Security Enhanced Anonymous User Authenticated Key Agreement Scheme Using Smart Card
2018-04-08JaewookJungDonghoonLeeHakjunLeeandDonghoWon
Jaewook Jung, Donghoon Lee, Hakjun Lee, and Dongho Won
1.Introduction
With the rapid development of the Internet service and electronic commerce technology, many people rely on computer networks to exchange information, access resource,and process data in wireless networks now. Such public wireless networks may be intruded by malicious attackers and other unauthorized users. To ensure the secure environment, the password-based user authentication technique is one of the most widely adopted mechanisms to deal with the secret data over the public channels.
Since Lamport[1]first proposed a user authentication protocol in 1981, numerous user authentication schemes have been proposed[2]-[9]afterwards. In 2009, Xu et al.[2]proposed a smart-card-based password authentication scheme. They claimed that the scheme can resist various types of attacks even if the information stored in the smart card is revealed.However, in 2010, Song[3]proved that Xu et al.’s scheme[2]cannot be secure against an impersonation attack, and then Song[3]proposed an improved scheme. In the same year, Sood et al.[4]also found that Xu et al.’s scheme[2]cannot resist the off-line guessing attack and forgery attack, and then presented an enhanced scheme. Unfortunately, in 2013, Chen et al.[5]demonstrated that Song’s scheme[3]is vulnerable to stolen smart card attack. Chen et al.[5]also proved that Sood et al.’s scheme[4]does not provide mutual authentication, which means that a legitimate user has no way to verify the validity of the server. Then Chen et al.[5]proposed a robust smart-card-based remote user password authentication scheme. However, in 2013, Li et al.[6]pointed out that Chen et al.’s scheme[5]cannot ensure the perfect forward secrecy and detect the wrong password in login phase. Besides that, the password change of Chen et al.’s scheme[5]is inefficient since the user has to communicate with the server to update his/her password. Then Li et al.[6]proposed an enhanced user authentication scheme.
Recently, Liu et al.[7]pointed out that Li et al.’s scheme[6]is insecure against the man-in-the-middle attack and insider attack. To address the weaknesses in the Li et al.’s scheme[6],Liu et al. proposed an improved smart card based password authentication scheme[7]. However, after careful analysis, we find that Liu et al.’s scheme is vulnerable to off-line password guessing attack and user impersonation attack as well as it fails to preserve user anonymity in login phase. In order to eliminate all the above problems existed in Liu et al.’s scheme, a security enhanced anonymous user authenticated key agreement scheme is proposed.
The remainder of the paper is organized as follows: Section 2 describes a review of Liu et al.’s scheme. Section 3 points out the weaknesses of Liu et al.’s scheme. The proposed scheme and security analysis of the proposed scheme are presented in Sections 4 and 5, respectively. Lastly, Section 6 concludes this paper.
2.Review of Liu et al.’s Scheme
This section describes Liu et al.’s authentication scheme[7]which involves four phases: Registration, login, authentication,and password change. For convenience, the notations used throughout this paper are summarized in Table 1.
2.1 Registration Phase
Step 1. The user Uiselects his/her IDiand PWi, and generates random number r. Then Uicomputesand sends a registration requestto the server S through a secure channel.

Table 1: Notations
Step 2. The server S computes,, and. The server S storesinto a smart card and issues this smart card to the user Uithrough a secure channel.
Step 3. The user Uistores the random number r into the card. Finally, the smart card contains.
2.2 Login Phase
Step 1. The user Uiinserts his/her smart card into a card reader and inputs IDiand PWi. The smart card computesand, then compares Ci′ with the stored value Ci. If this condition is hold,the smart card acknowledges the legitimacy of Ui, and proceeds with the next steps. Otherwise, it terminates this phase.
Step 2. The smart card generates a random number α,computesand.
Step 3. Finally, the user Uisends login request messageto the server S.
2.3 Authentication Phase
Step 1. The server S checks the validity of timestampand computes, then compares Di′ with the received value Di. If this condition is hold, the procedure goes to the next steps. Otherwise, this phase is terminated.
Step 2. The server S generates a random number β,computesand. Then the server S sends the authentication messageto Ui.
Step 3. The user Uichecks the validity of timestampand computes, then compares F′ with the received valueiFi. If this condition is hold, the Uiacknowledges the legitimacy of the S, and proceeds with the next step. Otherwise, it terminates this phase.
Step 4. Finally, the user Uicomputes a session keyand the server S also computes the same shared session key
2.4 Password Change Phase
Step 1. The Uiinserts his/her smart card into a card reader and inputs IDiand password PWi.
Step 2. The smart card computes, then compareswith the stored value Ci. If it is hold, Uiselects a new passwordOtherwise, this phase is terminated.
Step 3. The smart card computesand. Finally, the smart card replaces (Bi, Ci) with (,), respectively.
3.Security Weaknesses of Liu et al.’s Scheme
In this section, the weaknesses of Liu et al.’s scheme[7]are demonstrated. We find that Liu et al.’s scheme cannot resist the off-line password guessing attack and user impersonation attack as well as it fails to preserve user anonymity. The details of these weaknesses are described as follows.
3.1 Failure to Preserve User Anonymity
User anonymity is a highly desirable property for user authentication scheme, as the leakage of user’s identity may allow an unauthorized entity to track the user’s login record and behavior pattern. However, in Liu et al.’s scheme,user’s identity IDiis in plaintext form in the login request. Using an eavesdropping attack, the attacker can maliciously monitor the public channels[8]-[10], and also identify some of the valuable information in messages transmitted over these public channels[11]-[17]. In this manner, an attacker can eavesdrop on login messages to collect the plaintext identities without difficulty. For this reason, user anonymity cannot be preserved in Liu et al.’s scheme[7].
3.2 Off-Line Password Guessing Attack
In Liu et al.’s scheme[7], the attacker can obtain the informationin the smart card after physically monitoring power consumption[10], and intercept login request message. Then the off-line password guessing attack can be done by performing the following steps:
Step 1. The attacker extracts the stored parametersfrom the stolen smart card by using the power consumption attack[10].
Step 2. The attacker obtains the exact user’s identity IDiby executing the steps discussed in subsection 3.1.
Step 3. The attacker selects a password candidate
Step 4. By using the obtained user’s identity IDi, the attacker computes
Step 5. The attacker repeats above steps from step 3 to step 4 until the computed result Ci*equals the stored Ci.
If they are equal, PWi*= PWi, this means that the attacker has successfully obtained the user’s password PWiby offline password guessing attack.
3.3 User Impersonation Attack
In this subsection, we demonstrate that an attacker can successfully login to the server S by using the stolen smart card of a user Ui. The steps are as follows:
Step 1. The attacker obtains the user’s identity IDiby executing the steps discussed in subsection 3.1 and also obtains the user’s password PWiby executing the steps discussed in subsection 3.2.
Step 2. The attacker generates a random number R, and computesThen The attacker sends the forged messageto the server S for login request.
Step 3. Upon receiving the forged login request messagefrom the attacker, the server S first checks the validity of timestamp. After that, S computesthen compares Di′ with the received value
Step 4. Finally, the server S successfully verifies the forged login request messagebecause the computed value Di′ correctly equals the received valueWith these correct verifications, the server S accepts the forged login request and allows the attacker to login.
Through the aforementioned steps, we can see that the attacker can successfully impersonate the legal Ui.
4.Proposed Scheme
In this section, we propose a security enhanced authentication and key agreement scheme to overcome the security weaknesses in Liu et al.’s scheme[7]. The proposed scheme also consists of four phases: Registration, login,authentication, and password change. The notations in the scheme are summarized in Table 1. Fig. 1 provides an illustration of login and authentication phases of the proposed scheme.
4.1 Registration Phase
Step 1. The user Uiselects his/her IDiand PWiand generates the random number r. Then Uicomputes h(r||PWi)and sends a registration requestto the server S through a secure channel.
Step 2. The server S computes,The server S stores {Bi, Ci, h(·)} into a smart card and issues this smart card to the user Uithrough a secure channel.
Step 3. The user Uistores the random number r into the card. Finally, the smart card contains {Bi, Ci, h(·), r}.
4.2 Login Phase
Step 1. The user Uiinserts his/her smart card into a card reader and inputs IDiand PWi. The smart card computesthen compares Ci′ with the stored value Ci. If this condition is hold,the smart card acknowledges the legitimacy of the Ui, and proceeds with the next steps. Otherwise, it terminates this phase.
Step 2. The smart card generates a random number α and computes,, and.
Step 3. Finally, the user Uisends the login request message{Di, Ei, Fi, Ti} to the server S.
4.3 Authentication Phase
Step 1. The server S checks the validity of timestampand computes, then compares Fi′ with the received value Fi. If this condition is hold, the procedure goes to the next steps. Otherwise, this phase is terminated.
Step 2. The server S generates a random number β, and computes. Then the server S sends the authentication message {Gi, Hi, Ts} to Ui.
Step 3. The user Uichecks the validity of timestampand computesand, then compares Gi′ with the received value Gi. If this condition is hold, Uiacknowledges the legitimacy of the S, and proceeds with the next step. Otherwise, it terminates this phase.
4.4 Password Change Phase
Step 1. The user Uiinserts his/her smart card into a card reader, inputs IDiand password PWi.

Fig. 1. Login and authentication phase of the proposed scheme.
Step 2. The smart card computesthen compareswith the stored Ci. If it is hold, Uiselects a new password. Otherwise, this phase is terminated.
Step 3. The smart card computesandFinally, the smart card replaces (Bi, Ci) with,).
5.Security Analysis of Proposed Scheme
In this section, we will analyze the proposed scheme in terms of security. Table 2 shows the security comparisons of the proposed scheme and other related schemes[5]-[7]. The detail descriptions are as follows.
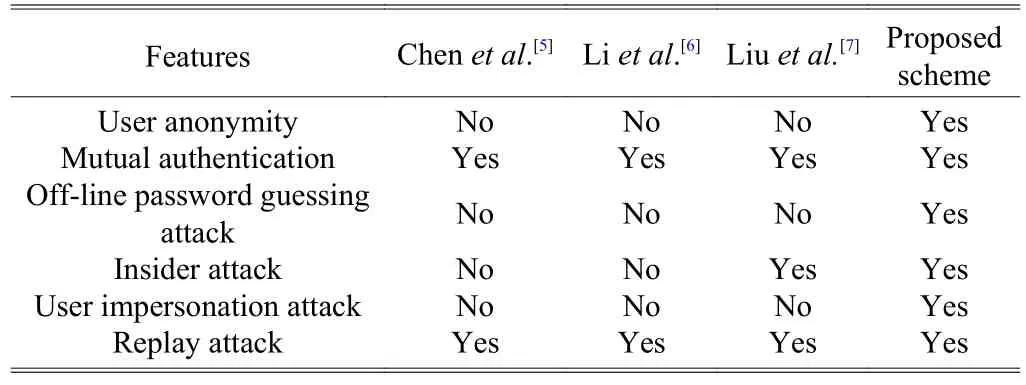
Table 2: Security comparisons of the proposed scheme and other related schemes
5.1 Preserve User Anonymity
Suppose that the attacker has intercepted the user Ui’s login request {Di, Ei, Fi, Ti}. However, it is not feasible to derive IDifrom the login request because the login request includes Diinstead of IDi. Therefore, the use of Diwill ensure any information related to the user identity could not be acquired by the attacker.
5.2 Provide Mutual Authentication
In the scheme, the server S can authenticate the user by checking whether the login request {Di, Ei, Fi, Ti} is correct.Also, the user Uican authenticate the server S by checking whether the authentication message {Fi, Gi, Ts} is correct.
5.3 Resistance to Off-Line Password Guessing Attack
To successfully carry out a password guessing attack in the proposed scheme, the attacker has to know the user’s IDi. However, it is impossible for the attacker to obtain the user’s identity IDiin the proposed scheme. Thus, the proposed scheme is secure against the off-line password guessing attack.
5.4 Resistance to Insider Attack
In the proposed scheme, the user Uisends the password information to the server S in the form of h (r||PWi) instead of the form PWi. Accordingly, the inside attacker is unable to acquire the user’s password PWi.
5.5 Resistance to User Impersonation Attack
If an attacker tries to impersonate a legal user Uiin order to cheat the server S, the attacker needs to modify {Di, Ei, Fi, Ti}to start a new session. In order to change these values, the attacker has to guess the secret key x. However, the probability of successfully guessing x is negligible.
5.6 Resistance to Replay Attack
An attacker can intercept data packets and try to resend it to server in order to launch the replay attack. However, the login request message of the proposed scheme includes a current timestamp, i.e., Tiof {Di, Ei, Fi, Ti}. Hence, the proposed scheme can withstand against the replay attack.
6.Conclusions
We have proposed an enhanced user authentication scheme in order to remedy the security weaknesses of Liu et al.’s scheme[7]. The proposed scheme achieves the mutual authentication and the user anonymity. In addition, the proposed scheme can withstand the password guessing attack, user impersonation attack, and insider attack even if the attacker obtains the user’s smart card. The security of the proposed scheme has been analyzed and the result shows that the scheme is more secure than other related schemes.
[1]L. Lamport, “Password authentication with insecure communication,”Communications of the ACM, vol. 24, no.11, pp. 770-772, 1981.
[2]J. Xu, W.-T. Zhu, and D.-G. Feng, “An improved smart card based password authentication scheme with provable security,”Computer Standards and Interfaces, vol. 31, no. 4,pp. 723-728, 2009.
[3]R. Song, “Advanced smart card based password authentication protocol,”ComputerStandardsand Interfaces, vol. 32, no. 5-6, pp. 321-325, 2010.
[4]S. K. Sood, A. K. Sarje, and K. Singh, “An improvement of Xuet al.’s authentication scheme using smart cards,” inProc. of the 3rd Annual ACM Bangalore Conf., India, 2010,pp. 22-23.
[5]B.-L. Chen, W.-C. Kuo, and L.-C. Wu, “Robust smart-cardbased remote user password authentication scheme,”Intl.Journal of Communication Systems, vol. 27, no. 2, pp. 377-389, 2012.
[6]X. Li, J. Niu, M. K. Khan, and J. Liao, “An enhanced smart card based remote user password authentication scheme,”Journal of Network and Computer Applications, vol. 36, no.5, pp. 1365-1371, 2013.
[7]Y.-J. Liu, C.-C. Chang, and S.-C. Chang, “An efficient and secure smart card based password authentication scheme,”Intl. Journal of Network Security, vol. 19, no. 1, pp. 1-10, 2016.
[8]D. Kang, J. Jung, J. Mun, D. Lee, Y. Choi, and D. Won,“Efficient and robust user authentication scheme that achieve user anonymity with a Markov chain,”Security and Communication Networks, vol. 9, no. 11, pp. 1462-1476,2016.
[9]Y. Choi, D. Lee, J. Kim, J. Jung, J. Nam, and D. Won,“Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography,”Sensors,vol. 14, no. 6, pp. 10081-10106, 2014.
[10]P. Kocher, J. Jaffe, and B. Jun, “Differential power analysis,”inProc. of Annual Intl. Cryptology Conf., 1999, pp. 388-397.
[11]J. Kim, D. Lee, W. Jeon, Y. Lee, and D. Won, “Security analysis and improvements of two-factor mutual authentication with key agreement in wireless sensor networks,”Sensors, vol. 14, no. 4, pp. 6443-6462, 2014.
[12]J. Moon, Y. Choi, J. Kim, and D. Won, “An improvement of robust and efficient biometrics based password authentication scheme for telecare medicine information systems using extended chaotic maps,”Journal of Medical Systems, vol. 40, no. 3, pp. 1-11, 2016.
[13]Y. Chung, S. Choi, Y. Lee, N. Park, and D. Won, “An enhanced lightweight anonymous authentication scheme for a scalable localization roaming service inwireless sensor networks,”Sensors, vol. 16, no. 10, pp. 1653: 1-21, 2016.
[14]J. Moon, Y. Choi, J. Jung, and D. Won, “An improvement of robust biometrics-based authentication and key agreement scheme for multi-server environments using smart cards,”Plos One, vol. 10, no. 12, pp. e0145263: 1-15, 2015.
[15]F. B. Degefa, D. Lee, J. Kim, Y. Choi, and D. Won,“Performance and security enhanced authentication and key agreement protocol for SAE/LTE network,”Computer Networks, vol. 94, no. 15, pp. 145-163, 2016.
[16]J. Nam, K. K. R. Choo, S. Han, M. Kim, J. Paik, and D.Won, “Efficient and anonymous two-factor user authentication in wireless sensor networks: Achieving user anonymity with lightweight sensor computation,”Plos One,vol. 10, no. 4, pp. 0116709: 1-21, 2015.
[17]Y. Choi, Y. Lee, and D. Won, “Security improvement on biometric based authentication scheme for wireless sensor networks using fuzzy extraction,”Intl. Journal of Distributed Sensor Networks,, vol. 2016, no. 2, pp. 1-16, 2016.
杂志排行
Journal of Electronic Science and Technology的其它文章
- Multi-Reconfigurable Band-Notched Coplanar Waveguide-Fed Slot Antenna
- Pairing-Free Certificateless Key-Insulated Encryption with Provable Security
- Overview of Graphene as Anode in Lithium-Ion Batteries
- High Power Highly Nonlinear Holey Fiber with Low Confinement Loss for Supercontinuum Light Sources
- Modeling TCP Incast Issue in Data Center Networks and an Adaptive Application-Layer Solution
- Message from JEST Editorial Committee
