Resilient Event-Triggered Model Predictive Control for Adaptive Cruise Control Under Sensor Attacks
2023-03-27ZhijianHuRongSuKaiZhangZeyuanXuandRenjieMa
Zhijian Hu, Rong Su,, Kai Zhang,Zeyuan Xu, and Renjie Ma,
Dear Editor,
This letter addresses the resilient model predictive control (MPC)problems for adaptive cruise control (ACC) systems under sensor attacks.In the light of vulnerabilities of ACC systems to sensor attacks, an intrusion detection mechanism is proposed at the controller side to distinguish abnormal data.Then, the robust control gains are derived to design the terminal region constraint for MPC.Further, an improved event-triggered scheme is presented, which shows the ability to relieve the computation burden in the implementation of MPC, by combining the memory-based event-triggered condition and the maximum allowed time interval condition.Finally,efficacy validations are given in simulations.
ACC provides critical auxiliary techniques for autonomous vehicles, and facilitates a safe and comfortable journey for both drivers and passengers [1]–[3].The main function of ACC system is to monitor the other vehicles’conditions by sensors and then maintain the constant velocity, acceleration and the longitudinal distance with them.In recent decades, a flood of concerns regarding to ACC have been addressed by researchers from different perspectives.Some focused on the control methods formulation [4], while others emphasized the application scenarios exploration and performance enhancement [5]–[7].
Due to the intrinsic constraints of position, velocity, and acceleration involved in ACC, the MPC methods are seen as a kind of promising solutions.In [5], road elevation information and fuel-saving factor were simultaneously considered to design MPC for ACC system.Reference [7] constructed a MPC framework for ACC system with the consideration of four objectives, including comfort, fueleconomy, safety, and car-following.However, none of the above methods considered the calculation volume when implementing MPC, let alone the countermeasures of reducing the calculation burden.
To reduce the calculation burden of implementing MPC for ACC,the event-triggered scheme has been considered as a category of efficient means.Under the event-triggered scheme, the measured output is used as the feedback signal only if well-designed event-triggered conditions hold.In existing related works, most of the event-triggered schemes were designed by comparing measured outputs at adjacent time instants, such as [8]–[11].However, these event-triggered conditions overlooked the feature of system dynamic curves.As an improvement, memory-based event-triggered schemes have been proposed in recent years [12], in which several historic released signals were collected to formulate the event-triggered conditions.
Sensor attacks are nothing new in autonomous vehicle control systems [13]–[18].From adversary’s perspective, two different categories of malicious attacks are possible on sensors to implement their conspiracy.One category is classified as the denial-of-service (DoS)attack [16], which makes sensors cannot produce the successive measurements.The other is classified as the false data injection (FDI)attack, which plants the false information to the sensor and destroys the data’s authenticity.In [17], an adaptive control framework was constructed to mitigate both sensor and actuator attacks.However,these investigations with the sensor attack considerations are not directly applicable to ACC systems.
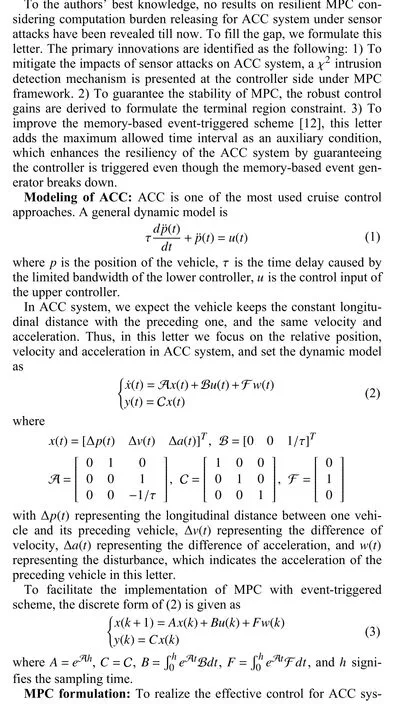


Fig.1.Position, velocity, acceleration signals with and without χ2attack detection mechanism.

Fig.2.Event-triggered instants and intervals.
Conclusion:In this letter, a resilient MPC method is investigated for ACC system under sensor attacks.To mitigate the impacts of sensor attacks on system dynamics, an intrusion detection mechanism is designed.To relieve the calculation burden in the implementation of MPC, traditional memory-based event-triggered scheme is improved by integrating of the maximum allowed time interval as a complementary event-triggered condition.Comparison simulations verify that both the proposed intrusion detection mechanism and the eventtriggered scheme are effective.
Acknowledgments:This work was supported in part by A*STAR under its RIE2020 Advanced Manufacturing and Engineering (AME)Industry Alignment Fund-Pre Positioning (IAF-PP) (Award A19d6a 0053); the Agency for Science, Technology and Research (A*STAR)(I2001E0067) and the Schaeffler Hub for Advanced Research at NTU; National Natural Science Foundation of China (62203142); the China Postdoctoral Science Foundation (2022M710966, 2022TQ 0096).Any options, findings and conclusions or recommendations expressed in this material are those of the author(s) and do not reflect the views of A*STAR.
杂志排行
IEEE/CAA Journal of Automatica Sinica的其它文章
- Meta-Energy: When Integrated Energy Internet Meets Metaverse
- Cooperative Target Tracking of Multiple Autonomous Surface Vehicles Under Switching Interaction Topologies
- Distributed Momentum-Based Frank-Wolfe Algorithm for Stochastic Optimization
- A Survey on the Control Lyapunov Function and Control Barrier Function for Nonlinear-Affine Control Systems
- Squeezing More Past Knowledge for Online Class-Incremental Continual Learning
- Group Hybrid Coordination Control of Multi-Agent Systems With Time-Delays and Additive Noises
