Fuzzy Logic Based UAV Suspicious Behavior Detection
2016-02-09,,
, ,
College of Civil Aviation, Nanjing University of Aeronautics and Astronautics, Nanjing 211106, P.R.China
Fuzzy Logic Based UAV Suspicious Behavior Detection
SunRui*,ZhangYucheng,HuMinghua
College of Civil Aviation, Nanjing University of Aeronautics and Astronautics, Nanjing 211106, P.R.China
(Received 18 January 2016; revised 20 June 2016; accepted 5 July 2016)
In recent years, unmanned air vehicles (UAVs) are widely used in many military and civilian applications. With the big amount of UAVs operation in air space, the potential security and privacy problems are arising. This can lead to consequent harm for critical infrastructure in the event of these UAVs being used for criminal or terrorist purposes. Therefore, it is crucial to promptly identify the suspicious behaviors from the surrounding UAVs for some important regions. In this paper, a novel fuzzy logic based UAV behavior detection system has been presented to detect the different levels of risky behaviors of the incoming UAVs. The heading velocity and region type are two input indicators proposed for the risk indicator output in the designed fuzzy logic based system. The simulation has shown the effective and feasible of the proposed algorithm in terms of recall and precision of the detection. Especially, the suspicious behavior detection algorithm can provide a recall of 0.89 and a precision of 0.95 for the high risk scenario in the simulation.
UAV; suspicious behavior detection; fuzzy logic; decision making
0 Introduction
UAVs have been increasing rapidly within recent years in military and civil applications, especially for surveillance, reconnaissance and search/destroy missions. The arbitrary flying UAVs will bring potential safe threat to some important regions, such as the airport or other military base areas. In addition, with the great advantages over the manned aerial vehicles, the UAVs could be used for criminal or terrorist purposes. Therefore, it is crucial to detect suspicious behaviors of incoming UAVs for preventing the possible threats and ensuring the safety of the important regions. Designing an advanced algorithm to extract the real-time UAV behaviors from the measurement of UAV on-board sensors is essential for recognition of the suspicious UAV behaviors.
Some previous research has addressed the issue related to UAV behaviour detection. Lin et al.[1]proposed a Mahalanobis distance based anomalies behaviours detection algorithm in UAV. Mitchell and Chen[2]introduced an adaptive behavior rule-based UAV intrusion detection based on the comparison of the current UAV states with the defined specified safe states. Khalastchi et al.[3-4]proposed an online data driven approach for the UAV anomaly data detection. Birnbaum et al.[5]introduced a prototype of UAV behaviour monitoring system based on the judgement of the estimation for the real-time flight data, airframe and controller parameters. From the discussion of related literatures, most of the research is still on the preliminary stage. Furthermore, the assumptions for most of the current approaches are too ideal and thus not adaptive for practical applications. Moreover, current research only focuses on the anomaly or non-anomaly detection, while none of the research has mentioned different levels of suspicious behavior classification, which is critical for the UAV behavior detection.
In this paper, a novel fuzzy logic based UAV suspicious behavior detection algorithm has been presented. Fuzzy logic variables define a truth value that ranges in degree between 0 and 1 instead of the traditional logic theory, where only true or false is defined for the binary sets. Fuzzy logic is able to deal with the concept of partial truth, where the truth value is ranging between completely true and completely false. The three stages of the fuzzy logic system are: Fuzzification, fuzzy inference and defuzzification[6]. The contributions of the paper can be illustrated as follows: (1) A newly designed fuzzy logic based UAV behavior grade classification algorithm by fusion the on-board sensor data, location information and expert knowledge information; (2) Simulations are presented to demonstrate the success application of the different levels of suspicious behavior detection algorithm based on the designed scenarios.
1 Fuzzy Logic Based Model Design
The flowchart of the system framework for the fuzzy logic based UAV suspicious behavior detection algorithm is illustrated in Fig.1.
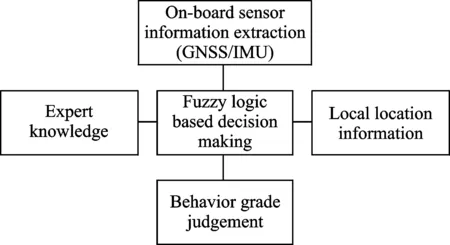
Fig.1 Structure of the behavior detection algorithm
The assumption for this paper is as follows. The incoming commercially civilian UAV devices are with several open ports by default and therefore, could be accessed remotely by a third party[7]. Based on this assumption, the real-time data from on-board sensors of the incoming UAVs could be extracted. The global positioning system (GPS) senor and inertial measurement unit(IMU) sensor output information, including the UAV positioning and dynamic information, is used for determing the UAV status. The output information of the GPS/IMU sensors is then to feed the fuzzy logic based decision making system, which is supported by the expert knowledge information and local map information. Finally, different risk levels of the UAV behavior are output based on the proposed algorithm.
The first input of fuzzy logic parameter is the heading velocity of the UAV, which is extracted from the GPS/IMU integrated results based on the Kalman filter. The fuzzy values are defined to be low (L), medium (M) and high (H). The second input of fuzzy logic parameter is the region of the UAV located, which is extracted from the Kalman filter estimated positioning results. The region type is designed by the scenario. The fuzzy values are defined to be non-interest (NI), ambiguous (A), high-Interest (HI). The fuzzy output parameter is the risk, which is defined to be Low (L), Medium (M) and High (H). The designed membership function of fuzzy inputs and outputs are illustrated in Fig.2 and the corresponding fuzzy rules for the fuzzy logic system are in Table 1 and the surface view of the fuzzy rules is in Fig.3. It is indicated that as the increase of the velocity and interest level of the region, the risk level of the UAV behavior will increase. In the following section, the simulation scenarios are designed based on the defined fuzzy logic parameters and rules to test the effectiveness of the proposed algorithm.
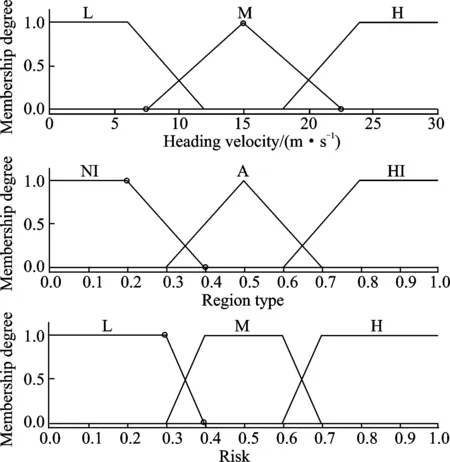
Fig.2 Membership functions for the fuzzy inputs and outputs
Table 1 Fuzzy rules for the fuzzy inference system based UAV dangerous behavior detection
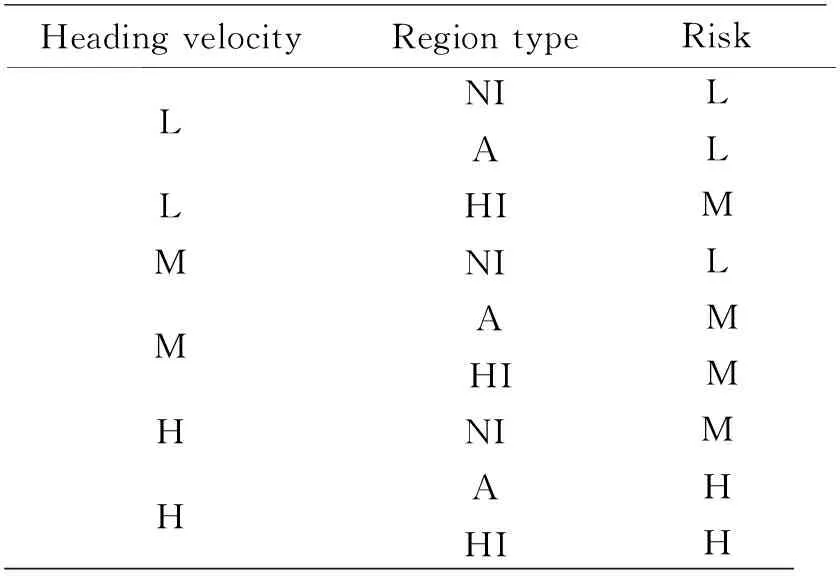
HeadingvelocityRegiontypeRiskLNILALLHIMMNILMAMHIMHNIMHAHHIH
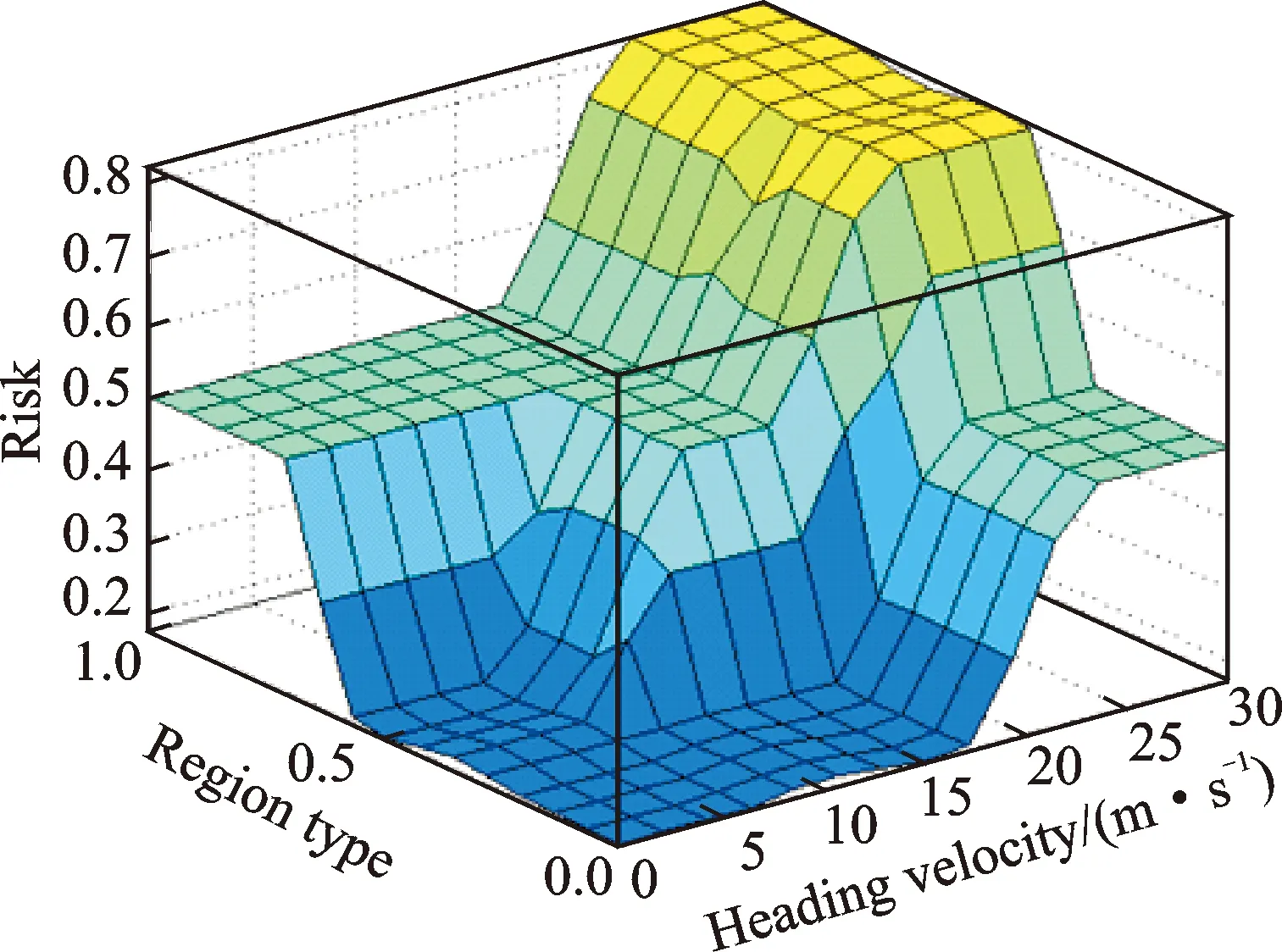
Fig.3 Surface view of the fuzzy rules
2 Numerical Simulation
This section presents the numerical simulation scenario for the flying UAV. The simulated UAV starts to approach the military base and then leaves the place of interest based on the designed route. The simulation time is about 140 s and the simulated UAV′s trajectory includes the behaviors with different heading velocities towards the different level of place of interest. Fig.4 shows the region of interest for the designed scenario. The route of the UAV is from the non-interest area to the less interest area and then to the high interest area and finally flies out to the non-interest area again. The designed flying velocity is changing from around 15 m/s to 30 m/s, which is an achievable flying velocity for the commercial UAV. The red region is the designed military base, which is not allowed for entering. The region with blue color is designed for the high interest region. The flying UAVs in this region may results in the potential threats to the base safety. The region with green color is considered as the less interest area. The fuzzy values of the region type for the UAV′s positions are calculated in three steps. Firstly, the position of the UAV′s real time location is calculated to match with the simulated map information for the determination of the UAV′s location in the region. Secondly, calculate the distance between the UAV′s location and nearest region border. Finally, based on the computed distance between the location and nearest region border, normalize the distances for all of the positioning points in the located region. The simulation is based on the Matlab and Simulink. The UAV motion model is based on the constant turn rate and velocity (CTRV) model, as it has been proved to perform reasonable estimations for the vehicle dynamic states[8]. The reference risk level in the simulation is the predefined risk level for the UAV trajectory from the expert knowledge. The estimated risk level output from the designed fuzzy logic based behavior detection is compared with the reference to evaluate the performance of the proposed algorithm.
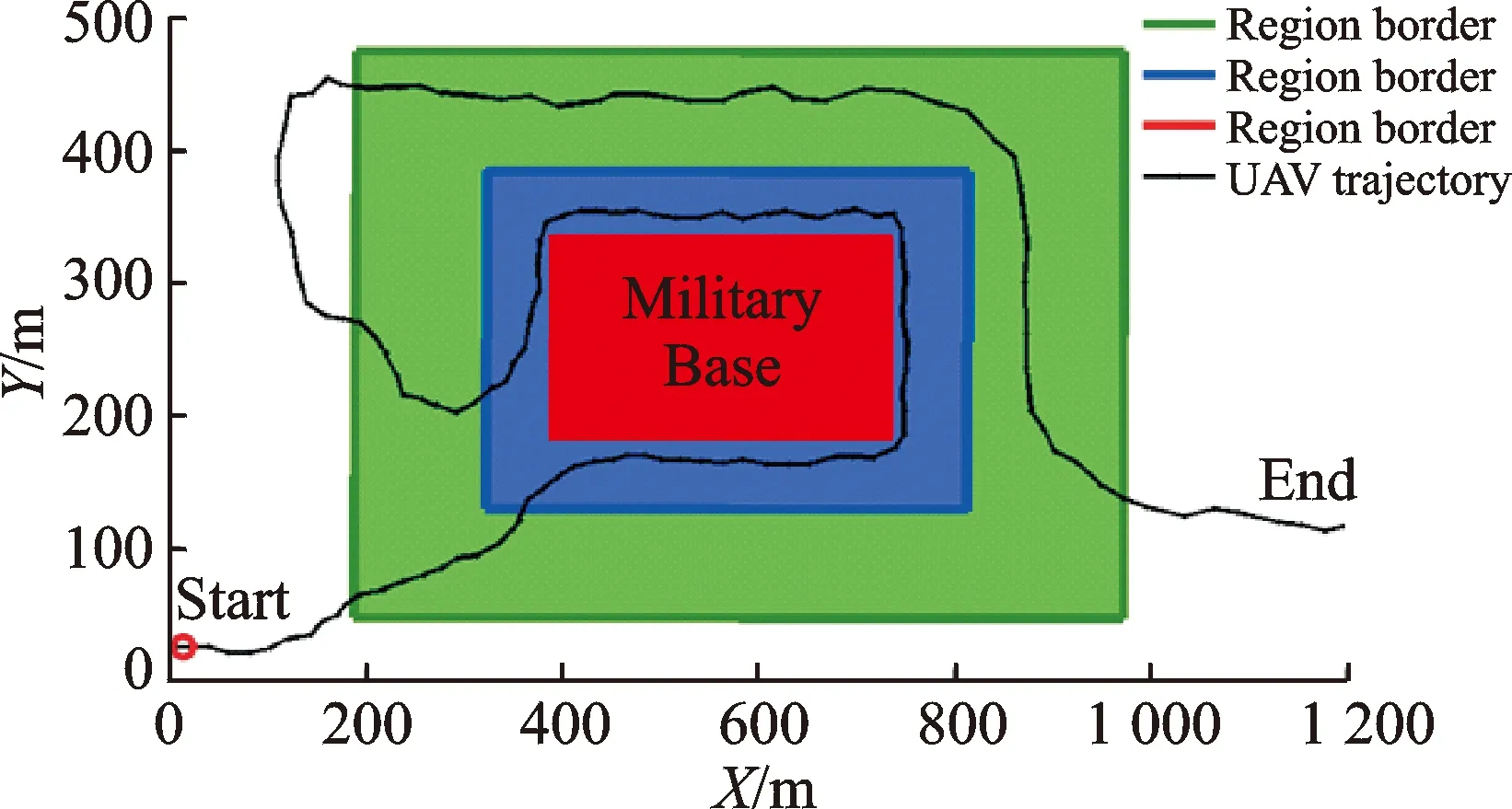
Fig.4 Simulated UAV trajectory and region of interest for the designed scenario
Fig.5 shows the simulation results for the designed fuzzy logic based UAV dangerous behavior detection algorithm. The values of input velocity and region type with the corresponding output risk level has been presented. It is obviously that output risk level is identified as ″High″ during 10 s to 80 s, in which the UAV is flying in the blue region with high interest. Afterwards, during the time interval form 80 s to 100 s, the UAV is heading to the less interest area, which is corresponding to the drop risk level as indicated in the figure. The risk level is continuously indicated as medium when the UAV is flying in the green region and dropped dramatically after it entering the non-interest region.
Recall and precision are two of the parameters proposed to quantify the performance of the proposed algorithm. Recall is the percentage of correct detected activities in relation to the number of total known activities and precision is the percentage of the correct activities in relation to the total number of detected activities by the algorithm.
The recall and precision can be expressed as
(1)
(2)
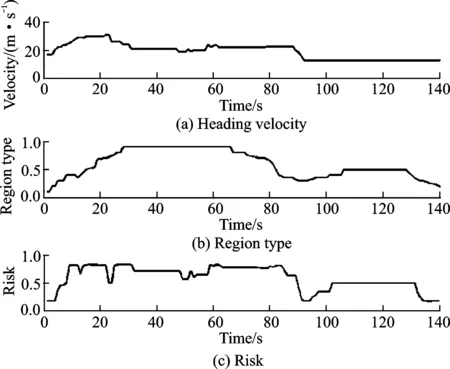
Fig.5 Simulation results of the designed fuzzy logic based UAV dangerous behavior detection algorithm
The performance evaluation for the low risk scenario, medium risk scenario and high risk scenario are presented in Table 2. It is shown that the proposed algorithm has performed the highest recall and precision for the high risk scenario, followed by the low risk scenario. The medium risk scenario provides the least satisfactory results. The reason for the worst performance of the medium risk scenario is due to the insufficient accuracy of the positioning estimations for the UAV during the border of the region based on the on-board navigation sensors outputs.
Table 2 Performance evaluation for the simulated UAV trajectory
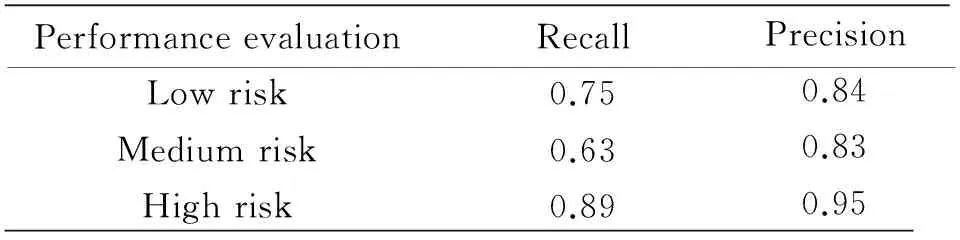
PerformanceevaluationRecallPrecisionLowrisk0.750.84Mediumrisk0.630.83Highrisk0.890.95
3 Conclusions
A novel UAV dangerous behavior detection algorithm has been presented in this paper. This study exploits the fuzzy logic based algorithm to classify the UAV behaviors in different risk levels. The performance of the algorithm developed in this paper has been demonstrated in the simulation based on the designed scenarios. The simulation results have shown the effectivness of the designed dangerous behavior detection. Future work will involve collection filed data in different real scenarios and evaluate the designed algorithm in different field situations. The location choice, region level definition and the expert knowledge extraction for the UAV behaviors are the critical issues may be proposed in the field test[9-11].
Acknowledgement
This study is supported by the Fundamental Research Funds for the Central Universities(No. NJ20160015).
[1] LIN R, KHALASTCHI E, KAMINKA G A. Detecting anomalies in unmanned vehicles using the mahalanobis distance[C]∥Robotics and Automation (ICRA), 2010 IEEE International Conference Anchorage. AK: IEEE,2010: 3038-3044.
[2] MITCHELL R, CHEN R. Adaptive intrusion detection of malicious unmanned air vehicles using behavior rule specifications[J]. Systems, Man, and Cybernetics: Systems, IEEE Transactions on, 2014, 44(5): 593-604.
[3] KHALASTCHI E, KAMINKA G A, KALECH M, et al. Online anomaly detection in unmanned vehicles[C]∥The 10th International Conference on Autonomous Agents and Multiagent Systems—Volume 1. International Foundation for Autonomous Agents and Multiagent Systems, Taiwan:AAMAS,2011: 115-122.
[4] KHALASTCHI E, KALECH M, KAMINKA G A, et al. Online data-driven anomaly detection in autonomous robots[J]. Knowledge and Information Systems.Taiwan: AAMAS, 2015, 43(3): 657-688.
[5] BIRNBAUM Z, DOLGIKH A, SKORMIN V, et al. Unmanned aerial vehicle security using recursive parameter estimation[C]∥IEEE 2014 Conference on Unmanned Aircraft Systems (ICUAS).Colorado, USA: IEEE, 2014: 692-702.
[6] LECCE V D, CALABRESE M. Experimental system to support real-time driving pattern recognition[C]∥Advanced Intelligent Computing Theories and Applications with Aspects of Artificial Intelligence, International Conference on Intelligent Computing.Shanghai, China:ICIC, 2008:1192-1199.
[7] PEACOCK M, JOHNSTONE M N. Towards detection and control of civilian unmanned aerial vehicles[C]∥2013 Australian Information Warfare Conference.Perth, Australia:Edith Cowan University,2013:9-15.
[8] TSOGAS M, POLYCHRONOPOULOS A, AMDITIS A. Unscented Kalman filter design for curvilinear motion models suitable for automotive safety applications[C]∥2005 International Conference on Information Fusion.Philadelphia, USA:IEEE,2005:1295-1302.
[9] GAO Yanhui, ZHU Feifei, ZHANG Yong.Wind estimation for uav based on multi-sensor information fusion[J].Transactions of Nanjing University of Aeronautics and Astronautics,2015,32(1):42-47.
[10]YUAN Suozhong, ZHEN Ziyang, JIANG Ju. Guidance and control for UAV aerial refueling docking based on dynamic inversion with L1 adaptive augmentation[J]. Transactions of Nanjing University of Aeronautics and Astronautics, 2015,32(1):35-41.
[11]HUANG Daqing, XU Cheng, HAN Wei. UAV velocity measurement for ground moving target[J]. Transactions of Nanjing University of Aeronautics and Astronautics, 2015, 32(1):9-15.
Dr. Sun Rui joined the College of Civil Aviation at Nanjing University of Aeronautics and Astronautics in 2015 as a Lecturer in Air Traffic Management (ATM). She received her Ph.D. degree in Intelligent Transportation Systems (TIS) from Imperial College London, UK and Master′s degree in Satellite Positioning Technology from the University of Nottingham, UK. Dr. Sun′s research interests span a variety of aspects of intelligent transport systems and services (ITSS), integrated GNSS and other location sensors for road transport, Air traffic management (ATM), ubiquitous computing and advanced filtering technologies. Dr. Sun is the memeber of Royal Institute of Navigation (RIN) and also is the reviewer of many top journals, such as Journal of Intelligent Transportation Systems, Expert System with Applications, Journal of Location Based Services etc.
Mr. Zhang Yucheng received B.S. degree in Air Traffic Management from Nanjing University of Aeronautics and Astronautics in 2015 and currently a postgraduate in air traffic management.
Prof. Hu Minghua is the dean of college of civil aviation and his research is focused on air traffic management and traffic planning.
(Executive Editor: Zhang Bei)
TN925 Document code: A Article ID: 1005-1120(2016)06-0721-05
*Corresponding author, E-mail address:rui.sun@nuaa.edu.cn. How to cite this article: Sun Rui, Zhang Yucheng, Hu Minghua. Fuzzy logic based UAV suspicious behavior detection[J]. Trans. Nanjing Univ. Aero. Astro., 2016, 33(6):721-725. http://dx.doi.org/10.16356/j.1005-1120.2016.06.721
杂志排行
Transactions of Nanjing University of Aeronautics and Astronautics的其它文章
- A Sequential Adaptive Method for Enhancing DOA Tracking Performance
- A Directional Differential-Fed UWB Antenna with Stable Radiation Pattern
- Numerical Simulation of An Axial Flow Fan with Proper Aft Fins for Floating Wind Turbines Model Test
- Capacity Analysis on Distributed Antenna System with Imperfect CSI over Rayleigh Fading Channel
- Acknowledgement to Reviewers
- TRANSACTIONS OF NANJ ING UNIVERSITY OF AERONAUTICS AND ASTRONAUTICS
