A Fine-Grained Data Encryption and Sharing Scheme in Fog and Cloud Computing Environments
2024-01-11ZHOUXianBinJIANGRui
ZHOU Xian-Bin, JIANG Rui
School of Cyber Science and Engineering, Southeast University, Nanjing 210096, China
Abstract: With the fast development of Internet of Things(IoT),5G(the fifth generation communication system)and 6G networks,the corresponding encryption algorithms need to be adapted for both fog and cloud computing environments, with fine-grained data encryption function including attribute revocation mechanism and resistance against collusion attacks.Current research on these theoretical and technical issues needs to be further developed and improved.Based on ciphertext-policy attributebased encryption (CP-ABE) structure, this paper proposes a new data sharing scheme (NDSS-FC),which can fit for both the fog and the cloud computing environment, and can realize fine-grained data access control in fog and cloud computing architecture, such as secure attribute revocation, secure dynamic user management, with collusion attack resistance and outsourced decryption.Firstly, the proposed NDSS-FC scheme can achieve secure data sharing in fog and cloud computing environments with outsourced decryption.In the proposed NDSS-FC scheme, fog nodes are employed to construct new analogous CP-ABE structure, in which there are two kinds of data owners and data users.The fog nodes can deal with the outsourced decryption for those users who have limited computation resources.Secondly, the proposed NDSS-FC scheme can realize secure attribute revocation.In the proposed NDSS-FC scheme, the new analogous CP-ABE structure is combined with one-way function tree (OFT) technique to share attribute group keys for revoking users’ attributes.Thirdly, the proposed NDSS-FC scheme can securely and dynamically manage users.In the proposed NDSS-FC scheme, there is a version key that is distributed via a polynomial and is embedded in the ciphertext.When a user is removed from or added into the system, the version key will be updated.Moreover,the proposed NDSS-FC scheme can withstand the collusion attacks.Both performance and formal security analysis show that the proposed NDSS-FC scheme is efficient and secure.
Key words: fog and cloud computing environments; fine-grained data encryption; attribute revocation; dynamic user management; outsourced decryption; collusion attack resistance
1 Introduction
With the fast development of computer science and network technology, cloud computing is regarded as a promising and mature paradigm to provide rich and diverse applications, such as resourcesharing services, unconditional access, flexible resource rentals, and so on.People with resourceconstrained devices tend to outsource their data to the cloud for storage and computation.However,two major concerns must be focused especially and necessarily, that is, security and centralization in cloud computing[1].
As the data is outsourced to the cloud for further services, the security and privacy of the data for their owners cannot be guaranteed.Access control, a crucial defense to maintain users’ privacy and data security, has been extensively studied[2].As a result, Attribute-Based Access Control (ABAC) is the state of the art for access control which has attracted a large number of researchers.Ciphertext-Policy Attribute-Based Encryption (CP-ABE), a promising cryptographic primitive, can provide finegrained access control to meet the secure and flexible data sharing requirement in cloud environment.More specific research based on CP-ABE in the cloud has caught the attention of scholars, such as attribute revocation[3–11], collusion attack resistance[12–14], key escrow problem[7,15], outsourced computation[12,16–20], hidden policy[21,22], and multi-attribute authority[8,23].
Fog computing[24]is a promising architecture which extends the cloud computing to the edge of the network so as to address the shortcomings and deficiencies for cloud computing.When a huge amount of data is aggregated to the cloud, network bandwidth is under tremendous pressure, which may make the result for network congestion and slow response.Moreover,the remote distance between terminals and the cloud may cause high latency which cannot meet the users’needs,especially for some time-sensitive applications.Hence, in fog computing environment, the system may deploy very large number of fog nodes with wild-spread geographical distribution and location awareness to provide near services for those who are close to them by wireless access[25].There are varieties of applications based on fog architecture, such as Internet of Things (IoT)[13,26], smart grid[14,27], healthcare[28,29], and other practical scenarios.
However, with the rapid development of heterogeneous networks such as the 5G (the fifth generation communication system) network, the 6G network, and the Internet of Things (IoT) network,the fine-grained access control algorithms should be designed to fit for both the fog and the cloud computing environment.Unfortunately, the existing ABE schemes just focus on either the cloud computing environment or the fog computing environment.To the best of our knowledge, there is no any research on data sharing algorithm, which can be both fit for fog and cloud computing environments.In order to build a secure and efficient data sharing scheme in fog and cloud computing environments,there are several necessary issues should be addressed.Firstly, attribute revocation should be dealt with since the attribute sets of those smart objects change frequently.The revoked users should stop accessing the subsequent encrypted data, while other valid users with sufficient attributes should not be affected.In addition, smart objects may be removed from or added into the system dynamically because of their lifecycle or for any other reasons.Hence, dynamic user management should be ensured.Moreover, collusion attack resistance is an unavoidable topic, since malicious users may try to decrypt the ciphertext illegally by colluding with other users.Finally, due to the resource-constrained property of smart objects, outsourcing decryption operations to the third party is a good choice for them to reduce complex computation overhead on their own side.
1.1 Related Works
Attribute-Based Encryption(ABE)is a promising cryptographic approach which can achieve finegrained access control.Sahai and Waters first introduced this primitive as an extension of Identity-Based Encryption (IBE)[30].The main idea of ABE is that a predefined access policy is related to either the ciphertext or users’secret keys,which classifies two categories of ABE algorithms.The one is Ciphertext-Policy Attribute-Based Encryption (CP-ABE)[31], and the other is Key-Policy Attribute-Based Encryption (KP-ABE)[32].CP-ABE is more suitable for outsourcing data to the cloud or the fog since data owners totally define a group of people who can decrypt the data on their own.
In CP-ABE algorithm, with cloud computing environment, the attribute revocation is a necessary requirement for the sake of dynamic changes on users’ attribute sets.Pirretti et al.[3]came up with a technique to solve attribute revocation problem in CP-ABE by assigning an expiration time to every attribute.So attributes were revoked in a periodical manner by adopting this mechanism.However,a new user may access to the previous data and a revoked user may access to the subsequent data because of the indirect property, which may cause some secure issues.Yu et al.[4]proposed a revocable CP-ABE scheme.However, their scheme required heavy communication and computation cost.Subsequently, some schemes[5–9]achieved attribute revocation by re-encrypting relevant components on both ciphertext and user’s secret key for the advantage of high efficiency, low computation and storage cost.Tysowski and Hasan[5]applied the re-encryption technique to execute attribute revocation due to the fact that users hold the same group secret key generated by the group.Hur and Noh[6]introduced the concept of attribute group and separated each user into different groups based on their attributes, then the attribute manager (AM) distributed updated secret keys by key encrypting key(KEK) trees.Hur[7]enhanced the security and efficiency of attribute groups by applying polynomials to distribute and update attribute encrypting keys so as to realize attribute revocation.However, in these schemes, when the number of users in an attribute group was increasing, the data users’ storage overhead would be linearly growing.Based on Scheme [6], Li et al.[9]proposed an improved scheme which bound each user’s decryption secret key (DSK) and key encrypting key (KEK) together by a random number to prevent the revoked users from colluding with the existing users.Yang et al.[8]proposed a scheme which assigned a version number for each attribute.Hence, the components associated with the revoked attribute in secret keys and ciphertexts needed to be updated when performing attribute revocation.However, Wu et al.[33]pointed out, in Scheme [8], the revocation security could not be guaranteed.
In CP-ABE algorithm, another necessary requirement is dynamic user management in fog and cloud computing environments, where the smart objects are added into or removed from the system dynamically and frequently.Schemes [3–9] cannot achieve efficient and dynamic user management.When a user is added into or removed from the system, other users’ attribute keys will be affected accordingly, which may cause high computation and communication overhead for the system.Fan et al.[34]proposed an efficient, secure and revocable data sharing scheme for vehicular fogs.However, in their scheme,the transformation key generated by each AA was stored in the cloud server.When a user was restricted from accessing the outsourced data,the transformation key would be deleted so that the cloud server could no longer conduct transformation algorithm for the user.Wen et al.[14]proposed a scheme which provided secure and efficient access control in fog-based smart grid.However, the secure and dynamic user management in the scheme could not be guaranteed.Generally,a data user removed from the system should be prevented from decrypting any subsequent ciphertext.Unfortunately,in the scheme, the removed user could still have the valid secret key as long as his attribute set satisfied the access policy embedded in the ciphertext.Hence, the removed user could still decrypt the subsequent ciphertext.
Outsourcing decryption operations to the third party is another significant and unavoidable requirement in fog and cloud computing environments.Smart terminals often take the form of resourceconstrained devices such as wearable devices, wireless sensors, smart healthcare devices, and so on.Since the original work of Scheme [16], recently, some outsourced ABE schemes[12,17–20]were proposed.Scheme [12] could support both secure outsourced key-issuing and decryption, and could check the correctness of the outsourced computation results in an efficient way.In Scheme [17], the authors proposed an ABE scheme with verifiable outsourced decryption to simultaneously check the correctness of ciphertext for the authorized users and unauthorized users.In Scheme[18],the authors proposed an efficient and generic construction of ABE with verifiable outsourced decryption based on an attributebased key encapsulation mechanism, a symmetric-key encryption scheme and a commitment scheme.In Scheme [19], the authors came up with a new notion called auditableσ-time outsourced CP-ABE,which offloaded expensive pairing decryption operation to the cloud and audited the correctness of the operation efficiently.In Scheme [20], the authors built a fast CP-ABE scheme, which was fit for the mobile terminal devices with low computational and storage power, and could verify the correctness of decryption by applying a Boneh-Lynn-Shacham short signature scheme.Unfortunately, all the schemes mentioned above could not be directly applied to the fog and cloud computing environments.The reason is that all these schemes just dealt with the aspect of outsourced decryption, regardless of other unavoidable requirements, such as attribute revocation and dynamic user management.
Recently, Zhang et al.[35]focused on the key escrow and user revocation issues to provide a key escrow-free CP-ABE scheme with the user revocation, which could withstand collusion attack between malicious users and revoked users.Moreover, most of decryption operations were outsourced to the decryption cloud server provider(D-CSP)to decrease computation costs.In order to solve the problem that the authorized decryption user may be unable to recover the message online in time,Chen et al.[36]provided a CP-ABE scheme with shared decryption.In the scheme, multiple delegated users could collaborate to recover the message, and the correctness of the decrypted results could be verified.Moreover, the author used the access tree technique to reduce the computation cost for encryption and decryption.Li et al.[37]proposed a CP-ABE scheme to enable fine-grained access control of encrypted IoT data on cloud.In the scheme, the author first provided an access control system model for CloudIoT platform based on ABE.And then they provided a detailed CP-ABE scheme with hidden access structure as well as ensuring accountability for key abuse.Unfortunately, the Schemes [35–37]are only dealing with the cloud computing environment, not fitting for the promising fog computing environment.
1.2 Our Contributions
In order to fit for both the fog and the cloud computing environment, to realize fine-grained data access control with outsourced decryption, to achieve secure and efficient attribute revocation, to realize flexible and dynamic user management, and to withstand collusion attacks, we propose a novel data sharing scheme in fog and cloud computing environments (NDSS-FC).The main contributions of this paper are summarized as follows.
(1) Our NDSS-FC scheme can guarantee secure data sharing and fine-grained access control in fog and cloud computing environments with outsourced decryption.In our NDSS-FC scheme, we design fog nodes to construct new analogous CP-ABE structure, in which there are two kinds of data owners and data users.The fog nodes can deal with the outsourced decryption for those users who have limited computation resources.A data user can access to the encrypted data if and only if his attribute set satisfies the access policy specified by the data owner.
(2) Our NDSS-FC scheme can achieve secure and efficient attribute revocation.In the proposed scheme,we separate data users into different attribute groups according to their attributes.To securely share the attribute group key, we design the one-way function tree (OFT) technique,and seamlessly merge the OFT technique with the new analogous CP-ABE structure.Hence,the revoked users can no longer decrypts the latest ciphertext so as to ensure the secure and efficient attribute revocation.
(3) Our NDSS-FC scheme can realize flexible and dynamic user management.In our NDSS-FC scheme,we construct a polynomial to distribute the version key,which is a component embedded in the ciphertext and independent of those attributes in the access policy.When a user is removed from or added into the system, which means all attributes of the user are revoked simultaneously or the user is simultaneously granted a number of attributes corresponding to his identity,the version key will be updated to the latest version and the ciphertext is updated accordingly.Only those users who are authorized by the system can update their secret keys correctly.Hence, our NDSS-FC scheme can dynamically and flexibly manage the data users.
(4) Our NDSS-FC scheme can withstand collusion attacks.In this paper,collusion attacks include the attacks launched by the legitimate user and the revoked user, or by the revoked user and the external attacker, or by the revoked users.In our NDSS-FC scheme, we uniquely assign a random number to each user, and embed this unique random number into user’s secret key.In this way, only the user who has the enough key components can decrypt the ciphertext.Therefore, our NDSS-FC scheme can realize collusion resistance for the data sharing in fog and cloud computing environments.
1.3 Organization
The rest of this paper is organized as follows.Preliminaries are introduced in Section 2.We describe system model and threat model in Section 3.The concrete construction of our NDSS-FC algorithms is presented in Section 4.The formal security analysis is proved in Section 5.Performance analysis is done in Section 6.We conclude the whole paper in Section 7.
2 Preliminaries
In this section, we introduce the basic mathematic algorithms and methods applied in the paper.
2.1 Bilinear Parings
Definition 1 Let G0and G1be two multiplicative groups with prime orderp.A mape:G0×G0→G1is a bilinear map if the following properties are satisfied:
• Bilinearity:∀g,h ∈G0,∀a,b ∈Zp,e(ga,hb)=e(g,h)ab.
• Computability: There exists an efficient algorithm to computee(g,h)∈G1,∀g,h ∈G0.
• Non-degeneracy:e(g,h)̸=1.
2.2 Access Structure [38]
Definition 2 Let{P0,P1,···,Pn}be a set of parties.A collection A∈2{P1,P2,···,Pn}is monotone ifB,C: ifB ∈A andB ⊆CthenC ∈A.An access structure (respectively, monotone access structure) is a collection (respectively, monotone collection) A of non-empty subsets of 2{P1,P2,···,Pn},i.e., A∈2{P1,P2,···,Pn}{∅}.The sets in A are called authorized sets.And the sets not in A are called unauthorized sets.
2.3 Access Tree [32]
Definition 3 LetTdenote an access tree with an access policy.Each non-leaf node of the access tree has a threshold gate described by its children and a threshold value.We mark numxas the number of children for a nodex, andkxas its threshold gate value, thus 0<kx≤numx.The threshold gate is an AND gate whenkx=numx, and an OR gate whenkx=1.Each leaf nodeyassociates an attribute and its threshold valueky=1.Letλydenote the attribute associated with the leaf nodeyin the tree,andp(z) represent the parent node of a nodezin the tree.The children of every node are labeled from 1 to numx, and the function index(z) denotes the index value for the nodez.The index values are uniquely assigned to the nodes in the access structure with a given key in an arbitrary manner.
2.4 One-way Function Tree (OFT) [39]
Definition 4 LetTbe a one-way function tree which is a binary tree used for sharing a group key.Each nodevinThas two cryptographic values which are the node secret nxvand the node key nkv.Each leaf node is associated with a group member.If nodevis a leaf node, the node secret nxvis received from the group manager.If nodevis an interior node, the node secret nxvis defined as nxv=f1(nxvL)⊕f1(nxvR), wherevLandvRdenote the left and right children ofvrespectively,⊕is bitwise exclusive-or, andf1(·) is a special one-way function.For each nodev, the node key nkvis defined as nkv=g1(nxv), whereg1(·) is another special one-way function.
The node secret of the rootvRdenotes the group key.A group member associated with a leaf nodevmaintains the node secret nxv, and{∀i ∈paths(v) :Enki[f1(nxsibling(i))]}, where paths(v) is denoted as the set which includes the node and all ancestor nodes of the nodevexcept for the root nodevR, sibling(v) is denoted as the sibling node ofv, andEis a symmetric encryption function.Figure 1 is an example for one-way function tree (OFT) to compute the group key.

Figure 1 Example for one-way function tree (OFT)
In Figure 1, the leaf node set is{v5,v6,v7,v8,v9}, the interior node set is{v1,v2,v3,v4}, and the root node isv1.Each nodev ∈{vi|i ∈[1,9]}has a node secret nxvand a node key nkv.The node secrets of interior nodes are computed as nxv=f1(nxvL)⊕f1(nxvR), wherevLandvRare the left and right children ofv.The node secrets of leaf nodes are assigned by the group manager.The node keys of all nodes are computed as nkv=g1(nxv).For the nodev9with paths(v9) ={v9,v4,v2}, the group member placed in the nodev9can calculate nk9=g1(nx9),f1(nx8) =Dnk9[Enk9[f1(nx8)]],nx4=f1(nx8)⊕f1(nx9), nk4=g1(nx4),f1(nx5) =Dnk4[Enk4[f1(nx5)]], nx2=f1(nx4)⊕f1(nx5),nk2=g1(nx2),f1(nx3) =Dnk2[Enk2[f1(nx3)]], and finally get nx1=f1(nx2)⊕f1(nx3), which is the group key.
2.5 DBDH Assumption [32]
Definition 5Suppose thate: G0×G0→G1is a bilinear map, andgis a generator of G0.Leta,b,c ∈ZpandX ∈G1be chosen at random.The DBDH assumption states that no polynomial time adversary is able to distinguish the tuple (A=ga,B=gb,C=gc,Z=e(g,g)abc) from (A=ga,B=gb,C=gc,Z=X) with more than a negligible advantage.
2.6 Security Model
In this paper, the security model is presented by defining a game between a challengerBand an adversaryAas following steps.
Init.Achooses a challenge access structureT ∗that he wishes to be challenged upon.
Setup.Bruns the setup algorithm and gives the public parameters toA.
Phase 1.Ais allowed to issue queries for private keys for many attribute setsS1,···,Sd1,but the restriction is that allSjcannot satisfyT ∗.Aalso makes update key queries.Bgives the corresponding update attribute group information to the adversaryA.
Challenge.Apicks two symmetric keysK0,K1with equal length before sending them toB,thenBflips a random coinb ∈{0,1}, and encryptsKbwithT ∗, the dataMis encrypted asEKb[M].The ciphertext is passed toA.
Phase 2.Amay query more secret keys and updated keys, as long as they do not violate the following constraints: (1) The queried secret keys do not satisfyT ∗.(2)Ais not able to query the correct group information that can update the queried secret keys to decrypt the challenge ciphertext.
Guess.Aoutputs a guessb′ofb.
The advantage of an adversaryAin this game is defined as Pr[b′=b]−1/2.
2.7 Indistinguishability Under Chosen Plaintext Attack (IND-CPA)
Given a public key encryption scheme Π = (KGen,Enc,Dec) and an adversaryA, the IND-CPA security is related to the indistinguishability game PubKCPAΠ,A(K) below.
(1) The challengerBruns the KGen algorithm to generate (pk,sk) and sends pk toA.
(2)Apicks two messagesm0,m1with equal length and sends them toB.
(3)Bchooses a random bitb ∈{0,1}and encrypts asc=Enc(mb,pk).ThenBsendsctoA.
(4)Aoutputs a guessb′ofb.

3 System Model and Threat Model
3.1 System Model
There are five entities in our NDSS-FC scheme, which is illuminated in Figure 2.They are data owner (DO), data user (DU), cloud service provider (CSP), fog device (FD), and attribute authority(AA), respectively.

Figure 2 System model
DO is a data provider/owner who wants to store data in the cloud and share the data with the desired target group.According to the computation and storage capacity of the DO, it is classified into two specific types which are DOfand DOc.A DOfcan be a smart sensor, a wearable device, and other smart object with limited computation and storage resources.The DOflies in the lowest layer in the fog and cloud computing environments.Before storing the data to the CSP, the DOfneeds to access to the target FD for further service.A DOccan be a mobile phone, a desktop, and other smart device with moderate computation and storage resources.The DOclies in the middle layer in the fog and cloud computing environments, that is, the DOcis a traditional data owner in the cloud computing environment.Different from the DOf, the DOccan directly outsource the data to the CSP without the aid of an FD.
DU is a data consumer/user who wants to access to the data stored in the cloud.According to the computation and storage capacity of the DU, it is classified into two specific types which are DUfand DUc.A DUfcan be a smart sensor,a wearable device,and other smart object with limited computation and storage resources.The DUflies in the lowest layer in the fog and cloud computing environments.After obtaining the data from the CSP, the DUfneeds to ask the target FD for outsourced decryption help.A DUccan be a mobile phone, a desktop, and other smart device with moderate computation and storage resources.The DUclies in the middle layer in the fog and cloud computing environments,that is, the DUcis a traditional data user in the cloud computing environment.Different from the DUf, the DUccan directly decrypt the data from the CSP without the aid of an FD.CSP is the cloud server provider to store the encrypted data.It also provides the ciphertext update service for attribute revocation and dynamic user management.
FDs are fog devices which are deployed at the network edge and offer a variety of services.They re-encrypt the ciphertext and upload the whole ciphertext to the CSP.Moreover, they help users DUfto decrypt the ciphertext from the CSP.
AA is an attribute authority that generates and distributes keys for all DUs, and is in charge of updating the components for the relevant ciphertext and users’ secret keys.
3.2 Formal Definition of NDSS-FC
The framework of NDSS-FC consists of the following phases.
Phase 1: System Setup.This phase contains two steps.
Setup(1κ)→(PK,MK): The Setup algorithm takes no input other than the security parameterκ, and outputs the system public parameter PK and master secret key MK.
UserReg→(GU,{∀λy ∈L}): The UserReg algorithm takes as inputs users’ identity information,and outputs the user groupGUand attribute groups{∀λy ∈L}.
Phase 2: Key Generation.
KeyGen(PK,MK,S)→SK1: The KeyGen algorithm takes as inputs the system parameter PK,the master secret key MK and an attribute setSassociated with a user.It outputs the secret key SK1for the user.
Phase 3: Data Encryption.This phase contains two scenarios.
Scenario 1: Data Encryption by a DOf.
DOF.Encrypt(PK,T,M)→CT1: This algorithm takes as inputs the system parameter PK, an access treeTrepresenting an access policy,and the plaintextM.It outputs the intermediate ciphertext CT1.
FD.ReEncrypt(CT1,{Kλy:y ∈Y})→CT: This algorithm takes as inputs the intermediate ciphertext CT1and a set of attribute group keys{Kλy:y ∈Y}.It outputs the ciphertext CT.
Scenario 2: Data Encryption by a DOc.
DOC.Encrypt(PK,T,M,{Kλy:y ∈Y})→CT: This algorithm takes as inputs the system parameter PK, an access treeTrepresenting an access policy, the plaintextMand a set of attribute group keys{Kλy:y ∈Y}.It outputs the ciphertext CT.
Phase 4: Data Decryption.This phase contains two scenarios.
Scenario 1: Data Decryption by a DUf.
DUF.GroupKeyDecrypt(Hdr,S,SK1)→({Kλy:λy ∈S},SK): This algorithm takes as inputs the group information Hdr, an attribute setSand the secret key SK1.It outputs a set of attribute group keys{Kλy:λy ∈S}and the updated secret key SK.
DUF.OutsourceDecrypt(SK,CT)→{z,CT∗}: This algorithm takes as inputs the user’s secret key SK and the ciphertext CT.It outputs the transformation keyzand outsourced decryption parameter CT∗.
DUF.Decrypt(z,CT∗)→M: This algorithm takes as inputs the transformation keyzand outsourced decryption parameter CT∗.It outputs the plaintextM.
Scenario 2: Data Decryption by a DUc.
DUC.GroupKeyDecrypt(Hdr,S,SK1)→({Kλy:λy ∈S},SK): This algorithm takes as inputs the group information Hdr, an attribute setSand the secret key SK1.It outputs a set of attribute group keys{Kλy:λy ∈S}and the updated secret key SK.
DUC.Decrypt(SK,CT)→M: This algorithm takes as inputs the user’s secret key SK and the ciphertext CT.It outputs the plaintextM.
Phase 5: Attribute Revocation.
AttrRev(SK,CT,λi)→(SK′,CT′): The AttrRev algorithm takes inputs the user’s secret key SK, the ciphertext CT and the revoked attributeλi.It outputs the updated ciphertext CT′and the updated user’s secret key SK′.
Phase 6: Dynamic User Management.
UserMag(U′G,Msg,SK,CT)→(SK′,CT′): The UserMag algorithm takes as inputs the current user groupU′G, the version key message Msg, the user’s secret key SK and the ciphertext CT.It outputs the updated ciphertext CT′and the updated user’s secret key SK′.
3.3 Threat Model
In our NDSS-FC scheme, we define the threat model in terms of the CSP, the FD, the AA, the legitimate users, the revoked users, and the external attackers.
The CSP and the FD are honest but curious, which means that they will correctly perform all operations needed in the scheme, but they may be curious about the secrets of the ciphertext.
The AA is honest and trustworthy, which means that the AA will honestly perform all operations needed in the scheme and will not be curious about the secrets of the ciphertext.
The legitimate users have the ability to decrypt the corresponding ciphertext as long as their attribute sets satisfy the access policy.
The revoked users are not allowed to decrypt the corresponding ciphertext because their attributes are revoked so that their attribute sets no longer satisfy the access policy.They may be curious about the secrets of ciphertext and try to decrypt it.
The external attackers are the network attackers who have no secret keys but try to decrypt the ciphertext illegally.
In our NDSS-FC scheme, the legitimate users, the revoked users and the external attackers may collude with each other to launch the collusion attack and decrypt the ciphertext illegally.It is noticed,in this paper, as an exception, the legitimate user will not leak the current version key VK to collude with others.
3.4 Notation
The explanation of the symbols in our NDSS-FC is shown in Table 1.

Table 1 Symbol explanations
4 Construction of Our NDSS-FC Scheme
In this section, we describe a detailed construction of our NDSS-FC scheme in fog and cloud computing architecture.Our NDSS-FC scheme has six phases which are System Setup, Key Generation,Data Encryption, Data Decryption, Attribute Revocation, and Dynamic User Management.
4.1 System Setup
In this phase, there are two steps which are Setup and UserReg, respectively.
Setup.The AA chooses a bilinear mape:G0×G0→G1,where G0and G1are two multiplicative groups with prime orderp,whose size are determined by the security parameterκ,andgis a generator of G0.Then the AA randomly selectsα,β ∈Zp, selects two hash functionH:{0,1}∗ →G0,H1:{0,1}d →Zpand two different one-way functionsf1andg1on Zp.Finally, the AA outputs the system parameter and a master secret key as follows.
UserReg.For each legitimate user,the AA selects a globally unique uidt ∈{0,1}das his identity,then randomly selects an exponentrt ∈Zpfor the user.The AA generates user groupGUand attribute groups{Gy:λy ∈L}.For example, if users in the system areu1,u2andu3, and the attribute sets of them are{λ1},{λ1,λ2}and{λ1,λ2,λ3}respectively, thenGU={u1,u2,u3},G1={u1,u2,u3},G2={u2,u3}, andG3={u3}.
4.2 Key Generation
In this phase, there is one step which is called KeyGen.

The AA sends the secret key to user uidtvia secure channel.If the data is owned by a DOf, the AA distributes{Kλy:Gy ∈G}to the target FD who manages the DOf.And if the data is owned by a DOc, the AA distributes{Kλy:Gy ∈G}to the DOc.
4.3 Data Encryption
In this phase, there are two scenarios that need to be considered separately.
4.3.1 Data Encryption by a DOfIn this scenario, there are two steps which are DOF.Encrypt and FD.ReEncrypt, respectively.
DOF.Encrypt.The DOfselects a random symmetric keyKand encrypts the dataMto generateEK[M], then specifies an access treeTand finally generates the ciphertext CT1.The details are as follows.
For each nodexin the access treeT, the algorithm setsdx=kx −1, wheredxis the degree of the polynomialqx,kxis the threshold value of the node.For the root nodeR, the algorithm chooses a randoms ∈Zpand setsqR(0)=s.Then,the algorithm constructsqR=aRdRxdR+aRdR−1xdR−1+···+aR1x+s,where{aRdR,aRdR−1,···,aR1}are chosen randomly.For any other nodex,the algorithm setsqx(0)=qp(x)(index(x)),and constructsqx=axdxxdx+axdx−1xdx−1+···+ax1x+qp(x)(index(x)),where{axdx,axdx−1,···,ax1}are chosen randomly.The DOfreceives the current version key componentgVKfrom the AA, and computesC2=e(gVK,gs) =e(g,g)sVK.LetYbe the set of leaf nodes inT,the DOfencrypts the dataMas follows.
Finally, the data owner DOfuploads CT1to the target FD.
FD.ReEncrypt.Before outsourcing CT1to the CSP, the FD does as follows.The FD receives a set of attribute group keys{Kλy:Gy ∈G}from the AA, then re-encrypts the CT1as follows.
Finally, the FD uploads the final ciphertext CT to the CSP.
4.3.2 Data Encryption by a DOc
In this scenario, there is only one step which is DOC.Encrypt.
DOC.Encrypt.The DOcselects a random symmetric keyKand encrypts the dataMto generateEK[M], then specifies an access treeTand finally generates the ciphertext CT.The details are as follows.
For each nodexin the access treeT, the algorithm setsdx=kx −1, wheredxis the degree of the polynomialqx,kxis the threshold value of the nodex.For the root nodeR, the algorithm chooses a randoms ∈Zpand setsqR(0)=s.Then, it constructsqR=aRdRxdR+aRdR−1xdR−1+···+aR1x+s,where{aRdR,aRdR−1,···,aR1}are chosen randomly.For any other nodex,the algorithm setsqx(0)=qp(x)(index(x)), and constructsqx=axdxxdx+axdx−1xdx−1+··· +ax1x+qp(x)(index(x)), where{axdx,axdx−1,···,ax1}are chosen randomly.The DOcreceives the current version key componentgVKfrom the AA, and computesC2=e(gVK,gs) =e(g,g)sVK.LetYbe the set of leaf nodes inT,the DOcencrypts the dataMas follows.
Finally, the data owner DOcuploads CT to the CSP.
4.4 Data Decryption
In this phase, there are two scenarios that need to be considered separately.
4.4.1 Data Decryption for a DUf
In this scenario, there are three steps which are DUF.GroupKeyDecrypt, DUF.OutsourceDecrypt,and DUF.Decrypt, respectively.
DUF.GroupKeyDecrypt.The user DUfwith uidtmay recover each attribute group keyKjfor allj ∈S.Assuming that the user uidtis marked as a nodevin the OFT corresponding to the attributej, then the user uidtcan obtain{∀i ∈paths(v) :Enki[f1(nxsibling(i))]}and recover node secrets in a down-to-top manner.Thus the user uidtcan recover the root secret, which is the attribute group keyKjin the OFT.On recovering each attribute group key{Kj:j ∈S}, the user uidtcan calculate SK as follows.
DUF.OutsourceDecrypt.In this step, the DUfwith uidtrandomly chooses a transformation keyz ∈Zpand calculates the outsourced decryption key TK as follows.
Then, the DUfwith uidtsends a decryption request to the FD together with the outsourced decryption key TK.The FD proceeds as follows.The FD first defines a recursive algorithm FD.DecryptNode(CT,TK,x) that takes as inputs a ciphertext CT, an outsourced decryption key TK,which is associated with an attribute setSfor the user uidt, and a nodexin the treeT.
• When nodexis a leaf node, the FD defines FD.DecryptNode(CT,TK,x) as follows.Ifλx ∈S,then FD.DecryptNode(CT,TK,x) =e(Dx1,Cx1)/e(Dx2,Cx2) =e(g,g)rtqx(0)/z.Ifλx/∈S,then the FD defines FD.DecryptNode(CT,TK,x)=⊥.
• When nodexis a non-leaf node, the algorithm FD.DecryptNode(CT,TK,x) proceeds in a recursive manner.For each children nodecofx,it performsFc=FD.DecryptNode(CT,TK,c).LetQx={c|p(c)=x,Fc ̸=⊥}.

If the attribute setSfor DUfsatisfies the access treeT, the FD can getA=FD.DecryptNode(CT,TK,R) =e(g,g)rts/zaccording to the definition of FD.DecryptNode.Then the FD calculatesB=e(C,D)/Aand returns CT∗=(EK[M],B,C1,C2) to the DUfwith uidt.
DUF.Decrypt.In this step, the DUfwith uidtperforms data decryption with the DUF.Decrypt algorithm, which takes as inputs CT∗and their transformation keyz.The user uidtobtains the symmetric encryption key by calculatingK=(C1,C2)/Bz.Since the user uidtrecovers the symmetric encryption keyK, he can decrypt the data by calculatingM=DK[EK[M]].
4.4.2 Data Decryption for a DUc
In this scenario, there are two steps which are DUC.GroupKeyDecrypt and DUC.Decrypt.
DUC.GroupKeyDecrypt.The user DUcwith uidtmay recover each attribute group keyKjfor allj ∈S.Assuming that the user uidtis marked as a nodevin the OFT corresponding to the attributej, then the user uidtcan obtain{∀i ∈paths(v) :Enki[f1(nxsibling(i))]}and recover node secrets in a down-to-top manner.Thus the user uidtcan recover the root secret, which is the attribute group keyKjin the OFT.On recovering each attribute group key{Kj:j ∈S}, the user uidtcan calculate SK as follows.
DUC.Decrypt.In this step, the DUC.Decrypt algorithm proceeds as follows.The DUcwith uidtfirst defines a recursive algorithm DecryptNode(CT,SK,x) that takes as inputs a ciphertext CT,a user’s secret key SK, which is associated with an attribute setSof the user uidt, and a nodexin the treeT.
• When nodexis a leaf node, the decryption algorithm is defined as follows.Ifλx ∈S, then DecryptNode(CT,SK,x)=e(Dx1,Cx1)/e(Dx2,Cx2)=e(g,g)rtqx(0).Ifλx/∈S,then the algorithm defines DecryptNode(CT,SK,x)=⊥.
• When nodexis a non-leaf node,the algorithm DecryptNode(CT,SK,x)proceeds in a recursive manner.For each children nodecofx, the algorithm performsFc=DecryptNode(CT,SK,c).LetQx={c|p(c)=x,Fc ̸=⊥}.

If the attribute setSfor DUcsatisfies the access treeT, the user with uidtcan getA=DecryptNode(CT,SK,R) =e(g,g)rtsaccording to the definition of DecryptNode.Then the user with uidtobtains the symmetric encryption key by calculatingK= (C1·C2)/(e(C,D)/A).Since the user uidtrecovers the symmetric encryption keyK, he can decrypt the data by calculatingM=DK[EK[M]].
4.5 Attribute Revocation
In this phase, there is only one step which is called AttrRev.
AttrRev.When the attributeλiof the user uidMis revoked, then the secret key for each legitimate user who holds the same attributeλiand the ciphertext will be updated.Figure 3 is an example for this process.In Figure 3, the OFT is constructed according toGi, in which all the users hold the attributeλi.Once the attributeλifor the user uidMis revoked, the corresponding node in Figure 3 should be revoked.In Figure 3, the user uidMis assigned as the leaf nodevM, and the revocation ofλifor user uidMmeans the leaf nodevMshould be revoked so that the user uidMcan no longer figure out the new attribute group key.The detailed process is as follows.

Figure 3 Example for attribute revocation
(1) The AA firstly constructs a new groupG′i=Gi{uidM},which includes the nodev6,v7,v8,v9,andv10in Figure 3.
(2) The AA still assigns a new virtual node secret nx′vMto the nodevM, which is the nodev11in Figure 3.In this way, the structure of the OFT remains unchanged, which guarantees the efficiency of attribute revocation.
(3) The AA computes the new root node secretK′λiaccording to the updated OFT.Then the

While the revoked user uidMcannot figure outK′λi, the reason is that, the AA no longer assigns the new virtual node secret nx′vMto uidM, which is a must to figure outK′λi.In addition, the revoked user uidMcannot obtain any useful information from the broadcasted message to figure outK′λi, either.
4.6 Dynamic User Management
In this phase, there is only one step which is called UserMag.
UserMag.When a user is removed from or added into the system, the AA runs UserMag to dynamically manage users by updating the relevant ciphertext and secret key component.
4.6.1 Removing a User from the System
When the data user uidµis removed from the system, which means all attributes of uidµare revoked simultaneously, the user group changes toGU1={uid1,uid2,···,uidm}{uidµ}.The AA randomly selects a VK′, which is different from the previous version key VK, computes the updated key as CUK=VK′/VK, and sends the updated key to the CSP for updating CT′as follows.
4.7 Correctness of Our NDSS-FC Scheme
Theorem 1 Our NDSS-FC scheme is correct, that is, the system and legitimate users can successfully encrypt the plaintext and decrypt the ciphertext, respectively.
Proof 1 After correctly carrying out the System Setup phase and the Data Encryption phase,the CT is generated as CT = (EK[M],T,C=hs,C1=Ke(g,g)αs,C2=e(g,g)sVK,{∀y ∈Y:Cy1=gqy(0),Cy2= (H(λy)qy(0))Kλy}).After correctly carrying out the Key Generation phase,the DUF.GroupKeyDecrypt step and the DUF.OutsourceDecrypt step, the outsourced decryption key of TK is TK = (D=g(α+rt+VK)/(βz),{∀j ∈ S:Dj1=grt/zH(j)rj/z,Dj2=grj/(zKj)}),wherezis the transformation key of DUf.After carrying out the Key Generation phase and the DUC.GroupKeyDecrypt step, the secret key of DUcis SK = (D=g(α+rt+VK)/β,{∀j ∈S:Dj1=grtH(j)rj,Dj2=(grj)1/Kj}).
We firstly prove that a legitimate user DUfcan successfully decrypt the CT.The recursive algorithm FD.DecryptNode(CT,TK,x) is performed correctly.
(1) Ifxis a leaf node andλx ∈S, then

5 Security Analysis
5.1 Formal Proof
Theorem 2 Suppose there exists an adversaryA, that can attack NDSS-FC in the IND-CPA game with advantageε.Then, we can construct a simulatorBthat can distinguish a DBDH tuple from a random tuple with advantageε/2.
Proof 2 Lete: G0×G0→G1be an efficiently computable bilinear map, where G0is prime orderpwith generatorg.Next, the DBDH challengerCrandomly selects the following parametersa,b,c ∈Zp,µ ∈{0,1}, andX ∈G1.CdefinesZto bee(g,g)abcifµ= 0.Otherwise,CsetsZ=X.Z=Xthen gives (g,A,B,C,Z) = (g,ga,gb,gc,Z) toB.Now,Bplays the role of challenger in the following game.
Init.Achooses a challenge access structureT ∗that he wishes to be challenged upon.
Setup.Brandomly choosesα′,β ∈Zpand definesα=α′+ab.Bgives PK ={G0,g,gβ,g1/β,e(g,g)α}toA.The corresponding master key is MK=(β,gα).
Phase 1.Ais allowed to issue queries for private keys for many attribute sets{S1,S2,···,Sd1},but the restriction is that allSjcannot satisfyT ∗.Bchoosesrt,VK∈Zpand selectsrj,Kj ∈Zpfor each attributej ∈Sj.The secret key forSjisSj= (D=g(α+rt+VK)/β,{∀j ∈Sj:Dj1=grtH(j)rj,Dj2=grj/Kj}).
Towards the update key queries, supposeAqueries the pairs{uid,λi}, in which uid is a user’s identity andλiis the revoked attribute.Assume that the revoked user is marked as nodevM, then the challenger returns the new attribute group information{∀i ∈paths(vM) :Enksibling(i)[f1(nxi)]}toA.If uid is a non-revoked user,Bsends back the new attribute group keyK′λi.Otherwise,Bresponses⊥.
Challenge.Apicks two symmetric keysK0,K1with equal length before sending them toB,thenBflips a random coinb ∈{0,1}, and encryptsKbwithT ∗.The dataMis encrypted asEKb[M].Bsetss=c.The ciphertext is set as CT = (EKb[M],T ∗,C=hc,C1=KbZe(g,g)α′c,C2=e(g,g)cVK,{∀y ∈Y:Cy1=gqy(0),Cy2=(H(λy)qy(0))Kλy}), whereYis the set of leaf nodes forT ∗.Then,Bsends CT to the adversaryA.
Phase 2.Phase 1 is repeated.
Guess.Aoutputs a guessb′ofb.Ifb′=b,Boutputs 0 to guess thatZ=e(g,g)abc.Otherwise,Boutputs 1 to indicate thatZis a random group element in G1.
IfZ=e(g,g)abc, the adversary sees an encryption ofKb.The adversary’s advantage in this situation isεby definition, that is, Pr[B(g,ga,gb,gc,Z=e(g,g)abc)=0]=1/2+ε.
IfZ=X, then the adversary gains no information aboutb, that is, Pr[B(g,ga,gb,gc,Z=X) =0]=1/2.
The overall advantage of the simulator in the DBDH game is as follows.
Hence, the result is in contradiction with DBDH assumption.Therefore, the adversary cannot exist, and our NDSS-FC is IND-CPA secure.This completes the proof of Theorem 2.
Theorem 2 proves that NDSS-FC scheme can successfully resist IND-CPA under the DBDH assumption, which means our NDSS-FC scheme can realize secure data sharing with fine-grained access control in fog and cloud computing environments.

Proof 4 Once the userA2is removed from the system,in order to break our NDSS-FC scheme,we assumeA2requires at leastkmore attributes to satisfy the access policy embedded in the ciphertext.

Theorem 4 proves that the removed users cannot decrypt the ciphertext, that is, our NDSS-FC scheme can manage users dynamically and securely.
Theorem 5 NDSS-FC is collusion-resistant, that is, NDSS-FC can prevent collusion attacks among the legitimate users, the revoked users and the external attackers.
Proof 5 For the legitimate user uid1and the revoked user uid2, we suppose thatλk ∈S2is revoked.Since uid1holds the attributeλk, he can obtain the attribute secret key ofλkasDk1=gr1H(λk)rk,Dk2=grk, thus he can decrypt the leaf node secret associated withλkas DecryptNode(CT′,SK′1,k) =e(g,g)r1(qk(0)+s′)and send it to uid2.uid2can decrypt the leaf node secret associated withλy ∈S2which he still holds as DecryptNode(CT′,SK′1,y) =e(g,g)r2(qy(0)+s′).However, uid2cannot gete(g,g)r2(s+s′)as the valuer2is different fromr1.Thus he cannot decrypt the symmetric encryption keyKwhich is a key requirement for decrypting the ciphertext.Thus uid2cannot collude with uid1to decrypt the ciphertext illegally.
For the collusion attack launched by the revoked users uid3and uid4,we suppose that the attributesλµ ∈S3andλγ ∈S4are revoked, uid3still holds the attributeλγand uid4still holds the attributeλµ.uid3and uid4cannot decrypt the current ciphertext because their attribute sets do not satisfy the access policy any more.Since uid3holds the attributeλγ, he can obtain the attribute secret key ofλγasDγ1=gr3H(λγ)rγ,Dγ2=grγ, thus he can decrypt the leaf node secret associated withλγas DecryptNode(CT′,SK′3,γ) =e(g,g)r3(qγ(0)+s′)and send it to uid4.uid4can decrypt the leaf node secret associated withλµwhich he still holds as DecryptNode(CT′,SK′4,y) =e(g,g)r4(qy(0)+s′).However, uid4cannot gete(g,g)r4(s+s′)as the valuer3is different fromr4.Thus he cannot decrypt the symmetric encryption keyKwhich is a key requirement for decrypting the ciphertext.Thus uid4cannot collude with uid3to decrypt the ciphertext illegally.
For the legitimate user uid5and the external attackerA, since the attribute set of uid5does not satisfy the access policy embedded in the ciphertext, he is obviously cannot decrypt the data.Ahas no knowledge about the secret key.It would not be helpful even if uid5sends his secret key toA.SoAcannot collude with uid5to decrypt the ciphertext illegally.
Theorem 5 proves that our NDSS-FC scheme can resist collusion attacks launched by the legitimate user and the revoked user, or by the revoked users, or by the revoked user and the external attackers.
5.2 Security Comparison
In this section, we compare our scheme with other ABE schemes[6,7,13,14,20]in Table 2 in terms of attribute revocation, user management, collusion attack resistance, outsourced decryption and computing paradigm.Note that “Yes” means to have the ability, “No” means to have not.According to Table 2, our NDSS-FC scheme can realize all the security goals.Both Schemes [6] and [7] cannot realize dynamic user management, outsourced decryption, and can only be applied in cloud environment.Both Schemes [20] and [13] cannot realize attribute revocation, dynamic user management, and can only be applied in fog environment.Scheme [14] cannot realize dynamic user management, and can only be applied in fog environment.
6 Performance Analysis
In this section, we analyze the performance of our NDSS-FC scheme and other related schemes in terms of communication overhead and computation overhead.We apply the standards for Hur’s benchmark timing[7]in terms of paring in G0(2.9 ms), exponential operation in G0(1.0 ms) and exponential operation in G1(0.2 ms), which was implemented with the PBC library ver.0.4.18 for a Type A curve on a 3.0 GHz processor PC.The public parameters are selected to provide 80-bit security level.The implementation uses a 160-bit elliptic curve group based on the supersingular curvey2=x3+xover a 512-bit finite field.Note thatC0represents the size of elements in G0,C1represents the size of elements in G1,CTrepresents the size of an access treeTin the ciphertext,trepresents the number of attributes appeared inT,lrepresents the number of attributes that the user satisfiesT, andmrepresents the number of users in an attribute group.
6.1 Communication Overhead
Communication overhead is mainly caused by the ciphertext size, which represents the communication cost for each entity to send each other the ciphertext in the system.In Table 3, we compare the size of a ciphertext for participated entities among different schemes[6,7,13,14,20], and our NDSS-FC.
In Schemes [6] and [7], the length of a ciphertext for the DO and the CSP is same as (2t+1)C0+C1+CT.The length of a ciphertext for the DO and the CSP in our NDSS-FC scheme is(2t+1)C0+2C1+CT, which is slightly larger than that in Schemes [6] and [7].The reason is that in our scheme, the ciphertext contains one more element in G1to realize dynamic user management.In addition, the FD in our NDSS-FC is participated in re-encrypting and transmitting the ciphertext.However, our scheme enables dynamic user management, which is not available in Schemes [6] and [7].
In Scheme [20], the size of the partial ciphertext for the DO is 4C0+C1, and the size of the whole ciphertext for the CSP is (2t+4)C0+C1+CT.The size of the partial ciphertext for the DO in our NDSS-FC scheme is (2t+1)C0+2C1+CT, which is larger than that in Scheme [20].The reason is that, in Scheme [20], the system may outsource the encryption operations to the outsourced encryption service provider (OESP).The size of the whole ciphertext for the CSP in our NDSS-FC scheme is (2t+ 1)C0+ 2C1+CT, which is slightly smaller than that in Scheme [20].The reason is that, in Scheme [20], the ciphertext contains several redundant components to achieve outsourced encryption.In addition, the FD in our NDSS-FC is participated in re-encrypting and transmitting the ciphertext.
In Scheme[13],the size of the ciphertext for the FD is(2t+2)C0+CT,the length of the ciphertext for the DO is(2t+2)C0+C1+3CT,and the length of the ciphertext for the CSP is(2t+2)C0+C1+2CT.The size of the ciphertext for the FD in our NDSS-FC scheme is (2t+1)C0+2C1+CT, which is slightly larger than that in Scheme [13].The reason is that, in Scheme [13], the FD carries out the first encryption and the ciphertext contains no components related to the plaintext.The length of the ciphertext for the DU and the CSP in our NDSS-FC scheme is (2t+1)C0+2C1+CT, which is slightly smaller than that in Scheme [13].The reason is that, in Scheme [13], the ciphertext contains one redundant component to achieve outsourced encryption and one more access policy to update ciphertexts.
In Scheme[14],the size of the partial ciphertext for the DO is 3C0+C1,the length of the ciphertext for the FD and the CSP is (2t+3)C0+C1+CT.The size of the partial ciphertext for the DO in our NDSS-FC scheme is (2t+1)C0+2C1+CT, which is larger than that in Scheme [14].The reason is that, in Scheme [14], the system may outsource the encryption operations to FDs.The length of the ciphertext for the FD and the CSP in our NDSS-FC scheme is (2t+1)C0+2C1+CT, which is slightly smaller than that in Scheme [14].The reason is that, in Scheme [14], the ciphertext contains several redundant components to achieve outsourced encryption.
6.2 Computation Overhead
In this section, we analyze the computation overhead in terms of encrypting (by a DO) and decrypting (by a DU) among our NDSS-FC scheme and other Schemes [6,7,13,14,20].Note that the comparatively negligible hash operations and arithmetic operations on Zpare ignored in the time result.
6.2.1 Comparison of Encryption Computation
Figure 4 shows the results for comparison of computation overhead for encryption.

Figure 4 Comparison of computation overhead for encryption
The computation overhead for encryption in Schemes [6] and [7] is 2t+1.2 ms.The computation overhead for encryption in our NDSS-FC scheme is 2t+ 5.1 ms, which is slightly larger than that in Schemes [6] and [7].The reason is, in order to realize dynamic user management, our NDSS-FC scheme should apply one additional exponential operation in G0and one additional paring in G0to generate a version key component and embed it in the ciphertext.Although the computation overhead in our scheme is a little larger, our scheme enables dynamic user management, which is not available in Schemes [6] and [7].
The computation overhead for encryption in Scheme[20]is 4.2 ms.The computation overhead for encryption in our NDSS-FC scheme is 2t+5.1 ms,which is larger than that in Scheme[20].The reason is that Scheme [20] outsources the most encryption operations to the outsourced encryption service provider (OESP) with only constant operations for the DO.Although the computation overhead in our scheme is larger, our scheme enables secure attribute revocation and dynamic user management,which is not available in Scheme [20].
The computation overhead for encryption in Schemes [13] and [14] is 3.2 ms.The computation overhead for encryption in our NDSS-FC scheme is 2t+5.1ms,which is larger than that in Schemes[13]and [14].The reason is that Schemes [13] and [14] outsources the most encryption operations to the corresponding FD with only constant operations for the DO.Although the computation overhead in our scheme is larger, our scheme enables dynamic user management, which is not available in Schemes [13]and [14].
6.2.2 Comparison of Decryption Computation
In this section, we compare the decryption computation of our NDSS-FC with Schemes [6,7,13,14,20].Since Schemes [13] and [14] are constructed in the fog computing environment, we compare our NDSS-FC scheme with Schemes [13] and [14] in terms of decryption overhead for a DUfand a fog node.Since Schemes [6,7,20] are constructed in the cloud computing environment, we compare our NDSS-FC scheme with Schemes [6,7,20] in terms of decryption overhead for a DUc.
In Figure 5(a), we can see the decryption time for a DUfin Schemes [13] and [14] is same as 2.9 ms.The decryption time in our NDSS-FC scheme is a constant 0.2 ms, which is slightly smaller than that in Schemes [13] and [14].The reason is that in our NDSS-FC scheme, the user only needs an exponential operation in G1to finish the decryption process, instead of a paring operation in G0in Schemes [13] and [14].
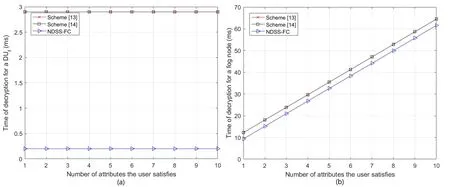
Figure 5 Comparison of computation overhead for decryption I
In Figure 5(b), we can see the decryption time for a fog node in Schemes [13] and [14] is same as 2.9(2l+2)+0.2 logtms.The decryption time in our NDSS-FC scheme is 2.9(2l+1)+0.2 logtms, which is slightly smaller than that in Schemes [13] and [14].The reason is that a fog node in Schemes [13] and [14] needs one more pairing operation in G0to complete the outsourced decryption process.
In Figure 6, we can see the decryption time for a DUcin our NDSS-FC and Scheme [7] are the same as 2.9(2l+2)+0.2 logtms.The decryption time in Scheme [20] is a constant 0.2 ms.The reason is that Scheme [20] outsources most of the decryption operations to the outsourced decryption service provider (ODSP).The decryption time in Scheme [6] is 2.9(2l+2)+0.2 logt+mlms, which is the largest among the compared schemes.

Figure 6 Comparison of computation overhead for decryption II
7 Conclusion
In this paper, to combine the traditional cloud computing and the promising fog computing,we propose a novel data sharing scheme in fog and cloud computing environments (NDSS-FC).Our NDSS-FC scheme can achieve secure and efficient data sharing in fog and cloud computing architecture with outsourced decryption.Moreover, our NDSS-FC scheme can realize secure attribute revocation and dynamic user management.Then, we formally prove that our NDSS-FC scheme can resist chosen plaintext attack, can securely revoke attributes, can securely manage users, and can resist the collusion attacks.Finally, comparisons of both communication overhead and computation overhead indicate that our NDSS-FC scheme is secure and efficient.
