Behavior Consistency Computation for Workflow Nets With Unknown Correspondence
2018-01-26MimiWangGuanjunLiuPeihaiZhaoChungangYanandChangjunJiang
Mimi Wang,Guanjun Liu,Peihai Zhao,Chungang Yan,and Changjun Jiang
I.INTRODUCTION
WORKFLOW nets(WF-nets)have become one of the standard ways to model and analyze workflows[1].In fact,WF-nets can also model many other distributed and parallel systems such as web services composition in which multiple processes interact via sending/receiving messages[2]−[4]and distributed systems[5]−[8].
To support the operation and maintenance of services systems in the open and dynamic environment,it is needed to transform from the way of building data-driven system to the construction way of behavior consciousness and from tightly coupled architecture to loosely-coupled one.Therefore,it is necessary to model and analyze systems from the perspective of behaviors.The consistency comparison of behaviors of systems is an interesting topic[9].For example,when a behavioral model is mined from a system’s logs[10],consistencycomparison between the mined model and the real model can help one evaluate the disadvantage and advantage of a method.Consistency of two models means that their semantics match each other,and this matching relation is usually built on the basis of a mapping between the graphical data.Therefore,consistency can reflect whether the mapping is effective or not[11].Consistency analysis has been applied in many fields such as security evaluation in cloud computing[12],and process mining[13].
In[2]consistency is defined by Weidlichet al.on the basis of an alignment which requires the identification of correspondences of models.Given a correspondence,the question whether two data models are equivalent is similar to the question whether a mapping between data schema is valid,which is known from the field of data integration[2].In this area,various properties for evaluating the validity of a schema mapping have been proposed.For instance,satisfiability of a mapping of two models[9]requires the existence of such single trace that is possible in the two models after the corresponding elements have been resolved.Weidlichet al.studied the given correspondence of simple correspondence and complex correspondence.For the unknown correspondence,they also thought that it was a difficult job.However,in realworld,the correspondence is often unknown such as Fig.3.The consistency relation can be used to measure the two models consistency when we do not know the correspondence.And the condition of two models with unknown correspondence usually exit in the real world.For example,for a group of users behaviors patterns,we can mine their behaviors models from their logs.Obviously,the correspondence relation among these models are not given.Then under this condition we can only obtain different models from different users,and we do not know the whole profiles for these models due to their unknown correspondence relation.To manage these users and recommend more suitable or appropriate service,we should compute maximal consistency degree of these unknown influence of correspondence.To do this,we should ravel out the influence of correspondence on consistency of two WF-nets.
In addition,trace equivalence[14],[15]and bisimulation[16]are two classical notions used to determine whether two systems are of equivalent behaviors.However,these notions only ascertain whether two systems’behaviors are consistent or not.They cannot measure their degree when their behaviors are consistent.In consequence,Weidlichet al.proposed the notion of behavioral profile and proposed a formula to measure the degree of inconsistency of behaviors of two WF-nets[11],[17]−[21].However,the results are not too accurate for some cases when we use this method.For example,there are two WF-nets,modeling the same system such that one is dead lockfree but another one is not.Obviously,their behaviors should not be equivalent.The main cause of this phenomenon is that the three behavioral relations of behavioral profiles should be refined.In addition,Weidlichet al.did not discuss the unknown correspondences.
What we should do is to obtain a more accurate behavioral relation and give a method to compute consistency degree of unknown correspondences.However the behavioral relation of two actions is usually difficult to obtain.Therefore we should give a method to compute the behavioral relation(see Section III-A).At the same time,for the unknown correspondence,how to compute the consistency degree is a challenge.
This paper focuses on these questions and obtains the following results:
1)By analyzing event relations of branching process,we give a method to obtain the behavioral relation of transition of WF-net.
2)Based on the relation profile of a WF-net,a behavioral matrix can be constructed.And different matrix arrangement can represent different correspondence.We propose a permutation method of behavioral matrix to obtain the maximal consistency degree.
3)We present a new formula to measure the consistency degree of behaviors of two WF-nets on the basis of behavioral matrices.And we propose to give a method to compute the maximal value,when the degree of consistency is maximal.
The paper is organized as follows:Section II introduces some basic concepts in order to understand the work of this paper easily.Section III introduces the behavioral relation and the method to obtain the relation,and a behavioral matrix.Section IV proposes a new formula to measure the consistency degree and maximal consistency degree.Section V introduces some related work.Finally,we conclude this paper in Section VI.
II.PRELIMINARIES
A.WF-net and Branching Process Unfolding
This section recalls the basic concepts and definitions used in this paper.For more details,one can refer to[1],[22]−[25]and[26].
A net is a 3-tupleN=(P,T,F)wherePis a finite set of places,Tis a finite set of transitions,F⊆(P×T)∪(T×P)is a set of arcs,andP∩T=Ø.
A net may be thought of as a directed graph in which a circle represents a place and a box represents a transition.
Given a netN=(P,T,F)and a nodex∈P∪T,•x={y|(y,x)∈F}is the pre-set ofx,andx•={y|(x,y)∈F}is the post-set ofx.IfX⊆P∪T,its pre-set and post-set are defined as follows:•X=∪x∈X•xandX•=∪x∈X x•.
(N,M0)=(P,T,F,M0)is a Petri net if
1)N=(P,T,F)is a net;
2)M0is the initial marking;
3)mappingM:P→N is a marking function where N={0,1,2,...};and
4)it has the following rules:
i)a transitiont∈Tis enabled atM,denoted byM[t〉,if∀p∈•t:M(p)≥1;
ii)firing an enabled transitiontyields a new markingM′and this is denoted byM[t〉M′,where
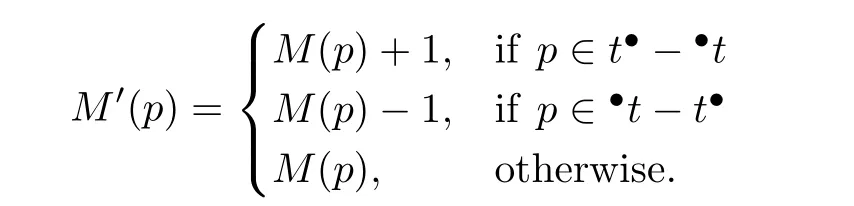
iii)if there exist transitionst1,t2,...,tk,and markingsM1,M2,...,M ksuch thatM[t1〉M1[t2〉···M k−1[tk〉M k,thenM kis reachable fromM.All markings reachable fromMare denoted byR(M)andM∈R(M).
WF-nets have become one of the standard ways to model and analyze workflows and are introduced as follows.
Definition 1(WF-net):A netN=(P,T,F)is a WF-net if it has a source placei∈Pwith•i=Øand a sink placeo∈Pwitho•=Ø,andis strongly connected wheret/∈T.
A branching process of a net systemis a labeled occurrence netβ=(O,h)=(B,E,G,h)where the labeling functionhsatisfies the following properties:
1)ndpreserves the nature of nodes);
2)for everye∈E,the restriction ofhto•eis a bijection between•e(in Σ)and•h(e)(inβ),and similarly fore•andh(e)•(hpreserves the environments of transitions);
3)the restriction ofhto m in(O)is a bijection between m in(O)andM0(βstarts atM0);
4)for everye1,e2∈E,if•e1=•e2andh(e1)=h(e2)thene1=e2(βdoes not duplicate the transitions ofΣ).
Branching process unfolding(BPU)is the least upper bound of the set of all branching processes.
The relevant concepts and algorithms of branching process can be refereed to[27],[28].We will useBPUto represent branching process unfolding.
1)Two nodesxandyare in causal relation,denoted byif the net contains a path with at least one arc leading fromxtoy.
In words,xandyare in conflict if the net contains two paths leading toxandywhich start at the same place and immediately diverge.
3)xandyare in concurrency relation,denoted byif neithernornor
B.Behavioral Profiles and Correspondence Relation
To study the behavior relations of transitions of a WF-net,the weak order relation and behavioral profiles are defined in[11]:
Let(N,M0)=(P,T,F,M0)be a Petri net.A pair of transitions(x,y)is in the weak order relation overT,denoted asx≻y,if there exists an enabled transition sequencet1t2...tnsuch that∃j,k∈{1,2,...,n}:j<k∧tj=x∧tk=y.
Based on the weak order relation,the following three relations are defined in[11]:A pair of transitions(x,y)is in
2)the exclusiveness relation
3)the interleaving relation‖,ifx≻y∧y≻x.
新常态的背景下,以腾讯为例,探究信息化人力资源管理到大数据人力资源管理的演进过程中,数据管理转型是一种构建模式,需要在组织竞争的优势上进行验证,提升专业的技术性与复杂性,并在实践的过程中,帮助企业实现人力资源数据管理演进,并对大数据的挖掘、分类、预测等内容进行有效的分析与探究。将大数据新理念渗透到人力资源各个板块当中,实现用户和员工共同参与的开放性共享创新生态构建。
Let(N1,M1)=(P1,T1,F1,M1)and(N2,M2)=(P2,T2,F2,M2)be two Petri nets.Reference[2],[29]defined the following two concepts.
1)A correspondence relationassociates correspondence transitions of the two systems.is defined as{t|∃t′∈T2:(t,t′)∈∼}.Similarly,we can define.For Figs.1(a)and(b),it holds that2),(D1,D2).
2)Letandbe two sets of transitions such thatIfandbe maximal w.r.t.⊆,i.e.,andthenis called a correspondence and written as
In fact,if the maximal value is nonexistent,then the correspondence is an unknown correspondence.Then we give the unknown correspondence concept as follows:
A unknown correspondence relationassociates correspondence transitions of the two systems.is defined asincorrect and not clear.Similarly,we can definesuch as Fig.3.

Fig.1.Two workflow nets:(a)and(b)are in the simple correspondence relation when we give the correspondence{X1}and{X2}(X=A,B,C,D).
Now,we define the following complex correspondence relations.
For instance,{C}ofN11and{C1,C2}ofN12in Fig.2 are in the complex correspondence relation.The correspondencec1,c2andc3are all complex correspondences.Let(N1,M1)=(P1,T1,F1,M1)and(N2,M2)=(P2,T2,F2,M2)be two Petri nets,B1and B2be their behavioral profiles,and2be a correspondence relation.LetandThe set of behavioral profile consistent transition pairsforcontains all pairssuch that:
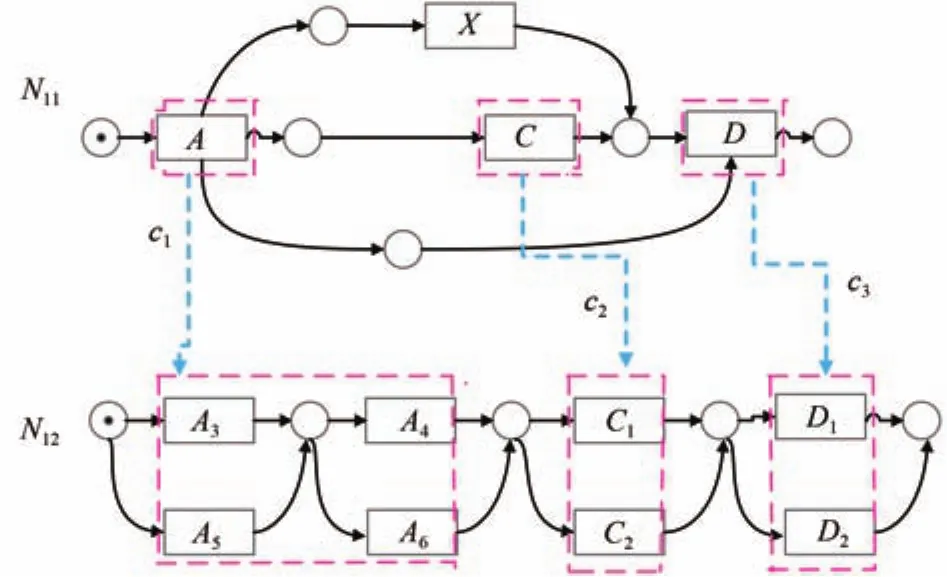
Fig.2.Complex correspondence.
1)iftx=ty,thenwith
2)iftx/=ty,thenwith
ii)
The setfor(N2,M2)is defined accordingly.Based on these,the behavioral profiles’consistency degree[2]is defined as follows:
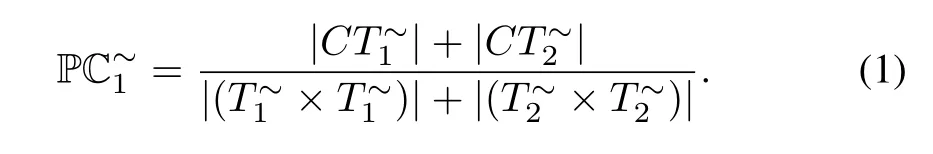
C.Motivation Examples
The dining problem of philosophers is a classical example of synchronization and concurrency in computer science[30].For simplification,we consider two philosophers whose dinning model is shown in Fig.4(a).The dinning processes are modeled by transitionsb,c,d,gfor philosopher 1 and byh,k,m,qfor philosopher 2.As we all know Fig.4(a)has a deadlock.Murat a and Wu used Token[31]to prevent deadlock in philosophers’dining problem.We can get Fig.4(b)by addingp12into Fig.4(a)wherep12represents a Token.We know that Fig.4(b)has no deadlock.The consistency degree of behavioral profile consistency of the two WF-nets in Figs.4(a)and(b)is 1 by behavioral profiles consistency[2].However,behaviors of Figs.4(a)and(b)should not be thought of being completely consistent from the aspect of quantification because the former has a deadlock but the latter has not.Therefore,we should obtain behavioral relations and refine them(see Section III-A).
In Fig.3,the three WF-nets express three different systems.We do not know the correspondences of them.Therefore,we should obtain behavioral relations and refine them(see Section IV-A).
III.BEHAVIORAL SEQUENCE RELATION AND BEHAVIORAL MATRIX
To compute consistency degree,we first refine the behavioral relation of two transitions based on the event structures in BPU.Next,to formulate consistency degree conveniently,we use a matrix to represent the behavioral relations of all transitions of a WF-net.
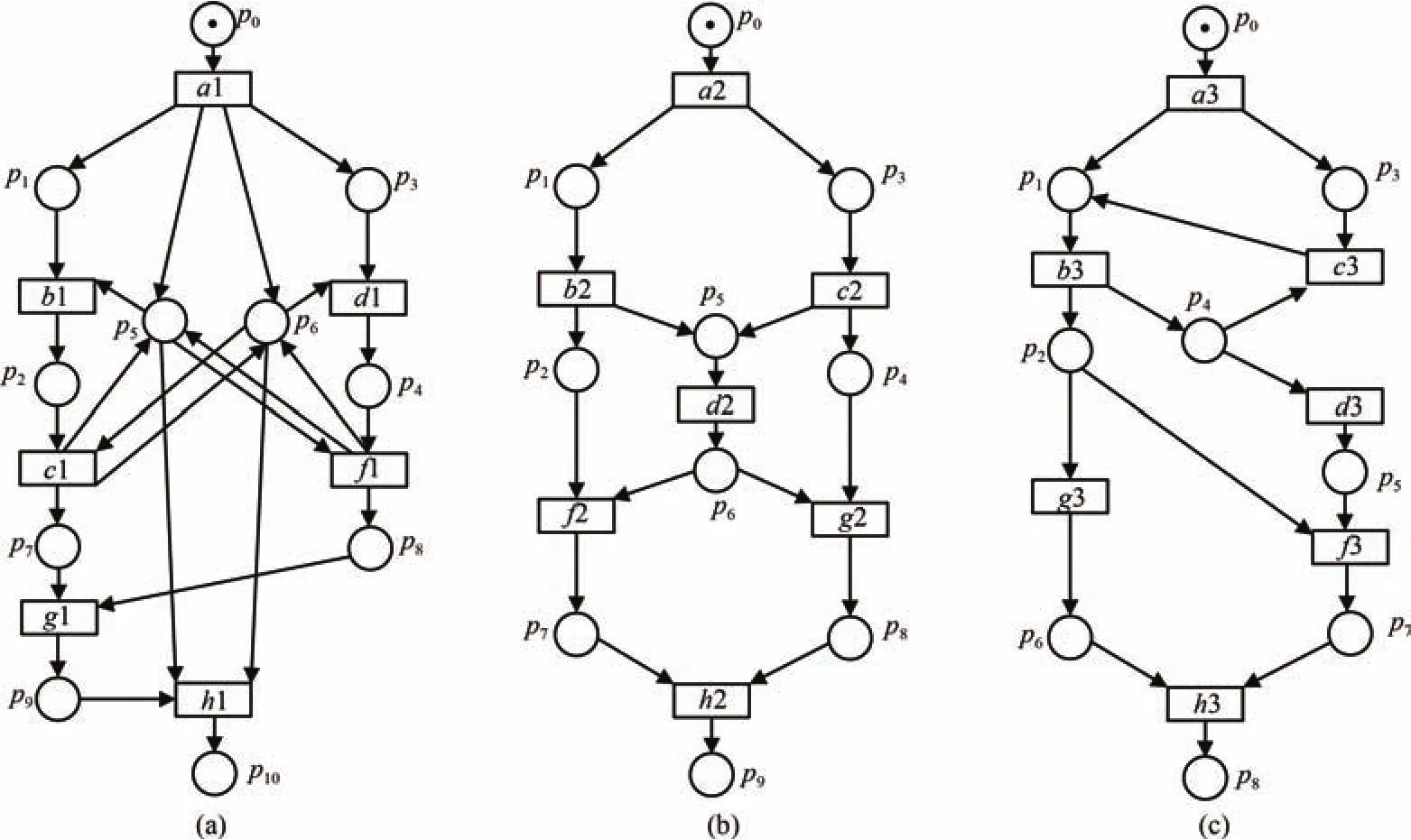
Fig.3.Three WF-nets with unknown correspondence.

Fig.4.Two workflow nets:(a)the WF-net of two philosophers’dining problem;and(b)the WF-net with Token.
A.Behavioral Sequence Relation
Based on the weak order relation,we define the relations between events.According to relations between events of BPU,the behavioral sequence relation can be expressed as follows.
Definition 2(Behavioral Sequence Relation(BSR)):Let Σ=(N,M0)=(P,T,F,M0)be a net system,and its unfolding of Σ is:Unf(Σ)=(B,E,G,h),where(B,E,G)is an occurrence net,and a homomorphismh:B∪E→P∪T.For every transition pair(t1,t2)∈T×Tis in the behavioral sequence relations as follows.
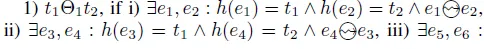
such that:

such that:
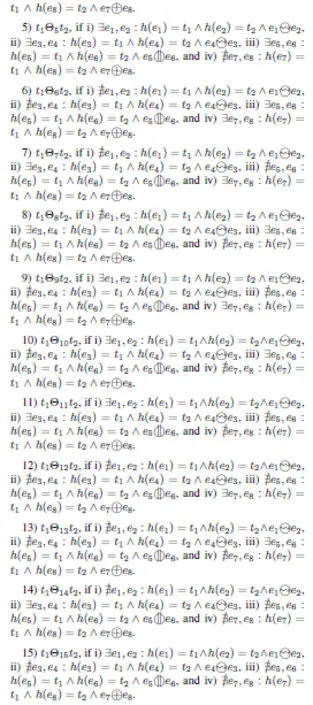
such that:
is the behavioral sequence relation set.
Notice that each kind of behavioral sequence relation in Definition 2 is based on the event relations betweene1ande2.However,thee1ande2can be obtained by BPU.Although until now we do not have a tool to obtain this BPU,we can obtain BPU by using the algorithm of[27].

Algorithm 1.Event relation
The events set of the transitiontimay have only one element when the number ofh−1(ti)is 1.And it may have more than one element when the number ofh−1(ti)is greater than 1.We denote the set asEi.
When the number of elements inEiis greater than 1,we will compute the events relations of more than one pair.
According to Definition 2,to compute behavioral sequence relation of two transitions,we should mainly obtain the their event relations.So far,we do not know if the relation of any two transitions in a general WF-net is computable because the net system may be unbounded and its branching process may be infinite.But for bounded WF-nets,we can decide which relation any two events are in.Algorithm 1 shows the computing process.
Lemma 1:For any WF-net holds that the behavioral sequence relation of Definition 2 is mutually exclusive.
According to Definition 2,it is easy to prove the lemma.
Based on Lemma 1 and Definition 2,we know that behavioral sequence relations are complete.The formal representation is as follows:
Theorem 1:Given a WF-netNand its behavioral sequence relationBSR,then for∀x,y∈T,∃R∈BSR:xRy.
In fact,for any two transactionsx,y∈T,if they are not in a kind ofBSR,then there are following two cases:
1)if,then they must be in one of the relationsΘ15};
if,then they must be in one of the relationswhenandthen they must be in one of the relations{Θ1,Θ4,Θ5,Θ11}.
Similarly in this way,we can see that for any two transactionsx,y∈T,they are in one of the relation ofBRS.
That is to say,behavioral sequence relations are complete,for a WF-netNand its behavioral sequence relationBSR.The proof process can be referred to the proof of completeness of behavioral profiles relations[2].
B.Behavioral Matrix
For convenience,we use behavioral matrix to describe the behavioral sequence relations of a WF-net.
Definition 3(Behavioral Matrix):Let Σ=(P,T,F,M0)be a WF-net,be the behavioral sequence relation overT={t1,t2,...,tn}.The behavioral matrixBMis ann×nmatrix:
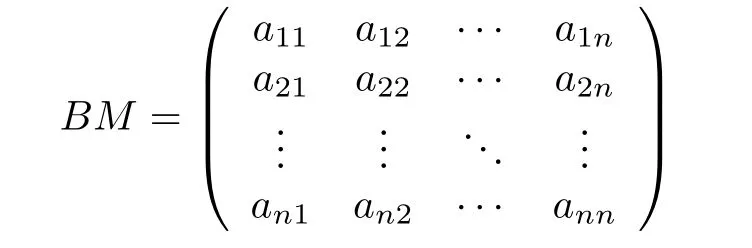
such that:

Property 1:There aren!kinds of correspondences for two(n×n)-order behavioral matrixBM.
Proof:In fact,for the two netsN1,N2and their(n×n)-order behavioral matricesBM1andBM2,we make arrangement toncolumns ofBM1,BM2,which can getn×(n−1)×···×1=n!kinds of correspondence situations.
For Figs.3(b)and(c),there are 7!= 5040 kinds of correspondences.
IV.CONSISTENCY DEGREE COMPUTING
In this section,in order to find the different consistency degree on the basis of different correspondence relations,firstly we study the behavioral matrix permutation,and then look for the correspondence relation when consistency degree is the maximal value.
A.Behavioral Matrix Permutation
Different correspondences mean that their behavioral matrix has the permutation for rows and columns.
Lemma 2:The two(n×n)-orderBM1andBM2,their all correspondences can be represented as{BM1,BM′}(BM′=(C1C2···Cm)BM2(Cm···C2C1),Ci(i=1,2,...,m≤n!)is the permutation matrix).
Proof:BM′=(C1C2···Cm)BM2(Cm···C2C1)explains that it is obtained by doing the row and column transformations onBM2.For two matrices,one of them remains unchanged,another one does the row and column transformations,which can get all correspondences.And according to Property 1,there aren!kinds of correspondence relations of two(n×n)-order BM,then the time of doing permutation is less than or equal ton!.
According to Lemma2,the problem of maximal consistency degree of models is that the number of 0 elements in matrixBM1−BM′is at least.
B.Computing Consistency Degree
Definition 4(Consistency Degree):Let Σ1=(N1,M1)and Σ2=(N2,M2)be two net systems,BPU1,BPU2be their branching process unfolding andBM1andBM2be their behavioral matrices.Consistency degree is defined as:

where
1)
Definition 4 means that the different parts from two behavioral matricesBM1andBM2are the inconsistent parts.In other words,the nonzero elements ofBM1−BM2are non-consist parts.Therefore,the consistency degree is the maximum consistency degree if the nonzero elements ofBM1−BM2are minimum.
Definition 5(Maximal Consistency Degree):Let Σ1=(N1,M1)and Σ2=(N2,M2)be two net systems,BPU1,BPU2be their branching process unfolding andBM1andBM2be their behavioral matrices.Maximal consistency degree based onBM1andBM2is defined as:
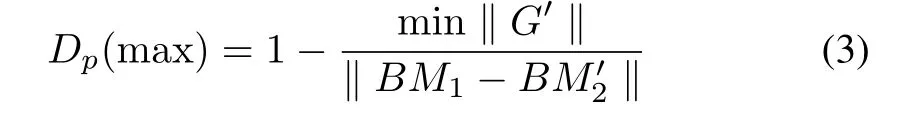
where
1)2,...,m≤n!)is the permutation matrix;
2)
3)andxpress the number ofBM1−BM2andG′,respectively.
Algorithm 2 shows the computing process.According to Algorithm 2,we can see that for two behavioral matrices,we can obtain minimal‖G′‖,and the matrixby permutation.And according to(3),we can obtain the maximal consistency degree.
Theorem 2:Given two WF-nets and their behavioral matricesBM1andBM2,we have thatDpcomputed by(2)is always less than or equal toDp(max)computed by(3).
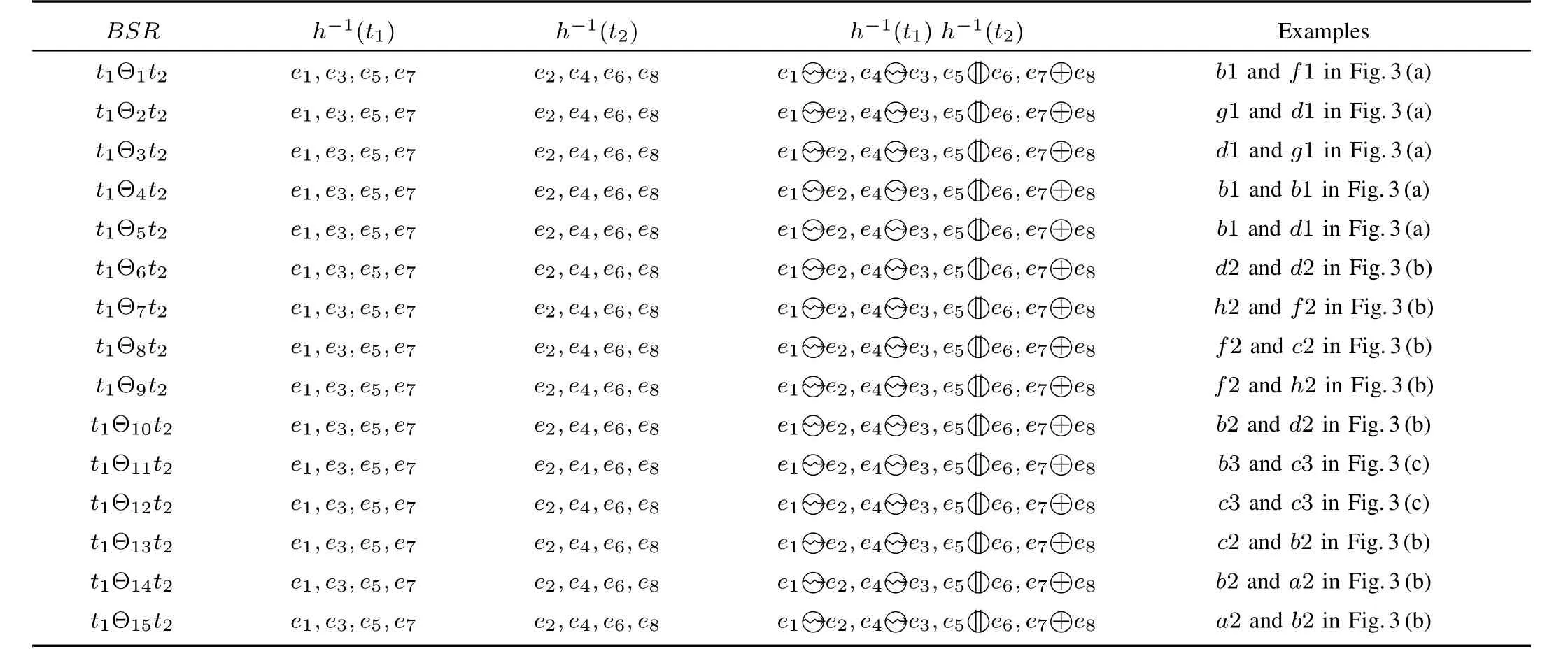
TABLE I BEHAVIORAL SEQUENCE RELATION INTRODUCTION
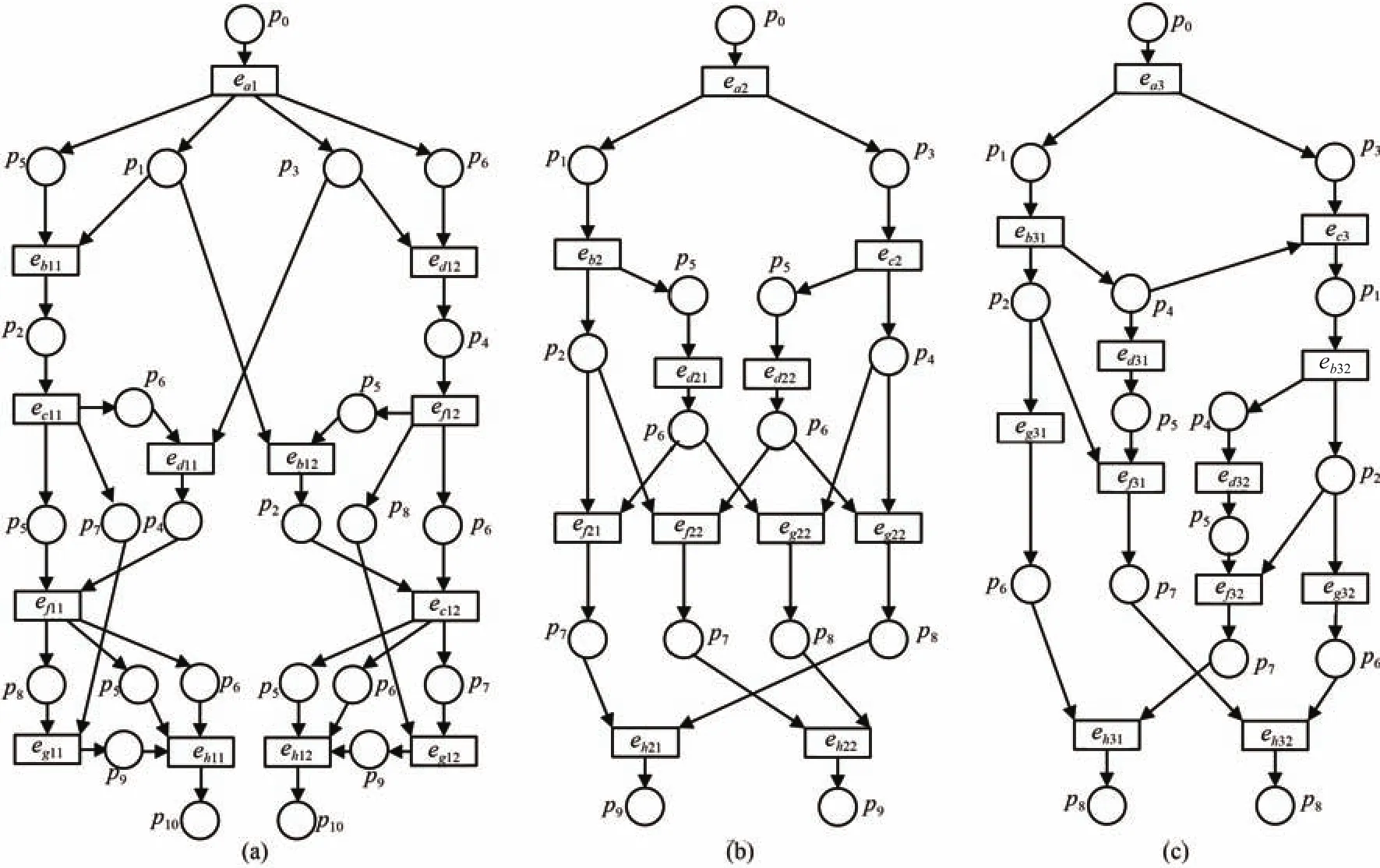
Fig.5.BPU of Fig.3.
Based on the above conclusion,we can see that the consistency degree based on behavioral matrix is effective to compute the consistency of two bounded WF-nets.In fact,when the WF-net is unbounded,there is no effective method to compute its branching process.We will be dedicated to do this research in the future.
C.Case Study
According to Definition 2,we can decide the behavioral sequence relation between two transitions using four kinds of relations between events.For readability,Table I shows these relations and gives the related examples.To decide the relations between events,we must obtain the BPU.For a bounded WF-net,we can compute its BPU by the algorithms in[27]and[28].For example,for Figs.3(a)−(c)we can obtain their BPUs as shown in(4)and(5).
In Figs.3(b)and(c),we do not know whether there is a correspondence.For these WF-nets,we easily obtain their BPU as shown in Fig.5.For instance,the behavioral matrices of Figs.3(b)and(c)are shown in(4)and(5).
According to Algorithm 2,we use the permutation for matrixBM3.The result is shown in Fig.6.In Fig.6,we can see that Fig.3(c)does the permutations{1 4 3 2 6 5 7},i.e.,rowrow 2,rowrow 6,columncolumn 2 and columncolumn 6.And according to(4)and(5),we can get the permuted matrixofBM3is shown in(6).And theas shown in(7).Finally,according to(3),the maximal consistency degree of Figs.3(b)and(c)isDp(max)=1−17/49≈0.6531.Similarly,we can obtain all maximal consistency degrees of Fig.3 as shown in Table II.In fact,for two 7×7-order matrices,the time to compute their maximal consistency degree is 0.02−0.03 second.

Similarly,we can obtain the minimal consistency degree if necessary.In fact,if Fig.4 is based on an unknown correspondence,we can compute this condition using our method.
In fact,according to the Theorem 1 and the theorem of behavioral profiles relations in[2],we have shown that our method is more accurate.
V.RELATED WORK
Existing consistency analysis techniques for process models are based on three complementary aspects[3]:task labels,structure and behavior.In order to meet the complex and fickle application requirements,to compare the consistency betweenmodels and multiple interaction components has become a new trend.Existing models behavior consistency methods are mainly divided into two aspects:one is the semantic behavior consistency[32]−[38],other one is process behavior consistency [39]−[52].[39]gave a consistency method of using an expected value to measure a model and the expected one,but did not involve the degree of consistency.[40]proposed the concept of process-oriented protocol and proposed a standard of detect consistency automatically.[41]proposed a method of determining whether the overall model can run locally or not based on semantic consistency,and gave an algorithm of generating local models from the entire model.But it did not consider behavior satisfiability.[42]proposed a method which would determine behavior pattern and tiny deviations once determining the matching.[43],[44]explained non-conformance and consistency only for a execute sequence.[45]−[47]introduced the measure similarity method of correcting distance in semantics.[48]proposed a more standard and more open architecture to assess the service interaction.[49]used trace equivalence or bisimulation to analyze the behavioral consistency between the models.[50],[51]defined the similarity degree between two process models by using causal footprints.[52]is a family of binary relations that represented the behavior of a process in an×nmatrix.

Algorithm 2.Maximal consistency degree


TABLE II MAXIMAL CONSISTENCY DEGREE OF FIG.3

Fig.6.Implementation result by Algorithm 2 and using MATLAB for Figs.3(b)and(c).
It offered a plethora of different relations and each cell in the matrix can contain more than one relation.However,4C spectrum suffers from the same issues as the behavioral profiles because it does not guarantee any of the well-known notions of equivalence.Furthermore,the relations in this family not clear.
V I.CONCLUSIONS
In this paper,we present a method of generating behavioral sequence relations based on BPU and event relations.We refine behavioral sequence relations between two actions,and present a more accurate consistency measurement of two WF-nets with uncertain correspondence.
In the future,we would like to focus on the structure and behavioral characteristic influencing the consistency of WF-nets.In addition,to obtain a tool of the branching process unfolding is our future work.
[1]W.M.P.Van der Aalst,“The application of petri nets to workflow management,”J.Circuits Syst.Comput.,vol.8,no.1,pp.21−66,Feb.1998.
[2]M.Weidlich,J.Mendling,and M.Weske,“Efficient consistency measurement based on behavioral profiles of process models,”IEEE Trans.Softw.Eng.,vol.37,no.3,pp.410−429,May−Jun.2011.
[3]M.Dumas,L.Garćea-Bañuelos,and R.M.Dijkman,“Similarity search of business process models,”Bull.IEEE Comput.Soc.Tech.Comm.Data Eng.,vol.32,no.3,pp.23−28,Jan.2009.
[4]R.Dijkman,M.Dumas,B.Van Dongen,R.Käärik,and J.Mendling,“Similarity of business process models:Metrics and evaluation,”Inf.Syst.,vol.36,no.2,pp.498−516,Apr.2011.
[5]T.Bauer and P.Dadam,“Efficient distributed workflow management based on variable server assignments,”inProc.2000 Int.Conf.Advanced Information Systems Engineering.Berlin,Heidelberg,Germany,2000,pp.94−109.
[6]G.A lonso,C.Mohan,R.Gunthör,D.Agrawal,A.El Abbadi,and M.Kamath,“Exotica/FMQM:a persistent message-based architecture for distributed workflow management,”inProc.IFIP working Conf.Infor-mation Systems Development for Decentralized Organizations.Berlin,Heidelberg,Germany,1995,pp.1−18.
[7]P.Muth,D.Wodtke,J.Weissenfels,A.K.Dittrich,and G.Weikum,“From centralized workflow specification to distributed workflow execution,”J.Intell.Manuf.Inf.Syst.,vol.10,no.2,pp.159−184,Mar.1998.
[8]B.Finkbeiner,M.Gieseking,and E.R.Olderog,“Adam:causality based synthesis of distributed systems,”inComputer Aided Verification,D.Kroening and S.Păšareanu,Eds.Cham,Germany:Springer,2015,pp.433−439.
[9]G.Rull,C.Farré,E.Teniente,and T.Urpí,“Validation of mappings between schemas,”Data Know l.Eng.,vol.66,no.3,pp.414−437,Sep.2008.
[10]W.M.P.van der Aalst,Process M ining:Discovery,Conformance and Enhancement of Business Processes.Heidelberg,Germany,Dordrecht,Japan,London,Britain:Springer,2011.
[11]M.Weidlich,“Behavioural profiles:a relational approach to behaviour consistency,”Ph.D.dissertation,Potsdam,Univ.Potsdam,Diss.,Germany,2011.
[12]X.W.Fang,M.M.Wang,and S.B.Wu,“A method for security evaluation in cloud computing based on petri behavioral profiles,”inAdvances in Intelligent Systems and Computing,Z.Yin,L.Pan,and X.Fang,Eds.Berlin,Heidelberg,Germany:Springer,vol.212,pp.587−593,2013.
[13]X.W.Liu,X.W.Fang,M.M.Wang,and Z.X.Yin,“The behavior trustworthiness analysis methods of composite web services based on process mining,”Appl.Math.Inf.Sci.,vol.7,no.5,pp.1985−1992,Sep.2013.
[14]V.Cheval,V.Cortier,and S.Delaune,“Deciding equivalence-based properties using constraint solving,”Theor.Comput.Sci.,vol.492,pp.1−39,Jun.2013.
[15]P.Buchholz,J.Kriege,and D.Scheftelowitsch,“Equivalence and minimization for model checking labeled Markov chains,”inProc.9th EAIInt.Conf.Performance Evaluation Methodologies and Tools,Berlin,Germany,2016,pp.119−126.
[16]L.M.F.Fioriti,V.Hashemi,H.Hermanns,and A.Turrini,“Deciding probabilistic automata weak bisimulation:Theory and practice,”Form.Asp.Comput.,vol.28,no.1,pp.109−143,Mar.2016.
[17]A.Polyvyanyy,A.Armas-Cervantes,M.Dumas,and L.GarćıaBañuelos,“On the expressive power of behavioral profiles,”Form.Asp.Comput.,vol.28,no.4,pp.597−613,Jul.2016.
[18]M.Weidlich,M.Weske,and J.Mendling,“Change propagation in process models using behavioural profiles,”inProc.IEEE Int.Conf.Services Computing,2009.SCC’09.,Bangalore,India,2009,pp.33−40.
[19]M.Weidlich,A.Polyvyanyy,N.Desai,J.Mendling,and M.Weske,“Process compliance analysis based on behavioural profiles,”Inf.Syst.,vol.36,no.7,pp.1009−1025,Nov.2011.
[20]S.Sm irnov,M.Weidlich,and J.Mendling,“Business process model abstraction based on synthesis from well-structured behavioral profiles,”Int.J.Coop.Inf.Syst.,vol.21,no.1,pp.55−83,Mar.2012.
[21]M.Weidlich,A.Polyvyanyy,J.Mendling,and M.Weske,“Causal behavioural profiles-efficient computation,applications,and evaluation,”Fund.Inform.,vol.113,no.3−4,pp.399−435,Aug.2011.
[22]J.L.Peterson, “Petri nets,”ACM Comput.Surv.(CSUR),vol.9,no.3,pp.223−252,Sep.1977.
[23]T.Murata,“Petrinets:properties,analysis and applications,”Proc.IEEE,vol.77,no.4,pp.541−580,Apr.1989.
[24]W.M.P.Van Der Aalst,“Woflan:a petri-net-based workflow analyzer,”Syst.Anal.Modell.Simul.,vol.35,no.3,pp.345−357,1999.
[25]M.M.Wang,G.J.Liu,C.J.Jiang,and C.G.Yan,“Computation of secure consistency for real systems,”inProc.9th Int.Conf.Security,Privacy and Anonymity in Computation,Communication and Storage,Cham,Germany,2016,pp.84−97.
[26]M.W.P.van der Aalst,“Verification of workflow nets,”inApplicationand Theory of Petri Nets 1997,P.Azëma and G.Balbo,Eds.Berlin,Heidelberg,Germany:Springer,1997,pp.407−426.
[27]J.M.Couvreur,D.Poitrenaud,and P.Weil,“Branching processes of general petri nets,”inApplications and Theory of Petri Nets,L.M.Kristensen and L.Petrucci,Eds.Berlin,Heidelberg,Germany:Springer,2011.
[28]J.Engelfriet,“Branching processes of petri nets,”Acta Inform.,vol.28,no.6,pp.575−591,Jun.1991.
[29]M.Weidlich,R.Dijkman,and M.Weske,“Behaviour equivalence and compatibility of business process models with complex correspondences,”Comput.J.,vol.55,no.11,pp.1398−1418,Feb.2012.
[30]E.W.Dijkstra, “Hierarchical ordering of sequential processes,”Acta Inform.,vol.1,no.2,pp.115−138,Jun.1971.
[31]T.Murata and Z.H.Wu,“Fair relation and modified synchronic distances in a petri net,”J.Franklin Inst.,vol.320,no.2,pp.63−82,Aug.1985.
[32]W.Khlif and H.Ben-Abdallah,“Integrating semantics and structural information for BPMN model refactoring,”inProc.IEEE/ACIS 14th Int.Conf.Computer and Information Science(ICIS),Las Vegas,NV,USA,2015,pp.656−660.
[33]M.Ehrig,A.Koschm ider,and A.Oberweis,“Measuring similarity between semantic business process models,”inProc.Fourth Asia-Pacific Conf.Comceptual Modelling,Ballarat,Australia,vol.67,pp.71−80,2007.
[34]D.Sangiorgiand V.Vignudelli,“Environmental bisimulations for probabilistic higher-order languages,”inProc.43rd Annu.ACM SIGPLANSIGACT Symp.Principles of Programming Languages,St.Petersburg,FL,USA,2016,pp.595−607.
[35]B.Luttik,“Unique parallel decomposition in branching and weak bisimulation semantics,”Theor.Comput.Sci.,vol.612,pp.29−44,Jan.2016.
[36]M.Taheriyan,C.A.Knoblock,P.Szekely,and J.L.Ambite,“A scalable approach to learn semantic models of structured sources,”inProc.2014 IEEE Int.Conf.Semantic Computing(ICSC),Newport Beach,CA,USA,2014,pp.183−190.
[37]S.de Cesare,D.Juric,and M.Lycett,“Automated taxonomy extraction from semantic business process models,”inProc.2016 49th Hawaii Int.Conf.System Sciences(HICSS),Koloa,HI,USA,2016,pp.4394−4403.
[38]D.Ritze,J.Völker,C.Meilicke,and O.Sväb-Zamazal,“Linguistic analysis for complex ontology matching,”inProc.5th Int.Workshop on Ontology Matching.Shanghai,China,vol.689,pp.1−12,2010.
[39]X.W.Fang,C.J.Jiang,Z.X.Yin,and X.Q.Fan,“The trustworthiness analyzing of interacting business process based on the induction information,”Comput.Sci.Inf.Syst.,vol.8,no.3,pp.843−867,Jun.2011.
[40]W.M.P.van der Aalst,N.Lohmann,P.Massuthe,C.Stahl,and K.Wolf,“Multiparty contracts:Agreeing and implementing interorganizational processes,”Comput.J.,vol.53,no.1,pp.90−106,Jan.2010.
[41]J.M.Zaha,M.Dumas,A.H.M.TerHofstede,A.Barros,and G.Decker,“Bridging global and local models of service-oriented systems,”IEEE Trans.Syst.,Man,Cybern.,C,vol.38,no.3,pp.302−318,May2008.
[42]C.Girault and R.Valk,Petri Nets for Systems Engineering:AGuide to Modeling,Verification,and Applications.Berlin Heidelberg:Springer,2003.
[43]R.E.Lopez-Herrejon,L.Linsbauer,and A.Egyed,“A systematic mapping study of search-based software engineering for software product lines,”Inf.Softw.Technol.,vol.61,pp.33−51,May2015.
[44]H.A.Duran-Limon,C.A.Garcia-Rios,F.E.Castillo-Barrera,and R.Capilla, “An ontology-based product architecture derivation approach,”IEEE Trans.Softw.Eng.,vol.41,no.12,pp.1153−1168,Dec.2015.
[45]J.Becker,D.Pfeiffer,M.Räkers,T.Falk,and M.Czerwonka,Semantic Business Process Modelling and Analysis,J.vom Brocke and M.Rosemann,Eds.Berlin Heidelberg,Germany:Springer,2015.
[46]Z.Bellahséne and M.Lëonard,“Advanced information systems engineering,”inProc.20th Int.Conf.CAiSE,Montpellier,France,2008,pp.16−20.
[47]S.H.Yeganeh,J.Habibi,H.Rostami,and H.Abolhassani,“Semantic web service composition testbed,”Comput.Electr.Eng.,vol.36,no.5,pp.805−817,Sep.2010.
[48]J.Puttonen,A.Lobov,and J.L.M.Lastra,“Semantics-based composition of factory automation processes encapsulated by web services,”IEEE Trans.Industr.Inform.,vol.9,no.4,pp.2349−2359,Nov.2013.
[49]K.Yongsiriw it,M.Sellam i,and W.Gaaloul,“A semantic framework supporting business process variability using event logs,”inProc.2016 IEEE Int.Conf.Services Computing(SCC),San Francisco,CA,USA,2016,pp.163−170.
[50]M.Schrefl and M.Stumptner,“Behavior-consistent specialization of object life cycles,”ACM Trans.Softw.Eng.Methodol.,vol.11,no.1,pp.92−148,Jan.2002.
[51]S.Boubaker,A.Mammar,M.Graiet,and W.Gaaloul,“A formal guidance approach for correct process configuration,”inProc.2016 Int.Conf.Service-Oriented Computing,Cham,Germany,2016,pp.483−498.
[52]A.Polyvyanyy,M.Weidlich,R.Conforti,M.La Rosa,and A.H.M.Ter Hofstede,“The 4C spectrum of fundamental behavioral relations for concurrent systems,”inApplication and Theory of Petri Nets and Concurrency,G.Ciardo and E.Kindler,Eds.Cham,Germany:Springer,2014,pp.210−232.
猜你喜欢
杂志排行
IEEE/CAA Journal of Automatica Sinica的其它文章
- Encoding-Decoding-Based Control and Filtering of Networked Systems:Insights,Developments and Opportunities
- Internet of Vehicles in Big Data Era
- Residential Energy Scheduling for Variable Weather Solar Energy Based on AdaptiveDynamic Programming
- From Mind to Products:Towards Social Manufacturing and Service
- Analysis of Autopilot Disengagements Occurring During Autonomous Vehicle Testing
- A Methodology for Reliability of WSN Based on Software De fined Network in Adaptive Industrial Environment
