Improving Video Watermarking through Galois Field GF(24)Multiplication Tables with Diverse Irreducible Polynomials and Adaptive Techniques
2024-03-12YasminAlaaHassanandAbdulMonemRahma
Yasmin Alaa Hassan and Abdul Monem S.Rahma
1Department of Computer Science,College of Science,University of Baghdad,Baghdad,Iraq
2Department of Computer Science,College of Science,Al-Maarif University College,Al-Anbar,Iraq
ABSTRACT Video watermarking plays a crucial role in protecting intellectual property rights and ensuring content authenticity.This study delves into the integration of Galois Field (GF) multiplication tables,especially GF(24),and their interaction with distinct irreducible polynomials.The primary aim is to enhance watermarking techniques for achieving imperceptibility,robustness,and efficient execution time.The research employs scene selection and adaptive thresholding techniques to streamline the watermarking process.Scene selection is used strategically to embed watermarks in the most vital frames of the video,while adaptive thresholding methods ensure that the watermarking process adheres to imperceptibility criteria,maintaining the video’s visual quality.Concurrently,careful consideration is given to execution time,crucial in real-world scenarios,to balance efficiency and efficacy.The Peak Signal-to-Noise Ratio(PSNR)serves as a pivotal metric to gauge the watermark’s imperceptibility and video quality.The study explores various irreducible polynomials,navigating the trade-offs between computational efficiency and watermark imperceptibility.In parallel,the study pays careful attention to the execution time,a paramount consideration in real-world scenarios,to strike a balance between efficiency and efficacy.This comprehensive analysis provides valuable insights into the interplay of GF multiplication tables,diverse irreducible polynomials,scene selection,adaptive thresholding,imperceptibility,and execution time.The evaluation of the proposed algorithm’s robustness was conducted using PSNR and NC metrics,and it was subjected to assessment under the impact of five distinct attack scenarios.These findings contribute to the development of watermarking strategies that balance imperceptibility,robustness,and processing efficiency,enhancing the field’s practicality and effectiveness.
KEYWORDS Video watermarking;galois field;irreducible polynomial;multiplication table;scene selection;adaptive thresholding
1 Introduction
In the rapidly evolving landscape of multimedia content,video watermarking stands as a crucial mechanism for safeguarding intellectual property rights,curbing unauthorized distribution,and ensuring the authenticity of digital content [1].This field has witnessed significant advancements,with researchers continuously exploring innovative techniques to strike a delicate balance between imperceptibility and robustness in watermarking applications[2,3].
Video watermarking is a technique used to embed hidden information,such as a logo,copyright notice,or owner’s identification,into a video in a way that is imperceptible to human viewers [4,5].The purpose of video watermarking is to protect intellectual property rights,prevent unauthorized distribution or piracy,and track the origin of the content[6].One approach to video watermarking is by utilizing the mathematical properties of finite fields,specificallyGF(24),also known as the Galois field.A Galois field is a finite field with a prime number of elements,andGF(24)is a particular type of Galois field with 16 elements[7,8].It is represented using binary polynomials of degree 4.GF(24)is a suitable choice for video watermarking due to its ability to perform bitwise operations,such as XOR,which are essential for manipulating the video data at the bit level.These operations allow for the seamless embedding of watermark information without significantly affecting the visual quality of the video[9].
Video watermarking has emerged as a pivotal technique for safeguarding multimedia content from unauthorized distribution and manipulation [10].This study presents a comprehensive comparative analysis of video watermarking employing Galois Field (GF) multiplication tables with diverse irreducible polynomials in the context ofGF(24).In addition,the study incorporates an adaptive thresholding mechanism for scene selection,enhancing the watermarking process’s efficiency.
The selection of an appropriate irreducible polynomial significantly influences the characteristics of the Galois Field,directly affecting the watermark embedding processes.To enhance the performance of watermarking schemes,an adaptive thresholding approach is introduced during scene detection,dynamically adjusting the threshold value based on the pixel intensity distribution within frame differences.This mechanism contributes to the identification of significant scene changes,optimizing the selection of frames for watermark embedding [11].Watermarks are embedded in selected frames through XOR blending,utilizing watermark values represented via the chosenGFmultiplication table.The study provides insights into the trade-offs between various irreducible polynomials,computational efficiency,and watermarking performance,considering adaptive scene selection.
The evaluation and validation of watermarking techniques are inherently multifaceted endeavors.The proposed approach leans on the Peak Signal-to-Noise Ratio(PSNR)as a yardstick to measure the watermark’s imperceptibility and the resultant video quality.This metric provides a reliable gauge for understanding the subtle yet critical interplay between watermark imperceptibility,execution time,and computational complexity.In the realm of multimedia security and watermarking,several noteworthy developments have contributed to the evolution of techniques and methodologies.In one instance,a watermarking method,as discussed in [12],drew on the foundation of Discrete Wavelet Transform and Singular Value Decomposition (DWT-SVD) but elevated its capabilities by harnessing Particle Swarm Optimization (PSO).This adaptation sought to bolster the method’s resistance to diverse attacks while preserving its imperceptibility.Furthermore,both the conventional and the enhanced algorithms exhibited a distinct diagonal line pattern in the extracted watermark image when subjected to specific noise attacks.
Meanwhile,reference[13]introduced an innovative approach that leveraged the Jigsaw Transform(JT) in tandem with the iterative cosine transform within a finite field for image encryption and decryption.The JT,characterized as a nonlinear operation,played a pivotal role in enhancing the security of encrypted images through the introduction of new encryption keys and decryption mechanisms.This approach was firmly rooted in the principles of finite fields,where a finite set of integer numbers underpinned mathematical operations conducted using modular arithmetic.
The dynamic realm of video watermarking and scene change detection was explored in[14].To address the challenge of detecting scene changes in complex environments,a novel approach was presented.Central to this approach was the introduction of a novel color descriptor,the local color difference pattern (LCDP),which remained resilient in the presence of shadows while effectively capturing both color and texture features at the pixel level.In addition,a scene change detection framework was introduced,built on the concept of sample consensus,seamlessly integrating LCDP and an innovative spatial model fusion mechanism.
Another pioneering method,as documented in [15],offered a compelling solution to alleviate the computational burden associated with video classification while simultaneously bolstering its accuracy.The heart of this approach lay in its intelligent frame selection process,which judiciously eliminated challenging-to-classify frames.Departing from the conventional practice of evaluating frames in isolation,this method undertook a collective assessment,resulting in a more efficient and balanced selection of‘high-quality’frames.The outcome resembled the creation of a coherent narrative through evenly distributed snapshots throughout the video.Reference[16]focused on the construction of S-boxes,particularly utilizing coset graphs and group actions involving the alternating group A5 and the symmetric group S256 over finite fields.The core of the work involves analyzing the constructed Sboxes against various security criteria to assess their cryptographic strength.Additionally,the S-box’s performance in image encryption is evaluated,demonstrating its capability to enhance data security against cyber-attacks.
In a world where multimedia content is ceaselessly evolving,and where security concerns parallel the pace of innovation,this study holds the potential to redefine watermarking strategies.By unraveling the symphony ofGFmultiplication tables,irreducible polynomials,scene selection,adaptive thresholding,imperceptibility,execution time,and PSNR,this exploration advances our understanding and fortifies the foundation for future multimedia security endeavors[17].
The subsequent sections of this paper have been organized as follows: Section 1.1 introduces the fundamentals ofGF(24),Section 1.2 discusses Scene Detection and Frame Selection,Section 1.3 elaborates on Adaptive Thresholding for Frame Selection,Section 1.4 outlines image and video watermarking: similarities and differences.The proposed method is detailed in Section 2,and the experimental results and discussions are presented in Section 3.The conclusion is provided at the end of this work(Section 4).
1.1 GF(24)Multiplication Table and Its Transformative Role
The utilization of Galois FieldGF(24)multiplication tables in video watermarking indeed represents a unique and innovative approach in the field of digital watermarking.This concept provides a novel knowledge-based way to manipulate pixel values within video frames,facilitating subtle and effective watermark embedding.While digital watermarking techniques have been explored extensively,the specific application ofGF(24) multiplication tables for this purpose appears to be a pioneering idea,offering new avenues for research and development in the field of multimedia security and content protection.Further exploration and experimentation in this area could yield valuable insights and potentially lead to advancements in video watermarking technology.
1.2 Scene Detection and Frame Selection
Scene detection involves the identification of transitions between scenes in the video,such as cuts or fades,to determine significant changes in content.These transitions indicate potential scene changes,which are crucial for determining the appropriate frames to watermark.The algorithm analyzes the differences between consecutive frames,considering factors like frame intensity,to pinpoint scene change instances.Once these instances are detected,a predetermined percentage of frames,often around 20%of the total frames,is selected for watermarking.The rationale behind this selection is to ensure a representative sample while avoiding overloading the video with watermarked frames,which could affect the video’s perceptual quality[18–20].
1.3 Adaptive Thresholding for Frame Selection
This section explores the concept of adaptive thresholding,a critical aspect of frame selection.Adaptive thresholding is a dynamic technique that calculates thresholds based on the specific characteristics of the data under analysis.In the context of video watermarking,it plays a vital role in distinguishing frames with substantial content changes from those with minor variations.
Rather than relying on a single fixed threshold,this approach utilizes adaptive thresholding,allowing it to compute local thresholds for distinct video frames.This adaptive strategy is contextaware and responsive to local frame features,ensuring that frames are chosen based on their content and context.This dynamic approach enhances scene change detection precision and results in the selection of frames with unique and substantial content.The adaptive thresholding technique is particularly valuable when dealing with videos that encompass varying lighting conditions,complex scenes,or rapid content alterations.It effectively overcomes the limitations associated with traditional frame selection methods[21,22].
Moreover,the use of adaptive thresholding is well-suited for video watermarking applications,as it helps ensure that watermarks are inserted into frames where they are least likely to disrupt the video’s quality or visibility.This balances the imperceptibility and robustness of the watermark,a critical factor in ensuring viewer satisfaction and the preservation of the video’s authenticity.The application of adaptive thresholding ensures that the scene detection process remains adaptable to variations in lighting,motion,and content complexity,resulting in a more precise and context-aware selection of frames for watermarking[23,24].
1.4 Image and Video Watermarking:Similarities and Differences
This section delves into the world of watermarking and explores the shared attributes and distinctions between watermarking techniques applied to both images and videos.By highlighting these similarities and differences,a comprehensive understanding of how watermarking strategies are adapted to suit the characteristics of images and videos is provided,offering valuable insights into the domain of multimedia content protection.
1.4.1 Similarities
• Embedding Process: Both photos and videos undergo an embedding process to insert a watermark.This typically involves altering the pixel values in the media to incorporate the watermark information.
• Watermark Extraction: Both photos and videos require an extraction process to retrieve the watermark.Special algorithms and keys are used to separate the watermark from the media.
• Purpose:The primary purpose of watermarking in both photos and videos is to claim ownership,protect copyright,and deter unauthorized use.
1.4.2 Differences
• Temporal Context: Frames in a video are temporally related,and it is essential to consider this temporal context when watermarking videos.Unlike images,videos involve a sequence of frames where each frame follows the preceding one.
• Scene Changes: Videos often contain scene changes,where the content or context may shift abruptly.These scene changes impact the watermarking process.In contrast,images do not have scene changes,making the watermarking process more straightforward.
• Efficiency: Frame processing allows to optimization of the algorithm by watermarking only selected frames,typically at scene changes or predetermined intervals.This approach reduces computational load and minimizes potential visual artifacts in the video.
In summary,while image processing deals with standalone images,frame processing considers the unique characteristics of video data,such as temporal context,scene changes,efficiency,and visual continuity.These distinctions are necessary for the effective and robust watermarking of videos,ensuring that the watermark is both imperceptible and resistant to removal[3,25–27].
2 Proposed Method
Watermarking,a pivotal facet of multimedia security,is tasked with embedding hidden information into digital content to safeguard intellectual property,combat unauthorized distribution,and ensure authenticity.However,watermarking presents challenges,including imperceptibility to human perception,and computational efficiency.This study seeks to tackle these challenges by creatively incorporatingGFmultiplication tables with scene selection techniques based on adaptive thresholding.The main goal is to improve the efficiency of watermarking by utilizing the unique properties offered by theseGFmultiplication tables.These tables,rooted in abstract algebra,offer properties conducive to robust watermarking,such as information hiding,error correction,and tamper detection.The methodology centers on harnessing these properties for watermark embedding,ultimately contributing to a more secure and authentic multimedia landscape.The effective utilization ofGFmultiplication tables hinges on their meticulous construction.This involves creating these tables and subsequently employing them as a transformative tool for embedding watermarks.The transformation involves XOR blending of watermark values derived from the selectedGFmultiplication table.The strategic choice of employing the Galois field with 16 elements (GF(24)) significantly influenced the research direction in this study.Deliberately prioritizing the 4 least significant bits(LSB)within this field was undertaken to mitigate any potential impact on video quality.It is important to note that the 4 LSB represent a relatively minor portion of the data,as opposed to the 4 most significant bits (MSB).Specifically,GF(24)(GF(16))was opted for to strike an equilibrium between computational complexity and imperceptibility.By concentrating on the 4 LSB,video quality was successfully maintained at an acceptable level while managing computational demands.Various irreducible polynomials withinGF(24),such as (x4+x+1) or (x4+x3+1) or (x4+x3+x2+x+1) have been used as a comparative exploration of watermarking process.Irreducible polynomials fundamentally influence the algebraic properties ofGFmultiplication tables,thereby affecting watermarking robustness and imperceptibility.The experiment examines these polynomials to identify the most effective one that yields optimal results,both in terms of secure embedding,good quality,and less execution time.Addressing the challenge of selecting frames for watermarking,an adaptive threshold-based approach has been adopted that ensures both diversity and relevance.Specifically,approximately 20%of frames in a video have been chosen to add a watermark.
Overall,this algorithm performs video watermarking by selecting frames based on scene changes and then blending the watermark to the four corners of selected frames using aGF(24) table.The watermarking process is controlled by the frame selection technique,which determines the number of frames to watermark based on the adaptive threshold which is determined automatically depending on the pixel intensity distribution in each video The duration of the videos varies,with some being lengthy and comprising a substantial frame count,while others are shorter and encompass fewer frames.The number of frames to watermark is set to 20%of the total frames,making it a general approach that works for different videos without manually adjusting the threshold value.With this approach,the threshold is determined dynamically based on the pixel intensity distribution in each video.Therefore,it works reasonably well for different videos without the need to manually adjust the threshold value.
2.1 GF(24)Multiplication Tables Construction
The construction of multiplication tables forGF(24)with different irreducible polynomials offers a pivotal exploration into the realm of finite fields.These tables serve as fundamental tools for cryptographic operations and encoding techniques withinGF(24).This comparative study delves into the creation of three distinct multiplication tables using three specific irreducible polynomials.Through a systematic process of generating elements via polynomial reductions and multiplication operations,the distinct properties and attributes of these diverse multiplication tables have been revealed,contributing significant insights to the domain.The following algorithm illustrates theGF(24) multiplication table construction using three irreducible polynomials that result in different three tables used as transformations in this work.

2.2 Frame Selection and Adaptive Thresholding
The calculation of the frame difference can be represented by the following equation:
where:
•frame_diff(i,j):Pixel value of the frame difference at location(i,j)
•I(i,j):Pixel value of the current frame at location(i,j)
•I_prev(i,j):Pixel value of the previous frame at location(i,j)
• ||:Absolute value
This equation calculates the absolute difference between the pixel values of the corresponding locations in the current frame and the previous frame,resulting in the frame difference image.It is a key step in detecting scene changes and determining where the watermark should be added.
The calculation of the adaptive threshold used for scene change detection can be represented by the following equation:
•Threshold:represents the adaptive threshold used for scene change detection.
•hist_sum(k):Cumulative histogram sum up to bin k
•total_pixels:Total number of pixels in the frame
•total_hist_sum:Cumulative histogram sum of the entire frame
In this equation,the adaptive threshold is calculated based on the pixel intensity distribution in the frame difference image.It helps in determining whether the current frame indicates a scene change by comparing the mean difference of the frame with the adaptive threshold.
2.3 Video Watermarking Using GF(24)Multiplication Tables
The forthcoming elucidation delves into each sequential stage of this process,delving into how mathematical theory seamlessly intertwines with video files to attain an exceptional watermark embedding outcome.

Fig.1 illustrates the block diagram of the proposed algorithm visually.This algorithm begins by loading a video and extracting its properties.It then intelligently selects a subset of frames for watermarking based on a user-defined percentage and scene change detection.The watermark,converted intoGF(24)values,is embedded into the selected frames,and the process is timed and assessed using the Peak Signal-to-Noise Ratio(PSNR).The watermarked frames are saved,and the algorithm calculates the average PSNR and execution time for performance evaluation.This approach optimizes the watermarking process for video while considering scene dynamics,ensuring robustness and content preservation.The algorithm seamlessly integrates the watermark with the frames by employing bitwise operations and a carefully selectedGF(24) multiplication table.It prioritizes the 4 least significant bits (LSB),which represent a small fraction of the video data,ensuring the imperceptibility of the watermark while preserving the overall video quality.
Overall,this algorithm performs video watermarking by selecting frames based on scene changes and then blending the watermark in selected frames using aGF(24) table.The more frames you select for watermarking,the lower the PSNR is likely to be due to the increased modifications to the video content.Conversely,if you select too few frames,the watermark might not be robust enough.You can adjust this value based on your requirements and the desired trade-off between watermark imperceptibility and robustness.
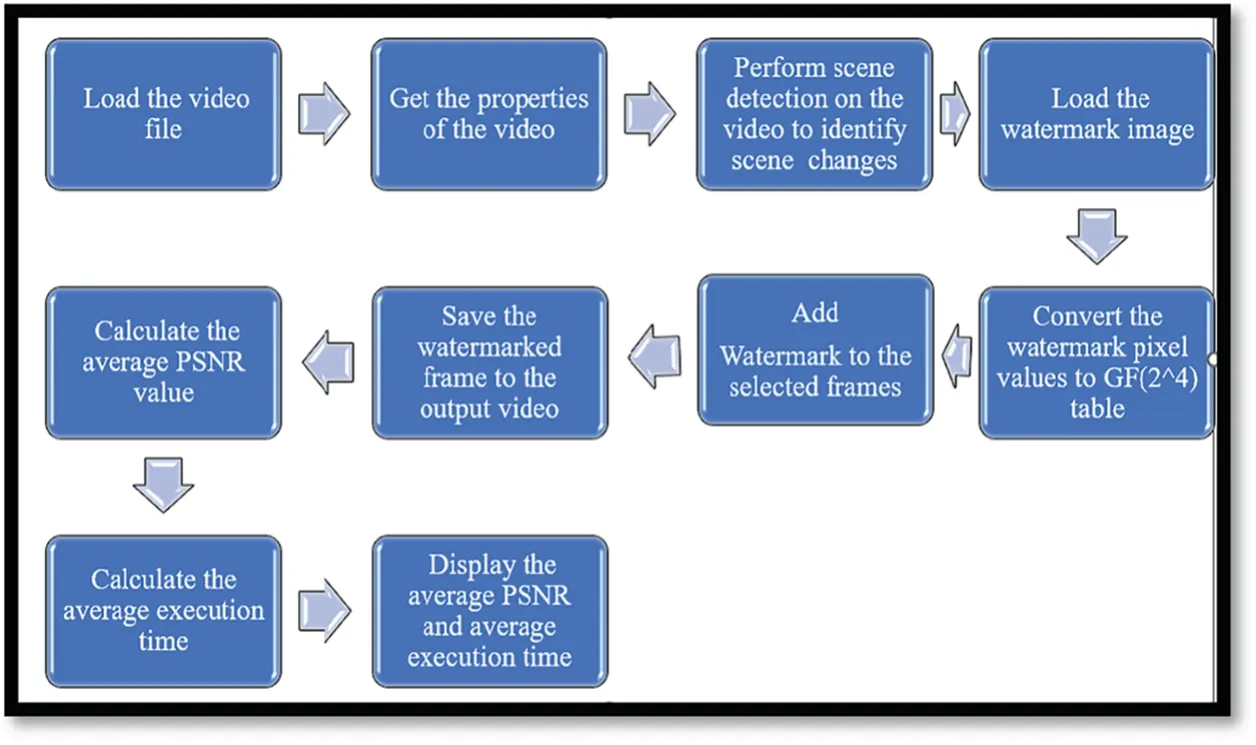
Figure 1:Block diagram of the proposed system
2.4 Image Watermarking Using GF(24)Multiplication Table
In contrast,image watermarking primarily deals with individual frames,requiring unique strategies.While image watermarking may lack the complexities tied to scene changes,it places greater emphasis on spatial fidelity and perceptual quality over temporal considerations.
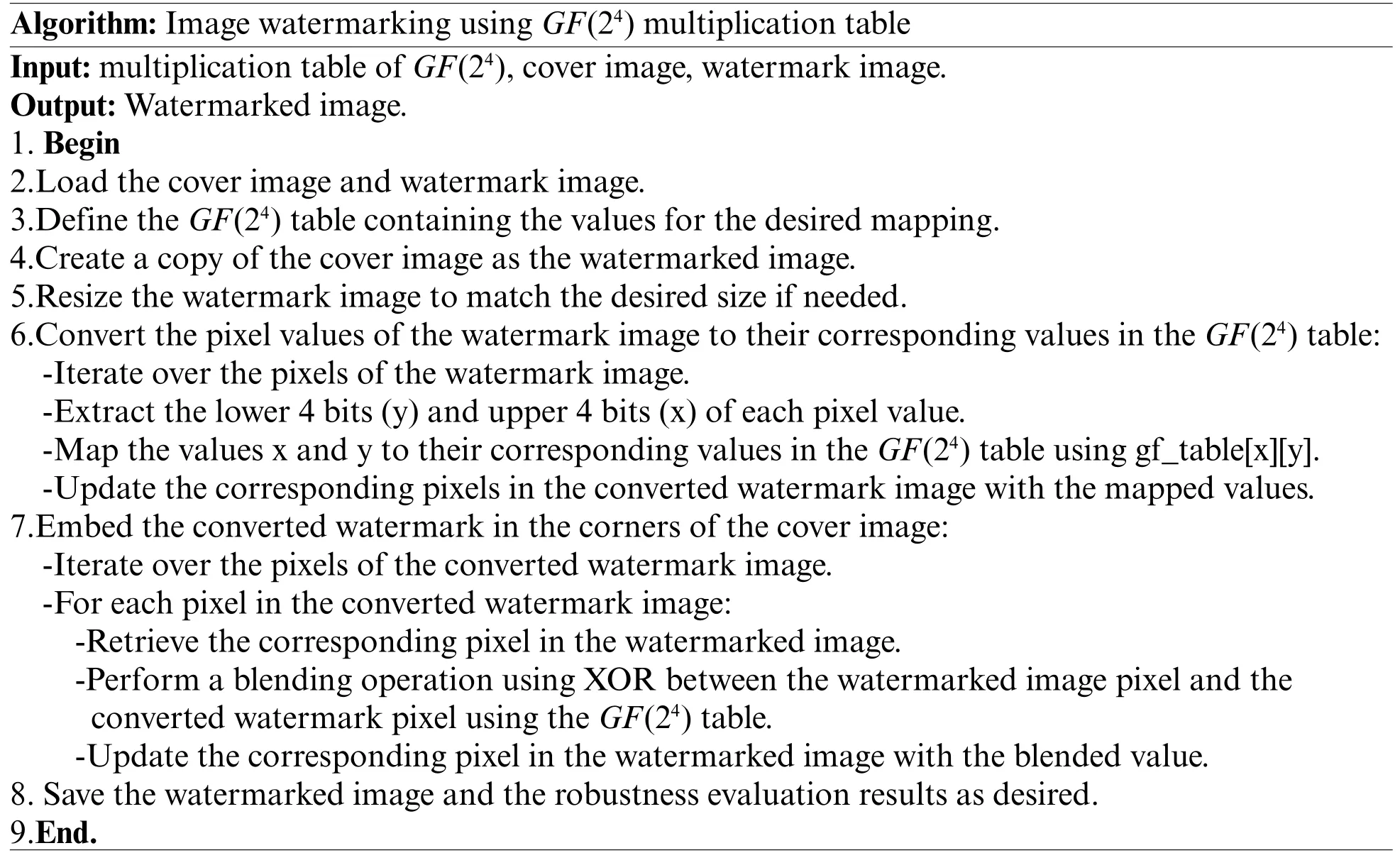
This algorithm ensures that the watermark is embedded in a manner that minimizes its visibility to the human eye while utilizing theGF(24)table for robustness against image processing operations.AGF(24) multiplication table has been employed in this investigation along with the irreducible polynomial(x4+x+1).Image watermarking,unlike video watermarking,does not encompass the intricacies of scene selection,making the process significantly more straightforward.The absence of temporal considerations in image watermarking allows for a more direct focus on the spatial attributes of individual frames,eliminating the need for scene change detection and adaptive thresholding.Instead,image watermarking emphasizes spatial fidelity,ensuring that the watermark is subtly embedded within the image to maintain its quality and visibility,all within the confines of a single,static frame.
3 Experimental Results and Discussions
The experimental results obtained from the conducted study shed light on the effectiveness and potential of utilizing Galois Field (GF) multiplication tables for video watermarking.Through the utilization of various irreducible polynomials in the construction of these tables,the intricate interplay between mathematical foundations and practical applications was sought to be uncovered.Through rigorous experimentation and analysis,our study delved into the robustness,imperceptibility,and computational complexity aspects of the video watermarking process.The obtained results offer valuable insights into the influence of different irreducible polynomials on watermarking performance,contributing to a deeper understanding of how algebraic structures can be harnessed to enhance multimedia security solutions.In this study,a range of video files were employed,(v1,v2,and v3)have been obtained from a personal camera to ensure the preservation of others’rights.These videos encompass indoor and outdoor scenes,impacting both the content and specific details within the videos.Furthermore,the comparison entails the utilization of three conventional video files(Foreman,Akiyo,and Coastguard),which are commonly employed in academic literature.The videos utilized were in the (.mp4) format,while the watermark image was in (.png) format,using two resolutions for the same image as the watermark named watermark1 and watermark 2,featuring a resolution of(225 × 225) and (100 × 100).The experimentation was conducted on the Python platform version 3.8,running on a Windows 10 system with a Core i7 CPU and 16 GB of RAM.Table 1 illustrates the cover video data and watermark images used in this study.

Table 1: The cover videos and the watermark image utilized in this study

Table 2: Multiplication table of GF(24)with irreducible polynomial x4+x+1

Table 3: Multiplication table of GF(24)with irreducible polynomial x4+x3+1
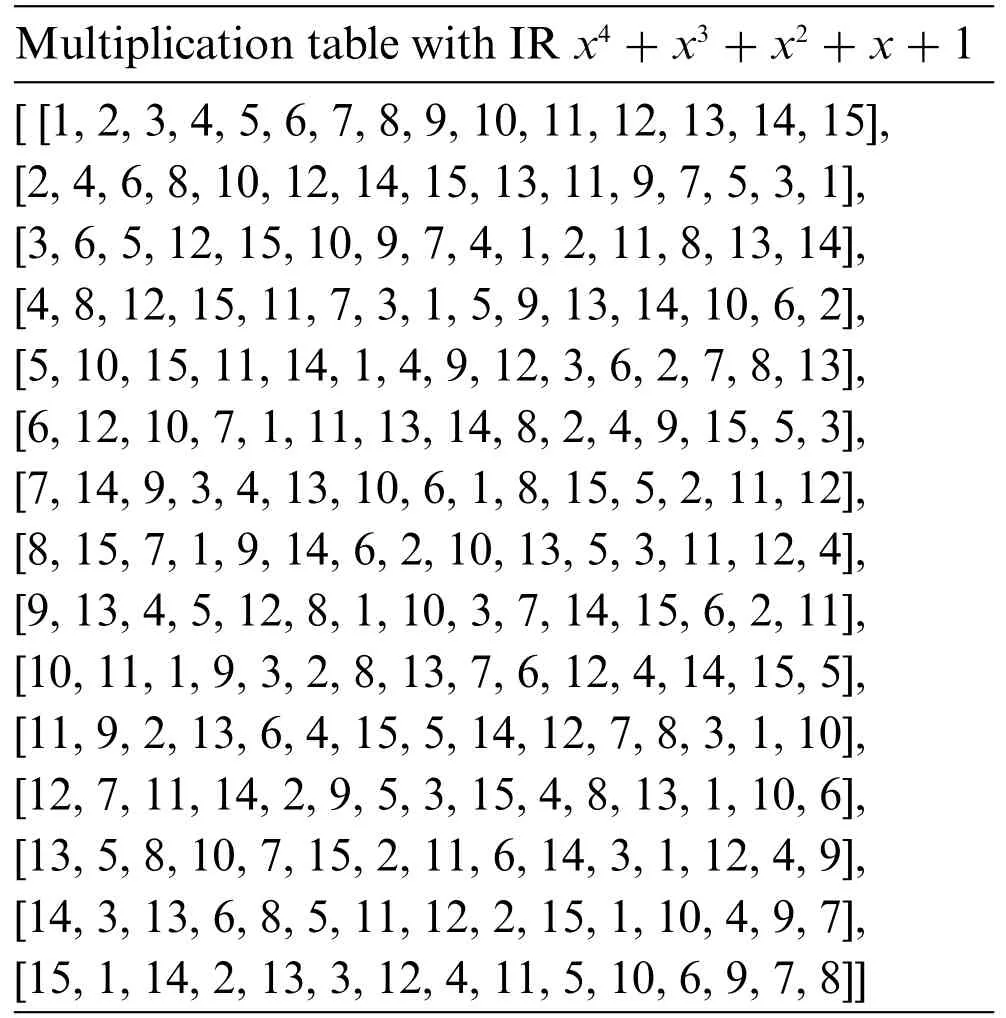
Table 4: Multiplication table of GF(24)with irreducible polynomial x4+x3+x2+x+1
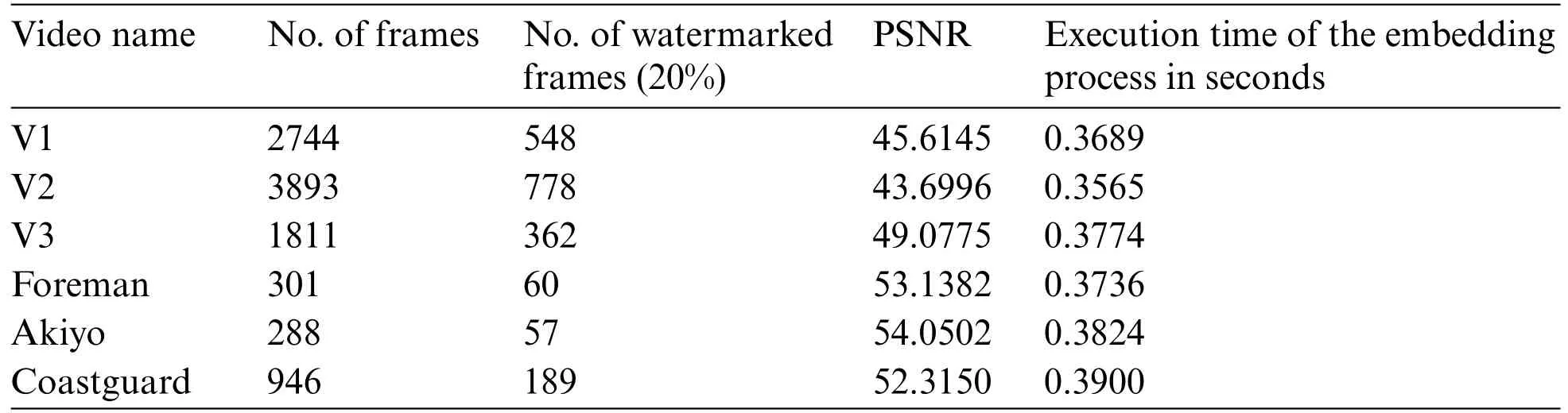
Table 5: Results of the proposed scheme using GF(24) with irreducible polynomial x4 + x+1 and watermark1

Table 6: Results of the proposed scheme using GF(24) with irreducible polynomial x4 + x3+1 and watermark1

Table 7:Results of the proposed scheme using GF(24)with irreducible polynomial x4+x3+x2+x+1 and watermark1
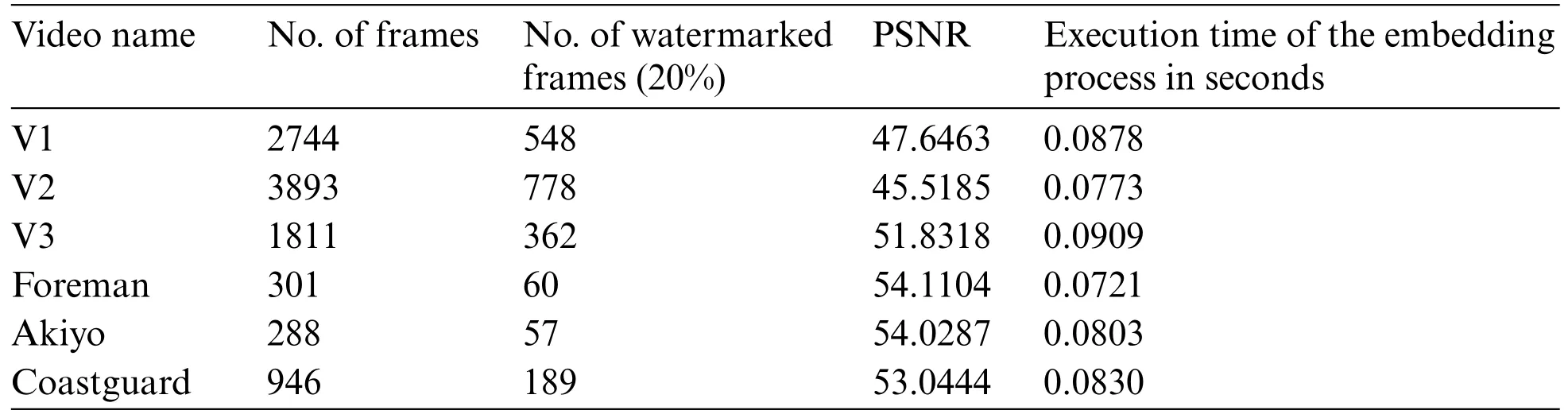
Table 8: Results of the proposed scheme using GF(24) with irreducible polynomial x4 + x+1 and watermark2
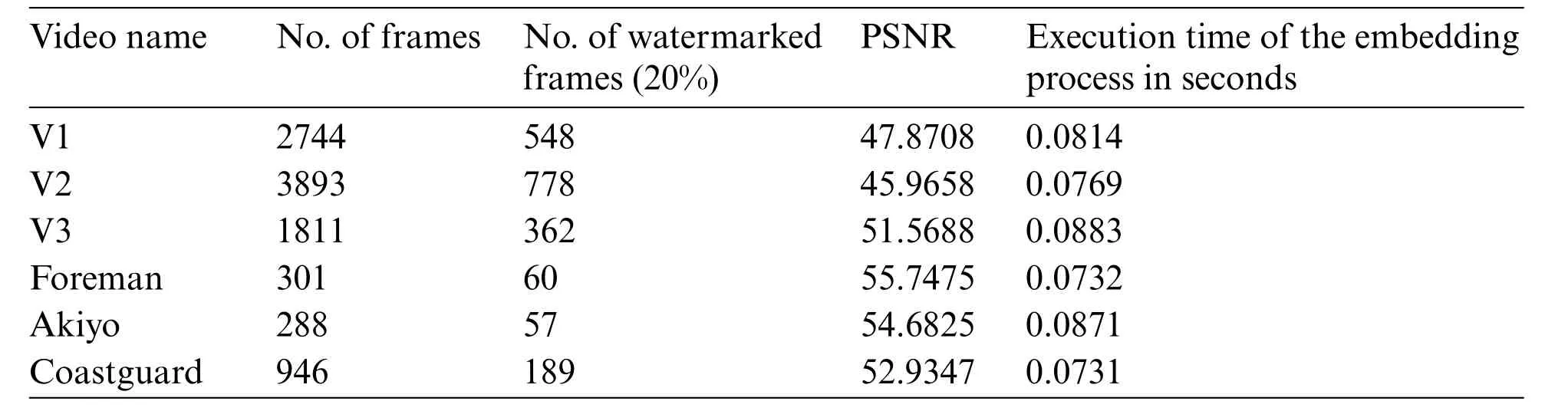
Table 9: Results of the proposed scheme using GF(24) with irreducible polynomial x4 + x3+1 and watermark2

Table 10:Results of the proposed scheme using GF(24)with irreducible polynomial x4 +x3 +x2 +x+1 and watermark2
Tables 2–4 illustrate the constructedGF(24) multiplication tables based on the three irreducible polynomials.
3.1 Evaluation Metrics
Peak Signal-to-Noise Ratio (PSNR) is a metric widely employed to assess the imperceptibility and quality of images or videos after applying various transformations or watermarking techniques.It quantifies the difference between the original and the modified image,giving insight into the level of distortion introduced by the process.
Mathematically,PSNR is calculated using the Mean Squared Error(MSE)between the original and the modified images,which measures the average squared difference between corresponding pixel values:
•I(i,j)represents the pixel value of the original image at location(i,j),
•K(i,j)represents the pixel value of the modified image(e.g.,watermarked image)at the same location,
•MandNare the dimensions of the image.
The PSNR is then calculated using the MSE as follows:
where:MAX is the maximum possible pixel value(e.g.,255 for 8-bit images).
In the context of watermarking,comparing the PSNR values of watermarked images with their corresponding original images helps to quantify the perceptual quality of the watermarking process,providing insight into how well the watermark is embedded while maintaining the visual integrity of the content.
Normalized Correlation (NC) is another essential metric for evaluating the quality of watermarked images.It quantifies the degree of similarity or correlation between the original and watermarked images.NC ranges from-1(perfect negative correlation)to 1(perfect positive correlation),with 0 indicating no correlation.The Normalized ross-Correlation(NC)between two signals or images can be computed using the following equation:
where:
•I1andI2are the two signals or images being compared.
•andare the means(averages)ofI1andI2,respectively.
• The numerator represents the cross-covariance betweenI1andI2.
• The denominator is the product of the square roots of the variances ofI1andI2.
3.2 Results of Video Watermarking Using GF(24)Multiplication Tables
In Fig.2,a series of frames is provided as an illustrative example of a watermarked video.These frames demonstrate the process of watermark embedding at all four corners of the video frames.While the watermark in the algorithm is imperceptible,it has been deliberately made visible in this example solely for illustrative purposes.The first row of frames depicts the original cover video frames before the watermark is embedded.In the second row,you can see the watermark applied to all frames without considering scene selection.However,it is important to note that this approach can be time-consuming and may consume significant storage space.

Figure 2:An example of video frames before and after watermarking
On the other hand,when employing a scene selection process,the watermarking scheme becomes more efficient.This streamlined approach not only accelerates the watermarking process but also enhances its practicality for real-world applications.The proposed approach’s application usingGF(24)multiplication tables,established through three distinct irreducible polynomials,is demonstrated in Tables 5–10.Tables 5–7 use watermark 1 with resolution 225 × 225 and Tables 8–10 use watermark 2 with resolution 100 × 100.These tables showcase the utilization of the scheme across varying video lengths.Notably,the No.of watermarked frames pertains to a selection of 20%of the entire video frames.This selection is accomplished using a frame selection technique that focuses exclusively on significant scenes.The integration of an adaptive threshold within this process expedites watermark embedding.
3.3 Results of Image Watermarking Using GF(24)Multiplication Table
In Table 11,the results of embedding an invisible mark or signal into digital images using the image watermarking process to protect intellectual property,authenticate users,and identify the content of the image.UtilizingGF(24),one of the mathematical characteristics ofGFs,as a transformation mechanism is one way to accomplish this.
3.4 Robustness Measurements
In Table 12,the result of robustness experiments that have been presented and conducted to evaluate the performance of the watermarking algorithm under a variety of real-world attacks.It presents the results of various attacks on three video sequences (Akiyo,Foremen,Coastguard),focusing on the measurements of PSNR(Peak Signal-to-Noise Ratio)and NC(Normalized Correlation)for each attack.These metrics are commonly used in video watermarking to assess the quality and robustness of watermarked videos under different attacks.The results show the trade-off between video quality(PSNR)and the robustness of the watermark to various attacks.While some attacks result in reduced PSNR values,indicating a quality loss,the watermark remains relatively robust,as suggested by the high NC values.This implies that even under these attacks,the watermark can still be reliably detected.The choice of attack should align with the desired balance between video quality and watermark robustness in a specific application.

Table 12: PSNR and NC of applying geometric attacks on watermarked video
In Table 13,a comparison of average PSNR values between the proposed method and other approaches using the standard videos (foreman,Akiyo,coastguard).The average PSNR of the proposed method was computed using the three irreducible polynomials with two watermarks.By analyzing the Peak Signal-to-Noise Ratio values,the performance and efficacy of our approach in video watermarking are assessed in comparison to alternative methods.This evaluation allows for insights into the robustness and quality of the proposed technique,highlighting its potential superiority in upholding watermark imperceptibility while contending with various challenges posed by different scenarios.

Table 13: Comparison of the average PSNR values of the proposed method with other approaches
Upon careful examination of the data presented in Tables 4–6,a clear trend emerges:the utilization of the second irreducible polynomial (x4+x3+1) consistently leads to the most favorable and promising outcomes.This polynomial exhibits a remarkable ability to effectively integrate with theGFmultiplication tables and significantly enhance the watermarking process.The watermark embedding results achieved through the application of this polynomial showcase higher levels of imperceptibility and robustness when compared to the other irreducible polynomials.This superiority can be attributed to the specific mathematical characteristics inherent in thex4+x3+1 polynomial,which enables it to facilitate a more seamless and efficient transformation mechanism for watermark embedding.
The algorithm exhibits linear time complexity concerning the number of frames the complexity of scene change detection,and the dimensions of video frames,and it requires additional space for scene change frames and watermark storage.The exact computational complexity may vary depending on the specific implementation and optimizations.The overall computational complexity is approximately O(NM+WH+K),where the specific values of N(number of frames),M(number of scenes detected),W(width),H(height),and K(denotes the space required for watermark storage)depend on the video and watermark characteristics.As these values increase,the algorithm’s computational demands will also increase accordingly.
As the number of frames chosen for watermarking increases,the likelihood of a decrease in PSNR due to heightened alterations in video content becomes evident.On the contrary,opting for a minimal number of frames may lead to insufficient watermark robustness.This value can be adapted by the requisites and the intended balance between watermark imperceptibility and resilience(1).
4 Conclusion
Video watermarking usingGF(24)is a powerful technique for embedding hidden information in video streams.By leveraging the mathematical properties of Galois fields,this approach provides an effective means of protecting intellectual property rights,ensuring content integrity,and enabling the traceability of videos in various applications.
The frame selection and adaptive thresholding withGF(24) tables using different irreducible polynomials to blend the watermark with the most important frames,ensuring that the watermark is imperceptible while minimizing execution time.The outcomes of this investigation demonstrate favorable PSNR values,particularly notable when employing the second irreducible polynomial (x4+x3+1).
Overall,this algorithm performs video watermarking by selecting frames based on scene changes and then blending the watermark in selected frames using aGF(24)table.The more frames have been selected for watermarking,the lower the PSNR is likely to be due to the increased modifications to the video content.Conversely,if the selected frames were too few,the watermark might not be robust enough.Therefore,it is important to adjust this value based on the requirements and the desired trade-off between watermark imperceptibility and robustness.The limitation arises when working with very short videos,as the outcomes tend to be ambiguous and unclear due to the inadequate presence of sufficient scenes for robust watermarking evaluation.The proposed method shows good results that are superior to the others in this field.In a world where multimedia content is ceaselessly evolving,and where security concerns parallel the pace of innovation,this study holds the potential to redefine watermarking strategies.By unraveling the symphony ofGFmultiplication tables,irreducible polynomials,scene selection,adaptive thresholding,imperceptibility,execution time,and PSNR,this exploration advances our understanding and fortifies the foundation for future multimedia security endeavors.Regarding future work,efforts will be made to investigate techniques aimed at further optimizing watermarking systems,with a particular emphasis on real-time applications such as live streaming and video conferencing.
Acknowledgement:None.
Funding Statement:The authors received no specific funding for this study.
Author Contributions:The authors confirm contribution to the paper as follows:study conception and design:Yasmin Alaa Hassan and Abdul Monem S.Rahma;data collection,analysis and interpretation of results,draft manuscript preparation:Yasmin Alaa Hassan.Both authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials:Using two different sources of video data in this study:1.Private Camera Data:This refers to video data that is obtained from private sources,such as personal cameras or non-publicly accessible sources.This data may not be readily available to the general public and might require specific permissions or access.2.Publicly Available Web Data: This indicates that another portion of video data comes from publicly available sources on the internet,such as websites or platforms where videos are shared openly and can be accessed by anyone without restrictions.
Conflicts of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.
杂志排行
Computers Materials&Continua的其它文章
- Structured Multi-Head Attention Stock Index Prediction Method Based Adaptive Public Opinion Sentiment Vector
- Intelligent Solution System for Cloud Security Based on Equity Distribution:Model and Algorithms
- A Hybrid Model for Improving Software Cost Estimation in Global Software Development
- Real-Time Detection and Instance Segmentation of Strawberry in Unstructured Environment
- Leveraging Augmented Reality,Semantic-Segmentation,and VANETs for Enhanced Driver’s Safety Assistance
- Efficient Object Segmentation and Recognition Using Multi-Layer Perceptron Networks
