Controlled Secure Direct Communication Protocol via the Three-Qubit Partially Entangled Set of States
2019-03-18GangXuKeXiaoZongpengLiXinXinNiuandMichaelRyan
Gang Xu ,Ke Xiao ,Zongpeng Li,Xin-Xin Niu and Michael Ryan
Abstract:In this paper,we first re-examine the previous protocol of controlled quantum secure direct communication of Zhang et al.’s scheme,which was found insecure under two kinds of attacks,fake entangled particles attack and disentanglement attack.Then,by changing the party of the preparation of cluster states and using unitary operations,we present an improved protocol which can avoid these two kinds of attacks.Moreover,the protocol is proposed using the three-qubit partially entangled set of states.It is more efficient by only using three particles rather than four or even more to transmit one bit secret information.Given our using state is much easier to prepare for multiqubit states and our protocol needs less measurement resource,it makes this protocol more convenient from an applied point of view.
Keywords:Controlled secure direct communication,cluster state,three-qubit partially entangled state,entanglement swapping.
1 Introduction
Since the Bennett and Brassard’s original article [Bennett and Brassard (1984)] was published,quantum key distribution (QKD) has an approach using quantum mechanics[Jiang,Jiang and Ling (2014)] principles for the participants of communication to share a private key with unconditional security.
With the development of quantum cryptography [Wei,Chen,Niu et al.(2015)] and network communication,security of communication is widely concerned [Chen,Tang,Xu et al.(2018); Chen,Sun,Xu et al.(2017); Xu,Chen,Li et al.(2015); Xu,Chen,Dou et al.(2015); Xu,Chen,Dou et al.(2016)].Different from QKD,quantum secure direct communication (QSDC) is another field of quantum cryptography.In 2002,Boströ m and Felbinger presented a ping-pong QSDC protocol using Einstein-Podolsky-Rosen (EPR)state [Boströ m and Felbinger (2002)].After that,a series of QSDC protocols [Deng and Long (2004); Wang,Deng,Li et al.(2005); Wang,Fang and Tane (2006); Cao,Yang and Wen (2010)] have been proposed.
Recently,the controlled quantum secure direct communication (CQSDC),a new kind of QSDC,has been proposed and has attracted much attention [Chen,Wang,Du et al.(2008); Chen,Wen,Guo et al.(2008); Gao,Yan and Wang (2005); Xia and Song (2007);Wang,Zhang and Tang (2006); Xia,Song and Song (2008); Zhang,Zhan and Zhang(2009); Chang,Lin,Zeng et al.(2012); Hassanpour and Houshmand (2015); Fang(2014)].In CQSDC scheme,the receiver cannot get any secret information without the controller’s admission.Besides that,if the number of controllers,senders or receivers is more than one,the protocol could also be deemed as a network protocol [Lu,Wang and Wang (2012); Lv and Wang (2017); Pang,Liu,Zhou et al.(2017); Li,Wang,Li et al.(2018); Li,Chen,Sun et al.(2016)].By using partially entangled GHZ state,Chen et al.[Chen,Wang,Du et al.(2008)] proposed a CQSDC protocol,whose aim is to share the private quantum entanglement keys to encrypt and decrypt the secret information.Using W state,Chen et al.[Chen,Wen,Guo et al.(2008)] proposed a novel CQSDC protocol in which entanglement swapping is utilized and the quantum circuit of it is also put forward.However,W state is difficult to prepare under the conditions of the experiment for multiqubit states.Chang et al.[Chang,Lin and Zeng (2012)] proposed a CQSDC protocol using single photons to carry dealer’s information.And they declared that if any eavesdropper wants to steal dealer’s information,the lawful participants will discover it and abort their transmission.Hassanpour et al.[Hassanpour and Houshmand (2015)]proposed a CQSDC protocol based on GHZ-like state.In their scheme,the receiver can obtain two-secret bits using entanglement swapping,which guarantees the security of the process.Fang [Fang (2014)] proposed a CQSDC protocol based on EPR pair entanglement swapping to complete the communication,five-particle cluster state is utilized in this protocol to achieve eavesdropping detection which makes the detection probability more than 88%.
A secure CQSDC protocol must meet two needs.First,an outside eavesdropper cannot obtain any information about the transmitted state.Second,if the controller(s) doesn’t permit,the receiver cannot obtain the secret information.In 2009,Zhang et al.[Zhang,Zhan and Zhang (2009)] designed a CQSDC protocol (the ZZZ protocol) with four particle cluster states using swapping quantum entanglement and local unitary operations.However,Yang et al.[Yang,Chai,Teng et al.(2011)] shown that the dishonest party Bob can give a special attack strategy.By using fake entangled particles,Bob can obtain Alice’s secret information without the permission of the controller.Besides that,they gave a further improvement to resist their proposed attack.Then,Qin [Qin (2012)]analyzes the ZZZ protocol and found another special attack,disentanglement attack.Using this attack,the control function of Charlie in the ZZZ protocol [Zhang,Zhan and Zhang (2009)] can be eliminated by the receiver Bob without the knowledge of Charlie.In addition,this new attack is also valid for the improved scheme in Yang et al.’s protocol [Yang,Chai,Teng et al.(2011)].However,Qin did not propose a further improved protocol.In conclusion,no effective protocol is proposed at last.
According to the above three papers,we further analyze the reasons why the ZZZ protocol cannot resist fake entangled particles attack and disentanglement attack.At last,we find out two reasons.On one hand,Bob prepares the four particle cluster states and he is the last one to measure his own particles in the detection of eavesdropping.Under this circumstance,he can prepare any state (fake entangled particles) which can be used to deceive Charlie,the controller,without being detected.On the other hand,he owns half particles of the four particle cluster states.And one of his two particles is equal to Alice’s particle and another is equal to Charlie’s.Then,Bob can measure the particle which is equal to Charlie’s and get rid of the control of Charlie (disentanglement attack).
Considering these weaknesses,we investigate whether it is possible to make it secure by letting Charlie prepare the four particle cluster states and Alice be the last one to measure her particles.However,if we only change these of the protocol,it is still insecure under disentanglement attack.Thus,we can let Charlie perform some operations on the cluster states as secret information which is only known by him,and then Bob cannot use disentanglement attack to make Charlie out of the control of the communication.In summary,we propose a novel protocol with two versions of improvement in which the communication is secure under the above two attacks as well as some other attacks.What’s more,without the permission of the controller,the secret information cannot be recovered by the receiver or any other.
Furthermore,based on three-qubit partially entangled set of states,we also investigate a new CQSDC protocol which has many distinct advantages compared with many previous protocols.First,our protocol uses less quantum resources to transmit the same information.In other words,the protocol [Chen,Wang,Du et al.(2008)] transmits one bit by using six particles,but in our protocol,one bit is transmitted only by using three particles.Second,our three-qubit partially entangled set of state is much easier to prepare than GHZ state in Wang et al.’s protocol [Wang,Zhang and Tang (2006)],W state [Xia,Song and Song (2008)] and four particle cluster state [Zhang,Zhan and Zhang (2009)].Third,our protocol uses less effective measurements than the ZZZ protocol.In some sense,our protocol has a lower cost than the ZZZ protocol.
The rest of this paper is organized as follows.In Section 2,two new improved protocols are proposed.Then we analyze that our new improved protocol is secure under fake entangled particles attack and disentanglement attack.In Section 3,we give a new CQSDC protocol.Finally,the paper is ended up with a conclusion in Section 4.
2 The new improved CQSDC protocol
In this section,we propose a new improved CQSDC protocol which is secure under the fake entangled particles attack and disentanglement attack.In our improved protocol,it is Charlie rather than Bob who prepares four particle cluster states.In fact,Bob wants to remove Charlie’s control and obtain Alice’s secret freely.Yang et al.[Yang,Chai,Teng et al.(2011)] presented a fake entangled particles attack on the ZZZ protocol,in which Bob prepares two Bell states rather than a four-qubit cluster state.Then,Bob can obtain Alice’s secret information freely without Charlie’s control.And they also gave an improvement to resist their fake entangled particles attack.
However,Qin [Qin (2012)] analyzed further and discovered another special attack,disentanglement attack.Using this attack,the control function of Charlie in the ZZZ protocol can be eliminated by the receiver Bob without the knowledge of Charlie.Moreover,this new attack is also valid for the improved scheme [Yang,Chai,Teng et al.(2011)].But to our disappointment,Qin did not give a further improvement.Therefore,in the next part,we will give two new improvements to the ZZZ protocol.
2.1 Improvement for the ZZZ protocol
2.1.1 The first improvement
In this part,we will propose our first improvement of the ZZZ protocol.And we give a detailed description of our new improved protocol as follows.(S1) Charlie preparesN+mfour-qubit states inThen he performs one of four kinds of operationsU1,U2,U3,U4on particlestnandkn,each with the probability of 1/4,whereU1=I⊗I,U2=I⊗σx,U3=σx⊗IandU4=σx⊗σx.
Therefore,he gets the following states
Charlie takes the particleshnfrom each state to form an ordered particle sequence[h1,h2,...,hN+m],and names it as theHsequence.Similarly,the remaining particles constituteTsequence [t1,t2,...,tN+m],Ksequence [k1,k2,...,kN+m]andCsequence[c1,c2,...,cN+m].
(S2) Charlie prepares three checking sequences,DH,DTandDKfor the analysis of the eavesdropping.These sequences are large enough.Let the number of particles in them bel.They are randomly chosen fromThen,Charlie minglesDHwithHsequence to getH′sequence,DTwithTsequence to getT′sequence andDKwithKsequence to getK′sequence.And he also makes a record of the insertion positions and the measurement basis of the checking particles.Finally,Charlie sendsH′sequence to Alice,T′,K′sequence to Bob and holdsCsequence.
(S3) Charlie confirms that Alice and Bob have received the travelling particles.Then,Charlie let Alice and Bob measure checking particles inH′,T′andK′,respectively.After that,he tells Alice and Bob the positions and the corresponding basis ofDH,DTandDK.
Alice and Bob measure their checking sequences with the corresponding basis announced by Charlie.Alice and Bob tell their measurement results to Charlie.Then,Charlie can determine the existence of the eavesdropping in the communication in accordance with Alice’s and Bob’s measurement results.If the error rate of the eavesdropping checking is higher than a set threshold,Charlie will restart the protocol.If not,they will carry out the next step.
(S4) Also,Alice and Bob need to check whether the state is four particle cluster state or not.Alice randomly selectsmparticles from herHsequence and performs randomly one of the two unitary operationsU1′=IandU2′ =iσyon each selected particle.Then she asks Charlie randomly to measure his corresponding particles using one of two measurement basesandThen Charlie informs his measuring results of Alice and Bob.Additionally,he must inform Bob of what operations he has performed on Bob’s corresponding particles.According to Charlie’s public information,Bob can first do the same operations {U1,U2,U3,U4}on his particles and then take the Bell measurement orZ-basis on the corresponding particles and inform Alice of his measurement results.According to the measurement results of Bob and Charlie,Alice measures her particles and can determine whether the state is four particle cluster state or not.
In fact,after Alice’sU1′orU2′operation and Bob’s one of four operations,the state(i=1,2,3,4)will change into
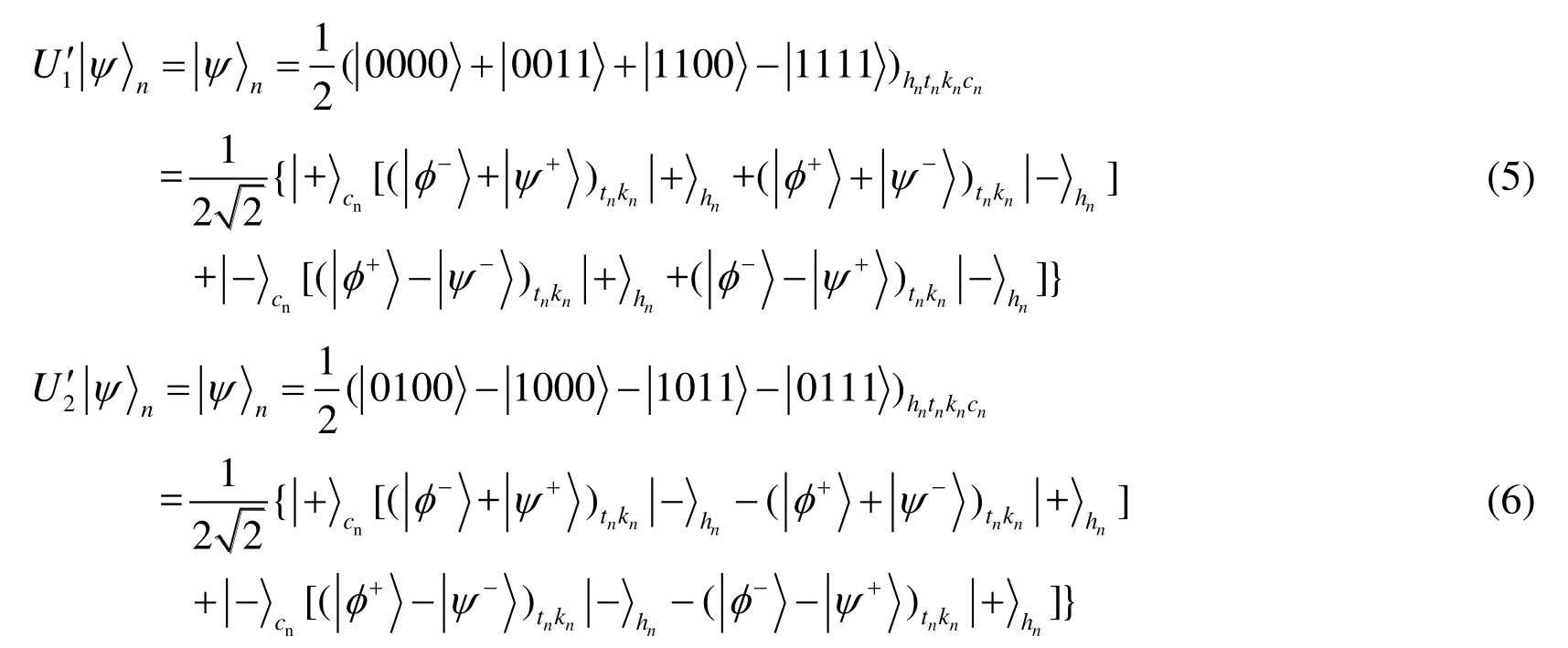
If the error rate is higher than a set threshold,Alice can conclude that the states are not four-qubit cluster states and give up the communication.
(S5) Suppose Alice wants to transmit secret information to Bob.After confirming the security checking,Alice takesMhset by way of two particles as encoding-decoding groups.Group 1 includes particlesh1andh2,group 2 includes particlesh3andh4etc.Afterward,Alice announces the encoding-decoding groups in theMhset.
(S6) After that Alice’s announcement,Bob and Charlie form ordered encoding-decoding groups which consist of the corresponding particles inMt,Mkset andMcset,severally.
(S7) Alice requires Charlie to perform a Hadamard operation on eachcnin order inMcset,and then Eqs.(1)-(4) will be transformed into the states
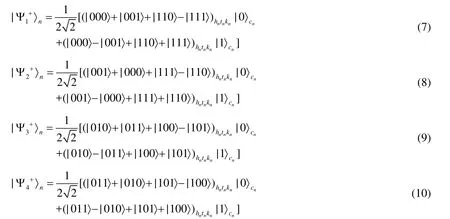
And then,Charlie measures particlecnlike the ZZZ protocol.
(S8) Charlie informs Bob of his measurement results and his operations on each particle in (S1).According to Charlie’s information,Bob performs the same operations on the particles in his hand,the rest steps are the same as the steps (S7-S9) of the ZZZ protocol.
2.1.2 The second improvement
Our second improvement of the ZZZ protocol is similar with the first improvement.And we give a detailed description of our second improved protocol as follows.
(S1’) Charlie preparesN+mfour-qubit states inThen he performs one of four kinds of operationsU1,U2,U3,U4on particlestnandkn,each with the probability of 1/4,whereU1=I⊗σz,U2=I⊗iσy,U3=σx⊗IandU4=σx⊗σx.
Therefore,he gets the following states

Charlie takes the particleshnfrom each state to form an ordered particle sequence[h1,h2,...,hN+m],and names it as theHsequence.Similarly,the remaining particles composeTsequence [t1,t2,...,tN+m],Ksequence [k1,k2,...,kN+m]andCsequence [c1,c2,...,cN+m].
(S2’)-(S6’) are the same as the steps (S2-S6) of the first improvement.
(S7’) Alice requires Charlie to perform a Hadamard operation on eachcnin order inMcset,and then Eqs.(11)-(14) will be turned into

And then,Charlie measures particlecnlike the ZZZ protocol and tells Alice and Bob his measurement results.
(S8’) Alice and Bob utilize the local operationUnm(n,m=0,1)to encode secret information.Here,U00=I,U01=σx,U10=-iσyandU11=σz.For convenience,let two cbit strings 00,01,10 and 11 correspond to them,severally.Alice uses local operationUnmto encode two-bit on the encoding-decoding groups inMcset.Later,
Alice measures all the encoding-decoding groups with Bell bases and announces measurement results and the order of the encoding-decoding groups.
(S9’) Bob makes the Bell measurements on their corresponding particles inMtandMkset,separately.As shown in Tab.1,Bob can obtain Alice’s secret information when he receives Charlie’s and Alice’s measurement results.For example,suppose that Charlie’s state is | Ψ2〉2and his measurement results are | 0〉c1and | 0〉c2,then | Ψ2〉1and | Ψ2〉2will be collapsed into
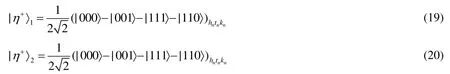
If Alice performs aU00operation on one particle of group 1,the state composed of particles (h1t1k1;h2t2k2)is
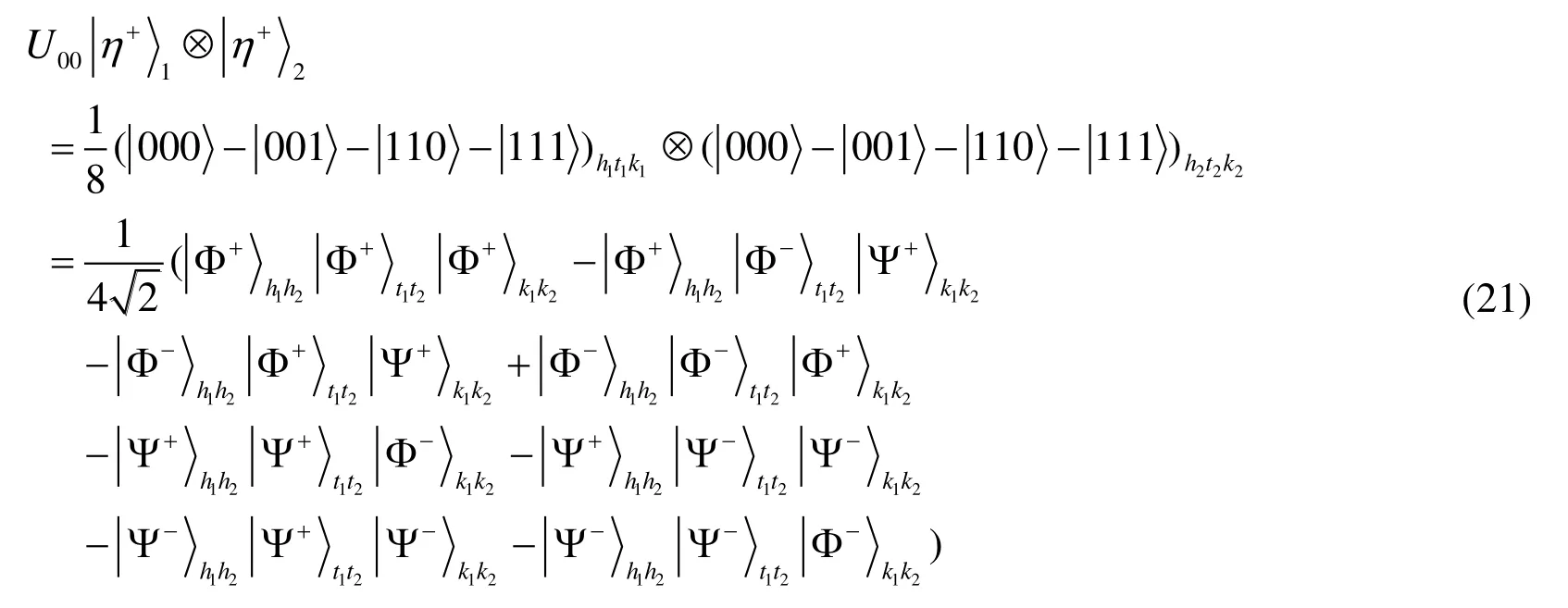
But there is one more point that we need to notice,that is,the Eq.(12) of the ZZZ protocol is written wrong,and it should be written as follows.

Table1:Alice’s and Bob’s measurement results according to the unitary operation Unm and the initial states
2.3 Security analysis
Mathematics provides some important tools [Dong,Zhang,Zhang et al.(2014)] to analyze and solve practical problems.The security of our protocol could be proved in theory and by mathematics.In this section,we will show that our protocol is secure under fake entangled particles attack and disentanglement attack which the original ZZZ protocol cannot resist.
Case1:The fake entangled particles attack.In our new proposed CQSDC protocol,it is Charlie rather than Bob who prepares the four particle cluster state,so it is impossible for Bob to prepare two Bell states in Yang et al.’s protocol [Yang,Chai,Teng et al.(2011)] to deliver fake entangled particles attack on Charlie.That is to say,Bob cannot prepare fake entangled particles to deceive Charlie with the attempt of getting rid of control of Charlie.However,chances are that Charlie may prepare two entangled states instead of four particle cluster state to obtain Alice secret information.In this condition,Charlie sends one entangled state to Bob and shares one entangled state with Alice.But in the check of four particle cluster state,Alice and Bob can conclude that error rate is higher than a set threshold.For Charlie does not know Alice’s operations,he can guess wrong with the possibility of 1/2.And there aremCluster states,therefore he has the possibility of to guess all right,which is impossible whenmis large enough.
Case2:The disentanglement attack.As Qin [Qin (2012)] has pointed out,if Bob wants to get rid of Charlie’s control,he can measure every particle inKsequence usingbasis.However,in our protocol,Charlie performs four kinds of unitary operations.In our first improvement,if Bob measuresKsequence,then he will not know what the state collapses into.If the state isit can be rewritten as follows.
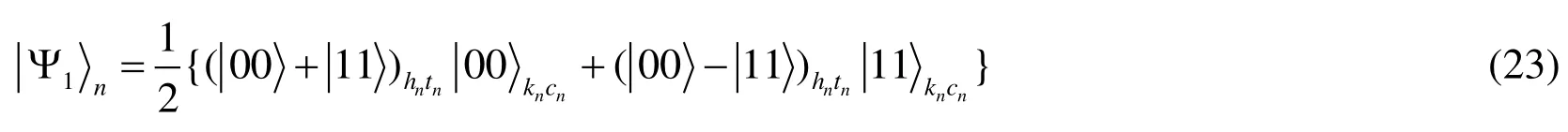
When Bob’s measurement outcome isthe cluster state after the measurement immediately collapses into
Otherwise,the state collapses intoAnd if the state isthe result will be different from the stateWhen Bob’s measurement result isthe state collapses intoOtherwise,the state will collapse intoAnd the rest stateswe can see details in Tab.2.

Table2:Correlations among Bob’s measurement results on K sequence,the states after Charlie’s operations and the collapsed states
It is apparent that Bob cannot know what the state will collapse into after his measurement onKsequence.Therefore,he cannot get rid of Charlie’s control.In the second improvement,the four states can be rewritten as follows.

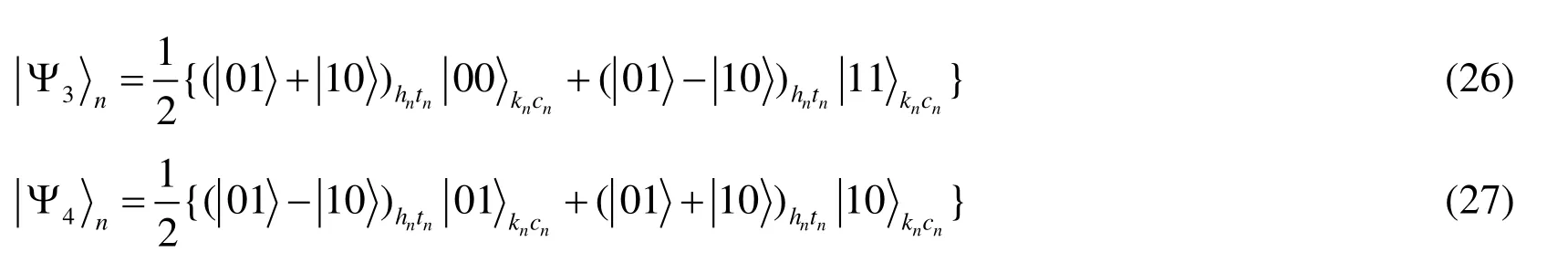
And we can see,if Bob measures particleknbefore Charlie’s measurement,he cannot know what the state will collapse into.So,he can’t get rid of Charlie’s control.
Case3:The out of control attack.Another attack strategy is that when the controller Charlie sendsHsequence to Alice,Bob intercepts it and then sends Alice another particle sequence which prepared by himself in order to get out of Charlie’s control.But in our protocol,Charlie inserts decoy particles randomly inHsequence in (S3),because Bob doesn’t know the exact position and the original state of the decoy particles,he cannot prepare the right fake sequence,so our protocol can resist this kind of attack.
3 A New CQSDC protocol by using three-qubit partially entangled set of states
Without respect to the security of the ZZZ protocol,there still exist another two disadvantages in it.First,it is not easy to obtain a four-particle cluster state in real experimental setups.Second,the efficiency of the protocol is not high,because it uses four particles to transmit one bit secret information.
In this section,we will propose a new protocol by using the three-qubit partially entangled set of states.It is shown that our protocol can resist fake entangled particles attack and disentanglement attack.Moreover,our protocol uses three particles to transmit one bit secret information and three-qubit partially entangled states are also much easier to prepare.
This section is organized as follows.Subsection 3.1 is a detailed description of our new protocol.And in Subsection 3.2,we give the security analysis of our new proposed CQSDC protocol.
3.1 The process of new CQSDC protocol
In 2013,Kumar et al.[Kumar,Adhikari,Banerjee et al.(2013)] pointed out that they can prepare three-qubit partially entangled set of states from the generalized GHZ states.In the beginning,we prepare GHZ states.

A Hadamard operation is applied on the third-qubit of the GHZ state,and we will get the following state
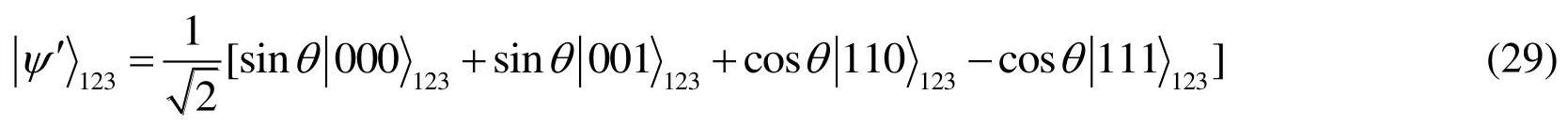
And we perform a CNOT operation on particles 2 and 3.Here,particle 3 is the control one and particle 2 is the target one.Finally,we obtain our communication channel
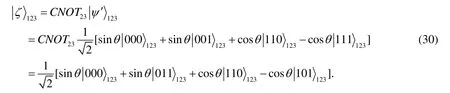
Next,we depict our protocol in detail as follows.
(S1) Charlie preparesN+mthree-qubit partially entangled states.
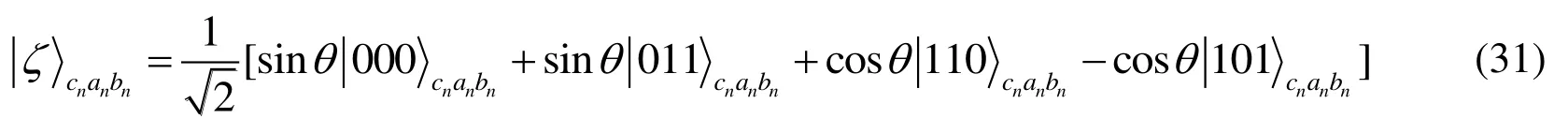
Here,n∈ { 1,N+m},cn,anandbndenote the three particles of the partially entangled state.
Charlie takes the particlescnfrom each state to form an ordered particle sequence[c1,c2,...,cN+m],and names it as theCsequence.Similarly,the remaining particles make upAsequence [a1,a2,...,aN+m]andBsequence [b1,b2,...,bN+m].(S2) Charlie prepares two checking sequences,DAandDBfor the analysis of the eavesdropping.These sequences are large enough.Let the number of particles in them bel.They are randomly chosen fromThen,Charlie minglesDAwithAsequence to getA′sequence andDBwithBsequence to getB′sequence.And he also makes a record of the insertion positions and the measurement basis of the checking particles.Finally Charlie sendsA′sequence to Alice,B′sequence to Bob and holdsCsequence.
(S3) Alice and Bob confirm that they have received the travelling particles.Then,Charlie let Alice and Bob measure checking particles inA′andB′.He tells the positions and the corresponding basis ofDAto Alice andDBto Bob,respectively.

Then,Alice and Bob measure their checking sequences with the corresponding basis announced by Charlie.After that,Alice and Bob notify Charlie of their measurement results.After that,Charlie can determine the existence of the eavesdropping in the communication according to Alice’s and Bob’s measurement results.If the error rate of is higher than a set threshold,Charlie will restart the protocol.Otherwise,they(S4) Alice and Bob check whether the state is the three-qubit partially entangled states or not.Alice asks Charlie to measure his particles usingZ-basis,and then he publishes his measurement results.Then Alice and Bob randomly choosempositions and measure their corresponding particles.That is,Bob measures his particles in using one of two set of measurement basisThen he informs his measurement basis and corresponding measurement results of Alice.According to Bob’s announcement,Alice chooses the same measurement basis and measures her particles.Then she can determine whether they have shared the three-qubit partially entangled states.Here,we must note that if Charlie only prepares Bell states and does not prepare the three-qubit partially entangled states,can our protocol work? The answer is yes.Because Charlie still controls the protocol.If he does not publish his classical bits,then Alice and Bob do not know what states they share.
(S5) We suppose Alice wants to send some messages to Bob.In the (S4),if Charlie obtains the result0c,particles (an,bn)will collapse into

Otherwise,particles (an,bn)will collapse into

(S6) Alice and Bob use the local operationUnm(n,m=0,1)to encode secret information.Here,U00=I,U01=σx,U10=-iσy,andU11=σz.let two cbit strings 00,01,10 and 11 correspond to them,severally.
Alice sets two particles as an encoding-decoding group,such as particlesa1anda2as group 1,particlesa3anda4as group 2,etc.,and Bob sets his encoding-decoding group too.
Alice performs the operationUnmon the encoding-decoding groups to encode her two-bit secret information.Then,she uses Bell bases to measure all the encoding-decoding groups and announces her measurement results and the group’s order.(S7) Bob measures his encoding-decoding groups using Bell basis too.Subsequently,he can get Alice’s secret information after he knows Alice’s and Charlie’s measurement results.For example,we assume Charlie’s measurement results arethen Alice’s and Bob’s particles collapse into the state

If Alice performsU00on one particle of group 1,then the state composed particles(a1b1;a2b2)is
If Alice’s result of a Bell state measurement isit’s easy to conclude that Bob’s measurement result isThus,Bob can obtain that Alice performs a00Uoperation on one particle of group 1 and,therefore,extract the bits (00),and he can read the two-bit secret information.
3.2 Security analysis
In this section,we show our protocol is secure under some possible types of attacks as follows.
Case1:The intercept-and-resend attack.In our protocol,the eavesdropper doesn’t know the exact position and the original state of the decoy particles,(e.g.,since these particles are randomly inserted in the transmitted sequences (for instance,H'sequence,T'sequence,K'sequence).Therefore,if the eavesdropper try to measure and resend the particles,the probability to be detected will be 1-(3/4)l.Here,ldenotes the number of decoy particles.Iflis large enough,the eavesdropping detection probability 1-(3/4)lis approximately 1.
Case2:The entangle-and-measure attack.An eavesdropper Eve may try to obtain the secret information between Alice and Bob.However,he does not know the positions and the states of the checking particles in the intercepted Charlie’s sequenceH′.For instance,Eve prepares some ancillary particlesand entangles these ancillary particles with theH'sequence via a unitary operation.
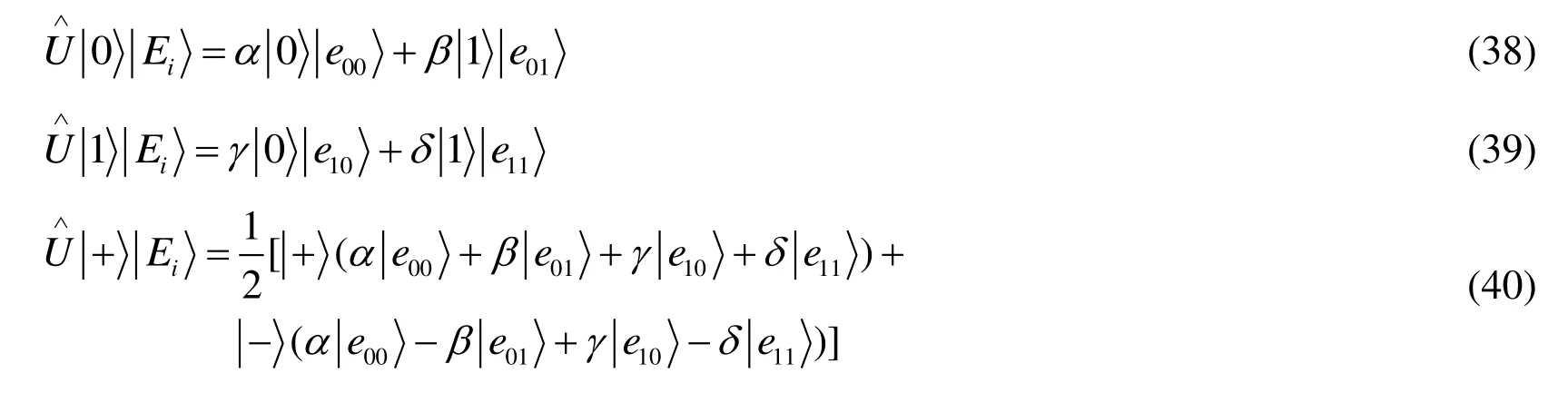
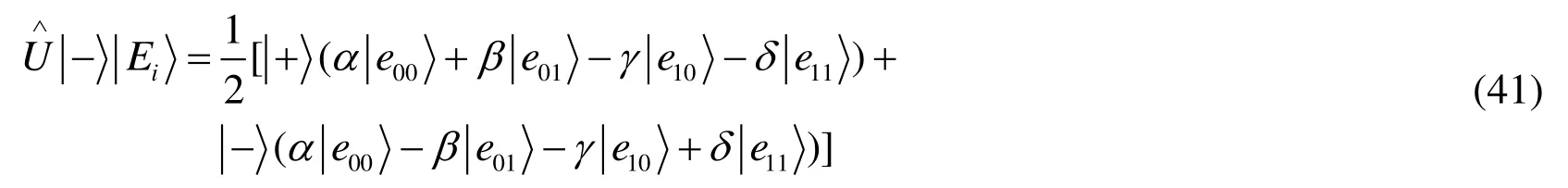
Case3:The fake entangled particles attack.Because we only use three-particle states as a communication channel and the controller Charlie prepares states,Bob cannot prepare two entangled states instead of the three-qubit partially entangled set of states.However,chances are that Charlie may prepare other states instead of three-qubit partially entangled state to obtain Alice secret information.Under this condition,Charlie may send one particle to Bob and shares one entangled state with Alice.But in the check of the three-qubit partially entangled state,Alice and Bob can conclude that error rate is higher than a set threshold.Charlie does not know Alice’s operations,so he can guess wrong with the possibility of 1/2.And there arementangled states,therefore he has the possibility of (1/2)mto guess all right,which is impossible whenmis large enough.Thus,fake entangled particles attack cannot work.
Case4:The disentanglement attack.Each of the three parties (Alice,Bob and Charlie)only has one particle of the three-qubit partially entangled state,so Bob cannot measure his particles to get rid of the control of Charlie,which means,using disentanglement attack is not effective.For example,we assume Charlie prepares three-qubit partially entangled state in (13).

After Bob measures his particles,if his measurement result isparticles (cn,an)will collapse into the state

If his measurement results isparticleswill collapse into the state

We can conclude that Bob’s particles are no longer entangled with Alice’s,and he cannot get any secret information from Alice.Thus,disentanglement attack is not effective in this condition.
Case5:The modification attack.In this attack,the eavesdropper Eve may try to perform malicious modify operations on the particles which Charlie wants to send Alice or Bob.However,Charlie doesn’t know the positions of the decoy particles,so the modify operations will lead to the wrong measurement results of checking particles.
4 Conclusion
In this paper,we have analyzed the reasons why the ZZZ protocol is insecure under fake entangled particles attack and disentanglement attack.Firstly,it is the secret receiver Bob who prepares the four particles cluster state.So he can prepare other states which are beneficial to him.Moreover,he is the last one to measure his particles.Then,he can perfectly deceive the controller,Charlie,by preparing two fake entangled particles without being detected.Secondly,Bob has half particles of the states and one of his two particles is equivalent to Alice’s,another is equivalent to Charlie’s.So it is easy for Bob to measure his particle which is equivalent to Charlie’s to get rid of Charlie’s control.In essence,this happens because Charlie’s control information is not enough and Bob has too much power.Therefore,by making Bob powerless and Charlie have more control information,we have proposed a new improved secure protocol.In our new protocol,we have two versions of improvement,and both of them can prevent the two attack strategies we have mentioned above.
Besides,we have proposed a novel secure protocol using a more useful and practical state,the three-qubit partially entangled set of state.In our protocol,on one hand,it is impossible for Bob to carry out fake entangled particles attack,for he is not the one who prepares the three-qubit partially entangled set of states,and it is also impossible for Charlie to deliver fake entangled particles attack,for he will be detected by Alice and Bob in the detection of three-qubit partially entangled states.On the other hand,it is difficult for Bob to carry out disentanglement attack too.Because he has only one particle of the state,he cannot measure his particle to make Charlie out of control of their communication.We also analyze some other possible attacks and find out these attacks do not work.And also,we have pointed out that our protocol is easier and more secure to prepare the resource states.Moreover,efficiency in transmitting of secret information via a particle is higher than Chen et al.’s protocol [Chen,Wang,Du et al.(2008)].In addition,our protocol needs less measurement resource,which makes this protocol more convenient from an applied point of view.
Acknowledgement:Project supported by NSFC (Grant Nos.61671087,61272514,61170272,61003287,61571335,61628209),the Fok Ying Tong Education Foundation(Grant No.131067),the National Key R&D Program of China under Grant 2017YFB0802300,the Open Foundation of Guizhou Provincial Key Laboratory of Public Big Data (2018BDKFJJ016) and Hubei Science Foundation (2016CFA030,2017AAA125).
杂志排行
Computers Materials&Continua的其它文章
- R2N:A Novel Deep Learning Architecture for Rain Removal from Single Image
- Yield Stress Prediction Model of RAFM Steel Based on the Improved GDM-SA-SVR Algorithm
- A Straightforward Direct Traction Boundary Integral Method for Two-Dimensional Crack Problems Simulation of Linear Elastic Materials
- Effect of Reinforcement Corrosion Sediment Distribution Characteristics on Concrete Damage Behavior
- Research on the Law of Garlic Price Based on Big Data
- Modeling and Analysis the Effects of EMP on the Balise System
