Technological Means and Response Mechanisms for Personal Information Theft
2021-01-07HePeiyuTengXiaoshuoMiaoHua
He Peiyu Teng Xiaoshuo Miao Hua
Abstract: While internet technology has brought great convenience to modern life, it also provides opportunities for criminals. Through information theft methods such as hacking, malware, social attacks, privilege misuse and new technology theft, criminals collect and steal personal information of high value. These illegal acts seriously harm personal information security and lead to various social problems. At present, the problems of the deficiency of personal information protection legal system, unclear definition of related technical concepts, as well as difficulties of investigating criminal responsibility for thieves have caused adverse effects for establishing personal information protection framework in China. This paper analyses the technical means of personal information theft and builds a personal information protection framework. It deems that by refining current laws and regulations, formulating special personal information protection laws, and clearing law supervision and accountability mechanisms for individuals, the risk of personal information theft can be reduced.
Key words: information security; network safety technology; autonomous information protection framework; personal information theft response system; personal information protection law
CLC:D 923 DC:A Article ID:2096?9783(2021)06⁃0138⁃11
1 Introduction
Rapid development of internet technology has brought human beings into the information era. As the cornerstone of this era, information and its value have been realized and excavated by the world. Mastering information assets and making intelligent decisions have become the key to an enterprise's out performance. Some active and influential companies have massive information, such as transaction information, credit information, user behavior information and social information. Companies' behavior covers information collection, information storage, information analysis, information visualization and information security. Companies may have a powerful interactive information mining platform to build the underlying structure of information circulation, collection and sharing to meet different information mining and analysis needs. For instance, giant companies like Amazon and Google have amassed vast amounts of information, which offers them a striking advantage over their competitors by selling advertisements to targeting groups and providing personalized services.
The correct use of big data can bring great convenience to people, but it can also bring technical challenges to information security. Proliferating personal information theft, including social engineering attacks, trojans and spyware, is the driving force of the unprecedented boom of the black network industry chain. The collection and use of personal information in the online society makes it possible for the private space of natural persons to be involuntarily disclosed. The current personal information security network is showing a repeated cycle of "frequent problems ?⁃ regulatory crackdowns ⁃⁃ security stable period ⁃⁃ problems recurring again". The trends of diversification of theft methods, complexity of technology, diversification of behaviors and total information loss have brought a growing destructive threat to personal information safety. For example, with the maturity of artificial intelligence applications, face recognition technology is widely used in various fields of life, which has caused the public to worry about the current situation of personal biological information collection. Due to the coexistence of positive and negative externalities of personal information, it is difficult to accurately measure the overflow results and make correct regulatory choices. Therefore, it is necessary to review the security situation of personal information in the big data era and construct personal information safety mechanisms from aspects of technology, regulation and legislation as well.
The problems between law and technology have become increasingly prominent since the rapid development of technologies. Difficult cases concerning technology position in judiciary have also appeared repeatedly. The law adjusts itself based on different aspects of technological value, reconstructs itself in the collision of technological value and legal value, and solves the problem of imputation principle and regulation construction caused by technology.
The relationship between law and technology is essentially a collision between two kinds of value. The functional value of technology is determined by its objective attributes, and the social value generated by technology is determined by social regulations. But the concept of technology's social value is too broad, which can be interpreted completely different based on different methodology. Nevertheless, law's respondent to technology's social value is different from the conflicting social evaluation, because the law has its own value setting and logic[1].
In recent years, in response to the requirements of the era, China's personal information protection legal system is improving constantly. The Civil Code of the People's Republic of China, the Cyber Security Law of the People's Republic of China, and the Data Security Law of the People's Republic of China have not only completed the construction of the basic system, but also established the basic principles and general rules for the protection of personal information. The Personal Information Protection Law of the People's Republic of China (Draft) systematically integrates past practice experience and achieves a breakthrough system supply, marking that China has entered a new stage of comprehensive protection of personal information. The legal system's designs and arrangements have contributed Chinese wisdom and solutions to the world's personal information protection process. Based on the above?mentioned series of legal systems, we can re⁃examine the security situation of personal information in the era of big data, and build a personal information security protection mechanism from the aspects of technology, legislation, and supervision.
2 Security Situation Analysis of Personal Information Theft in Big Data Era
The technology revolution has radically increased the volume and the processing speed of information. As processing technology can release the potential value of big data, the demand for personal information continues to increase. Current information protection is far from perfect, making some companies or individuals vulnerable to illegal information collection or even information theft.
2.1 The Statistic Analysis of Personal Information Theft in Big Data Era
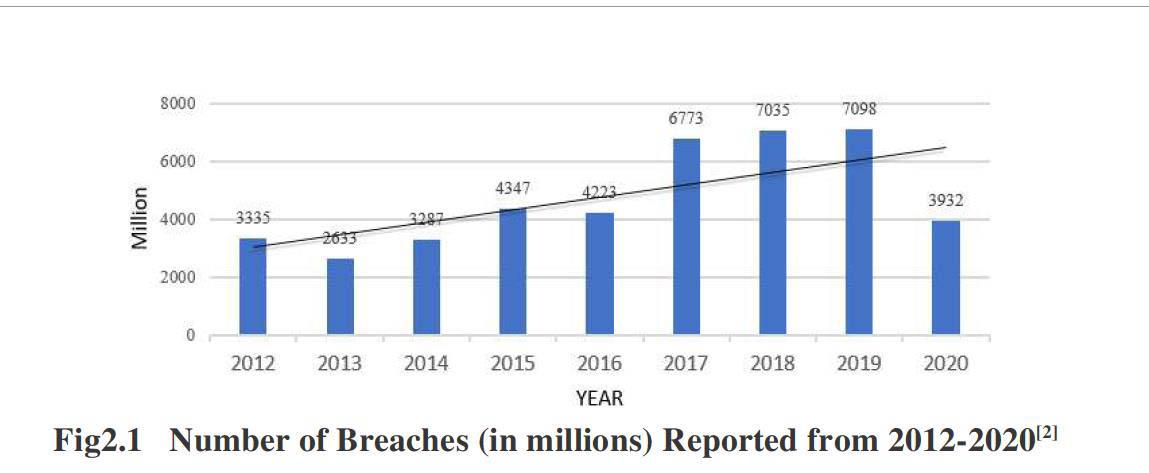
According to Risk Based Security Company, which is "a global leader in vulnerability intelligence, breach information and risk ratings"[2], the overall trend of information breaches is rising. The company aggregated publicly available information about data breaches throughout the world, and its Year End Data Breach Report from 2012 to 2020[3] shows that though the number of breaches have some fluctuations, it has been increased constantly year by year (see Fig2.1).
In 2020, it seems that the number of breaches has decreased (3932 millions) compares to 2019 (7098 millions), however, this trend does not mean fewer breaches are happening. Multiple factors are affecting the number of violations, such as reduced media coverage, no longer targeting personally identifiable information and slow reporting, which together led to a 48% decrease in the number of reported violations.
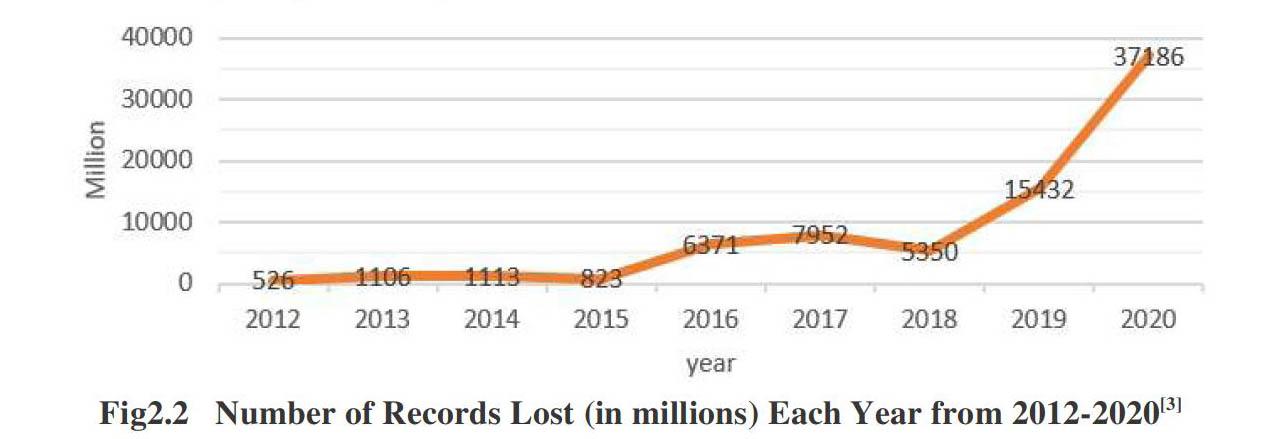
The actual number of records lost exposed in information breach may also be underestimated in the last few years. From 2012 to 2020, the rocket growth of lost records' number means that the world is becoming much tougher for information security (see Fig2.2). In 2020, 37186 million records were lost, which was more than twice the amount of records in 2019. This may be due to the enact and application of various information protection regulations with breach notification requirements worldwide, including the European Union's General Information Protection Regulation (GDPR), New York's Cybersecurity Requirements for Financial Services Companies and Australia's Notifiable Information Breach (NDB) Scheme, etc.
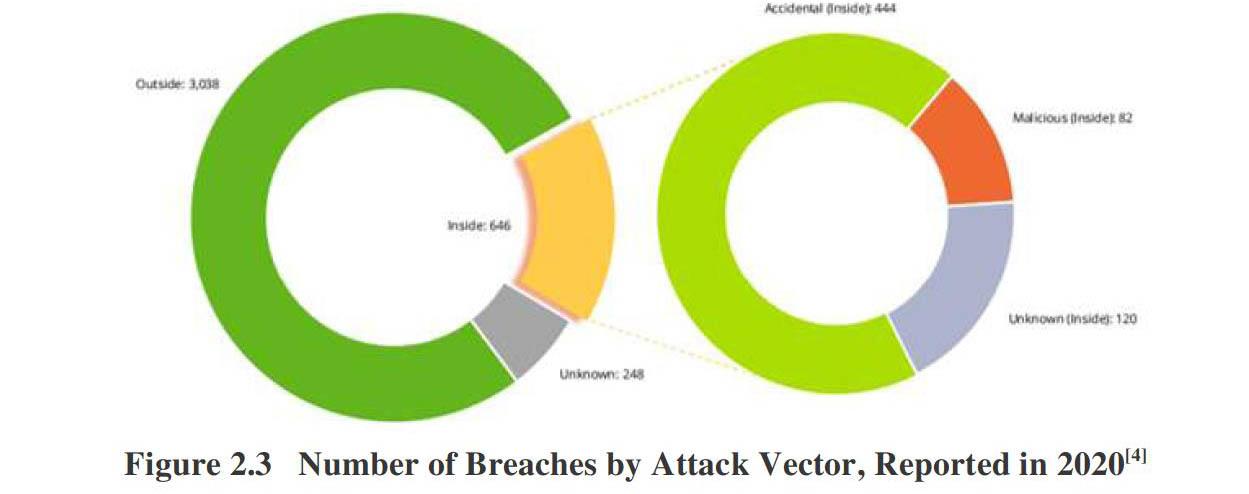
According to Verizon's report, the threat factors which is most likely to cause information breaches in year 2020 are individuals outside the victim organization, accounting for 77% of reported information breaches. In terms of insider threats, 69% of violations can be attributed to employee errors, mistakes or negligence. Of the 82 incidents attributed to malicious insiders, approximately 44% involved the theft of personal information for identity theft or other fraudulent activities. 13.5% of incidents included theft of intellectual property, from proprietary codes to secret designs and formulas[2].
2.2 Types of Personal Information Theft in the Big Data Era
The progress of microelectronics technology, computer technology and communication technology has liberated people from material production. Instead, human beings now have more time and energy to engage in science, art, education and other undertakings, and enjoy the economic and cultural benefits brought by technology progress[5]. However, the ensuing negative effects are becoming harder to ignore, computer crimes and viruses, theft of databases and trade secrets, as well as the infringement of privacy rights are occurring frequently, upgrades of traditional theft methods and up?to⁃date theft technology have posed an alarming threat to personal information protection.
Technology is a powerful tool, but how to use it and whether it can bring happiness or disasters to mankind is entirely up to us. High⁃tech has penetrated into all areas of social production and life, greatly promoting the modernization of social production, and comprehensively improving people's quality of life. However, technology itself is innocent, but technological behavior has an inherent duality. If there is a lack of awareness of its potential hazards timely prevention and guidance, these high⁃tech developments will also bring a series of serious social problems and undermine social stability[4].
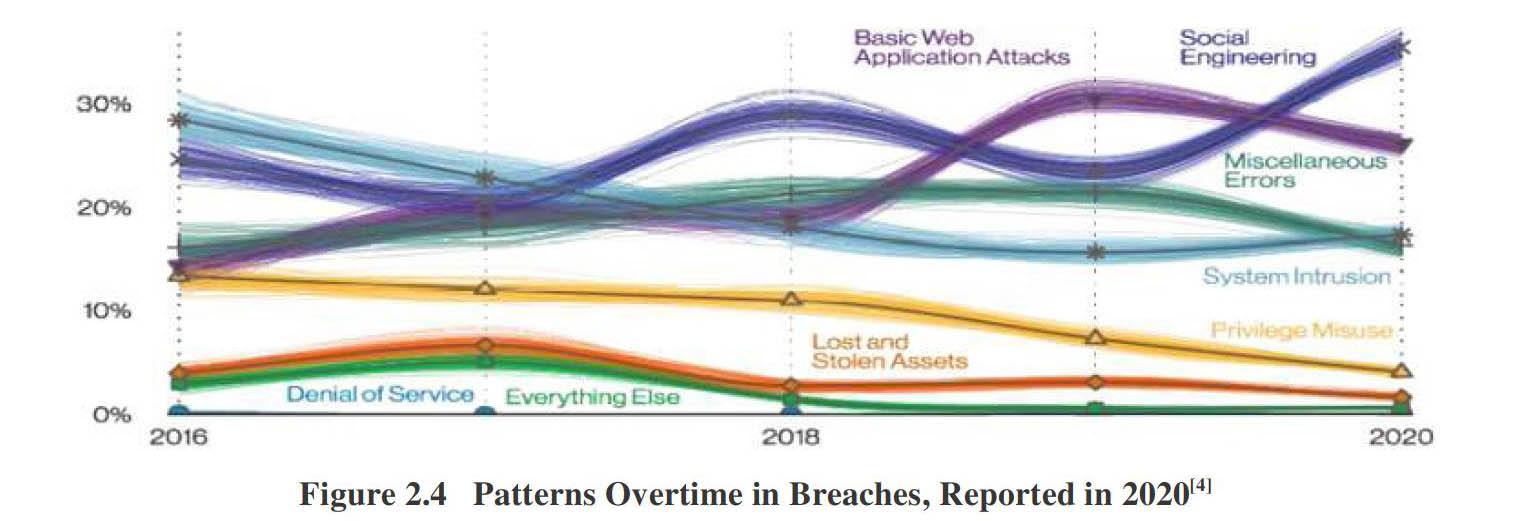
To effectively against cyber security attacks, it is essential to know who is behind the breaches and what are the tactics of adversaries. According to Verizon's 2021 Information Breach Report[3], malicious outsiders are responsible for the biggest percentage of information breach incidents, followed by internal actors. These thefts mainly happened online and can be roughly divided into eight categories, which are social engineering, basic web application attacks, miscellaneous errors, system intrusion, privilege misuse, lost and stolen assets, denial of services and everything else.
·System Intrusion: System intrusion capture uses malicious software and/or hackers to achieve their goals in complex attacks, including the deployment of ransomware. Hacking technology theft refers to the act of directly attacking company systems containing large amounts of information to obtain users' personal information. Due to the limitation of security design, security vulnerabilities, such as misconfiguration of various system services or applications are inevitable, and they are easy to be exploited by hackers. Continuous large?scale attacks can also obtain a large amount of personal information in a short period of time.
·Privilege Misuse: Accidental behavior directly endangers the security attributes of information assets. This does not include lost equipment, which is classified as theft. The hardest type of information breach to detect, involves mishandling information or installing unapproved software or hardware, either maliciously or accidentally, for access control or account abuse. A direct result of privilege misuse is the loss of sensitive information or shutdown of the critical systems or applications. In practice, the public, healthcare, and finance industries are the primary targets among the various victims of these breaches.
·Lost and Stolen Assets: Any loss of information assets, whether due to misplacement or malicious intent. Phishing is the activity of a thief tricking users to input relevant personal information by cloning bank websites and famous e⁃commerce websites, based on the victims' lack of awareness of these websites. Malware theft means that malicious software, mainly Trojans, spyware and ransomware, secretly collect users' personal information. While hacking, accounted for the biggest percentage of information breach incidents, malware theft is also the major cause of information breach incidents. In many cases, impostors often create invented scenarios to steal personal information or influence the behavior of targeted victims.
·Denial of Service Attacks: Designed to compromise the availability of networks and systems, including network and application layer attacks. Many companies tend to put customers' personal information in the public cloud and the information is easy to be stolen due to the poor defense system and little control on it[6]. Besides, increasingly wearable devices can achieve real?time information collection and constant surveillance. Without users' consent, some intelligent equipment may collect personal health information, personal identified information or personal medical information directly into companies' information base for commercial use. This will pose a heavy threat to personal information safety[7]. It must be pointed out that except for the above listed situations, there are also four patterns of breaches which should be paid more attention.
·Social Engineering: A person's psychological compromise, which changes their behavior to take action or violate confidentiality regulations.
·Basic Web Application Attacks: After the initial web application is attacked, it perform a simple web application attack with a few steps/additional operations.
·Miscellaneous Errors: Incidents where unintentional actions directly compromised a security attribute of an information asset. This does not include lost devices, which is grouped with theft instead.
·Everything Else: It covers all events that cannot be included into the above types.
The misuse, abuse, and unethical use of personal information can bring potential or actual social harm to society, cause various social disputes as well. Certain individuals use their technical expertise to improperly gain profits, threatening the public's information safety and personal property. The harm caused by personal information theft must be regulated by corresponding laws, and legal remedies should be given to victims. As for research and development of information achievements, if their application can harm human society and cause irreversible consequences, corresponding legislation should be used to prescribe the scope and nature of the application. Using the normative function of law to suppress the negative impact of information theft behavior on human society, thus to predict and prevent crimes has become the consensus of all countries in the world today[4].
3 Construct a Technical Response System for Personal Information Theft
As personal information continues to be severely threatened, a response system constructed by technology should be established to deal with security issues in the era of big data[8]. Although global spending on information security is increasing and new information protection regulations have been introduced, obviously, there is a gap between defense mechanisms and security effectiveness. Personal information security defense has certain deficiencies in terms of technical support, legal protection and supervision.
The technology to prevent personal information theft is becoming more and more complex. Traditional security solutions focus on network peripheral technologies such as network firewalls, which are not enough in today's big data environment, as personal information is usually distributed outside the organizational boundaries. Since the flow and sharing of information is critical to business success, it ignores the fact that protecting information, instead of boundaries, will be a problem and must be a top priority.
Although encryption is a basic and reliable technology to protect information[9], such security measures are rarely used (no more than 4.2%) in security breaches reported since 2014. Encryption technology provides varying degrees of access to information stored in heterogeneous environments, and at the same time realizes the effective use of personal information.
In recent years, a large number of new technologies have emerged for protecting personal information such as consent/information subject rights management[10?11], anonymity[12⁃13], information minimization[14] and information tracking[15], etc. However, few of them have been put into practice or been widely adopted. There are two reasons for this worrying situation: On the one hand, current economic and regulatory environment hardly motivates companies to adopt new protection technologies. On the other hand, the income of some commercial companies is heavily depending on illegally collecting and processing users' personal information without their affirmative consent. Therefore, these companies have little incentive to deploy such technologies. The availability and trust of these new technologies also pose an obstacle to taking this critical step.
3.1 Introduction of the Autonomy Based Information Protection Framework
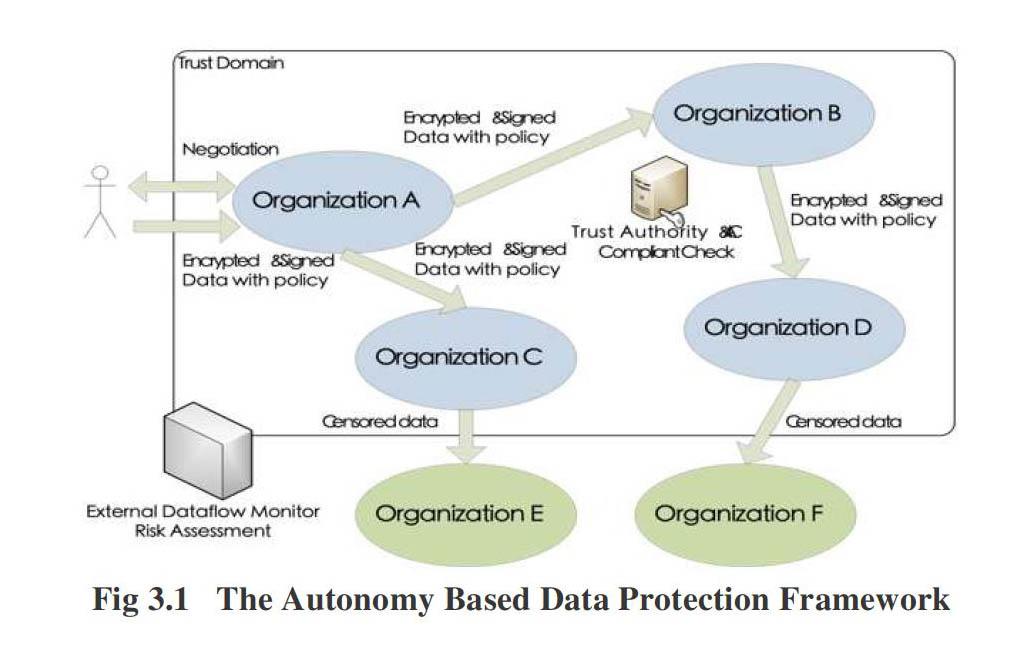
Based on the analysis of use cases and reported security incidents, a high⁃level technical framework has been proposed to protect personal information. The framework below is also deemed as an evolution of prior work described by Whitley and Jordi, and Josep[11⁃12] (see Fig3.1).
In this data protection framework, the user's data is propagated with the user's privacy preferences. Combined with the security policies of the entity, the generated security rules can be enforced in the organization within the trust domain by the security mechanism inherent in the framework. In contrast to prior works[10⁃11], this framework does not heavily rely on the Trust Authority (TA), instead it offers an offline management scheme. The organization in the trust domain is autonomous, which means that the entity can decide how to deal with user's data and what data should be released for specific purpose.
The Trust Authority (TA) sits at the heart of the trust domain acting as administrator and Certificate Authority (CA). The TA performs the compliance check for all organizations in the domain. If all compliance checks are satisfied and all requirements are fulfilled, the TA releases the certificates to the qualified organization. Otherwise, the TA will suspend the certificates of organizations which violate the domain security specification or result in data breaches.
After necessary and successful identity authentication, the customer negotiates with the security entity about the privacy of the user data. When the agreement has been reached, the customer delivers his encrypted and signed data under the protection of the public key of the entity which is obtained from the organization's certificate.
In formula 3.1, the data and the user's preferences are concatenated to form the delivering message (MSG).
In formula 3.2, the user signs the hash of the MSG using his private key and concatenates the signature with delivering message(MSG). Subsequently, the concatenated message is encrypted with a symmetric key K, and the symmetric key K is encrypted with the organization's public key extracted from the organization's certificate. Along with the user's certificate, all of the foregoing messages are sent to the organization, as shown in the formula 3.3:
Only with the paired private key (PRorg) corresponding to valid certificate, the organization can decrypt E(PUorg, K) to get the symmetric key K and subsequently decrypt the MSG_ENC in 3.2 using the key K. After getting the message and signature (MSG||Sig[PRuser,H(MSG)]), the entity can verify the signature using the user's public key extracted from the user's certificate. Obviously, the valid certificate of the organization issued by the TA is the real key point to access the trust domain, with which the TA can fulfill his management responsibilities and ensure the security mechanism of the data protection framework is working properly.
While an organization (e.g. organization B) requests the data within the scope of another (e.g. organization A) in the trust domain, organization A will retrieve the security rules and initiate the similar process mentioned above. Besides the retrieved security rules, organization A could append additional rules with the data according to his security regulation. As illustrated in formula 3.4, organization A may generate a watermarked message by encoding the digital signature S into the delivering message MSG_DELIVER.
For example, every audio file downloaded in Apple's iTunes contains the encoded signature consisting of the real name and apple ID of the user. Thus, the watermarked message could be used to identify and track the source of leaked data.
If the receiving parties (e.g. organization E and F) are not in the trust domain, the request must be strictly assessed and censored according to security policies. The released data should be sanitized and contains no privacy or confidential information. For instance, some sensitive details can be omitted or encrypted and only content consistent with security requirement can be disclosed. The external data flow monitor intercepts and tracks the data flowing through the border of the trust domain. Under the supervision of the external data flow monitor, the risk of information propagation was evaluated and security policies of the trust domain was checked. If appropriate, the external data flow monitor could act as an entrance of audit service.
3.2 Trusted Architecture of an Autonomous Organization
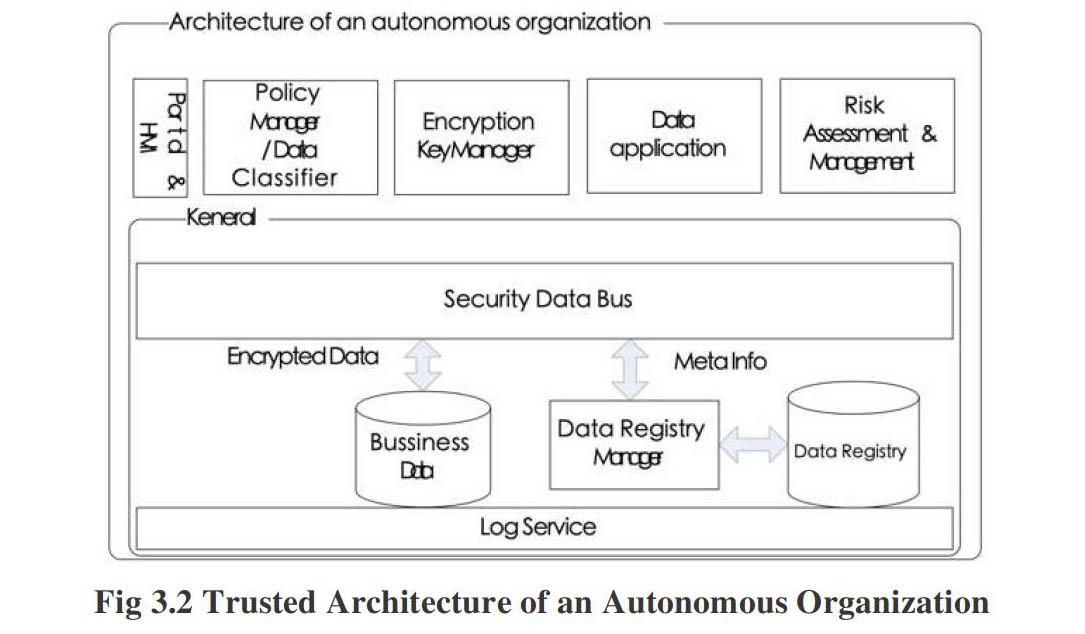
For the autonomous organization in the trust domain, we propose a flexible and component?based architecture to provide a certain degree of trust required by the Trust Authority (TA). The trusted architecture can be customized and deployed consistently with the business processes of the organizations. The components in the architecture can be deployed in the cloud environment or implemented in an overall stand⁃alone infrastructure.
The system implemented with these components provides privacy⁃aware and fine grained access control. Each data in the system is explicitly bound with the data owner and rules which are enforced by different keys generated by the key manager. The security data bus guarantees the security policies by layering and abstraction mechanisms which also enable comprehensive and easier logging and auditing. And the log service records the concerned events and supports the risk assessment/management component to perceive and supervise the situation of the system.
The overall set of functionalities and components of the architecture are illustrated in Fig3.2.
An autonomous organization in a trust domain should include but not limited to the following components:
·Portal & HMI (Human Machine Interface): Besides identity authentication, this component provides human machine interface and interacts/negotiates with the user to reach an agreement about privacy. The interface provides privacy choices and explains the privacy practices involved. After the choices are made, the user's privacy preference (preference in formula 3.1) is generated and the user can send the encrypted and signed data MSG_DELIVER in formula 3.3 with the help of the web plugin. After decrypting and verifying the MSG_DELIVER, this component sends MSG in formula 3.1 to the Policy Manager & Data Classifier component.
·Policy Manager & Data Classifier: Combined with the system security policies of the organization, this component transforms the user's privacy preference into machine⁃readable rules which can be automatically put into effect. This component also classifies the user data into predefined categories according to the generated security rules.
·Encryption Key Manager: To provide necessary granularity of data access, a related encryption key manager is a prerequisite. Based on the user's security rules, the encryption key manager interacts with the policy manager and releases keys for different purposes, which provides the user with flexible and fine⁃grained control over access and usage of his data.
·Data Registry Manager & Data Registry: In order to enforce the security policies of the system, the data registry manager keeps track of the owner of the data, the associated rules/keys and the location the data stored. The data registry manager stores or updates this meta information in the data registry whenever the user data is created or updated.
·Security Data Bus: The introduction of the security data bus in the system architecture embodies the design philosophy of layering and abstraction. The data within the organization can only be accessed through the security data bus in the general layer. When access requests for data are made to the security data bus, it will retrieve all relevant information in the data registry through the data registry manager. Equipped with all necessary information, the security data bus retrieves and decrypts compliance data from the business data repository.
·Log Service: This component intercepts the flows of data within the system and logs what happens in the organization. Furthermore, it acts as the underlying and fundamental service for the risk assessment/management and compliance checks of the TA.
·Risk Assessment & Management: Based on the log service, predefined security policies and known threats, this component performs analysis to help administrators identify security incidents and potential risks. It is the crucial service to fix the gap between security policies and mechanisms.
4 Technical and Legal Responses to Personal Information Theft in Big Data Era
Through the above?mentioned analysis of personal information theft situation worldwide and security prevention mechanism design, it is easy to find that in order to improve personal information protection level in the era of big data, the improvement of relevant legislation, the improvement of supervision mechanism, and the strengthening of technical protection are all in need[15]. The effective way to deal with the potential risks brought by science and technology is to actively avoid and respond to these risks. For the supervision of personal information theft activities, information privacy control strategies such as information privacy standardization and corporate licensing can be adopted, and strict restraint, prohibition and punishment mechanisms for information research, development, transformation, application and promotion processes can also be established to achieve full control of personal information theft risks. Information protection law aims at using civil, administrative, and criminal means comprehensively, which can both promote information technology progress and ensure that technology works for the benefit of mankind.
4.1 Upgrade and Develop Personal Information Security Technologies
Data encryption technology and data anonymity technology are not the final solution to user's privacy, but will be an important link in the final solution, providing technical support to protect the user's data privacy rights. A comprehensive and systematic solution of personal information to user data privacy can effectively prevent all privacy risks that users may face during the storage, transmission, and utilization process.
The new anonymization technology must be able to effectively process large?scale and multiple types of data in a short time, which requires different encryption methods for different types of data, such as k⁃anonymity technology for image data. For text data, that is easy to be recognized and replaced, ontology and dictionary technology are required. The encryption technology allows all access objects to perform a keyword search on encrypted data, which is also applicable for complex searches. As far as encryption technology is concerned, it is necessary to improve the processing capability and data access capability of unstructured data, such as increasing the development of public key searchable encryption, which allows all access objects to encrypt keyword search.
The inherent shortcomings of anonymization technology and encryption technology are difficult to overcome in a short time, so new technical means are needed to achieve full protection of personal information privacy. In recent years, some new technical solutions have been used gradually. For example, the automated security policy enforcement mechanisms can achieve privacy and security requirements for personal information. Trusted computing under this solution uses tamper⁃proof hardware storage. A machine⁃readable strategy is adopted and the data is encrypted twice. The outer encryption layer can only be decrypted by trusted hardware, and the inner encryption layer can only be decrypted by software that meets the policy requirements.
In addition, data provenance technology can prove the source, authenticity, and quality of personal information, which can analyze the leaks of user privacy. The function of data origin technology is to build a mechanism that facilitates the data subject to track the data processing process, even if the personal information has been converted and circulated many times, it can be tracked accurately. In addition, by establishing a time⁃series profile of behaviors, data controllers can use it to strictly monitor employees who may illegally steal user data and prevent insider threats.
4.2 Implement Personal Information Protection Law from Civil Law Perspective
Nowadays, the scope of personal information rights has become much wider, not only beyond the scope of traditional civil rights, but also breaking through the boundary of public and private law[16]. Personal information protection has some unique characters such as cross legal departments, multiple features, as well as integration of public law and private law[17]. According to the pattern of personal information operation, a comprehensive rights protection mechanism must be designed, by connecting different law departments, sanction for infringements, and finally build a complete personal information rights protection system. The Personal Information Protection Law should determine the specific types of personal information protection by enumerating methods, thereby limiting the specific protection scope of personal information and clarifying the specifics of personal information rights.
As a new type of right, personal information right has rich connotations. Personal Information Protection Law of the People's Republic of China (2021) stipulates that natural people have personal information rights. The processing of personal information include collection, retention, use, handling, transmission, provision, disclosure, erasure, etc. of personal information. Processing of personal information shall abide by the principles of legality, good faith, necessity and integrity. It shall not be conducted by means that are fraudulent, misleading, or coercive, etc.
Once personal information cannot be guaranteed, the individual basis of modern society will be severely violated. For example, the cross?border transmission and use of personal information such as genetic information, political preferences, etc., has exceeded the traditional business scope, and may potentially affect the social stability or even national security of the personal information transferred country. In essence, personal information right not only includes spiritual and material rights, but also civil liberties.
In the civil field, the principles of collecting and processing personal information should be extended to the entire civil field. The basic requirements for personal information protection are indispensable, and an individual's right of personal information should be a legal right. For example, people who have disputes about personal information should have the right to view the information. When someone's personal information is improperly processed, he can opt out and request for compensation.
In order to ensure the security of citizens' basic information rights, the administrative supervision and accountability mechanisms for individuals should be clarified. To achieve the integration of power and responsibility, it is also necessary to increase social participation. There are two main models of personal information protection laws in developed countries. One is the loose model of European countries, the other is a centralized model. These two models both have their advantages and disadvantages. The loose model has an expanding group, but it may harm modern administration. For the centralized model, its work efficiency is higher, but it faces the risk of confusion due to the lack of supervision atmosphere and determination[18]. Taking into account the various situations of personal information protection, it is recommended to establish a new type of administrative supervision system that focuses on the State Internet Information Office and the Ministry of Industry and Information Technology, and supplements other regulatory agencies. In this way, the distribution of administrative resources will be more reasonable, and the benefits of the personal information model will be better protected. This can also avoid conflicts of power and games of shirking responsibility.
4.3 Implement Personal Information Protection Law from Criminal Law Perspective
Well protection of personal information can effectively prevent and reduce cybercrimes. Article 253 of the Chinese Criminal Law establishes personal information infringement crime, which not only effectively protects personal information, but also responses to the demands of the information technology era. In the description of personal information infringement, it also pointed out that such crimes violated the Personal Information Protection Law, the Cyber Security Law and other related personal information protection laws and regulations of China.
From the perspective of criminal law, it is necessary to clarify the boundaries of personal information infringement. The criminal law is the last resort for personal information protection, and the protection of personal information by the criminal law depends on the further in?depth study of the laws of other departments. Without a legal source, obtaining a large amount of personal information constitutes a criminal offence. Personal information behaviors can be divided into three steps: information collection, information transmission, and information utilization. In order to avoid the vacancies in criminal laws and regulations and achieve comprehensive protection of personal information, the government can regulate the possible violations of personal information during different process.
In China, the frequency of crimes related to personal information is increasing. The current decentralized laws and regulations can no longer meet people's growing personal information protection needs, and relevant laws should be improved to fully protect the security of personal information. For further legislation, it is necessary to distinguish natural persons and legal person subjects in personal information theft crimes, to classify the status of staff members in the personal information theft crimes, and to expand the subject of natural persons' crimes. The criminal subject should also include staff of non?authority agencies, finance, telecommunications and other legal persons.
4.4 Summary and Suggestions
In practice, the following factors should be considered when handling personal information security cases:
·Ensure the legality of consent rules for personal information collection as well as the limited willingness to use personal information. The consent rules should ensure the legality of personal information collection, and the limited willingness to use it is to ensure the legality of the use of personal information.
·Clarify the security obligations of personal information controllers in case of information theft or leakage. Regarding the security obligations of personal information controllers, the purpose is to prevent data leakage or theft.
·Specify the scope of personal information and clarify the content of personal information rights. The scope of personal information and personal information rights should be clarified.
·Improve personal information protection remedial measures, provide victims with available remedial measures and introduce punitive damages. The personal information protection law should list some typical personal information, limit the scope of personal information protection, and clarify the content of personal information rights. Improve personal information protection remedial measures.
·Consider various factors while making judgments, such as the amount of personal data, subjective maliciousness of information controller, source of information, compensation for damages, etc. The personal information protection law should provide victims with available remedial measures and even introduce punitive damages.
In summary, personal information right has the characteristics of both moral and material rights[19]. The legal reform of personal information regulation must be adjusted and improved in terms of structural plasticity, system compatibility, mechanism flexibility, and timing flexibility, so as to effectively prevent technological risks on the basis of ensuring innovation. In response to the demands of people's information rights protection in this era, it is necessary to expand the horizons to the constitutional level, absorb overseas experience, protect personal information with constitutional rights[20], strengthen the construction of social liability ethics[21], and build a more scientific and complete legal system for personal information protection.
References:
[1] Zheng Yushuang. Solving the Problem of Technological Neutrality⁃Jurisprudence Rethinking the Relationship between Law and Technology[J]. Journal of East China University of Political Science and Law. Issue, 2018(1): 91⁃92.
[2] Risk Based Security. 2021. Homepage[DB/OL]. [2012⁃10⁃20]. <https://www.riskbasedsecurity.com/>.
[3] Risk Based Security. 2020 Year End Report Data Breach QuickView[DB/OL]. [2021⁃06⁃22]. https://pages.riskbasedsecurity.com/en/en/2020⁃yearend⁃data⁃breach⁃quickview⁃report.
[4] Verizon. 2020 Data Breach Investigations Report[DB/OL]. [2021⁃06⁃22]. https://enterprise.verizon.com/resources/?page=1.
[5] Fu Zitang. On the Regulatory Function of Law to Scientific and Technological Behavior in the Era of Knowledge Economy[J]. Studies in Law and Business. Issue, 2000(1): 5.
[6] SEN, J. Security and Privacy Issues in Cloud Computing[J]. International Journal of Grid & Distributed Computing, 2013, 06(55): 238⁃252.
[7] Gao Yutong. Wearable Devices and Personal Information Security[J]. Security Science and Technology, 2015(3): 69⁃71.
[8] Diao Shenxian and Qing qin. International Experiences and Reference of Personal Information's Administrative Protection[J]. Chong Qing Philosophy & Social Science, 2011(5): 68⁃74.
[9] Lv Xin and Han Xiaolu. Technological Architecture Research of Big Data Security and Privacy Protection[J]. Information Security Research, 2016(3): 244⁃250.
[10] Siani Pearson and Marco Casassa Mont. Sticky Policies: An Approach for Managing Privacy Across Multiple Parties[J]. Computer, 2011, 09(44): 60⁃68.
[11] Edgar A.Whitley. Informational Privacy, Consent and the "control" of Personal Data[J]. Information Security Technical Report, 2009, 14(3): 154⁃159.
[12] Joria⁃Comas, J. and Dimingo⁃Ferrer, J. Big Data Privacy: Challenges to Privacy Principles and Models[J]. Data Science & Engineering, 2016(1): 21⁃28.
[13] Wang Pinshui and Wang Jiandong. Overview of Anonymized Privacy Protection Technology Research[J]. Small and Micro Computer System, 2011(2): 248⁃252.
[14] Andreas Pfitzmann and Marit Hansen. A Terminology for Talking about Privacy by Data Minimization: Anonymity, Unlinkability, Undetectability, Unobservability, Pseudonymity, and Identity Management[DB/OL]. [2021?04⁃05]. https://dud.inf.tudresden.de/literatur/Anon_Terminology_v0.34.pdf.
[15] William Enck et al. TaintDroid: An Information⁃Flow Tracking System for Realtime Privacy Monitoring on Smartphones[J]. A⁃CM Transactions on Computer Systems, 2014,06(32): 1⁃29.
[16] Zhou Hanhua. Legal Positioning of Personal Information Protection[J]. Studies in Law and Business, 2021(3), 44⁃56.
[17] Ouyang Benqi. Redefining the Legal Interests in Criminalization of the Infringement of Citizens' Personal Information: A Shift from Private Law Rights to Public Law Rights[J]. Journal of Comparative Law, 2021(3), 55⁃68.
[18] Song Huiyu. Legal Control of Administrative Supervision[J]. Changhai Journal, 2012(3): 86⁃90.
[19] Liu Yanhong. The Legal Interests of the Crime of Infringing Citizens' Personal Information: Confirmation of Personal Legal Interests and New Rights[J]. Criminal Science, 2019(5)19⁃33.
[20] Wang Xixin, Guo Chun. The Constitutional Basis of the Personal Information Protection Legal System[J].Tsinghua University Law Journal, 2021(3), 6⁃24.
[21] Ma Zhiguo, Zhao Shiqiao. The Characteristics and Systematic Optimization of Scientific and Technological Legal Liability[J]. Science Technology and Law, 2021(1): 96?110.
防止个人信息窃取的技术手段与应对机制
何培育 滕小硕 苗华
(1.重庆理工大学 重庆知识产权学院,重庆400054;2.广东外语外贸大学南国商学院 经济学院,广州510545;3.重庆理工大学 计算机科学与工程学院,重庆 400054)
摘 要:互联网技术在给现代生活带来极大便利的同时,也为犯罪分子提供了可乘之机。犯罪分子通过黑客、恶意软件、社会攻击、特权滥用和新技术窃取等信息窃取手段,收集和窃取高价值的个人信息,严重危害个人信息安全,引发各种社会问题。目前,个人信息保护法律体系的不完善,相关技术概念的界定不明确,盗贼刑事责任追究难度大等问题都对我国建立个人信息保护机制造成了不利影响。因此,文章分析了个人信息被窃取的技术手段,构建了个人信息保护框架,认为通过完善现行法律法规,制定个人信息保护专项法律,明确法律监督和问责机制,可以降低个人信息被盗用的风险。
关键词:信息安全; 网络安全技术;自主信息保护框架;个人信息盗窃响应系统;个人信息保护法
