Countermeasure against blinding attack for single-photon detectors in quantum key distribution
2024-04-23LianjunJiangDongdongLiYuqiangFangMeishengZhaoMingLiuZhilinXieYukangZhaoYanlinTangWeiJiangHoulinFangRuiMaLeiChengWeifengYangSongtaoHanandShibiaoTang
Lianjun Jiang, Dongdong Li,2,3,†, Yuqiang Fang, Meisheng Zhao,2,3, Ming Liu, Zhilin Xie,4,Yukang Zhao, Yanlin Tang, Wei Jiang, Houlin Fang, Rui Ma, Lei Cheng, Weifeng Yang, Songtao Han,and Shibiao Tang,2,3,6,†
1QuantumCTek Co., Ltd., Hefei 230088, China
2Shandong Institute of Quantum Science and Technology Co., Ltd., Jinan 250101, China
3QuantumCTek (Beijing) Co., Ltd., Beijing 100193, China
4School of Cyber Science and Technology, University of Science and Technology of China, Hefei 230027, China
5Anhui Armed Police Force, Hefei 230026, China
6School of Electrical Engineering and Automation, Anhui University, Hefei 230601, China
Abstract: Quantum key distribution (QKD), rooted in quantum mechanics, offers information-theoretic security.However, practical systems open security threats due to imperfections, notably bright-light blinding attacks targeting single-photon detectors.Here, we propose a concise, robust defense strategy for protecting single-photon detectors in QKD systems against blinding attacks.Our strategy uses a dual approach: detecting the bias current of the avalanche photodiode (APD) to defend against continuous-wave blinding attacks, and monitoring the avalanche amplitude to protect against pulsed blinding attacks.By integrating these two branches, the proposed solution effectively identifies and mitigates a wide range of bright light injection attempts, significantly enhancing the resilience of QKD systems against various bright-light blinding attacks.This method fortifies the safeguards of quantum communications and offers a crucial contribution to the field of quantum information security.
Key words: quantum key distribution; single photon detector; blinding attack; pulsed blinding attack; countermeasure; quantum communication
1.Introduction
In the context of today's rapid digital advancement, the proliferation and expansion of networks undeniably underscore the significance of communication security.Quantum key distribution (QKD), rooted in the fundamental principles of quantum mechanics, possesses the unique capability to generate theoretically secure symmetric keys between distant parties[1,2], thereby offering a highly secure communication for the impending quantum computing era[3,4].After decades of sustained research and development, QKD technology has achieved remarkable progress[5-10], with notable enhancements in key performance metrics such as secure key rate and transmission distance[11-13], and continuous expansion in application scenarios[14-18].Various backbone and metropolitan networks have commenced the practical application of networked solutions[19-21].Free-space QKD has also realized secure satellite-to-ground communications[22,23], and the integrated space-to-ground quantum secure communication network has been experimentally demonstrated[24,25].
Although the information-theoretic security of QKD has been rigorously proven[2], this cannot ensure the security of the practical devices employed[26].The physical properties of the components in actual devices might deviate from the models in theoretical proofs, leaving room for quantum hacking exploits[27-30].Specifically, single-photon detectors at the receiving end are vulnerable to several potential attacks,including the blinding attack[31-33], the after-gate attack[34],the dead-time attack[35], the time-shift attack[36], the superlinear attack[37], the device calibration attack[38], the double-click attack[39], and the backflash attack[40], among others.Blinding attacks, in particular, involve bombarding the avalanche photodiode (APD) with bright illumination, causing it to regress from Geiger mode to linear mode, thereby manipulating the single-photon detector's response.Given the relative ease of executing blinding attacks and their potential to compromise the entire key information upon successful execution, they warrant serious attention in QKD systems.Existing protective strategies primarily involve monitoring the bias current of APDs[41-43], triggering an attack warning when the current escalates.However, this method suffers from low detection bandwidth and fails to detect blinding attacks using pulsed light[44,45].
In this paper, we present a countermeasure designed to fortify quantum key distribution systems against blinding attacks.Our approach centers around a schematic configuration that incorporates bias current detection and avalanche amplitude monitoring, tailored specifically for sinusoidally gated single-photon detectors[46,47].It effectively alerts to a wide range of bright light blinding attacks executed with continuous or pulsed light.Such a capability is instrumental in bolstering the security framework of practical QKD systems, effectively shielding them from a spectrum of blinding attacks.Moreover, the practicality and effectiveness of this strategy have been experimentally validated.
2.Method
QKD systems typically use gate-triggered Geiger-mode APDs as detectors.An APD operates in linear mode when the applied reverse bias voltage is below its breakdown voltage.Conversely, it enters Geiger mode when the reverse bias exceeds the breakdown voltage.During operation, these detectors are susceptible to a vulnerability called the blinding attack, where strong laser injections cause them to degrade from Geiger mode to linear mode.If blinded, detectors cannot response to single-photon signals.The attacker, named EVE, can exploit this vulnerability, forcing the detector into linear mode during a period called the blinding interval.While in this mode, EVE can trigger the detector with strong pulses.By adjusting the intensity correctly, she can hide her attacking activities.Considering APDs' operating principles and attack methods, we have developed a solution to protect high-speed, sinusoidally gated single-photon detectors in QKD systems from blinding attacks, as shown in Fig.1.
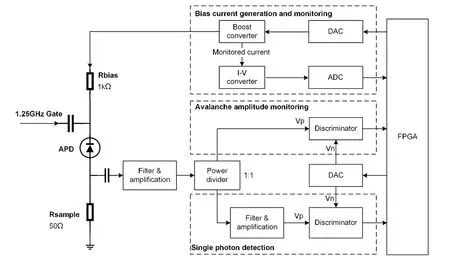
Fig.1.Schematic of the countermeasure against blinding attack for single-photon detectors.
A field-programmable gate array (FPGA) drives a boost converter through a DAC to provide the reverse bias voltage to the APD.This voltage, slightly lower than the APD's avalanche breakdown voltage (approximately 65 V), is applied to the APD's cathode through a Rbias (1 kΩ), rendering the APD incapable of single-photon detection as it operates in linear mode.A 1.25 GHz gating signal (10 V), superimposed on the reverse bias voltage via AC coupling, is applied to the APD's cathode, pushing the APD's reverse voltage above its avalanche breakdown voltage and enabling singlephoton detection in Geiger mode.
If the attacker launches a continuous-wave (CW) blinding attack, a persistent photocurrent is generated inside the APD.Due to the voltage division effect of the series resistance Rbias at the APD's cathode, even when the gating signal arrives, the reverse voltage across the APD remains below the avalanche breakdown voltage, keeping the APD in linear mode and leading to the detector being blinded throughout.To counter such attacks, we monitor the APD bias current to defend against continuous-wave blinding attacks.Specifically, we use a boost converter with current detection capability (model: SGM41285A) that can not only generate APD bias voltages ranging from 10 to 70 V but also mirror the APD bias operating current at a 1∶1 ratio.This mirrored current,referred to as "bias current", is digitized afterI-Vconversion and sampled by an ADC (model SGM58031, with the resolution of 16 bit and the sampling rate of 960 Hz).The FPGA controller continuously reads the sampled voltage values, using the changes in this bias current to identify the intensity of injected light and determine the presence of continuouswave strong light injection behavior.
If the attacker employs a pulsed blinding attack, the APD generates pulsed photocurrents, pushing the APD into a linear mode of operation.However, the strong light pulses are transient, causing the detector to be blinded only intermittently.Consequently, methods that monitor APD bias current are less sensitive to pulsed light and struggle to promptly detect such attacks.To counter these types of attacks, we capitalize on the inherent avalanche multiplication property of APDs, where stronger light induces larger photocurrents.We have developed a method to identify instances of pulsed bright light injection by recognizing the amplitudes of the avalanche signals.
The process begins with the avalanche signal from the APD's anode, which is first passed through a 50 Ω sampling resistor.It then undergoes initial filtering and amplification with a 25 dB gain via AC coupling.Subsequently, a 1∶1 power divider splits the signal into two separate paths.The first path is designated for single-photon detection.It extracts signals caused by single-photon avalanches, which have relatively low amplitudes.To ensure that these signals are discernible, they undergo further filtering and a second amplification stage (with a 20 dB gain) to elevate them to a few hundred millivolts.After reaching this level, a discriminator (model ADCMP572, with the bandwidth of 8 GHz) set at 50 mV for pulse recognition processes these signals.These regular detection events are then relayed to an FPGA for additional data processing.The second path is responsible for detecting bright pulsed light.The amplitude of these avalanches is much greater than that of single-photon avalanches and, are therefore detected after the first amplification stage.Additional amplification would risk saturating the amplifier's output, which would restrict the measurable range of light intensity.Thus, this channel bypasses further amplification and proceeds directly to amplitude discrimination.The discrimination threshold is adjustable, based on desired sensitivity levels.Once a signal exceeds this threshold, it is classified as an abnormal detection signal and fed into the FPGA.The FPGA then assesses whether the APD has been subjected to pulsed bright light injections.If it detects avalanche signals above the set threshold, an alarm is triggered to indicate a blinding attack.
Monitoring the bias current enables the identification of continuous-wave bright light injection, while avalanche amplitude monitoring detects pulsed bright light injection.Integrating these two strategies allows for comprehensive identification of various types of bright light injection.
3.Experimental test
We have developed a high-speed sinusoidally gated single-photon detector building on the protective strategies previously outlined.This detector has been tested and verified through comprehensive bright light injection experiments.The primary technical specifications of this single-photon detector are as follows: gating frequency at 1.25 GHz, dead time of 100 ns, detection efficiency of 20%, dark count rate of 1 kcps, and an after-pulse probability of 2%.The test environment for the blinding attack is shown in Fig.2.

Fig.2.(Color online) Test environment for the countermeasure against blinding attack.
To verify the defense effectiveness against continuouswave blinding attacks, our initial tests, conducted under CW attack conditions, determined the average optical power at which the detector becomes non-responsive.Appropriate bias current detection alarm thresholds were set.Fig.3 displays the detector count and bias current detection responses across a range of injected optical power.The right vertical axis represents the bias current code, referring to the quantized code value of the bias current after it has been converted through theI-Vprocess and subsequently captured by the ADC.
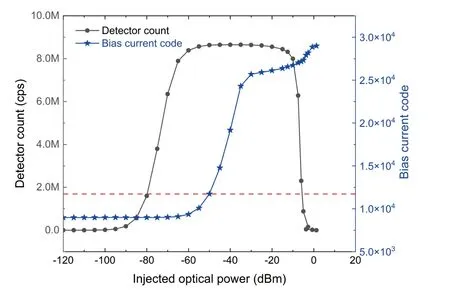
Fig.3.(Color online) Test for continuous-wave bright light injection.
As observed in Fig.3, the detector count markedly increases at an injected light power of -95 dBm, reaches saturation at -65 dBm, and plummets to nearly zero at around 0 dBm, indicating that the detector is blinded at this point.To ensure security, the detector should trigger an alarm and initiate preventive actions before reaching this blinded state,thus highlighting the need for setting a maximum light power threshold for the alarm.From the perspective of detection sensitivity, enhancing the ability to detect lower intensity light injections is crucial.Considering that the bias current code is 8890 with no light present—reflecting the intrinsic electronic current bias, including the avalanche photodiode (APD) reverse operating current and the bias detection working current—we established the alarm threshold at a bias current code of 12933, corresponding to -50 dBm of bright light injection, as denoted by the red dashed line in Fig.3.This setting allows for the detection of bright light injection activity 50 dB before the detector is at risk of being blinded.
To assess the defense against pulsed blinding attacks, we conducted tests targeting pulsed light injections.Pulsed blinding attacks can vary in emission frequency, intensity, temporal width, and the timing of injection.We carried out tests using a range of typical values for validation.Due to the unique gate signal waveform of the sinusoidally gated detector, detection efficiency differs across various areas, leading to a range of bright light avalanche pulse intensities.Initially,we used narrow pulsed light with a frequency of 625 kHz and a full width at half maximum (FWHM) of 50 ps, injecting it over the full gating period range of 800 ps.This tested the amplitude values of bright light avalanche pulses at different time, helping to establish the alarm threshold for bright light amplitude detection.We then applied attack light at the same frequency (625 kHz) with FWHMs of 50 ps, 1 ns, and 10 ns to span out-of-gate, in-gate, and the entire gate period regions.This comparison between bias current detection and avalanche amplitude detection informed our defense strategy against pulsed light attacks.
Fig.4 displays the avalanche amplitudes under varying optical power—ranging from 100to 105photons/pulse.Across all gating areas, the avalanche amplitude rises with increased injected light power.Additionally, the amplitude of the bright light avalanche is much greater than that from single-photon avalanches, which reaches a maximum of 60 mV as shown in Fig.4.When light intensity hits 103photons/pulse, the bright light avalanche amplitude reaches maximum value due to the saturation of the first-stage amplifier.Setting a lower detection threshold for bright light avalanche amplitude will lead to earlier detection of pulsed light injections.However, if the threshold is set too low, noise could cause false alarms.According to the results shown in Fig.4,we have set the alarm generation threshold at 200 mV, which correlates to tens of photons/pulse and is substantially above the single-photon avalanche pulse's maximum amplitude.The occurrence of even a single signal exceeding this threshold would indicate a pulsed blinding attack event.

Fig.4.(Color online) Detector response to pulsed blinding attack at different time of the gate.Each curve corresponds to a specific optical pulse intensity ranging from 100 to 105 (in the unit of photons/pulse).
Fig.5 shows the response of bright light avalanche detection counts and bias current codes to injected optical power,evaluating their efficacy in preventing pulsed light attacks.The horizontal red dashed line indicates the bias current detection alarm threshold, and a vertical black dashed line denotes the injected optical power at which all attack pulses are detectable.When subject to 50-ps narrow pulsed blinding attacks, both in-gate and out-of-gate, the bias current code increases slightly (from approximately 8850 to 8950) with higher injected light power, yet remain well below the alarm threshold of 12933.Consequently, bias current detection does not trigger an alarm and fails to detect pulsed light injection.In contrast, avalanche amplitude monitoring successfully identifies all attack pulses and events.For attacks using 1-ns and 10-ns pulsed light that span the entire gating period, the bias current rises more noticeably with increased injected light power (from about 8850 to 10500), but are still significantly lower than the alarm threshold.Therefore, bias current detection is unable to initiate an alarm and cannot discern pulsed light injection, while avalanche amplitude monitoring continues to effectively detect all attack pulses and events.

Fig.5.(Color online) Detector response to different pulse width of blinding attack.(a) Attack using pulse of 1-ns-width.(b) Attack using pulse of 10-ns-width.(c) In-gate attack using pulse of 50-ps-width.(d) Out-of-gate attack using pulse of 50-ps-width.
It is worth noting that lowering the threshold for bias current detection may marginally improve the sensitivity to detecting continuous-wave and pulsed light injections.Nevertheless, this method is vulnerable as attackers can simply decrease their attack frequency, leading to negligible changes in the average light power and thus, neutralizing the effectiveness of bright light attack detection that relies on APD bias current.On the other hand, the defense strategy that employs avalanche amplitude monitoring retains its efficacy against such low-frequency attacks.
4.Conclusion and outlook
In summary, we have proposed and demonstrated a countermeasure against blinding attack of the single-photon detectors in quantum key distribution.Our solution employs a dual-faceted approach combining bias current detection and avalanche amplitude monitoring, optimized for sinusoidally gated single-photon detectors.It is also adaptable for pulsed gated single-photon detectors, requiring adjustments in the signal extraction processing.This strategy has shown to be effective, offering preemptive alerts to a variety of bright light blinding assaults, utilizing both continuous-wave and pulsed light sources.Its implementation enhances the security infrastructure of QKD systems, providing robust protection against a wide range of blinding tactics.The feasibility and effectiveness of our approach is further affirmed by comprehensive experimental validation, contributing a significant enhancement to the domain of quantum cryptography security.
Acknowledgments
This work was supported by the Major Scientific and Technological Special Project of Anhui Province(202103a13010004), the Major Scientific and Technological Special Project of Hefei City (2021DX007), the Key R & D Plan of Shandong Province (2020CXGC010105), and the China Postdoctoral Science Foundation (2021M700315).
杂志排行
Journal of Semiconductors的其它文章
- Chemical vapor deposition for perovskite solar cells and modules
- Highlights in recent wireless power IC research
- Recent advancements in continuously scalable conversion-ratio switched-capacitor converter
- Towards efficient generative AI and beyond-AI computing:New trends on ISSCC 2024 machine learning accelerators
- Millimeter-wave PA design techniques in ISSCC 2024
- Light-emitting devices based on atomically thin MoSe2
