DRRS-BC: Decentralized Routing Registration System Based on Blockchain
2021-11-07HuiminLuYuTangandYiSun
Huimin Lu,,Yu Tang,and Yi Sun,
Abstract—The border gateway protocol (BGP) has become the indispensible infrastructure of the Internet as a typical interdomain routing protocol.However,it is vulnerable tomisconfigurations and malicious attacks since BGP does not provide enough authentication mechanism to the route advertisement.As aresult,it has brought about many security incidents with huge economic losses.Exiting solutions to the routing security problem such as S-BGP,So-BGP,Ps-BGP,and RPKI,are based on the Public Key Infrastructure and face a high security risk from the centralized structure.In this paper,we propose the decentralized blockchain-based route registration framework-decentralized route registration system based on blockchain (DRRS-BC).In DRRS-BC,we produce a global transaction ledge by the information of address prefixes and autonomous system numbers between multiple organizations and ASs,which is maintained by all blockchain nodes and further used for authentication.By applying blockchain,DRRS-BC perfectly solves the problems of identity authentication,behavior authentication as well as the promotion and deployment problem rather than depending on the authentication center.Moreover,it resists to prefix and subprefix hijacking attacks and meets the performance and security requirements of route registration.
I.INTRODUCTION
WITH the rapid development of network technology,how to effectively and securely manage the network is an important issue.For scalability,the Internet is divided into different autonomous systems (ASs).Each AS is consisted of a group of hosts and routers under the administrative control of an entity.It is a separate,manageable network group just like a university,an organization,or a company.Correspondingly,the routing protocols are also divided into two categories,intra-domain routing protocol and inter-domain routing protocol.The border gateway protocol (BGP) is a typical inter-domain routing protocol which has become the infrastructure of the Internet nowadays because of its robust and reliable design of the routing function.However,the security is weak and it even does not protect the authenticity to the route advertisement.Therefore,it remains vulnerable to misconfigurations and malicious attacks,which would lead to instability in the routing system or severe reachability problems.
The research by Murphyet al.[1],[2]shows that BGP has significant design flaws and security risks in terms of security.In BGP route propagation process,when a BGP router performs route propagation,the AS can only advertise its own prefix address block to the outside.The BGP neighbor node accepts any routing update information sent by the peer by default.In other word,the BGP router unconditionally trusts the routing advertisement of the peer.Even if an AS advertises a forged prefix while not its own,it will be accepted by the peer and the protocol will continue to propagate.This forged routing information will undoubtedly lead to many security problems.The most typical is the prefix hijacking which has caused many Internet security incidents.In 2006 [3],AS174 illegally announced the address prefix 64.233.161.0/24 assigned to Google by AS15169,which caused a large range of Google service requests to be redirected to AS174 and eventually led to a large-scale interruption of Google service requests.In 2006 [4],the AS27506 incorrectly advertised the address prefix 166.84.0.0/16 and brought about a hijacking traffic to Panix company.In 2008 [5],Pakistan Telecom (AS17557)incorrectly announced YouTube’s prefix 208.65.153.0/24,which caused the YouTube service to smash for 80 minutes and caused Pakistan Telecom to be overwhelmed by a large amount of network traffic.In 2017 [6],due to route misconfiguration,Google Inc.accidentally hijacked the traffic of NTT Communications Co.,Ltd.,causing a massive network disconnection in Japan for about one hour.NOCTION’s BGP Stream service has detected 3482 possible BGP hijackings in the monitored network from November 28,2015 to May 31,2017,and there would be much more in the global network.
Therefore,it is very important and necessary to solve the BGP prefix hijacking problem and improve the security of BGP.In this respect,the US BBN company proposed the secure BGP protocol (S-BGP) in 2000 [7],[8].S-BGP grants the public key and certificate to the IP address prefix and the AS owner to implement secure authentication of the address prefix and the AS identity.However,it brings about large computational cost and prolonged path convergence time [9].White proposed the secure origin BGP protocol (SoBGP) in 2003 [10].The SoBGP authenticates the prefix and AS identity by verifying the correctness and authorizing of the data from BGP and can resist misconfiguration and prefix hijacking.But the lack of the anchor’s address authorization reduces the security of SoBGP and it cannot defend against prefix-based hijacking attacks bases on routing policies [11].And then,Orschotet al.proposed the pretty secure BGP protocol (PsBGP) in 2007 [12].The PsBGP uses the mutual authentication between neighbors to prefix source AS authentication.In the PsBGP,each AS creates a public key certificate of its own BGP router and a prefix assertion list PAL.Where PAL consists of a set of address prefixes owned by itself and its neighbor ASs.However,due to the possibility of “perjury” between ASs,the feasibility of this scheme is greatly reduced.Hu proposed the security enhanced BGP protocol (SE-BGP) in 2009 [13].SE-BGP also uses certificate system and its certificate structure adopts the DRCM mechanism for AS Alliance.It introduces the TTM model to realize the in-band transfer of trust relationships through two signature conversions of key nodes.However,the protocol is too complicated,not only too computationally expensive but also difficult to deploy.Among these solutions,the most feasible solution is RPKI which is an infrastructure based on PKI led by the IETF’s SIDR working group.Its main purpose is to provide authenticity verification for the correspondence between IP prefix and AS number,and thus it effectively prevents BGP prefix hijacking.However,the potentially misconfigured,faulty or compromised RPKI authorities may introduce new risk and the deployment of RPKI also makes tardy progress.At present,there is only 6.55% address coverage,and among the 6.55%,only 62.48% are effectively protected [14].Cooperet al.systematically analyzed the risk of RPKI and pointed out that RPKI cannot prevent deleting and overw riting of objects from malicious authorities [15].Heilmanet al.then proposed a mechanism to improve the transparency of RPKI [16].Birge-Leeet al.proposed Bamboozling certificate authorities with BGP,but it still has the problem of certificate overissuing [17].Xinget al.proposed BGPcoin system based on Ethereum which did not design an independent blockchain system [18].Although all these solutions can protect the origin of IP address prefix,they produce another serious risk that authentication rights may be abused by authorities,which will damage the authenticity,integrity and usability of resources.However,the idea that utilizing blockchain to solve various problems is worth learning in solving the security problem of BGP [19]–[21].
In order to both protect the origin of IP address prefix and avoid centralized structural risk,in this paper,we innovatively propose a decentralized route registration system based on blockchain (DRRS-BC).In the proposed DRRS-BC,it records and audits the Internet number resource allocation,validates BGP origin route attestation and further authorizes and distributes address prefixes and AS numbers between multiple organizations and ASs.By applying blockchain,DRRS-BC perfectly solves the problems of identity authentication and behavior authentication rather than depending on the authentication center.
In a word,the contributions of this paper can be summarized as follows.
1) We propose the decentralized blockchain-based route registration framework in routing system to protect the origin of IP address prefix and avoid centralized structural risk.
2) DRRS-BC establishes a global network resource transaction ledge by the information of address prefixes and AS numbers between multiple organizations and ASs,which perfectly solves the security problems of identity authentication and behavior authentication in traditional BGP by introducing blockchain rather than depending on the authentication center.
3) Security analysis shows that DRRS-BC is secure to prefix and subprefix hijacking attacks.Experiments also show that DRRS-BC system can meet the performance and security requirements of route registration.
II.DRRS-BC
In this section,we firstly give the overview of DRRS-BC and then describe the proposed DRRS-BC in details.
A.Architecture Overview
Essentially speaking,DRRS-BC is a decentralized routing information database constructed based on blockchain.This database is jointly established by all organizations that participate in the assignments and authorizations of address prefixes and AS numbers and records every network resource transaction between all organizations.It provides a tamperproof and traceable proof of ownership of the AS numbers and address prefixes.The entire system consists of clients,endorsement nodes,block generation nodes,and ledger storage nodes without any authentication center.Each organization runs a client,endorsement node,and several ledger storage nodes.The core operators and organizations of the Internet run block production nodes and each autonomous system can also run a ledger storage node.The decentralized architecture of DRRS-BC is depicted in Fig.1.
When an organization needs to transfer an address prefix to another organization,the organization’s client creates a network resource transaction and broadcasts it to the endorsement nodes of the organizations in the network according to the endorsement strategy.After each endorsement node receives the transaction request from the client,it checks whether the transaction is qualified according to the defined endorsement logic.If it is qualified,the endorsement will be endorsed,and if it fails,it will reject the endorsement.If the client receives enough endorsement response,then the transaction endorsement succeeds,else the endorsement fails and the client abandons the transaction.A fter endorsement,it is the block producing phase.We apply speculative Byzantine fault tolerance (SBFT) consensus protocol between all block producing nodes to construct a totally ordered sequence of endorsed transactions grouped in blocks.Finally,the block producing node broadcasts the new block and further transferred it to each ledger storage node and then a network resource transaction ledger based on a unified consensus between all organizations creates like this.
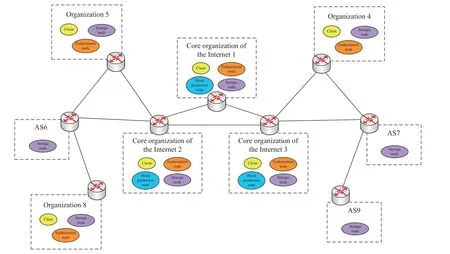
Fig.1.The architecture of DRRS-BC.
In the process of forming a global network resource transaction ledge,each organization runs a variety of nodes.Each type of node between organizations constitutes the entire blockchain network and the system is permissioned.A ll nodes that participate in the network have an identity provided by a modular membership service provider.In other words,only registered organizations can participate in this blockchain system for network resource transactions.
There are four main types of nodes in the system.
Clientis an entity that actually creates a transaction and it can communicate with all endorsement nodes and block production nodes in the network.When an organization wants to initiate a network resource transaction,the client creates a transaction according to a specific transaction structure.The transaction structure will be described in detail in Section II-B.Then,the client submits the transaction to each endorsement node for endorsement.Finally,the client constructs a legitimate transaction request and submits it to each block production node.
Endorsement nodesare run in each organization.They verify the transaction submitted by the client and complete the endorsement of the transaction.After an endorsement node receives the transaction endorsement request from the client,it verifies the validity of the transaction according to the verification rule.The validation rule will be described in detail in Section II-B.If the transaction satisfies the validation rule,the endorsement node attaches the endorsement signature of the endorsement node to the transaction and sends the message back to the client.Only when a transaction receives enough endorsement signatures,the transaction will be submitted as a legitimate transaction to the block production nodes for consensus.
Block production nodesare run in the core operators and organizations of the Internet and the number is determined.The function is to arrange legitimate transactions into a welldefined sequence,and package them into blocks for subsequent distribution.These blocks will become the blocks of the blockchain.The block production nodes collect all legitimate transactions submitted by the client,verify their endorsements,and package the transactions according to the block size or time window.Finally,a globally unique block is generated between the block production nodes through the SBFT consensus protocol and broadcasted to each ledger storage node.
Ledger storage nodesare run in each organization and autonomous system.They are the ultimate storage nodes in the network resource transaction blockchain.A ll BGP routers or ASs in the network can access the ledger storage nodes and query the ownership of the AS numbers and address prefixes.The ledger storage nodes are responsible for periodically receiving transaction blocks sorted by block production nodes,conducting final checks on these transactions and maintaining the blockchain ledger.Once the transactions are recorded in the blockchain,the ledger can not be changed.They can provide tamper proof and traceable proof of ownership of the AS numbers and address prefixes.
B.DRRS-BC
DRRS-BC is also a system for authorizing and distributing address prefixes and AS numbers between multiple organizations and ASs.The transaction flow of DRRS-BC across different types of nodes is depicted in Fig.2.
There are three phases in the proposed DRRS-BC.
1) Phase 1: Construct Legitimate Transaction
The legitimate transaction construction phase involves an interaction between a client and a set of endorsement nodes.This phase is only concerned with the client asking different organizations’ endorsement nodes to verify and agree the client-created transactions.
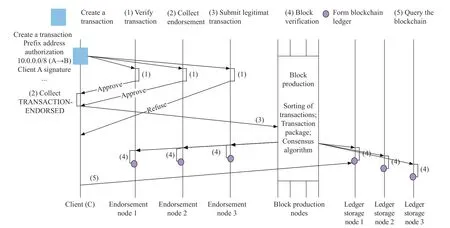
Fig.2.The workflow of DRRS-BC.
To start this phase,the client creates a transaction proposal according to the defined transaction structure,and then sends it to each of the required set of endorsement nodes for endorsement.The choice of endorsement nodes depends on the endorsement policy,which defines the set of organizations that need to endorse a proposed transaction before it can be accepted by the network.Each endorsement node then independently verifies the transaction proposal based on defined validation rules and generate a transaction proposal response indicating whether to endorse it.The endorsement node endorses a proposal response by adding its digital signature,and signing the entire payload using its private key.This endorsement can be subsequently used to prove that this organization’s endorsement node generated a particular response.When the client receives signed proposal responses from sufficient endorsement nodes,it attaches the endorsement policy and the digital signature of every collected endorsement node behind this transaction.So,a legitimate transaction consists of a transaction proposal,an endorsement policy and the digital signature of endorsement nodes.
For ease of understanding,we use the following example to explain Phase 1 in detail in Fig.3.
In this example,the client C1 generates the transaction proposal T1 and the set of endorsement nodes P which defines E1 and E2 as endorsement nodes.When the endorsement node E1 receives T1 and P,it verifies the transaction proposal T1 according to the endorsement policy P1 and synchronized ledger L1 at this moment.If the transaction passes verification,the endorsement node E1 generates the digital signature D1 as a response.Independently,the endorsement node E2 also generates a response D2 in the same way.Finally,after the client C1 collects sufficient response,it constructs a legitimate transaction and submits it to block production nodes.
● Transaction structure
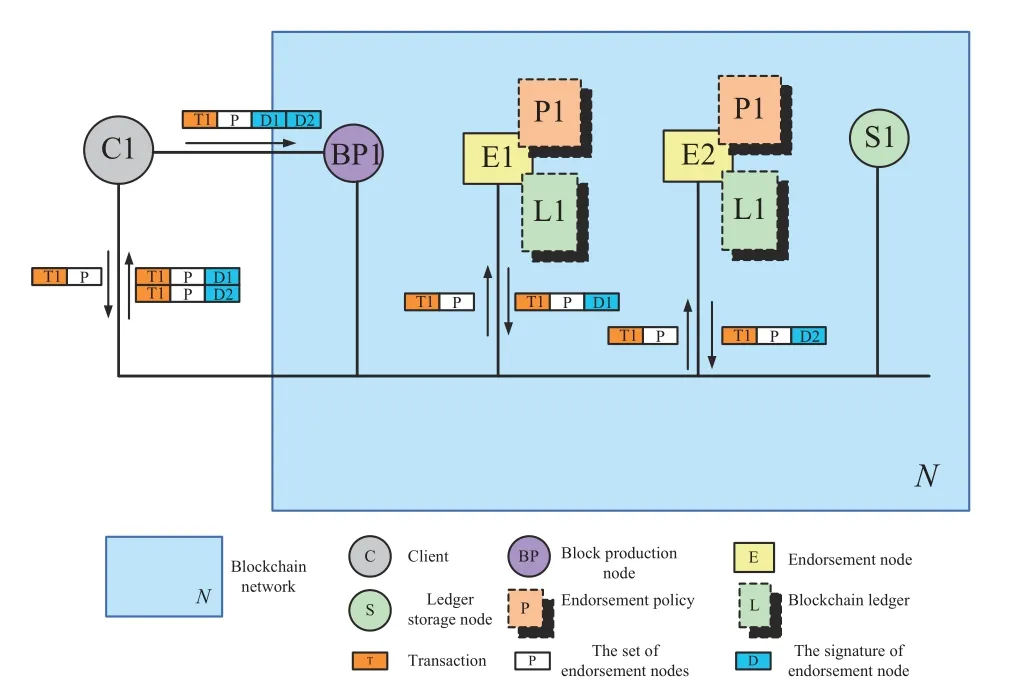
Fig.3.The schematic of Phase 1.
Transactions are the most important part in DRSS-BC.Everything else in DRRS-BC is designed to ensure that transactions can be created,propagated,validated,and finally added to the global ledger of the blockchain.In this system,a transaction consists of transaction header,input and output.The specific structure shown in Fig.4 is as follows.
a) Transaction header contains four parameters (Txid,Timestamps,Rental_Period,and Type)
Txid:An identifier used to uniquely identify a particular transaction.Specifically,the SHA256 hash of the transaction.Each transaction can be found via Txid.
Timestamps:The Unix time that the client creates the transaction.If this transaction is recorded in the blockchain,the use time of this address prefix will start from this timestamp.
Rental_Period:The time interval an address prefix is authorized.If Rental_Period is zero,it means that an organization authorizes or assigns a prefix address to another organization or autonomous system.If Rental_Period is nonzero,it means that an organization leases a prefix address to another organization or autonomous system.
Type:The type of a transaction.If Type is zero,it means that the transaction was authorized by one organization to delegate one address prefix to another organization.If Type is non-zero,it means that an organization assigns an address prefix to one of its autonomous systems and the value of Type is AS number.
Each transaction contains one input and multiple outputs.Each transaction input must come from the previous transaction output and each output waits as an unspent transaction output until a later input spends it.So,all transactions are chained together.
b) The input of the transaction is composed of (PreTxid,Index,
PreTxid:The Txid of a previous transaction.Index:The output number of the previous transaction.
The digital signature process is as follows,wheresign(·) is a signature function:
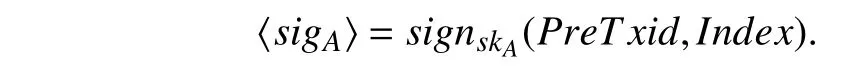
c) The output of the transaction may be one,two,or three
If an address prefix is completely transferred to another organization,the output is only one.If an address prefix only transfers the first half or the second half to another organization,the output is two.If an address prefix only transfers the middle part to another organization,the output is three.For example,an organizationAowns the address prefix[a,b].There are three ways to transfer this address prefix.
Case 1:If organizationAtransfers the address prefix [a,b]to organizationB,the output is {1,[a,b],0,
Case 2:If organizationAtransfers the address prefix [a,c]to organizationB,where a>c>b.The output is {1,[a,c],0,
Case 3:If organizationAtransfers the address prefix [d,e]to organizationB,where a
The transactions recorded in the blockchain indicate that an address prefix has been transferred to another organization or an autonomous system.During the transmission process of address prefix,the global ledger needs to be jointly maintained by the whole nodes and keeps consistent.In other words,each address prefix belongs to a unique organization or autonomous system.Therefore,the proposed input and output transaction structure makes each transaction traceable.Each output of a particular transaction can only be used as an input once in the blockchain.If the value of a transaction’s output exceeds its input,the transaction will be rejected.Fig.5 shows the relationship between transactions.
2) Phase 2: Produce Block
The block production phase is to package legitimate transactions submitted from clients and generate a globally unique block between all block producing nodes through consensus algorithm.The blockchain producing nodes are pivotal to this process.They order each transaction according to the packaging rules and package batches of transactions into blocks.Finally,they generate a unique block through the consensus algorithm and distribute back to all ledger storing nodes and endorsing nodes.
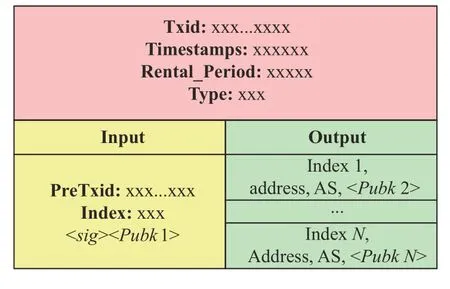
Fig.4.The structure of a transaction.
To start this phase,the block production nodes receives proposed legitimate transactions from many clients in the network.They check the endorsement of each transaction received,arrange these effective transactions into a welldefined sequence and package them into blocks for subsequent distribution.Once a block producing node has generated a block of the desired size,or after a maximum elapsed time,it will initiate a consensus process to generate a unique block for the current period and the block will be sent to all ledger storing nodes and endorsing nodes.These blocks will become the blocks of the blockchain.
We also use the example to explain this phase in detail in Fig.6.
In this example,the client C1 sends a transaction T1 endorsed by endorsement node E1 and E2 to the block production nodes.In parallel,the client C2 and C3 separately send the transaction T2 and T3 to the block production nodes.The block production nodes verify and sort the received transactions and package them into block.A globally unique block B is created by consensus algorithms between nodes.Finally,the transaction order of T1,T2,T3,etc.,is recorded in the blockchain.
3) Phase 3: Verify Block
The block verification phase of the transaction work flow is to check block format and add the verified block to the blockchain.When a new block is generated,all of the peers connected to the block producing nodes will be sent a copy of the new block.Each peer checks the new block independently,but in exactly the same way so that the ledger can be kept consistent.
● Validation rules
When the transaction proposal is sent to the endorsement nodes according to the endorsement policy,each endorsement node then independently verifies the transaction proposal based on defined validation rules and generate a transaction proposal response indicating whether to endorse it.The design of validation rules needs to meet the definition of address prefix resource delegation and assignment.
Definition 1:An organization transfers its address prefix resources to other organizations and the receivers has the right to further delegate the address prefix.
Definition 2:An organization assigns its address prefix resources to its own AS or AS for its service,but the AS can no longer delegate these address prefixes.
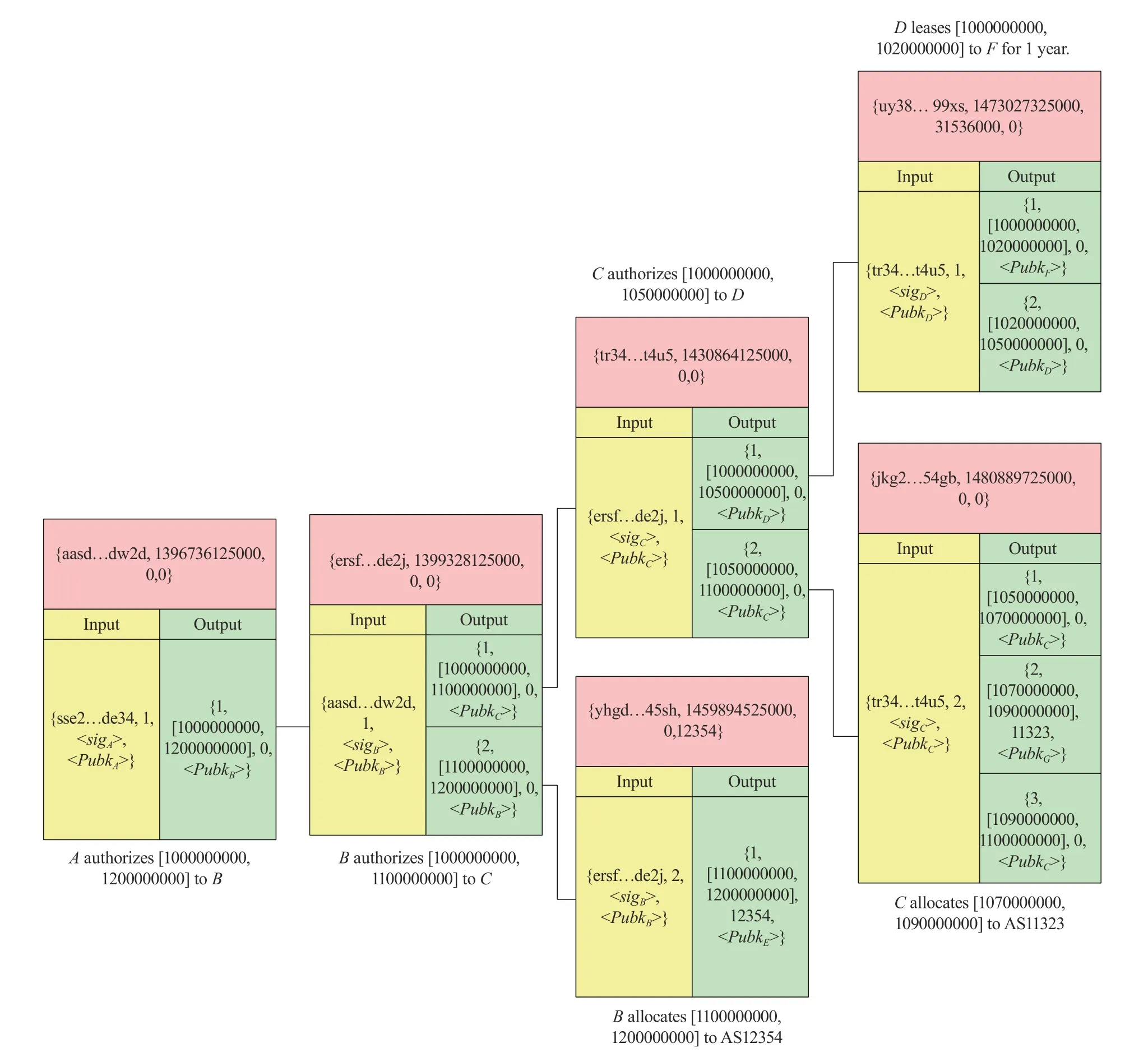
Fig.5.The relationship between transactions.
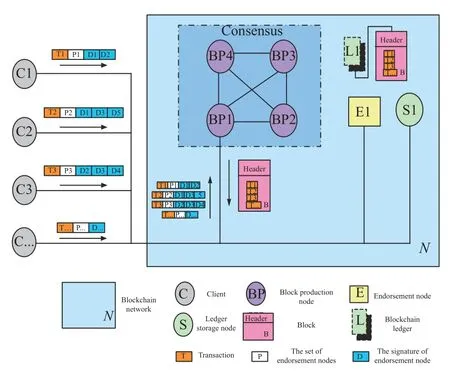
Fig.6.The schematic of Phase 2.
Definition 3:An address prefix cannot be simultaneously transferred to two organizations or ASs.
Definition 4:If an organization does not own this address prefix,the address prefix cannot be transferred to another organization.
Definition 5:If an organization leases an address prefix to another organization,the transaction automatically expires beyond the lease period.
● Packaging rules
The blockchain production nodes order each transaction and package batches of transactions into blocks.They encapsulate the transaction data received over a period of time into a timestamped block and connect it to the current longest main blockchain using the linked list structure.Each block of the DRRS consists of a block header and a block body.The block header contains the version number,the Hash value of the previous block,the current block height,the Merkle root of the current transactions,the timestamp,and the block signature.The block body packs the verified and sorted transactions in the current time period.
III.SECURITY ANALYSIS
In this section,we analyze the security of DRRS-BC in the light of the threat model.The target of the adversaries in our model is prefix or subpre fix hijacking.That means a network operator that has not been authorized to originate a prefix announces in the BGP route massage that the prefix is bound to its own AS number (ASN),and this false route origination is legitimized successfully and accepted by the BGP system.Hackers can achieve prefix hijacking by forging network layer reachability information in BGP update.In the following,we show how DRRS-BC defends against these attacks.
Prefix Hijacking:Prefix hijacking means that an AS advertises an unauthorized prefix.The so-called “unauthorized” means that the prefix belongs to other ASs or the address space of this segment has not been allocated.The allocation of Internet addresses follows the authorization level from IANA to regional Internet registries (RIR) to local Internet registries(LIR).If the AS violates the authorization to announce illegal prefixes,it will directly cause traffic hijacking.In this case,the malicious AS forges the NLRI information in the BGP Update message and advertises an illegal prefix.As shown in Fig.7(a),AS1 is the legal owner of the prefix 16.1.0.0/16,and it advertises the route to this segment of the URL.As shown in Fig.7(b),AS5 maliciously forged NLRI and also advertised the route to 16.1.0.0/16.In this way,according to the principle of BGP selecting the shortest AS_PATH path,AS4 will preferentially select the path from AS5 to 16.1.0.0/16.
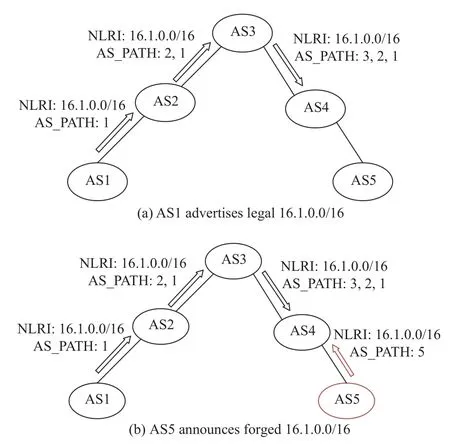
Fig.7.Prefix hijacking.
In a prefix hijacking attack,the adversarial AS5 announces identical BGP prefix that belongs to the victim AS1.Since AS4 has joined DRRS-BC and its local blockchain ledger has been synchronized,16.1.0.0/16 legally declared by AS1 has been recorded in the ledger.In the taxonomy of blockchains,this attack can be considered as double-spending.Therefore,the prefix update information forged by AS5 will be easily identified by DRRS-BC,and AS4 will reject the routing update information sent by AS5.
Subprefix Hijacking:The subprefix hijacking occurs when an attacker announces de-aggregated thus a more specific IP prefix than the actual owner of the prefix.The longest prefix match rule prefers more specific route.In this attack,A announces more specific prefixes than the ones owned by A.As such,this behavior cannot be immediately detected as a double-spent transaction since routing table will not have a prior transaction linked to V that contains prefixes announced by A.In this case,AS1 is the legal owner of the prefix 16.1.0.0/16,and it advertises the route to the segment of the URL.In Fig.8,AS5 maliciously forged NLRI and also advertised the route to 16.1.0.0/20.In this way,according to the longest matching principle of BGP,all other ASs will choose the fake path.
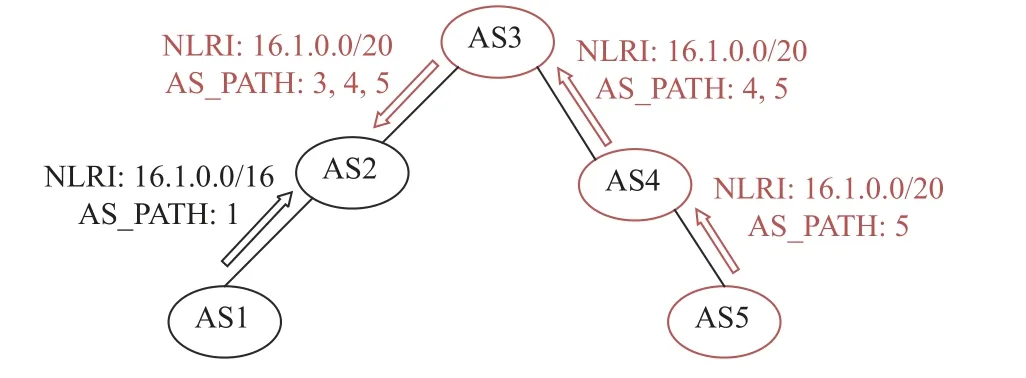
Fig.8.Forged sub-prefixes in NLRI information.
In a subprefix hijacking attack,the adversarial AS5 announces a subset of the BGP prefixes belonging to the victim AS1.The transaction structure of DRRS-BC makes the output of each transaction come from the input of the previous transaction,and the attribution of any sub-prefix can be traced back to its prefix set.Therefore,the proposed input and output transaction structure makes each transaction traceable.Each output of a particular transaction can only be used as an input once in the blockchain.Since AS2,AS3,AS4 all have joined DRRS-BC and their local blockchain ledgers have been synchronized,the prefix update information forged by AS5 will be easily identified by DRRS-BC,and all AS will reject the routing update information sent by AS5.
Because the global network resource allocation is recorded in the blockchain,and all synchronized ledgers maintain the consistency of transactions,all inter-domain routers and any audit program can access it and verify the authenticity of routing information.Therefore,based on historical trustworthiness,autonomous transaction auditing,and explicit resource ownership,DRRS-BC can minimize the ability of authorized institutions to eliminate the risk of configuration errors.
IV.SIMULATION AND RESULTS
The purpose of our system is to store the IP prefix addresses registered by all autonomous systems and to ensure the consistency of ownership of all IP prefix addresses.So we could evaluate DRRS-BC system’s suitability and performance in a real-life scenario.To this end,we deployed the above system in the Alibaba Cloud service and analyzed some performance indicators.We separately evaluated the transaction performance of the system,the scalability of the system,and the impact of block size on the processing efficiency of the system.
For system performance evaluation,we tested the system’s processing time for different quantities of transactions by sending a large number of transactions to the system.Since the construction of each transaction needs to undergo verification of UTXO status,transaction construction,transaction signature,sending transaction,etc.The throughput of the system is closely related to the processing efficiency of the transaction.The experimental results (Fig.9) show that each autonomous system can send 39 transactions per second to the network in the DRRS-BC system.This performance is sufficient for the performance requirements of organizations and autonomous systems for IP prefix registration.

Fig.9.Transaction processing efficiency.
For the evaluation of system scalability,we tested the impact of different numbers of nodes and block sizes on the formation of the final consensus block.In Table I,the increase in the number of nodes leads to a time-consuming increase in the process of final consensus,and the larger the block,the more time-consuming process of the final consensus process.When the number of nodes increases,the communication complexity required for consensus increases.The block size affects the increase in the amount of communication data,so when the network bandwidth is constant,the block size will affect the delay of the consensus process.
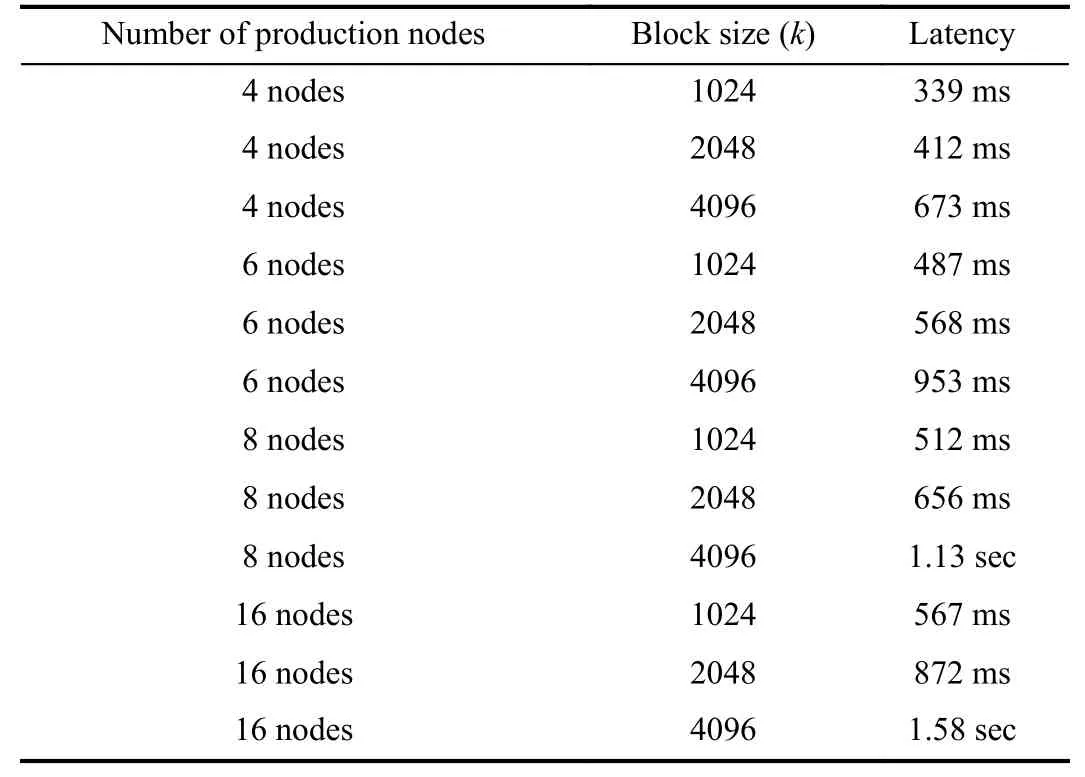
TABLE ISYSTEM SCALABILITY TEST RESULTS
In order to test the impact of block size on the processing efficiency of the system,we fill blocks of different sizes with real transactions.Before the block consensus,each production node will perform various verifications on the transactions in the block,so the size of the block will directly affect the overall operating efficiency of the system.The more transactions that are included in the block in Table II,the greater the processing delay of the block.
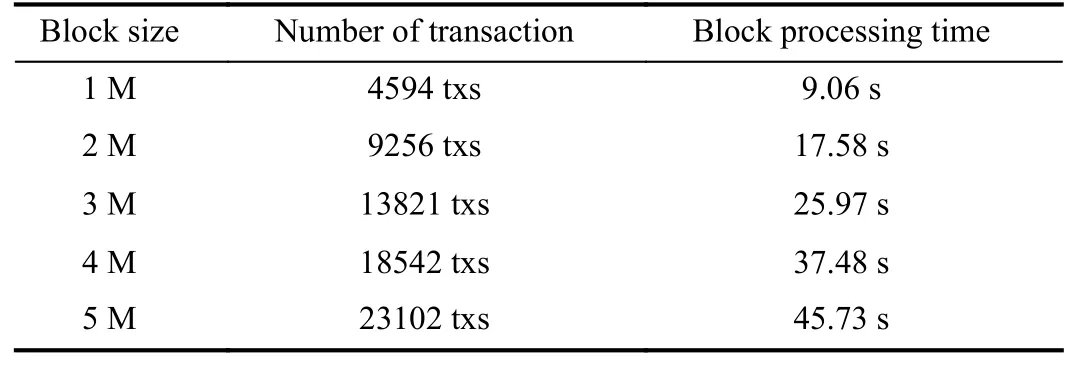
TABLE IISYSTEM OPERATION EFFICIENCY TEST RESULT
In summary,in order to make the DRRS-BC system meet the performance requirements of route registration,we actually set up 16 production nodes and 1 M block size system for deployment.The DRRS-BC is incrementally deployable and backwards compatible with the current operations of ASs.Organizations and autonomous systems can use the DRRS-BC as an additional security feature in parallel with existing routing policies and do not require the AS to switch from the old system to the new protocol paradigm.
V.IMPLEMENTATION AND DEPLOYMENT
The prototype system consists of a set of clients,endorsement nodes,block production nodes and blockchain ledger that perform all typical operations for the Internet resource and a client written in Go to interact with the blockchain nodes deployed in the P2P network.
We collected some real resource delegations (IP addresses and ASNs) from IANA to RIR,RIR to NIR,NIR to ISP and encoded them into the genesis block,and reproduced the IP address prefix and Internet number assignment and registration process in our experiment.Each organization and autonomous system deploys the client and generates the address and corresponding private key of each entity.Each entity can register,lease,assign,and revoke related Internet resources through the client.And we map the resource delegations in the real world to four kinds of transactions,IPregister,IPlease,IPassign,IPrevoke,that the resource delegator sent to the delegate.
VI.CONCLUSIONS
In this work,we proposed the decentralized blockchainbased route registration frame work-DRRS-BC,which can resist to prefix or subprefix hijacking attacks.By applying blockchain,DRRS-BC perfectly solves the problems of identity authentication,behavior authentication as well as the promotion and deployment problem rather than depending on the authentication center.Our future work will study how to combine blockchain with other technologies such as Internet of Things [22],cloud computing,edge computing [23],and sensor network [24]to design a new BGP protocol that is suitable for practical applications.
杂志排行
IEEE/CAA Journal of Automatica Sinica的其它文章
- Blockchain-Assisted Secure Fine-Grained Searchable Encryption for a Cloud-Based Healthcare Cyber-Physical System
- Multi-Candidate Voting Model Based on Blockchain
- Elastic Smart Contracts in Blockchains
- Blockchain-Based Secured IPFS-Enable Event Storage Technique With Authentication Protocol in VANET
- Adaptive Fuzzy Backstepping Tracking Control for Flexible Robotic Manipulator
- An Optimal Control Strategy for Multi-UAVs Target Tracking and Cooperative Competition
