Light Weight Cryptographic Address Generation (LWCGA) Using System State Entropy Gathering for IPv6 Based MANETs
2017-04-09ReshmiMurugan
Reshmi T.R*, Murugan K
1 VIT University, Chennai, India
2 Anna University, Chennai, India
* The corresponding author, email: reshmi.tr@vit.ac.in
I. INTRODUCTION
Mobile Ad-hoc Networks (MANETs) are infrastructure-less networks with self-configured hosts communicated via multi-hop communications. IPv6 autoconfiguration was designed to automatically attach a new node to a network and obtain information needed for connectivity. The main goal of autoconfiguration is to have the entire process occur automatically without human interaction, which eases the formation of spontaneous MANETs.Generally key exchange schemes are used to ensure secured communication in MANETs.But these automatic key exchanges can occur only between hosts with established IPv6 addresses. So IPsec is incapable of performing an automatic key exchange, and secure auAtoconfiguration process.
IPv6 uses a hierarchical addressing scheme for the ease of address management. The IPv6 provides an active network interface with a default IPv6 address called the link-local address. This address is fully functional within the local segment and is not routed by routers.Hosts use this address to communicate with other hosts in same network. The 128-bit link local address consists of two 64-bit portions:a special link-local prefix (FE80:: /10) and a MAC address derived Extended Unique Identifier (EUI-64). The 48-bit MAC is first divided into two 24-bit halves and is filled with 16-bit FFFE in the middle. The 7th bit of the interface identifier (IID) signifies whether the address is global (0) or local (1). The 8th bit is called the group bit; and it signifies whether the address is unicast (0) or multicast (1). The EUI-64 based address generation in Stateless Address Autoconfiguration (SLAAC) [2] is shown in figure 1.
When a node generates a tentative link-local address, it is checked for duplication on the subnet by the Neighbor Discovery Protocol(NDP) [1] assisted process called Duplicate Address Detection (DAD). Each network interface card (NIC) has multiple valid IPv6 addresses such as link-local, assigned unicast, solicited-node multicast, and all-nodes multicast addresses etc. The interfaces are configured with the all-nodes and solicited-node multicast group addresses to perform DAD. During DAD process, the Neighbor Solicitation (NS)messages are sent to the solicited-node multicast address. A Neighbor Advertisement (NA)message allows two nodes to detect the use of the same addresses on the network. When a duplicate is detected, the node with a permanent address, sends back an NA message to the requestor’s solicited node multicast address stating the collision. The node then performs regeneration of addresses and DAD up to two more times, after which a warning is written to the system log and the interface attempting to autoconfigure is disabled. If no duplication is detected, the address is considered unique and is assigned as permanent address.

Fig. 1 EUI-64 generation in SLAAC
The link-local address is used as an initial default address to retrieve the global and other network-prefix addresses. In a network, when a node receives a Router Advertisement (RA)(unsolicited or as a reply for Router Solicitation (RS)), it creates an IPv6 address appropriate for the advertised network prefix. These addresses are created by attaching the advertised prefix to the already derived EUI-64.
The EUI-64 in IPv6 addresses remains stable for each subnet with the same network interface address, even when the client moves across different networks. So the one-to-one mapping of MAC addresses and EUI-64 in IPv6 addresses paves way to many privacy and security issues. When a node continues using the identity of a EUI-64 based link-local address and retrieves other addresses, it will be permanently bounded to the node and hence the mobility pattern of the node can be easily tracked. Beyond creating privacy issues,it also poses as potential source for information leakage. The EUI-64 based addresses in SLAAC are prone to different types of attacks given below.
● Impersonation: The lack of link layer control and spoofed MAC addresses can indulge any node to claim to be the existing member node in a network by generating the genuine member’s EUI-64 based address. These attacks can impersonate as both routers and hosts too. The address spoofing of router results in higher damage,as it can imply man-in-the-middle attacks.
● Denial of Service (DoS): Spoofing of DAD replies can introduce DoS attacks as the neighbor nodes consider that the network is undergoing a network merge or partition.Thereby the attackers will never allow genuine member nodes to participate or get services in the network.
The SeND augmented IPv6 packets with the different fields of CGA options is given in figure 2.
The above three categories of attacks are launched by altering the Internet Control Message Protocol Version 6 (ICMPv6) messages exchanged during autoconfiguration. The details of the ICMPv6 message exchanges are given in table 1.
“没错,这两栋楼之间的距离并不远。如果用木板架起一座桥的话,就好解释多了。”霍铁不动声色地说,“可是,我向陆叔叔的助手了解过了,这段时间他根本就没出过工作室的门。”
ii. L1 Data Cache: The L1 cache also known as the primary cache memory in the processor core possesses information of the latest data used by a processor. In the LW-CGA, the cache lines of the L1 data cache are assumed to be in one of the seven possible states. This data is usually mapped in the SCROLL table between any one of the available 32 byte block .The L1 cache is selected as one of the 7512 possible states.The processor might additionally possess L2 and L3 caches which are not considered in this implementation.

Table I ICMP message exchanged during autocofiguration

Table II Attacks launched during autoconfiguration

Table III ICMPv6 option types in SeND

Fig. 2 SeND augmented IPv6 packet format
The proposal is a light weight cryptographic address generation which is an alternate for CGA in SeND, The proposed scheme aims to bring a new address generation technique to adapt to MANET environment and is not targeted to improve the security of the scheme.The motivation of the proposed scheme is to assure:
(1) The IPv6 addresses after CGA generation does not any way relate to MAC addresses and are unique within each subnet for each address in the same network interface of the same client.
The LW-CGA includes several options to regenerate the CGA, resulting in different IPv6 addresses. These regenerations are explicitly prompted by a function call REGENERATE( )in the daemon. The various options provided by the LW-CGA regeneration are listed below.
(3) The CGA based IPv6 addresses are reconfigured during network merging, partitioning or renumbering.
The paper is organized into five sections.Section 1 discusses the introduction of the paper following the discussion of the existing work in Section 2. The Section 3 discusses the proposed work and the working of the scheme.Section 4 discusses the experimental setup and evaluations. Section 5 discusses the conclusion and the future works.
II. BACKGROUND
The SeND uses an asymmetric cryptography to enforce authentication and integrity without changing the zero configuration standard of the ND protocol. SeND encodes its ICMPv6 messages [6] by using few new option types that are not used in the regular ND messages.The table 3 lists the new ICMPv6 option types used in SeND. RSA keys and Cryptographically Generated Address (CGA) [5] are used to ensure authenticity in SeND. CGA alike regular IPv6 address has two 64-bit portions.
● Redirection: The methodology of redirection attack is almost similar to the impersonation attack. The attacker misdirects the target node or nodes attempting to connect to the destination nodes by directing to any other unsafe destination to capture the communication packets or interrupt the node communication. Attackers may also announce the change in router address, or network prefixes to interrupt the node communications.
The first 64 bits represents the network prefix and the second represents the IID, which is derived using the SeND specific CGA generation process. The augmented option fields of CGA in SeND includes Public Key,128-bit-modifier, 64-bit subnet prefix of the address and 8-bit collision count. The SeND uses two hash functions using the parameters given in the CGA option field. The HASH1 and HASH2 functions play a major role in CGA generation. The generations of CGAs involve determining the public key of the owner address, selecting the appropriate security-level (Sec) ranging from 0 to 7and generation of a random 128 bit modifier. Then it is subjected to SHA-1 hashing and is looped continuously with various values assigned to the modifier until 16 × Sec leftmost-bits of HASH2 equals zero. This final modifier value is again used along with the various other CGA parameters as the input to the HASH1. HASH1 is the leftmost 64-bit of the SHA-1 hash function.It concatenates the modifier, subnet, collision count and the public key fields of CGA options. HASH1 resultant is modified and used as the IID in CGA. The seventh bit of HASH1 is modified to represent whether the address is global or local. The eighth bit represents whether the address represents unicast or multicast groups. TheHASH1 uses a hash extension technique using the Security Parameter (Sec) to decide the strength of the hash function. In CGA Sec is used as the first 3 bits of the IID. The CGA generation process is represented in figure 3.
During the verification process, the CGA options in the ICMPv6 packets are first extracted to calculate the HASH1 and HASH2 values. At first the bit sequence (excluding seventh and eighth bit) of the calculated HASH1 is compared with the IID. The SeND daemon then compares the 16 x Sec leftmost bits of HASH2 to zero. If any of these comparisons fails, the packet processing is stopped and the packet is discarded. Following these verification the digital signatures are verified.The RSA signature method helps to prove whether the public key corresponds to the private key of the packet sender. This binds the CGA and the key pair of the same origin.Even though authentication is well addressed by CGA and RSA, authorization is still a challenging issue in SeND. Hence this scheme is prone to rouge router attacks like poisoned router, malicious router, default router kill etc.(discussed in table 2).
Both packet size and the computational intensity for CGA generation in SeND is a major concern for MANETs. In general,MANETs are at risk as it would be easy for an attacker to flood the network with large, expensive-to-process packets, consuming bandwidth, resources and energy, resulting in limited responsiveness of the nodes. Due to the frequent exchange of packets during merging and partitioning of MANETs, SeND employs reconfiguration of nodes that would greatly increase the resource consumption of nodes.
A SeND context is an internal data structure that stores information about the interface,options, prefixes, and keys used by packets.So for every packet that fails or pass the verification process adds a context to the stored information, and hence adds unnecessary computation. The computational cost of a CGA generation, with a non-zero Sec value,increases the address configuration time. Even though there are many modifications suggested in SeND, these schemes couldn’t overcome the issues faced by the existing schemes. The privacy addresses generated in a scheme proposed by Narten et al. [7] used the Message Digest (MD5) on the message stored in a stable storage to retrieve the addresses. But these addresses can be easily predicted by tracking the file usage history. Bos et al. [8] proposed an analyzed optimal CGA generation, but the scheme is for infrastructure based networks and hence is not adopted for MANETs. Jiang[9] introduced an interactive method of address generation with DHCPv6, but the dynamic nature of MANETs restricted assigning dedicated services and interactive communication packets.

Fig. 3 CGA generation
The extended SeND [10] and windows based SeND [11], were not implemented and standardized because of the limitation of applicability. The cryptographic algorithms of SeND are extended or modified in many schemes [12-19] by replacing RSA with ECC and newly designed cryptographic algorithms to reduce the computational complexity of authentication. But as MANETs are provided with low resources, these schemes may drain the resources and hence are not applicable for MANETs. SAVI [20] scheme is a link-layer authentication protocol scheme which ensures the authenticity of the packets exchanged during autoconfiguration. But it fails to assure protection against other ND vulnerabilities.The surveys [21-23] on the existing schemes emphasize the requirement for a light weight and empirically strong CGA generation for resource constrained MANETs and is the motivation for the proposed work.
III. PROPOSED WORK
The SeND protocol designed to overcome the security threats during autoconfiguration has proven to face security and technical issues in MANETs (discussed in Section 2). The paper proposes an unpredictable random number based address generation using internal system states, for ensuring security of autoconfiguration with minimum resource consumption. The internal system states based address generation is an inspirational proposal of Hardware Volatile Entropy Gathering and Expansion(HAVEGE) [24]. Pseudo random numbers exhibiting high degree of randomness are needed for highly secured cryptographic algorithms.
A heuristic algorithm that relies on entropy gathered from unpredictable system events is proposed. This entropy gathering technique is used in pseudorandom number generator to generate the IID during autoconfiguration. The algorithm implements a hardware clock cycle counter to gather the entropy from the system states of the nodes. The system states are hardware mechanisms that improve performance of caches, branch predictors and external devices. These system states are not architectural, but volatile and cannot be directly monitored by the user and hence are used as source for highly random pseudorandom numbers.Since the system state includes thousands of internal volatile hardware states, it is impossible for the user to reproduce the generated bit sequences. Any attempt to indirectly gather the bit sequence triggers the internal state of the system and therefore, reproducing the bit sequences is virtually impossible. Although the proposed address generation method is a light weight scheme with fewer computations,it has proven compliance to all the security standards discussed in NIST statistical test suite [25]. The internal system states based address generation called as Light Weight Cryptographic Address Generation (LW-CGA) is a novel light weight autoconfiguration scheme designed to ensure high security and adaptability in MANETs.
3.1 Light weight cryptographic address generation (LW-CGA)
iv. Regeneration at regular intervals: The regeneration at regular interval is an option included for maintenance and security purposes. The option has been included to add the renumbering features.
The algorithmic steps are given below.
Step 1:The functionCLKREAD()is defined to read and return the hardware clock counter value of the node.
Step 2:Two concurrentSCROLLoperations are performed in parallel in a table of 4B. The table 1s twice the size of L1 data cache. If theSCROLLis random, then the probability of a hit in the cache is very close to 1/2 on each data reading from the table.
陈邦设强调,“我们在检验工作成效时,要以企业增效、员工增收、企业经营质量持续增长、企业团队能力持续提升为标准”。因为,只有合理、高效地进行企业人事管理,才能增加员工对企业的信任感;也只有这样,团队对企业文化的认同感才会转化为强大的力量,推动企业蒸蒸日上地发展。
Step 3:Two data dependent tests are introduced on iterations ofSCROLLto make its behavior depend on branch prediction information. For both branches, the probability of the branch being taken is 1/2 if the content of the table 1s random.
每个调类有15个单字,共有75个单字,为防止受试有不熟悉的字,75个单字提前打印以供受试熟悉。录音和语音分析软件为Praat,录音在安静环境中进行,每人相同字表都录音两次,3人均为一次性录完.
在中职教育以及旅游业快速发展的过程中,中职旅游专业教育也进一步扩张。当前,中职旅游管理专业已经慢慢发展成为较为成熟的发展体系,不过在教学过程中并没有彻底摆脱传统的灌输式教学模式,这样就导致培养的人才不能满足社会发展需要。因此,旅游业重点关注的问题是各院校如何培养适应社会需要的旅游管理专业人才。通过实践调查研究发现,我国当前在旅游管理专业人才培养以及教育改革方面的研究比较少,特别是在“互联网+”时代,更应该加强此方面的探索。
Step 4:TheSCROLLis iterated to the number of unrolled steps (y) for data reads from instruction cache. This maximizes the number of instruction blocks (and associated branch prediction information) extracted from the instruction cache on each operating system interrupts.
Step 5:The two distinct data read (Steps 3 and 4) acquired duringSCROLLperforms Exclusive-OR (XOR) in memory table. If memory table 1s directly read for random number generation, then an observer can follow up theSCROLLfor a while and try to guess the partial content of the table. XOR is used to hide the content of theSCROLLtable from any possible observer.
Step 6:The 64 bit Least Significant Bits(LSB) extracted from random bits of the output of the algorithm are used as IID for CGA generation.
3.1.1 System states for random number generation
The system states of the nodes are unpredictable 5olatile hardware states and are activated by the instruction cache and branch predictors.Any node with a processor can implement the algorithm and collect the system states. The volatile states of the nodes are influenced by the following components.
方法二:将a,b看成一元二次方程x2=3x-1的两根,用根与系数的关系分别求出a+b,ab的值代入式子得到18.

Fig. 4 Algorithm of CGA generation in LW-CGA
i. DATA Translation Look-aside Buffer(TLB): The TLB buffer is a table consisting of information of the pages in the memory that are accessed by the processor. Each entry of a page in the TLB possesses about 129 states which invoke system states. The LWCGA is constructed with a loop that access 128 pages of memory.
The various sub classes of attacks launched in the networks during autoconfiguration are also given in table 2. These attacks are launched in both infrastructure and ad-hoc networks with the ICMPv6 messages. The survey[3] states that most of the attacks launched in ad-hoc networks are still not addressed and exist as an open research area. The unique or unpredictable 1nterface identifier based address can reduce the chances of exposure to these attacks. But today there are many solutions available to alter the unique MAC addresses of the devices and hence it is impossible to assure uniqueness of MAC addresses. More over MANETs are dynamic, with frequent merging and partitioning; therefore setting a static policy and expecting it to uphold a secure state is unrealistic. Moreover the Neighbor Discovery(ND) was not designed to deal with security issues and is not suitable for MANETs. Secure Neighbor Discovery Protocol (SeND)[4] addresses few of these issues and it was targeted for infrastructure based networks. As MANETs are infrastructure-less multi-hop communication networks with high resource consumption, there are many technical issues for the implementation of SeND in MANETs.
iii. L1 Instruction Cache: The L1 instruction cache consists of 256 sets in which, each set possesses 7 possible states. The LW-CGA is made of a loop body that performs self-modifying paces over the level 1 instruction cache.
3.1.2 Regeneration options of LW-CGA
由图16可以获得faFM和waFM欧式空间点的坐标变换,faFM在Lv、Q方向的变动范围分别为-0.08 mm~0.08 mm和-0.1 mm~0.1 mm,waFM在Lv、Q方向的变动范围都为-0.2 mm~0.2 mm。
(2) The CGA based IPv6 addresses cannot be predicted by the attacker.
i. Regeneration on updated RA and NA: The RA and NA message contains new prefix advertisements or updates to indicate prefix-change or MANET merging or partitioning. So whenever an advertisement with new prefix is received the daemon calls REGENERATE( )
综上所述,再次定位CT2图像较首次定位CT1图像肺的体积增大,肿瘤靶区体积缩小,能够减小患肺及全肺受照射剂量,可减轻放疗副作用及保护正常器官,值得临床关注。
ii. Regeneration on interface status change:The option enables a new IID generation when a node enables a network interface.So when an interface is enabled state it will be configured with a new address even if the network-prefix remains the same. By default as in existing schemes, each node with multiple interfaces will be configured with different IIDs.
装配式建筑结构对住宅产业的发展和推动起到了很大的促进作用,这与日本政府的干预和大力支持是密不可分的:日本政府方面制定了一系列的建设住宅工业化方针,并建立了相应统一的标准。这样就解决了标准化与住宅多样化、复杂化之间的各种矛盾。通过在不断的探索和研究中,继续进一步的快速进步。
iii. Regeneration on user choice: The CGA generation can be explicitly invoked by the user based on his/her choice. This feature is added for testing purpose and entropy calculation on each generation.
The LW-CGA algorithm uses a heuristic algorithm to collect entropy of system states and generate a sequence of random number bits as IID. A hardware clock counter is used to gather the sequence of uncertainty of the system states. The entropy gathered from the system states are generated from the instruction cache and branch prediction structures. A function to read the hardware clock called CLKREAD( )is used and it verifies the difference with last read values. The counter INTERRUPTCOUNT is incremented by function CLKREAD( ) when the difference of the clock read is higher than a threshold level MAX indicating an interrupt between two successive reads. Throughout the algorithm,CLKREAD( )is called several times and the resultant is combined by XOR and shifts in an arrayENTROPY[ ].Since the entropy in the least significant bits (LSB)of the hardware clock counter is more than the most significant (MSB), the read value is combined with circular shift of the previously accumulated data for even diffusion of entropy throughout the arrayENTROPY [ ].The entropy collection loop runs until theINTERRUPTCOUNTreaches a predefined threshold.BUFFERSIZEis the size of the table used to gather the values of the hardware clock counter. At an instance the content of theENTROPY[ ]is saved and reinitialized to zero. The savedENTROPY[ ]is combined with a simple pseudorandom number generator. ADYNAMTABLE[]is used to record the two instants of updates in the singleENTROPY[ ]table.SCROLL[ ]is a memory table which is twice the size of the L1 Cache (discussed in Section 3.2.1 and is assumed in power of 2). TheSCROLL[ ]stores the resultant empirically strong random number which is assigned as the IID of the CGA addresses. The random bit sequence from the internal micro architectural status of a system and integration to the link local address makes the addresses unpredictable. The figure 4 shows the pseudocode of LW-CGA algorithm.
IV. EXPERIMENTAL EVALUATIONS
The LW-CGA and SeND autoconfiguration schemes are implemented in real networks for experimental evaluations. The flow chart of LW-CGA and SeND implementation is shown in figure 5.
4.1 Experimental set-up
● IID regeneration time is the time taken for the IID regeneration by CGA regeneration without key generation. The CGA regeneration of SeND requires a HASH1 calculation alone, whereas only a random number generation in LW-CGA.
The LW-CGA as like SeND uses the RSA based key (1024 bits) exchange scheme during the first CGA generation. But during regeneration of CGA (caused by node mobility or change in network gateway), the keys are not regenerated but verified for authenticity. In SeND scheme, the HASH1 alone is recomputed during CGA regeneration. The SeND evaluation of Sec values higher than 1are not validated as it is proven to be impractical [23].The following parameters are used for evaluations.
● IID generation time is the total time duration for the generation of public key, their verification and computation of CGA followed by IID configuration
如今,因为担心夫人摔着,潘际銮院士不再骑车载她了,而是改为手牵手,去菜场、去学校、去访学……时时刻刻不分离。潘际銮是南昌大学的老校长,南昌大学有一条“际銮路”,老两口回南昌大学故地重游,牵手走在这条路上,也被学生拍到了。
新的有机硅树脂工厂将位于陶氏在张家港的有机硅一体化生产基地。该基地坐落于江苏扬子江国际化学工业园,于2006年开工建设,2010年投产,占地近百万平方米,是中国最大的有机硅生产基地。
The Linux kernel version of 2.6.34 is used in nodes for the implementation of the LW-CGA and SeND autoconfiguration schemes. The experimental analysis can be interrupted by the scheduler as its time is accounted for the measurements. Hence single mode Linux kernels are used for experimentations. The SLAAC implementation of IPv6 is modified for the implementations. The modified kernel provides several sys-controls which can be read and written to and by user-space programs,controlling the operation of IPv6 privacy extensions. SeND-CGA project developed and maintained by Huawei Technologies Corp.and BUPT (Beijing University of Post and Telecommunications) [26], is implemented as a modified kernel and invoked with a daemon.The LW-CGA is an extension of HAVEGE[24] and the same is implemented as a modified kernel. The kernel sys-controls are adjusted to characterize MANETs. No changes pertaining to IPv6, ICMPv6, and NDv6 parameters were made, so as to preserve the other network layer features. SeND is compiled with the minimal options required to compile on Linux and is used for the testing.
● Entropy is the measure of randomness in a closed system. The entropy of a random variable X with probabilities pi, …, pnis defined as

Fig. 5 Flow Chart of LW-CGA and SeND Implementations
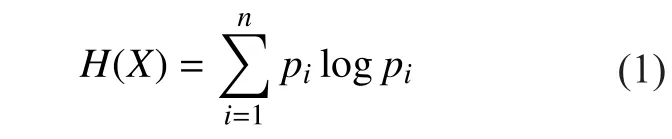
The NIST Test Suite [25] is a statistical package with 15 tests to test the randomness or entropy of the binary sequences generated by the algorithms. We have conducted NIST tests to test the randomness of binary sequences generated by SHA-1 in SeND and random number generator in LW-CGA. These tests focus on a variety of non-randomness that could exist in a sequence. Various statistical tests were applied to the bit sequence generated by LW-CGA and SeND to compare and evaluate the randomness. The randomness of bit sequences was characterized and described in terms of probability. These statistical tests were formulated to test a specific null hypothesis (H0). The null hypothesis was the sequence being tested is random. Associated with this null hypothesis is the alternative hypothesis (Ha), for which the sequence is not random. For each test, the decision declares the acceptance or rejection of null hypothesis,i.e., whether the sequence generated is truly random or not. In each test, a relevant randomness statistic was chosen to determine the acceptance or rejection of the null hypothesis
A mathematical method was used to determine the theoretical reference distribution of this statistic under null hypothesis. A critical value was selected from this reference distribution (typically, this value is “far out” in the tails of the distribution say, out at the 99% point). During the tests, the statistic value computed on the bit sequence was compared to the critical value. If the test statistic value was higher than the critical value, the null hypothesis was rejected. Otherwise, the null hypothesis was accepted. For these tests, the probability of randomness determined as P-value was compared with the derived significant level (α). If P-value ≥α, then the bit sequence was considered random and if it was not so, then it was considered non-random.Typically, α was chosen in the range 0.001 and 0.01.
Fifteen tests of NIST Statistical Test Suite have significant purpose to confirm the randomness of the bit sequence. The Block and Frequency Monobit tests determine whether the number of ones and zeros in a sequence are approximately the same as expected for a truly random sequence. The Binary Matrix Rank Test checks for linear dependence among fixed length substrings of the original sequence. The Longest Run Test determine whether the length of the longest run of ones within the tested sequence is consistent with the length of the longest run of ones as expected in a random sequence. The Run Test determines whether the oscillation between ones and zeros of various lengths is as expected for a random sequence. Spectral Discrete Fourier Test (DFT) detects repetitive patterns in the tested sequence to indicate a deviation from the assumption of randomness. Non-Overlapping Template Matching Test checks whether too many occurrences of a given non-periodic pattern occur in tested sequence. Overlapping Template Matching Test determines the number of occurrences of pre-specified target strings. It uses the same m bit window as in Non-Overlapping Template Matching Test, to search for a specific m bit pattern (B). The difference is that when the pattern is found, the window slides only one bit before resuming the search.
唐诗的模糊美初探 ……………………………………………………………… 王华琴,张青华,张 红(5.76)
The Maurer’s Universal Test detects whether the sequence is significantly compressed without loss. The Linear Complexity Test determines whether the sequence is complex enough to be considered random. The Serial Test determines whether the number of occurrences of the 2m m bit overlapping patterns is approximately the same as expected for a random sequence. Approximate Entropy Test compares the frequency of overlapping blocks of two consecutive lengths (m and m+1) against the expected result for a random sequence. The Cumulative Sum (cusum) Test determines whether the cumulative sum of the partial sequences in the sequence is too large or too small relative to the expected behavior of cumulative sum for random sequences. The Random Excursion Test determines whether the number of visits to a particular state within a cycle deviates from that expected for a random sequence. The Random Excursion Variant Test detects deviations from the expected number of visits to various states in random scroll.
4.2 Experimental results
The CGA generation time of SeND and LWCGA is measured with an internal counter clock. The experimental results of more than 100 samples have been averaged to validate the analysis. The result shown in table 4 concludes that the LW-CGA takes less time when compared to SeND. The key generation time is almost the same for both the schemes, but the verification and CGA generation time is high in SeND which contributes to extra time consumption.
该水库防渗工程施工结束后,经蓄水检验,主副坝下游坡原潮湿散浸现象完全消失;据坝后量水三角堰量测,主坝为0.33L/s,副坝为0.015L/s,相比除险加固前均大为减少,达到除险加固目的。
The CGA generation time for Sec=1 is greater than Sec=0 of SeND. The difference in time is to generate the modifier that requires further time for calculating HASH2 values until the 16 x Sec leftmost bits are zeros. Hence at Sec=1 the key generation followed by verification, HASH1 and HASH2 computation for CGA generation time contribute to the total IID generation time. At Sec=0, the key generation time, verification time and HASH1 computation time for CGA generation time only contribute to the total IID generation time. The HASH1 and HASH2 computation involves the use of public key as a parameter;hence these computations are sequential and are interdependent (discussed in Section 2).The LW-CGA uses a key exchange scheme for verification and validation of the keys generated. The CGA generation scheme in LW-CGA is not dependent on the keys and involves random bit generations from entropy gathered from system states. LW-CGA scheme uses a less computational intensive method for CGA generation and hence the time taken for the IID generation is comparatively very less compared to the SeND.
The CGA regeneration time of SeND at Sec=0 and Sec=1 does not involve key exchanges and verifications, but computation of HASH1. The LW-CGA just recertifies the authenticity of the keys and regenerates the random number. The results conclude that the time required for CGA generation in LW-CGA is very less when compared to SeND.
The security of the schemes can be evaluated with the entropy of the algorithms. The security flaws of SHA-1 have invoked many on-going works in the CGA and SeND maintenance working group in IETF. These have issued the recommendation of SHA-2, SHA-256 etc. But these schemes are highly computational intensive and fail in resource constrained environments. The SHA-1 in SeND and random number generator in LW-CGA are tested using the NIST statistical test suite [25].The recommended statistical tests are done to evaluate the performance in security algorithms. For a p-value ≥ 0.001, the sequence is considered to be random with a confidence of 99.9% or else non random with a confidence of 99.9%. The analysis shows that random number generator of LW-CGA performs well in cryptanalysis.
图5是原始WENO-CU6-M2格式及其改进A和改进B在400个网格点上计算得到的t = 0.038时刻的密度和速度曲线及局部放大. 它们在图5(a)和图5(b)中初看起来没有差别, 但在图5(c)和图5(d)的局部放大图中可观察到, 原始WENO-CU6-M2格式的密度曲线和x≈0.865附近的激波出现了微小的伪波, 而两种改进格式消除了这些伪波.
V. CONCLUSION AND FUTURE WORKS
SeND uses RSA and SHA-1 implementation for ensuring privacy enabled autoconfiguration. The generation time and the computational intensity of CGA make SeND implementation impractical for MANETs. Moreover the improved security level of SeND varying from 0 to 7 worsens the computational intensity and battery consumption in wireless devices. Thepaper proposed a light weight cryptographic scheme called LW-CGA that ensures high security with minimal and faster computations.The random number generations in the scheme uses an entropy gathering algorithm from the system states and are independent of the keys.The bit sequences generated by the algorithm are impossible for guessing and cannot be even monitored by the system users. Hence the scheme is highly random and assures security.It’s proven that the usages of LW-CGA satisfies all the characteristic requirements of cryptographic algorithms and are more suitable for constrained devices like PDA and Tablet PC.The schemes are evaluated with real time implementation to study CGA generation using SHA-1 in SeND and random number generation in LW-CGA. The experimental results show significantly reduced address generation time while using LW-CGA. The NIST statistical tests demonstrate that a higher security is assured with LW-CGA without the need for a high cost algorithm. Future works of the authors mainly focus on more light weight techniques for privacy enabled autoconfiguration in MANETs.

Table IV IID generation time of SeND (at Sec=0 and Sec=1) and LW-CGA

Table V IID regeneration time of SeND (at Sec=0 and Sec=1) and LW-CGA

Table VI NIST statistical tests on SeND and LW-CGA
[1] T. Narten et al., “Neighbor Discovery for IP Version 6 (IPv6),” RFC 4861, Sept. 2007; htp://tools.ietf.org/ html/rfc4861.
[2] S. Thomson, T. Narten, and T. Jinmei, “IPv6 Stateless Address Autoconfiguration,” RFC 4862,Sept. 2007; htp://tools.ietf.org/html/rfc4862.
[3] P. Nikander, J. Kempf, and E. Nordmark, “IPv6 Neighbor Discovery (ND) Trust Models and hreats,” RFC 3756, May 2006, htp://tools.ietf.org/html/rfc3756.
[4] J. Arkko et al., “SEcure Neighbor Discovery(SEND),” RFC 3971, Mar. 2005, htp://tools.ietf.org/html/rfc3971.
[5] T. Aura, “Cryptographically Generated Addresses (CGA),” RFC 3972, Mar. 2005, htp://tools.ietf.org/html/rfc3972.
[6] Conta, S. Deering, and M. Gupta, “Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (IPv6) Speciication,”RFC 4443, Mar. 2006, htp://tools.ietf.org/html/rfc4443.
[7] T. Narten, R. Draves, and S. Krishnan, “Privacy Extensions for Stateless Address Autoconiguration in IPv6,” RFC 4941, Sept. 2007, htp://tools.ietf.org/html/ rfc4941.
[8] J.W. Bos, O. Ozen, and J.-.P Hubaux, “Analysis and Optimization of Cryptographically Generated Addresses,” LNCS 5735, Springer, pp. 17–32,2009.
[9] S. Jiang, “Analysis of Possible DHCPv6 and CGA Interactions,” draft, 12 Mar. 2012, htp://tools.ietf.org/html/drat-ietf-csi-dhcpv6-cga-ps-09.
[10] S. Chiu and E. Gamess, “A Free and Didactic Implementation of the SEND Protocol for IPv6”,Machine Learning and Systems Engineering, vol.68, S.-I. Ao, B. Rieger, and M.A. Amouzegar, eds.Springer, pp. 451–463, 2010.
[11] H. Raiee, A. AlSa’deh, and C. Meinel, “WinSEND:Windows Secure Neighbor Discovery,” 4th Int’l Conf. Security of Information and Networks(SIN 11), ACM, pp.243–246, 2011.
[12] Kukek and B.A. Zeeb, “Native Send Kernel API for BSD,” 2010; htp://people.freebsd.org/~anchie/SeND_AsiaBSDCon_2010.pdf.
[13] T. Cheneau, A. Boudguiga, and M. Laurent,“Significantly Improved Performances of the Cryptographically Generated Addresses thanks to ECC and GPGPU,” Computers & Security, vol.29, no. 4, pp. 419–431, 2010.
[14] S. Guangxue et al., “A Quick CGA Generation Method,” 2nd Int’l Conf. Future Computer and Communication (ICFCC), IEEE, pp. V1-769–V1-773, 2010.
[15] S. Jiang and S. Xia, “Configuring Cryptographically Generated Addresses (CGA) Using DHCPv6,” 11 Apr. 2012, http://tools.ietf.org/html/draft-ietf-dhc-cga-config-dhcpv6-02.
[16] T. Aura and M. Roe, “Strengthening Short Hash Values,” http://citeseerx.ist.psu.edu/viewdoc/summary?doi 10.1.1.145.7681
[17] Gont, F., and W. Liu, “A Method for Generating Semantically Opaque Interface Identifiers (IIDs)with the Dynamic Host Configuration Protocol for IPv6 (DHCPv6)”, RFC 7943, 2016.
[18] Shah JL, “A novel approach for securing IPv6 link local communication”, Information Security Journal: A Global Perspective, Vol. 22, 1-5, 2016.
[19] Rehman SU, Manickam S, “Novel Mechanism to Prevent Denial of Service (DoS) Attacks in IPv6 Duplicate Address Detection Process”, International Journal of Security and Its Applications,Vol. 10(4), 143-54, 2016.
[20] Supriyanto, Iznan Husainy Hasbullah, Raja Kumar Murugesan, Sureswaran Ramadass, “Survey of Internet Protocol Version 6 Link Local Communication Security Vulnerability and Mitigation Methods”, IETE Technical Review, Vol 30,2013.
[21] Minoli, Daniel, and Jake Kouns, “Security in an IPv6 environment”, CRC Press, 2016.
[22] Rehman SU, Manickam S, “Significance of duplicate address detection mechanism in IPv6 and its security issues: A survey”. Indian Journal of Science and Technology, 8(30), 2015.
[23] A.AlSa’deh and C. Meinel, “Secure Neighbor Discovery: Review, Challenges, Perspectives,and Recommendations”, IEEE Security & Privacy Magazine, Vol. 10, no. 4, pp. 26 –34, August 2012.
[24] Seznec, N. Sendrier, “HAVEGE: a user-level software heuristic for generating empirically strong random numbers”, ACM Transaction on Modeling and Computer Simulations (TOMACS), Vol.13, Issue 4, October 2003.
[25] National Institute of Standards and Technology,NIST Special Publication 800-22rev1a, “A Statistical Test Suite for the Validation of Random Number Generators and Pseudo Random Number Generators for Cryptographic Applications”,http://csrc.nist.gov/groups/ST/toolkit/rng/documents/SP800-22rev1a.pdf, April 2010.
[26] https://code.google.com/p/ipv6-send-cga/downloads/list
猜你喜欢
杂志排行
China Communications的其它文章
- An Iterative Detection/Decoding Algorithm of Correlated Sources for the LDPC-Based Relay Systems
- Homomorphic Error-Control Codes for Linear Network Coding in Packet Networks
- Polar-Coded Modulation Based on the Amplitude Phase Shift Keying Constellations
- A Privacy-Based SLA Violation Detection Model for the Security of Cloud Computing
- An Aware-Scheduling Security Architecture with Priority-Equal Multi-Controller for SDN
- A Flow-Based Authentication Handover Mechanism for Multi-Domain SDN Mobility Environment
