SVM-DT-Based Adaptive and Collaborative Intrusion Detection
2018-01-26ShaohuaTengNaiqiWuSeniorHaibinZhuSeniorLuyaoTengandWeiZhang
Shaohua Teng,,NaiqiWu,Senior ,Haibin Zhu,Senior ,Luyao Teng,and Wei Zhang
I.INTRODUCTION
INTRUSION detection is an important means to guarantee the safety of a network to avoid illegal operations that are launched by intruders(such as attackers and hackers)via authentication identification[1].An intrusion detection system(IDS)is the most significant tool to ensure the security of a network by analyzing the audit data and current state.There are many measures to protect a network system,however,most of the conventional methods are inefficient.Since some attacks are composed of a series of users’operations,the users’behavior should be analyzed to detect an intrusion.To do so,users’actions are divided into normal and abnormal ones to separate the data.Then,classification is used to justify the detection result.
With the explosive grow th of transmission data and the wide application of high speed network,traditional intrusion detection methods are out of date and cannot meet the current requirements.Furthermore,an intrusion detection system should not affect the normal operation of a network system when it works,especially in the Big Data and high-speed network environment.
Support vector machines(SVM s)[2]are a powerful tool for machine learning which is widely utilized in many applications such as classification,intrusion detection,and pattern recognition.Since the current network is very complicated,an intrusion detection system needs to not only be an effective detection tool but also possess an adaptive mechanism.This work proposes an adaptive collaboration intrusion detection method and develops a corresponding intrusion detection model.The algorithms of SVMs and decision trees(DTs)are used in the model.
To build an effective and adaptive intrusion detection model,we introduce the environments-classes,agents,roles,groups,and objects(E-CARGO)model as a tool which helps us to design the detection system.Also,SVM classifiers and the DT algorithm are applied.Group role assignment is studied.Experiments on data set KDD CUP 1999 are done to illustrate the effectiveness and performance of the proposed method.The experimental results show that the proposed method can not only improve the accuracy of classification,but also save time and storage space.
The remainder of this paper is arranged as follows.Section II briefly reviews the related work.Section III introduces the ECARGO model and intrusion detection.The major work is developed in Section IV,including the adaptive and collaborative intrusion detection method,its architecture and components.Section V exhibits the suspicious behavior detector based on SVMs and DTs.We build the whole model containing suspicious behavior detection roles and intrusion agents.Section VI shows the self-adaptive mechanism of cooperative intrusion detectors.We illustrate our work with experiments in Section VII.Section VIII summarizes the main contribution of this work.
II.RELATED WORK
An SVM is a binary classifier and is applied to intrusion detection by many researchers[3]−[16].
Tenget al.[3]introduce a fuzzy SVM into intrusion detection and propose a collaborative network intrusion detection model.It is a multi-agent model including three kinds of agents which are used to detect transmission control protocol(TCP)attacks,user datagram protocol(UDP)attacks,and internet control message protocol(ICMP)attacks,respectively.Each agent plays a role that is realized by a fuzzy SVM.
Kuangetal.[4]propose an SVM model for intrusion detection.This model is formed by amulti-layer SVM classifier by combining kernel principal component analysis(KPCA)with genetic algorithm(GA).By this method,KPCA is used as a preprocessor with a GA algorithm being embedded.With the KPCA,the dimension of feature vectors can be reduced and the training time can be shortened,while the GA algorithm is employed to optimize the kernel parameterσ,the punishment factorC,and the tube sizeεof the SVM.
Lietal.[5]present a classifier for intrusion detection,which combines clustering,ant colony algorithm,and an SVM.This classifier can identify whether a network visit is normal or not.Bamakanet al.[6]use time-varying chaos particle swarm optimization and propose an intrusion detection framework based on multiple criteria linear programming(MCLP)and SVM.A weighted objective function is designed and implemented,and a particle swarm optimization(PSO)algorithm is introduced for searching the optimum.Aburomman and Reaz[7]use a PSO algorithm to calculate the weights of classifiers and generate an ensemble model for detecting intrusions.They use the local unimodal sampling approach as a meta-optimizer to obtain better parameters for PSO.
Linet al.[8]propose an intelligent anomaly intrusion detection algorithm with feature selection and decision rules.The algorithm is formed by integrating SVM,DT,and simulated annealing(SA).By this algorithm,the DT and SA are used to produce decision rules for new attacks and improve the accuracy of classification,while the SVM and SA are used to find the best candidate features for detecting anomaly attacks.The best parameter settings for the DT and SVM are adjusted by SA.
Fenget al.[9]introduce SVMs and clustering into intrusion detection based on self-organized ant colony network(CSOACN).Classifiers are generated by combining two existing machine learning methods:SVMs and CSOACN.They illustrate the detection effectiveness by experiments.
Kimet al.[10]propose a hybrid intrusion detection model by hierarchically integrating a misuse detector and an anomaly detector in a decomposition structure.The C4.5 DT is used to build them is use detector that divides the normal data into smaller subsets.Then,SVM s are used to create an anomaly detector in each decomposed region.With this integration,the anomaly detector can indirectly use the known attack information to enhance its detection ability when profiles of normal behaviors are built.Hornget al.[11],Ravaleet al.[12]combine a hierarchical clustering algorithm and the SVM technique,and build an SVM-based intrusion detection model.This hierarchical cluster provides the SVM with a smaller,abstracted,and higher-qualified data set that is derived from the original data set.This method not only greatly shortens the modeling time,but also improves the performance of the resultant SVM.
Linet al.[13]develop intrusion detection techniques by extracting a feature representation approach to the malicious network traffic data.They present a method for how to extract more representative features for normal connections and effective detection of attacks.In their paper,two distances are measured.One is the distance between each sample and its cluster center,and the other is that between the data and its nearest neighbor in the same cluster.
Mitrokotsaet al.[14],[15]study the intrusion detection problem in mobile ad-hoc networks(MANET)by evaluating the performance of classification methods.They select varied traffic conditions and mobility patterns,then examine the classifier’s performances on a database.Cataniaet al.[16]focus on how to deal with imbalanced data and present an approach for autonomously labeling the routine traffic based on an SVM.These labeling processes are described in SNORT[1].
There are some limitations of SVMs,such as high dependency on parameters,huge number of support vectors in the calculating process,and a long training time.In many cases,an SVM model does not behave flexibly as we need.Hence,we cannot directly apply this method in different network scales.Especially,traditional intrusion detection methods and technologies are difficult to utilize in the current high-speed network environment with tremendous amounts of data.For intrusion classification in complicated network environments,we put forward an adaptive cooperation method based on the E-CARGO model and test it with the KDD CUP 1999 data set.
Tenget al.[17]and Zhanget al.[18]introduce collaborative computing and granular computing into intrusion detection,and present a cooperative multi-agent intrusion detection model,where every agent plays a detector role and these agents form a distributed intrusion detection model.This model improves the performance of detecting intrusions.However,designing and implementing an agent are very complicated,and a distributed model needs to hold and manage a lot of agents,agents’actions,and their communications[17]−[19].Note that the problem for building an intrusion detection model falls in the software engineering field.An ECARGO model is a tool in software engineering and includes a set of software components.They are groups,roles,agents,environments,objects,and classes[20]−[22].Therefore,an E-CARGO model is applied in the proposed method and its components are used to describe the architecture,the modules,and their relationship.
Role-based collaboration[20]−[22]uses roles as underlying mechanisms to realize abstraction,collaboration,allocation and assignment,and interaction.A role(r)in an E-CARGO model can be defined as a requirement and assigned to some intrusion detection agents.A current agent(a)is currently playing a detection role and the potential ones possess the detecting ability,but they are not currently playing that role.A group(g)which often contains many agents performs a function of an intrusion detection component.An environment(e)can include many roles and it confines a number range[l,u]for each role.The role with range[l,u]means that at leastldetection agents are required to play it and can be played by at mostudetection agents.A groupgis workable when each role inghas enough(l)agents to play it currently.
III.INTRUSION DETECTION AND E-CARGO
A common intrusion detection framework(CIDF)was proposed by the defense advanced research projects agency(DARPA)[1],[2],[23].The CIDF divides an intrusion detection system into four components:event generator,detector,response unit,and database.These four components are used in our model.
In this paper,components and their collaboration are specified by environments,classes,agents,roles,groups,and objects in the E-CARGO model[17],[20]−[22].In the ECARGO,requirements are regarded as roles.All the intrusion detection components are taken as requirements such that they are defined as roles.A rolerrealizes a function about intrusion detection and is assigned to some agents that play roler.Agents that play the same role form a groupg.gthen composes detection results of the agents in the same group.
The three fundamental components in the E-CARGO are agent,role,and group[17],[20]−[22].These components are defined as follows.
Definition 1[20]−[22]:class:c::=〈n,D,F,X〉,where
1)nis the ID ofc;
2)Dis a data structure which describes the state of an object;
3)Fis a set of mapping functions or methods;
4)Xis a unified interface of all the objects in the class,which is a set of message patterns that tells how to send a message to invoke a function.
Note thatcrepresents a class.It can be an event generator class,an event detector class,or a response unit class.Cis the set of all classes.
Definition 2[20]−[22]:role:,where
1)nis the ID ofr;
2)denotes a set of messages withMinbeing the input messages andMoutthe output messages;
3)Nais an ID set of agents that are playingr;
4)Nois an ID set of objects including classes,environments,roles,and groups which can be accessed by agents playingr.
Symbolrrefers to a role andRrepresents the set of all the roles.There are three kinds of roles and they are event generator role EvGenRole,event detector role EvDetRole,and response unit role ResUnitRole.EvGenRole generates suspicious events that come from users’behaviors,EvDetRole detects attacks,and ResUnitRolemakes a response according to the detected attacks.
An event generator role EvGenRole is defined as follows.
Definition 2’[1]:RoleEvGenRole:r::=〈n,I,Na,No〉,where
1)nis the ID ofr;
2)denotes a set of messages withMinbeing the collected network messages andMoutoutput messages to role EvDetRole;
3)Nais an ID set of agents that are playing EvGenRolerfor generating suspicious events;
(4)Nois an ID set of objects,including detecting environment,detecting roles,and detecting groups which can be accessed by agents playing EvGenRoler.
Others roles can be similarly defined as follows.
Definition 3[20]−[22]:group:g::=〈n,e,J〉,where
1)nis the ID ofg;
2)eis an intrusion detection environment,all agents ingwork under the samee;
3)Jis a set of tuples for identifying an agent and role,i.e.,
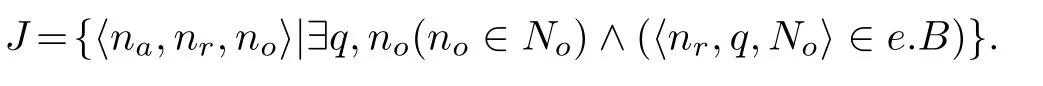
In this paper,Gdenotes the set of all groups,andgis a specific group.There are two kinds of groups:big and small ones.A big group is denoted by BigGroup,while a small one is denoted by SmallGroup.There are three BigGroups and they are EvGenGroup,EvDetGroup,and ResUnitGroup.EvGenGroup is used to produce suspicious intrusion events,EvDetGroup detects these suspicious events,and ResUnit-Group responds to detection results.
A BigGroup contains some SmallGroups.In this paper,EvGenGroup contains four SmallGroups and they are sensor SmallGroup EvGenGroupsen,decoding SmallGroup EvGenGroupdecod,filtering SmallGroup EvGenGroupfilt,and generating suspicious intrusion event SmallGroup EvGenGroupgen.EvDetGroup has four SmallGroups and they are SmallGroup EvDetGrouptcpfor detecting TCP attacks,SmallGroup EvDetGroupudpfor detecting UDPattacks,SmallGroup EvDetGroupicmpfor detecting ICMP attacks,and SmallGroup EvDetGroupcontfor detecting contents.ResUnit-Group can have one or more groups according to network traffic.
Definition 4[20]−[22]:agent:a::=〈n,ca,s,Nr,Nbg,Nsg〉,where
1)nis the ID of agenta;
2)cais a class describing the properties of agenta;
3)sis a data structure that includes attributes or states;
4)Nrdenotes a set of roles that the agent is playing;
5)Nbgdenotes a set of IDs of BigGroups;
6)Nsgdenotes a set of IDs of SmallGroups.
It should be noticed that the potential abilities of an agent in a BigGroup are stronger than that of an agent in a SmallGroup.
There are two classes of agents.One belongs to a BigGroup and the other belongs to a SmallGroup.The former can play different roles in the same BigGroup and the latter can enact only the role in the same SmallGroup.
Definition 5[20]−[22]:environment:e::=〈n,B〉,where
(1)nis the ID ofe;
(2)Bis a set of tuples,i.e.,wherenris the ID of a role,qis described by(l,u)and tells that how many agents can play this role ineand how many agents may play the same rolering.SetNoconsists of the objects accessed by the agents that playr.|No|denotes the number of resources visited by agents.
Here,edenotes an intrusion detection environment.The symbolqis a range,such as(3,8),(10,20),(7,7),or(2,60).
IV.INTRUSION DETECTION COMPONENTS
According to the CIDF,an intrusion detection system(IDS)is composed of an event generator,an event detector,a response unit,and an event database.Except the event database,the others are defined as three kinds of roles:EvGenRole,EvDetRole,and ResUnitRole.Role EvGenRole corresponds to the event generator,role EvDetRole corresponds to the suspicious event detector,and role ResUnitRole states the response unit.
A.Event Generator and Event Generation Role
The function of an event generator in CIDF is mainly composed of a sensor,a decoder,a filter,and an event generator.Because event generation role EvGenRole expresses functions of the eventgenerator,it includes sensing,decoding,filtering,and generating suspicious events.Then,role EvGenRole is divided into role EvGenRolesen,role EvGenRoledecod,role EvGenRolefilt,and role EvGenRolegen.They are in charge of gathering network packages,decoding,filtering,and generating suspicious events,respectively.Their construction is shown in Fig.1.

Fig.1.Role,group about event generator.
In Fig.1,every role is played by some agents.All of the agents that play the same role form a group.EvGenGroup contains four small groups:EvGenGroupsen,EvGenGroupdecod,EvGenGroupfilt,and EvGenGroupgen.Because agentain EvGenGroupsencollects data from the Internet,its data structure includes all fields of the network packet.In this paper,a small group includes a role and its agents,e.g.,EvGenGroupsenhas many sensors.
B.Event Detector and Event Detection Role
The event detector in CIDF is designed to detect suspicious events generated by event generators.The function of the event detector is defined as role EvDetRole such that Role EvDetRole is responsible for detecting suspicious events.
Three kinds of suspicious event detector roles are generated according to the network protocols TCP,UDP,and ICMP.These three roles are role EvDetRoletcp,role EvDetRoleudp,and role EvDetRoleicmp.They are responsible for detecting TCP suspicious events,UDP suspicious attacks,and ICMP suspicious attacks,respectively.In addition,role EvDetRolecontdetects the content of the network packet extracted.The content feature denotes data content in a network packet,including a user’s messages,the protocol of the application layer,the root user or administrator information,and the important data.The structure of event detectors is shown in Fig.2.
In Fig.2,EvDetGroup includes four SmallGroups:EvDetGrouptcp, EvDetGroupudp, EvDetGroupicmp, and EvDetGroupcont.The detection role is played by some detection agents and a SmallGroup is composed of agents that play the same detector role.For example,EvDetGrouptcphas many agents that detect TCP attacks.
The creation of event detectors is presented in Section V.
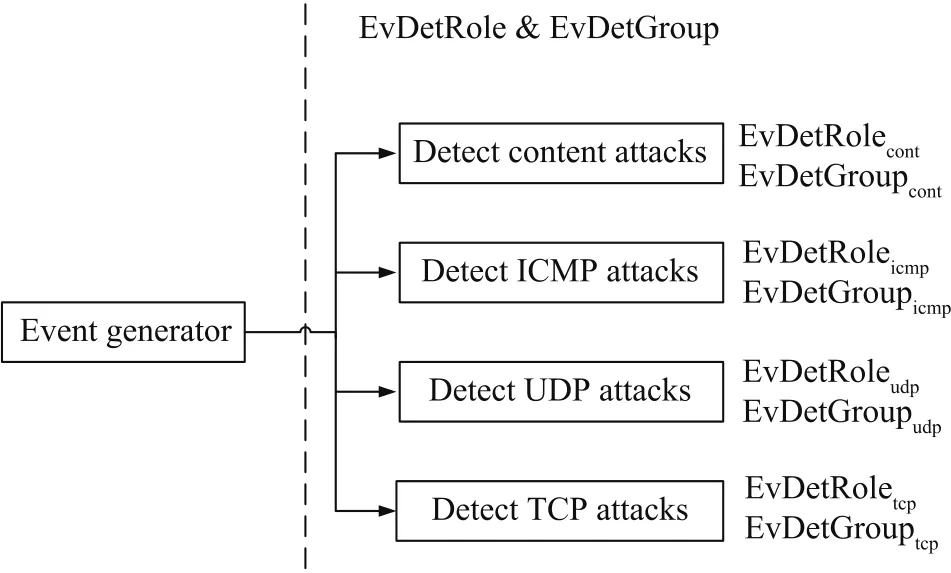
Fig.2.Role,group about event detector.
C.Response Unit and Its Role
The response unit is a component in the CIDF and makes corresponding responses according to the detection results.Role ResUnitRole isdefined as the requirement of the response unit.Many agents are assigned to play the role ResUnitRole.
D.Role and Group
The roles defined in this paper are listed in Fig.3 and groups are given in Fig.4.
E.The Collaboration Detection Architecture
A new collaboration intrusion detection framework is proposed in this section and a multi-agent cooperative detection model is designed and implemented.This model includes four components:event generators,event detectors,a response unit,and a database.An event generator contains a sensor,a decoder,a filter,and a generator.An event detector includes a TCP detector,a UDP detector,an ICMP detector,and a content detector.The adaptive collaboration detection model is shown in Fig.5.It is abbreviated as CAIDM.
According to the E-CARGO model,these components are all taken as requirements and are defined as roles.There are three kinds of roles:event generator role EvGenRole,event detector role EvDetRole,and response unit role ResUnit-Role.In Fig.5,there are five kinds of detector roles:role EvDetRoletcp,role EvDetRoleudp,role EvDetRoleicmp,role EvDetRolecont,and role EvDetRolefc.These roles are used to detect TCP attacks,UDP attacks,ICMP attacks,the content of network packages,and fusion detection,respectively.The resultant detection messages are sent to the response unit and the database.
Each roleris played by some agents and the agents that perform the same task(a role)form a small group.In order to cope with different network traffics and environments,three kinds of detecting scales are introduced in the system,i.e.,small,middle,and large modes.These modes are used for diverse detection instances for various network traffics and an adaptive detection mechanism is required and implemented.
F.Role and Agent
There are three kinds of roles and they are EvGenRole,EvDetRole,and ResUnitRole.
Role EvGenRole is divided into role EvGenRolesen,role EvGenRoledecod,role EvGenRolefilt,and EvGenRolegen;Role EvDetRole falls into role EvDetRoletcp, role EvDetRoleudp,role EvDetRoleicmp,role EvDetRolecont,and role EvDetRolefc.
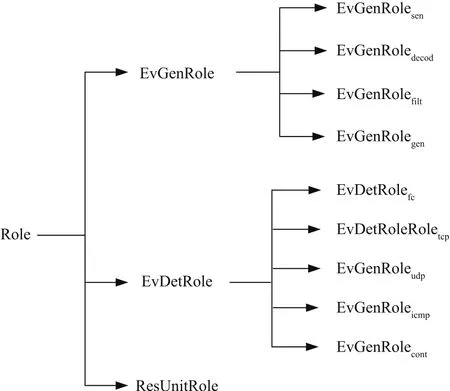
Fig.3.Roles and their relations.
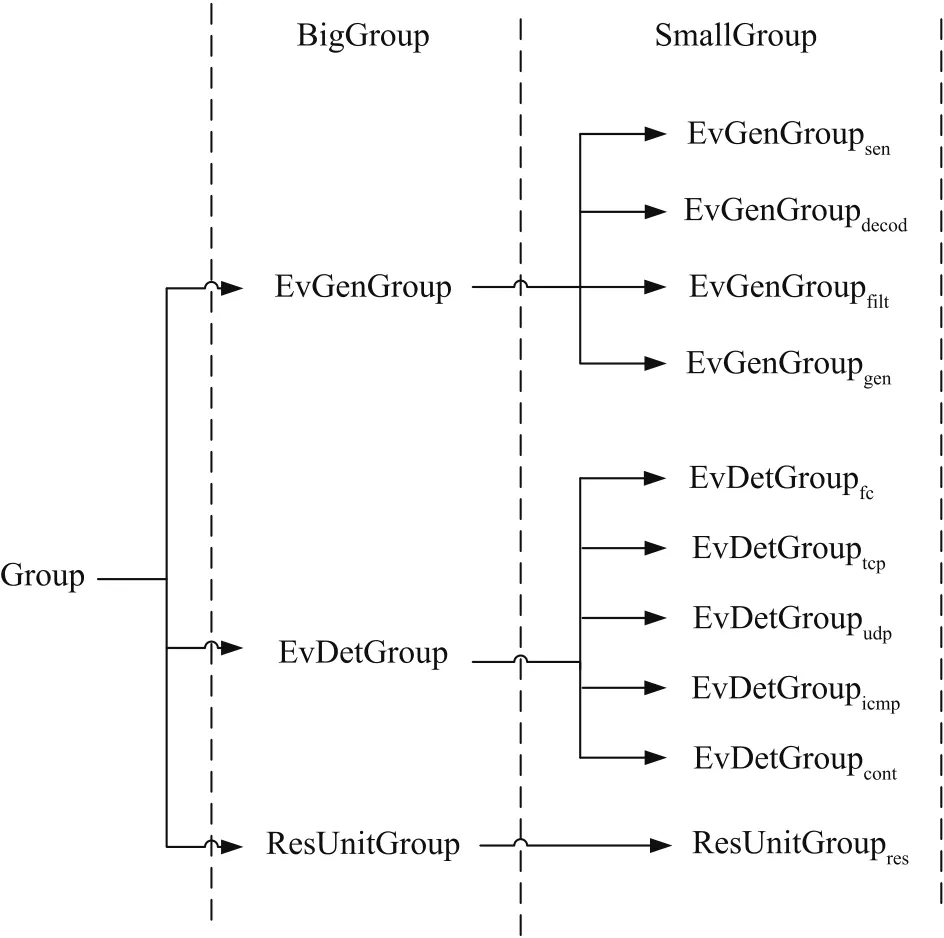
Fig.4.Groups and their relations.

Fig.5.The collaborative and adaptive intrusion detection model(CAIDM).
A rolercan be assigned to some agents.Agents that play the same rolerform a small group.For example,an EvGenRolesenrsenis defined as for collecting data from network packet and all agents that play EvGenRolesenrsenmust extract data from network packet.These agents form SmallGroup EvGenGroupsengsen.
In the next section,the procedure of creating TCP detector is discussed.
V.BUILDING INTRUSION DETECTOR
Because TCP attacks are more frequent than others,building TCP detector is discussed in this paper.
There are five classes of suspicious event detector roles which are used to detect TCP attacks,UDP attacks,ICMP attacks,and contents of packages,and synthesize detections in the fusion center,respectively.These suspicious event detector roles are described below.Agents are created with each of them being composed of SVM s and DT.
A.SVM and Multi-Class SVMs
There are two major categories[2]of SVMs for solving multi-class problems:1)establishing a group of 2-class classifiers and 2)establishing amulti-class classifier.The former has many types,including 1-v-r(one-versus-rest),1-v-1(one versus-one),directed acyclic graph(DAG)SVM(large interval multi-class SVM classifier based on directed acyclic graph),the binary SVM,etc.
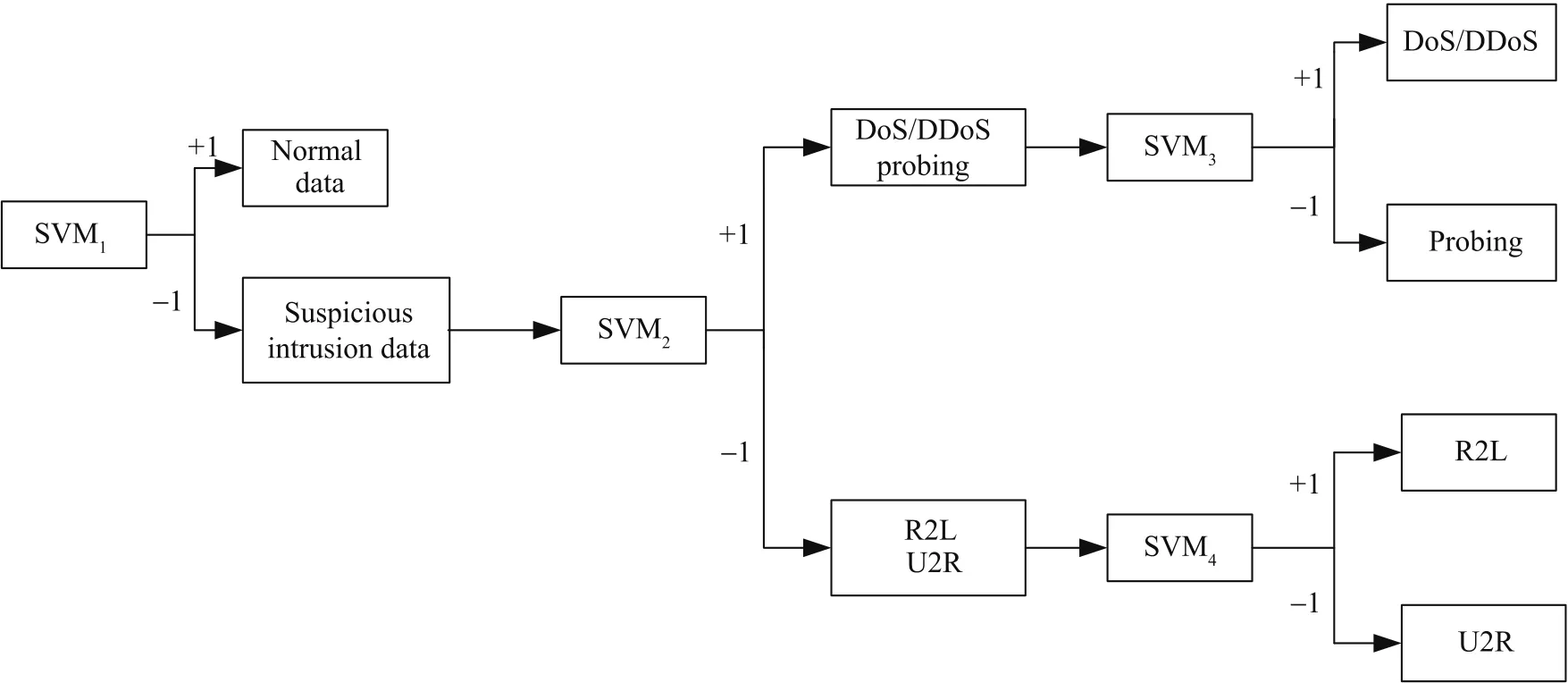
Fig.6.The collaborative intrusion detector based on SVM s and DT for TCP.
In this paper,a multi-class classifier of the 1-v-r type is used to perform the intrusion detection as a detector.It needs to establish many 2-class classifiers.After network packets are decomposed into four parts corresponding to the TCP,UDP,ICMP protocols,and content,a group of 2-class classifiers based on SVM s and DTs are built to detect intrusions.Four 2-class classifiers are created to implement such a detector for TCP protocol.
B.Data and Suspicious Event Detector
A network data stream can be decomposed into three sets:the TCP data,the UDP data,and the ICMP data.Four kinds of detector roles are designed and implemented,and they are used to detect TCP,UDP,ICMP,and content-based attacks,respectively.According to the DT method,building these intrusion detectors includes two steps:modeling and testing.The preprocessed historical data(network data or experimental data)is decomposed into training data and testing data.The former(training data)is applied to produce the detection agents based on SVMs and DTs,and the latter(testing data)is used to assess these detection agents.
KDD CUP 1999[3],[17],[18]decomposes attacks into four types,including probing,denial of service(DoS),remoteto-local(R2L),and the user-to-root(U2R).A probing attack acquires objective services provided by the object,including possible bugs,related system information,and so on[17],[18].DoS attacks damage the target system and stop normal services by interrupting normal service delivery,causing a system collapse or shutdown[17],[18].R2L and U2R are attacks that illegally promote users’privileges[17],[18].The former obtains the permission to enter the target system by stealing user information.The latter upgrades one’s permission by changing common users’privileges in the system or changing root authority.Thus,tasks for ensuring the security of a system are very complicated,especially when attacks are combined to form collaborative attacks.Each record in KDD CUP 1999 has 41 attributes,of which 34 attributes are continuous and seven are discrete.Before the experiments,the discrete attributes are converted into numerical ones by counting the frequency of their values.All data is turned into the standard and available format.
To build TCP detectors,a collaborative and adaptive intrusion detection model is designed based on SVM sand DTsand implemented in this text.A TCP detector has three layers and the detector at each layer can be defined as a role.Every role asks agents to perform it.Then,many 2-class SVM explorers are set up,and each 2-class SVM is a 1-to-rest classifier.The number of classifiers is related to the network traffics and the detection task load.Agents that detect TCP attacks are adaptive and are activated by the agent playing the manager role.
In order to make detection faster and more efficient,normal data is first separated from suspicious data.By doing so,one can reduce the amount of data to be further dealt with.In addition,we try to decrease the output of a 2-class SVM detector.Then,an optimized,cooperative,and adaptive intrusion detection model based on SVMs and DT is designed and implemented for a TCP detector as shown in Fig.6.At each layer,a detecting role is required and we build a 2-class SVM or more to play the role.When the network traffic is heavy,many agents are required to perform the same event detector role at the same layer.These agents form a small group.In Fig.6,SVM1decomposes the whole data set into normal and suspicious attack data,and performs the role at layer 1.At layer 2,SVM2separates the suspicious intrusion data into two parts.One of them includes DoS,DDoS,and probing attacks,and the other contains R2L and U2R attacks.Here,SVM2plays the role at layer 2.There are SVM 3 and SVM4at layer 3.SVM3is assigned to detect probing and DoS/DDoS attacks,while SVM4is used to detect U2R and R2L attacks.Similarly,SVM3and SVM4play two roles at layer 3,respectively.An optimized DT-based detector is shown in Fig.6.
C.Building SVM and DT-Based Detection Agent
Building a detection agent based on SVM needs to train and test it iteratively.After preprocessing,data is decomposed into four data sets corresponding to the network protocols TCP,UDP,ICMP,and content.Each data set is also divided into training and testing data.
Building a TCP detector is as follows.A group of SVM detectors is set up by using the training samples with the class label,i.e.,four2-class classifiers which are used to detect the normal data,the DoS/DDoS attacks,the probing attacks,and R2L or U2R attacks.In this paper,these detectors are all defined as roles in the E-CARGO model,and these roles require agents to play.When SVM s are used to implement these agents,some support vectors and the homologous parameters in the model should be brought out and be produced.
When testing,the testing data is delivered to four 2-class SVM classifiers according to TCP,UDP,ICMP protocols,and content,respectively.By comparing the classification results with testing data with the known class label,we can evaluate the detection accuracy of these SVM detectors.The SVM that meets the detection accuracy requirements is the expected detection agent.Hence,we build four 2-class SVMs:SVM1,SVM2,SVM3,and SVM4as shown in Fig.6.
VI.ADAPTIVE MECHANISMS
Due to different network environments,huge varieties of intrusions,high-speed traffics,and the big data generated from the network and so on,to be effective,an intrusion detection system should be flexible.The intrusion detection system needs to gather data from different networks and hosts.Moreover,it is required that the system should detect attacks on time and respond in a very short time.Because a single intrusion detector is difficult to provide enough security protection for a complicated network,a multi-agent collaborative and adaptive intrusion detection method is used to overcome the disadvantage of a single detector system.
In addition,to make such a system efficient within an acceptable cost,intrusion detection needs to be adaptive according to different network conditions.An adaptive mechanism of a collaborative intrusion detection model is proposed in this paper.All the components of CAIDM are defined as roles of the E-CARGO model and each role is assigned to some agents.The agents playing the same role form a group.
A.Local and Global Agent
Definition 6:Local agent:supposepis an agent and belongs to a small group,thenpis a local one and can play the role corresponding to this small group only.
Definition 7:Global agent:supposepis an agent and belongs to a big group,thenpis a global one and can play any role corresponding to the big group.
Here,two theorems are given below.
Theorem 1:Letpbe an agent,SG is a small group and BG is a big group.Then,we have
1)∀p∈EvGenGroup⇒p∈EvGenGroupsen∧p∈EvGenGroupdecod∧p∈EvGenGroupfilt∧p∈EvGenG roupgen.
That is:
pcan play any role in EvGenRole.
2)∀p∈EvDetGroup⇒p∈EvDetGrouptcp∧p∈EvDetGroupudp∧p∈EvDetGroupicmp∧p∈EvDetGroupcont.
That is:
pcan perform any role in EvDetRole.
Theorem 2:Letqbe an agent and suppose BG be a big group,SG1and SG2be two small groups.Then,if SG1/=SG2,we have

For example,∀a2∈EvGenGroupsen,we havea2/∈EvGenGroupdecod∧a2/∈EvGenGroupfilt∧a2/∈EvGenGroupgen.The others are similar.
B.Network Traffic and Levels
For convenience,we set three different levels to detect attacks under the current network condition in this paper.In fact,because E-CARGO model is referred to our model,any scheduling can be applied by agent evaluation and role assignment.
There are three levels and they are called idle,normal,and busy level.
If the network condition is normal,we use a group of agents to detect attacks.If the network condition is busy,more agents than that in normal condition are generated to detect attacks.While the network condition is idle,fewer agents are required.
Tland Thare set as thresholds to define the levels.We have the definition below.
Definition 8:Network traffic:suppose Tl,ThandXbe real numbers,Xdenotes the network traffic,and 0≤Tl<Th,then,
1)Normal:The network traffic is normal,if Tl≤X<Th;
2)Idle:IfX<Tl,then the network traffic is idle;
3)Busy:IfX≥Th,then the network traffic is busy.
There are three scheduling cases in this paper and they are described by the following theorem.
Theorem 3.Suppose Tl,ThandXbe real number,Xdenotes the network traffic,and 0≤Tl<Th.We have
Case 1:WhenXis less than Tl,a few of roles are required,and a small scale scheduling is executed.
Case 2:WhenXis between Tland Th,a medium number of roles is required,and a middle scale scheduling is performed.
Case 3:WhenXis greater than Th,plenty of roles are required,and a big scale scheduling is activated and carried out.
Therefore,network conditions and suspicious behaviors determine the number of agents being active ata layer,which makes it possible for the E-CARGO model to activate or shut down an agent independently,leading to a self-adaptive agent action.
C.Scheduling Policy
Because there are big and small groups,some agents belong to big groups,while some others belong to small ones.An adaptive scheduling plan is proposed as follows.
Let SG1denote a small group,BGla big group,SGl-idle a set of agents that are idle,SRla role in SGl,andalan agent.Then,we have the scheduling policies as follows.
Policy 1:If SG1is busy,then
ifandalcan play SRl,thena1is assigned to SRlandal∈SGl;
else if SGl-idle=φ,and∃al∈BGlandalcan play SRl,thenalis assigned to SRlandal∈SGl;
else no assignment happens.
Policy 2:If SG1is not busy,then
ifis idle,thenalis recovered,andal∈SGl-idle oral∈BGl.
Policy 3:Ifqdenotes aggregation requirements,Tland Thare two thresholds such that 0≤Tl<Th.We have:
1)ifq<Tl,then the small scale scheduling is performed;
2)if Tl≤q<Th,then the middle scale scheduling is executed;and
3)ifq≥Th,then the big scale scheduling is carried out.
D.EvGenRole and EvGenGroup
EvGenRole acts as an event generator role that requires agents to perform.EvGenRole contains a sensor role,a decoding role,a filtering role,and a generating event role.EvGen-Group denotes an active generator group and is a big group.It includes four members:EvGenGroupsen,EvGenGroupdecod,EvGenGroupfilt,and EvGenGroupgen.EvGenGroupsenrequires agents playing the sensor role,EvGenGroupdecodthe decoding role,EvGenGroupfiltthe filtering role,and EvGenGroupgenthe generating event role.
Some agents are global and belong to a big group EvGen-Group,while the others are local and belong to a small group.One agent in a small group must be in one of the four small groups:EvGenGroupsen,EvGenGroupdecod,EvGenGroupfilt,and EvGenGroupgen.
E.EvDetRole and EvDetGroup
EvDetRole is a suspicious event detector role,and EvDetRole includes four kinds of roles.Agents playing EvDetRole form a big group EvDetGroup.There are five detector smallgroups in big group EvDetGroup.These groups are EvDetGrouptcp, EvDetGroupudp, EvDetGroupicmp,EvDetGroupcont,and EvDetGroupfc.EvDetGrouptcpholds agents that are in charge of detecting TCP attacks,EvDetGroupudpowns agents that detect UDP attacks,EvDetGroupicmpaccommodates agents that find out ICMP attacks,EvDetGroupcontcontains agents that detect content attacks,and EvDetGroupfcincludes fusion agents that fuse the result of detectors.
F.Agent and Group
Agents for the same role form a small group.The suspicious behavior detector role is assigned to agents.Especially,Fig.6 indicates that the data processed by group SVM1is far more than that by group SVM2,the data processed by group SVM2is more than that by group SVM3or group SVM4,and the data processed by group SVM4is the least.Therefore,we decompose the layers into three levels as listed in Fig.6.From the top to bottom,each layer represents the data dealt with by groups SVM1,SVM2,SVM3,and SVM4,respectively.At the top,group SVM1possesses the most number of agents for the largest gathered data.The next layer is group SVM2,then group SVM3and group SVM4is at the bottom.
The actions of agents are all adaptive.The group evaluation and role assignment are carried out by the scheduling process.
The scheduling process executes the scheduling plan made in advance according to Definition 8 and the three policies.
Moreover,some agents are created to perform the response unit role.These agents implement the functions of the response unit role and fulfill the response tasks.
G.Role,Group,and Communication
Communications among components in CIDF are implemented based on groups.Communications are divided into three types that happen between two SGs,between an SG and a BG,and between two BGs.Communication between two SGs is from one small group to another small group,such as from SG EvGenGroupsento SG EvGenGroupdecod,from SG EvGenGroupdecodto SG EvGenGroupfilt,and from SG EvGenGroupfiltto SG EvGenGroupgen.The second type is from a small group to a big group or from a big group to a small group,such as from SG EvGenGroupgento BG EvDetGroup,or from BG EvDetGroup to SG EvDetGrouptcp.The last one is from a big group to another big group,such as from EvDetGroup to ResUnitGroup.
The data format of communication is user datagram in TCP/IP.The specification,rule,and mode of the communication are defined in the specification of roles,and the input and output specification of roles express the requirement of the communication.The input specification describes the criterion that a receiver receives and the output depicts the specification that a sender sends.A ll of the communications happen between two groups.
This kind of communication efficiently decreases transferring data among components.Hence,the traffic in IDS is reduced.
VII.EXPERIMENT AND RESULT ANALYSIS
The operating system of the experimental computer is Windows 7 with 64bytes.The CPU is Intel(R)Core(TM)i3-2130CPU@3.40GHz,and its RAM is 4.00GB.The experiment software is MATLAB 2012a.
A.Data Source and Feature Extraction
The experimental data is extracted from KDD CUP 1999[3],[17],[18].There are over 212960 records for testing,while there are over 467420 records for training.There are 24 types of attacks in the training set and 14 new attacks are added into the testing set to reinforce the effort.These total 38 attacks are divided into four categories according to their attack type:Probing,DoS,R2L,and U2R.A whole TCP session is regarded as a connection record.Each record contains four types of attribution collections:basic features,host-based traffic features,time-based traffic features,and content features.
In the training stage,the training data in the KDD CUP 1999 is divided into 46742 groups,each group possesses10 records.A record is extracted from a group and is used as a training sample.The testing data is similar and 21296 groups are generated.21296 records are extracted from the testing data.Especially,a multi-feature classification method is adopted to build TCP,UDP,ICMP,and content-based detection agents in this paper,since a single attribute is difficult to discriminate complicated attacks.We have the following:
1)32 selected attributes are used to generate a TCP attack detection agent;
2)21 extracted attributes are used to produce a UDP attack detection agent;
3)18 chosen attributes are used to detect ICMP attacks.
B.The Results and Analysis
The candidates of the training and testing data are exhibited in Table I.Experimental results list in Table II.

TABLE I DISTRIBUTION OF THE RECORDS

TABLE II EXPERIMENTAL RESULTS
From Tables I and II,we have the following conclusions:
1)The training time of UDP detector is the shortest,that of ICMP goes after,and that of TCP is the longest.
2)The number of detecting UDP attacks is the lowest,that of TCP goes after,and that of ICMP is the highest.
3)The detecting accuracy is directly related to the number of attack samples in the training data set.
4)23382 ICMP training samples contain 23332 attack samples.The proportion of ICMP attack samples is99.7862%.
5)14313 TCP training samples contain 9203 attack samples.The proportion of TCP attack samples is 64.2982%.
6)9047 UDP training samples only have 865 attack samples.The proportion of UDP attack samples is 9.5612%.
7)The detecting accuracy of new,unknown,and abnormal attacks is low.When the attack samples of the testing data set are greater than that of the training data set,the detecting rate is lower.
Here,we compare the detection accuracy of the collaborative and adaptive intrusion detection model(CAIDM)with that of a set of a single SVM detector(they are composed of a set of SVM detectors,every SVM detector solely detects suspicious data in different levels.)Their detection results are listed in Table III.
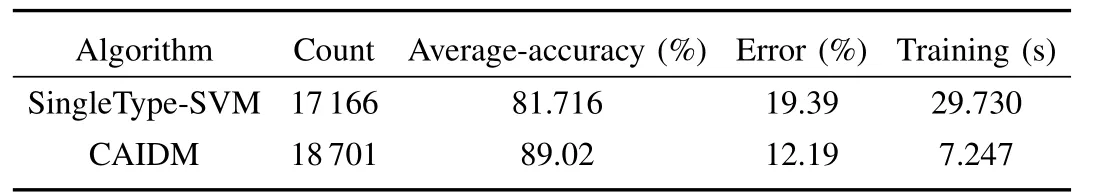
TABLE III COMPARISON BETWEEN CA IDM AND SINGLE SVM DETECTOR
The total records correctly detected by CAIDM are:2544+1994+1+12+120+8809+196+35+83+4823+84=18701.
The total test records are:4700+11295+5012=21007 and the total detection accuracy is:18701/21007=89.02%.
The total records correctly detected by a set of a single SVM detector are 17166;and the detection accuracy rate is:17166/21007=81.716%.
In addition,the training time of a set of a single SVM detector is about 29.730s,while the training time of the CAIDM only requires 7.247 s.The above results reveal that the CAIDM based on 2-class SVMs and DTs is better than a set of a single SVM detector in terms of both the training time and the detection accuracy.
C.Live Detection
In a real network environment,detection data comes from current network packets.TCP/IP network packets can be decomposed into four parts:TCP,UDP,ICMP and application layer protocol.TCP means connection-oriented services,UDP means connectionless datagram services,and ICMP is the internet control message protocol.Three intrusion detectors are built according to TCP,UDP,and ICMP protocols.Furthermore,the content-based detector is built to cope with application layer protocols.A group of agents that play detector roles are created,and these data are detected by three intrusion detectors.
V III.CONCLUSION
In this paper,a collaborative and adaptive intrusion detection method based on 2-class SVM s and DTs is proposed.A detection model called CAIDM is created and implemented.The E-CARGO model is used as a tool for describing the intrusion detection and modeling.In this paper,roles,groups,and agents are all studied and applied,for instance,the response unit role,the suspicious event detection role,the generating suspicious event role,etc.A role is assigned to some agents.A group(SmallGroup)contains many agents that perform the same role.TCP/IP protocols can be decomposed into four categories:TCP,UDP,ICMP,and application layer protocols.These protocols include different attributes.A variety of intrusion detectors are designed and implemented.There are four types of SVM identification functions designed and implemented,and related agentsare created.These agents built by using different properties are applied to find out attacks for TCP,UDP,ICMP,and application layer protocols,respectively.The TCP detection agent is used as one example to explain the agent creation process.At last,the proposed method’s effectiveness is confirmed by experiments with the KDD CUP 1999 data set.Experimental results reveal that the optimized collaborative and adaptive intrusion detection model(CAIDM)based on 2-class SVM sand DTs is more accurate and efficient than the detector system with a set of single type SVM s.
[1]S.H.Teng,N.Q.Wu,W.Zhang,and X.F.Fu,“Cooperative intrusion detection based on object monitoring,”Acta Sci.Nat.Univ.Suny.,vol.47,no.6,pp.76−81,Nov.2008.
[2]E.Alpaydin,Introduction to Machine Learning.3rd ed.New York,NY,USA:The M IT Press,2014.
[3]S.H.Teng,H.L.Du,N.Q.Wu,W.Zhang,and J.Y.Su,“A cooperative network intrusion detection based on fuzzy SVMs,”J.Netw.,vol.5 no.4,pp.475−483,Jan.2010.
[4]F.J.Kuang,W.H.Xu,and S.Y.Zhang,“A novel hybrid KPCA and SVM with GA model for intrusion detection,”Appl.Soft Comput.,vol.18,pp.178−184,May2014.
[5]Y.H.Li,J.B.Xia,S.L.Zhang,J.K.Yan,X.C.Ai,and K.B.Dai,“An efficient intrusion detection system based on support vector machines and gradually feature removal method,”Expert Syst.Appl.,vol.39,no.1,pp.424−430,Jan.2012.
[6]S.M.H.Bamakan,H.D.Wang,Y.J.Tian,and Y.Shi,“An effective intrusion detection framework based on MCLP/SVM optimized by time varying chaos particle swarm optimization,”Neurocomputing,vol.199,pp.90−102,Jul.2016.
[7]A.A.Aburomman and M.B.Reaz,“A novel SVM-kNN-PSO ensemble method for intrusion detection system,”Appl.Soft Comput.,vol.38,pp.360−372,Jan.2016.
[8]S.W.Lin,K.C.Ying,C.Y.Lee,and Z.J.Lee,“An intelligent algorithm with feature selection and decision rules applied to anomaly intrusion detection,”Appl.Soft Comput.,vol.12,no.10,pp.3285−3290,Oct.2012.
[9]W.Y.Feng,Q.L.Zhang,G.Z.Hu,and J.X.Huang,“Mining network data for intrusion detection through combining SVM s with ant colony networks,”Future Generation Comput.Syst.,vol.37,pp.127−140,Jul.2014.
[10]G.Kim,S.Lee,and S.Kim,“A novel hybrid intrusion detection method integrating anomaly detection with misuse detection,”Expert Syst.Appl.,vol.41,no.4,pp.1690−1700,Mar.2014.
[11]S.J.Horng,M.Y.Su,Y.H.Chen,T.W.Kao,R.J.Chen,J.L.Lai,and C.D.Perkasa,“A novel intrusion detection system based on hierarchical clustering and support vector machines,”Expert Syst.Appl.,vol.38,no.1,pp.306−313,Jan.2011.
[12]U.Ravale,N.Marathe,and P.Padiya,“Feature selection based hybrid anomaly intrusion detection system using K means and RBF kernel function,”Procedia Comput.Sci.,vol.45,pp.428−435,Dec.2015.
[13]W.C.Lin,S.W.Ke,and C.F.Tsai,“CANN:An intrusion detection system based on combining cluster centers and nearest neighbors,”Know l.-Based Syst.,vol.78,pp.13−21,Apr.2015.
[14]A.Mitrokotsa,and C.Dimitrakakis,“Intrusion detection in MANET using classification algorithms:The effects of cost and model selection,”Ad Hoc Netw.,vol.11,no.1,pp.226−237,Jan.2013.
[15]S.Pastrana,A.Mitrokotsa,A.Orfila,P.Peris-Lopez,“Evaluation of classification algorithms for intrusion detection in MANETs,”Know l.-Based Syst.,vol.36,pp.217−225,Dec.2012.
[16]C.A.Catania,F.Bromberg,and C.G.Garino,“An autonomous labeling approach to support vector machines algorithms for network traffic anomaly detection,”Expert Syst.Appl.,vol.39,no.2,pp.1822−1829,Feb.2012.
[17]S.H.Teng,C.Y.Zheng,H.B.Zhu,D.N.Liu,and W.Zhang,“A cooperative intrusion detection model for cloud computing networks,”Int.J.Sec.Appl.,vol.8 no.3,pp.107−118,May2014.
[18]W.Zhang,S.H.Teng,H.B.Zhu,and D.N.Liu,“A cooperative intrusion detection model based on granular computing and agent technologies,”Int.J.Agent Technol.Syst.,vol.5,no.3,pp.54−74,Jul.2013.
[19]W.Zhang,S.H.Teng,X.F.Fu,J.H.Fan,Y.Teng,and H.B.Zhu,“A cooperative intrusion detection model based on granular computing,”inProc.17th Int.Conf.Computer Supported Cooperative Work in Design,Whistler,BC,Canada,2013,pp.325−331.
[20]H.B.Zhu and M.C.Zhou,“Efficient role transfer based on Kuhn-Munkres algorithm,”IEEE Trans.Syst.Man Cybern.A Syst.Hum.,vol.42 no.2 pp.491−496,Mar.2012.
[21]H.B.Zhu,W.Zhang,Y.Wang,J.X.Zhu,D.N.Liu,and S.H.Teng,“A role-permission assignment method of RBAC involved conflicting constraints under E-CARGO,”Int.J.Cognit.Inf.Nat.Intell.,vol.9 no.4,pp.49−64,Oct.2015.
[22]H.B.Zhu,D.N.Liu,S.Q.Zhang,Y.Zhu,L.Y.Teng,and S.H.Teng,“Solving the Many to Many assignment problem by improving the Kuhn-Munkres algorithm with backtracking,”Theor.Comput.Sci.,vol.618,no.C,pp.30−41,Mar.2016.
[23]X.J.Zhu.“Anomaly detection through statistics-based machine learning for computer networks,”Ph.D.dissertation,Univ.Arizona,Arizona,USA,2006.
杂志排行
IEEE/CAA Journal of Automatica Sinica的其它文章
- Encoding-Decoding-Based Control and Filtering of Networked Systems:Insights,Developments and Opportunities
- Internet of Vehicles in Big Data Era
- Residential Energy Scheduling for Variable Weather Solar Energy Based on AdaptiveDynamic Programming
- From Mind to Products:Towards Social Manufacturing and Service
- Analysis of Autopilot Disengagements Occurring During Autonomous Vehicle Testing
- A Methodology for Reliability of WSN Based on Software De fined Network in Adaptive Industrial Environment
