Access Control Policy Analysis and Access Denial Method for Cloud Services
2013-07-14ChiLunLiu
Chi-Lun Liu
1. Introduction
Cloud computing is an important trend in the Internet and computer technologies. In the emerging cloud computing model, servers can be dynamically provisioned and configured to deliver services in a scalable manner[1].In this model, personal applications and data are kept not only on the personal computers of users, but also in the cloud operated by a could computing service provider.Since cloud computing service providers rarely know their users in advance, assigning user roles in access control policies is difficult[2]. Therefore, developing a new access control mechanism for the new context of cloud computing is an important theoretical and practical issue.
The business use of cloud computing has two essential characteristics: the payment status and service level agreement. The payment status can be defined as an accounting record of one stage in the payment process used by cloud providers. In practice, cloud computing access control models usually consider service accounting records of cloud computing providers[2]. Cloud computing service providers often use a pay-per-use strategy to charge service fees. In contrast, charges in the pay-per-use strategy are based on the quantity used[3]. The above discussion indicates that the payment status for service fees is important for cloud access control.
A service level agreement (SLA) is a service contract that defines the level of service and controls the use of computing resources[2]. Cloud computing service providers generally use an SLA to guarantee the service level that the enterprise has committed to provide[3]. An SLA should also be considered in cloud computing access control models[2].
To address cloud computing business characteristics and access control requirements, this work proposes an access control method based on the payment status and service level agreement for the personal data storage. The proposed access control method comprises policy and requirement metadata, policy analysis rules, and access denial rules. The proposed metadata reveal what information should be considered in the access control policy and specify the user requirements. For example, a policy metadata comprises four elements: the payment status, access permission, service level agreement, and cloud computing service. An example of an access control policy is: the paid (payment status) user can access (access permission) a 10 G (service level agreement) personal backup cloud service (cloud computing service). The proposed policy analysis rules reveal redundant or conflicting policies. The proposed access denial rules also inhibit illegal access requests.
The theoretical foundation of the proposed access control method is the use of ontologies, which is the shared and explicit conceptualization of a domain knowledge structure[4], to provide semantic information needed to execute policy analysis and access denying rules.
The rest of this paper is structured as follows. Section 2 discusses related works in access control. Section 3 introduces the proposed access control method and its use of metadata and rules. A scenario in Section 4 is used as an example of a personal backup service in cloud computing.Section 5 presents the evaluation of the proposed method.Section 6 discusses the implication of the proposed method from a managerial perspective. The final conclusion section summarizes the contribution of this study.
2. Related Work
Table 1 summarizes related works in the literature. Le et al.[5]proposed an access control method for a hospital ubiquitous information system, in which access is authorized according to user activities. Masoumzadeh and Joshi[6]used ontologies and policy rules to control access in online social networks. Hu et al.[7]used a semantic web technology to control cloud computing access. Zhu et al.[8]extended role-based access control (RBAC) to the cloud computing context. Ruj et al.[9]provided an attribute-based access control mechanism in the data storage cloud service.
Most of the above access control methods focus on cloud computing. However, few of the methods in these works address the relationships between the payment issue and access control mechanism. Few works consider the service level issue as an important element in the access control methods. In contrast, although these methods usually apply ontologies, few existing methods discuss the policy conflict issue. Therefore, this work proposes an ontological access control method based on the payment status and service level agreement to address the above issues.
3. Proposed Method
Fig. 1 shows how the proposed access control method is used in a situation involving four actors and six steps,where the actors are the end user, administrator, access control server, and cloud. The six steps of the usage process of the access control method are as follows. In the first step,the end user requests the access control server to provide a specific cloud computing service. The access control server then applies policies for confirming whether the end user has the authority to use this cloud service according to the payment status and service level request in step 2. The policies are managed by the administrator. After confirming that the end user has the authority, the access control server performs step 3 and step 4 to request and acquire the required cloud resources. If the end user has no authority,steps 3 and 4 are skipped, and the access control server records service logs. The final step is service delivery to the end user.
The proposed metadata have four core elements: the payment status, access permission, service level, and cloud.The metadata (Fig. 2) comprise two cloud policies and one user requirement. The proposed policy analysis rules (Table 2) are used to analyze the four relationships (RPS2-PS2,RAP1-AP2, RSL1-SL2, and RC1-C2) between access control policies ACP1and ACP2to identify conflicts and redundancies in the two policies. The other four relationships among the control policy ACP1and user requirement UR3are used by the proposed access denial rules (in Table 3) to deny and allow access. In Table 2 and Table 3, “∨” denotes “or”, Eq is “equal”, Ex is “exclusion”,K is “kind”, and A is “antonym”.
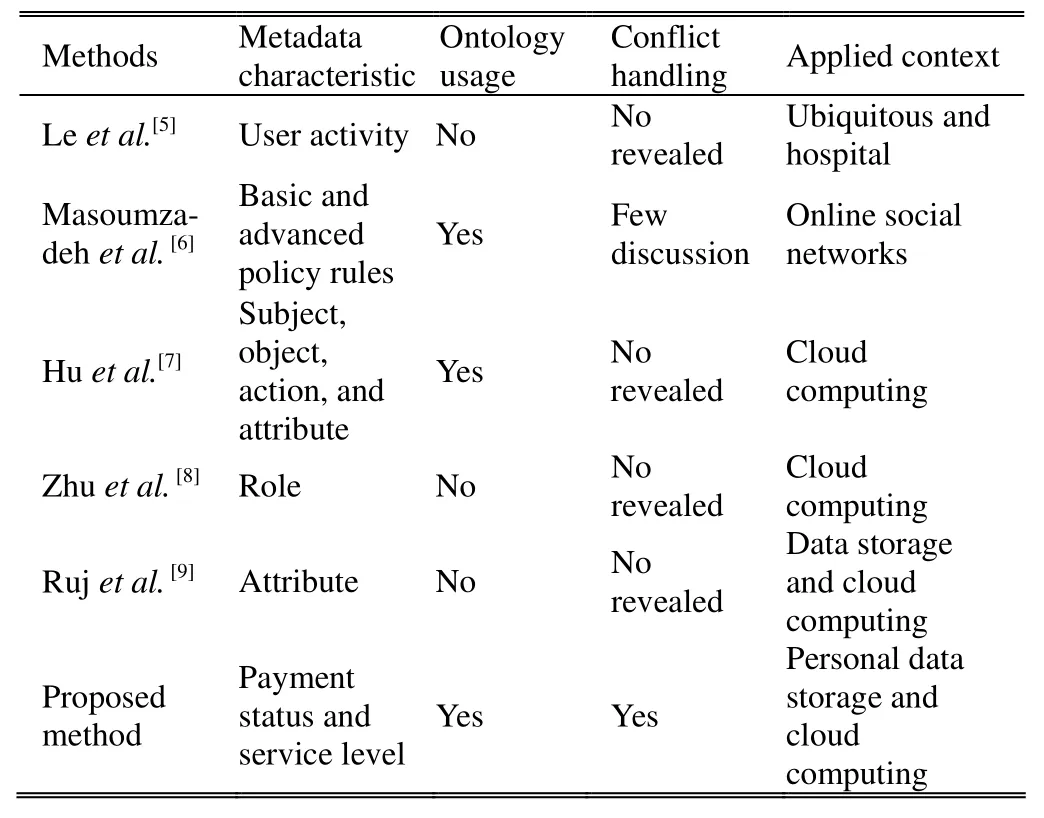
Table 1: Related access control method
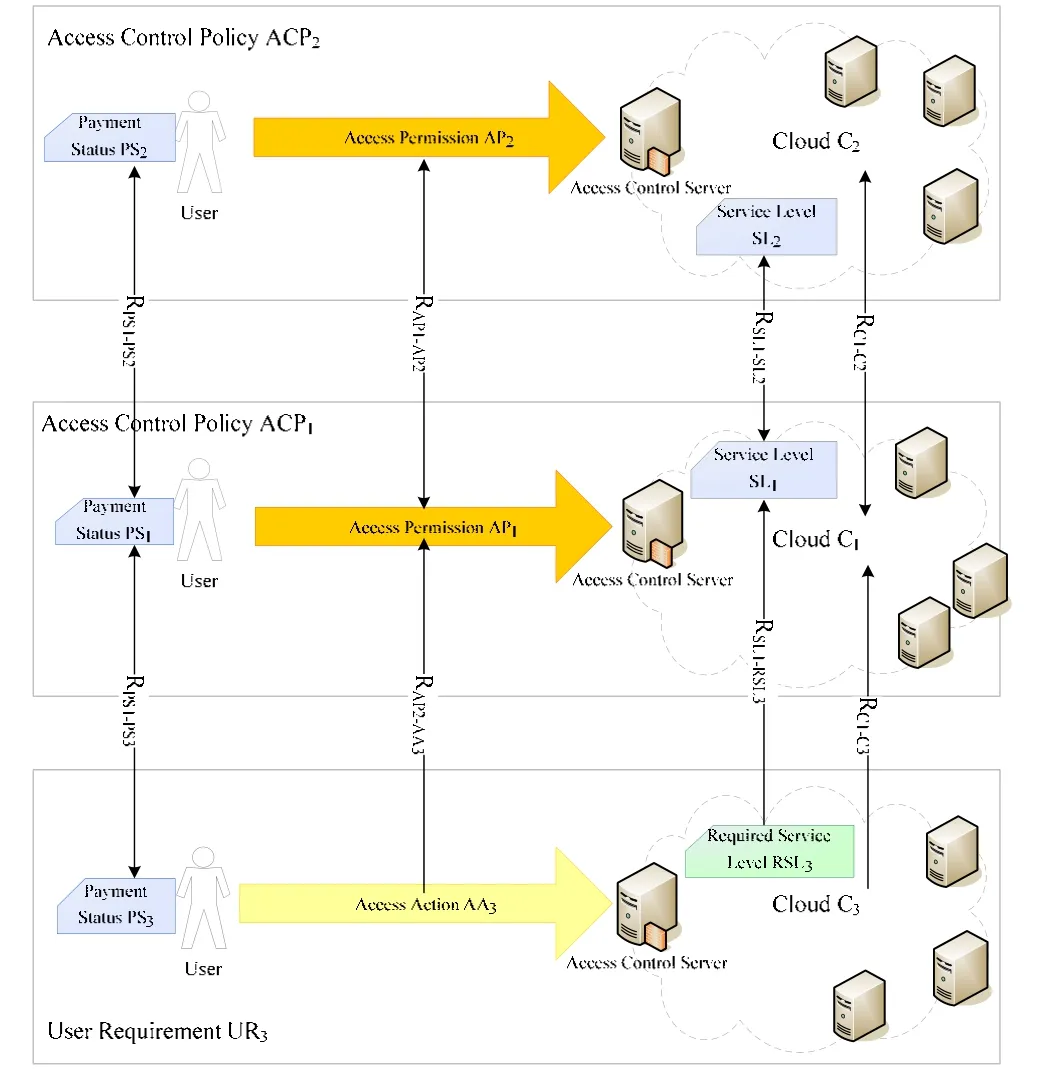
Fig. 2. Metadata of paired access control policies and a user requirement.
Table 2 summarizes the three proposed policy analysis rules for detecting conflicts and redundancies. These rules,which are developed according to the proposed metadata in Fig. 2, are described as follows.
RulePA1: IF, an equality or kind relationship exists between payment status PS1and PS2; AND IF, an antonym relationship exists between access permission AP1and AP2;AND IF, an equality or kind relationship exists between service levels SL1and SL2; AND IF, an equality or kind relationship exists between clouds C1and C2; and THEN,access control policies ACP1and ACP2are in conflict.
RulePA2: IF, an exclusion relationship exists between payment status PS1and PS2; AND IF, an equality or kind relationship exists between access permission AP1and AP2;AND IF, an equality or kind relationship exists between service levels SL1and SL2; AND IF, an equality or kind relationship exists between clouds C1and C2; and THEN,access control policies ACP1and ACP2are in conflict.
RulePA3: IF, an equality or kind relationship exists between payment status PS1and PS2; AND IF, an equality relationship exists between access permission AP1and AP2;AND IF, an equality or kind relationship exists between service levels SL1and SL2; AND IF, an equality or kind relationship exists between clouds C1and C2; and THEN,access control policies ACP1and ACP2are redundant.
Three rules based on the metadata in Fig. 2 are proposed to deny illegal access. These access denial rules are introduced as follows and summarized in Table 3.
RuleAD1: IF, a quality or kind relationship exists between payment status PS1and PS3; AND IF, an access action AP3is an antonym of access permission AP1; AND IF, the required service level RSL3equals or is a kind of service level SL1; AND IF, cloud C3is equal to or a kind of cloud C1; and THEN, the user access is denied because the access control policy ACP1inhibits the user requirement UR3.
RuleAD2: IF, an exclusion relationship exists between payment status PS1and PS3; AND IF, the access action AP3is equal to or a kind of access permission AP1; AND IF, the required service level RSL3equals or is a kind of service level SL1; AND IF, cloud C3is equal to or a kind of cloud C1; and THEN, the user access is denied because the access control policy ACP1excludes the user requirement UR3.
RuleAD3: IF, an equality or kind relationship exists between payment status PS1and PS3; AND IF, the access action AP3is equal to or a kind of access permission AP1;AND IF, the required service level RSL3exceeds service level SL1; AND IF, the cloud C3is equal to or a kind of cloud C1; and THEN, the user access is denied because the user requirement UR3exceeds the service level limitation of access control policy ACP1.
4. Cloud Service Data Backup Scenario
The scenario used as an example in this section is a personal data backup service for cloud computing. This scenario involves four ontologies and six examples for each rule. These ontologies, which include payment status ontology, access permission and action ontology, service level ontology, and data backup service ontology, are depicted in Fig. 3 to Fig. 6.
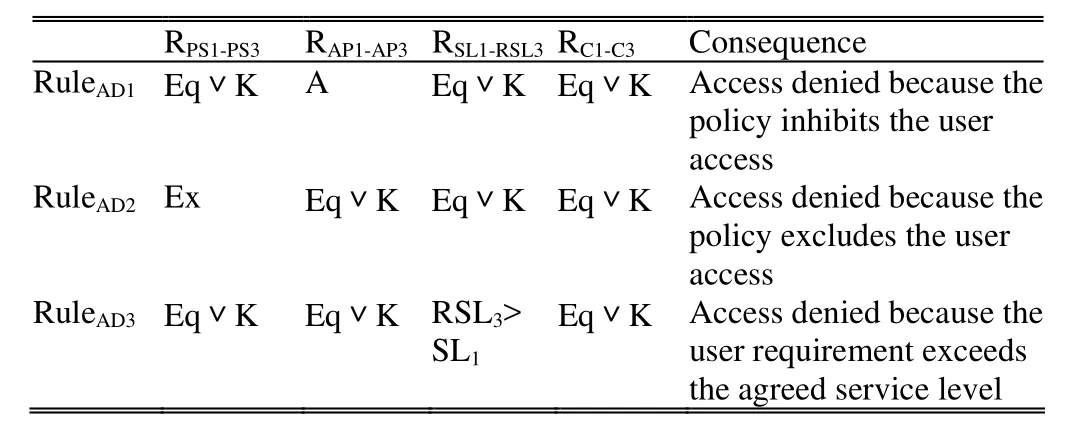
Table 3: Access denial rules
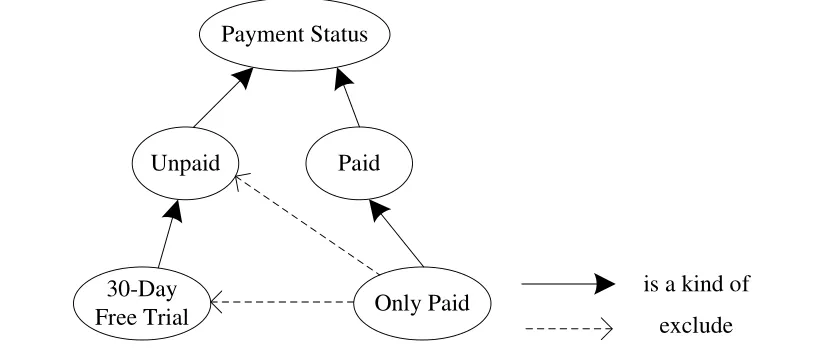
Fig. 3. Payment status ontology.
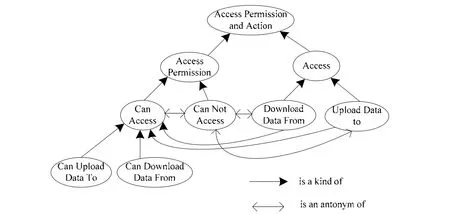
Fig. 4. Access permission and action ontology.
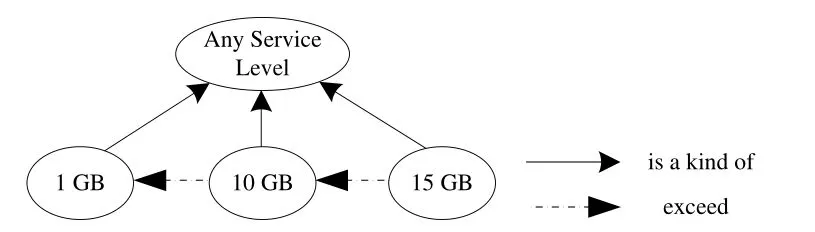
Fig. 5. Service level ontology.
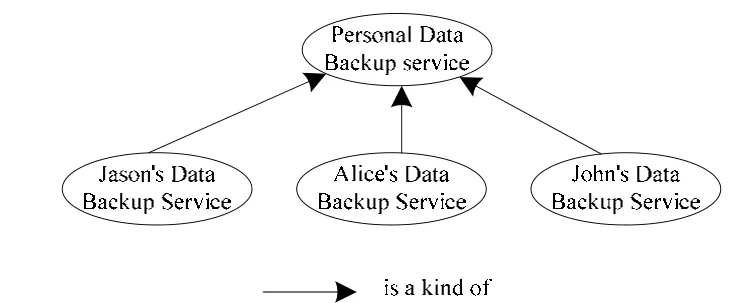
Fig. 6. Data backup service ontology.
The above ontologies (Fig. 3 to Fig. 6) and the metadata(Fig. 2) are applied in the following example of a data backup service to demonstrate and validate the proposed rules in Table 2 and Table 3. The example of RulePA1to RulePA3demonstrates the proposed policy analysis rules given in Table 2. In the RulePA1example, ACP1is “the unpaid (PS1) user can not access (AP1) any service level(SL1) personal data backup service (C1)”, and ACP2is “the unpaid (PS2) user can access (AP2) a 1 GB (SL2) personal data backup service (C2)”. Here, PS1equals PS2. Fig. 4 indicates that AP1(can not access) is an antonym of AP2(can access). Fig. 5 reveals that SL2(1 GB) can be any SL1(i.e., any service level). The C1equals C2. According to RulePA1in Table 2, ACP1and ACP2are in conflict.
The example of RulePA2is a conflict between ACP1and ACP2. The ACP1is “only the paid (PS1) user can access(AP1) 10 GB (SL1) personal data backup service (C1)”. The ACP2is “the unpaid VIP (PS2) user can access (AP2) a 10 GB (SL2) personal data cloud service (C2)”. Fig. 3 shows that, in this case, PS1(only paid) excludes PS2(unpaid).The AP1equals AP2. SL1equals SL2. The C1and C2are the same service. According RulePA2in Table 2, ACP1and ACP2are in conflict.
RulePA3example is a redundancy between two polices.The ACP1is “only the paid (PS1) user can access (AP1) a 10 GB (SL1) personal data backup service (C1)”. The ACP2is “the paid (PS2) user can upload data to (AP2) a 10 GB(SL2) personal data backup service (C2)”. Here, Fig. 3 indicates that a kind relationship exists between PS1and PS2and between AP1and AP2. Both SL1and SL2are 10 GB.The C1equals C2. According to RulePA3in Table 2, ACP1and ACP2are redundant policies.
The examples of RuleAD1to RuleAD3demonstrate the proposed access denial rules shown in Table 3. The RuleAD1example shows why access by a user Jason (in Fig. 6) is inhibited by the policy. In this case, ACP1is “the unpaid(PS1) user cannot access (AP1) any service level (SL1)personal data backup service (C1)”. The UR3is “the unpaid(PS3) user Jason download data from (AP3) 10 GB (RSL3)Jason’s data backup service (C3)”. The UR3means “data downloaded by an unpaid user Jason from a 10 GB data backup service”. In the above situation, PS1 equals PS2.Fig. 4 shows that AP1 is an antonym of AP3. Fig. 5 reveals that RSL3 is a kind of SL1. Fig. 6 shows C3is a kind of C1.According to RuleAD1, the access is denied because the policy ACP1inhibits the UR3access.
The RuleAD2example is a case of access exclusion. In this example, ACP1is “only paid (PS1) user can access(AP1) a 10 GB (SL1) personal data backup service (C1)”.The UR3is “a 30-day free trial (PS3) user, Alice, uploads data to (AP3) 10 GB (RSL3) Alice’s data backup service(C3)”. The UR3 means “30-day free trial for a user Alice to upload 10 GB of data to the data backup service”. Fig. 3 shows that PS3excludes PS1. Fig. 4 reveals that AP3is a kind of AP1. The SL1equals RSL3. Fig. 6 presents that C3is a kind of C1. According to RuleAD2, the user access is denied because the policy ACP1excludes UR3access.
In the example of RuleAD3, the user requirement exceeds the agreed service level. The ACP1is “only the paid (PS1)user can access (AP1) 10 GB (SL1) personal data backup service (C1)”. The UR3is “a paid (PS3) user John uploads data to (AP3) 15 GB (RSL3) John’s data backup service(C3)”. The PS1(only paid) is a kind of PS3(paid) in Fig. 3.The AP3is a kind of AP1in Fig. 4. RSL3exceeds SL1.Additionally, C3is a kind of C1. According to RuleAD3, the access is denied due to the service level excess problem.
5. Method Evaluation
The “service level” and “cloud” are two important classifications of cloud objects. The proposed method classifies objects according to the service “level” and“cloud”. The first formula calculates the object concept number of the proposed method:

The RBAC mechanism only uses “object” to represent the controlled resource. The RBAC mechanism does not consider the “service level”. A cloud might have several service levels, and a set of service levels might be applied in a set of clouds. The second formula for calculating object concept number in RBAC is
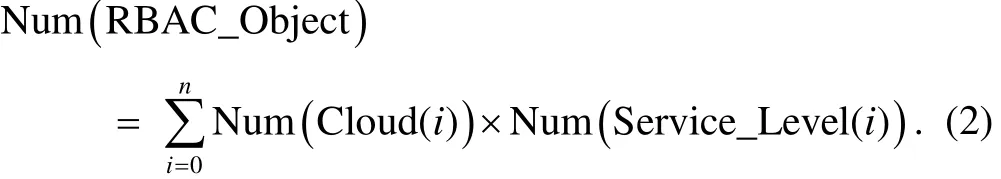
The following example shows how (1) is applied. In group 1, four service levels are used to describe three clouds. In group 2, two service levels are used to describe another cloud. The three clouds in group 1 are the data backup service, personal computer (PC) data backup service, and mobile device data backup service. The four service levels in group 1 are any service level, 1 GB, 10 GB,and 15 GB. The cloud in group 2 is a game service. Two service levels for the game service in group 2 are the general version and professional version. According to (1),the object concept number of the proposed method is
Num(Proposed_Method_Object)=(3+4)+(1+2)=10.
If RBAC is applied in the above example, group 1 needs twelve object concepts and group 2 needs two object concepts. The twelve object concepts in group 1 are “any service level-data backup service”, “1 GB-data backup service”, “10 GB-data backup service”, “15 GB-data backup service”, “any service level-PC data backup service”, “1 GB-PC data backup service”, “10 GB-PC data backup service”, “15 GB-PC data backup service”, “any service level-mobile device data backup service”, “1 GB-mobile device data backup service”, “10 GB-mobile device data backup service”, and “15 GB-mobile device data backup service”. The two object concepts in group 2 are the “general version-game service” and “professional version-game service”. According to (2), the object concept number in RBAC is

According to the above two formulas and their examples, the proposed method obtains fewer cloud objects compared with RBAC both in term of Num(Cloud(i)) and Num(Service_Level(i))≥2.
6. Managerial Implications
The above discussion has three managerial implications for the information systems and marketing departments of cloud service enterprises:
1) Assigning a specific service level for each customer type is convenient because the proposed access method classifies customers according to the service level and payment status. Cloud service providers can use the proposed method to maintain access control polices used to assign service levels to customers according to payment status.
2) Access control policies are intuitively aligned with marketing strategies because the proposed method uses payment status and service level based policies to control access. Cloud services are often marketed at different prices and service levels. Therefore, the proposed method intuitively applies the optimal marketing strategy for cloud service providers.
3) The method alleviates policy conflicts and redundancies because it provides rules for detecting conflicts and redundancies between access control policies.Therefore, it can decrease the cost of managing policy conflicts and redundancy problems.
7. Conclusions
The novel approach of the proposed algorithm is based on the ontology theory from both billing and contract perspectives. One theoretical contribution of the method is the application of ontologies to new phenomena. This work proposes an innovative theoretical set of rules for policy analysis and access denial. The practical contribution of the proposed method is to support billing and contract matters,which are essential elements in the cloud computing business model. The proposed method can facilitate cloud service providers in controlling user access according the account receivable, received payment, and agreed service level.
[1] S. Paquette, P. T. Jaeger, and S. C. Wilson, “Identifying the security risks associated with governmental use of cloud computing,” Government Information Quarterly, vol. 27, no.3, pp. 245-253, 2010.
[2] H. Takabi, J. B. D. Joshi, and G. J. Ahn, “Security and privacy challenges in cloud computing environments,” IEEE Security & Privacy, vol. 8, no. 6, pp. 24-31, 2010.
[3] D. Durkee, “Why cloud computing will never be free,”Communications of the ACM, vol. 53, no. 5, pp. 62-69, May 2010.
[4] M. Gruninger and J. Lee, “Ontology: applications and design,” Communications of the ACM, vol. 45, no. 2, pp.39-56, Feb. 2002.
[5] X.-H. Le, S. Lee, Y.-K. Lee, H. Lee, M. Khalid, and R.Sankar, “Activity-oriented access control to ubiquitous hospital information and service,” Information Sciences, vol.180, no. 16, pp. 2979-2990, Aug. 2010.
[6] A. Masoumzadeh and J. Joshi, “OSNAC: an ontology-based access control model for social networking systems,” in Proc. of the IEEE Int. Conf. on Social Computing/IEEE Int.Conf. on Privacy, Security, Risk and Trust, Minneapolis,2010, pp. 751-759,.
[7] L. Hu, S. Ying, X. Jia, and K. Zhao, “Toward an approach of semantic access control for cloud computing,” Lecture Notes in Computer Science, vol. 5931, pp. 145-156, Dec. 2009.
[8] T. Zhu, W. Liu, and J. Song, “An efficient role based access control system for cloud computing,” in Proc. of the 11th Int.Conf. on Computer and Information Technology, Beijing,2011, pp. 97-102.
[9] S. Ruj, A. Nayak, and I. Stojmenovic, “DACC: distributed access control in clouds,” in Proc. of IEEE the 10th Int.Conf. on Trust, Security and Privacy in Computing and Communications, Changsha, 2011, pp. 91-98.
杂志排行
Journal of Electronic Science and Technology的其它文章
- Analysis of Key Attributes Influencing the User Satisfaction towards Applications
- Parallelizing Modif i ed Cuckoo Search on MapReduce Architecture
- Design of a House Lease Management System in Cloud Computing
- A Unified Framework of the Cloud Computing Service Model
- ID-Based User Authentication Scheme for Cloud Computing
- Modified Packing Algorithm for Dynamic Energy-Saving in Cloud Computing Servers
