Distributed Application Addressing in 6G Network
2024-04-28LiuJieChenSiboLiuYuqinMoZhiweiLinYilinZhuHongmeiHeYufeng
Liu Jie,Chen Sibo,Liu Yuqin,Mo Zhiwei,Lin Yilin,Zhu Hongmei,He Yufeng
China Telecom Research Institute,Guangzhou 510632,China
Abstract: To ensure the extreme performances of the new 6G services,applications will be deployed at deep edge,resulting in a serious challenge of distributed application addressing.This paper traces back the latest development of mobile network application addressing,analyzes two novel addressing methods in carrier network,and puts forward a 6G endogenous application addressing scheme by integrating some of their essence into the 6G network architecture,combining the new 6G capabilities of computing&network convergence,endogenous intelligence,and communication-sensing integration.This paper further illustrates how that the proposed method works in 6G networks and gives preliminary experimental verifciation.
Keywords: application addressing;CNC(Computing&Network Convergence);DNS(Domain Name System);ICN(Information-Centric Network);6G
I.INTRODUCTION
The contradiction between “network” and “application”is the internal driving force to promote the continuous evolution of network architecture,while application addressing is the key factor that connects“network”and“application”.Applications are usually addressed by DNS(Domain Name System)in the Internet architecture [1].For centralized deployed applications,there is no need to consider the access location of UE (User Equipment) when processing DNS requests,while for distributed deployed applications,such as CDN,the address of the nearest server among the many distributed servers should be responded to the UE in the DNS response[2].Although traditional CDN is a distributed deployment,server locations are relatively high level.Usually,the approximate location of the UE estimated by the network address is suffciient to determine the nearest service point.In mobile network,UE address usually does not change because of mobility,and with the development of mobile edge computing,the trend of marginalized application deployment is more and more obvious,so the traditional addressing method is no longer applicable.
6G has attracted widespread interest from academia and industry,and research has been carried out on the 6G vision,use cases,architecture,key capabilities,key technologies,etc [3-8].In 2030 and beyond,diversifeid applications such as holographic communication,immersive XR,machine intelligence,integrated communications and sensing,and multidimensional perception will emerge [9,10],all of which put forward extreme and widely varying performance requirements.The introduction of touch and mind,the realization of immersive experiences,and the closed-loop control of factory automation have all increased the requirement for latency to less than 1ms [11].Huge amounts of data such as spatial data for holographic services,and sensory information for sensing services,need to be collected,transmitted or updated in real time,with extremely high peak rate requirements,which will reach 1Tbit/s or even 10Tbit/s[12],and the traffci density requirements will be 10~100 times higher than 5G,reaching 1Gps/m2[13].For services related to human beings or public infrastructure,such as mobile machine motion control,complete reliability should be guaranteed,which should be higher than 99.99999%,otherwise human life,social order and even the safety of human life may be affected [10,14].Further,industry,energy,Internet of Vehicles,telemedicine and other feilds put forward deterministic requirements for network transmission indicators(such as bandwidth,delay,jitter,packet loss),requiring timely and accurate transmission of information for precise machine control.
In order to meet capabilities requirements of 6G network,support extreme performances and traffci offloading,overcome the complexities and security risks of centralized network,and obtain flexibilities of customized networks,6G network will adopt a decentralized hierarchical network architecture based on distributed computing power with centralized and distributed collaboration [13,15].Many researches on 6G distributed solutions are in full swing,e,g.literature[16]constructs a multiagent system(MAS)-based Energy-Effciient resource allocation method in Massive IoT for Industrial 6G Applications.Distributed autonomous edge subnetworks are main components of 6G network.Edge subnetworks,as well as applications can be orchestrated on demand,and applications/contents be collocated with or cached in edge subnetworks[17,18].In the vision of 6G distributed network architecture with application deep-marginalizeddeployed,distributed application addressing will be an even bigger challenge.In other words,addressing has been considered as a problem of capital construction for building next generation mobile Internet ecology,so it is necessary to determine a 3rd-party-friendly application addressing method under the new architecture,as to promote network-application coordination.
When we observe the research on public Internet,we fnid that there have been many researches on distributed application addressing,typically including ICN (Information-Centric Network) and CNC (Computing&Network Convergence).
ICN puts forward a new architecture,where the routing mechanism is based on interested contents/applications rather than position,so no rely on plug-in DNS process and solves distributed application addressing endogenously.
CNC sets addressing logic with the perspective of network and computing collaboration through mapping application requirements into abstract and quantifaible resource requirements,accordingly implements unifeid scheduling of computing,storage resources and network resources,aiming at realizes optimal adaption between service requirements and resources.The predecessor of CNC was put forward in 2019 by IETF (Internet Engineering Task Force as CFN(Computing First Networking).The subsequent concepts such as INC (In-Network Computing) in IETF which is different from ICN of the same abbreviation,CPN (Computing Power Network) and CAN(Computing-aware Networking) in ITU-T (International Telecommunication Union-Telecommunication Standardization Sector)are similar.These similar concepts have been unifeid in the relevant research of China’s CCSA(China Communications Standards Association) as CNC,of which researches include resource allocation,scheduling,routing and can be taken as addressing related implementation.Still,other standardization organizations may use their previous def-i nitions.
Great progress have been made in this feild in the past two years.Literature [19] proposes a distributed technology,i.e.CFN-dyncast,which can dispatch clients’ requests to an optimal site according to the load of each computing site and the network status.Literature[20]integrates computing capability to NDN and proposes a new network framework to realize the access control optimization of computing service.Literature [21] proposes a centralized fault detection protocol,i.e.CFN-Watchdog,which achieves intelligent allocation of computing resources for edge computing according to computing load and network status.Literature [22] proposes Cyber-CFN,a technology that uses CFN for unifeid sampling in cloud native data centers.Literature [23] proposes a technical scheme of deterministic communication to realize real-time transmission and real-time computing of computing tasks.
Unfortunately,ICN and CNC cannot be used directly under the mobile network architecture.Therefore,we explore and propose an endogenous scheme based on the 6G architecture.The contributions of this paper is as follows:
1) Analyzes the distributed application addressing challenges in the evolution of mobile network,especially in 6G distributed network,and the latest researches for 5G.
2) Illustrates new progress in distributed application addressing,i.e.analyzes the mechanisms of ICN and CNC.
3) Compares ICN,CNC and those in 5G mobile network to show that they cannot adapt to the 6G network architecture.
4) Puts forward a 6G endogenous addressing scheme basing on 6G characteristic features and by converging the essence of CNC method into 6G new architecture.
5) Explains the preliminary experimental verifciation results for the 6G scheme.
The rest of this paper is organized as follows.Addressing problems and the latest research in mobile network as well as 6G addressing challenge are described Section II.Two newly mechanisms related to application addressing in carrier network are described in Section III.In Section IV,comparison between upto-date schemes is carried out.Then in Section V,a 6G endogenous addressing scheme is put forward and described in detail.Finally,Section VI concludes this paper.
II.ADDRESSING PROBLEMS AND CHALLENGES IN MOBILE NETWORK
2.1 Traditional Distributed Application Addressing Schemes
Traditional distributed application addressing,typically the requirement of CDN (Content Delivery Network) services in Internet,is resolved by DNS(Domain Name System) service scheduling system.There are two main scheduling mechanisms,namely,HttpDNS scheduling scheme and DNS redirection scheduling scheme.
A.HttpDNS scheduling
This scheme is mainly used in the scenario where CDN service provider deploys HttpDNS server to execute scheduling task.As shown in Figure 1,where the serving system includes a CDN central node and multiple CDN edge nodes,and the DNS server is confgiured in the UE.The process is described as follows:

Figure 1.Schematic diagram of the CDN HttpDNS scheduling method.
1) UE initiates a DNS request to the confgiured DNS system,the confgiured DNS system resolves the FQDN and returns the IP address of HttpDNS server of the CDN service provider.
2) UE initiates a CDN service request to the HttpDNS of the CDN service provider with the IP address got in step 1.
3) The HttpDNS server determines the nearest CDN node by matching the scheduling rules,considering the UE location according to the network address of the UE where the UE location can be roughly determined,then responses a redirect message guiding the UE to redirect to the edge service node.
4) UE redirects to the edge service node.
5) The hit content on the edge service node is returned to the UE.
B.DNS redirection scheduling
This scheme is mainly used in the scenario where DNS recursive system is used to execute DNS requests,as shown in Figure 2 where the serving system includes a CDN central node and multiple CDN edge nodes,and the confgiured DNS server and the authoritative DNS form part of the DNS recursive system.The process is described as follows:
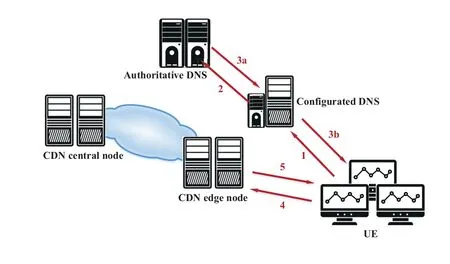
Figure 2.Schematic diagram of the CDN DNS redirection scheduling method.
1) UE initiates a DNS request to a confgiured DNS server.
2) The confgiured DNS server forwards the DNS request to the authoritative DNS server through recursive handling,the authoritative DNS server do matches with scheduling rules,and determines an edge service node according to the UE location roughly determined by the IP address of the confgiured DNS server.
3) Local DNS server acts as a proxy and returns the Edge service node IP address.
4) UE accesses to the edge service node.
5) The hit content on the edge service node is returned to the UE.
2.2 Addressing Problem in 5G
Mobile edge computing is fristly introduced in 5G network.It enables operator’s and 3rd-party’s services to be hosted close to the UE’s access point of attachment,so as to achieve an effciient service delivery through the reduced end-to-end latency and load on the transport network[24].Supporting user plane(re)selection,local routing and traffci steering,session and service continuity,etc.,are characteristic features of 5G networks.However,5G did not consider network collaboration with the application layer addressing mechanism in its initial edge computing design.Addressing,which from the view of 5G network,can be taken as resource discovery(RD),is one of the main challenges in edge computing [25],and the challenge is essentially because of deep marginalized deployment of application,as well as mobility of UE.Further,when UE moves,in order to maintain the characteristics of the nearest serving,the address of both UE and edge applications may change,the network should always maintain the connection between UE and the nearest service node,while ensuring that all the changes caused by network address changing are synchronized to the application and application changes are unperceived to the user,which is the ultimate objective of distributed application addressing.
In the scenario of 5G mobile edge computing,UE location cannot be directly judged from its network address or the IP address of local DNS,therefore,the key to solve the addressing problem lies in how the network helps the 3rd party HttpDNS systems or the authoritative DNS servers to obtain suffciiently fnie UE position.
Edge computing has been widely used in 5G,but it is mainly used in edge private networks for nomadic UEs.This situation is not because general Internet UEs have no need for distributed application services,but that addressing problem is an obstacle to provide such services.Nowadays,there is no effective method to solve distributed addressing problem in 5G existing network.
2.3 Two Potential 5G Addressing Schemes
2.3.1 Mobile Core Network Enhancement Scheme From the perspective of the network,the mobile core network enhancement scheme,based on the principle of retaining existing DNS procedure for traditional distributed applications with no change on client,no modifciation on application logics,introduce a new network function called EASDF(EAS Discovery Function)to assist localized service discovery.EASDF can obtain the UE location from other network function.Utilizing DNS enhancement mechanism,EASDF adds EDNS Client Subnet (ECS) enhancement information into the DNS request messages for specifci FQDN (Fully Qualifeid Domain Name) before forwarding them,where ECS carries UE location related information,thus the 3rd party scheduling systems or the authoritative DNS servers can obtain relative fnie UE location.
Session Breakout is the most used connectivity model for Internet UEs where a PDU (Protocal Data Unit) session has a PSA (PDU Session Anchor) UPF(User Plane Function) in a central site (C-PSA UPF)and one or more PSA UPF in the local site (LPSA UPF) [26].As a typical example,a discovery procedure for session breakout connectivity model is illustrated in Figure 3 where gNB (next generation NodeB),AMF (Access and Mobility Management Function),SMF (Session Management Function),EASDF are all network functions of 5G system.When UE establishes a PDU session,SMF selects an EASDF and includes the IP address of the EASDF as DNS server/resolver for the UE in the PDU Session Establishment Accept message.

Figure 3.Illustration of mobile core network enhancement scheme.
The relevant steps are described below:
1) The UE sends a DNS Query message to the EASDF in order to access some edge application.
2) The EASDF is provisioned with the DNS message handling rule(s),before the DNS Query message is received at the EASDF or as a consequence of the DNS Query reporting.
3) The EASDF handles the DNS Query message received from the UE according to DNS message handling rule as the following:
• The EASDF adds the EDNS Client Subnet option into the DNS Query message and sends it to central DNS server,or
• The EASDF sends the DNS Query message to the Local DNS server.
4) If the DNS query message is forwarded to the authoritative DNS server or 3rd party HttpDNS,the authoritative DNS server or HttpDNS selects a proximity edge service node and returns its address based on UE location information in the eDNS packet,or,if the DNS query message is forwarded to the local DNS server,the local DNS server might probably resolve it directly.In the situation where the local DNS server have no matching items for this DNS message,it will further forward it,just as the central DNS do,and UE location information can be judged by the address of local DNS server.
5) EASDF receives DNS response and sends the DNS response to UE.
6) The UE can then access to edge application node according to the IP address in the DNS response.
2.3.2 Edge Application Layer Enabling Architecture Scheme
Edge application layer enabling architecture scheme is an application layer solution.It defnies an application layer architecture for enabling edge computing,which includes the following functional entities[27]:
• Edge Enabler Client (EEC): EEC provides supporting functions needed for AC(Application Client)(s),including those of discovery of EAS(Edge Application Server)(s),i.e.distributed application addressing.
• Edge Confgiuration Server (ECS): ECS provides supporting functions needed for the EEC to connect with an EES such as provisioning edge confgiuration information for the EEC to distinguish amongst the EESs.
• Edge Enabler Server (EES): EES provides supporting functions needed for EASs and EEC,including registration functionalities for EAS which enable getting EAS deployment information,EEC context transferring between EESs,exposing events related to ACT (Application Context Transfer),etc.
The architecture is illustrated in Figure 4,where the EDN (Edge Data Network) is a local data network,EAS(Edge Application Server)and the EES are contained within the EDN.Confgiurations related to the EES provided by ECS includes details of the EDN hosting the EES.The UE contains AC (Application Client)(s)and the EEC.The EAS(s),the EES and the ECS can interact with the 3GPP Core Network.
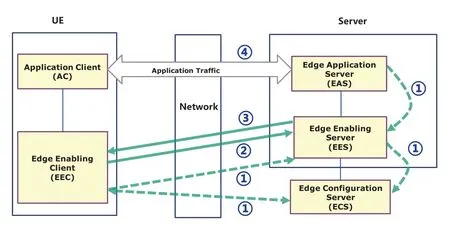
Figure 4.Illustration of edge application layer enabling architecture scheme.
The application layer architecture provides mechanisms for an EEC to discover available EASs.EAS discovery procedures enable the UE to obtain information about suitable EASs of interest (specifeid as discovery fliters)in the EDN.EES is confgiured with ECSP(Edge Cloud Service Provider)’s policy for EAS discovery.Enabler entities interact with each other to transfer UE location,capability,application deployment information,service strategy,etc.or,obtain network information,user information,as well as request network to implement network QoS policy through network exposure.EES might triggering the EAS instantiation on demand and execute ACR(Application Context Relocation)related operations.
A typical implementation process is illustrated in Figure 4 and described as follows:
1) EES registers to ECS,EAS and EEC register to EES.EEC obtains the EES address for its location and relative application from ECS.
2) EEC sends an EAS discovery request to the EES,including security credentials,EAS discovery fliters and may also including UE location.
3) When the EEC is authorized,the EES checks if UE’s location information is available,and obtains the UE location by utilizing the capabilities of the 3GPP core network if not available,then the EES identifeis the EAS based on the provided EAS discovery fliters and the UE location.
4) Upon receiving the EAS discovery response,the EEC uses the endpoint information for routing of the outgoing application data traffci to EAS(s),as needed.
III.NEW PROGRESS IN DISTRIBUTED APPLICATION ADDRESSING
Although there are some potential solutions for 5G application addressing,they are either coupled with the 5G network architecture,which is based on the network architecture of logically centralized control plane and supposed to be different from the 6G network composed of edge autonomous subnets,or relied on great changes in application layer.Therefore,even if the 5G scheme is introduced to the 6G scheme,it cannot be used as a universal scheme.
After reviewing the latest research,we found that the goals and ideas of application addressing and computing/application&network convergence control are consistent.Below,two typical up-to-date methods in carrier network based on convergence control are described,namely ICN distributed addressing scheme and CNC addressing scheme.
3.1 ICN Distributed Addressing Scheme
There are two ICN construction types,one is to completely change Internet’s IP-based architecture and addressing pattern,by defniing a totally new set of routing mechanism,another is aimed at graceful evolution and reuses the existing IP infrastructure,operates on top of IP protocol stack[28].Because ICN routes by contents,stripping the relationship between contents and UE locations,it can easily solve mobility problems[29].Besides,ICN uses publishing/subscription interactive pattern,with ICP publishing content flies and user subscribing to content with content name,enables decentralized networking,and thus improves transmission effciiency.
NDN(Named Data Networking)is one of the mainstream implementations of ICN.NDN data pieces are identifeid by application-defnied names [30].NDN router maintains three modules,namely,Content Store(CS),Pending Interest Table (PIT),and Forwarding Information Base(FIB).
The application/content addressing process is illustrated in Figure 5 and briefly described below:
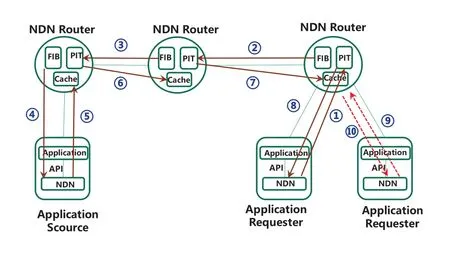
Figure 5.Illustration of NDN distributed addressing scheme.
1) ①to ④: When NDN router receives the interest packet,it checks if the corresponding content is cached in the CS
a) Yes: Directly replies with the Data packet;
b) Not: Checks PIT for matching entries;
i.Matched: Records the ingress interface receiving the Interest packet without forwarding
ii.No matched: Forwards interest packet according to FIB and forwarding policies,adds the corresponding PIT entries,or discard the interest packet based on relevant information.
2) ⑤to ⑧: As long as receives corresponding Data packet,the NDN router forwards the packet according to corresponding PIT entry,removes the corresponding PIT entry,and decides whether to update the content stored in the CS according to caching policy and replacement mechanism.
3) ⑨to ⑩: If the content is newly cached in step 2,next time,it will be directly return to the requester.
3.2 CNC Addressing Scheme
As described in literature [31],the computing network architecture system is logically divided into four functional modules: Computing Service Layer,Computing-aware Routing Layer,Computing &Network Orchestration and Management Layer,and Computing &Network Infrastructure Layer,as shown in Figure 6 and described below:
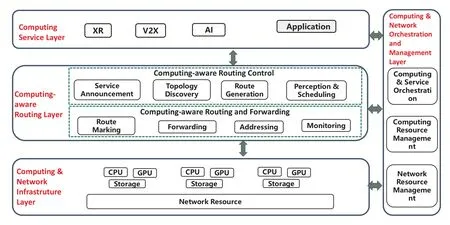
Figure 6.General architecture of CNC.
• Computing Service Layer: This layer is composed of applications and capabilities of resolving service SLA,and transfers resolved SLA to the Computing-aware Routing Layer.
• Computing-aware Routing Layer: Based on the perception of computing node status and service requirements,this layer dispatches different computing nodes for the service,and feeds back the results to the Computing Service Layer.
• Computing &Network Orchestration and Management Layer: This layer realizes operation,orchestration and management of computing services,and manages computing-aware routing strategies,computing resources and network resources.
• Computing&Network Infrastructure Layer:This layer is composed of computing and network resources,and provides ubiquitous and heterogeneous computing resources,such as CPU,GPU,etc.and network transmission.
CNC perceives all available computing and services requirement with no need for users to understand deployment states or locations of application services.For it,addressing to the optimal existing service nodes can be dynamically scheduled,new service nodes can be deployed or the existing network and computing resources be adjusted dynamically if the existing service nodes cannot meet the service SLA.
The Computing-aware Routing Layer supports two basic implementation mode,namely centralized control mode and distributed control mode.
In the centralized mode,the centralized platform(also known as the controller)collects the resource information and implements dispatching strategies,selects the appropriate computing resources and establishes the network connection according to the service requirements.It collects status of each computing node and network resources,constructs a unifeid view of entire resources,and further produces traffci strategies and establishes forwarding path among computing nodes.
In the distributed mode,resource information is announced as routing indexes among network nodes by the extended routing protocol,addressing and routing are achieved synchronously when routing convergences.
An example of the distributed control mode is illustrated in Figure 7 where R1~R6 are network nodes executing computing-aware routing,wherein computing gateway receives resource registrations and user service requests.The basic steps are described as follows:
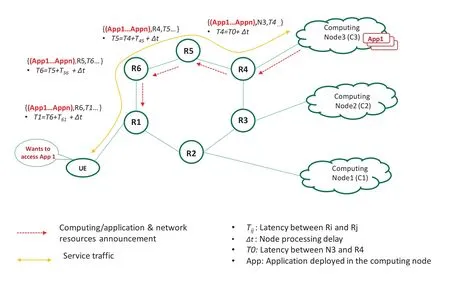
Figure 7.Illustration of CPN addressing scheme.
1) Each computing gateway node constantly perceives and collects the status of network resources and computing resources in real time.These measurements,as well as application/content IDs,will be announced among the network nodes[32].Each node runs computing-aware routing protocol until routing tables for application/content have been set up.
2) When UE initiates a request for an application service,application requirements such as bandwidth,delay,packet loss,application ID computing power requirements etc.,are resolved to routing indexes.When network nodes receive the request,they will forward it by matching their routing tables or executing other routing rules,eventually,the request will be forwarded to the optimal application service node.
The advantage of distributed control is that the control logic is decentralized,and the effects of errors is relatively small.However,given computing status is an unstable factor,it is easy to cause route oscillation.Centralized mode can achieve more flexible and effective overall optimization through unifeid control,but it is necessary to prevent the concentration point from becoming a bottleneck.
IV.COMPARATIVE ANALYSIS OF UP-TODATE SCHEMES
This section compares the four schemes described in Section 2.3 and Section III on the additional requirements on existing UE,server side functions,network functions,and conformity of evolution,as well as maturity,as shown in Table 1.
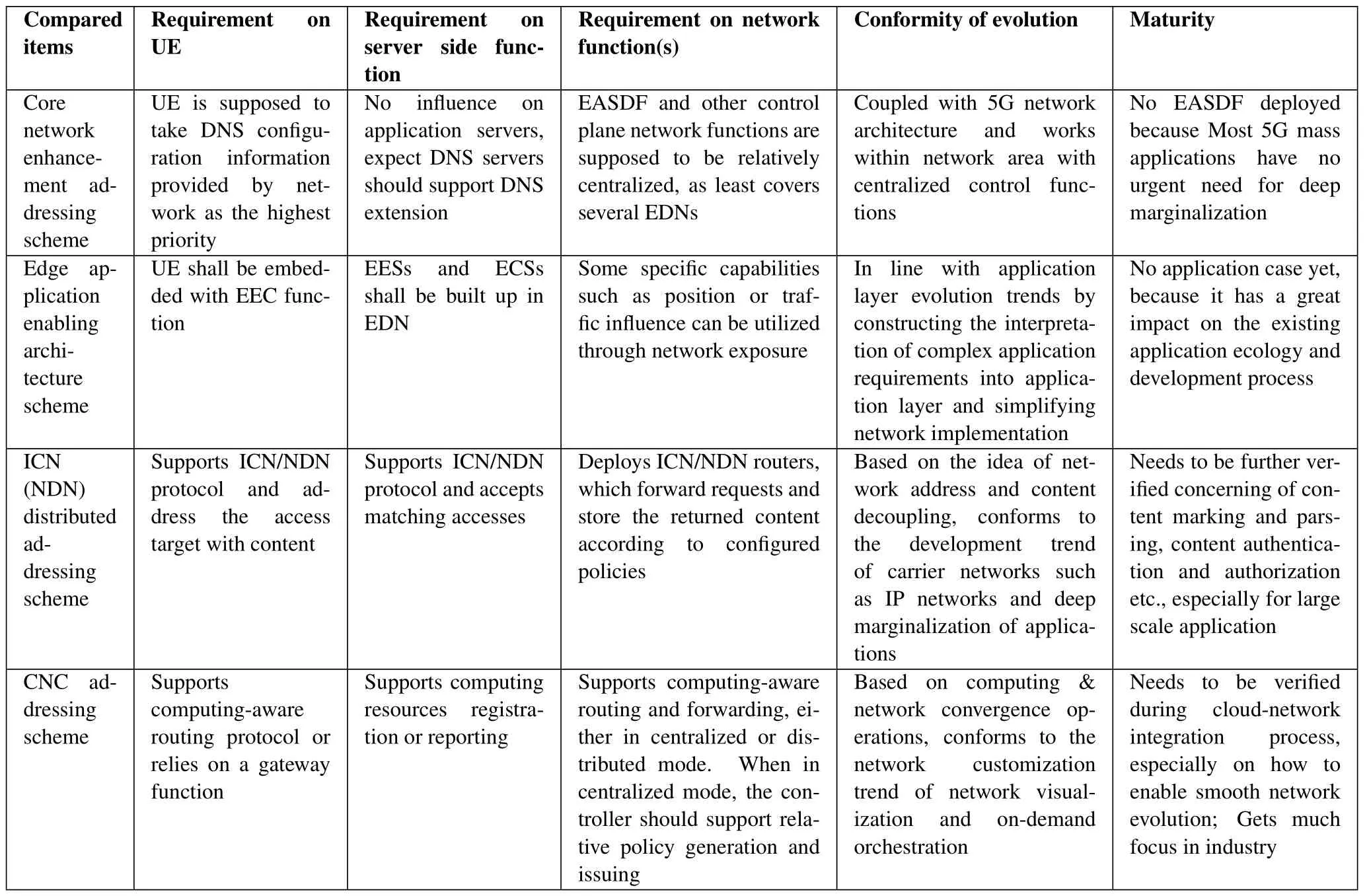
Table 1.Forwarding and control delay under different number of application instance.
Core network enhancement scheme is based on 5G network architecture and existing mobility and session management control mechanisms.It is a plug-in scheme,low threshold for use,but it’s designed based on 5G network architecture with centralized control plane thus suitable to be used as a recent solutions or transition solution.The general conditions of relatively centralized deployment will be broken in 6G era,leaving limited room for this scheme to be applied.
Edge application enabling architecture scheme introduces enabling functions at the application layer to convey application confgiuration and service strategy information.It can cooperate with mobile network by utilizing network exposure and simplify network implementation,simultaneously solve the application continuity problem in a single procedure,i.e.ACR procedure.However,it requires the application ecology be enhanced to support enabling entities.As ecological transformation is concerned,it depends on upstream and downstream industrial ecology to cooperate.
ICN addressing scheme is in line with the developing trends of network distribution,and is a distributed addressing implementation in nature.However,it puts too many transformations on existing networks and mechanisms and still needs many verifciations.ICN has different technology branches,the overlap method implemented on IP protocol stack seems more mature,but the superimposed protocol stack somewhat affects its application performance.In short,from the current research perspective,ICN is unable to fundamentally change the Internet protocol system either in fxied Internet or mobile Internet,and is more suitable for a limited range deployment.
CPN addressing scheme is in line with the developing trends of computing&network convergence.Besides solving distributed addressing problem,it solves other problems concerning flexible resource orchestration and dispatching.Although CNC scheme is still to be improved technically,it can reuse SRv6 routing mechanism or SDN implementation and it is more favored by operators and in academic circles.CNC is regarded as an important feature of 6G networks and gets much focus.Industrial supports greatly accelerate the maturity of the technology,it can be used directly in next generation fxied network,but still cannot be introduced into 6G network without any reform.
In general,from the perspective of 6G network,distributed application addressing solution should not be a plug-in one,and it’s not suitable to use an application layer solution as a basic one.The essence of CNC can be absorbed,but the key is to consider how to integrate relative ideas designed for carrier network into the 6G network architecture.
V.A ENDOGENOUS 6G APPLICATION ADDRESSING SCHEME
5.1 Methodologies
Below are some methodologies for constructing a 6G scheme:
• As application addressing is critical for application service performance,it should be a capital construction rather than a plug-in.
• When the physical address and content are separated due to the deep distribution,it is better to consider the computing and application characteristics in the addressing design,rather than the target IP address.
• Based on the characteristics of 6G computing&network convergence and dynamic orchestration,considering the coordination with the requirements of on-demand application deployment of applications and end-to-end performance guarantee,the CNC addressing mechanism is selected as the reference benchmark.
• Thinking about 6G scenarios,the demands of applications on computing and the network can be very different.The resource status of computing nodes may change frequently.As described in 3.2,under the CNC distributed control mode,continuous state changes are likely to cause route oscillations,resulting in network performance andreliability degradation,while the centralized control mode is compatible with the anchoring based session management mechanism of mobile networks,and it is easy to integrate with the programmable SRv6 protocol that is recognized as the 6G carrier network technology,therefore,the application addressing infrastructure of the 6G network is supposed to be built on the CNC centralized control mechanism.
• When considering how to integrate the CNC mechanism into the 6G network,combines the Computing-aware Routing Control Function of the Computing-aware Routing Layer with the 6G Network Control Layer,combines the Computing-aware Routing &Forwarding functions with the 6G Network Resource Layer.The 6G Network Control Layer collects not only network information,but also computing resource information,and achieves unifeid scheduling through a unifeid view.
5.2 6G Application Addressing Architecture
A 6G application addressing architecture based on the methodologies described in Section 5.1 is proposed below.
As showed in Figure 8,6G application addressing architecture emphasizes the design and deployment of addressing related functions in the 6G basic architecture.That is,the architecture in Figure 8 is actually the 6G architecture,includes four layers and a management body running through all layers.The details are as follows:
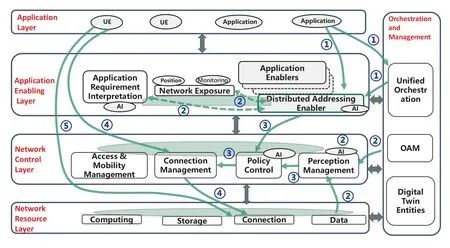
Figure 8.Illustration of 6G scheme based on 6G application addressing architecture.
• Network Resource Layer: Besides computing,storage resources,this is the executive layer of routing and forwarding.Compared to the architecture of Computing and Network Convergence,it is composed of Computing &Network Infrastructure Layer and those functions of computingaware routing &forwarding in the Computingaware Routing Layer,executing addressing routing rules issued from the upper layer.
• Network Control Layer: This is an organic fusion of computing-aware routing control functions and the know mobile network control plane functions,which receives interpreted information from applications,or by notifciations,network inspections or analyses,constructs control strategies by programmable technology and delivers them to Network Resource Layer to establish forwarding paths.Functions in this layer are supposed to be distributed deployed but cooperate organically.The application servers,i.e.the serving computing nodes,are usually determined by the policy control function in this layer when addressing is concerned.
• Application Enabling Layer: It undertakes some functions of the Computing Service Layer.It is composed of enabling components which assist the collaboration between application and network,such as network exposure function and application requirement interpretation functions,of which functionalities are built to enable UE capability negotiation,application policy confgiuration,etc.Distributed addressing enabler function,is one of the enabler components that maps application requirements to specifci network KPIs and policy parameters or providing registration service for applications so to obtain the application deployment topology and application KPIs.These parameters are passed to the Network Control Layer for setting up policies related to distributed application addressing.The enabler function can determine the serving application node on behalf of the Network Control Layer when suffciient information is obtained,and further trigger state synchronization between application instances,i.e.ACR to achieve service continuity in application layer along with that on network side.
• Application Layer: Comparatively,it also undertakes specifci functions exists in the Computing Service Layer,composed of various applications,i.e.consumers of network and computing services,such as XR,V2X,etc.Applications are usually distributed or marginalized and may be cached in network functions.
• 6G Operation &Management Layer: Corresponds to the Computing &Network Orchestration and Management Layer in computing&network convergence,it provides information about application lifecycle,confgiuration and OAM to the application addressing enabler function or policy control function.
5.3 A Schematic Process of the 6G Distributed Application Addressing
A schematic process is identifeid in Figure 8 with fgiures and one-way arrows as below:
1) ①represents application deployment procedure.The distributed addressing enabler function obtains the deployment information and KPI information of the application through the registration of the application or the interface with the orchestration or management functions when the application is initiated by unifeid orchestration function
2) ② represents perception and informationobtaining procedure.The perception management function collects resource status information from the perception entities in the Network Resource Layer through communication-sensing integration or from OAM system.The distributed addressing enabler function can use the network exposure function or obtain the assistance of the application requirement interpretation function or other AI entities to obtain network requirement parameters.
3) ③represents policy generation procedure.The perception management function and the distributed addressing enabler function transfer their perception data to the policy control function for overall analyses so to construct scheduling policies.Among these policies,the forwarding policy can be pushed to the connection management function or pulled later.Policy construction function usually uses network AI to acquire more suitable index es for applications.Corresponding forwarding rules can further be issued to the Network Resource Layer.
4) ④represents UE connection establishment procedure.When 6G Network Control Layer receives the UE’s request to access a specifci application,it frist determines a serving computing node based on UE location,resource status,UE mobility characteristics etc.and according to the scheduling polices,then indicates the Network Resource Layer to establish a connection between the UE and the selected application node.In this way,traffci forwarding can be split from computing node selection,and the control and forwarding mechanisms such as SDN can be used.
5) ⑤represents application accessing procedure.As network connection has been set up in step 4,UE can access the expected application directly.
It can be seen that 6G application addressing scheme proposed here makes full use of the characteristic capabilities of 6G,including computing &network convergence,endogenous network AI and communication-sensing integration capability,as well as innovative interactive methods between layers in 6G network architecture.
5.4 Experimental Verification
At present,6G is still in the process of exploration,and we do not have a complete 6G prototype system yet.Therefore,we verify our scheme in the aspects of forwarding policies distribution and forwarding execution,only the Network Control Layer and the Network Resource Layer are involved.It is assumed that the collection of resource status and AI analysis had been done.The experimental verifciation is conducted by open source software.Mininet [33] is used to simulate part of 6G network which includes the connection management function in the Network Control Layer and forwarding functions in the Network Resource Layer,while bind9 [34] simulates the policy control function which responds the exact application instance.We select the number of nodes(i.e.,distributed application instances) in the interval from 2 to 100,test the policy issuing (simulating session management operation because of user mobility) and data forwarding (simulating the user plane operation of mobile network) delay with 1000 tests per case,and fnially calculate the average delays.In the experiment,we assume that the network node connecting each computing node was different and connected in series,and the optimal computing node is at the end of the series.The Network Control Layer evaluates according to the addressing policy and decides the far-end computing node as the best service node and replies it to the UE.We test the forwarding delay of accessing an application and obtain control layer delay by reissuance of forwarding rules triggered by the change of computing resources.
The experimental data is showed in Table 2 and presented in Figure 9,where in Figure 9,the primary coordinate represents the forwarding delay,the secondary coordinate represents the control delay,and the dotted lines represent average values.

Table 2.Forwarding and control delay under different number of application instance.
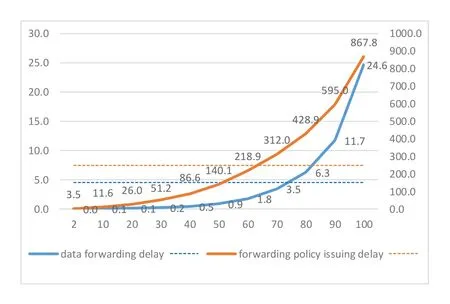
Figure 9.Forwarding and control delay under different number of application instance(in ms).
To summarize,the average forwarding delay is 0.109ms.The more nodes the forwarding passes through,the larger the delay.It can be seemed that the average forwarding delay is already in a relatively small range compared with the processing delay of ordinary services,so it can be expected that the selection of service nodes with suffciient computing capabilitywill improve the delay more signifciantly.
The control delay increases with the increase of network nodes.Compared with the empirical delay(100~250ms)of SMF executing user plane path handover due to UE mobility,the simulation results of the proposed 6G scheme are slightly larger in general,the number of network nodes might be an influencing factor.Considering the influence from the perception and AI learning process,the actual control delay will be larger in theory,so it is necessary to go in for how to optimize the control mechanism.Under simple conditions similar to that of our experiment,it is in the same order of magnitude as the average level of 5G and within an acceptable range.
To emphasize,our experiment is preliminary,and we can’t draw a conclusion about the performance at this stage,rather to fnid out the problems that need to be focused on while designing 6G.
VI.CONCLUSION
This paper frist traces back the latest development of mobile network application addressing,then analyzes two novel addressing methods in carrier network,involved schemes include mobile core network enhancement scheme,edge application layer enabling architecture scheme,ICN distributed addressing scheme and CNC addressing scheme.The paper also compares these schemes concerning conditions of necessary enhancements,maturity and conformity of network evolution trends to show they are not suitable to be applied to 6G as a whole.Based on 6G basic architecture,an 6G endogenous application addressing architecture and corresponding scheme are proposed,integrating essence of CNC addressing schemes and making use of key capabilities of 6G,including computing &network convergence,endogenous intelligence,communication-sensing integration,etc.The methodologies,addressing architecture,a schematic process and preliminary experimental verifciation are discussed further for the proposed 6G scheme.It shows 6G application addressing enabling scheme is a 6G endogenous method and is in line with mobile network development trends.With no overall prototype,the experimental data cannot show the expected performance advantages,but it indicates the problems that we should pay attention to.More in-depth verif-i cation tests will be conducted while designing 6G.
ACKNOWLEDGEMENT
This work was supported by the National Key R&D Program of China (Project Number:2022YFB2902100).
杂志排行
China Communications的其它文章
- Integrated Clustering and Routing Design and Triangle Path Optimization for UAV-Assisted Wireless Sensor Networks
- A Self-Attention Based Dynamic Resource Management for Satellite-Terrestrial Networks
- A Support Data-Based Core-Set Selection Method for Signal Recognition
- Actor-Critic-Based UAV-Assisted Data Collection in the Wireless Sensor Network
- Joint Task Allocation and Resource Optimization for Blockchain Enabled Collaborative Edge Computing
- Stochastic Gradient Compression for Federated Learning over Wireless Network
