A Cross-Tenant RBAC Model for Collaborative Cloud Services
2019-07-18ZhengtaoLiuandJinyueXia
Zhengtao Liu and Jinyue Xia
Abstract: Tenants in the cloud computing environment share various services, including storage, network, computing, and applications.For better use of services in the cloud computing environment, tenants collaborate in tasks, resulting in challenges to the traditional access control.This study proposes a cross-tenant role-based access control (CT-RBAC) model for collaborative cloud services.This model covers the CT-RBAC0, CT-RBAC1, CT-RBAC2, and CT-RBAC3 models.The model not only extends the RBAC model in the multi-tenant cloud computing mode but also includes four types of authorization modes among tenants.Consequently, the role inheritance constraint is increased, and fine-grained authorization access among trusted tenants is realized.
Keywords: Cloud computing, multi-tenant, collaboration, fine-grained authorization.
1 Introduction
Cloud computing [Nist (2015); Wood, Ramakrishnan and Shenoy (2015)] is a mode that pays for usage.This mode provides useful, convenient, and on-demand network accesses into configurable computing resource-sharing pools (resources include network, server, storage, application software, and services).These resources can be offered quickly and require a few management works or interactions with service suppliers.With unique advantages, such as broadband internet, resource pool sharing, flexible configuration, service on demand, and pay for service, cloud computing can lower the maintenance costs of users for computing and storage and reduce the constraints brought by restricted storage and computing resources of users.
In the cloud computing environment, clients (tenants) deploy all services or data on the cloud computing platform of the cloud computing supplier, such that tenants share various services, including storage, network, computing and applications, thereby reducing the cost and increasing efficiency.Tenants are isolated mutually, presenting a challenge to their collaboration.Hence, the corresponding safety mechanism and system structure must be designed to protect the confidentiality, integrity, and usability of user data [Curry, Darbyshire, Fisher et al.(2010); Ghazizadeh, Zamani, Manan et al.(2013)].Access control protects information resources from illegal use and access by restricting the information access capability and scope of users.The access control technology under the traditional computing mode can effectively protect information resources from illegal access.Research on access control under the cloud computing environment has developed with cloud computing.Before cloud computing, numerous scholars have studied the access control problem in grids.Since grid technology was replaced by cloud computing technology, the research has shifted to the access control of cloud computing.Cloud computing features numerous safety problems.Thus, access control is the core content of cloud computing security.
2 State-of-the-art
Given that tenants share physical resources and the difficulty in achieving reliability of resources, tenants can gain useful information from the bottom physical resources through side channel attacks [Meghanathan (2013)].In addition, the deployment of access control strategies on a virtual machine might cause conflicts among multiple tenants accessing resources, thus resulting in unapproved information flow or information flow with incorrect authorization distribution on the physical host.In the cloud environment, communication among different tenants shall be guaranteed by access control.Moreover, each tenant possesses a unique access control strategy, which increases the complexity of access control on the entire cloud platform.
Different tenants can access different applications and computing resources on the same cloud server.Access control technology can be regressed to studies on the model to avoid access control failure.Many scholars have added multi-tenant technology into the traditional access control model to generate new access control models and strengthen the data access control of tenants.Yang et al.[Yang, Lai and Lin (2013)] proposed the multitenant role-based access control (RBAC) model that determines the identity and role of users through identity management and realizes the independence of application programs and data isolation through the access rights of tenants.Users in the cloud environment are divided into ordinary users and resource owners according to the structure of cloud computing.Users could only access corresponding resources upon authorization of resource owners [Tang, Wei, Sallam et al.(2012)].Li et al.[Li, Shi and Guo (2010)] suggested separating the security duty between the cloud service supplier (CSP) and the tenant (client) and proposed an access control model based on multitenants.In this model, CSP can add, delete and manage tenants in the cloud and process relevant security problems.The model manages the access control of tenants and assures the security of tenants through access control.Wang et al.[Wang, Wang, Guo et al.(2018)] proposes a data access control model for individual users.Through the semantic dependency between data and the integration process from bottom to top, the global visual range of inverted XML structure is realized.
She thinks of her father’s God and how she now feels that God abandoned her. All at once, a single tear makes a trail down her thin, drawn16 face. Then another and another, and she is crying. “Oh Daddy, they say I’ll never walk again! They’re the best and they say I’ll never walk. Daddy, what will I do?”
The above model realizes access control of multi-tenants but overlooks the collaboration of multiple tenants.The access control problems in collaboration have been extensively addressed in traditional environments.Various extensions of RBAC have been proposed to enable multi-domain access control [Cohen, Thomas, Winsborough, et al.(2002); Li, Zhang, Xu et al.(2009); Lin, Rao, Bertino et al.(2008); Zhang, Zhang and Sandhu (2006)].These methods must define the collaboration strategies of different domains by centralized means.However, users of cloud computing originate from different organizations and utilize independent management authorization platforms.Therefore, these methods cannot adequately adapt to the characteristics of cloud computing.
Current Infrastructure as a Service (IaaS) cloud platforms have their own authorization system, containing different access control policies and models.Clients with accounts in multiple cloud providers struggle to manage their rules in order to provide a homogeneous access control experience to users.Sette et al.[Sette, Chadwick and Ferraz (2017)] proposes a solution: an Authorization Policy Federation (APF) of heterogeneous cloud accounts.To realize collaboration among different tenants, Tang et al.[Tang (2013)] proposed the administration of a multi-tenant approval system (MTAS) in combination with the RBAC model.Trust conditions were added to the AMTAS model, which performs formal analysis of trust among different tenants, based on MTAS.Later, the MT-RBAC model was proposed based on AMTAS [Tang, Sandhu and Li (2015)].This model extends the traditional RBAC model, increases two built-in components (issuer and tenant), and realizes collaboration of different tenants by setting up the trust relationship among different tenants.The MT-RBAC model integrates three different tenant trust models, namely, MT-RBAC0, MT-RBAC1, and MT-RBAC2.MT-RBAC0 is the basic model and requires all trustors to gather all roles and expose corresponding authorization to the trustee.To restrict unnecessary authorization information of trustors, the MT-RBAC1 model divides the role set into two subsets, in which the public role is exposed to all trustees.The MT-RBAC2 model provides more detailed constraints and offers different role authorization sets according to the trust level of trustees.
5.He did not know how wisely God apportions riches and poverty:Tatar points out that this phrase was added by the Brothers (194). The change makes the tale less subversive19 (Tatar 194).Return to place in story.
Who can tell the despair which seized the poor maiden when she heard this news! As soon as she could speak she implored15 the Wind to do all he could to get the wedding put off for two or three days, for it would take her all that time to reach the palace of the king
Based on the MT-RBAC, a cross-tenant RBAC (CT-RBAC) model is proposed in this study.Based on the extensively used RBAC96 [Sandhu (1997)] (RBAC0, RBAC1, RBAC2, and RBAC3), the proposed CT-RBAC model is used to design the CT-RBAC0, CT-RBAC1, CT-RBAC2, and CT-RBAC3 models.Compared with the MT-RBAC model, the CT-RBAC model not only considers different types of authorization modes among different tenants, the exposure of users and role information in authorization, and management of role inheritance but also extends the RBAC model in the multi-tenant cloud computing mode.
3 Equations and mathematical expressions
The CT-RBAC model covers the unilateral trust relationships among different types of tenants.Trustors and trustees can set up flexible trust relationships according to practical demands.
After this the Prince again asked the aid of his friends the birds, and when they had assembled from all the country round he tied about the neck of each one a tiny lamp of some brilliant colour, and when darkness fell he made them go through a hundred pretty tricks before the delighted Potentilla, who clapped her little hands with delight when she saw her own name traced in points of light against the dark trees, or when the whole flock of sparks grouped themselves into bouquets48 of different colours, like living flowers
Definition 1:T refers to the set of all tenants, and the trust relationship of all tenants is a multiple-to-multiple relationship.For ∀ti, tj∈T, tiis the trustor, and tjis the trustee, which is denoted as ti◃tj.If tiand tjrepresent the same tenant, then ti≡ tj.
The backdoor opened. My husband walked outside. I love you, he said. I was wondering where you were. I chuckled11, as he came over and kissed me, then turned around and went back inside. Where s the quiet time? I asked God. My heart fluttered. There was no pain, only a beat that interrupted me yet again. This is impossible, I thought. There s no time to be still and to know that God is with me. There s too much going on in the world and entirely12 too much activity all around me.
The ∀ti, tj, tk∈T, and TT relationship includes the following properties:
(1) Self-inspective: ti◃ti
By the side of the pool stood the tree of beauty, with the talking bird on one of its boughs21; and she caught the bird, and placed it in a cage, and broke off one of the branches
To realize the fine-grained cross-tenant RBAC model for collaborative cloud services, the structure of the CT-RBAC model is designed first.Subsequently, the formal definition of the CT-RBAC model is provided, and model operations are defined.Finally, the model constraints are discussed.
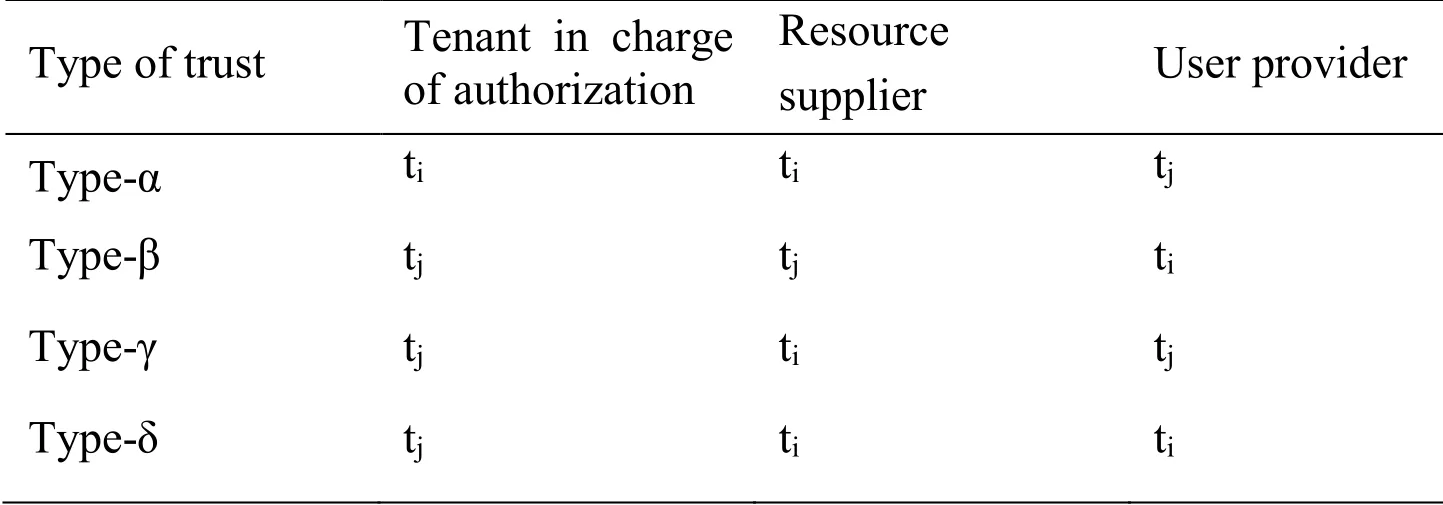
Table 1: Types of CT trust relationships
4 CT-RBAC model
Four types of trust relationships that can realize cross-tenant access are introduced[8], namely, Type-α, Type-β, Type-γ, and Type-δ.The trust relationship of tenants involves four key problems.(1) Who is responsible for managing the trust relationship? (2) Who is responsible for authorization behavior? (3) Who provides resources? (4) Who is the authorization object? Consideringin all four types, trustor tiis held responsible for the maintenance of trust relationship.Tab.1 shows the differences among the four types of trust relationships.
4.1 CT-RBAC structure
As shown in Fig.1, the CT-RBAC model comprises five parts, namely, tenants (T), users (U), roles (R), permissions (P), and sessions (S).Compared with the traditional RBAC model, the CT-RBAC model includes an additional tenant module and a built-in tenant attribute in U, R, and P for constructing one-to-multiple role ownership (RO) relations between roles and tenants, one-to-multiple user ownership (UO) relations between users and tenants, and one-to-multiple permission ownership (PO) relations between permissions and tenants.In other words, users, roles, and permissions all belong to one tenant in the CT-RBAC model.
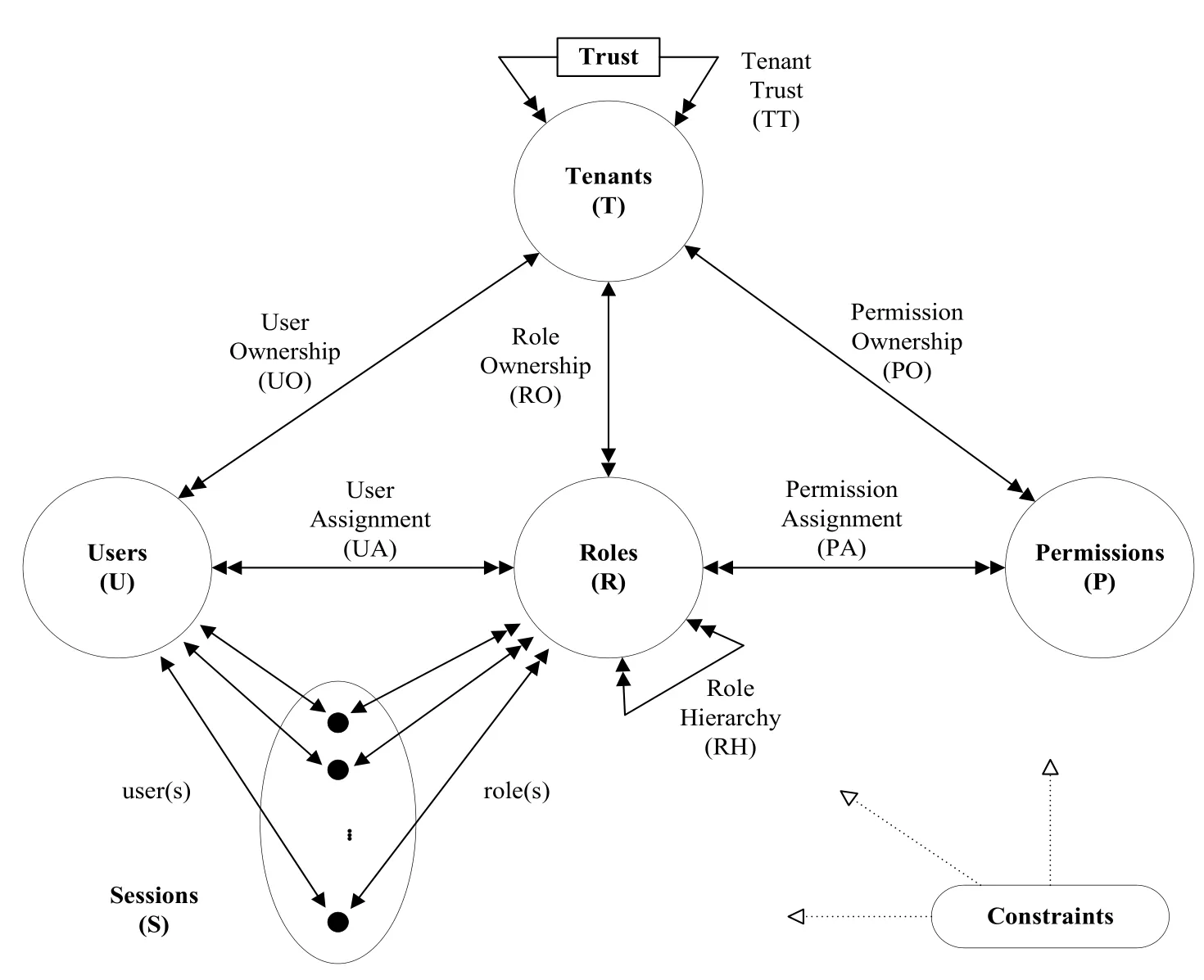
Figure 1: CT-RBAC model
Tenants (T): In the cloud computing environment, the CSP uses tenant as a logic unit to provide user storage, computing, network, and application services.T can be either an organization or a working unit.For instance, a tenant in the IaaS CSP offers 100 GB of memory space, and he/she can distribute the right to use memory space to internal users according to his/her needs.In the present study, the tenant set is denoted as T.
Users (U): User is a subject with access to resources in one tenant independently.A user might be a person, a machine, or a system.Users belong to one tenant, and one tenant can include multiple users.Here, the user set is denoted as U, and the relationship between users and tenants can be expressed by @.For example, user ujin tenant tican be expressed as ti@uj.
Roles (R): One role is the object in a tenant that can implement a specific work or responsibility.R represents qualification, rights, and responsibility.R belongs to any tenant, and one tenant can cover multiple roles.The role set is denoted by R, and the relationship between roles and tenants is expressed by #.For example, role rjin tenant tiis expressed as ti#ri.
● Hierarchical inheritance excludes the inheritance ring.
Sessions (S): Session is a temporary activity established by one user.A session is constructed when one user activates the subset of all roles.Each session is connected with single users, and each user can be related with one or multiple sessions.Sessions about the activated roles of users in the cross-tenant cloud computing environment may be included in more than one tenant.
The CT-RBAC model covers four models, namely, the CT-RBAC0, CT-RBAC1, CTRBAC2, and CT-RBAC3 models.These four models extend the RBAC0, RBAC1, RBAC2, and RBAC3 models, which are family members of the RBAC96 model.The formal definition of the CT-RBAC0 model is introduced as follows.
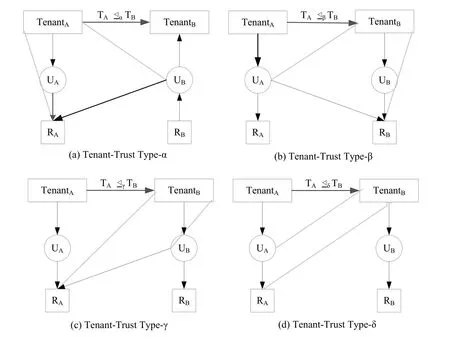
Figure 2: User-role assignment in peer-to-peer tenant-trust
4.2 Definition of models
The trust relationship among tenants must be set up to realize their colorations.The CRRBAC model introduces a trust relationship based on roles.Fig.2 shows the trust relationships among tenants.
Definition 2.The CT-RBAC0 model contains the following components:
What they said was very true; for a few days after the King s son caused it to be proclaimed, by sound of trumpet41, that he would marry her whose foot the slipper would just fit. They whom he employed began to try it upon the princesses, then the duchesses and all the Court, but in vain; it was brought to the two sisters, who did all they possibly could57 to thrust their foot into the slipper, but they could not effect it. Cinderella, who saw all this, and knew her slipper, said to them, laughing:
T, U, R, P, S, and TT are finite sets of tenants, users, roles, permissions, sessions, and trust relationship of tenants, respectively.
● UO⊆U×T represents the mapping of relationship between each user and the tenant (multiple-to-one relationship) and is also recorded as “@”.Accordingly, userOwner(u:U)→T is a function that maps the relationship between one user and the corresponding tenant.Here, userOwner(u) = t only when (u,t)∈UO.
Elizabeth and I are 18 now, and about to graduate. I think about our elementary-school friendship, but some memories have blurred. What happened that day in fifth grade when Beth suddenly stopped speaking to me? Does she know that I ve been thinking about her for seven years? If only we could go back, discover what ended our relationship.
● RO⊆R×T reflects the mapping of relationship between each role and the tenant (multiple-to-one relationship); it is denoted as “#”.Accordingly, roleOwner(r:R) →T is a function that maps the relationship between one role and the corresponding tenant.In the present study, roleOwner(r) = t only when (r,t)∈RO.
● PO⊆P×T implies the mapping of relationship between one permission and the tenant (multiple-to-one relationship), and it is also denoted as “%”.Accordingly, permOwner(p:P)→T is a function that maps the relationship between one permission and the corresponding tenant.permOwner(p) = t only when (p,t)∈PO.
● PR(ti,tj:T)→2Ris a function that maps the role set of tenant tiauthorized to tenant tj.
● PU(ti,tj:T)→2Uis a function that maps the user set of tenant tiauthorized to tenant tj.
● canUse(r:R)→2Tis a function that maps the set of tenants accessible by one role.Formally, canUse(r) ={t}∪{ti∈T|t◃ti∧r∈PR(t,ti)}, where (r,t) ∈RO.
The CT-RBAC0 model is the core model of CT-RBAC, and it allows setting up different types of trust relationships (Type-α, Type-β, Type-γ, and Type-δ) among different tenants.In authorization, the trust relationship is managed by trustors.The authorization party can assign roles to users according to different types of trust relationships, but he/she is forbidden to assign roles for CTs.
● UA⊆U×R is a multi-to-multi relationship between one user and one role.It reflects the role assigned by one user.(u,r)∈UA only when userOwner(u)∈canUse(r).
● PA⊆P×R is the multi-to-multi relationship between one permission and one role.It shows the permissions to assign roles.(p,r)∈UA only when permOwner(p)∈canUse(r).
● user(s:S)→U maps a function between each session and one user who is in the stated period of the session.
However, Lin Guirui, a professor of psychology9 at Capital Normal University, encourages students to face up to their poverty. It s not a shame to be poor, Lin said.
● roles(s:S)→2Ris the role set in the life span of each session.roles(s) ⊆{r∈roles|(user(s,r) ∈UA∧userOwner(user(s))∈canUse(r)}.
● canUse(u:U)→2Tis a function that maps the set of tenants accessible by one user.Formally, canUse(u) ={t}∪{ti∈T|t◃ti∧r∈PU(t,ti)}, where (u,t) ∈UO.
Type-α:timust set up a trust relationship between two tenants when ∀ti, tj∈T, and ti◃tjto realize CT access.tjsets the PU between two tenants, tisets the PR between two tenants, and tiaccomplishes the authorization process.
After walking for a great many days without being able to find any work, she came to a large farm where they were in want of a shepherdess, and engaged her gladly
Type-β:timust set up a trust relationship between two tenants when ∀ti, tj∈T, and ti◃tjto realize CT access.tisets the PU between two tenants, tjsets the PR between two tenants, and tjaccomplishes the authorization process.
Now listen towhat I tell you! You can snore; you are snoring the whole night, and Ihardly a quarter of an hour! And the blood rose to the head of theexcited criminal; he threw himself upon his comrade, and beat him with his clenced fist in the face
Type-γ:timust set up a trust relationship between two tenants when ∀ti, tj∈T, and ti◃tjto realize CT access.tjsets the PU between two tenants, tisets the PR between two tenants, and tjaccomplishes the authorization process.
Type-δ:timust set up a trust relationship between two tenants when ∀ti, tj∈T, and ti◃tjto realize CT access.tisets PU and the PU between two tenants, whereas tjaccomplishes the authorization process.
According to the analysis of the authorization of four types of trust relationships, the CTRBAC0 model can avoid leakage of user information and role information, thereby increasing system security.Tenants can manage the PU and PR after setting up the trust relationship.PU and PR are deleted automatically after the removal of trust relationship.Among the RBAC96 models, RBAC1 involves a role inheritance compared with the core model.Similarly, the CT-RBAC1 model adds role inheritance relative to the CT-RBAC0 model.The inheritance of the CT-RBAC1 model covers the role inheritance in one tenant and that among different tenants.The role inheritance in one tenant in the CT-RBAC1 model follows the inheritance method of the RBAC1 model.However, the role inheritance among different tenants mainly features the following problems.(1) Who is responsible for setting up the roles? (2) Who provides the inheriting role? (3) Who offers the inherited role? (4) Who is responsible for managing role inheritance? To prevent exposure of role information, all roles in CT-RBAC1 are accomplished in the same tenant rather than among different tenants.Among the four types of trust relationships, the CTRBAC1 model realizes CT role inheritance according to the following three rules.Rule 1: Resource supplier (role) offers the inherited role.
Rule 2: The user who provides the access resources offers the inheriting role.
Rule 3: The authorization person is responsible for role inheritance management.
Tab.2 presents the inheritance modes among tenants in the four types of trust relationships given ∀ti, tj∈T, and ti◃tj.
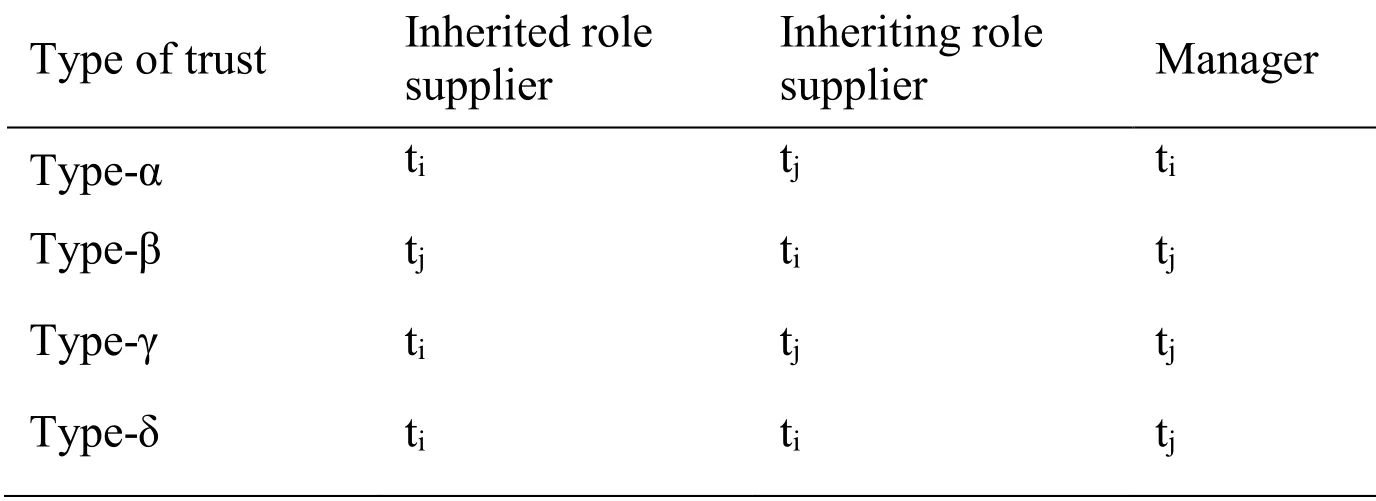
Table 2: CT role inheritance
To prevent exposure of information on the inheriting role and inherited role, the set of inheriting roles and set of inherited roles that must be respectively exposed shall be established in a different tenant.The set of inherited role overlaps with the PR.
When I passed the displayed of dog kennels2() , I heard a dog barking in a kennel1. This kennel was just a displayed to show customers, so why was there a dog inside? I bent3 down and had a look.
Definition 3.CT-RBAC1 inherits all components of CT-RBAC0 and meets the following conditions:
● PRH (ti,tj:T)→2Ris the function of the role set in tenant tithat can be inherited by the roles in tenant tj.
● RH⊆R×R is the partial ordering relations on a role set and is also called role inheritance and recorded as “≥”r.ri≥rjonly when roleOwner(ri) ≡roleOwner(rj)∨ (rj∈PR∧ri∈PRH).If one role can inherit another role, then this role and the inherited role are either in the same tenant, or the role is in the inheritable CT role set.Meanwhile, the inherited role must be in the set of tenants that can authorize the inherited role.
The CT-RBAC1 model allows tenants to realize role inheritance under four types of trust relationships.The setting of roles at CT inheritance must be achieved by tenant managers.The inheritance modes of the four types of trust relationships are introduced as follows:
Type-α:timust set the PR between two tenants, whereas tjsets the PRH between two tenants, and tiinherits roles when ∀ti, tj∈T and ti◃tjto realize CT access.
Type-β:tjmust set the PR between two tenants, whereas tisets the PRH between two tenants, and tjinherits roles when ∀ti, tj∈T and ti◃tjto realize CT access.
Type-γ:timust set the PR between two tenants, whereas tjsets the PRH between two tenants and inherits roles when ∀ti, tj∈T and ti◃tjto realize CT access.
The RBAC2 model involves additional constraints, including static responsibility separation and dynamic responsibility separation, based on the RBAC0 model.Unlike the RBAC2 model, the constraint of the CT-RBAC2 model exists not only in the same tenant but also between tenants.
Definition 4.Static responsibility separation.
Type-δ:timust set the PR and PRH between two tenants, whereas tjinherits roles when ∀ti, tj∈T, and ti◃tjto realize CT access.
where rs is a set of roles, t is a subset of rs, and n is a natural number higher than 2.The role set where rs lies not only covers roles in the same tenant but also roles that trust tenants can use.
Definition 5.Dynamic responsibility separation.
∀rs∈2R, n∈N, and (rs,n)∈D ⇒n≥2|rs|≥n.Moreover,
∀s ∈S, ∀rs ∈2R, ∀role_set ∈2R, n ∈N, (rs,n) ∈D, role_setrs, and
Definition 6: CT-RBAC2 inherits all components of CT-RBAC0 and satisfies the following conditions:
● It conforms to the static responsibility separation.
● It conforms to the dynamic responsibility separation.
Definition 7: Inheritance ring.Among mutually trusted tenants, the role inheritance among new tenants forms a ring-shaped inheritance structure, which is called the inheritance ring.
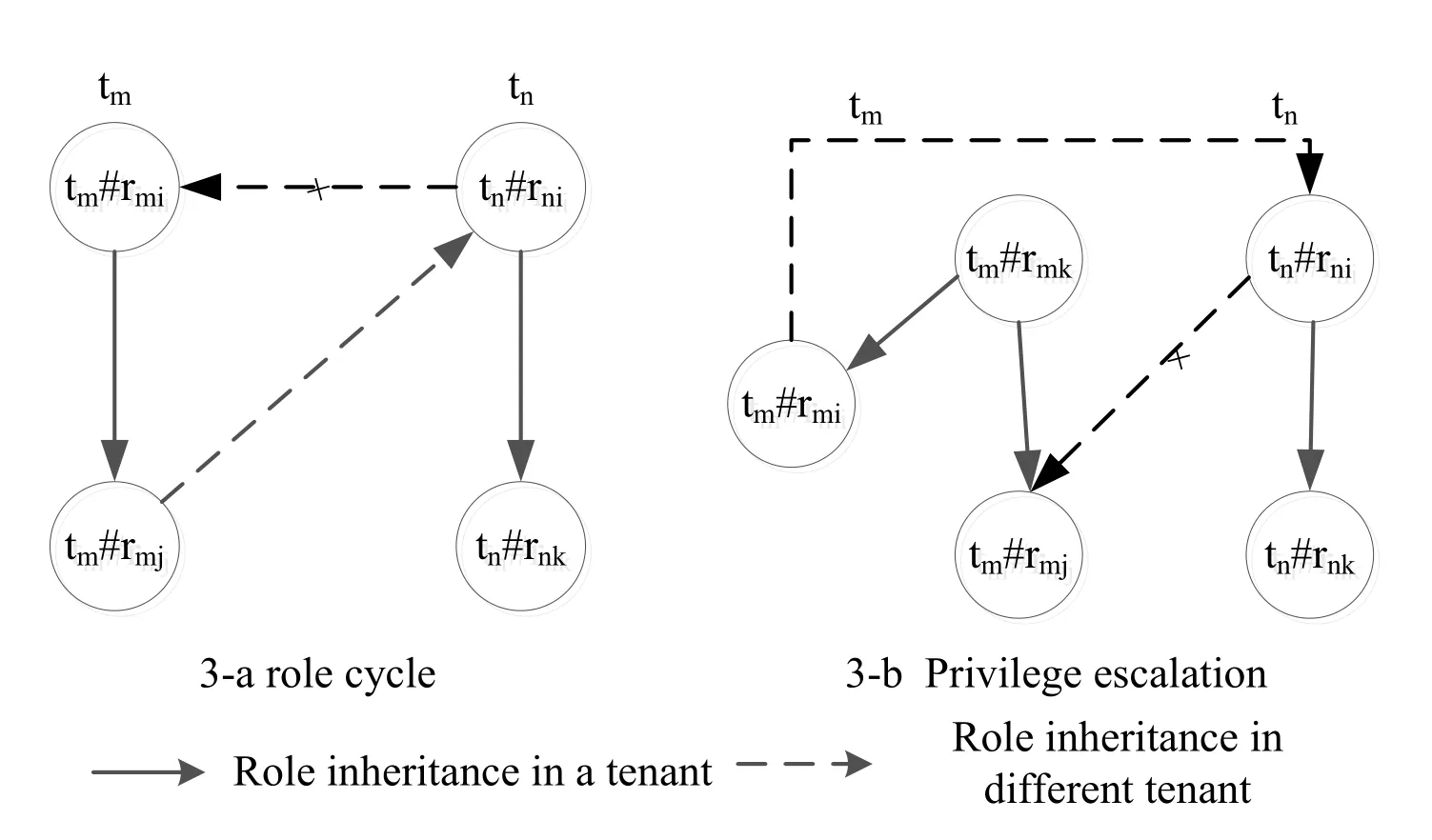
Figure 3: Conflict on role inheritance among different tenants
Fig.3(a) shows the inheritance ring: tm◃tnand tm#rmi≥tn#rni,tm#rmj≥tm#rmi.tn◃tmand tn#rni≥tm#rmj.The inheritance ring of different roles is formed due to the inheritance of trust relationships among different tenants.
Definition 8:Privilege escalation.A role gains the role accession rights, which are prohibited in the tenant, due to the role inheritance among different tenants.
Fig.3-b illustrates the privilege escalation.tm◃tnand tn#rni≥tm#rmi.tn◃tmand tm#rmj≥tn#rni.For role tm#rmj, a tenant gains access rights to roles tm#rmiin the same tenant due to the inheritance relationship among different tenants.
Definition 9:The CT-RBAC3 model covers CT-RBAC1 and CT-RBAC2.This model covers not only the hierarchical problems in CT-RBAC1 but also the constraint problems in CT-RBAC2.Hierarchical problems include the following:
Permissions (P): Permission refers to the access permission of one or multiple objects in one tenant to access in a specific mode.Permission is related with implementation details, such as reading and writing of a document in the system.Permission belongs to one tenant, and one tenant can cover multiple permissions.Here, a permission set is denoted by P, and the relationship between permissions and tenants is expressed by %.For example, permission pjin tenant tican be expressed as ti%pj.
The most beautiful landscapes looked like boiled spinach2, and the best people looked repulsive3 or seemed to stand on their heads with no bodies; their faces were so changed that they could not be recognised, and if anyone had a freckle4 you might be sure it would be spread over the nose and mouth
● Hierarchical inheritance features no privilege escalation.
The CT-RBAC0 model in the CT-RBAC model family is the basic model, and CTRBAC1 performs hierarchical management roles compared with the basic model.CTRBAC2 contains additional constraints relative to the basic model.CT-RBAC3 covers both CT-RBAC1 and CT-RBAC2.Specifically, CT-RBAC1 and CT-RBAC2 are incompatible.The relationships of the four models are similar with those of the family members of the RBAC96 model.
4.3 Operations of the CT-RBAC model
The operations of the CT-RBAC model mainly include the functions used by the manager of the cloud platform, the management function used by tenant managers, and the functions used by CT managers.The functions used by CT management determine who uses the functions according to the type of trust relationships among different tenants.Tab.3 lists the major operation functions of the models.
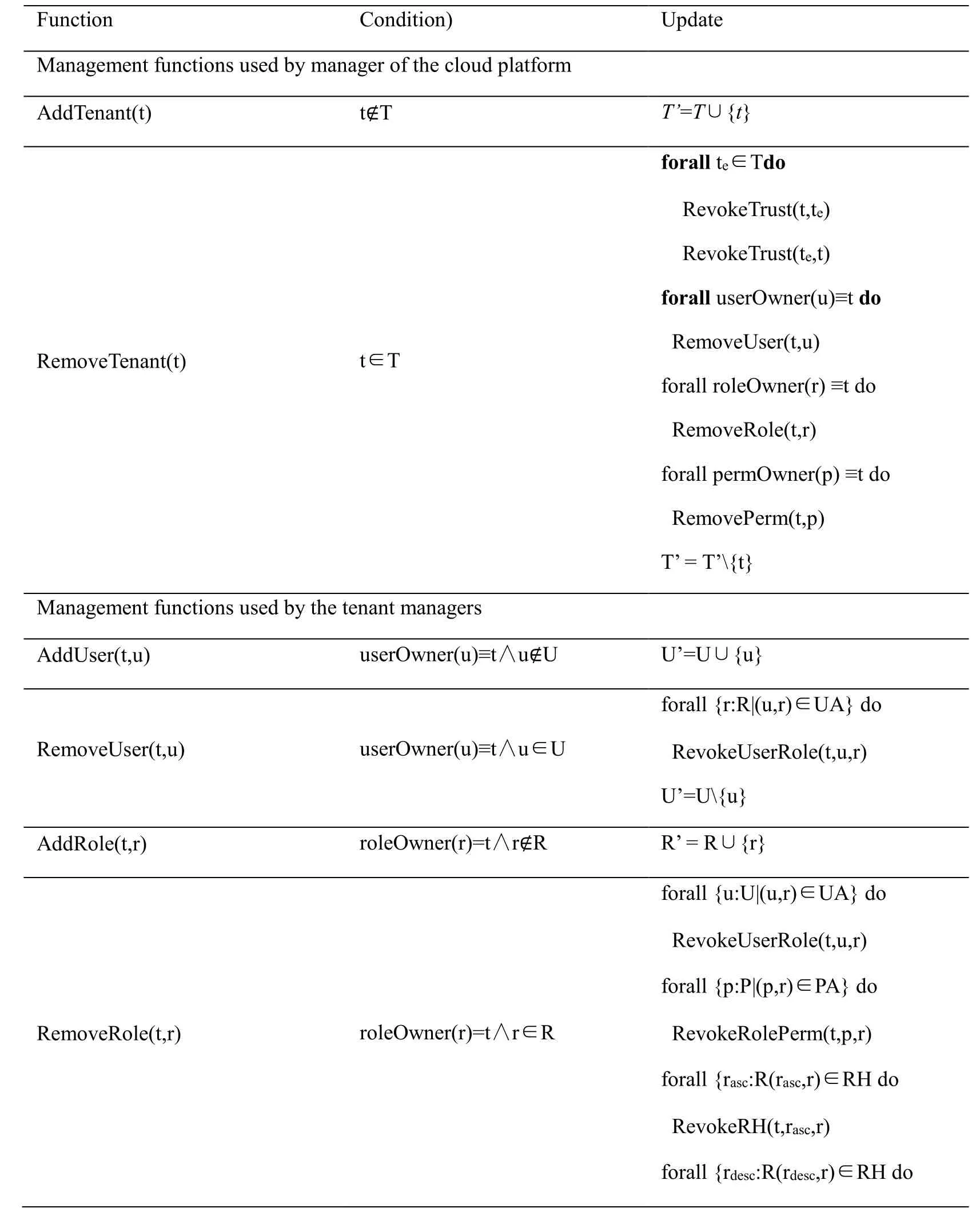
Table 3: Operation functions of the CT-RBAC model

RevokeRH(t,rdesc,r) R’ = R{r} AddPerm(t,p) permOwner(p)=t∧p∉P P’=P∪{p} RemovePerm(t,p) permOwner(p)=t∧p∈P forall {r:R|(p,r)∈PA} do RevokePerm(t,p,r) AssignUserRole(t,u,r) t=roleOwner(r)∧u∈U UA’ = UA∪{(u,r)} RevokeUserRole(t,u,r) t=roleOwner(r)∧u∈U∧(u,r)∈UA UA’ = UA{(u,r)} AssignRolePerm(t,p,r) t=permOwner(p) ∧ t ∈canUse(r) PA’=PA∪{(p,r)} RevokeRolePerm(t,p,r) t=permOwner(p) ∧ t ∈canUse(r) ∧(p,r) ∈PA PA’=PA{(p,r)} AssignRH(t,rasc,r) t=roleOwner(r) ∧ t ∈canUse(rasc) ∧canInherit(rasc,r) ≥’=≥∪{(rasc,r)} RevokeRH(t,rasc,r) t=roleOwner(r) ∧ t ∈canUse(rasc)∧rasc≥r ≥’=≥{(rasc,r)} Cross-tenant access function AssginTrust(t,te) te∈T TT’=TT∪{ (t,te)} RevokeTrust(t,te) te∈T∧(t,te)∈TT TT’=TT{ (t,te)} ExposeRole(t,te,r) (t,te)∈TT∧roleOwner(r)=t TTR’=TTR∪{(t,te,r)} RevokeExposeRole(t,te,r) (t,te)∈TT∧(t,te,r)∈TTR TTR’=TTR{(t,te,r)} ExposeUser(t,te,u) (t,te)∈TT∧userOwner(u)≡t TTU’ =TTU∪{(t,te,u)} RevokeExposeUser(t,te,u) (t,te)∈TT∧(t,te,u)∈TTU TTU’=TTU{(t,te,u)}
In cross-tenant access functions, the system can remove all access relations among tenants automatically when the tenant trust is revoked, including accessible users, accessible roles and authorization relationships of users.Similarly, the system removes authorization and inheritance of an accessible role automatically when this role is revoked from users.The rest cross-tenant access functions can be done in the same way.
5 Conclusions
Security is one of the core problems in cloud computing.In the present study, a CTRBAC model is proposed to solve authorization problems caused by the collaboration of tenants in the cloud computing environment.At the same time, the structure, formalized definition, and operations of the model are interpreted.The proposed model possesses the characteristic of inheriting the minimum privilege principles and responsibility separation rules of the RBAC model.The model also realizes the fine-grained CT RBAC model for collaborative cloud services by the exposure of user and role information within the authorization and role inheritance constraint.
Acknowledgement:This work was sponsored by Qing Lan Project of JiangSu Province and National Natural Science Foundation of China (No.61772280).The authors are grateful for the anonymous reviewers who made constructive comments and improvements.
References
Cohen, E.; Thomas, R.K.; Winsborough, W.; Shands, D.(2002): Models for coalition-based access control (CBAC).Proceedings of the Seventh ACM Symposium on Access Control Models and Technologies, pp.97-106.
Curry, S.; Darbyshire, J.; Fisher, D.W.(2010): Infrastructure Security: Getting to the Bottom of Compliance in the Cloud.The Security Division of EMC.
Ghazizadeh, E.; Zamani, M.; Manan, J.A.; Pashang, A.(2013): A survey on security issues of federated identity in the cloud computing.IEEE International Conference on Cloud Computing Technology & Science.
Li, X.Y.; Shi, Y.; Guo, Y.; Ma, W.(2010): Multi-Tenancy based access control in cloud.International Conference on Computational Intelligence and Software Engineering, pp.1-4.
Li, Q.; Zhang, X.; Xu, M.; Wu, J.(2009): Towards secure dynamic collaborations with group-based RBAC model.Computers & Security, vol.28, no.5, pp.260-275.
Lin, D.; Rao, P.; Bertino, E.; Li, N.; Lobo, J.(2008): Policy decomposition for collaborative access control.Proceedings of the 13th ACM Symposium on Access Control Models and Technologies, pp.103-112.
Meghanathan, N.(2013): Review of access control models for cloud computing.Computer Science & Information Science, vol.3, no.1, pp.77-85.
Nist, S.P.(2015): A NIST definition of Cloud computation.Communications of the ACM, vol.53, no.6, pp.50-50.
Sandhu, R.(1997): Rationale for the RBAC96 family of access control models.Proceedings of the 1st ACM Workshop on Role-Based Access Control.
Sette, I.S.; Chadwick, D.W.; Ferraz, C.A.(2017): Authorization policy federation in heterogeneous multicloud environments.IEEE Cloud Computing, vol.4, no.4, pp.38-47.
Tang, B.; Sandhu, R.(2013): Cross-tenant trust models in cloud computing.Proceedings of the 14th IEEE Information Reuse and Integration, pp.129-136.
Tang, B.; Sandhu, R.; Li, Q.(2015): Multi-tenancy authorization models for collaborative cloud services.Concurrency and Computation: Practice & Experience, vol.27, no.11, pp.2851-2868.
Tang, Z.; Wei, J.; Sallam, A.(2012): A new RBAC based access control model for cloud computing.International Conference on Advances in Grid and Pervasive Computing, pp.279-288.
Wang, M.; Wang, J.; Guo, L.; Harn, L.(2018): Inverted XML access control model based on ontology semantic dependency.Computers, Materials & Continua, vol.55, no.3, pp.465-482.
Wood, T.; Ramakrishnan, K.K.; Shenoy, P.; Merwe, J.V.D.; Hwang, J.et al.(2015): CloudNet: dynamic pooling of cloud resources by live WAN migration of virtual machines.ACM Transactions on Networking, vol.23, no.5, pp.1568-1583.
Yang, S.J.; Lai, P.C.; Lin, J.(2013): Design role-based multi-tenancy access control scheme for cloud services.International Symposium on Biometrics and Security Technologies, pp.273-279.
Zhang, Z.; Zhang, X.; Sandhu, R.(2006): ROBAC: scalable role and organization based access control models.International Conference on Collaborative Computing: Networking, Applications and Worksharing, pp.1-9.
杂志排行
Computers Materials&Continua的其它文章
- A DPN (Delegated Proof of Node) Mechanism for Secure Data Transmission in IoT Services
- A Hybrid Model for Anomalies Detection in AMI System Combining K-means Clustering and Deep Neural Network
- Topological Characterization of Book Graph and Stacked Book Graph
- Efficient Analysis of Vertical Projection Histogram to Segment Arabic Handwritten Characters
- An Auto-Calibration Approach to Robust and Secure Usage of Accelerometers for Human Motion Analysis in FES Therapies
- Balanced Deep Supervised Hashing
