a∈{0,1}kand replies back the response as

Where, v ← Berε
Car receives the response and verifies weather Zreader1satisfies Eq.2. If it is correct then we say that the first authentication is successful.
Round 2
Similarly, when user enters inside the range of second antenna (5m in our case), the second antenna sends out another random challenge b∈{0,1}kto the tag. After receiving the random k-bit stream, tag multiplies second secrete shared key s2with the received random bit-stream ‘b’ and replies back with the response as

Cars receive the response and verify weather Zreader2satisfies Eq.3. If this verification is also correct, then we say that the second authentication will also be successful. Reader does the final authentication by sending continuous ping to detect the presence of key in nearest proximity around the car.
The proposed algorithm is designed in such a way that the process of authentication should be in a synchronized way to minimize the advantage for adversary. If the key does not complete the first authentication process successfully, it can never start the second authentication. In the proposed scheme, the outer two fields have distance more than one meter from the car’s transceiver, so a relay device present in these proximities (placed more than 1 meter away or carried by a walking attacker)is unable to effectively capture the correct information about the secrete key [4]. Therefore,the attacker only has the choice to place the relay device inside the nearest proximity in order to execute the attack. The proximities of the antennas can be changed respectively to detect the relay devices placed by an attacker.If second authentication initiates before the first authentication process, the relay attack can be detected (key cannot directly enter the smaller proximity without passing through the larger proximity range).

Fig. 5. First authentication: physical key is present between 5 meters and 8 meters.
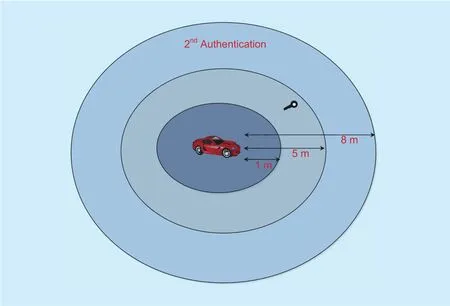
Fig. 6. Second Authentication: physical key is present between 1 meter and 5 meters.
Round 3
Finally when user approaches the innermost proximity of car, then the 3rdauthentication is performed in a similar way i-e the third antenna sends final random challenge c∈{0,1}kto the tag. After receiving the random k-bit stream, tag similarly multiplies third secrete shared key s3with the received random stream‘c’ and reply back the response as


Fig. 7. Third authentication: physical key is present inside 1 meter.

Table II. Inside 8 meters.
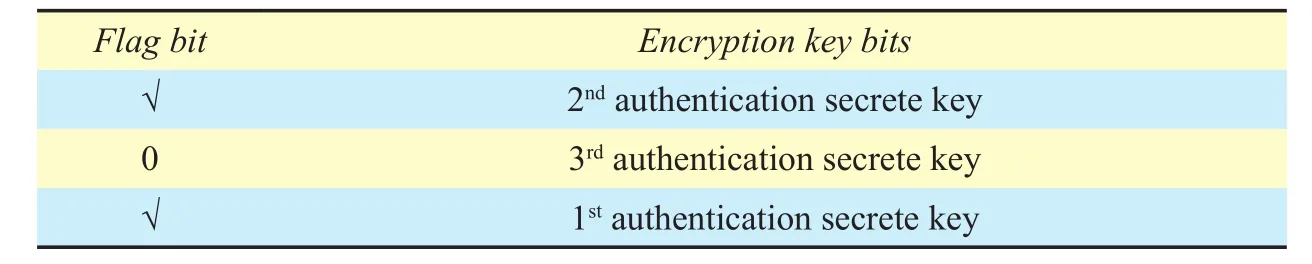
Table III. Inside 5 meters.

Table IV. Inside 1 meter.
Car again receives the response in a similar way to first and second authentication and verifies weather Zreader3satisfies Eq. 4.
If this verification is correct, then we say that the final authentication is also successful and the door locks are opened.
If the tag is detected by two or more antennas at the same time during the first authentication process (when the user should only be present in the proximity of longest range antenna) then the reader detects the attacker and the process is stopped. In this case, a user has to press the fob present on key to open the door locks.
Tag-end modifications
The basic modifications for the tag are mostly similar to those as described for reader.Tag also uses three different security encryptions keys instead of one. At each authentication round, the tag receives a challenge and replies with the respective response. The system is designed in such a way that there is a flag bit reserved for every secrete encryption key. Initially; when the tag is outside the proximity of car, all the flag bits are set to zero. As the tag enters the car proximity, first encryption key is placed on the top of the stack. For a successful authentication, the flag turns to ON-state and the next encryption key comes on top of the stack. Similarly; as second authentication is successful, the flag of second encryption key also turns to ON-state. If all the authentications are successful then all the flag bits reset to zero and the stack is also reset to its initial state as shown in the below Table 2,3 and 4.
IV. SYSTEM DESIGN AND RESULTS ANALYSIS
4.1 Setup
Our propose design consists of a circuit consisting of RFID reader which contains 3 antennas on a single chip i-e AN11314 (RC632 and PN512 family). The concept is verifying the tag in 3 different locations and being able to detect that it has travelled through all defined vicinities. An analog RF switch/MUX IC is required between the 3 antennas plus their impedance matching circuit and the reader IC, connecting the MUX control to Aurdino microcontroller which is also connected to the reader data interface via SPI. By this design,firmware can create ‘continuous scanning’ of the antennas. When a tag is detected, it can determine from which MUX position it was read.
4.2 Secrete Encryption keys
The choice of secrete keys is very important factor that should be considered during the setup of a secure system. Key size plays a vital role in security and effectiveness of the system. Long secrete keys provide strong security but authentication process requires large calculations which make the process slow [39].So there is a need of tradeoff between security and speed of the system. We have chosen 128 bit key length secrete key which has been used in a standard AES cipher and proved to be secure secrete key in symmetric ciphers [39].Figure 8 shows the set of 3 shared keys used in the proposed system.
4.3 Results analysis
a. “Z-values” for reader
Z-values are the product of the secrete key with a random bit-stream. At each authentication round a unique challenge of random bit stream is sent which helps the reader to detect and prevent any active attack against HB protocol mentioned in section 2.2. Z-values of reader are calculated to compare them with the Z-values of tag. Reader verifies Z1, Z2and Z3at each authentication round and continue the process only if these values are same as the tag’s Z1, Z2and Z3respectively. Figure 9 shows the first 128 bits of three different Z-values of the reader which are calculated at each round of the authentication process i-e three different vicinities around the car.
b. Comparison of tag’s “Z-values” with the reader’s “Z- values”
Most important step of the simulation is the comparison of “Z” values of reader shown in Figure 9 with response values of tag. The tag receives random bit streams ,b and c . Multiply these bit streams with the known secrete keys shown in Figure 8 and add noise v ← Berεto it at each round. After calculations, tag sends back the response to the reader. We receive the response and apply LPN algorithm on each response for the bit reconciliation at each round.

Fig.8. Shared secrete keys a, b and c.

Fig. 9. “Z” values for reader.
Figure 10 shows the “Z” values, calculated after applying LPN algorithm on tag’s response. It is noted that the tag’s response values shown in Figure 10 has the same bit values as compared to reader’s challenge values in Figure 9. Each Z-value represents one round of authentication. These simulation results indicate the complete authentication process i-e the authentication is successful during each round of challenge and response.Main advantage of this proposed protocols is that, it is extremely lightweight and both tag and reader needs to perform relatively few number of arithmetic operations such as AND/XOR etc. Compared to conventional ciphers it can thus be implemented using 3-5K gates.The simulation results also formally verify the security functionality of the proposed scheme keeping in view the resource constrains.
V. CONCLUSION
In this article, we have reviewed the PKES systems based on RFID technology with the vulnerability exploration. In order to overcome these vulnerabilities, we proposed a system based on multiple antennas that are generating different proximity levels around the car. A light weight RFID authentication (HB) protocol which works on LPN problem is modified in such a way that different encryption keys are allocated for every antenna. Therefore,proposed system allows detecting any relay device placed inside car’s vicinity, which minimizes the risk of various known attacks.Moreover, by continuous scanning of multiple antennas, a car is able to authenticate the true presence of physical key. We performed numerous simulations in order to validate the effectives of our proposed system. After employing three stages of security mechanism,simulation results show that proposed scheme is effective to protect against the attack. Comparative results showed that our proposed system outperforms the existing techniques in terms of relay detection. Consequently, we can say that, the proposed technique is feasible for practical use to prevent against most possible attacks related to PKES systems. This study opens a new research direction; the use of multiple antennas for existing cryptographic protocols.
ACKNOWLEDGEMENT
This work was supported by the National Key Research and Development Program (No.2016YFB0800602), the National Natural Science Foundation of China (NSFC) (No.61502048), and Shandong provincial Key Research and Development Program of China(2018CXGC0701, 2018GGX106005).
杂志排行
China Communications的其它文章
- Pedestrian Attributes Recognition in Surveillance Scenarios with Hierarchical Multi-Task CNN Models
- Cost-Aware Multi-Domain Virtual Data Center Embedding
- Statistical Analysis of a Class of Secure Relay Assisted Cognitive Radio Networks
- Moving Personal-Cell Network: Characteristics and Performance Evaluation
- A Novel 3D Non-Stationary UAV-MIMO Channel Model and Its Statistical Properties
- Mode Selection for CoMP Transmission with Nonideal Synchronization
