An Iterative Detection/Decoding Algorithm of Correlated Sources for the LDPC-Based Relay Systems
2017-04-09HaiqiangChenHangCaoXiangchengLiYoumingSunHaibinWanTuanfaQin
Haiqiang Chen, Hang Cao, Xiangcheng Li, Youming Sun, Haibin Wan, Tuanfa Qin
The School of Computer and Electronic Information, Guangxi University, Nanning 530004, China
Guangxi Key Laboratory of Multimedia Communications and Network Technology, Guangxi University, Nanning 530004, China
Guangxi Colleges and Universities Key Laboratory of Multimedia Communications and Information Processing, Guangxi University,Nanning 530004, China
* The corresponding author, email: tfqin@gxu.edu.cn
I. INTRODUCTION
The basic single relay system was first investigated by Van de Meulen in 1971 [1]. Early research work on the relay system mainly focuses on the capacity analysis under some fundamental coding strategies, such as the decode-and-forward strategy and the estimate-and-forward strategy [2-6]. Parallel with these work, coding/decoding designs of how to approach the relay channel capacity have also been extensively studied [7-11]. The decoding schemes therein commonly adopt the iterative turbo-like strategy, such as the partial factor-graph decoupling in [8] and the cooperative constellation decoding in [9], where the transmitted data can be recovered based on two consecutive received signals at the destination between two detection/decoding systems.
In [12], Daneshgaran et al. invented a de-coding algorithm of correlated sources based on low density parity-check code (LDPC)for a basic communication model with three nodes, where two of which send correlated data blocks to the third destination node. It is shown that, the destination node can use the correlation of the data blocks to obtain coding gains.
Two iterative detection/decoding algorithms, the traditional turbo-like algorithm and the presented algorithm of correlated sources are investigated and compared in this paper.
Simulation results show that the presented algorithm performs slightly better than the traditional turbo-like algorithm. Besides, the presented algorithm requires fewer computing operations per iteration and has faster decoding convergence rate. Therefore, the presented algorithm of correlated sources provides a candidate for decoding the LDPC-based relay systems.
II. PRELIMINARIES
2.1 Relay structure

Fig. 1 (a) Relay system (b) Distance-oriented relay model
A single relay channel can be simply described in figure 1(a) with three nodes: the source (S), the relay (R) and the destination(D) nodes. The authors in [11] presented a corresponding physical model, as shown in figure 1(b). In this physical description, the R-node is positioned in the same line with the S-node and the D-node. Besides, the physical communication distance of the S-D link is normalized to 1. Consequently, the distance of S-R link isand the distance of R-D link isSimilar to the large-scale path loss model in [8], the channel coefficients of the three links are defined asandwhere the parametersandrepresent the channel gains of the S-D, the S-R and the R-D links, respectively. The parameter α is the pathloss-exponent, whose value is typically chosen from 2 to 5, depending on different channel conditions [13].
2.2 System model
Transmitting: 1)S-node:Letbe the k-bit information block at time t. The block utis encoded into a codeword wtwith length n. For simplicity, we only consider the BPSK modulation here. The modulated signal vector with respect to wtcan be denoted aswhereThen the S-node sends the modulated signalto the S-R and S-D channels. 2) R-node:During time t, the R-node re-encodes the hard-decision resultof the previous information blockresulting a codewordSimilarly, the modulated vector ofwhereThen the R-node transmits the modulated signalto the D-node.
Receiving: 1)R-node: the R-node receives the noised version offrom the S-node at time t, as follows

巷道帮部喷浆层壁后0.3 m范围内围岩非常破碎,成块状分布;帮部在0.3~1.2 m范围内围岩以裂隙带向节理带转换形式分布,裂隙密度逐步减小;顶板1.5 m以上区域围岩完整性相对较好,未见明显裂隙、离层,但孔壁存在泥块剥离现象。

Detection/Decoding: 1)R-node: at time t, the R-node performs the decoder and gets the hard-decision result(an estimate of ut). Thenis re-encoded and will be sent to the D-node at the next time2) D-node:two detectors/decoders are employed at the D-node. When both of the signalsandhave been received, the presented decoding algorithm of correlated sources can be applied to recover the transmitted block ut.
Note:the power allocation strategy will affect the decoding performance. Letdenote the power allocation parameter, whereis the total transmit power. Similarly to [9], the parameteris determined by simulations in this paper.
III. THE ITERATIVE JOINT DECODING ALGORITHMS FOR THE RELAY SYSTEMS
3.1 The iterative decoding algorithm using turbo-equalization principle
The turbo-like decoding system at the D-node includes two blocks: 1) the detector’s soft output computing (figure 2(a)); 2) the iterative turbo-like decoding (figure 2(b)).



Detector 1 and Detector 2 in figure 2(b)are designed to computeandas follows:
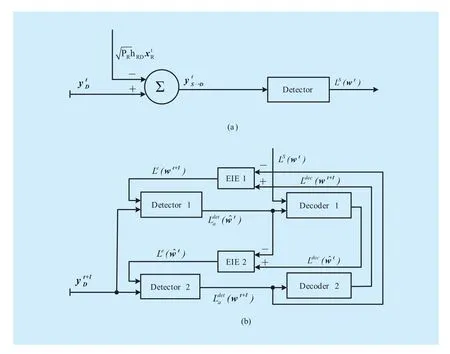
Fig. 2 (a) Soft output of the detector (side information) (b) Turbo-like decoding unit


and

The turbo-like detection/decoding algo-rithm can be described in Algorithm 1.
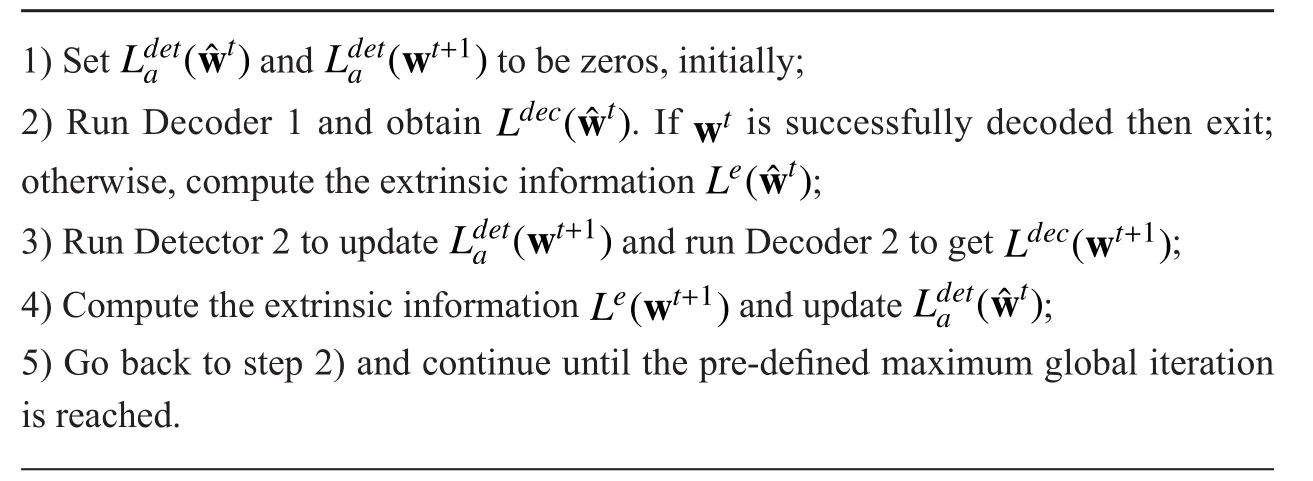
Algorithm 1: The turbo-like iterative decoding algorithm for LDPC-based relay systems:
3.2 The iterative detection/decoding algorithm of correlated sources for the LDPC-based relay systems
3.2.1 Motivation
Considering a basic communication model with three nodes A, B and C, where A and B have correlated data blocks to be transmitted to C. The empirical cross-correlation between two binary correlated data blocks is defined as follows

The task of the D-node is to recover the data utbased on two consecutive received signals.Evidently, bothandcontain the information about ut. Based on this fact, the system model can be transformed equivalently into a coded correlated source (see figure 3).At time t, utis encoded into wtand then sent to the S-D link. The corresponding received signal at the D-node isAt time t + 1,an estimateof utis encoded intoat the R-node. A binary vectoris intro-
where α is the number of places in which the two data blocks take the same value and k is the data block size [12]. The authors in[12] proposed an LDPC-based iterative decoding algorithm of correlated messages for this model. It is shown that, node C can use the correlation between two received blocks to achieve coding gains, especially when the blocks are highly correlated (ρ is nearly 1 or 0). Motivated by this work, we will show in the next subsection that the relay systems can be re-formulated and then decoded as correlated sources.
3.2.2 Re-formulating the LDPC-coded relay systems as correlated sources duced to indicate the (possibly existing) difference between utand. The codewordis transmitted over the R-D channel. Taking the signal from S-D link at timeas interferences, the superposition received signal can be formulated as

Note that, the data blocks utandare highly correlated, especially when the channel condition between the S-node and the R-node is good enough. Hence, the two consecutive received blocks at the D-node can be treated as correlated encoded blocks. We then present the iterative decoding algorithm of correlated sources to recover the transmitted data for LDPC-based relay systems.
Remarks:the cross-correlation coefficientmay vary from block to block in this paper.This is different from the work in [12], where the performance is evaluated under a fixed value.
3.2.3 Algorithm description
Figure 4 shows the iterative detection/decoding algorithm of correlated sources for the LDPC-based relay systems. Detector 1 is to computeaccording to (5), from which we can obtainone of the soft inputs to Decoder 1. Similarly, Detector 2 is to computeaccording to (6) to obtainone of the soft inputs to Decoder 2.

The extrinsic information passed to Decoder 1 and Decoder 2 can be evaluated by [12]
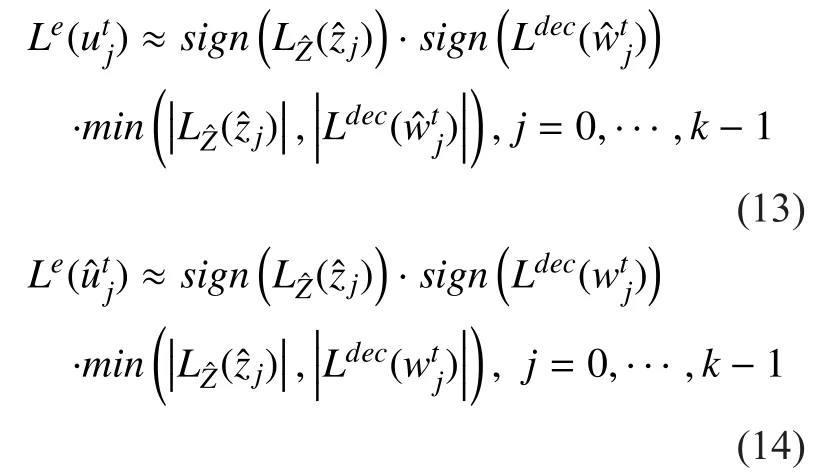
The iterative decoding algorithm of correlated sources for the relay systems can be described in Algorithm 2.

Algorithm 2: The iterative detection/decoding algorithm of correlated sources for LDPC-based relay systems:
IV. COMPLEXITY ANALYSIS AND SIMULATION RESULTS
4.1 Complexity analysis

Fig. 4 The iterative joint decoding scheme of correlated sources

Table I The complexities of the two algorithms

Fig. 5 The BER performances of the (255,175) EG-LDPC code under different power ratios

Fig. 6 The BLER performances of the (255,175) EG-LDPC code under different power ratios
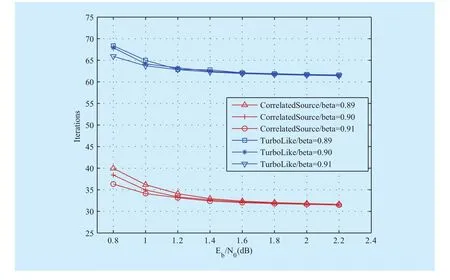
Fig. 7 Convergence rates of the (255,175) EG-LDPC code under different power ratios
Since the turbo-like decoding algorithm and the correlated source decoding algorithm both employ the same detectors and decoders, the complexity differences between these two algorithms are mainly caused by the computation of the soft messages involved. For the turbo-like decoding algorithm, we need 4n real multiplications (RM) to compute the soft inputs for the detectors and n real additions(RA) to compute the soft inputs for Decoder 1. Besides, 2n real substractions (RS) are required to compute the extrinsic information.For the correlated source decoding algorithm,we need 2k real additions to compute the soft inputs for the decoders and 2k real comparisons to compute the extrinsic information. To compute the sequencewe need k XOR operations (modulo-2 additions). The complexities of the two algorithms are shown in table 1. It can be seen that, compared to the turbo-like algorithm, the correlated source algorithm has less computational complexity and can be more convenient for hardware implements.
4.2 Simulation results
In our simulations, the sum-product algorithm(SPA) is employed for the decoders. The simulation parameters are listed as follows: 1) The distance of the S-node and the R-node d is set to be 0.25; 2) The pathloss-exponent α is set to be 2; 3) The maximum local iteration number is set to be 30; 4) The global iteration number between the two decoders is set to be 3; 5) The max block number is set to be 1000000. We give two examples here to compare the performances of the turbo-like decoding algorithm and the presented correlated source decoding algorithm.
Example 1:Consider the (255, 175) LDPC code designed by the Euclidean geometry(EG) method [16]. The bit error rate (BER)and the block error rate (BLER) performances of the two decoding strategies for this code are shown in figure 5 and figure 6, respectively.It can be seen that, with a (sub)optimal power ratiothe performance gaps between the two decoding algorithms can be negligible in the low SNR region; while the correlated sources decoding algorithm performs slightly better (about 0.1dB performance gains around BLER=10-4) than turbo-like algorithm, especially for the high SNR. Figure 7 indicates the convergence rates. The total iteration is counted when wtis successfully decoded (no matter decoded by Decoder 1 or Decoder 2), which is calculated by the sum of the local iteration performed by Decoder 1 and Decoder 2, respectively.
It is shown that, compared to the turbo-like decoding algorithm, the presented iterative correlated sources decoding algorithm can achieve much faster decoding convergence speed. For example, at, it takes only about 32 iterations for the presented algorithm, while the turbo-like algorithm requires about 63 iterations.
Example 2:Consider the (961,721) quasi-cyclic (QC) LDPC code [17] designed with finite fields. The BER performance and the convergence rate are shown in figure 8 and figure 9, respectively. As expected, we have a similar observation: the two decoding algorithms have equivalent performances. Compared to the turbo-like decoding algorithm, the presented iterative correlated sources decoding algorithm can achieve about two times faster decoding convergence speed.
V. CONCLUSION
Two iterative detection/decoding algorithms,the traditional turbo-like algorithm and the presented algorithm of correlated sources are investigated and compared in this paper. The first algorithm is designed as the iterative turbo-like detection/decoding algorithm, whereby the information from the previous block is taken as side information. Then we re-formulate the relay system as correlated sources and present the second decoding algorithm. For the presented algorithm, the previous block is treated as a highly correlated codeword instead of side information to the current block and the extrinsic information is computed by the LLR associated with the XOR vector derived from two correlated hard decision results. It has been shown by simulations that the presented algorithm has slightly better performance than the traditional turbo-like algorithm. Besides, the presented algorithm requires fewer computing operations per iteration and has faster decoding convergence rate.Therefore, the presented algorithm provides a candidate for decoding the LDPC-based relay systems, which may find applications in the extremely energy-constrained system.

Fig. 8 The BER performances of the (961,721) QC-LDPC code under different power ratios

Fig. 9 Convergence rates of the (961,721) QC-LDPC code under different power ratios
ACKNOWLEDGEMENTS
This work was supported by NSF of China (No. 61362010, 61661005) and NSF of Guangxi (No. 2015GXNSFAA139290,2014GXNSFBA118276, 2012GXNSFAA053217). Part of this work was done when H. Chen was working on his doctoral degree. The authors would like to thank Prof.X. Ma from Sun Yat-sen University for his helpful comments.
[1] E. C. van de Meulen, “Three-terminal communication channels”, Advanced Applied Probability,vol. 3, pp. 120-154, 1971.
[2] T. M. Cover and A. A. El Gamal, “Capacity theorems for the relay channel”, IEEE Transactions on Information Theory, vol. IT-25, pp. 572-582, Sep.1979.
[3] F. M. Willems, “Information theoretical results for the discrete memoryless multiple access channel”, Ph.D. dissertation, Katholieke Univ.Leuven, Leuven, Belgium, Oct. 1982.
[4] C. M. Zeng, F. Kuhlmann, and A. Buzo, “Achievability proof of some multiuser channel coding theorems using backward decoding”, IEEE Transactions on Information Theory, vol. 35, no.6, pp. 1160–1165, Nov. 1989.
[5] G. Kramer, M. Gastpar, and P. Gupta, “Cooperative strategies and capacity theorems for relay networks”, IEEE Transactions on Information Theory, vol. 51, no. 9, pp. 3037-3063, Sep. 2005.
[6] Z. Zhang and T. M. Duman, “Capacity-approaching turbo coding and iterative decoding for relay channels”, IEEE Transactions on Communications, vol. 53,no. 11, pp. 1895-1905, Nov.2005.
[7] M. A. Khojastepour, N. Ahmed, and B. Aazhang,“Code design for the relay channel and factor graph decoding”, in Proceedings of the 38th Asilomar Conference on. Signals, Systems &Computers, pp. 2000-2004, Nov. 2004.
[8] J. Hu and T. M. Duman, “Low density parity check codes over wireless relay channels”, IEEE Transactions on Wireless Communications, vol.6, no. 9, pp. 3384-3394, Sep. 2007.
[9] C. Li, G. Yue, M. A. Khojastepour, X. Wang, and M. Madihian, “LDPC coded cooperative relay systems: performance analysis and code design”, IEEE Transactions on Communications, vol.56, no. 3, pp. 485-496, Mar. 2008.
[10] H. Chen, D. Yu, and X. Ma, “Cooperative signal constellation for LDPC-coded relay system”,IEEE Communications Letters, vol. 15, no. 7, Jul.2011.
[11] X. Huang, H. Chen and X. Ma, “Achievable rates and forward-backward decoding algorithms for the Gaussian relay channels under the onecode constraint”, in Proceedings of the 2014 IEEE International Conference on Communications(ICC), Sydney, Australia, pp. 2135-2140, Jun.2014.
[12] F. Daneshgaran, M. Laddomada, and M. Mondin, “LDPC-based channel coding of correlated sources with iterative joint decoding”, IEEE Transactions on Communications, vol. 54, no. 4,pp. 577-582, Apr. 2006.
[13] T. S. Rappaport, “Wireless communications,principles and practice, seconded”, Upper Saddle River, NJ: Prentice Hall PTR, 1996.
[14] A. de Baynast and D. Declercq, “Gallager codes for multiple user applications”, in Proceedings of the IEEE International Symposium on Information Theory (ISIT), Lausanne, Switzerland, pp.335, Jun. 2002.
[15] X. Ma and P. Li, “Coded modulation using superimposed binary codes”, IEEE Transactions on Information Theory, vol.50, no. 12, pp. 3331-3343, Dec. 2004.
[16] Y. Kou, S. Lin and M. P. C. Fossorier, “Low-density parity-check codes based on finite geometries:A discovery and new results”, IEEE Transactions on Information Theory, vol. 47, no. 7, pp. 2711-2736, Nov. 2001.
[17] L. Lan, L. Zeng, Y. Tai, L. Chen, et al., “Construction of quasi-cyclic LDPC codes for AWGN and binary erasure channels: a finite field approach”,IEEE Transactions on Information Theory, vol. 53,no. 7, pp. 2429-2458, Jul. 2007.
猜你喜欢
杂志排行
China Communications的其它文章
- Homomorphic Error-Control Codes for Linear Network Coding in Packet Networks
- Polar-Coded Modulation Based on the Amplitude Phase Shift Keying Constellations
- A Privacy-Based SLA Violation Detection Model for the Security of Cloud Computing
- An Aware-Scheduling Security Architecture with Priority-Equal Multi-Controller for SDN
- A Flow-Based Authentication Handover Mechanism for Multi-Domain SDN Mobility Environment
- Light Weight Cryptographic Address Generation (LWCGA) Using System State Entropy Gathering for IPv6 Based MANETs
