Joint Optimization of Energy Consumption and Network Latency in Blockchain-Enabled Fog Computing Networks
2024-04-28HuangXiaogeYinHongboCaoBinWangYongshengChenQianbinZhangJie
Huang Xiaoge ,Yin Hongbo ,Cao Bin ,Wang Yongsheng ,Chen Qianbin ,Zhang Jie
1 School of Communications and Information Engineering,Chongqing University of Posts and Telecommunications,Chongqing 400065,China
2 State Key Laboratory of Networking and Switching Technology,Beijing University of Posts and Telecommunications,Beijing 100876,China
3 School of Communication and Information Engineering,University of Sheffeild,United Kingdom
Abstract: Fog computing is considered as a solution to accommodate the emergence of booming requirements from a large variety of resource-limited Internet of Things (IoT) devices.To ensure the security of private data,in this paper,we introduce a blockchain-enabled three-layer device-fog-cloud heterogeneous network.A reputation model is proposed to update the credibility of the fog nodes(FN),which is used to select blockchain nodes (BN) from FNs to participate in the consensus process.According to the Rivest-Shamir-Adleman (RSA) encryption algorithm applied to the blockchain system,FNs could verify the identity of the node through its public key to avoid malicious attacks.Additionally,to reduce the computation complexity of the consensus algorithms and the network overhead,we propose a dynamic offloading and resource allocation (DORA) algorithm and a reputation-based democratic byzantine fault tolerant(R-DBFT) algorithm to optimize the offloading decisions and decrease the number of BNs in the consensus algorithm while ensuring the network security.Simulation results demonstrate that the proposed algorithm could effciiently reduce the network overhead,and obtain a considerable performance improvement compared to the related algorithms in the previous literature.
Keywords: blockchain;energy consumption;fog computing network;Internet of Things;latency
I.INTRODUCTION
In 5G networks,there are billions of Internet of Things(IoT)devices(IoTD),such as sensors,mobile phones,and so on[1-4].With the explosive growth of IoTDs,vast information needs to be processed in time.This will undoubtedly put tremendous pressure on the central cloud server[5].In addition,due to the long distance between IoTDs and the cloud server,the unacceptable task processing latency and the massive transmission energy consumption should be taken into consideration[6-8].
To solve these problems existing in the cloud computing network,the fog network has become a complementary option,which could offer expert knowledge access,computational power,storage capability,and diverse services for IoTDs or applications[9].In this case,the fog network could promote network location awareness,mobility support,real-time interaction,and scalability.However,due to the interplay of heterogeneous fog nodes (FN),and the migration of services across FNs,the data security and privacy of IoTDs are signifciant challenges[10].Nowadays,the high-ranking types of security and privacy contained in the fog network come from two sources:IoTDs and FNs.Security threats from IoTDs include spoofnig attacks,malicious data,denial of service (DoS) attacks and Sybil attacks,etc,which will transmit false information to increase the network traffci load.While security threats from FNs include selective forwarding,acknowledge flooding,etc,which will cause data security problems.Therefore,it is necessary to design a robust mechanism against malicious attacks.
Blockchain,as the core technology behind Bitcoin,has been gained widespread public attention in the academic and industrial circle,because of it’s security and immutability[11,12].The asymmetric encryption and the consensus mechanism are the most important parts of the blockchain system.The Rivest-Shamir-Adleman(RSA)encryption algorithm commonly generates a pair of public and private keys to encrypt,in which the public and private keys could be encrypted and decrypted for each other.Besides,the hash operation is carried out in the blockchain on the transaction information,and the hash value is kept in the block header to uniquely identify a block.In this way,the security of data could be ensured,and the likelihood of attack could be reduced.Therefore,the blockchainenabled fog network could not only release the burden for cloud services but also remove a series of security challenges [13].Generally,the blockchain-enabled fog network is becoming an inevitable trend[14-16].
1.1 Related Work
Recently,blockchain technology is considered in the fog network to solve security issues.In [17],a FN cluster (FNC) based blockchain was proposed to reduce the required computing power consumption and storage space,where FNs in the same FNC could share the same access control list (ACL) protected by the blockchain.In[18],the authors proposed a distributed fog-blockchain method for reputation management,and a multi-factor reputation evaluation method was introduced to identify malicious users.Although blockchain security has been improved,the inherent characteristics of blockchain still result in higher costs.In[19],a novel scalable public blockchain with a dualchain structure was proposed for IoT service computing,which select a leading group to improve the transaction effciiency for block generations.It effectively improves the scalability of blockchain,but it is diff-i cult to achieve adaptive security in dynamic environments.
On the one hand,most of the blockchain-enabled fog networks concentrated on accelerating the consensus process by using advanced verifciation techniques or blocks consensus algorithms.On the other hand,the feild of research tends to propose novel offloading methods to reduce energy consumption.In [20],the Reputation Byzantine Fault Tolerance(RBFT)algorithm was used to calculate the reputation of FNs based on their behaviors,which could identify and remove faulty nodes in time.However,the consensus process involving all nodes would result in signifciant costs,and malicious nodes would still participate in consensus,reducing the security of the system.
Due to the limited computing and storage capability of IoTDs,the mobile edge computing (MEC) enabled wireless blockchain framework was presented in[21],in which IoTDs could offload their tasks to the nearby edge computing nodes or a group of IoTDs.Besides,the stochastic geometry method was introduced to make offloading decisions.It requires further work to address security challenges,especially in malicious nodes scenarios.
Nevertheless,it is rarely mentioned time varying parameters in the realistic scenario in the blockchainenabled fog network,which is considered in this paper to verify the performance of the proposed algorithm.
1.2 Contribution
In this paper,a blockchain-enabled three-layer devicefog-cloud heterogeneous network is established to minimize the network overhead,including energy consumption and network latency.The main contributions of this paper are outlined as follows:
Firstly,a blockchain-enabled three-layer devicefog-cloud heterogeneous network is introduced to ensure the security of IoTDs.Besides,a reputationbased dynamic blockchain nodes selection (RDBS)algorithm is proposed to effectively detect malicious nodes while balancing the tradeoff between network security and consensus latency to determine the number of blockchain nodes(BNs).
Secondly,a dynamic offloading and resource allocation(DORA) algorithm is introduced to reduce energy consumption,in which the nearby FNs or IoTDs could dynamically adjust the allocated computation resource based on their current tasks to satisfy the network latency tolerance.These links between IoTDs and FNs are established based on energy consumption.
Thirdly,based on the RDBS algorithm,a reputation-based democratic Byzantine fault-tolerant(R-DBFT)algorithm is proposed to minimize the network latency of the block consensus process,in which only parts of FNs are selected as BNs to generate a block.
Fourthly,the actual scene of the campus is used to verify the performance of the proposed algorithm and the simulation result shows the effciiency of the proposed algorithm.
The rest of this paper is organized as follows.Section II presents the system model,which contains the network model,the communication model,and the computation model.In Section III,the blockchainenabled fog network model is introduced,including the reputation model and the block consensus model.In Section IV,the DORA algorithm and the R-DBFT algorithm are proposed to minimize energy consumption and network latency.Simulation results are presented and discussed in Section V.The limitations of this paper and discussion of future work are introduced in Section VI.Finally,Section VII concludes the paper.
II.SYSTEM MODEL
2.1 Network Model
Consider a three-layer blockchain-enabled device-fogcloud heterogeneous network,which includes the cloud layer,the fog layer and the device layer,as shown in Figure 1.IoTDs could dynamically join or leave the network.The cloud layer is composed of distributed clouds which are responsible for handling high-level computing tasks.When the computing capacity of FNs could not satisfy the task requirements,the task will be transferred to the cloud layer.The fog layer consists ofNgeo-distributed FNs to provide computing,storage,and communication resources to nearby IoTDs.The set of FNs is denoted asN={1,..,n,..,N},the computation capacity and credibility of FNnare denoted byFnandRn,respectively.

Figure 1.Network scenario.
Additionally,the blockchain is deployed in the fog layer to store transaction records from IoTDs.FNs with higher credibility have a higher probability to verify,broadcast,and record transactions or block information as BNs,while those FNs with low credibility are considered malicious nodes.When the transaction of an IoTD is successfully added to the blockchain,the IoTD will obtain the hash value of the relevant transaction and the block.Then the IoTD could employ the hash value to verify whether the transaction is recorded.Assume there areKBNsK={1,..,k,..,K},which are randomly selected from FNs.In addition,there areMrequest IoTDs(RID),denoted asM={1,..,m,..,M}andLidle IoTDs (IID),denoted asL={1,..,l,..,L}.RIDs could offload their tasks to nearby FNs or IIDs through a wireless link,i.e.,the device-to-infrastructure(D2I)link or the device-to-device (D2D) link.The task offloading process is described as follows.
Firstly,a RID will obtain pairs of public and private keys,which are used to encrypt or decrypt information after registrations.The public key will be broadcast to all nodes.When the RID has task offloading requirements,it could send request messages encrypted by its private key to the fog network.
Secondly,the nearby FNs and IIDs could use the public key of the RID to decrypt this message,which is called the verifeid signature.If the public key could decrypt the encrypted message,the public key matches the private key of the RID,which indicates that the message was sent by the RID itself.Therefore,the signature is proved as true.The RID will be allowed to access the network.After that,the nearby FNs and IIDs will calculate the energy consumption of the offloading tasks from RID.
Thirdly,the fog network will select appropriate nodes among FNs or IIDs to minimize energy consumption and establish the communication link from the RID to the associated nodes.
Finally,to record transaction information,FNs and IIDs will broadcast the transaction records to nearby BNs.BNs will write these transaction records into blocks,and return the block index and hash value of the transaction to RIDs.
2.2 Communication Model
In the network scenario,the orthogonal frequency division multiplexing (OFDM) technology is adopted for data transmission,thus FNs could share the same radio resources without the transmission interference.Assume the total bandwidth isUand it allocated to RIDmis denoted asBm.The transmission power and the channel gain from RIDmto FNnand IIDlare denoted asG={Gm,n,Gm,l},respectively.Cm,nandCm,ldenote the channel-toinference-plus-noise ratio(CINR)from RIDmto FNnand IIDl,respectively.Hence,the transmission rate from RIDmto FNnand IIDlare respectively given by
whereσ2is the noise power andPmaxrepresent the maximum transmission power of FN.
2.3 Computation Model
Letξm ∈{0,1}denote the offloading decision of RIDm,whereξm=0(mode 0)indicates RIDmwill offload tasks to FNnthrough the D2I link,whileξm=1(mode 1)represents RIDmwill offload tasks to IIDlby the D2D link.Each FN could accept multiple offloading requests from RIDs simultaneously,while an IID could only deal with one task at a time.Therefore,the computation model of mode 0 and 1 are as follows:
Task offloading on the D2I link(mode 0):
1)Task transmission phase: In this phase,RIDmwill offload tasks to FNnthrough the D2I link.Assume the offloaded task size isDm(bits),and the transmission rate from RIDmto FNnisSm,n.Thus,the task transmission latency and energy consumption from RIDmto FNncould be expressed as
2)Task execution phase: Assume FNs employ the dynamic voltage and frequency scaling(DVFS)technology,in which FNncould adjust the CPU-cycle frequencyfn(cycle/s)according to the complexity of the current task [22].When RIDmdecides to offload tasks to FNn,FNnwill adjust the CPU-cycle frequency to reduce the network overhead.Similar to [23],the power computation of CPU iswherehnis the effective switched capacitance of the CPU of FNn[22].The network latency and energy consumption are respectively given by
whereJnis the number of CPU cycles required for processing 1 bit of input data,andfm,ndenotes the CPU-cycle frequency required by FNnto process the task of RIDm(in cycle/s).
3)Task queuing phase: Since a FN could offload tasks from multiple RIDs simultaneously,the network overhead during the queuing process in the buffer should be taken into account.Assume the total number of CPU cycles for tasks in the buffer of FNnisQn,then the queuing latency and energy consumption could be calculated by
Accordingly,the total network overhead on mode 0 is given by
Task offloading on the D2D link(mode 1):
1)Task transmission phase: In mode 1,RIDmwill offload tasks to nearby IIDs through the D2D link.Assume RIDmoffloads the tasks to IIDl,then the task transmission latency and energy consumption from RIDmto IIDlare expressed as
2)Task execution phase: Assume the computing power of IIDs is fxied,the maximum computation power and computation capacity of IIDlare denoted asPlandFlrespectively.Therefore,the task transmission latency and energy consumption in the task execution phase are given by
Accordingly,the total network overhead of the offloading task on mode 1 could be calculated by
III.BLOCKCHAIN-ENABLED FOG NETWORK MODEL
To ensure the security of the fog network,blockchain technology is enabled into the fog layer.In this section,we propose a reputation model to calculate the credibility of FNs.Due to the high complexity of the traditional consensus model,there are big challenges to enable blockchain technology in the largescale fog network.Thus,we improve the block consensus model to reduce the network overhead.
3.1 Reputation Model
To identify malicious nodes in time,we employ the credibilityRn(Rn ∈{0,1})of FNnto represent its trust degree.There are two credibility thresholds,γ,andδ,set in the reputation model.IfRnis higher thanγ,it will be considered a trusted node.WhileRnis lower thanδ,FNnbe considered a malicious node.
Therefore,RIDs and the network administrators can distinguish between trusted nodes and potential malicious nodes based on the credibility of FNs.To reduce the number of interactions between FNs during the consensus process,a reputation-based dynamic BNs selection(RDBS)algorithm is proposed to select parts of FNs as BNs.Therefore,parts of FNs only offload tasks on the edge of the network,while others may also work as BNs.Specifcially,the credibility of FNs according to the identities and their behaviors.For newly joined FNs,Rwill be initialized as 0.5 [20].LetRn(t)denote the credibility of FNnat time slott,thusRn(t+1)is the credibility of FNnat the following time slott+1,which is given by
whereaindicates the credibility increase degree of FNn,whileb(0<b <1)is the credibility decrease degree of FNn.If FNnis not a BN,Condition 1,2 and 3 are“all information is accurate”,“parts of information are missing” and “there is false information”,respectively.Furthermore,if FNnis a BN,Condition 1,2 and 3 are“generate a new block”,“fail to generate a block”and“send an inconsistent vote”,respectively.
According to the identity of the node,FNs could be divided into edge computing nodes (ECN) and BNs,thus theRncould be calculated in two ways.For ECNs,Rnare related to the accuracy of their broadcast transactions.For BNs,Rnare related to the contributions of their block consensus processes.
It is worth noting that,Rnof FNnincreases faster at the beginning,and becomes slower gradually,which could force FNnto have continuous good behaviors to achieve a high reputation value.Otherwise,Rnwill be decreased sharply.The probability of FNnbeing selected as a BN is given by
Therefore,the FN with a higher reputation value will be more likely to be selected as the BN.
Assume the blockchain latency tolerance isτcand the number of malicious BNsf.Then,the maximum number of BNsKmaxcan be obtained byτc.At the same time,under the constraint of 1/3 fault tolerance of PBFT,the minimum number of BNsKmincould be calculated byKmin=3f+1.LetKmin>N×10%to ensure that at least 10%of FNs will participate in the consensus process.In addition,Kmax<Nensures that the maximum number of FNs joining the consensus process isN.Thus,we haveKmin<K <Kmax.
In order to minimize network latency while ensuring network security,we defnie the network security coeffciientη ∈[0,1]to represent the credibility of the network,andη=1 -H.WhereHrepresents the normalized entropy of the network,given by
whereKis determined byη,Kmin,andKmax.In a trusted network,where most of FNs are trustable andKminis small.In this case,we could reduceKto reduce the number of interactions between FNs during the consensus process,and further reduce network latency.On the other hand,when there are many malicious nodes in the network,Kminshould be increased to ensure security,resulting in a larger network latency.
3.2 Block Consensus Model
Assume FNnis selected as the primary(n ∈K),and other FNs with high credibility,such as FNk,FNk′(k,k′∈K,k,k′≠n),are replicas in this iteration of the consensus process,which are named as BNn,BNk,BNk′,respectively.The transmission rate from BNnto BNkisSn,k,while the transmission rate from BNkto BNk′isSk,k′.Besides,assume the number of CPU cycles required to execute the smart contract for a transaction and generate or verify a signature isα,β,respectively.The average data size of a transaction and a block of FNnare defnied asInandBn,respectively.
1)Block Generation Process: Assume FNnis selected as the primary,which generates a new block and writes the transaction information during a period into this block.Therefore,the block generation latency could be calculated by
2)Block Consensus Process: BNnwill broadcast the new block to replicas to verify it in the consensus process,which consists of four steps: pre-prepare,prepare,commit,and write.Each step is composed of two parts,namely,block propagation and block verif-i cation[24-27].
•Step 1.BNnbroadcasts the pre-prepare-message to replicas which is encrypted by the private key of BNn.Accordingly,the latency of step 1 is given by
where the former term refers to the block transmission time,and the latter term is the time to generate a signature.
•Step 2.Replicas verify the accuracy of the pre-prepare-message and generate the preparemessage with the verifciation results.Then,each replica sends the prepare-message to other replicas to indicate themselves votes on the new block from BNn.When BNkreceives the pre-preparemessage,it frist verifeis the signature of BNn.Then,it continues to execute the smart contract of the transaction information and verify the signature of each transaction information in the new block.After this,it sends the prepare-message with verifciation results to other replicas,such as BNk′.In this step,the calculation cost of BNkto verify the signature of BNnis denoted asβ.The cost of executing the smart contract for each transaction and verifying each signature of transaction in the block is given byThe cost of generating it’s signaturenisβ.The total calculation cost and latency of step 2 are given by
•Step 3.When replicakreceives prepare-message from more than 2/3 of BNs,it will dispatch commit-message to all BNs (including the primary).The calculation cost is consist of the verifying block information costthe cost of verifying 2/3 signatures of BNsand the cost of generating it’s signatureβ,respectively,given by
which indicates BNkneeds to verify the block information,signature and generate it’s own signature.Moreover,the latency could be calculated by
•Step 4.When BNnreceives the commit-message from more than 2/3 of BNs,it will append the new block to the blockchain.In this step,BNnwill verify the block information andsignature.Thus,the calculation cost and latency is given as
Therefore,the total network latency is expressed as
IV.PROBLEM FORMULATION
To reduce the network overhead of the blockchainenabled fog network,we propose a dynamic offloading and resource allocation (DORA) algorithm and a reputation-based democratic byzantine fault tolerant(R-DBFT) algorithm.The DORA algorithm could optimize the offloading decisions of RIDs to minimize energy consumption,while the R-DBFT algorithm could reduce network latency by decreasing the number of nodes in the blockchain.
4.1 Problem Formulation
In this section,we formulate an optimization problem to minimize the overhead of the whole network.The goal is to optimize the trade-off between energy consumption and network latency.Particularly,the objective function of the optimization problem is given by
The constraint (C1) shows the association between RIDmand FNn,IIDl,and(C2)indicates that RIDmcould only be associated with a FN or an IID.ξm=0 indicates RIDmwill offload tasks by the D2I link and connect to FNn.Otherwise,ξm=1 means RIDmwill offload tasks to IIDlthrough the D2D link.The constraint (C3) denotes the tolerable network latencyτof RIDmon mode 0 and mode 1.Besides,the constraint (C4) indicates the total CPU-cycle frequencyfm,nandfn,kof FNnshould be less thanF.The constraint(C5)ensures FNncould work properly.
4.2 Dynamic Offloading and Resource Allocation Algorithm
The original optimization problem is non-convex,which is challenging for the global optimal solution.To reduce the computation complexity,the optimization problem is divided into two sub-optimization problems,namely,the optimization of energy consumptionEmand network latencyTn.A dynamic offloading and resource allocation(DORA)algorithm is proposed to minimize the energy consumption under the network latency constraint,as shown in Figure 2,which is executed by the following three steps.


Figure 2.DORA algorithm.
Firstly,when RIDmregisters locally as a valid node,it gets pairs of public and private key<Pubm,Prim >andPubmwill be exposed to the whole network.After this,RIDmwill send a request messagedmto the fog network,which contains the geographical positionAmand task sizeDm.To ensure the integrity of the information,RIDmcould use the MD5 algorithm to generate the message digest.Thus the messagedmwill be generated as the 128-bit message digestMD5(dm).Then,RIDmwill employ the RSA algorithm to generate it’s signature,that is,the messagedmis encrypted as the encrypted digestRSA(dm)with private keyPrim.Finally,MD5(dm)andRSA(dm)will be broadcast to the whole network.
Secondly,the nearby FNs or IIDs will check the identity and calculate the offloading overhead of RIDmby three steps:Identity verifying,to verify the identity of RIDm;Information response,to respond the state information;Overhead calculation,to calculate the offloading energy consumption of RIDm.
Finally,the offloading decisions are obtained based on the previous steps.
•Identity verifying: The RSA is an asymmetric encryption algorithm which uses different pairs of public-private keys to encrypt or decrypt,and is employed in the identity verifying of blockchain.Hence,the verifeirs which consist of nearby FNs and IIDs could usePubmto verifyPrimandRSA(dm).Specifcially,the verifeirs could getMD5(dm) andRSA(dm) at beginning.Then,they try to get the decrypted request messagesthrough the public keyPubm.If it could not be decrypted,the signature is proved as wrong,thus RIDmwill be refused to access the network.On the contrary,the verifeirs will convertagain.If the decoded digestis equal to the original encrypted digestwill be proved the same as the original message digestdm.Therefore,the identifciation process has passed,and RIDmcould enter the network.
•Information response: After the identity process,nearby FNs or IIDs will collect themselves state messages,which contains the geographical locations of FNs or IIDs AN×1or AL×1,the currently available CPU cycles of FNs in the buffer QN×1,the CPU-cycle frequencies of FNs FN×1and so on.
•Overhead calculation: Nearby FNs or IIDs could calculate the distance between them and RIDm,denoted as ZN×Mor ZL×M,channel gain,denoted as GN×Mor GL×M,the transmission rate SN×Mor SL×Mand CINR CN×Mor CL×M.Then,they could calculate the energy consumption.For example,nearby FNnand IIDlcould calculate the energy consumption of RIDm,andBesides,because a FN could connect multiple RIDs simultaneously,the allocated CPUcycle frequency of FNn fncould be adjusted.Consequently,the energy consumption optimization problem between FNnand RIDmis
4.3 Reputation-Based Democratic Byzantine Fault Tolerant Algorithm
The traditional consensus algorithm will cause large latency due to the high computation complexity.To minimize the network latency of the consensus process,the R-DBFT algorithm is proposed that only a few FNs will be selected as BNs to reduce the computation complexity,while effectively identifying malicious nodes,as shown in Figure 3.The R-DBFT algorithm is composed of the following two steps.

Figure 3.Execution process of the R-DBFT algorithm.
Firstly,the fog network updates the credibility of FNs RN×1according to their previous behavior.The pro bability PN×1of a FN been selected as a BN could be calculated by formula(11).
Secondly,selectKFNs as BNs to participate in the consensus process.BNs are selected individually with unequal probability.Moreover,the one with the highest reputation value among BNs will be selected as the primary node,and the remainingK-1 nodes will be selected as replicas.These selected BNs will form a blockchain network after broadcasting their geographic location AK×1.This process can be divided into the following three steps.
1)Block generation: The primary will generate a new block and write all transactions into the block.Similarly to the MD5 algorithm,the primary (BNn)carries out the hash operation on the transaction informationdnin a transaction block and keeps the root hash valueMD5(dn)in the new block header.Then,the primary generates it’s signatureRSA(dn).Finally,the primary broadcastsMD5(dn)andRSA(dn)to the blockchain network.Assume the size of a transaction and the block isInandBn,respectively.Hence,block generation latency and broadcast latency are denoted asaccording to formula(14,15).
2)Block consensus:Replicas could verifyMD5(dn) andRSA(dn),and send their vote messagevkand generate signatureRSA(vk).The block needs to be validated multiple times to ensure network security.Therefore,the block consensus latency isaccording to formula(16,18).
3)Block written: When the primary receives more thanvote results,the block will be appended into the blockchain.Hence,the block written latency could be expressed asaccording to formula(19).
V.SIMULATION RESULTS
In this section,we evaluate the numerical performance of the proposed DORA and R-DBFT algorithms in all aspects via Matlab simulations.
5.1 Simulation Parameters
In this scenario,we consider an actual campus scene,where RIDs,FNs,and IIDs are randomly distributed in a range of 1×1 km2area.The channel path loss model is expressed as 140.7+36.7log10(Z),which is standard settings provided by 3GPP[22].Zrepresents the distance between RIDmand FNnor IIDl.The Noise power density is -174 (dBm/Hz) and the total system bandwidth is 180(kHz).Besides,the computing capability of FNs and IIDs is 25 GHz and 2.2 GHz,respectively.The main parameters used in the simulation are outlined in Table 1.

Table 1.Simulation parameters.
5.2 Simulation Results
5.2.1 Security
In Figure 4,we show the changes of the network safety coeffciientηand the number of BNsKfor different algorithms versus the proportion of malicious nodes.Consider three comparison algorithms,namely,the fxied value algorithm,whereK=Kmin,the average value algorithm whereK=(Kmin+Kmax)/2,and the proposed RDBS algorithm.According to formula 20,the blockchain consensus latency will increase as the number of BNsKincreases.On the one hand,when the proportion of malicious nodes is small,the network security coeffciientηis higher.In this case,the RDBS algorithm could select a smallKto participate in blockchain consensus to reduce consensus latency.On the other hand,as the proportion of malicious nodes increases,the network security coeffciientηwill decrease.The RDBS algorithm will adaptively adjustK,sacrifciing latency to ensure consensus security.The RDBS algorithm could optimize the number of BNsKto balance the tradeoff between network security and consensus latency,which achieves better performance than the comparison algorithms.

Figure 4.Change of network coefficient η and the number of BNs K versus the proportion of malicious nodes.
5.2.2 System Performance
Figure 5 analyzes the energy consumption and network latency of RIDs on the D2I link and the D2D link.From fgiure 5(b),we could observe that the network latency of some RIDs on the D2D link is larger than the maximum tolerable latencyτof the network,hence these RIDs will switch to the D2I link to meet the latency limitτ,while others will choose the lower energy consumption offloading link to reduce the network overhead.Figure 5(c) shows the selected offloading link of RIDs based on the DORA algorithm.Finally,the energy consumption of each RID is shown in fgiure 5(d).

Figure 5.Optimal offloading decisions of RIDs based on the DORA algorithm. (a)Energy consumption contrast. (b)Network latency contrast. (c) Offload link selection. (d)Final energy consumption.
In fgiure 6,the energy consumption versus the number of RIDs with different algorithms is presented.The ETO algorithm [30] and the MPCO algorithm[31] are used for comparison.Figure 6 shows that the energy consumption of different algorithms is an increasing function of the number of RIDs.This is because a larger number of RIDs will generate more offloading tasks,resulting in a higher power consumption.In addition,the proposed DORA algorithm could achieve a lower energy consumption than comparison algorithms with the same number of RIDs.This is because the DORA algorithm could optimize the offloading decisions for RIDs according to actual situation.

Figure 6.Energy consumption for different algorithms.
Figure 7 presents the network latency versus the number of RIDs with the proposed R-DBFT,PBFT,and DPoS [25].The network latency of the three algorithms is increasing with the increasing number of RIDs.This is because the amount of transaction information contained in the block is increasing with the number of RIDs,resulting in increasing of the block transmission latency and the block verifciation latency.Furthermore,the proposed R-DBFT algorithm could achieve a lower network latency compared with the other algorithms.This is because the PBFT requires all FNs to participate in the consensus process,while the DPoS has two voting sessions from all nodes which will increase the consensus latency.In the R-DBFT,there are only a few FNs with high credibility could participate in the consensus,which will dramatically reduce the block consensus latency.

Figure 7.Network latency for different consensus algorithms.
5.2.3 System Practicability
In the real scenario,the number and the location of RIDs are time varying.To verify the practicability of the proposed algorithm,the campus scene is considered in the simulation.The mobility of users on the campus is related to time,the location of users and the number of task requirements are also dependent on time,which shows a clear tidal effect in the communication.Consequently,the effciiency of the algorithm base on the activities of users could be approximated.Figure 8(a)shows the number of RIDs in campus throughout the day,where the left area of the fgiure is the geographical distribution of RIDs at 12 a.m,while the right area is the geographical distribution of RIDs at 8 p.m.Those red dots represent the current positions of RIDs.During the day,the number and the geographic locations of RIDs are time-varying.For example,a large number of RIDs will gather in the restaurant at 12 a.m,as seen in restaurant A and restaurant B,while most of them stay in the hotel at night,as seen in hotel A and hotel B.

Figure 8.The tidal effect during a day in the campus. (a)The distribution of RIDs in the campus. (b)The total energy consumption. (c)The total network latency.
Figure 8(b)and(c)show the cumulative value of the network energy consumption and the network latency at various moments during a day.From the result of the fgiure,the trend of the energy consumption and the network latency is similar to the change of RIDs in fgiure 8(a).This is because the energy consumption and the network latency are changing with the number of RIDs.In general,the larger the number of IoTDs,the greater the number of tasks,so the energy consumption and the network latency are relatively larger.
In Figure 9(a)and(b),we investigate the impact of the weight parameterw1on the energy consumption and the network latency.Accordingly,three weight parameters are set to show the performance of the proposed scheme,e.g.w1=0.2,w1=0.4,andw1=0.6,respectively.From fgiure 9(a)and(b),for a givenF,the performance of the energy consumption and the network latency degrades asw1increases.In addition,for a givenw1,the smallerFis,the smaller the energy consumption and the higher the network latency.This is because a largerFimplies that the performance of the blockchain network is more important than the fog network.To verify the impact of the weight parameterw1on the network overhead,we calculate the overhead at various moments during a day,and set three parameters,which arew1=0.2,w1=0.4,andw1=0.6,respectively.
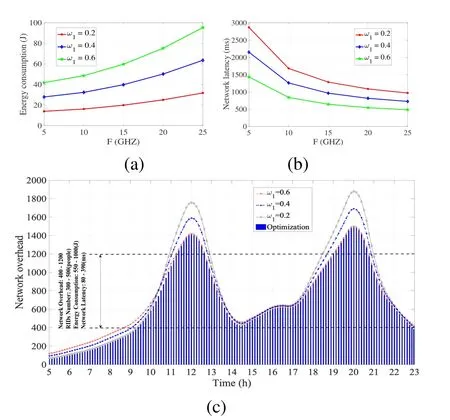
Figure 9.Impact of different weight parameters on the network overhead. (a)Energy consumption during a day. (b)Network latency during a day. (c)The changes in network overhead.
Figure 9(c)shows that the network overhead for different value of weight parameterw1.It could be seen that,for a givenF,the network overhead is time varying.This is because the number and locations of RIDs or the size of the task in a real scenario are time varying.Therefore,the proportion of the energy consumption and the network latency is different at different moments.In this case,we can not minimize the network overhead at every moment with a fxied weight parameterw1,as shown in fgiure 9(c).
Based on this,we should optimize the weight parameter for different times to minimize the network overhead.The weight parametersw1will be reduced when the proportion of the energy consumption is large.While the weight parametersw1will be increased when the proportion of the network latency is large.The blue shaded area in fgiure 9(c)is the minimized network overhead of the proposed scheme.
VI.FUTURE WORK
The application of blockchain in fog computing networks is mainly limited by its scalability and high energy consumption.Although the RDBS algorithm is proposed in this paper to reduce the cost of blockchain,it is still limited by the scalability of blockchain.Blockchain sharding technology is considered a promising technology for improving scalability.In future research,blockchain sharding technology could be applied in fog computing scenarios to ensure security while improving network scalability.In addition,blockchain smart contract technology could be applied to task offloading in fog networks.Future work could focus on researching blockchain smart contracts and deploying task offloading and resource allocation solutions in smart contracts to achieve distributed secure offloading.
VII.CONCLUSION
To guarantee the security of service for the Internet of Things devices (IoTDs),the fog network-enabled blockchain was established.Fog nodes (FN) and IoTDs could obtain the unique public-private keys when joining the network,thus FNs could verify the authenticity of these messages through these public keys to avoid malicious attacks.To reduce the network overhead including energy consumption and network latency,dynamic offloading and resource allocation (DORA),and reputation-based democratic byzantine fault-tolerant allocation (R-DBFT) algorithms were introduced.Simulation results demonstrated that the proposed algorithm could effciiently optimize the trade-off between the energy consumption and the network latency while ensuring the network security.
ACKNOWLEDGEMENT
This work was supported in part by the National Natural Science Foundation of China (NSFC) under Grant 62371082 and 62 001076;and in part by the National Key R&D Program of China under Grant 2021YFB1714100,and in part by the Natural Science Foundation of Chongqing under Grant CSTB2023NSCQ-MSX0726 and cstc2020jcyjmsxmX0878.
杂志排行
China Communications的其它文章
- Distributed Application Addressing in 6G Network
- A Support Data-Based Core-Set Selection Method for Signal Recognition
- Actor-Critic-Based UAV-Assisted Data Collection in the Wireless Sensor Network
- Integrated Clustering and Routing Design and Triangle Path Optimization for UAV-Assisted Wireless Sensor Networks
- Joint Task Allocation and Resource Optimization for Blockchain Enabled Collaborative Edge Computing
- Stochastic Gradient Compression for Federated Learning over Wireless Network
