Three-Party Quantum Key Agreement Protocol Based on Continuous Variable Single-Mode Squeezed States∗
2020-01-09YiHuaZhou周艺华JingTan谭晶JingZhang张静WeiMinShi侍伟敏andYuGuangYang杨宇光
Yi-Hua Zhou (周艺华),Jing Tan (谭晶), Jing Zhang (张静),Wei-Min Shi (侍伟敏),and Yu-Guang Yang (杨宇光)
Faculty of Information Technology,Beijing University of Technology,Beijing 100124,China
Beijing Key Laboratory of Trusted Computing,Beijing 100124,China
Abstract The difficulty of quantum key agreement is to realize its security and fairness at the same time.This paper presents a new three-party quantum key agreement protocol based on continuous variable single-mode squeezed state.The three parties participating in the agreement are peer entities,making same contributions to the final key.Any one or two participants of the agreement cannot determine the shared key separately.The security analysis shows that the proposed protocol can resist both external and internal attacks.
Key words: continuous variable,single-mode squeezed states,quantum key agreement
1 Introduction
With the continuous development of quantum computers,the classic key agreement scheme has faced the challenge of security.The quantum cryptography,which is guaranteed by the Heisenberg uncertainty principle and the quantum non-cloning theorem,[1]is attached great importance by scholars at home and abroad.According to different carriers carrying quantum information,it can be divided into discrete variable quantum cryptography and continuous variable quantum cryptography.The discrete variable cryptographic protocol refers to the finite dimensionality of the Hilbert space in which the quantum states used for encoding are distributed throughout the key distribution process.The continuous variable cryptographic protocol means that the Hilbert space in which the quantum states used for encoding are infinitely dimensional,and the carrier of the information is the regular component of the optical field.Through research,it is found that there are some shortcomings in the quantum key agreement protocol based on discrete variables.For example,the ideal single photon source is difficult to prepare,the detector efficiency is low,and it is easy to be interfered in channel transmission.In the continuous variable protocol,the quantum state is simple to prepare,has strong immunity to noise,and has high detection efficiency,which can make up for the deficiency of the discrete variable protocol.
In recent years,quantum key distribution protocols based on continuous variables and quantum key agreement protocol based on discrete variables have made great progress both theoretically and experimentally,and gradually began to move toward practical use.In 2010,Chong and Hwang[2]proposed the QKA scheme using the BB84 protocol,and the shared key was established with the technique of unitary operation and the delay measurement.
In 2011,Zhanget al.[3−4]designed a quantum cryptographic protocol based on continuous variables to realize the secret sharing between multiple parties and multiple parties,and analyzed it with information theory to prove its security.In 2013,Yinet al.[5]proposed a three-party quantum key agreement of two-particle entangled states on an ideal quantum channel.In 2014,Xuet al.[6]proposed a new multi-party quantum key agreement protocol based on GHZ states,and the protocol can be extended to multiple parties.Liet al.[7]proposed a continuous variable measurement device-independent quantum key distribution,which is measured by an untrusted third party,which protects the detector side channel and improves quantum efficiency.In 2017,Zhouet al.[8−9]proposed a quantum dialogue protocol based on continuous variable two-mode squeezed vacuum state and GHZ state,and the quantum dialogue efficiency was significantly improved.In the same year,Gu Junet al.[10]pointed out that Xu’s agreement had participants attacking and did not meet the fairness requirement,so an improved plan was proposed.In 2018,Gonget al.[11]proposed a quantum network dialog protocol based on the continuous variable GHZ states,which allows multiple communicating parties to conduct network conversations; They also propose a quantum network dialog protocol based on continuous variable single-mode squeezed states,[12]which is easier to implement than discrete variable quantum dialog protocols.So far,the multi-party quantum key agreement protocol based on continuous variables has not received extensive attention and lacks corresponding experimental results.Therefore,the design and analysis of multi-party quantum key agreement protocol for studying continuous variables has very important significance both theoretical and practical.
In this paper,the three-party quantum key agreement protocol based on continuous variable single-mode squeezed state is proposed.It is not only suitable for three parties,but also for multi-party quantum key negotiation.The remaining parts of the paper are arranged as follows: the second part introduces the single-mode squeezed state; the third part details the proposed protocol; the fourth part analyzes the security of the proposed protocol;the fifth part summarizes the proposed protocol.
2 Preliminaries
In quantum optics,a squeezed beam can be expressed as[13]
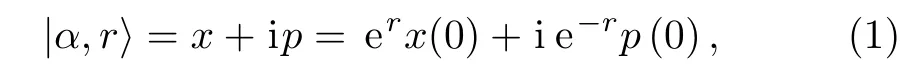
whererrepresents the compression factor,and if the compression factorris negative,it means that the amplitude of the beam is squeezed;ifris positive,it means the phase of the beam is squeezed.When an orthogonal component is infinitely squeezed,the compressed state becomes a straight line,which can be accurately measured,and the other component will diverge exponentially and become uncertain.[14]Amplitudex(0)and phasep0)obey the following distributionx(0)∼N(0,1/4),p(0)∼N(0,1/4),[x(0),p0)]= i/2,

The relationship between amplitude and phase satisfies the Heisenberg uncertainty theorem.The single mode squeezed state can be prepared by degenerate optical parametric amplification (DOPA) of two beams.[15]

The real and imaginary parts of the single-mode squeezed state can be expressed as
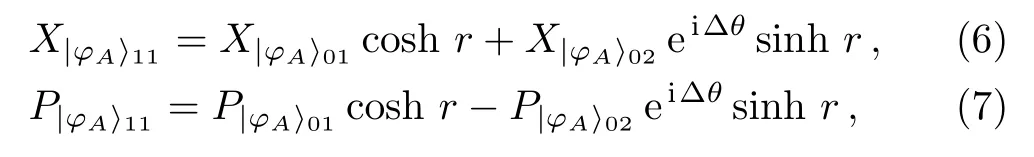
3 Design of Quantum Key Agreement Protocol Based on Continuous Variable Single Mode Squeezed State
3.1 Three-Party Quantum Key Agreement Protocol
The three-party quantum key agreement protocol model based on continuous variable single-mode squeezed states is shown in Fig.1.
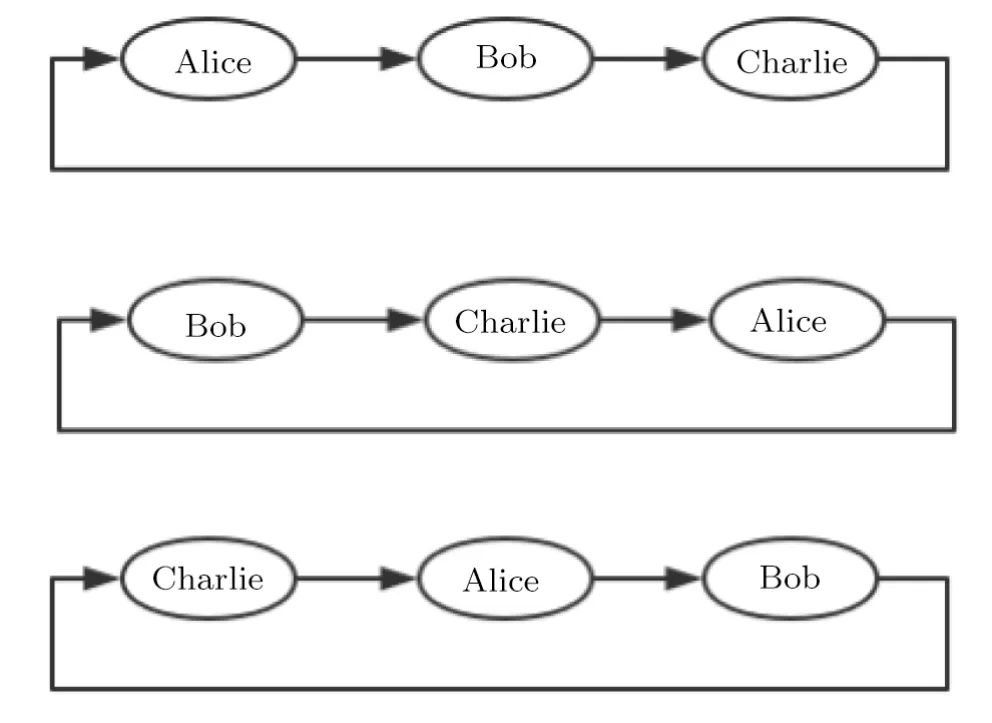
Fig.1 Detailed diagram of three-party QKA.
When Alice,Bob,and Charlie want to perform quantum key agreement,the three parties select the compression coefficients that are both positive or negative and operate at the same time.The specific steps are as follows.
S1Alice’s Operation
(i) Alice performs degenerate parametric amplification on the vacuum quantum statesto obtain single-mode squeezed stateAlice randomly selects the time slott1to perform balanced homodyne detection on the amplitude or phase of the quantum state according to the value ofr.Ifr >0,the quadrature phase component is measured; ifr <0,the quadrature amplitude component is measured.And have a record of the result.Alice selects the random variablesxAandpAand time slott2to perform a translation operationDA(aA=xA+ipA)onto generatewherexAandpAobey the Gaussian distributionXA∼N(0,NxAV0)andPA∼N(0,NpAV0) respectively.V0is the noise variance of the vacuum state,which is used as the unit of signal variance and noise.Alice selects a random translation operation at time slott3to perform a decoy operationDQA1(aQA1=xQA1+ipQA1) onto generateAlice sendsto Bob[16]through the quantum channel.
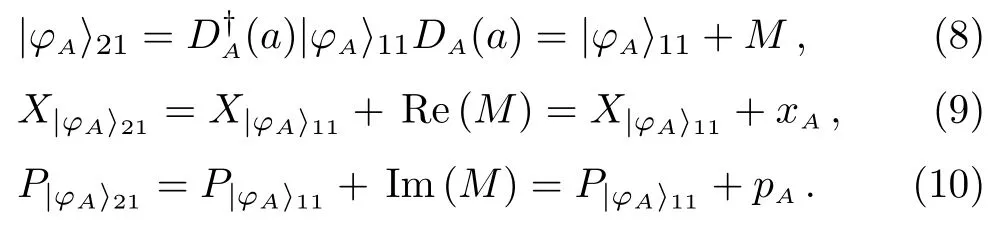
After Bob tells Alice to receive,Alice announces the decoy time slott3.Bob measures the amplitude or phase ofat time slott3and publishes the measurement results.Alice can determine whether there is eavesdropping on the channel based on the measurement published by Bob.If there is eavesdropping,the communication will be abandoned,otherwise the deception operationDQA1will be announced.
(ii) Bob removes the decoy information at time slott3to get.Bob selects random variablesxBandpBat time slott2to perform a translation operationDB(aB=xB+ ipB) to generate.Bob selects a random translation operation at time slott4to perform a decoy operationDQB1(aQB1=xQB1+ ipQB1) onto generate.Bob sendsto Charlie via the quantum channel.After Charlie informs Bob thathas been received,Bob announces that the decoy time slott4.Charlie measures the amplitude or phase ofat time slott4and announces the measurement results.Bob can determine whether there is eavesdropping on the channel based on the measurements published by Charlie.If there is eavesdropping,the communication is abandoned,otherwise the deception operationDQB1is announced.
(iii) Charlie removes the decoy information in time slott4and obtains.Charlie selects random variablesxCandpCin time slott2to perform a translation operationDC(aC=xC+ipC)on|φA〉41to generate.Charlie selects a random translation operation at time slott5to perform a decoy operationDQC1(aQC1=xQC1+ipQC1)onto generate.Charlie sendsto Alice via the quantum channel.After Alice informs Charlie that she has received,Charlie announced the deception time slott5.Alice measures the amplitude or phase ofat time slott5and announces the measurement.Charlie can determine whether there is eavesdropping on the channel based on the measurements published by Alice.If there is eavesdropping,the communication will be abandoned,otherwise the deception operationDQC1will be announced.
(iv) Alice removes the decoy information at time slott5to get.Alice selects the same measurement component at time slott2to perform balanced homodyne detection on the quantum state.The measurement result is
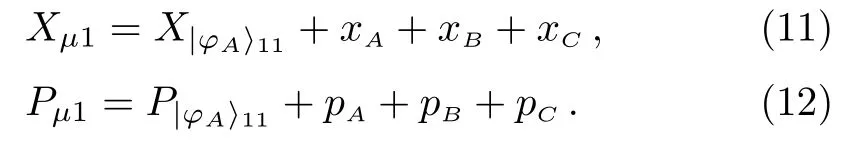
According to the measurement result ofand the formula (11),(12),Alice can deduce
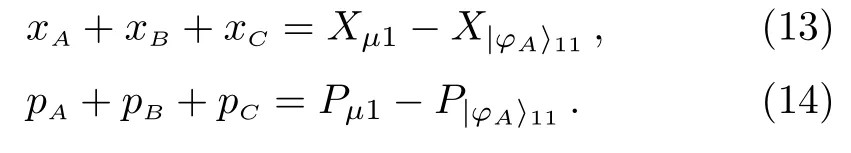
S2Bob’s Operation
(i) Bob performs degenerate parametric amplification on the vacuum quantum statesandto obtain single-mode squeezed state.Bob randomly selects the time slott1to perform balanced homodyne detection on the amplitude or phase of the quantum state according to the value ofr.Bob records measurement result.Bob selects the random variablesxBandpBat time slott2to perform a translation operationDBonto generate,wherexBandpBobey the Gaussian distributionXB∼N(0,NxBV0) andPB∼N(0,NpBV0) respectively.Bob selects a random translation operation at time slott3to perform a decoy operationDQB2(aQB2=xQB2+ipQB2)onto generate.Bob sendsto Charlie through the quantum channel.
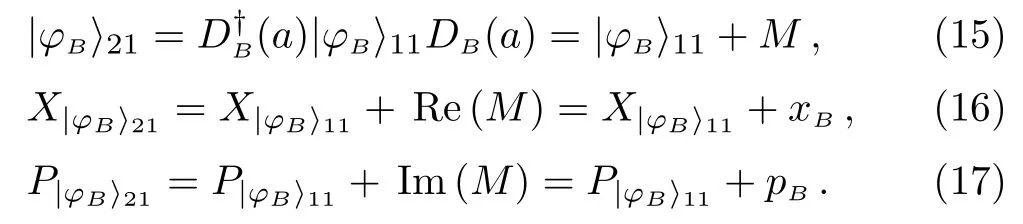
After Charlie tells Bob to receive,Bob announces the decoy time slott3.Charlie measures the amplitude or phase ofat time slott3and publishes the measurement results.Bob can determine whether there is eavesdropping on the channel based on the measurement published by Charlie.If there is eavesdropping,the communication will be abandoned,otherwise the deception operationDQB2will be announced.
(ii) Charlie removes the decoy information at time slott3to get.Charlie selects random variablesxCandpCat time slott2to perform a translation operationDCto generate.Charlie selects a random translation operation at time slott4to perform a decoy operationDQC2(aQC2=xQC2+ ipQC2) onto generate.Charlie sendsto Alice via the quantum channel.After Alice informs Charlie thathas been received,Charlie announces that the decoy time slott4.Alice measures the amplitude or phase ofat time slott4and announces the measurement results.Charlie can determine whether there is eavesdropping on the channel based on the measurements published by Alice.If there is eavesdropping,the communication is abandoned,otherwise the deception operationDQC2is announced.
(iii) Alice removes the decoy information in time slott4and obtains.Alice selects random variablesxAandpAin time slott2to perform a translation operationDAonto generate.Alice selects a random translation operation at time slott5to perform a decoy operationDQA2(aQA2=xQA2+ipQA2) onto generate.Alice sendsto Bob via the quantum channel.After Bob informs Alice that she has received,Alice announced the deception time slott5.Bob measures the amplitude or phase ofat time slott5and announces the measurement.Alice can determine whether there is eavesdropping on the channel based on the measurements published by Alice.If there is eavesdropping,the communication will be abandoned,otherwise the deception operationDQA2will be announced.
(iv) Bob removes the decoy information at time slott5to get.Bob selects the same measurement component at time slott2to perform balanced homodyne detection on the quantum state.The measurement result is
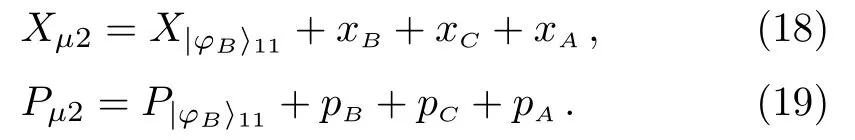
According to the measurement result ofand the formula (18)(19),Bob can deduce
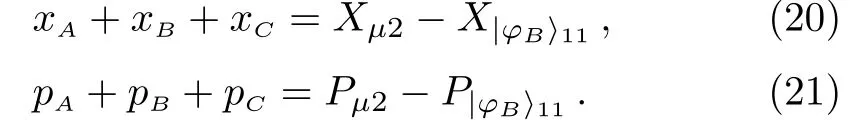
S3Charlie’s Operation
(i) Charlie performs degenerate parametric amplification on the vacuum quantum statesandto obtain single-mode squeezed state.Charlie randomly selects the time slott1to perform balanced homodyne detection on the amplitude or phase of the quantum state according to the value ofr.Charlie records measurement result.Charlie selects the random variablesxCandpCat time slott2to perform a translation operationDConto generate,wherexCandpCobey the Gaussian distributionXC∼N(0,NxCV0) andPC∼N(0,NpCV0) respectively.Charlie selects a random translation operation at time slott3to perform a decoy operationDQC3(aQC3=xQC3+ipQC3) onto generateCharlie sendsto Alice through the quantum channel.

After Alice tells Charlie to receive,Charlie announces the decoy time slott3.Alice measures the amplitude or phase ofat time slott3and publishes the measurement results.Charlie can determine whether there is eavesdropping on the channel based on the measurement published by Alice.If there is eavesdropping,the communication will be abandoned,otherwise the deception operationDQC3will be announced.
(ii) Alice removes the decoy information at time slott3to get.Alice selects random variablesxAandpAat time slott2to perform a translation operationDAto generate.Alice selects a random translation operation at time slott4to perform a decoy operationDQA3(aQA3=xQA3+ipQA3) onto generate.Alice sendsto Bob via the quantum channel.After Bob informs Alice thathas been received,Alice announces that the decoy time slott4.Bob measures the amplitude or phase ofat time slott4and announces the measurement results.Alice can determine whether there is eavesdropping on the channel based on the measurements published by Bob.If there is eavesdropping,the communication is abandoned,otherwise the deception operationDQA3is announced.
(iii) Bob removes the decoy information in time slott4and obtains.Bob selects random variablesxBandpBin time slott2to perform a translation operationDBonto generate.Bob selects a random translation operation at time slott5to perform a decoy operationDQB3(aQB3=xQB3+ipQB3)onto generate.Bob sendsto Charlie via the quantum channel.After Charlie informs Bob that she has receivedBob announced the deception time slott5.Charlie measures the amplitude or phase ofat time slott5and announces the measurement.Bob can determine whether there is eavesdropping on the channel based on the measurements published by Charlie.If there is eavesdropping,the communication will be abandoned,otherwise the deception operationDQB3will be announced.
(iv) Charlie removes the decoy information at time slott5to get.Charlie selects the same measurement component at time slott2to perform balanced homodyne detection on the quantum state.The measurement result is
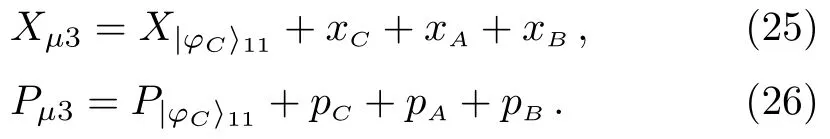
According to the measurement result ofand the formula (25) and (26),Charlie can deduce

S4Alice,Bob,and Charlie simultaneously publish a part of the secret informationxA+xB+xCorpA+pB+pCafter the quantum state is removed as the test key.If the test keys published by the three parties are the same,then the remainingxA+xB+xCorpA+pB+pCis used as the shared key.
3.2 Multi-Party Quantum Key Agreement Protocol
This protocol extends the three-party quantum key agreement protocol to the multi-party quantum key agreement protocol based on continuous variable single-mode squeezed states.Assume that the n-party of the participation agreement is A1,A2,...,An.Axis one of the participants.
Step 1A1prepares single-mode squeezed state,randomly select time slott1for balanced homodyne detection and record the measurement results.A1selects time slott2to perform a translation operation on the quantum state to encrypt its own information,and selects time slott3to perform a decoy operation on the quantum state.A1then sends the quantum state to A2via the quantum channel.After receiving the quantum state,A1determines whether there is eavesdropping based on the A2measurement result.If there is no eavesdropping,A2continues to select the time slott2to encrypt the information,performs the spoofing operation and then sends the quantum state to A3.Each remaining participant performs the same operation as A2until then-th participant Ancompletes the operation and sends the quantum state to A1.A1measures the received quantum state at the time slott2,and compares with the measurement result of the time slott1to obtain the sum of the n-party encrypted informationxA+xB+xCorpA+pB+pC.
Step 2Similar to step 1,theNparties participating in the protocol perform the same operation as A1at the same time,that is,Axprepares a single-mode squeezed state,randomly selects time slott1for balanced homodyne detection,and records the measurement result.Axperforms a translation operation on the quantum state at time slott2to encrypt its own information and performs a decoy operation on the quantum state at time slottx+2.Axthen sends the quantum state to Ax+1through the quantum channel.After receiving the quantum state,Ax+1measures the quantum state of thetx+2time slot to determine whether there is eavesdropping.If there is no eavesdropping,it continues to perform the translation operation of the quantum state in time slott2to encrypt its own information and performs a spoofing operation to prevent eavesdropping attacks.After the operation,the quantum state is sent to the next party until it is transmitted back to the sender of the quantum state.Since the information encrypted by the round participants in thet2time slot is the same,each participant obtains the sum of the encrypted information of the n-party after the n-round operation.
Step 3A1,A2,...,Ansimultaneously announces the secret informationxA+xB+xCorpA+pB+pCafter partial elimination of the three-party quantum state as the test key.If the test keys published by the n-party are the same,then the remainingxA+xB+xCorpA+pB+pCis taken as the shared key of the N-party.
4 Security Analyses
Security analysis is a crucial factor for quantum key agreement protocols.In theory,attacker Eve can attack the protocol through any kind of attack.In the analysis below,we usually list the attack mode used by the attacker and then analyze the security of the protocol in various attack modes.
4.1 Individual Attacks
Participants will pretend to be senders or receivers involved in the communication process to complete the manin-the-middle attack.However,the legitimate communication party can detect the eavesdropper Eve by performing quantum channel eavesdropping detection.Any party involved in the negotiation will terminate the communication as soon as it finds that there is a wiretapping attack.Suppose Eve plays the role of one of the communicating parties Bob and is not detected in the eavesdropping detection.The encoding in the amplitude direction will be described as an example.
(i) If Eve encrypts different information in three encoding operations,it also performs decoy operations.After three rounds of communication,participants can negotiate the following key
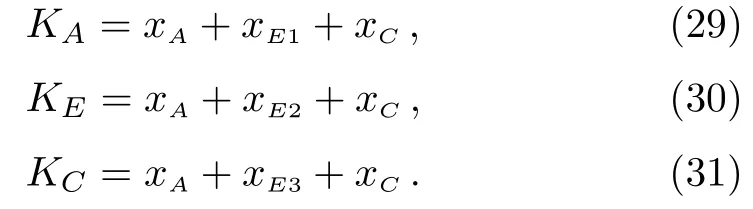
In step S4 of the tripartite protocol,if the above key is selected as the test key,the key is detected to be different and discarded.If the test key is not selected so that the key cannot be detected to be different,Eve cannot independently determine the key in the final keyK.
(ii) If Eve encrypts the same information in three encoding operations,the participants negotiate the key after three rounds of communication.

It can also be seen that Eve cannot determine the key independently.At this time,the keys obtained by the participating parties of the agreement are the same,so Eve is not considered to be an attacker.Therefore,the protocol can defend against individual attacks and ensure that information is not eavesdropped.
4.2 Collusion Attacks
Suppose Bob and Charlie conduct a collusion attack that was not detected in the eavesdropping test.After Bob receives the quantum state after Alice encryption,he can only measure the quantum state after adding the translation operation and cannot directly get Alice’s secret information.Moreover,the quantum state collapses as soon as it is measured.Eventually Alice discovered the existence of the eavesdropper.Assuming the encoded secret informationxB′sent by Bob,Charlie encodes the secret informationxC′.After three rounds of communication,the participants negotiate
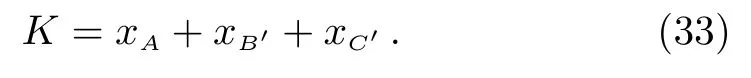
It can be seen that Bob and Charlie can not conspire to decide the key.Therefore,the agreement can resist collusion attacks and ensure that information is not eavesdropped.
4.3 Intercepting Resend Attacks
Intercepting retransmission attacks refers to the attacker Eve intercepting the quantum state in the channel,re-manufacturing a suitable quantum state according to the information of the measured measurement results and sending it to the next party.[15]However,the quantum non-cloning theorem states that the process of completely identical replication of any unknown quantum state in quantum mechanics is not achievable.Each participant performs a spoofing operation after encoding its own information in the quantum state.Although Eve intercepts the quantum state,the next party receives the quantum state sent by the eavesdropper and measures the amplitude or phase to find the eavesdropper’s existence and interrupt the communication.The deceptive information will not be published,so Eve cannot recover the secret information.Therefore,the protocol can resist interception retransmission attacks and ensure that information is not eavesdropped.
4.4 Beam Splitting Attack
The schematic diagram of beam splitting attack is shown in Fig.2.Taking the communication between Alice and Bob as an example,the security situation in the case ofr <0 is discussed.Whenr >0,the situation is similar.Let the channel transmission efficiency beη,the channel loss is caused by eavesdropping or the attenuation of the channel itself.The additive vacuum noise at Alice end isχ0=(1−η)/η,and the total additional noiseχ=χ0+ε.The signal sent by Alice is attenuated by 1−ηon theXcomponent,and the total signal variance on theXcomponent of the signal arriving at Bob is[14]

The total noise includes additional noise and channel additive vacuum noise.The total noise variance on theXcomponent of the signal arriving at Bob is
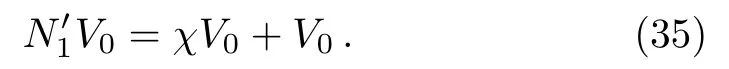
According to Shannon Information Theory,the mutual information between Alice and Bob is
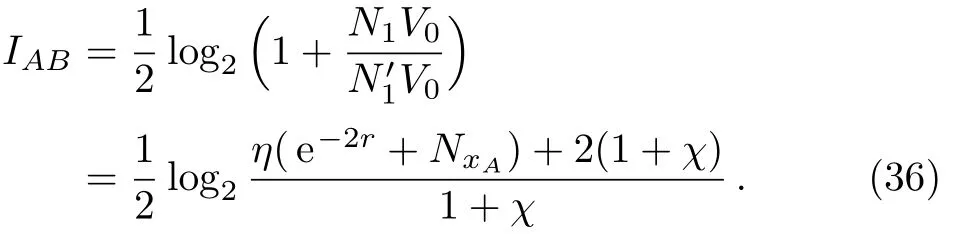
When the channel attenuationη <1,the best attack mode for the eavesdropper is to intercept only a part of the signal,and at most steal the 1−ηof the beam,so that the remaining part of the signal is transmitted to Bob without interference.The existence of an eavesdropper can be undetected.[17]
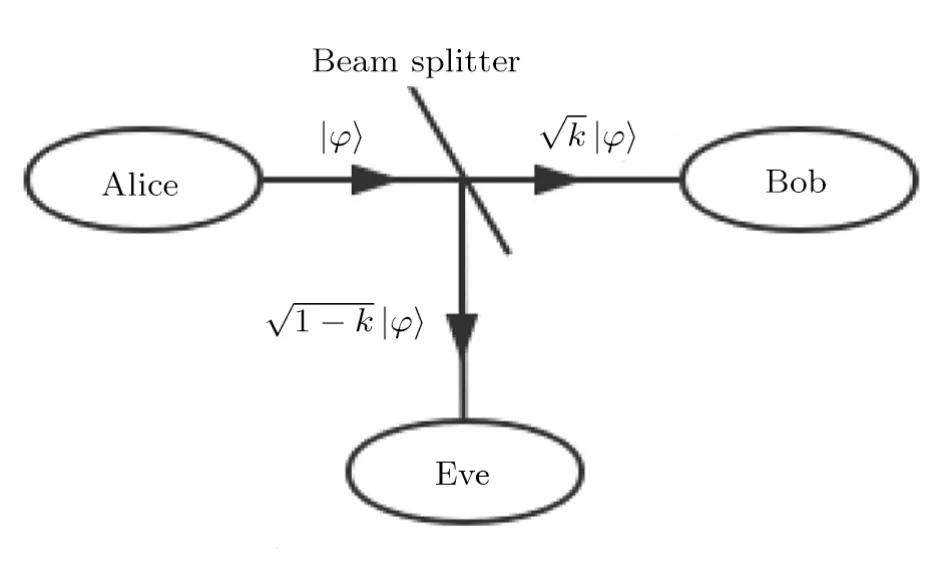
Fig.2 Schematic diagram of beam splitting attack.
Eve sets the splitter’s splitting ratioktoηto achieve a higher attack effect,while replacing the Eve to Bob channel with a non-attenuating channel.[18]The extra noise of Eve isχ−1,and the signal variance that he can steal is
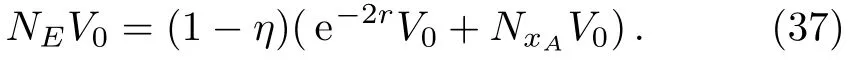
The noise variance is
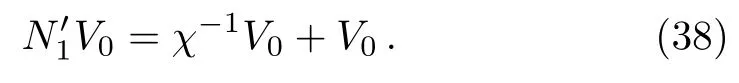
The secret information Eve can get is
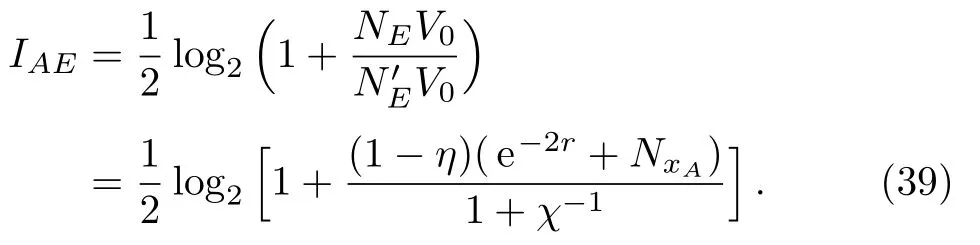
After the two parties communicated through negotiation and confidentiality,the maximum amount of information that can be consistent with each other is

For a given parameterr,a security key can be obtained as long asη,ε,andNxAsatisfy certain conditions to ensure∆I >0.
4.5 Trojan Horse Attack
Trojan horse attacks can be caused by defects in the system structure.The attacker gains information by using the Trojan horse hidden in the system to destroy the system.Yuet al.[19]pointed out that because any optical component in the system has reflected light,an attacker can obtain information by analyzing the reflected light of a modulation component (such as a phase modulator or a polarization modulator),thereby obtaining a secret by using a simple interception retransmission attack.Gisinet al.[20]pointed out how eavesdroppers in the QKD system obtain information about shared keys with Trojan horse attacks.The multiparty QKA protocol proposed in this paper may have Trojan horse attacks because the particles are transmitted multiple times in the channel.If each participant installs a wavelength quantum filter and a photon number splitter,the protocol can be guaranteed to resist Trojan horse attacks.[21−22]Among them,the wavelength quantum filter can filter invisible photons,[23]and the photon number splitter can find delayed photons.PNS is usually replaced by photon beam splitter(PBS:50/50)due to the limitations of existing technologies.
5 Summary
This paper designs and analyzes a three-party quantum key agreement protocol based on continuous variable single-mode squeezed states.The shared key is obtained by each party by measuring and comparing the remaining three-party secret coded quantum states and original quantum states.The security of the protocol is guaranteed by a random spoofing translation operation.Security analysis shows that the protocol is resistant to internal participant attacks and external eavesdropper attacks.The single-mode squeezed states used in the scheme is simple to make.The parties to the agreement are simultaneously implemented,with high efficiency and high feasibility.In addition,the protocol can be extended to the n-party for key negotiation,which has practical significance for the development and application of quantum key agreement.
猜你喜欢
杂志排行
Communications in Theoretical Physics的其它文章
- The Effects of Wettability on Primary Vortex and Secondary Flow in Three-Dimensional Rotating Fluid∗
- Periodic Orbits Around Kerr Sen Black Holes∗
- Relativistic Self-Focusing of Hermite-cosh-Gaussian Laser Beam in Magnetoplasma with Exponential Plasma Density Ramp
- An Improved Heterogeneous Mean-Field Theory for the Ising Model on Complex Networks∗
- Parameterized Post-Post-Newtonian Light Propagation in the Field of One Spherically-Symmetric Body∗
- An Optimal Analysis for 3D Flow of Prandtl Nanofluid with Convectively Heated Surface
