A Dual-Chaining Watermark Scheme for Data Integrity Protection in Internet of Things
2019-03-18BaoweiWangWeiwenKongWeiLiandNealXiong
Baowei Wang ,Weiwen Kong,Wei Li and Neal N.Xiong
Abstract:Chaining watermark is an effective way to verify the integrity of streaming data in wireless network environment,especially in resource-constrained sensor networks,such as the perception layer of Internet of Things applications.However,in all existing single chaining watermark schemes,how to ensure the synchronization between the data sender and the receiver is still an unsolved problem.Once the synchronization points are attacked by the adversary,existing data integrity authentication schemes are difficult to work properly,and the false negative rate might be up to 50 percent.And the additional fixed group delimiters not only increase the data size,but are also easily detected by adversaries.In this paper,we propose an effective dual-chaining watermark scheme,called DCW,for data integrity protection in smart campus IoT applications.The proposed DCW scheme has the following three characteristics:(1) In order to authenticate the integrity of the data,fragile watermarks are generated and embedded into the data in a chaining way using dynamic grouping; (2) Instead of additional fixed group delimiters,chained watermark delimiters are proposed to synchronize the both transmission sides in case of the synchronization points are tampered; (3) To achieve lossless integrity authentication,a reversible watermarking technique is applied.The experimental results and security analysis can prove that the proposed DCW scheme is able to effectively authenticate the integrity of the data with free distortion at low cost in our smart meteorological Internet of Things system.
Keywords:Dual-chaining,reversible watermark,integrity authentication,Internet of things.
1 Introduction
The rapid development of Internet of Things (IoT) has caused great changes in the national security,industry and people’s lives [Zhang,Sun and Wang (2016); Wang,Gu and Zhou (2017)].It has the potential to become a vital part of our infrastructure to enrich lives and make processes easier.It offers economically viable solutions for a variety of people-centric applications,such as,health care,working space automation,public safety and smart space.Smart campus is exactly the most typical application scenario of Internet of Things.As the core part of the smart IoT system perception layer,wireless sensor networks (WSNs) are organized by a great number of sensors with limited computational capacity and power to form a self-organizing network in wireless communication.In the smart campus system,the massive real-time sensory data is continuously collected by the source nodes and sent to the sink node through multi-hop relays.It is used to make decisions and discover deep levels of knowledge [Wang,Gu,Ma et al.(2017); Xia,Wang,Sun et al.(2014)].Due to the limited resources,traditional data security solutions based on cryptography and Message Authentication Code (MAC) cannot be applied to sensor nodes.Sensor nodes are susceptible to a variety of attacks,such as data forgery attack,data tampering attack,and packets selective forwarding attack.So,verifying the integrity of the transmitted data is critical for most smart space IoT applications.
Lightweight digital watermarking techniques are gradually introduced into the wireless sensor networks and smart Internet of Things to verify the integrity of the data [Feng and Potkonjak (2003); Wang,Yan,Li et al.(2015); Zhang,Liu,Das et al.(2008); Wang,Sun,Ruan et al.(2011); Dong and Li (2009)].Chaining watermarks are considered to be the most effective method [Guo,Li and Jajodia (2007)].The core ideas of the existing single chaining watermark schemes are as follows:The data collected by a source node is defined as a data stream.It is divided into multiple groups using the synchronization points or the group delimiters,and the fragile watermark generated by the data in the current group is embedded into the next (or previous) group to form a watermarking chain.Any tamper or attack on the watermarked data would corrupt the watermarking chain.It can efficiently detect and locate any modifications made to the data and authenticate the data integrity [Juma,Kamel and Kaya (2008); Kamel and Juma (2010);Kamel and Juma (2011); Shi and Xiao (2013); Liu,Ge,Zhu et al.(2014)].
But all existing single chaining watermarking schemes still have the following bottlenecks:(1) The tampering of the indispensable synchronization points may lead to a high false negative rate of 50 percent and result in completely meaninglessness of data integrity authentication; (2) The additional fixed group delimiters,which are usually special data elements or fixed packet segments,can be detected easily by the adversaries.(3) It is unacceptable that the embedding method leads to certain irreversible changes to the original data.
In this article,an effective dual-chaining watermark scheme is proposed to ensure the data integrity in the perception layer of smart IoT system.The proposed DCW scheme has the following three characteristics:
(1) Fragile watermarks are generated and embedded into the data stream using a dynamic chaining method to verify the data integrity.
(2) Instead of the additional fixed group delimiter,a chained watermark one is designed to synchronize the both transmission sides in case of the synchronization points failure.
(3) To achieve completely lossless integrity authentication,a reversible watermark algorithm is applied to DCW.
The proposed DCW scheme is evaluated in a real smart campus meteorological Internet of Things system,which is deployed in Nanjing University of Information Science and Technology.The experimental results and security analysis show that the proposed scheme can effectively authenticate the integrity of the data with free distortion and tiny computational overhead.It does not increase the data size nor change its accuracy.Furthermore,DCW can significantly improve the ability to detect and locate the various packet level attacks.Meanwhile,the adversaries can hardly detect the existence of the dual-chaining watermarking based integrity authentication scheme.
The rest of the paper is organized as follows.Section 2 introduces some related works of single chaining watermark schemes.Section 3 presents our proposed dual-chaining watermark scheme.In Section 4,the experimental results and the analysis are introduced.Section 5 includes the work.
2 Related works
Chaining watermark is considered as a most effective way to verify the integrity of streaming data in network environment.The first single chaining watermark scheme,called SGW,is proposed by Guo et al.[Guo,Li and Jajodia (2007)].The SGW scheme is used to authentication the integrity of streaming data in network environment.The data stream is divided into groups of variable size by synchronization points.Fragile watermarks are chained across data groups.Any modifications can be detected and located.The problem with the SGW scheme is that the data insertion,modification,and deletion attacks may create confusion at the receiver.It is difficult for the receiver to track the synchronization points.The synchronization points have been the biggest bottleneck of existing dynamic grouping-based single chaining watermark methods.
Juma et al.take the lead in applying the chaining watermark technology to wireless sensor networks.In Juma et al.[Juma,Kamel and Kaya (2008)],they presented two single chaining watermarking methods,called S-SGW and FWC,respectively.In Kamel et al.[Kamel and Juma (2010)],the authors proposed the LWC scheme to try to avoid several drawbacks of SGW.However,these three schemes still suffer from the same bottleneck as the SGW.In Kamel et al.[Kamel and Juma (2011)],the FWC-D scheme uses the group delimiters to synchronize the sender side and the receiver side.In FWC-D,the dynamic grouping method is abandoned,and additional data elements are used as the group delimiters.It is very easy to be detected by the adversaries.
Another common disadvantage of the existing schemes is that watermarks are embedded by replacing the least significant bits (LSB) of the data,which can significantly affect the data accuracy.It is unacceptable that the methods used to protect the data destroy its integrity,especially,in some critical applications such as smart campus,medical care and military applications.
Reversible chaining watermarking technologies are adopted to address this problem [Qiu(2017); Yuan,Xia and Sun (2017)].In Shi et al.[Shi and Xiao (2013)],a prediction-error expansion based reversible watermarking scheme is proposed by Shi and Li.It can avoid any modification to the data for watermark embedding.But the synchronization point is still its bottleneck.Once the synchronization points are attacked,the false negative rate will be up to 50% and the integrity authentication might be completely meaninglessness.
Shi’s scheme does not take into account the upper bound of the buffer size,the buffer overflow would occur in extreme cases [Liu,Ge,Zhu et al.(2014)].To address this problem,Liu et al.proposed a histogram shifting based reversible watermarking scheme for data integrity protection in BSN.Liu’s scheme does not use dynamic grouping but adopts a fixed grouping method to avoid the drawback of synchronization points.In the head segment of the system packet,a serial number (SN) segment and a group delimiter(DF) segment are attached.Not only increase the transmission overhead,but also easily detected by the adversaries.
3 The dual-chaining watermarking scheme
3.1 Overview of the system model
The system model of the proposed DCW scheme for data integrity protection in smart IoT system is illustrated in Fig.1.There are three types of nodes in the perception layer sensor network,including source sensor nodes,relay nodes and the sink node.Source sensor nodes continually collect data samplings,and send them to the sink using data packets through the multi-hop relay nodes.A data packet is represented as (headsegments,payload),where head segments are predefined parameters,including route,packet length,etc.; the payload is the encoded data samplings.For simplicity,we need not present the data on the packet level.Instead,each data sampling is represented as a data elementEi.All the sensory data of a source node is defined as an infinite numericaldata streamS={E1,E2,…,En}.

Figure1:The system model of DCW
To verify the integrity of the data stream,the proposed DCW scheme is adopted in the system’s perception layer.The dual-chaining watermarks are generated and embedded on the source node,extracted and verified on the sink node.
(1) On the source sensor,the data streamSis cached in two buffers and dynamically divided into different data groups.And two adjacent data groups form an authentication group.The dual-chaining watermarks,including the chaining fragile watermark and the pre-defined chained delimiter watermark,are embedded into the authentication groups in a chaining way.
(2) On the sink,it synchronizes the data groups using the synchronization point and the chained delimiter watermark,and verifies the integrity of the data stream using the chaining fragile watermark.If the data is not temped,the original data can be restored.
3.2 Definitions and rules
Firstly,some system parameters and notations used in the proposed DCW scheme are pre-defined.To simplify the description,all the notations and parameters are shown in Tab.1,and considered to be known parameters.
To embed and extract the dual-chaining watermarking,the data elements would firstly be cached and grouped on the both transmission sides,including the source node and the sink node.Two data buffers B0and B1,which are also denoted as Buffer (b0) and Buffer(b1),are needed to cache the data groups.The data buffer is defined as follows:
Definition 1:(Data Buffer,B) A data bufferBis an allocated memory space to cache the data elements.The capacityNof a data buffer means that it can cache up toNdata elements,which is usually a system-defined parameter.
Definition 2:(Synchronization Point,SP) A data elementEiis aSP,if and only if:Hash(Key,Ei) mod m == 0.
In DCW,the SPs are used for dynamic grouping of data.Since aSPis a selected data element using the secret key,and the group length is variable,it is very difficult to find out and destroy the data groups.All the data elements are cached in the two buffers B0and B1,alternately.When each data element is cached into a data buffer,Rule1is used to determine if a data group is cached successfully.
Rule 1:(Data Grouping Rule) For each elementEkCached in a buffer:(1) ifEkis not aSP && k < N,then continue to buffer the data; (2) ifEkis aSP && k < L,whereLis defined as the lower bound of the group length,then continue to cache data; (3) ifEkis aSP && L ≤ k ≤ N,then all the data elements cached in the buffer is defined as a Data GroupGx={E1,E2,…,Ek}; (4) else,that is,when the buffer is full,a suitableSPhas not been found,then all the data elements cached in the buffer is defined as a Data GroupGx={E1,E2,…,EN},(no SP is included).
In summary,two adjacent data groups are cached in two buffers.The group sizekis a variable value and is bounded byLandN.Buffer overflow would not occur in any cases.The two adjacent data groups can be defined as an Authentication Group,which is the workspace for embedding and verifying the dual-chaining watermark scheme.To avoid confusion,they are denoted as the previous group (Gi-1) and the current group (Gi).
As shown in Fig.2,the data elements in each data group are divided into three segments,includingSF={E1,E2,…,Ek-l-1},SD={Ek-l,Ek-l+1,…,Ek-1} andSP=Ek.The lengthlofSDis a fixed value; and the length ofSFisk-l-1.The well-designed fragile watermark and delimiter watermark are embedded intoSFandSDof theprevious group Gi-1respectively,using a reversible method.The fragile watermarkFWiis generated by all the original data elements in the current groupGi,the delimiter watermarkDWi-1is generated using Rule 2.

Figure2:The proposed Dual-Chaining Watermarking Model
The workflow of the dual-chaining watermarking embedding:When a data groupGis cached in the buffer using Rule 1,the following two operations are performed:(1)Firstly,the fragile watermark binary stringFWiof the current groupGiis computed according to Rule 3,and is embedded into theSFsection of the previous groupGi-1using Rule 4.A fragile watermarking chain is formed.It is used to verify the data integrity.(2)Meanwhile,the delimiter watermarkDWis generated using Rule 2,and is embedded into theSDsection ofGi-1using Rule4.That is the other watermarking chain to keep the both transmission sides synchronized.It can avoid failure in sync grouping whenSPConfusion happens.Once the dual-watermarking embedding ends,the data in the groupGi-1will be sent to the sink node and the next groupGi+1will be buffered.
Rule 2:(Delimiter Watermarks Definition) The delimiter watermarks,which is denote asDW={DW1,DW1,…,DWl},are a set of well-defined fixed-size binary strings.They are embedded into fixed position in each group of data,one by one,to form a watermark chain.Fo r simplicity,they can be generated by a fixed delimiterWD,DWiis denoted asWD⊕i,inwhich “⊕” is theXORoperation.XORis a reversible operation.The length ofWDandDWiis l,which is equal to the length ofSD.
Rule 3:(Fragile Watermark Generation Rule) The fragile watermarkFWiis generated by the hash of the concatenation of all the data elements in the current group and then embedded into the previous group.FWiis denoted asGroupXOR (H1⊕H2⊕…⊕Hk),in which “⊕” is theXORoperation.The length ofFWi,which is a fixed value,depends on the hash function.If the length ofSFin previous group is larger than the length ofFWi,FWiwill be embedded repetitively.
In DCW,to make the both watermarks reversible,a difference expansion-based reversible embedding algorithm is designed [Chen,Sun,Sun et al.(2013); Alattar (2004)].The reversible watermarking embedding rules are defined as follows.
Rule 4:(Watermarking Embedding Rule) Given an numerical data groupGx={E1,E2,… ,Et},and a binary watermarkW,(its length ist-1),the embedding rule is as follows:(1)calculate the average value ofGxdata,denoted asu=⎿(E1+E2+…+Et)/t」; (2) compute the differences between each data elementEj(j=2,3,…,t)andE1,denoted asdj=Ej-E1;(3) shiftdjone bit to the left and embed the corresponding bit ofWinto the vacant least significant bit ofdj,that isdj'= 2×dj+W[j-2]; (4) we can get the watermarked dataGx',in whichE1'=u-⎿(d2'+d3' +…+ dt')/t」,Ej'=E1'+dj' (j=2,3,…,t).
Since the data elements are collected in a short period of time,and thedjChanges in a small range,the 1-bit left-shifted operation overflow will not happen [Kamel and Juma(2010); Kamel and Juma (2011)].
Rule 5:(Sync Data Grouping Rule) The only difference between the sync grouping rules and the Rule 1 is:the group ends before the buffer is full,if and only whenEkis aSPand simultaneously a delimiter watermark can be extracted from the data elements beforeEk.
Rule 6:(Watermark Extraction and Data Recovery Rule) Given a watermarked data groupGx'={E1',E2',…,Et'}:(1) calculate the average value ofGx',denoted asu=⎿(E1'+E2' +…+Et')/t」; (2) compute the differences between eachEj'(j=2,3,…,t) andE1',denoted asdj'=Ej'-E1'; (3) the binary watermarkingWx'Can be extracted from the least significant bit of the differences; the corresponding watermark bit isWx' [j-2] =LSB(dj'),and the length ofWx'ist-1; (4) shiftdj'one bit to the right,dj= ⎿dj'/2」; (4) we can get the recovered dataGx,in whichE1=u-⎿(d2+d3+…+ dt)/t」,Ej=E1'+dj(j=2,3,…,t).
The workflow of the dual-chaining watermarking based data integrity authentication scheme is as follows:(1) Two groups of dataGi-1'andGi'are cached correctly using Rule 5.As shown in Fig.2,data elements in each data group can be divided into three parts,includingSF,SDandSP; (2) the fragile watermarkingFWi'Could be extracted from sectionSFofGi-1',according to Rule 6; and then the watermarkingFWi''Can be recalculated using Rule 3.ThenFWi'is equal toFWi'',the data in Gi'is complete; (3) The original dataGiCan be regained fromGi'using Rule 6.
3.3 Watermarking embedding algorithm
Without loss of generality,the dual-chaining watermarking generation and embedding schemes,which run on the source sensor node in the perception layer of a smart Internet of Things system,are introduced formally in this section.Two data buffers,which are denoted as Buffer (b0) and Buffer (b1),respectively,are needed on each source sensor node.The dual-chaining watermark embedding algorithm is presented in Algorithm 1.It includes the delimiter watermark embedding and the fragile watermark embedding.Algorithm 2 shows the data buffering process on the data source sensor node.The detailed course of the reversible watermarking embedding is designed in Algorithm 3.
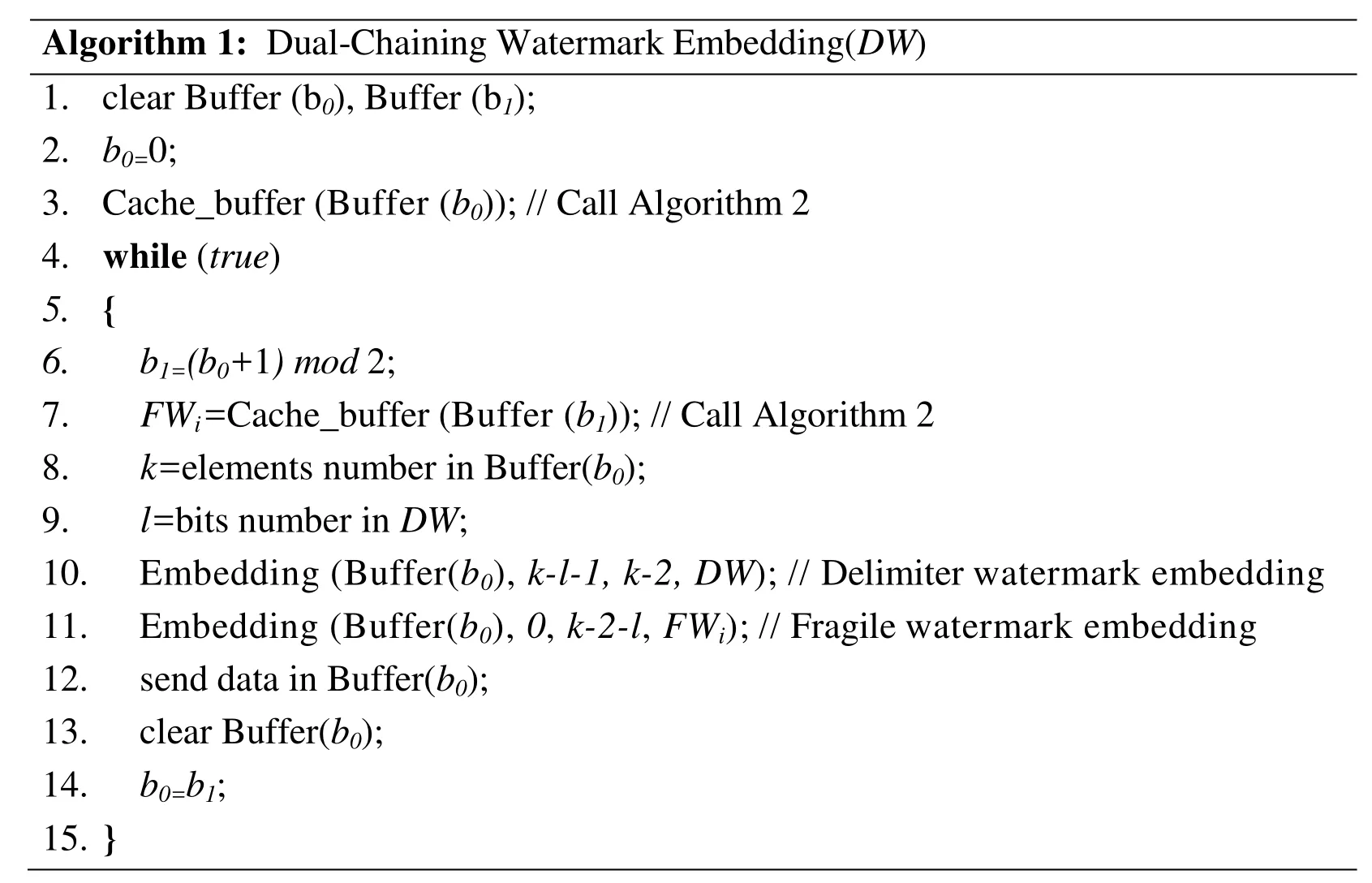
Algorithm 1:Dual-Chaining Watermark Embedding(DW)1.clear Buffer (b 0),Buffer (b 1);2. b0= 0;3.Cache_buffer (Buffer (b0));//Call Algorithm 2 4.while (true) 5. { 6.b1= (b0 + 1 ) mod 2;7. FWi =Cache_buffer (Buffer (b1));//Call Algorithm 2 8. k= elements number in Buffer(b0);9. l= bits number in DW ;10. Embedding (Buffer(b0), k-l-1,k-2,DW);//Delimiter watermark embedding 11. Embedding (Buffer(b0), 0 , k-2-l , FWi);//Fragile watermark embedding 12. send data in Buffer(b0);13. Clear Buffer(b0);14. b0= b1 ;15.}

Algorithm 2:Cache_buffer (Buffer(b))1. k =0; W =0;2.while (receive a data element Ei)3.{4.Buffer(b) (k ++)= Ei ;5. H=Hash (Key,Ei ) ;6. W = W ⊕ H ;7.if ((H mod m==0) && (k >= L) && (k <= N) || (k == N))8.return W ;9.}
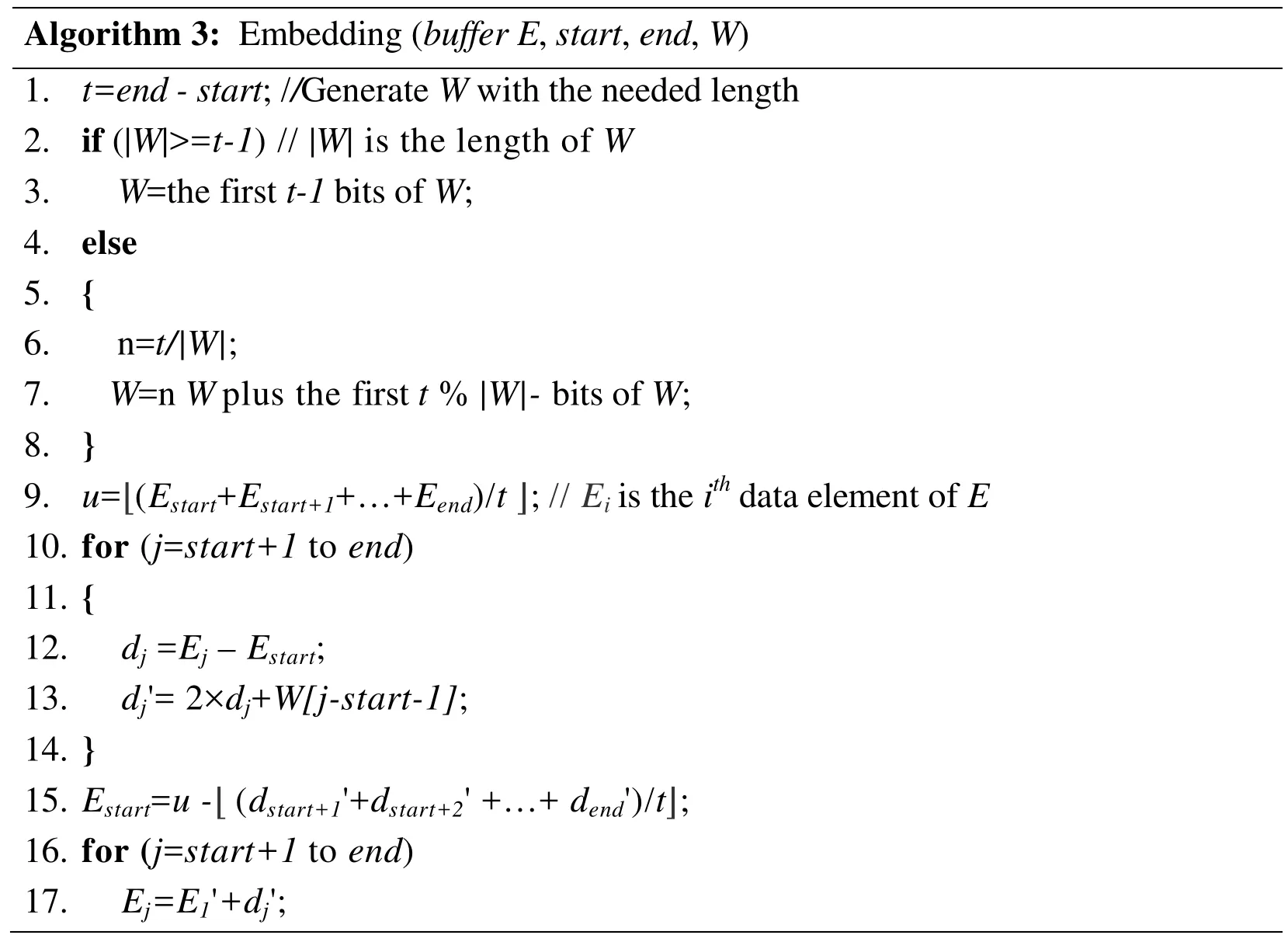
Algorithm 3:Embedding (buffer E , start , end , W)1. t=end-start ;// Generate W with the needed length 2.if (| W |>= t-1)//| W | is the length of W 3. W =the first t-1 bits of W ;4.else 5.{6.n= t/|W| ;7. W =n W plus the first t % |W|- bits of W ;8.}9. u =⎿(Estart + Estart+1 +…+ Eend)/t 」;is the i th data element of E 10.for (j = start+1 to end)11.{12. dj = Ej – Estart ;13. dj '= 2× dj + W[j-start-1] ;14.}15. Estart = u- (dstart+1 '+ dstart+2 ' +…+ dend ')/t 」;16.for (j = start+1 to end)17. Ej =E1 ' +dj ';
3.4 Data integrity authentication algorithm
Without loss of generality,the data integrity authentication and data recovery algorithms,which run on the sink node in a smart Internet of Things system,are presented formally in this subsection.In a smart IoT application scenario,the computing resource,storage space and energy of the sink node are not constrained.It can cache data elements into the two buffers as well using Algorithm 6.As shown in Tab.1,the watermark embedding securityKey,the secret parameterm,and the lower bound of the buffer sizeLand the upper bound of the buffer sizeNare considered to be known parameters.The complete algorithm for data integrity authentication and original data recovery is shown in Algorithm 4.The extracted watermarks includeFWi'andDW'.Here,FWi'is the fragile watermark that is the group hash value for integrity protection constructed from the previous and the current group;DW'is the chained delimiter watermark,which extracted by Algorithm 5 for the verification of grouping.The data can be recovered using Algorithm 7.

Algorithm 4:Data Integrity Authentication 1.clear Buffer (0),Buffer (1);2. b0 = 0 ;3.Cache_sync_buffer (Buffer (b0));4. k= number of data elements in buffer(b0);5. l= number of bits in DW ;6. FWi '= Extraction(Buffer(b0), 0 , k-2-l);//Call Algorithm 7 7.while (true)8.{9. b1 =(b0 +1) mod 2 ;10. if (Cache_sync_buffer (Buffer (b1)) == 1)11. {12. k= number of data elements in Buffer(b1);13. FWi+1 '= Extraction(Buffer(b1), 0 , k-2-l);//Call Algorithm 7 14.for (j = 0 to k-1)15. FWi ”=FWi ”+Hash (Buffer(b1) (j));16.if (FWi ' == FWi ”) 17.return 1;//Integrity 18.else 19.return 0;//Tampered 20.}21.else 22.return 0;//Tampered 23.clear Buffer(j0);24. b0= b1 ;25.}

Algorithm 5:Delimiter (buffer E' , start,end)1.for (j = start+1 to end)2.{3. dj ' = Ej '- Estart ' ;4. W' [j-start-1] =LSB(dj ') ;5.}6.return W’ ;

Algorithm 6:Cache_sync_buffer (Buffer(b))1. k= 0; W= 0;2.while (receive a data element Ei)3.{4.Buffer(b) (k ++)= Ei ;5. H= Hash (Key,Ei ) ;6. W=W ⊕ H ;7.if (((H mod m == 0 && Delimiter ( Buffer(b), k-1-l,k-1) == DW) &&(k >= L) && (k <= N)) || (k == N && Delimiter ( Buffer(b), k-l,k) == DW))8.return 1;//Sync Success;9.if ((Delimiter (Buffer(b), k-l,k) ! =DW && k == N)10.return 0;//Sync Failure 11.}

Algorithm 7:Extraction (buffer E',start,end)1.t= end-start ;2. u' =(Estart ' + Estart+1 ' +…+ Eend ')/t 」;3.for (j = start+1 to end)4.{5. dj ' = Ej '- Estart ' ;6. W' [j-start-1]=LSB(dj ') ;7. dj= ⎿ dj ' /2」;8.}9. Estart '= u ' - (dstart+1 + dstart+2 +…+ dend)/t 」;//Data Recovery10.for (j = start+1 to end) 11. Ej ' =Ej ' +dj ;12.return W’ ;
4 Experiments and performance evaluation
In the performance evaluation section,we evaluate the performance of the proposed dualchaining watermark scheme for data integrity protection from multiple perspectives.We use our own real smart meteorological Internet of Things system which is deployed in Nanjing University of Information Science and Technology,as shown in Fig.3.The sensor nodes used in this meteorological IoT system are our self-developed products[Wang,Gu,Ma et al.(2017); Wang,Gu and Yan (2018)],which is shown in Fig.4.The propose DCW scheme is implemented on the node.In this IoT system,the temperature,humidity data are gathered once per minute,and are used for embedding the dualchaining watermarks.

Figure3:The smart meteorological Internet of Things system deployed in NUIST

Figure4:The self-developed sensor nodes used in the experiment
4.1 Data accuracy
In the people centric Internet of Things systems,such as smart campus application,the data accuracy is very important.The watermark embedding method introduces some data changes.Since these changes are usually very small,and insignificant on the perception results,it is hard to be perceived.So,the data accuracy and the invisibility are acceptable under normal circumstances.Tab.2 shows the statistical comparison in terms of the rate of change of the mean and the variance of data change.Small changes in mean and variance indicate that our proposed dual-chaining watermark scheme has fairly better invisibility.Furthermore,people can recover the original data stream with scarcely error when needed.

Table2:The statistical comparison of the data change

2 14.53 0.0012 0.0006 0.0034 14.53 3 23.36 0.0017 0.0018 0.0047 23.36 4 49.45 0.0013 1.0054 0.0946 49.45 5 57.50 0.0026 0.0027 0.0625 57.50
4.2 Data transmission amount
In this subsection,we present the comparison of the data transmission amount among the original data,the existing single chaining watermark scheme (FWC-D) and the proposed dual-chaining watermarking scheme (DCW).In Fig.5,the x-axis denotes the sense data amount and the y-axis denotes the corresponding data transmission amount.Because the FWC-D scheme directly adds the additional group delimiters into the data groups,the additional amount of data transmission is extremely high.Furthermore,the LSB-based watermarking embedding also destroys the accuracy of the data.Different from FWC-D,DCW takes the chained delimiter watermarks as the GDs.The experimental results show that the DCW scheme doesn’t increase the amount of data transmission.It can also recover the original data.
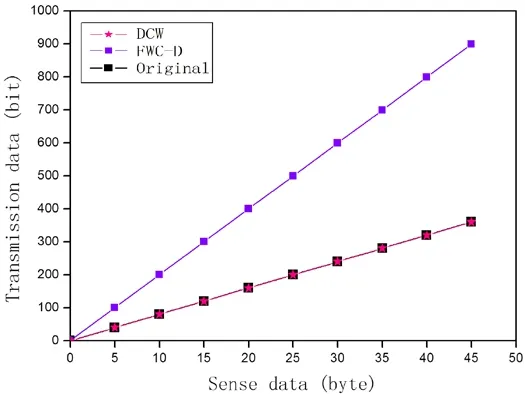
Figure5:Comparison of the amount of the data transmission among three schemes
4.3 False positive rate comparison
In all the existing single chaining watermark schemes,such as SGW,FWC,when the watermarked data groups cannot be synchronized by the sink node,false positives happen.In the proposed DCW scheme,the chained watermark delimiters can synchronize the both transmission sides in case of the synchronization points are tampered.Fig.6 shows the comparison of the false positive rate among the SGW scheme,the FWC scheme and the proposed DCW scheme.The false positive rate decreases with the parameterm.Meanwhile,compared with the SGW scheme and the FWC scheme,the false positive rate of DCW reduces significantly.That is because the DCW can locate the SP by delimiter watermark.
In total,the false positive performance of the proposed dual-chaining watermark scheme is better than anyone of the previous single chaining watermark schemes.

Figure6:Comparison of the false positive rate
4.4 Anti-attack capability evaluation
In this subsection,we evaluate the anti-attack capability of the proposed DCW scheme.We discuss four most common attacks that can be launched in the wireless smart Internet of Thing application scenario,including packet tampering attack,packet forgery attack,selective forwarding and packet replay attack.We define that an attack is successful if it is not detected by the sink node.In our experiments,we randomly select 5 relay sensor nodes as the malicious nodes,which can launch these four attacks.And each type of attack is evaluated 500 times.The experimental results of anti-attack capability of the proposed DCW scheme are shown in Tab.3.
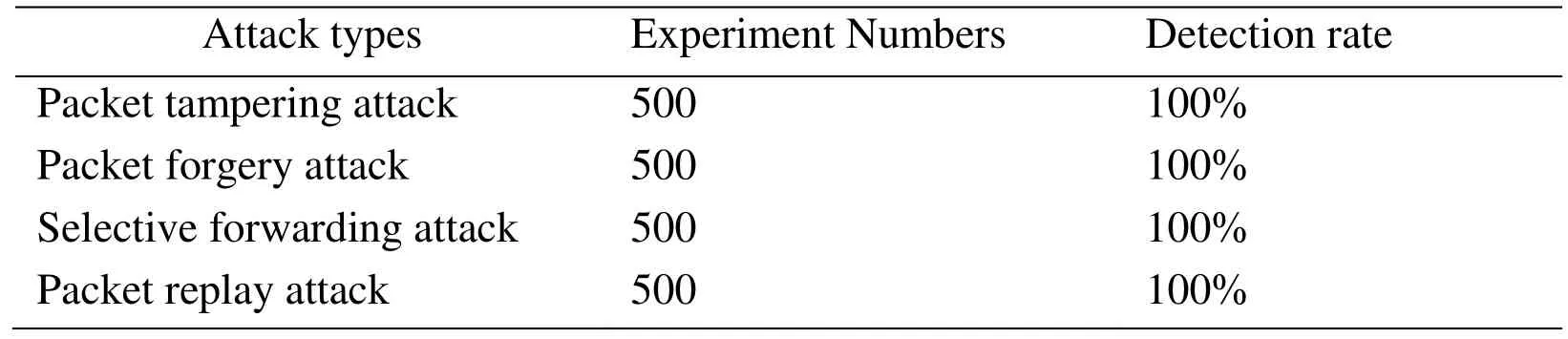
Table3:Anti-attack capability evaluation
In our proposed DCW scheme,the well-designed dual-chaining watermarks,including the chaining fragile watermark and the pre-defined chained delimiter watermark,are embedded into the data in a dynamic and reversible way.It is difficult for the adversaries to analysis any data information by capturing the data packets without the data grouping secret key.The DCW scheme embeds chained delimiters watermarks which can prevent the adversaries to track and improve the security greatly compared to the single chaining watermarking scheme.According to the experimental results shown in Tab.3,the prosed DCW scheme achieved 100% detection rate on all the four types of packet attacks.We can see that the proposed DCW scheme can verify the integrity of the data stream.It can be used to ensure the authenticity of the data.
4.5 Computation overhead and energy consumption analysis
It is difficult to accurately evaluate the energy consumption of the proposed dualchaining watermark scheme in the real smart meteorological Internet of Things experiment environment.So,we only evaluate energy consumption using the computation overhead analysis according to common practice.Generally,the energy consumed to transmit one bit data over a distance of 100m by radio can execute about 3000 instructions [Kamel and Juma (2011)].That is,if1Erepresents the energy consumed to execute one instruction,the energy consumption to transmit 1-bit data is 3000E.So,we can see that the energy consumption for data transmission is far greater than processing the sensory data.In DCW,the chained delimiter watermarks and the fragile watermark are both embedded into the data elements instead of being transmitted as additional data.It does not introduce any data transmission overhead.So,the total energy consumption of the perceptual layer of the network is reduced.The network lifetime of the smart Internet of Things system is extended significantly.
5 Conclusion
In this article,a dual-chaining reversible watermarking method for data integrity protection in the perception layer of the IoT system.The proposed reversible scheme can ensure the integrity of the data with free distortion.In addition,DCW scheme takes the chained watermarking delimiters to synchronize the data source node and the sink node.It makes the adversaries difficult to detect the existence of the watermarking and track the data groups.The dual-chaining watermarks can resist various types of attacks such as packet forgery attack,selective forwarding attack,packet replay and tampering attack,and authenticate the integrity of data effectively.Meanwhile,the proposed dual-chaining watermark scheme does not increase the transmission overhead.Experimental results have shown that the DCW has remarkable advantages over the existing single chaining watermark methods not only in terms of data accuracy,but also data security and the lifetime of the wireless sensor network.
Acknowledgement:This work is supported by the Major Program of the National Social Science Fund of China under Grant No.17ZDA092; by the Electronic Information and Control of Fujian University Engineering Research Center Fund under Grant No.EIC1704; by the National Key R&D Program of China under grant 2018YFB1003205;by the National Natural Science Foundation of China under grant 61173136,U1836208,U1536206,U1836110,61602253,61672294; by the Priority Academic Program Development of Jiangsu Higher Education Institutions (PAPD) fund; by the Collaborative Innovation Center of Atmospheric Environment and Equipment Technology (CICAEET) fund,China.
杂志排行
Computers Materials&Continua的其它文章
- R2N:A Novel Deep Learning Architecture for Rain Removal from Single Image
- A Straightforward Direct Traction Boundary Integral Method for Two-Dimensional Crack Problems Simulation of Linear Elastic Materials
- Effect of Reinforcement Corrosion Sediment Distribution Characteristics on Concrete Damage Behavior
- Research on the Law of Garlic Price Based on Big Data
- Controlled Secure Direct Communication Protocol via the Three-Qubit Partially Entangled Set of States
- Modeling and Analysis the Effects of EMP on the Balise System
