A Survey on Smart Collaborative Identi fier Networks
2018-04-04HaifengLiHongkeZhang
Haifeng Li, Hongke Zhang
National Engineering Lab on Next Generation Internet,Institute of Electronic and Information Engineering, Beijing Jiaotong University, Beijing 100044, China.
I. INTRODUCTION
The current Internet was designed decades ago, when a network was merely needed to allow a few computers to be shared among different universities. The original requirement is forwarding and routing data packets among a limited number of trusted computers. These key designs of the Internet make it very easy to link new network device to the Internet,enabling its large-scale growth. Up to now, the Internet has been a public and global network,which connects millions of network equipment and hundreds of countries. In current Internet,more and more high-requirement applications have emerged such as autonomous vehicles,three Dimensional Gaming and Virtual Reality(VR). In this context, the primitive designs of the Internet expose series of problems including security, mobility, scalability.
In order to solve these problems, functional patches for the Internet begin appearing increasingly, such as Content Delivery Network(CDN), Transport Layer Security (TLS) and Mobile IP. However, these functionality patch-es cannot solve the root problems of the current Internet, while making the overall architecture more and more complexity and bloated[1]. The root causes of the problems are the triple bindings model, namely, control/data binding, resource/location binding and user/network binding [2]. They make the network relatively static and rigid, and fundamentally impede the development of the Internet. The problems related to the triple bindings are shown in figure 1.
In order to decouple the triple bindings,many clean-slate network architectures have emerged [4] [6] [7]. Software-Defined Networks (SDN) is proposed with the separation concept of control plane and data plane[4]. It enables the Internet to become more programmable, manageable, and cost-effective. Information-Centric Networks (ICN)introduces “resource/location separation” to evolve the Internet from host-centric paradigm to content-centric paradigm [6]. By naming information uniquely, ICN aims at providing accessing named information as a principal network service, thus facilitating the efficient and timely delivery of information to users.Additionally, to design a scalable and flexible network architecture, Locator/Identifier Separation Protocol Networks (LISP) decouples user/network binding [7]. LISP sufficiently improves the routing scalability and security of the Internet.
Any of SDN, ICN and LISP decouple one of the triple bindings, they can solve the partial problems of the current Internet. To comprehensively address these problems, Smart Collaborative Identi fier Networks (SINET) is proposed [2] [3]. SINET provides a “three layers” and “two domains” network model to separate the triple bindings completely. The “three layers” are composed of (i) Smart Pervasive Service Layer (L-SPS), (ii) Dynamic Resource Adaptation Layer (L-DRA), and (iii) Collaborative Network Component Layer (L-CNC).The “two domains” consist of (i) Entity Domain (D-EN) and (ii) Behavior Domain (DBE). Based on the “three-layer” and “two-domain” model, SINET dynamically perceives network status and intelligently adopts service requirements, hence, improving the scalability,mobility, security and reliability.
In this paper, we comprehensively introduce SINET and the related research works.
There have been many research efforts on SINET [9] [10] [11] [12] [13] [14] [15]. [9] focused on the great innovation of SINET for 5G communications. It proposed a specific prototype system (SCN-R) to promote efficient and reliable communications in High-Speed Railway (HSR) scenarios. Inspired by SCN-R,Zhang et. al [10] proposed a quite lightweight but effective solution to improve the current Internet experience for HSR scenarios. By integrating SINET techniques and the traditional Internet, a data-driven Link State Prediction(LSP) mechanism for HSR reliable transmission (LSP4HSR) was proposed. LSP4HSR operated in HSR’s on-board routers directly.Abundant simulation results demonstrated that LSP4HSR is able to suf ficiently improve communication quality for HSR communication systems. Zhang et. al [11] applied the concepts of SINET to wireless communication architecture to improve the scalability and flexibility.Zhang et. al [12] aimed at dealing with mobility-caused outdated mappings in SINET. In[13], a set of generalized models for SINET function based collaboration was provided.This work established a fundamental theory for collaboration in SINET, guiding the later researchers to research SINET better. Furthermore, by finding the prominent group with the highest Group Betweenness Centrality (GBC),Guan et. al [14] proposed a GBC-based caching function group selecting algorithm in SINET. This GBC-based algorithm promoted the content delivery in SINET, and improved operability of the network. In addition, Jiang et. al [15] proposed a SINET-based communication architecture. This architecture is a meaningful exploration which can boost the development of both smart grid and SINET.

F ig. 1. The triple bindings and the corresponding problems.
Although lots of very good research papers exist on SINET (e.g., [2], [16] and [17]), there are not a survey paper that comprehensively introduces SINET and its research efforts. In this paper, we present a comprehensive literature survey on SINET. The aim of this survey is to focus on SINET architecture and its state of the art evenly and broadly. We explain the context and introduce the motivation for SINET in Section II. The main design concepts of this novel future Internet architecture are presented in Section III. We explain how SINET differs from the traditional and the other future networks. The concepts underlying SINET is the separation of the triple bindings.Based on the triple bindings, SINET reference model and fundamental principle are discussed. Furthermore, Section IV introduces the design principles and theory in every layer in SINET, presenting how SINET can implement separation of the triple bindings. In Section V, the discussion on ongoing research efforts is expanded, with many aspects including scalability, mobility, security and reliability. Besides, several SINET products are introduced, such as high-speed railway routers and industrial wireless sensor network equipment.Finally, we discuss the challenges of SINET.
II. STATE OF THE ART IN NETWORKS
Recently, there have been increasing research efforts to contribute to solve drawbacks of the traditional Internet. We group these works into two types: (i) evolutionary researches and (ii)clean-slate researches.
2.1 Evolutionary researches
Evolutionary researches focus on patching and enhancing the current Internet, these are two mainstream technologies, namely (i)Software-De fined Networks and (ii) Network Function Virtualization.
(i) Software-Defined Networks (SDN)is an emerging network architecture where the network control plane is separated physically from the forwarding plane [4]. By abstracting the underlying infrastructure hardware for network services, SDN makes network directly programmable and manageable. Its features can be described with the following four pillars:
1) Functionally Separated. The control and data planes are decoupled. In network switches and routers, control functionality is removed and moved to their outside, which make the infrastructure device simple enough.
2) Broadly Flow-based. Forwarding decision is flow-based instead of destination-based.Besides, flow entries can be configured dynamically, which enables unprecedented flexibility.
3) Centrally managed. Network intelligence is logically centralized in software-based SDN controllers, which maintain a global view of the network, hence, simplifying the network deployment and making network management more sophisticatedly and intelligently.
4) Directly programmable. The network is programmable through software applications,which promotes the innovation of network functionalities.
With the separation of control/data binding,SDN improves the programmability of networks [4] [5], however, there are also many new challenges in SDN. First, the resilience of SDN is a challenge [18] [19]. Its resilience relies on not only fault-tolerance in the data plane but also on the high availability of the centralized control plane functions. Second,the scalability of SDN is also a challenge. The control plane brings additional traf fic into network load, hence, being a potential bottleneck.Additionally, for data plane, switches/routers are con figured in real-time by control planes,which also brings extra overheads and delay.In large-scale networks, these overheads and delay of control planes setting up flow table would become intolerable [20]. Third, there are a number of security challenges in SDN due to the central management [21]. Besides,the traditional security threats, SDNs have many security issues which is the specific to SDN architectures, such as exploiting logically centralized controllers, compromising controller leading to compromise the entire network, and development and deployment of malicious applications on controllers.
(ii) Network Function Virtualization(NFV)is a network architecture that utilizes IT virtualization technologies to virtualize network node functions, hence, accelerating the deployment of new network services [22]. It decouples network functions from the underlying hardware infrastructures, and transfers network functions from special hardware appliances to standard IT equipment. NFV offers a new way to design, deploy and manage networking services, its advantages are described as follows:
1) Reduce capital expenditure: reducing the need to purchase purpose-built hardware and supporting pay-as-you-grow models to eliminate wasteful over-provisioning.
2) Reduce operational expenditure: reducing power, cooling and space requirements of network equipment and simplifying the roll out and management of network services.
3) Accelerate service deployments: reducing the time to deploy new network services to support changing business requirements.
4) Deliver agility and flexibility: quickly scaling up or down network services to respond changing demands, supporting innovation by enabling services to be delivered via software on standard hardware.
Although NFV has many attractive advantages, it faces certain challenges which would hinder its deployment at the Internet-scale[22]. First, security attacks will be increased when we implement network functions in a virtualization environment. NFV generates Virtual Network Functions (VNFs) with Virtual Machines (VMs) generated by VM hypervisors. VM hypervisors would bring in new security threats to telecommunications industry,such as unauthorized access and data leakage[23]. Besides, NFV uses APIs to provide programmable orchestration and interaction with its infrastructure, which introduce higher security dangers on VNFs. Second, NFV would degrade network performance. For NFV, it is a key to success that VNFs should provide comparable performance to network functions running on special hardware. However, the performance of VNFs probably is impacted seriously by the virtual environment underlying hardware characteristics including CPU architecture, cache memory size, memory bandwidth. Third, carrier-grade service assurance is a big challenge for NFV. Currently, NFV mostly uses open-source softwares to provide network services. It is dif ficult to provide high availability and reliability due to uneven software performance [24].
2.2 Clean-slate Researches
Unlike evolutionary researches, clean-slate researches concentrate on the clean-slate design of the future architecture. Besides SINET,there are another two widely accepted cleanslate future network architectures, namely, (i)Information-Centric Networks and (ii) Locator/Identi fier Separation Protocol Networks.
(i) Information-Centric Networks (ICN)is a network architecture to evolve the Internet away from a host-centric paradigm to information-centric paradigm [6]. In ICN, uniquely named content is independent from location.The content can be cached and replicated in any caching routers. Hence, ICN facilitates efficient and timely delivery of content, reducing network workloads and user access delay. The concepts and principles of ICN are discussed as follows:
1) Resource Naming: ICN fundamentally decouples resource from location, and names uniquely a chunk of resource, rather than specifying a source-destination hots pair for communications. It uses the receiver-driven resource retrieval ways. Once a request received,the network is responsible for searching the best source that can provide the requested resource using name-based routing mechanism.
2) Resource Delivery: ICN can satisfy an information request not only through locating the original servers, but also using the in-network caching routers. Resource delivery can be efficiently accomplished in network layer,without resorting to add-on proprietary and costly solutions in application layer like the traditional Internet (e.g., CDNs). Meanwhile,ICN supports the aggregation functionality that allows ICN routers to forward users requests only once, enhancing network utilization.
3) Mobility: ICN address host mobility by utilizing publish/subscribe communication model [25] [26]. Users who are interested in information subscribe to it, and then users who offer information publish advertisements for this information. In ICN, publishers involve only announcement of the availability of information to the network. Publication and subscription operations are decoupled in time and space [27], hence, allowing for the efficient mobility support.
ICN can address many emerging requirements of the current Internet, however, it also generates new technological challenges. There are many issues to be addressed and tackled,which include naming, security, routing and caching scalability [28]. As every new born element, ICN cannot be deployed successfully at once, and it still has a long way ahead.
(ii) Locator/Identifier Separation Protocol Networks (LISP)is a network architecture which employs the locator identi fier separation approach to improve the routing scalability[7] [8]. In LISP, the identi fication (identi fier)and the localization (locator) of every terminal is split. The link between identifiers and the Locators is ensured by a mapping system. The advantages of LISP are presented as follows:
1) Routing scalability: different from the traditional Internet, LISP utilizes a separated numbering space for routing locators to assign addresses. Therefore, it allows a high level of aggregation, reducing the number of globally announced prefixes and improving routing scalability [29].
2) Mobility: LISP employs two separate name spaces, namely, locators and identi fiers,and provides a dynamic mapping system between these two spaces. Therefore, the identify can be decoupled from topology, which allows the end-point identifier space to be mobile without the routing that interconnects the Locator space. These enable LISP to have better mobility.
3) Improved traffic Engineering capabilities: by separating ID and locators, traf fic between end points and routing locators can be redistributed by utilizing the identi fier-to-routing-locator mapping systems. Therefore, it can better improve traf fic engineering capabilities.
There are challenges such as mapping system designs and security in LISP. LISP separates IP addresses into two namespaces: Endpoint Identifiers (EIDs), which are assigned to end hosts, and Routing Locators(RLOCs), which are assigned to devices that form the global routing system. Therefore, it is necessary to design a huge identi fier-to-locator mapping system to map identi fiers onto locators, and it would be a critical challenge.Another challenging problem in LISP concerns to security, including the authentication of LISP messages and the authentication of the mapping entries. Although some approaches have come up, which focus on authenticating and authorizing the mapping entries requests,there is not an integrated solution for mapping entries authentication yet. Therefore, LISP still has security problems such as man-in-themiddle attacks.
As mentioned above, the future Internet has become a hot research topic, and there have been many future Internet architectures introduced to address the key issues of the traditional Internet. However, all of the research works are in their infancy yet, there are still the unprecedented challenges which are not addressed.
Besides, these network architectures merely decouple parts of the triple bindings. They cannot solve the problems of the current Internet completely. To completely separate the triple bindings, SINET has emerged. As promising candidate for the future Internet architecture, SINET concentrates on the separation of the triple bindings and aims at addressing the Internet problems better.
III. WHAT IS SMART COLLABORATIVE IDENTIFIER NETWORKS?
SINET is developed from the Identi fier-Based Universal Networks (IUN) [30]. IUN is the primary achievement in our national 973 Program named “Fundamental Research on the Universal Network for Supporting Pervasive Services”. IUN introduces two-layer network model, namely, Network Communication Layer and Service Layer. It can solve perfectly mobility and security problems. Furthermore,to address the other Internet problems such as scalability and energy saving, we propose SINET. It is supported by the second 973 Program “Fundamental Research on Smart Collaborative Network”.
3.1 Decoupling triple bindings
SINET is a novel future network architecture,which completely removes the restriction from the triple bindings, namely control/data binding (c/d binding), resource/location binding (r/l binding) and user/network binding (u/n binding).
To decouple the triple bindings, many future Internet architectures have done lots of research efforts, and many advanced techniques have been available. However, most of future Internet architectures loosen triple bindings partially. The solution situations of separating the triple binding among the leading network architectures can be summarized in Table I.LISP decouples users from access networks using locator/identifier separation (u/n binding) mechanism; ICN separates resource from location (r/l binding) by naming information(content) uniquely and caching information on path; SDN/NFV separate control plane from data transfer to decouple c/d binding. Different from these architectures, SINET aims at providing an overall design to decouple the triple bindings completely. By introducing “three layers” “two domains” model in original, SINET separates the triple bindings thoroughly.Hence it achieves better security, higher mobility and scalability.
3.2 SINET reference model
The “three layers” “two domains” reference model of SINET is foundation to separate the triple bindings. It is shown in figure 2.
The three layers are (i) Smart Pervasive Service Layer (L-SPS), (ii) Dynamic Resource Adaptation Layer (L-DRA), and (iii) Collaborative Network Component Layer (L-CNC).L-SPS is responsible for the naming, registration and service managements. L-DRA manages and organizes network function groups to make an optimal decision and resource allocation. Each function group is composed of a set of network nodes or components with similar functions. These functions include mobility support, security enhancement, in-path caching, and energy saving, etc. L-CNC dispatches network components to carry out the speci fic task such as routing caching and mobility proxy.
The two domains are (i) Entity Domain (DEN) and (ii) Behavior Domain (D-BE). D-EN aims at providing identifiers for the entities such as network services, function groups, and network components. D-BE is responsible for describing properties for the services, functiongroups and network components. It includes service type, service cache and provider signature.
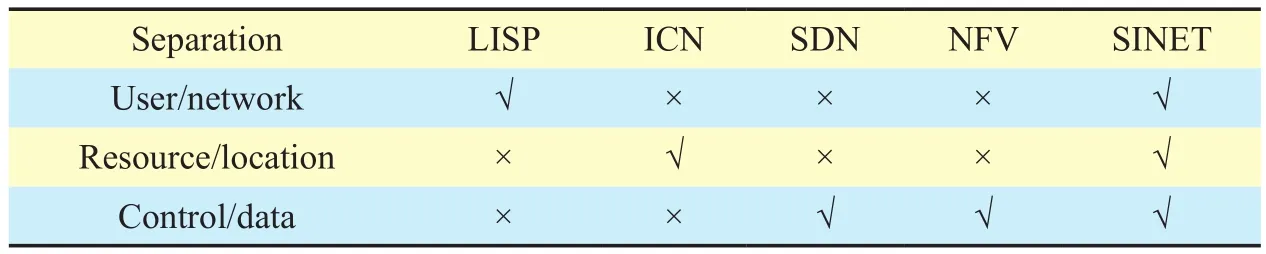
Table I. The comparison of separating the triple bindings (√ stands for “solved”,× means “unsolved”).

Fig. 2. SINET reference model.
3.3 SINET fundamental principle
Figure 3 shows the fundamental principle in SINET, which further promotes separation of the triple bindings.
The autonomic mapping mechanism is a technical way to solve the triple bindings problem. Particularly, “Entity Domain (DEN)” uses Service Identi fier (SID) to mark a service, to separate “resource/location binding”. D-EN employs Function-group Identi fier(FID) to denote a network function group, and Node Identifier (NID) to uniquely identify a network component, hence, decoupling “control/data binding” and “user/network binding”. In “Behavior Domain (D-BE)”, we use Service Behavior Description (SBD), Function-group Behavior Description (FBD) and Node Behavior Description (NBD) to describe the behavior characteristics of SID, FID and NID respectively.
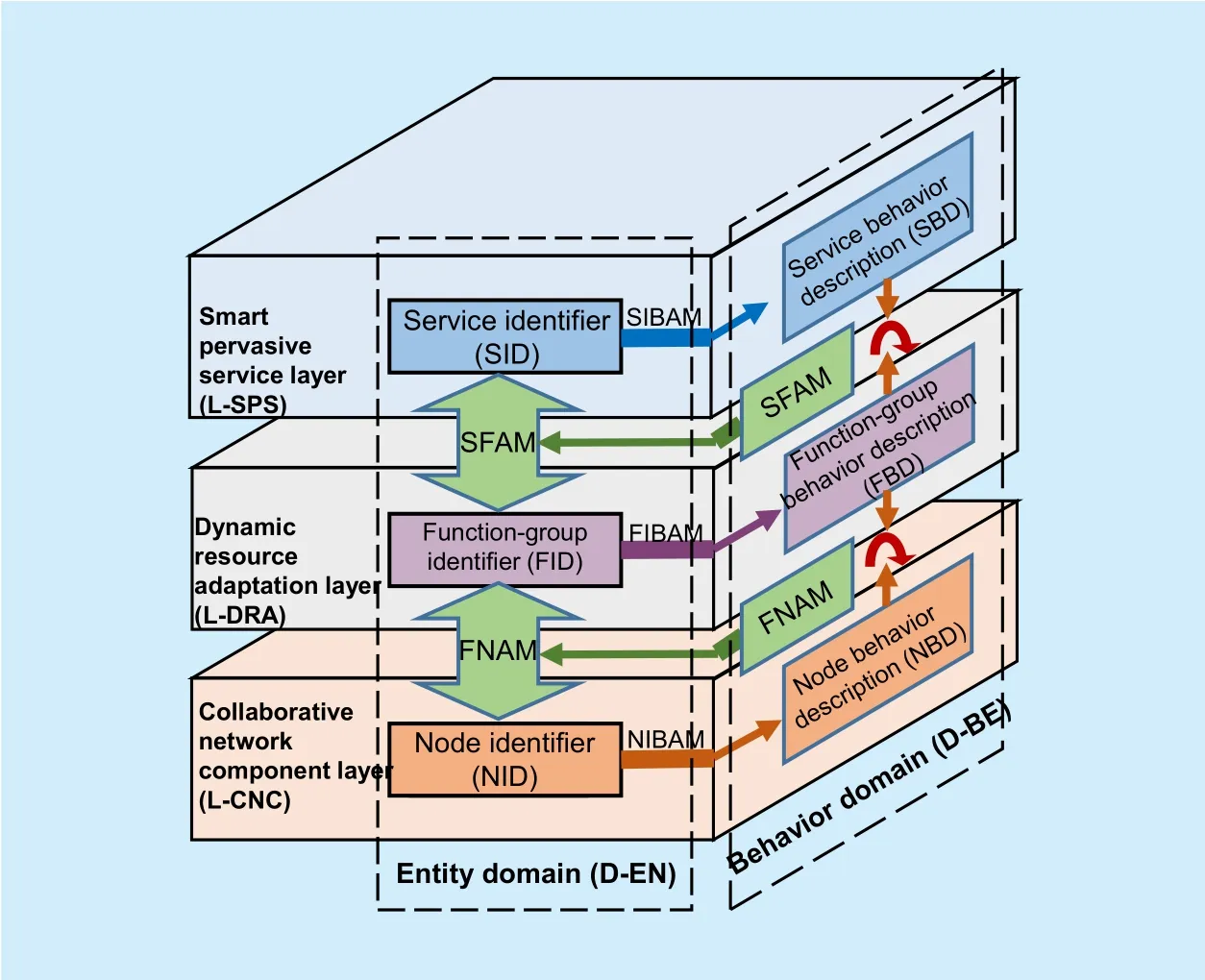
Fig. 3. The fundamental principle in SINET.
To connect the identifiers (SID, FID, and NID) and the behavior descriptions (SBD,FBD, and NBD) and maximize resource utilization, the efficient identi fier-behavior autonomic mapping mechanisms are designed and integrated in SINET. They are composed of Service Identifier-Behavior Autonomic Mapping (SIBAM), Function-group Identi fier-Behavior Autonomic Mapping (FIBAM), and Node Identi fier-Behavior Autonomic Mapping(NIBAM). They can be all implemented by current classic algorithms.
To connect Smart Pervasive Service Layer and Dynamic Resource Adaptation Layer, a Service-Function Autonomic Mapping mechanism (SFAM) is proposed. SFAM aims to finish the mapping between SIDs and FIDs according to the correlation of the SBDs and FBDs. Based on the SBDs and FBDs, SFAM selects network function groups by matching the service requirements with the function-groups. After that, the FIBAM further maps the selected FBD to the proper FID.
To connect Dynamic Resource Adaptation Layer and Collaborative Network Component Layer, Function-Node Autonomic Mapping(FNAM) is designed. FNAM aims to establish a relationship between FIDs and NIDs, according to the correlation of FBDs and NBDs.With FNAM, network nodes are aggregated into various function groups according to their behavior closeness, which can be calculated by fuzzy clustering algorithms. The NIBAM further maps the selected NBDs to the proper NIDs. Then these NIDs build a network function group with a FID to finish a special task.
Based on the “three layers” “two domains”model and the fundamental principle, SINET decouples perfectly the triple bindings. Furthermore, the behavior matching, behavior clustering and network complex behavior game are adopted to globally acquire network status and dynamically orchestrate network resource. Therefore, it can meet intelligently service requirement, increase the utilization of network resources, and reduce the consumption of energy.
IV. SMART COLLABORATIVE IDENTIFIER NETWORKS: DESIGN PRINCIPLE
This section introduces the design principles and theory in every SINET layer, presenting how SINET can implement separation of the triple bindings and solve the problem of the current Internet.
4.1 Principle of smart pervasive service layer
Smart Pervasive Service Layer (L-SPS) is responsible for providing service management,service acquisition and adaptive connection management [31]. To efficiently implement these tasks, we introduce two modules, namely, Virtual Service Module (VSM) and Virtual Connection Module (VCM) into L-SPS.Meanwhile, Service Identi fier (SID) is used to uniformly describe the service resource information. Connection Identi fier (CID) is utilized to identify the process of a user obtaining a service.
The model of L-SPS in SINET is shown in figure 4. First, VSM maintains SIDs, which uniformly identi fies various services in different network, hence, achieving the uni fied control and management of services. VCM maintains CIDs to manage the session connections for communication processes. CID is decoupled from service locations, and not changed during the entire communication process.Therefore, SINET is able to provide stable and reliable mobile communications. Second, SID Resolution-Mapping system (SID-RM) and CID Resolution-Mapping system (CID-RM)provide flexible resolution- mapping mechanism for network connections and transfer paths. Thus, SINET is able to satisfy pervasive service for various resource types and access methods. Third, CID provides L-SPS with a separated name space. It is separated from access locations, improving SINET scalability and security.

SID is a key factor to implement scalability,flexibility and security of SINET. Therefore,SID should be defined with the three pillars.First, SID space should be scalable, which means that SID can not only describe various current services, but also describe increasingly emerging services. Second, SID should be flexible. Network services can generate SID by themselves, which is not impacted by time and location. SID should provide friendly service interfaces consistently. Third, SID should be secure. SID should represent network service uniquely, providing insurance for services acquisition in SINET. Therefore, SINET employs a consistent Distributed Hash Table(DHT) algorithm to generate SID [41], the generation function of SID is defined by the formula (1):
where Pkey denotes the Public Key announced by a network service publisher, Name is the name of a network service. Besides, Abstract and Content, which are optional parameters,stand for the abstract information and content of a network service respectively.
CID is separated from a node location (denoted by Routing IDentifier), which enables SINET to efficiently support the mobility of nodes. When a service receiver requests a service provider, both the receiver and provider generate a CID, and the two tuple consisting of these two CIDs uniquely identi fies the service connection. Let zidenote the CID of the i-th connection, Z denote a set of CIDs. Theoretically, Z={z1, z2,...zm,...} is an in finite set,where m∈{1,2,...}. Therefore, we obtain the CID of the i-th connection as follows:
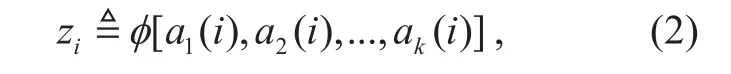
where ak( i ) is the k-th attribute of the i-th connection; φ(x) is the CID-generating func-tion (k∈{1,2,...}).
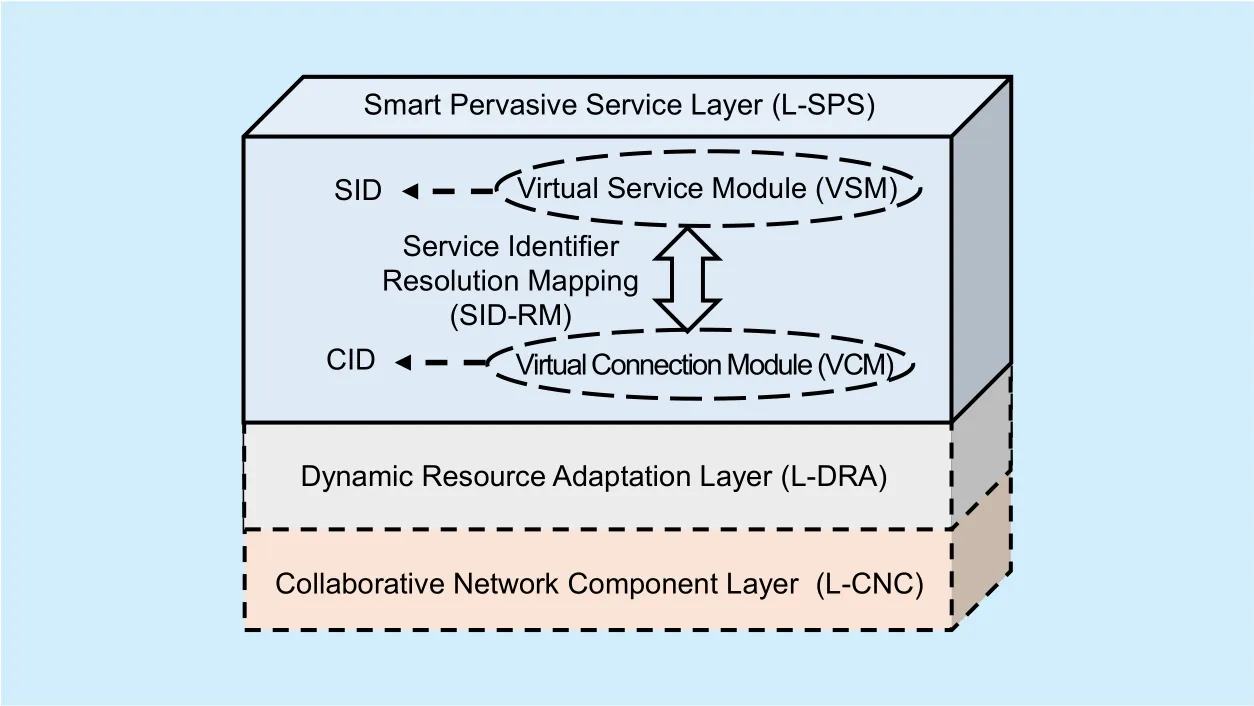
Fig. 4. Model of smart pervasive service layer in SINET.
SID-RM is designed to keep the relationships between SID and CID. Let Si( t ) denote all the services that node i obtains at the time t. Assume that Cm(t ) denotes CID set which is established for the on-going m-th service at the time t. Therefore, the resolution-mapping mechanism can be expressed as the formula(3):

where M stands for the number of SIDs at the time t, I represents the number of nodes which are accessing the service at the time t, Φ(x)is the algorithm that implements the mapping from SID space to CID space. To implement the transformation from CID to SID, we can employ the inverse mapping function Φ-1(x).
SID-RM is designed to provide a service-oriented data delivery efficiently. In the traditional Internet, applications are bounded with speci fic network addresses and protocols ports tightly. In SINET, it employs SID to name services uniquely, separating a service from network connection and utilizing SIDRM to map SID and CID flexibly. Therefore,SINET makes services independent from both network addresses and transport protocols,hence, making the Internet more scalable and flexible.
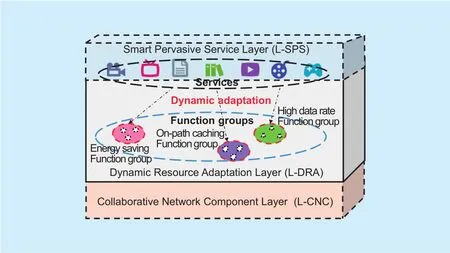
Fig. 5. Model of dynamic resour ce adaptation layer in SINET.
4.2 Principle of dynamic resource adaptation layer
Dynamic Resource Adaptation Layer (L-DRA)is designed to manage and orchestrate network function groups to dynamically satisfy services requirements. L-DRA employs Function group IDenti fier (FID) to represent a network function group, which is composed of many network components with similar behaviors.In particular, CID can be treated as a case of FID. The connection represented by CID is static for each communication process [32],while FID is adaptively and dynamically generated. FID is de fined as follows:

where FTdenotes topology behavior, FPdenotes performance behavior, FFis functionality behavior, and ϕ(x) is the generation function of FID.
On the basis of various Function Behavior Descriptions (FBD), network function groups can be divided into different classes. As shown in figure 5, there are different function groups which are dynamically orchestrated to provide different qualities services, such as energy saving [33], on-path caching [34] [35][36], load balancing [37] and high-data-rate function groups. FBD mainly contains three aspects, namely, topology, performance and functionality. Take functionality descriptions,for example. According to the properties of functionality, network functions can be divided into several groups, including servers, storages, sensors and switches. Besides, network function groups are scalable: they can increase with the increasing FBD of emerging network devices. FBD can be de fined as by the formula(5):
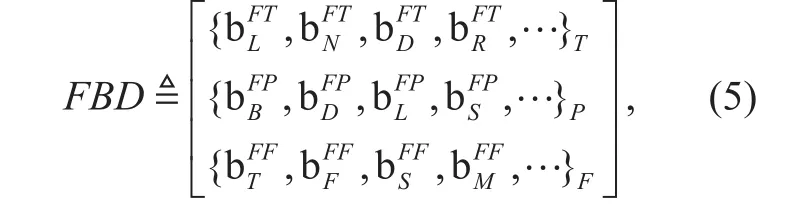
where T, P and F denote topology behavior, performance behavior and functionality behavior, respectively. Topology behavior includes the location, the number of components, the components distribution,and the neighbouring function group relations, etc. Performance behavior includes the bandwidth, the delay, the packet loss, and the stability, etc. Functionality behavior includes the type, the function, the security leveland the mobility, etc.
We further focus on the model of L-DRA which is shown in figure 5. L-DRA is in the middle layer between L-SPS and L-CNC. It is responsible for analysing service demands from the upper layer L-SPS and perceiving the status of network resources from the lower layer L-CNC. In L-DRA, the entities in the Entity Domain are created, based on the Behavior Domain decisions, which separates the control/data binding. According to various service demands, L-DRA controls and orchestrates different network components to form optimal network function groups to fulfil the needs of various services. With L-DRA, we can easily implement the dif ficult problems in the traditional Internet, such as co flow-aware network optimizations for data centers [38]and minimizing average coflow completion time [39]. It enables the manageability and flexibility of the Internet, and suf ficiently improves the utilization of network resources and the quality of services.
4.3 Principle of collaborative network component layer
Collaborative Network Component Layer(L-CNC) is responsible for uni fied access for terminals and global routing for packets.
Figure 6 presents the model of Collaborative Network Component Layer (L-CNC) in SINET. In L-CNC, there are two virtual modules, namely, Virtual Access Module (VAM)and Virtual Backbone Module (VBM). VAM introduces Access IDenti fier (AID) to identify network components in the access network.VBM employs Routing IDentifier (RID) to represent the network components in the core network. Both AID and RID belong to NID in SINET. They identify the network components which reside in access networks and core networks, respectively. These network components can be aggregated to different network function groups identified by FID. Besides,AIDs and RIDs can map to each other, and the relationships between AIDs and RIDs are managed by the Access IDenti fier Resolution Mapping (AID-RM).
AID is a unique identi fier which denote the terminal in the access network. The AID of a terminal remains unchanged even if its location is changed. Each terminal can be allocated one or more globally unique AIDs. Using AIDs, any terminals in any network all can access each other with a uniform way. AID provides a novel solution for supporting various heterogeneous networks, including ground mobile networks, fixed networks and satellite networks. It improves the scalability of networks and extends services scope and variety.
AID can be formulated. Let X denote a set of AIDs, and Xirepresent a type of terminal.Assume that the AID of the terminal n with a type i is denoted as Xi( n ). Thus Xi( n) can be obtained as the following formula:

where ak( n ) denotes the k-th property of terminal n (k∈{1,2,...}), and φi(x) is the AID-generating function that is related to i.
Based on the formula (6), with the presentation of all elements, we can further derive the formula (7):
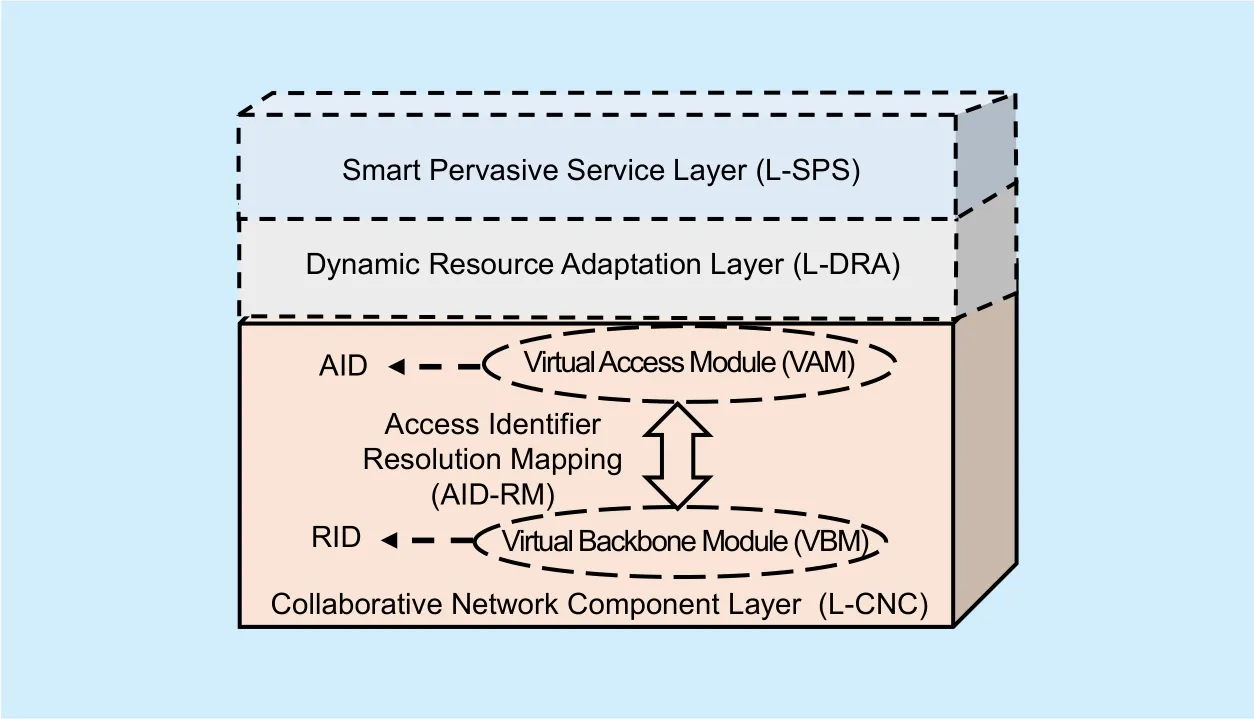
Fig. 6. Model of collaborative network component layer in SINET.
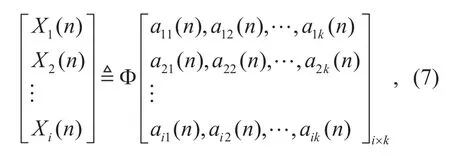
where Φ(x) is the general description of φi(x).
On the basis of the preceding descriptions,we can find that AID can be described by both plat structures or hierarchical structures. In practice, we can even use the IPv4 or IPv6 address format to represent AID, which provides a friendly transitional scheme from the traditional Internet to SINET.
RID is the unique identifier for the core network equipment. It is used for packets addressing, routing and forwarding in the core network. When packets are transferred from an access network to the core network, the source AIDs of them are replaced with the internal RIDs of the access network. On the contrast,when packets enter an access network from the core network, their RIDs are mapping to the corresponding AIDs.
We now formulate the RID. Let Z denote the set of RID, which can be divided into many subsets Zi. They satisfy the following relation formula: A=aRb

Additionally, Zican be derived by the formula (8):

where pi( z ) is the k-th characteristic of element z (k∈{1,2,...}), and ϕ(x) is the RID-generating function in set Zi.
For compatibility with the traditional Internet, RID can also be designed with IPv4 or IPv6 address format. However, note that using IP address as both RID and AID at the same time is forbidden, since RID and AID belong to different name spaces.
AID-RM is designed to maintain the mapping relationships between AIDs and RIDs[40] [41]. Let Q denote the number of access locations at the time t. On the basis of formula(6) and (8), the AID-RM can be expressed as the formula (9):

where q∈[1,Q], Ω(x) is the AID-RM function which is responsible for mapping AID space to RID space. To realize the transformation from RID to AID The inverse functionΩ-1(x) is utilized.
AID-RM decouples the user/network binding. It splits identi fiers from locators, hence, it can address several current Internet problems,such as poor scalability and unsupported mobility. With the mapping mechanism, access networks are insulated from core networks,and users’ privacy information can be protected. Besides, during the mapping process, we introduce an authentication mechanism to verify mapping legitimacy, further enhancing the security of the Internet.
V. ONGOING RESEARCH EFFORTS AND CHALLENGES
In this section, we discuss ongoing research efforts on SINET, with aspects including scalability, mobility, security and reliability. Speci fically, we present parts of SINET products which are applied in various areas (e.g., Telecom networks, high-speed railway networks,and industrial wireless sensor networks) to solve the specific issues. Finally, we outline the main challenges that remain unresolved for researchers interested in SINET.
5.1 Scalability
The traditional Internet is facing serious routing scalability problems. As a novel future Internet architecture, SINET creates several new rules to support scalable routing. First,it adopts the concept of “user/network separation” to eliminate the semantic overload of the addresses of the current Internet, hence,reducing the number of routing entries in the core routers. Second, SINET employs intro-/inter-domain routing separation to further enhance the routing scalability [42] [43].
There have been many inter-domain identifier-based scalable routing mechanisms in SINET, such as a path family-based routing mechanism and a source identifier routing mechanism. Take the path family-based routing mechanism for example. The path family-based routing mechanism depends on network component family, named path family. Path family is represented with Path family IDenti fier (PID). The path family is a collection of network components, which forms the transmission paths among different domains.Therefore, PID can be regarded as a type of FID. For a path between two adjacent domains, both the number of paths and the PID should be negotiated by these two domains,and the PID must be unique. The path family-based routing mechanism couples service location and inter-domain routing, while decouples them from forwarding. Its scalability is determined by two factors, the routing table size and the number of SIDs whose uppermost domain must be able to handle. Since the domains are not limited with any routing mechanisms, the size of the intra-domain routing table is well under control. Besides,SINET caches contents on all nodes within the domain, and then the number of messages among inter-domains is reduced sufficiently.Therefore, the routing mechanism which is family-based has a good scalability in SINET.
5.2 Mobility
The traditional Internet is originally proposed for static hosts. Its IP address carries two information, including both identifiers and locators. The dual roles of the IP address make it difficult to support mobility. SINET decomposes IP addresses into AIDs and RIDs,and then employs mapping systems to support hosts mobility and network mobility. Based on this design, a Network-based Mobility Management (NMM) scheme is proposed in SINET.
The Network-based Mobility Management (NMM) is able to support intra-domain mobility and inter-domain mobility. The intra-domain mobility means that Mobile Nodes(MNs) move from a Mobile Router (MR) to another one in the same Internet Service Provider (ISP) domains. Inter-domain mobility means that MNs move from one ISP domain to another one. For intra-domain mobility, it can be supported by local mobility mechanisms like CIP [44] and Hawaii [45]. It is simple and its handoff delay is on the order of milliseconds [46], since it does not cause the remapping between AID and RID. For inter-domain mobility, NMM utilizes a separating-mapping mechanism to support its mobility. Owing to the separation of AID and RID, when a MN changes its location, the AID remains unchanged. The variation of the access locations only changes the mapping relationship between the AID and the RID in the AID-RM systems. SINET makes the movement of MN transparent to network link. Besides, the new mapping relationship between AID and RID can be generated in a very short time using distributed AID-RM systems. Therefore, the connection established before movement is not interrupted.

Fig. 7. SINET applied in a high-speed railway.
A prototype s ystem (SCN-R) [9] has been developed and tested in a high-speed railway environment, further verifying the mobility of SINET. As shown in figure 7, by combining SINET with our advanced techniques [47][48] [49], we design a SINET Wireless Multilink Mobile Router (BJTU-SR-I) for highspeed railway network. Specifically, SCN-R is able to perceive the service requirements in L-SPS, such as service types, data rate and bandwidth. In L-DRA, SCN-R features the management of many specific network function groups, such as mobility-support function group and smart-access function group. Furthermore, SCN-R can adopt different wireless access components, including EVDO network for China Telecom, WCDMA network for China Unicom and TD-LTE network for China Mobile. All of these components can works intelligently and collaboratively. Therefore,SCN-R has a good support for efficient and reliable communications in high-speed mobile railway (the average speed is 250 km/h).
5.3 Security
Cyber-attacks against government units, financial institutions and research institutions such as Distributed Denial of Service (DDoS)attacks and worms, are becoming one of the main concerns of agencies around the world.These attacks are able to damage a nation’s wide network infrastructure. Therefore, identifying and preventing cyber-attacks are critical challenges in the traditional Internet.
Owing to the danger of cyber-attacks, security are top priorities in SINET. There have been many security enhancement solutions in SINET, such as an anomaly detection response mechanism (ADRM), a DDoS-preventing mechanism and a mitigation mechanism for worm propagation.
Based on mapping requests in SINET, an Anomaly Detection Response Mechanism(ADRM) is proposed. ADRM identifies and diagnoses some anomalous network behaviors by judging the mapping request traf fic anomaly. In SINET, when a host want to establish a connection with another one, the corresponding Access Switching Router (ASR) must request an IDenti fier Mapping System (IDMS)for identifier mapping. The ADRM is implemented in each IDMS to detect and diagnose the anomaly mapping between AID and RID.Besides, a celebrated cumulative sum algorithm is proposed to raise an anomaly alarm in real time. Once the alarm generated, the IDMS will control and even drop the attack traf fic.
Based on scalable identifier-separating mapping mechanism, SINET proposes a DDoS-preventing mechanism [50]. In practice, to launch a DDoS attack, a cyber attacker need to recruit enormous zombies in advance,and then control them to attack a certain victim by sending attack commands. To recruit dozens of zombies, an cyber attacker would use attacker tools to find vulnerable hosts, and then send packets to hosts to check whether they are vulnerable. However, with the scalable identi fier-separating mapping mechanism,the attacker’s ASR can only find the RIDs of these hosts which provide services to users(these hosts only account for to less than 1%of total hosts). As to those hosts that just serve as users, it cannot know their RIDs and thus it have no idea whether they are vulnerable, not to mention how to send control commands.Besides, in SINET, since packets sent by cyber attackers cannot be forwarded to IDMSs,it is impossible that attackers try to attack the IDMSs. Therefore, with SINET identi fier separation mechanism, it is convenient to prevent the DDoS attacks.
Besides, the design principle of SINET can mitigate worm propagation [51]. We model the mitigation of worm propagation both in the tradition network and the SINET future network, and analyze the mitigation of worm propagation with typical epidemiology model[52] and discrete time model [53]. There are three aspects to demonstrate the security of SINET, namely, address semantics, address space and mapping delay. For address semantics, SINET resolves the dual semantics of the IP address into RID and AID. RID can be sedulously concealed. AID is flat structure, which make it more dif ficult for worms to surmise the AID space since they don’t know the corresponding addressing law. For address space, the address space of SINET is composed of AID and RID. RID does not represent the identifier of any hosts. Therefore, it is meaningless for worms to scan RID spaces. As to mapping delay, when worms try to scan an AID, the corresponding ASR must request the mapping information for the AID from IDMSs. The request delay would alleviate worm propagation in a manner. Therefore,SINET is more resistant to worm propagation than the traditional Internet.
We have developed SINET routers (BJTUSR-II) for security and mobility application scenarios. As shown in figure 8, SINET equipment has been applied in network emergency system in government and police vehicles direction dispatching system. Comprehensive secure testing and practice have proved the security of SINET.
5.4 Reliability
The current Internet is a best-effort network where packet loss, variable delays and bandwidth fluctuation frequently occur during data delivery. Thus it is dif ficult for the current Internet to transmit real-time data with high reliability and great quality of service assurance.SINET adopts the concept of the “control/data separation”, employing a new logically centralized control structure in L-DRA. The logically centralized controller timely collect the status of network resource in L-CNC, dynamically orchestrate and schedule these resource,hence, providing the high-reliability services.
A high-reliability Smart Wireless Sensor Networks system (Smart-IWSN) has been designed and implemented as shown in figure 9.The Smart-IWSN has been applied to multiple Industrial Wireless Sensor Networks (IWSNs).In these IWSNs, the most crucial issues is how to obtain high-reliability. To meet this requirement, Smart-IWSN optimizes multiple SINET techniques in three layers. In L-CNC, integrated with the traditional leading techniques [54][55], a physical channel resource feedback mechanism and a comprehensive cross-layer design is implemented in Smart-IWSN. These designs enable Smart-IWSN to collect the status of network resources in different protocol layers, hence, scheduling them in real time. In L-DRA, the time function group is generated to dynamically orchestrate network resources to assure high-reliability link. In L-SPS, an end-to-end acknowledgement mechanism is proposed to further guarantee high-reliability services.
5. 5 Challenges

Fig. 8. SINET applied in network emergency system and police v ehicles direction dispatching system.

Fig. 9. SINET applied in Industrial Wireless Sensor Networks.
Currently, SINET has been applied to many private networks, including high-speed rail-way networks, industrial wireless sensor networks and emergency networks. Many key issues in SINET have been discussed and many advanced technologies have been available.However, as an emerging future Internet architecture, there are many challenges in SINET yet, and it still has a long way ahead. These challenges is outlined as follows:
1) How to intelligently schedule and manage function groups and network components is a challenges. In practical, a function group usually performs multiple tasks, and a network component belongs to multiple function groups and plays different roles in parallel.Therefore, it is complex task to intelligently schedule them.
2) How to deploy SINET at large-scale is a challenge. First, SINET introduces in-network caching mechanism to improve network performance. However, how to cache content at high-speed and large-capacity is not investigated thoroughly yet, and it still has a long way ahead. Second, the current Internet is occupied and managed by multiple stakeholders,it is dif ficult to replace old devices with new generation ones due to social interest. Therefore, how to reuse these existing devices in SINET is an important research subject.
3) How to design efficient mapping mechanisms is a challenge. SINET requires the delay of mapping operations as short as possible.However, the accurate and intelligent mapping algorithms usually have a large time and space complexity. Therefore, how to make an optimal trade-off between latency and intelligence is a formidable task.
VI. CONCLUSION
In this paper, we provide a comprehensive survey of the SINET research landscape. We discuss the problems of the current Internet,and present the state of the art in the future Internet. Several candidate technologies of the future Internet including SDN, NFV, ICN and LISP are discussed. They all provide a good solution for a part of issues of the current Internet. To decouple the triple bindings and solve the problems of the Internet completely,the SINET is proposed. We first present the reference model and fundamental concepts of SINET, explaining what is SINET. Furthermore, we describe the design principles and theory in each SINET layer, including Smart Pervasive Service Layer, Dynamic Resource Adaptation Layer and Collaborative Network Component Layer. These principles and theory further explain how SINET can decouple the triple bindings and solve the Internet problems. They have a great signi ficance to guide the later researchers to explore the research on SINET. There have been many research works on SINET. We present a part of these works in many aspects, including scalability, mobility,security and reliability. Speci fically, we present the SINET which are applied to multiple fields, such as high-speed railway networks,industrial wireless sensor networks and Telecom networks. These applications demonstrate that SINET is a promising fertile research field, and it has a great potential for addressing the current problems of the Internet. Finally,we outline the main challenges that remain unresolved for researchers interested in SINET.
ACKNOWLEDGEMENT
This work is supported by the National Natural Science Foundation of China (NSFC) under Grant No.61232017, and the Fundamental Research Funds for the Central Universities under Grant NO. 2017YJS032.
[1] M. Handley, “Why the internet only just works,”BT Technology J., vol. 24, no. 3, 2006, pp. 119–129.
[2] H. Zhang, W. Quan, H. Chao et al., “Smart identifier network: a collaborative architecture for the future internet,” IEEE network, vol. 30, no. 3,2016, pp. 46-51.
[3] H. Zhang, W. Su, W. Quan, “Smart Collaborative Identi fier Network: A Promising Design for Future Internet,” Springer, 2016.
[4] D. Kreutz, F. Ramos et al., “Software-defined networking: a comprehensive survey,” Proc. of the IEEE, vol. 103, no. 1, 2015, pp. 14-76.
[5] Bo L, Ming C, Chao H, et al. Optimizing the resource utilization of datacenter networks with OpenFlow[J]. China Communications, 2016,13(3): 1-11.
[6] G. Xylomenos, C. Ververidis et al., “A survey of information-centric networking research,” IEEE Communications Surveys & Tutorials, vol. 16,no. 2, 2014, pp. 1024-1049.
[7] W. Ramírez, X. Masip-Bruin et al., “A survey and taxonomy of ID/Locator Split Architectures,”Computer Networks, vol. 60, 2014, pp. 13-33.
[8] B. Feng et al., “Locator/Identi fier Split Networking: A Promising Future Internet Architecture,”IEEE Communications Surveys and Tutorials, vol.19, no. 4, 2017, pp. 2927-2948.
[9] H. Zhang, P. Dong, W. Quan et al., “Promoting efficient communications for high-speed railway using smart collaborative networking,” IEEE Wireless Communications, vol. 22, no. 6, 2015,pp. 92-97.
[10] H. Zhang, W. Quan, J. Song et al., “Link state prediction-based reliable transmission for highspeed railway networks,” IEEE Transactions on Vehicular Technology, vol. 65, no.12, 2016, pp.9617-9629.
[11] H. Zhang, P. Dong, S. Yu et al., “A scalable and smart hierarchical wireless communication architecture based on network/user separation,”IEEE Wireless Communications, vol. 24, no. 1,2017, pp. 18-24.
[12] H. Zhang, H. Luo, H. Chao, “Dealing with mobility-caused outdated mappings in networks with identi fier/locator separation,” IEEE Transactions on Emerging Topics in Computing, vol. 4, no. 2,2016, pp. 199-213.
[13] W. Quan, Z. Jiang, F. Song et al., “Generalized model of function based collaboration in smart identifier network,” Proc. IEEE Telecommunication Networks and Applications Conference(ITNAC), 2015.
[14] J. Guan, Z. Yan, S. Yao et al., “GBC-based caching function group selection algorithm for SINET,”Journal of Network and Computer Applications,vol. 85, 2017, pp. 56-63.
[15] Z. Jiang, W. Quan, J. Guan et al., “A SINET-based communication architecture for smart grid,”Proc. IEEE Telecommunication Networks and Applications Conference (ITNAC), 2015.
[16] H. Zhang, H. Luo, “Fundamental research on theories of smart and cooperative networks,”Acta Electronica Sinica, vol. 41, no. 7, 2013, pp.1249-1254.
[17] H. Zhang, “Smart collaboration network system and applications,” Journal of Beijing Jiaotong University, vol. 40, no. 4, 2016, pp. 60-64.
[18] M. Desai and T. Nandagopal, “Coping with link failures in centralized control plane architectures,” Proc. Communication Systems and Networks (COMSNETS), 2010 Second International Conference on IEEE, 2010, pp. 1–10.
[19] H. Kim, J. Santos et al., “Coronet: fault tolerance for software defined networks,” Proc. Network Protocols (ICNP), 20th IEEE International Conference, 2012, pp. 1-2.
[20] T. Benson, A. Akella, and D. Maltz, “Network traffic characteristics of data centers in the wild,” Proc. of the 10th ACM SIGCOMM Conference on Internet Measurement, New York, USA,2010, pp. 267–280.
[21] S. Scott-Hayward, G. O’Callaghan and S. Sezer,“SDN security: a survey,” Proc. Future Networks and Services (SDN4FNS), 2013, pp. 1-7.
[22] H. Hawilo, A. Shami et al., “NFV: state of the art,challenges, and implementation in next generation mobile networks (vEPC),” IEEE Network, vol.28, on. 6, 2014, pp. 13-26.
[23] V. Ashktorab, T. Seyed, “Security threats and counter- measures in cloud computing,” International Journal of Applications and Innovation in Engineering and Management (IJAIEM), Vol. 1,No. 2, 2012, pp. 234-245.
[24] T. Taleb, M. Corici, et al., “EASE: EPC as a Service to Ease Mobile Core Network,” IEEE Network,vol. 29, no. 2, 2015, pp. 78-88.
[25] T. Eugster, A. Felber et al., “The many faces of publish/subscribe,” ACM Computing Surveys,vol. 35, no. 2, 2003, pp.114–131.
[26] B. Feng et al., “Mobility Support in Named Data Networking: A Survey,” EURASIP Journal on Wireless Communications and Networking, vol.2016, no. 220, 2016, pp. 1-9.
[27] Y. Huang and H. Garcia-Molina, “Publish/subscribe in a mobile environment,” Wireless Networks, vol. 10, no. 6, 2004, pp. 643–652.
[28] A. Vasilakos, Z. Li et al., “Information centric network: Research challenges and opportunities,”Journal of Network and Computer Applications,vol. 52, 2015, pp. 1-10.
[29] B. Quoitin, L. Iannone et al., “Evaluating the benefits of the locator/identifier separation,”Proc. of 2nd ACM/IEEE international workshop on Mobility in the evolving internet architecture,2007.
[30] H. Zhang, W. Su, “Fundamental Research on the Architecture of New Network: Universal Network and Pervasive Services,” Acta Electronica Sinica, vol. 35, no. 4, 2007, pp. 593-598.
[31] W. Su, J. Chen et al., “Research on the service mechanisms in smart and cooperative networks”, Acta Electronica Sinica, vol. 41, no. 7,2013, pp. 1255-1260.
[32] H. Luo, H. Zhang, M. Zukerman et al., “An incrementally deployable network architecture to support both data-centric and host-centric services,” IEEE Network, vol. 28, no. 4, 2014, pp.58-65.
[33] J. Tian, W. Su and J. Chen, “Analysing and studying energy consumption of smart and cooperation network,” Computer Application and software, vol. 32, no. 5, 2015, pp. 136-140.
[34] M. Zhang, H. Luo, H. Zhang, “A survey of caching mechanisms in information-centric networking,” IEEE Communications Surveys &Tutorials, vol.17, no. 3, 2015, pp. 1473-1499.
[35] B. Feng et al., “Cache-Filter: a cache permission policy for information-centric networking,” KSII Transactions on Internet and Information Systems, vol. 9, no. 12, 2015, pp. 4912-4933.
[36] B. Feng et al., “A popularity-based cache consistency mechanism for information-centric networking,” Proc. IEEE Global Communications Conference (GLOBECOM), pp. 1-6, 2016.
[37] R. Jia, S. Gao et al., “Traffic matrix-based load balancing routing in flow-based smart identi fier network,” Journal on Communications, vol. 37,no. 4, 2016, pp. 128-138.
[38] Y. Zhao, K. Chen, W. Bai et al., “Rapier: integrating routing and scheduling for coflow-aware data center networks,” Proc. IEEE INFOCOM,2015.
[39] S. Luo, H. Yu, Y. Zhao et al., “Minimizing average co flow completion time with decentralized scheduling,” Proc. IEEE ICC, 2015.
[40] H. Luo, H. Zhang, C. Qiao, “Optimal cache timeout for identifier-to-locator mappings with handovers,” IEEE Transactions on Network and Service Management, vol. 10, no. 2, 2013, pp.204-217.
[41] H. Luo, Y. Qin, H. Zhang, “A DHT-based identi fier-to-locator mapping approach for a scalable Internet,” IEEE Transactions on Parallel and Distributed Systems, vol. 20, no. 12, 2009, pp. 1790-1802.
[42] S. Gao, H. Wang et al., “Research on cooperation mechanisms of smart network components,” Acta Electronica Sinica, vol. 41, no. 7,2013, pp. 1261-1267.
[43] M. Zhang, C. Xu et al., “Adaptive allocation routing scheme for smart and cooperative networks,” Acta Electronica Sinica, vol. 43, no. 7,2015, pp. 1249-1256.
[44] D. Johnson, C. Perkins, J. Arkko, “Mobility support in IPv6,” RFC 3775. http://www.ietf.org/rfc/rfc3775.txt, accessed at Jun 2004.
[45] N. Nakajima, A. Dutta, S. Das, “Schulzrinne H(2003) and measurement for SIP based mobility in IPv6,” Proc. IEEE ICC, 2003.
[46] R. Koodli, “IP address location privacy and mobile IPv6: Problem Statement,” RFC 4882.http://datatracker.ietf.org/doc/rfc4882/, accessed at May 2007.
[47] J. Wu, C. Yuen, B. Cheng et al., “Goodput-aware load distribution for real-time traきc over multipath networks,” IEEE Transactions on Parallel and Distributed Systems, vol. 26, no. 8, 2015, pp.2286-2299.
[48] J. Wu, B. Cheng, C. Yuen et al., “Distortion-aware concurrent multipath transfer for mobile video streaming in heterogeneous wireless networks,”IEEE Transactions on Mobile Computing, vol. 14,no. 4, 2015, pp. 688-701.
[49] C. Xu, Z. Li, L. Zhong et al., “CMT-NC: improving the concurrent multipath transfer performance using network coding in wireless networks,”IEEE Transactions on Vehicular Technology, vol.65, no. 3, 2016, pp. 1735-1751.
[50] D. Huang, D. Yang, H. Zhang et al., “Efficient dos-limiting support by indirect mapping in networks with locator/identifier separation,”Journal of Networks, vol. 8, no. 1, 2013, pp. 92-99.
[51] M. Wan, Y. Liu, J. Tang et al., “Locator/identi fier separation: comparison and analysis on the mitigation of worm propagation,” International Journal of Computational Intelligence Systems,vol. 5, no. 5, 2012, pp. 868-877.
[52] J. Frauenthal, “Mathematical modelling in epidemiology,” Springer, 1980.
[53] Z. Chen, L. Gao, K. Kwiaty, “Modelling the spread of active worms,” Proc. the 22nd annual joint conference of the IEEE computer and communications, 2003.
[54] C. Xu, Z. Li, J. Li et al., “Cross-layer fairness-driven concurrent multipath video delivery over heterogeneous wireless networks,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 25, no. 7, 2015, pp. 1175-1189.
[55] X. Zhang, S. Wang, Y. Zhao et al., “Multi-objective optimization for green network routing in game theoretical perspective,” IEEE Journal on Selected Areas in Communications, vol. 33, no.12, 2015, pp. 2801-2814.
杂志排行
China Communications的其它文章
- Coordinated Resource Allocation for Satellite-Terrestrial Coexistence Based on Radio Maps
- Spectral Eきciency and Power Allocation for Mixed-ADC Massive MIMO System
- Impact of Phase Noise on TDMS Based Calibration for Spaceborne Multi-Beam Antennas
- A Novel Roll Compensation Method for Two-Axis Transportable Satellite Antennas
- Heuristic Solutions of Virtual Network Embedding: A Survey
- Stochastic Dynamic Modeling of Rain Attenuation: A Survey
