Enhancing IoT Security:Quantum-Level Resilience against Threats
2024-03-12HosamAlhakami
Hosam Alhakami
College of Computing,Umm Al-Qura University,Makkah,Saudi Arabia
ABSTRACT The rapid growth of the Internet of Things (IoT) operations has necessitated the incorporation of quantum computing technologies to meet its expanding needs.This integration is motivated by the need to solve the specific issues provided by the expansion of IoT and the potential benefits that quantum computing can offer in this scenario.The combination of IoT and quantum computing creates new privacy and security problems.This study examines the critical need to prevent potential security concerns from quantum computing in IoT applications.We investigate the incorporation of quantum computing approaches within IoT security frameworks,with a focus on developing effective security mechanisms.Our research,which uses quantum algorithms and cryptographic protocols,provides a unique solution to protecting sensitive information and assuring the integrity of IoT systems.We rigorously analyze critical quantum computing security properties,building a hierarchical framework for systematic examination.We offer concrete solutions flexible to diverse as well as ambiguous opinions through using a unified computational model with analytical hierarchy process(AHP)multi-criteria decision-making(MCDM)as the technique for ordering preferences by similarity to ideal solutions(TOPSIS)in a fuzzy environment.This study adds practical benefit by supporting practitioners in recognizing,choosing,and prioritizing essential security factors from the standpoint of quantum computing.Our approach is a critical step towards improving quantumlevel security in IoT systems,strengthening their resilience against future threats,and preserving the IoT ecosystem’s long-term prosperity.
KEYWORDS Quantum security;quantum computing;Internet of Things;fuzzy decision-making
1 Introduction
In the present context,quantum technology strengthens various application areas,such as 5G wireless connections,the Internet of Things (IoT),wearable technology,and artificial intelligence(AI).Quantum computing is a highly centralized computing infrastructure that treats and caches data from the site of generation and the cloud.Quantum extends cloud computing.Moreover,it also complements the perception of agile devices,which can work on the fringes of the network.Quantum computing delivers assorted services while synchronously handling diverse sensors,processes,users,actuators,and connectivity by putting processing competence closer to the users.Quantum setups are proficient at handling various volumes of data provincially,acting on the premise that they are fully compact and may be built into amalgamated hardware.Quantum computing could help with IoT applications and overcome the limitations of the cloud when it comes to removing time-sensitive apps.
Though quantum computing is characterized as an augmentation of cloud computing,its’weird attributes in wireless connectivity,regional subtlety,and geographical receptiveness establish new concerns about security and forensics.There are still threats that have not been well addressed in cloud security or forensics.Most of the quantum operations are galvanized by the service and the users’necessities,while the security facets are usually neglected or taken as an afterthought.The possible security hazards associated with quantum computing in IoT systems demand an in-depth analysis of significant security threats.There are various essential threats,such as data breaches,unauthorized access,data interception,and cryptographic protocol compromise.When confronted with quantum attacks,these risks exploit the flaws of classical computer techniques.The privacy and security threats and assets in quantum computing have not been methodically diagnosed.The exploration of the privacy and security threats of quantum computing for the IoT is still in its infancy.The security threats to quantum computing are a subject of fascinating debate in academia.Since quantum computing is assumed to be a non-trivial expansion of the cloud,many privacy and security threats in the ambiance of cloud computing can be expected to impact quantum computing inevitably.Quantum computing faces new privacy and security threats besides those rooted in cloud computing.Some of the security threats can be addressed by using appropriate mechanisms.Still,the apparent features of quantum computing bring up a lot of essential problems and hazards.
By utilizing its unique features,quantum computing significantly improves the IoT environment.One standout benefit is its exponential processing capacity,which makes it possible to handle the intricate data analytics and optimization activities essential to IoT operations.Faster insights and decision-making,which are necessary for real-time IoT applications,are made possible by quantum computing’s parallel processing features.Quantum computing adds revolutionary components to security and privacy.Since eavesdropping attempts destroy the fragile quantum state,which immediately reveals infiltration,quantum encryption provides ultra-secure communication.Data secrecy is supported by quantum key distribution (QKD) as a quantum-based security mechanism,which offers unbreakable encryption keys.Due to the fundamental aspects of quantum mechanics,QKD uses quantum principles to generate encryption keys among parties,making them impervious to eavesdropping efforts.Unlike traditional critical exchange systems,QKD’s dependence on the uncertainty concept assures that any effort to intercept a key’s quantum state breaks its integrity,disclosing infiltration immediately.As it directly tackles the vulnerabilities of conventional encryption techniques to quantum attacks,it provides improved security against classical and quantum attackers.
Furthermore,quantum-resistant cryptographic techniques,such as lattice-based encryption,enable security in a post-quantum future by safeguarding sensitive data even with the advent of powerful quantum computers.Such quantum-enhanced procedures strengthen IoT security by utilizing the unique properties of quantum phenomena to combat both traditional and emergent threats.Quantumresistant algorithms also protect sensitive data from upcoming quantum attacks by fending off the cryptographic dangers of quantum computers.Compared to conventional computing techniques,this quantum-based security dramatically improves IoT privacy and protection,making quantumenhanced IoT a powerful platform for secure,effective,and privacy-preserving activities.
This research study contributes by discussing the essential problems with quantum-level security in the setting of the IoT.The researchers acknowledge the IoT market’s rapid expansion as well as the growing significance of quantum computing as an essential supportive technology.The study highlights the necessity to protect private data and uphold system integrity while identifying potential security threats to implementing quantum computing in IoT systems.The main contribution is outlining a thorough strategy to improve quantum-level security for IoT devices.The authors particularly want to incorporate quantum computing methods into current IoT security frameworks.They want to build robust security systems that can withstand attacks from regular and advanced adversaries by utilizing quantum algorithms and cryptographic protocols.The research offers a hierarchical structure of quantum computing security qualities to facilitate a systematic evaluation of security methods to accomplish this goal.The study also makes use of a unified computational model of multi-criteria decision-making(MCDM)that integrates the analytical hierarchy process(AHP)and the technique for ordering preferences by similarity to ideal solutions(TOPSIS)in a fuzzy setting.With this method,it is possible to identify,pick,and prioritize essential security criteria while considering conflicting information.The present study aims at investigating more feasible and workable solutions for security concerns in quantum computing.To do this,the authors have written about the many security aspects of quantum computing,as well as their sub-aspects,to help with the management of quantum layer security systematically.In addition,the researchers have also created a ranking system to manage and prioritize the security aspects.The rank,thus obtained,will assist the academics and the industry experts in systematically dealing with the security issues in quantum computing.
In addition to the above,the rest of this research work has been organized as follows:Section 2 discusses the recent work in this domain,followed by a discussion of the recognized quantum-level security attributes and their sub-attributes.After that,Section 3 discusses the materials and methods used to find the impact of the critical security attributes selected by the investigators in preparing their hierarchical model.Section 4 compares the results obtained by this method with those obtained by the classical AHP-TOPSIS.Section 5 presents a discussion of the findings of the research study.The conclusion and future guidelines are enumerated in Section 6.
2 Literature Review
To exploit the scope of the studies cited by different researchers and practitioners,commonly used substitutes and synonyms of words were identified to do an exhaustive literature review for this research study.A thorough analysis of the previous research literature in this context shows that the present security research threats and challenges can be classified as privacy,trust,authentication,threats and attacks,security audit,and access control.This section also looks at and points out the security threats and elucidation of auxiliary areas,including edge computing and cloud computing,which comprise the quantum computing setting.To ensure a comprehensive survey and analysis for our study,we perused various search settings for some of the most pertinent research articles in this domain.A manual search using distinct search engines in the areas of quantum and cloud security has been conducted to cater to the needs of the section.
Since the users’ prime concern is their data privacy [1],privacy conservation has become an essential issue in quantum.The information used in quantum computing arrives from diverse sources,including wireless networks,IoT devices,and cloud networks.Therefore,a convenient privacy affirmation should be considered a consequential security threat in the quantum environment.In 2020,Zhao introduced a new distributed algorithm for data analytics on quantum-enabled IoT devices[2].By integrating the distributed algorithm with homomorphic encryption,the author devised a method for protecting the privacy of edge devices.Vehicular cloud computing has become one of the biggest threats to this technology.
Xue et al.[3] also presented a study in the same context.A sophisticated computation burden is securely outsourced to cloud and quantum servers with privacy conservation and confidentiality.Wang et al.[4]discussed data privacy and confidentiality in 2018.The researchers worked on quantumoriented public cloud computing and pioneered the concepts of anonymity and secure accumulation.Pseudonyms,as well as combinatorial cryptographic techniques,were among their contributions.In 2017,Lu et al.[5] investigated the device and data privacy using lighter-weight privacy-preserving data accumulation techniques for quantum and IoT processes.The homomorphic cryptography,the Chinese Remainder Theorem,and one hash chain method were used.
In 2018,Rauf et al.[6] proposed a risk-oriented trust prototype method for the IoT setting.They presented a dynamic domain-adaptive security solution.They used criteria based on response time,availability,and reliability.In their work,they used direct and indirect perception for reliance estimation.Soleymani et al.[7] worked on securing trust formulation among vehicles in 2017.The authors proposed a fuzzy trust structure based on validity and understanding.They exhibited a series of security investigations in their work.In 2017,Dang et al.[8]proposed a dynamic data prevention scheme for quantum computing for mobility management services.Their work talks about privacyaware,role-centric access control techniques.They also introduced quantum-based region verification.
In 2019,Wazid et al.[9] established that the security of quantum devices may be assured with the help of key management and authentication schemes.The authors executed adequate and lightweight exercises.Dsouza et al.[10] introduced policy-oriented resource management in the Quantum network in 2014,which supports interoperability and secure association among assorted resources in the Quantum system.In 2018,Zhang et al.[11]proposed an encouraging CP-ABE-centric access controller for a quantum computing setting where encryption and decryption are outsourced.In 2018,Vohra et al.[12]also presented a quantum-based disseminated multi-authority credit-based data access protocol.Xiao et al.[13] proposed a mixture of explanations for fine-grained ownerenforced exploration and an access agreement covering user-quantum-cloud and encountering the supply restraints of end procedures.
Stojmenovic et al.[14]proposed an authentication scheme to mitigate MITM attacks.The authors concluded that encryption and decryption methods are only sometimes well-suited due to the system’s constraints.Homayoun et al.[15] 2019 used entirely mechanized and quantum node ransomware detection methods for the quantum layer.The study also established that deep learning methods may be used.Awan et al.[16]performed a comprehensive analysis using the fuzzy analytic hierarchy process (F-AHP) to address essential difficulties in the software business.Their research sought to determine and prioritize significant concerns in the software technology business,showing substantial impediments such as a need for more resources for innovative design and organizational reluctance to adopt new methods.Malina et al.[17]concentrated on privacy issues in the context of IoT/II services and the consequences of quantum computing.They performed an in-depth study emphasizing the significance of Privacy-Enhancing Technologies(PETs)in protecting privacy in IoT/II services.Their research mapped PET systems based on post-quantum cryptographic primitives that can withstand quantum computing challenges and investigated their practical applications using case studies.They also reviewed the obstacles and prospects for post-quantum PET development.Schöffel et al.[18]investigated how prospective post-quantum fundamental encapsulation mechanisms(KEMs),as well as digital signature algorithms (DSAs),could be applied to IoT infrastructures.They evaluated the impact of these new cryptographic algorithms on energy consumption,latency,and memory requirements throughout TLS handshakes in a low-power IoT scenario.Their findings shed light on the bandwidth-related latency of post-quantum primitives,the advantages of mixing several DSAs,and the possibility of implementing different cryptographic algorithms on IoT edge devices,putting dedicated hardware accelerators to the test.Table 1 shows the meta-analysis findings of related works.
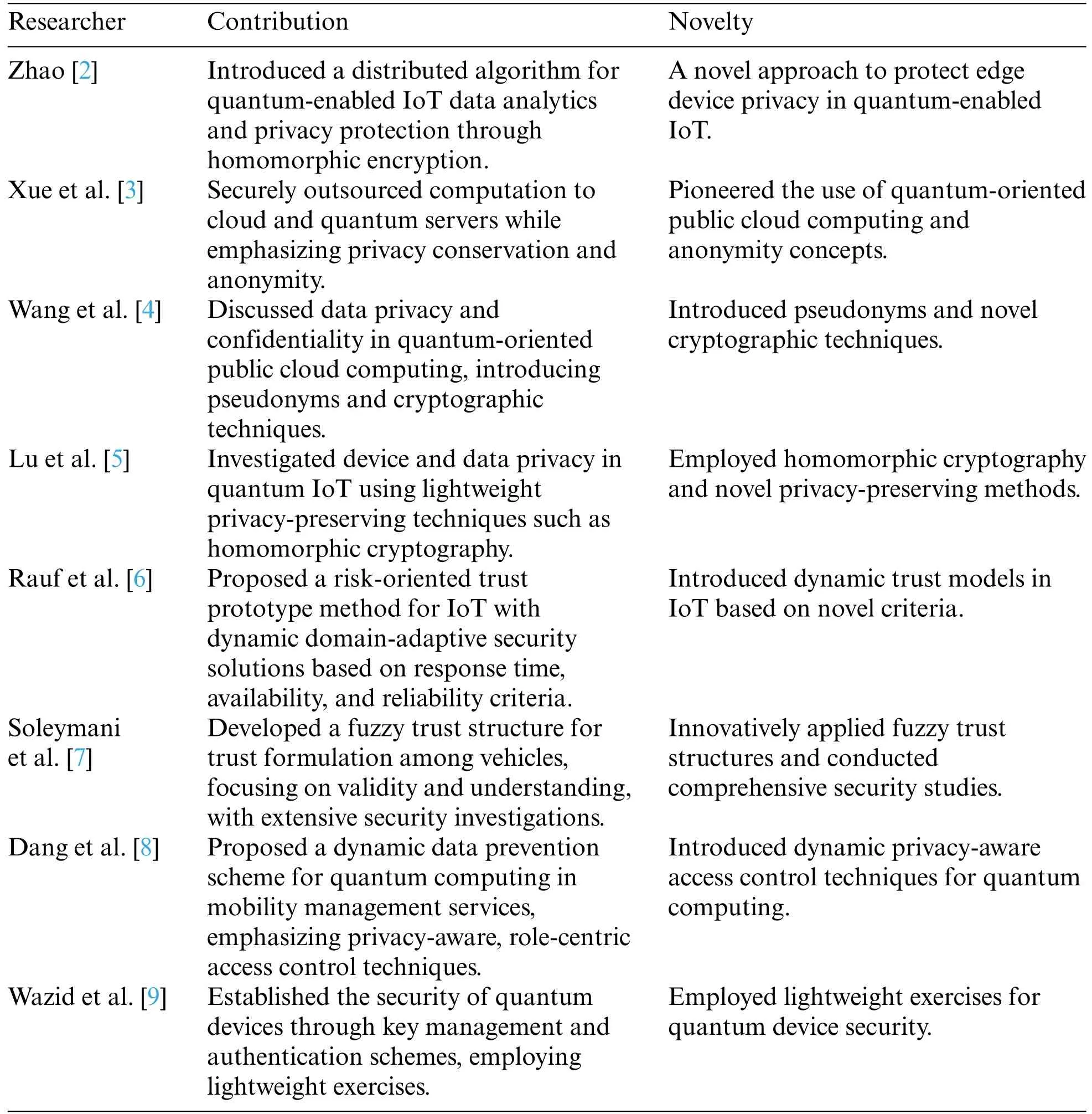
Table 1: Meta-analysis of related works
Undoubtedly,quantum computing is contemplated as being more secure than cloud computing.The collected statistics in quantum computing are cultivated and evaluated on local quantum nodes adjacent to data sources.This reduces the addiction to network connections.Further,the local data repository,transactions,and investigation make it extra challenging for the intruders to advance access to the user’s information.However,one cannot deny the number of security risks associated with data transactions between the user’s gadget and the quantum computing node or data transactions among different quantum nodes.Therefore,manifold threats exist in the process,and safeguarding privacy and security in quantum computing is not easy.Security issues can exist in diverse areas of quantum computing.The most critical areas in this context are networks,service infrastructure,virtualization,and users’devices.
There is inconsistency in the aggregation of all Quantum security-related concerns.Furthermore,only a limited number of elucidations are available to detect and prevent malicious attacks on the quantum platform.Hence,optimum security stands at the crux of ensuring the efficacy of quantum computing systems and,therefore,becomes an important research query.The lack of a thorough and unified evaluation of quantum security in the setting of IoT is the identified research gap in this study.Although the literature analysis highlights numerous research concentrating on certain quantum security issues such as privacy,trust,authentication,risks,attacks,security auditing,and access control,there is inconsistency in the way that these issues are combined into a single framework.Additionally,the study emphasizes that there are only a few ways to identify and stop hostile assaults in the context of quantum computing.Due to the dearth of thorough explanations,it is difficult to comprehend and mitigate the security risks associated with quantum computing,particularly when it comes to IoT devices.The study highlights the urgent need for an integrated strategy that takes into account all aspects of quantum security and overcomes the difficulties brought on by the special properties of quantum computing.This research gap is urgent due to the vulnerability of quantum computing caused by the many user-driven administrations of devices and the lack of strict control.As quantum computing grows more popular,creating adequate safeguards to protect IoT systems from quantum incidents becomes a critical but understudied field of research.None of the scholarly works we referred to provide a corroborative assessment of all the facets of quantum security.Quantum computing is vulnerable to astounding threats due to its segregated features.In the quantum computing environment,different users primarily drive and manage the devices.The quantum computing exemplar uses futile resources engendered by the users’gadgets.These gadgets are generally not examined by any of the definitive bodies,which can amplify the threats to security in the quantum environment.
3 Materials and Methods
3.1 Hierarchical Structure for Evaluation
As a centralized resource,the cloud exhibits an unexceptional opportunity to breach privacy.The current cloud-based security services continue to target perimeter-based safety[15–19].Cloud-based security services may cause an extreme moratorium for several applications and systems that desire impractically long-term communication bandwidth.If a threat penetrates these barriers,a system under safety will typically have finite and archaic competence to fight against the compromises.So,the current security model will not be able to protect the wide variety of IoT systems,devices,and applications.Thus,the following unique IoT security challenges need to be addressed:
• To gauge,authentically,whether a very diverse number of devices are operating securely.
• To secure an ample range of resource-constrained devices.
• To dynamically counter security breaches based on the requirements of the system and the risk levels of the violation.
Quantum computing plays an extensive role in this new security exemplar.In the realm of IoT security,traditional cryptographic protocols face vulnerabilities due to the computational power of quantum computers.Quantum algorithms,on the other hand,have the potential to solve complex problems exponentially faster than classical algorithms,which pose a significant threat to existing security mechanisms.Therefore,it becomes imperative to integrate quantum computing into the security paradigm to ensure robust protection against quantum adversaries.It administers a remedy to augment the privacy demands of the end-users of services.A quantum system is best positioned to deliver security services across diverse IoT devices [20].It is tangibly and reasonably adjacent to the endpoints.This will enable extensible and authentic oversight of various devices and execute timedemanding and resource-accelerated security assignments on behalf of the endpoints[21].Hence,any platform or system’s security basics and requirements must be appropriately investigated from the ground up.
The reciprocal interaction of quantum and heterogeneous smart devices makes security management a problematic problem under the quantum paradigm.As a result,studying all of the security elements involved has become an unavoidable concern.The hierarchical tree of quantum computing security attributes provides a structured framework for systematic and efficient security measure consideration.This method groups security risks into a logical hierarchy,providing a clear understanding of their interdependence and relationships.This hierarchy assists in prioritizing efforts and ensures that essential security aspects are thoroughly addressed.This technique offers a more strategic as well as holistic approach to strengthening quantum-level security in IoT systems by breaking down complicated security concerns into manageable components.Fig.1 depicts the hierarchal tree of the critical quantum computing security vulnerabilities,as highlighted by previous studies in this field.In addition,this shows the tree structure of the different security concerns about quantum computing that have been sorted based on research and conversations with people who work with it.Quantum computers are unable to crack encryption systems.According to the experts,quantum computers will be able to break all the current cryptographic coding schemes,including the Rivest-Shamir-Adleman(RSA),Diffie-Hellman,and elliptic curve(ECC)approaches,in a matter of time.Quantumsafe algorithms are being developed,and when a quantum computer renders today’s encryption technologies useless,such approaches will be required in government and commercial enterprises.“QDay”is the name given to the day[22].
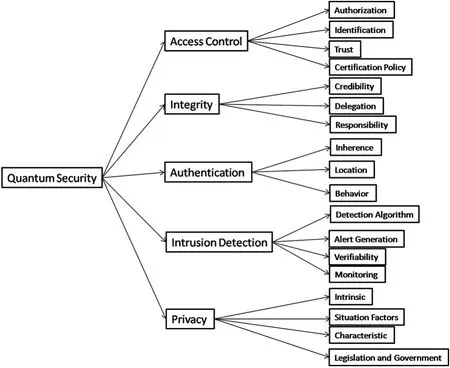
Figure 1:Tree structure of quantum security issues
3.1.1 Access Control[F1]
Access management is a security strategy in a virtualized environment that governs who or what can gain access to or use resources.It is a fundamental security notion that mitigates the threat to an organization or business.There are two kinds of access control systems: physical and logical.Physical access controls the access to academic institutions,buildings,and spaces,as well as tangible IT resources.Logical access controls the restriction of access to computer network systems,system files,and data.Workforce access to confined business locations as well as proprietary territories,like data centers,is monitored through security access control models that depend on login details,access card users,auditing,and reports.A few of these systems have access control panels that restrict who can gain entry to rooms and housing developments.They also have alarms and lockdown mechanisms to keep individuals at bay and prevent them from entering or doing things they should not.
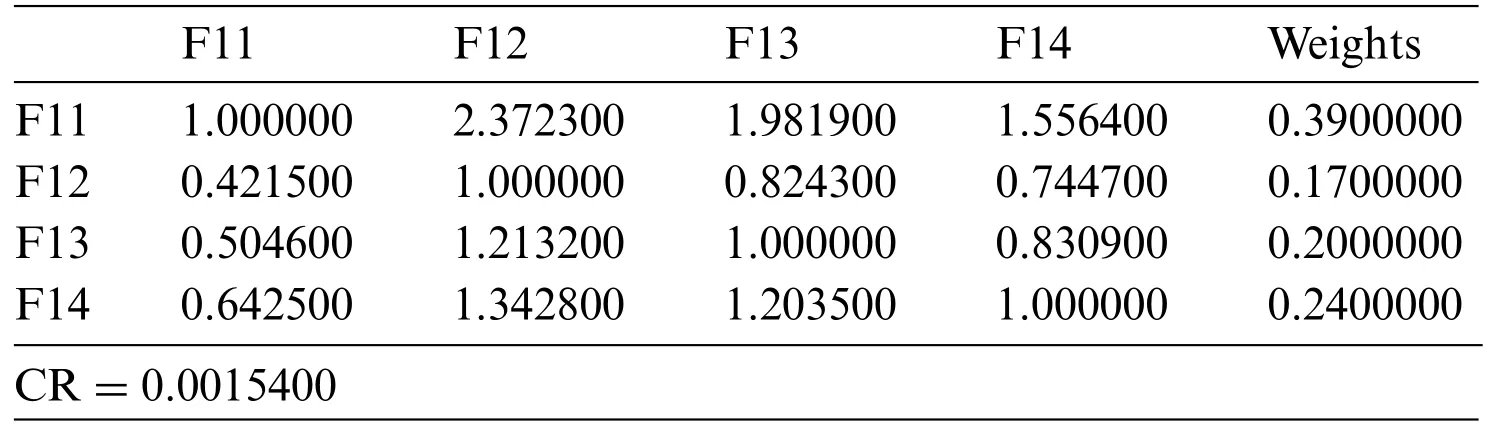
•Authorization[F11]:The process of permitting someone the right to use a resource is known as authorization[23].This explanation may appear ambiguous,but many real-life circumstances can exemplify what authorization implies and how to apply those notions to computer systems.The household’s ownership is a perfect example.The landlord has complete control over the assets(resources),and he or she can command the right of entry.
•Identification[F12]:Identification is a subject’s claim to its own identity[24].Authentication is the process of proving one’s identity by supplying credentials to an access control system.The technique that determines the subject’s access level(s)to the objects is called authorization.
•Trust [F13]:The belief in a machine’s or sensor’s ability to act consistently and securely,as well as consistently within a given environment,is known as trust [25].Cryptography,digital signatures,and electronic certificates are often used in M2M networks to establish trust.This method develops and assesses a trust chain among devices;however,it does not provide sufficient information about the feature of data transmission between machines.Information security is only one aspect of trust;it also comprises subjective criteria and experience.
•Certification Policy[F14]:Policy for users is a process in which you validate that someone who is attempting to access services and applications is indeed the one who he or she claims to be[26].This can be accomplished through a variety of certification methods.
3.1.2 Integrity[F2]
The ability to ensure that a framework and its data have not even been tampered with is referred to as integrity.Not only is data protected by integrity preservation,but even operating systems,applications,and hardware are protected from unauthorized access[27].
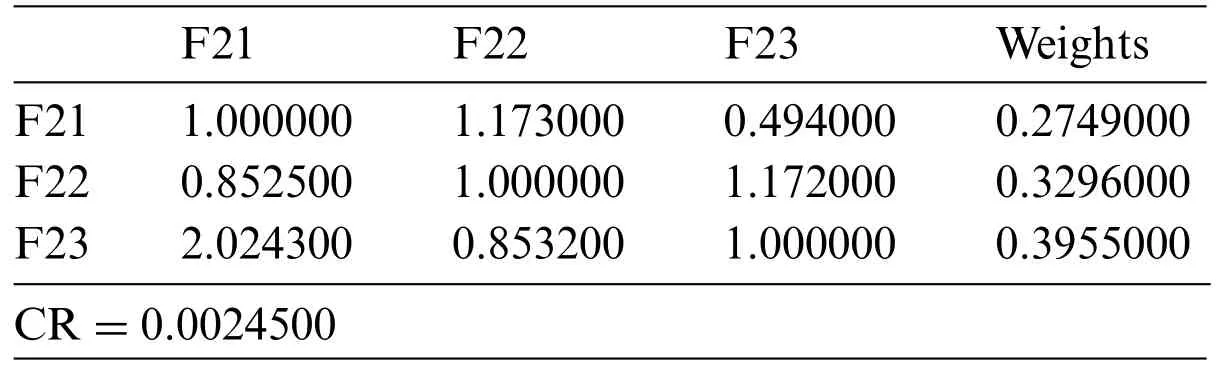
• Credibility[F21]:A key concern for companies is that they need to be trustworthy and reliable.They have to be extra careful about their systems to avoid getting into trouble with the law if something bad happens.If they do not handle data and security well,it can be a real problem[28].An example we have considered is that of an autonomous car.With no one in the driver’s seat,human error is eliminated,leaving only the systems to blame when something goes wrong.
• Delegation [F22]: Delegation is the procedure of a computer consumer handing over its authentication credentials to another user[29].In role-based access control models,delegation of authority involves delegating the roles that a user can assume or the set of permissions that the user can acquire to other users.
• Responsibility [F23]: This implies using advanced software security techniques following the technical reference architecture,implementing,testing,and running them [30].To increase software security,undertake ongoing security testing and code review.Issues that develop are troubleshot and debugged.
3.1.3 Authentication[F3]
Authentication is the procedure of validating the identity of the user or information [31].User authentication is the process of verifying the user’s identity at the time of login.Single-Factor Authentication(SFA):This was the first security solution devised.
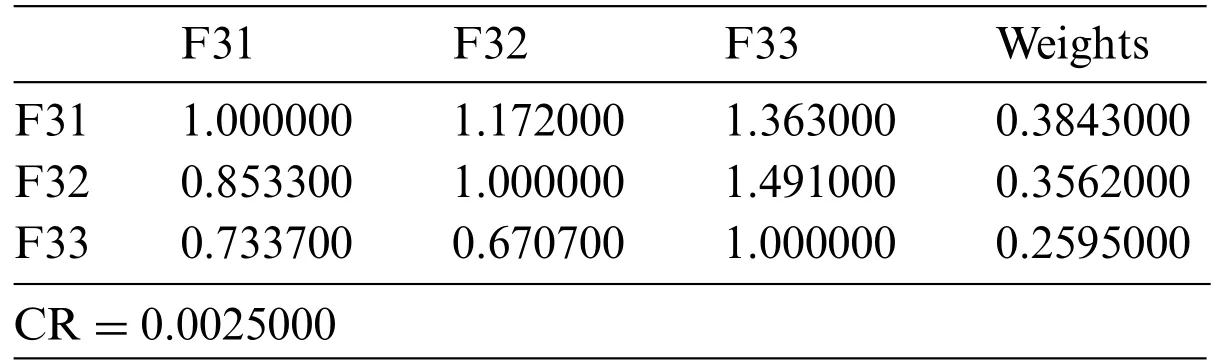
• Inherence [F31]: The inherent risk is a vulnerability that exists within an organization before the implementation of security measures[32].On the other side,residual risk is evaluated after all of these inherent hazards have been mitigated by cybersecurity measures.It considers every possible attack vector that could compromise a system or its data.
• Location[F32]:A secure location is an area in a defined site where entry is regulated by lock and key,backed up by an adequate security system,and only authorized company employees have access to that[33].
• Behavior [F33]: Behavior-based access control is a proactive strategy of protection in which all applicable actions are supervised to identify and address variances from regular patterns of behavior as soon as they occur[34,35].
3.1.4 Intrusion Detection[F4]
An intrusion detection system,or IDS for short,keeps an eye on network and system traffic for any unusual activities[36].Intrusion detection software will provide you with a notice after possible threats have been identified.
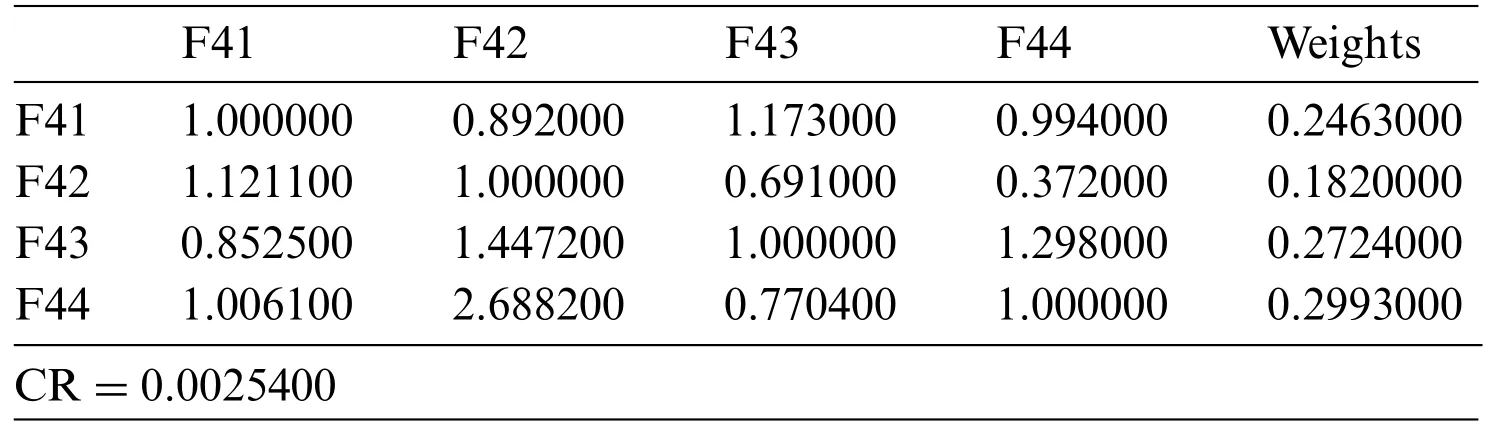
• Detection Algorithm [F41]: An intrusion detection system (IDS) is a network traffic analysis system that identifies strange activities and notifies the users when they are discovered [35].It is software that scans a computer system or network for malicious activity.Any malicious activity or policy violations are notified to an operations manager or the central monitoring unit by using an SIEM scheme.A SIEM scheme can collect data from various sources and use alarm scanning methods to differentiate between harmful and false alarms.
• Alert Generation[F42]:IT alerting software sends out notifications when a computer system fails [9–12].These tools will keep an eye on systems for issues including slow performance,infrastructure problems,and other IT management difficulties.Email,SMS,or other forms of communication may be used to provide these notifications.These tools are used by businesses to identify problems with their networks,IT infrastructure,and other IT systems to save time and prevent irreversible damage.By capturing incidents,collecting historical records,and analyzing them,some tools can help speed up the resolution and recovery procedures.
• Verifiability [F43]: Software verification pledges that “you built it right” as well as that the artifact,when carried out,meets the developers’ expectations [13].Software authentication guarantees that “you produced the proper thing”as well as that the invention,as delivered,meets the stakeholders’intended use and goals.
• Monitoring [F44]: Security monitoring is the automated process of acquiring and analyzing signals of potential security threats,prioritizing them,and taking appropriate action to address them[14].
3.1.5 Privacy[F5]
The term“privacy software”refers to applications that are designed to keep their users confidential [15].The program is generally used in combination with Internet usage to handle or restrict the amount of data made publicly available to third-party companies.The application is capable of a wide range of encryption and filtration.
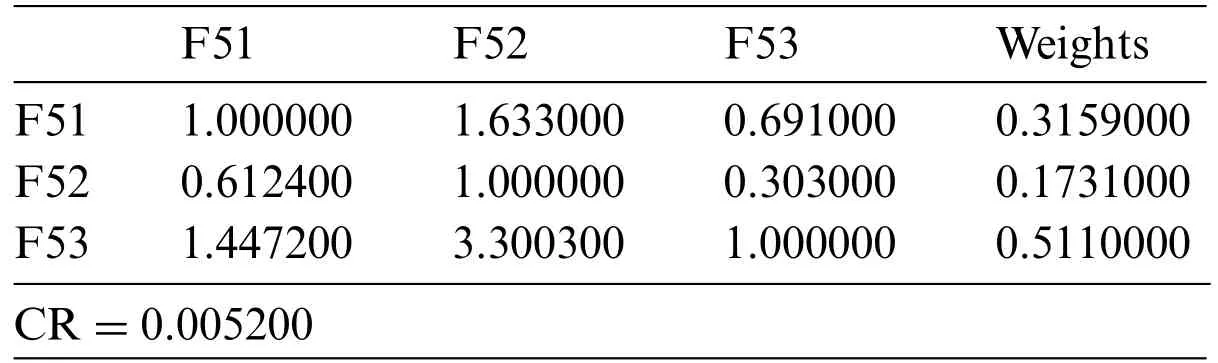
• Intrinsic [F51]: The intrinsic security model replaces the reactive model with a framework that enables the company to be proactive [16].Security is built into all of your environment’s critical control points,including the network,the cloud,endpoints,workloads,and identity management.
• Situation Factors[F52]:Human variables are psychological,physiological,and environmental characteristics that are both inherent in humans and influence how they interact with the rest of the world[17,18].Human variables such as fatigue,time of day,diversions,and even the way information is displayed on a screen are used to demonstrate the impact on how successfully individuals perform their tasks and how secure they are in industries such as aviation,trucking,healthcare,manufacturing,and nuclear power.
• Legislation and Government[F53]:Security legislation refers to all the laws that govern security protocols from time to time,along with the Aviation and Maritime Security Act of 1990,the International Code for the Security of Ships,as well as Port Facilities,and any manually configuring or substituting security legislative action[36].
3.2 Methodology
When paired with fuzzy sets,the multi-criteria decision-making (MCDM) model provides a systematic framework for choosing and prioritizing security factors in quantum computing for IoT.The model handles complicated,real-world scenarios by taking into account varied perspectives and uncertainty.This method allows practitioners to quantitatively assess security properties against a variety of criteria.It can,for example,assist in determining the most effective encryption method depending on a variety of characteristics such as processing efficiency,resistance to quantum assaults,and deployment expenses.The model could help choose access control strategies that balance user privacy,system efficiency,as well as security in scenarios involving vital infrastructure,such as smart grids.By integrating quantum computing into the security exemplar,we aim to harness the unique capabilities offered by this emerging technology to address the vulnerabilities and challenges faced by IoT systems.The extensive role of quantum computing in the exemplar underscores its potential to revolutionize IoT security and pave the way for resilient and quantum-resistant solutions.Managing security in software is the task of design management[37–40].To make an effective and secure software design,it is always significant to work on the tactics of design management[41].Hence,prioritizing this approach,the authors of the present study consulted several industry experts and researchers working in this area.After collating the recommendations given by these experts,the authors classified the various tactics and their sub-tactics.Thereafter,the next step was to design the computational model.For this,the authors adopted the most significant MCDM approach in the current era,i.e.,fuzzy AHP-TOPSIS[42–44].This approach provides an efficient and effective outcome in a situation where the user has more than one option to choose from.A descriptive discussion of the methodology is enunciated below.
Its fundamental precept is to find the highest-quality viable replacement among a set of alternative strategies and then rank all of them based on their evaluation metrics.Fuzzy-based AHP is used throughout the research to demonstrate the weights of the criterion(characteristics),as well as fuzzybased TOPSIS,which is used to prioritize the alternatives.To figure out how to calculate the results for this method,the authors had to do the following.
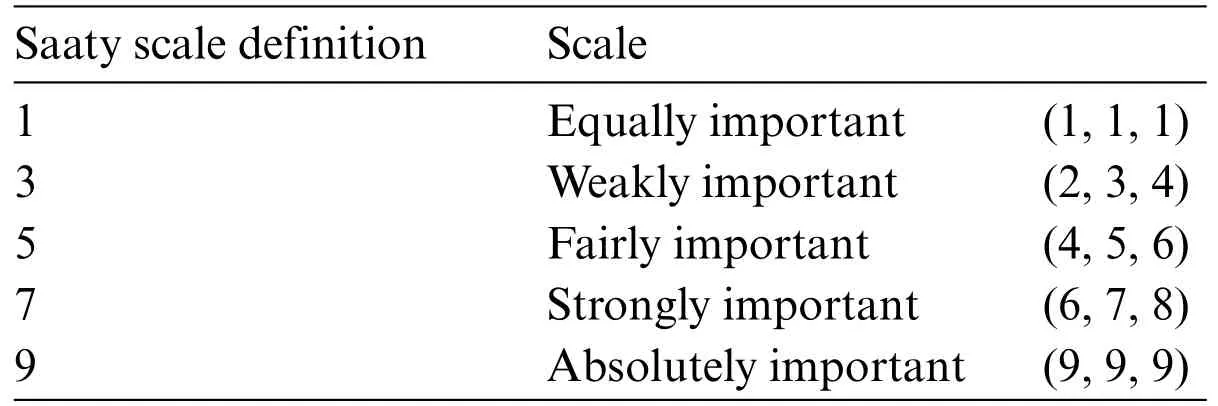
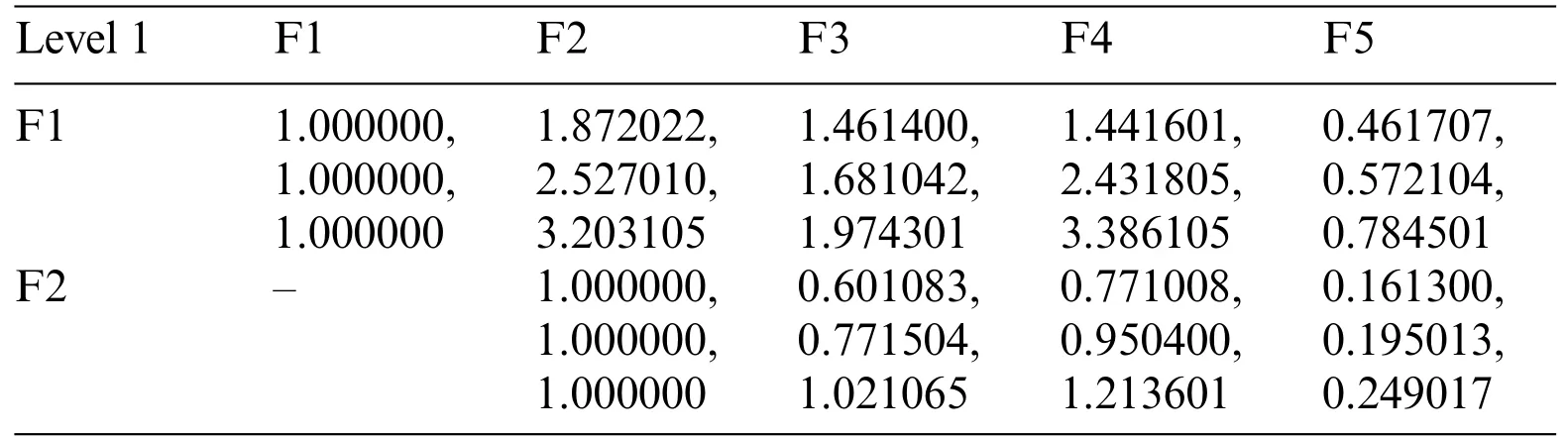
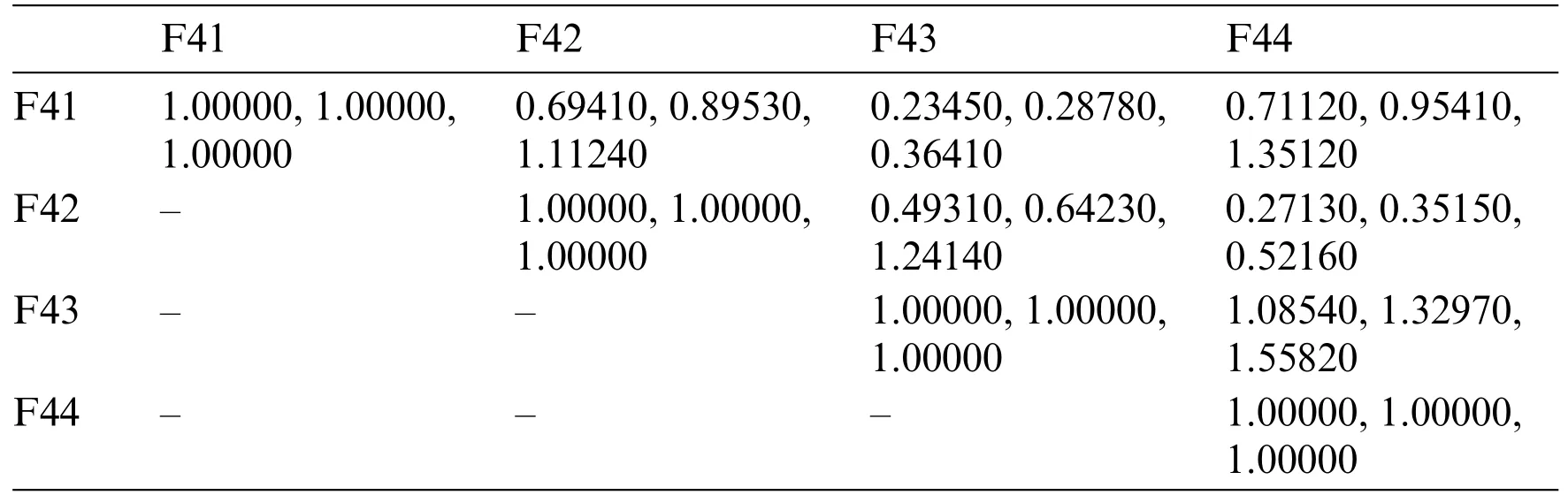
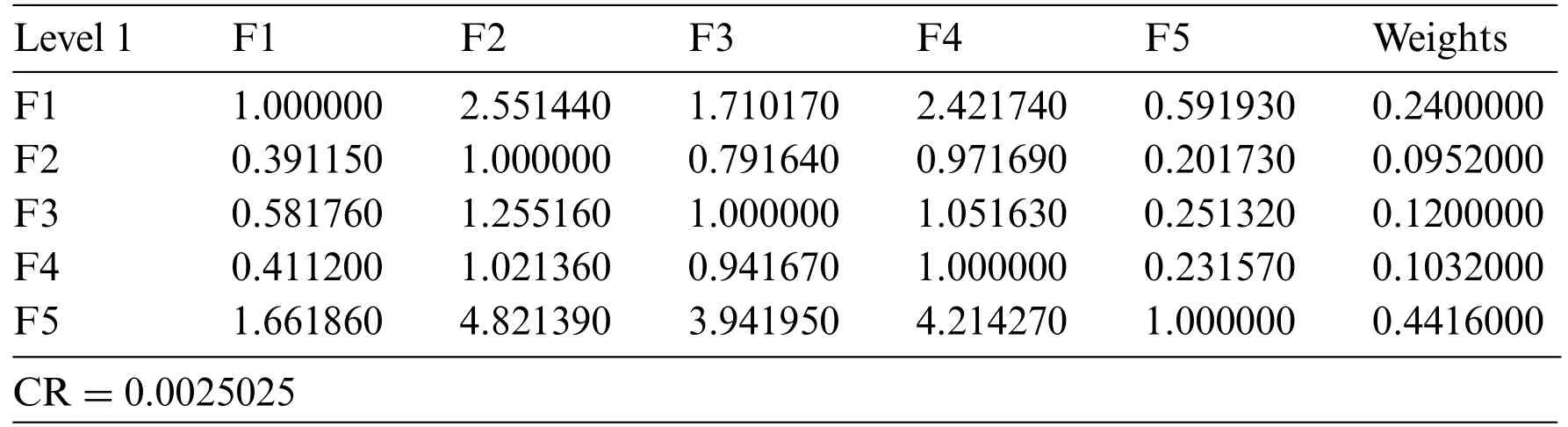
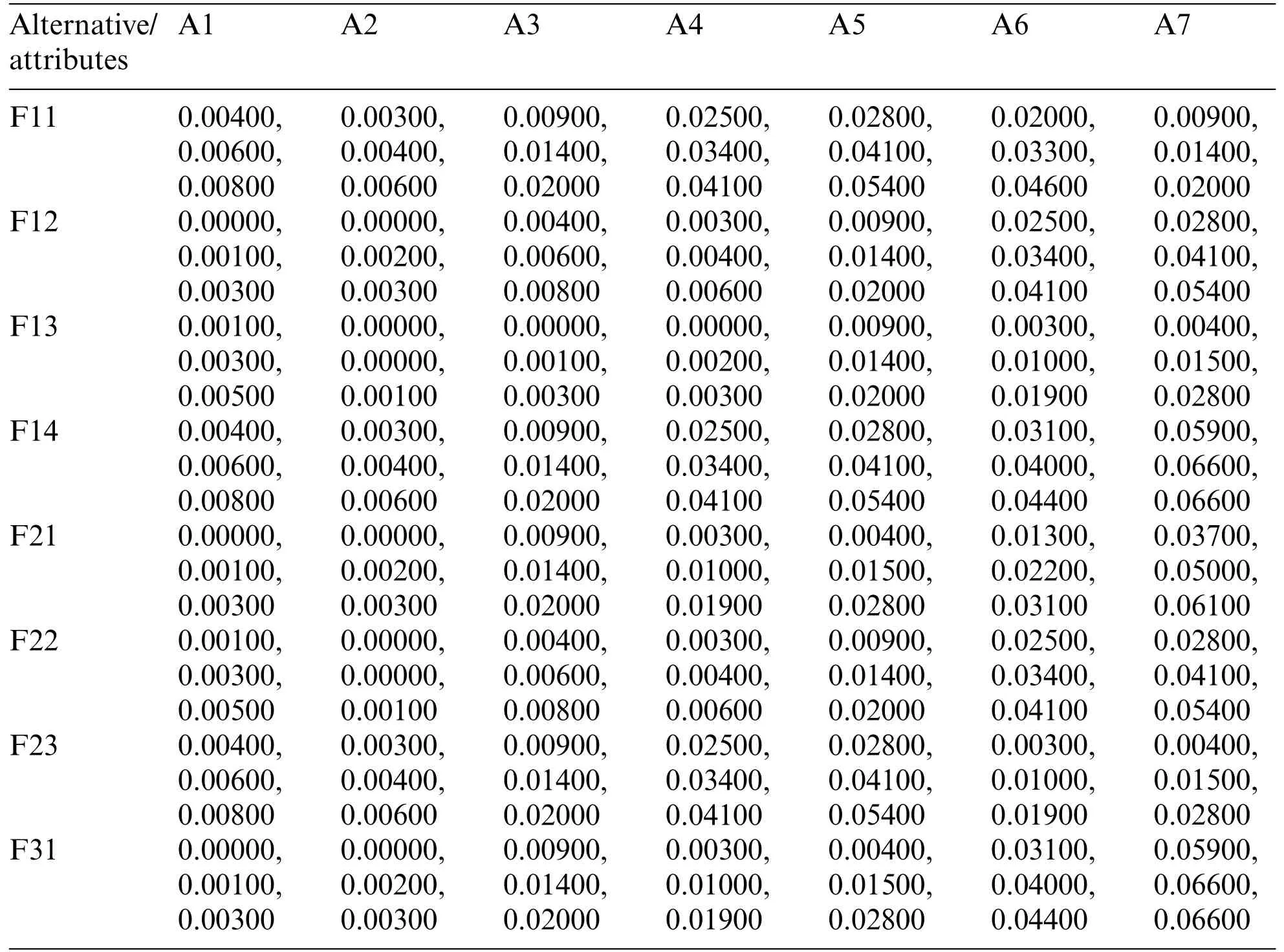
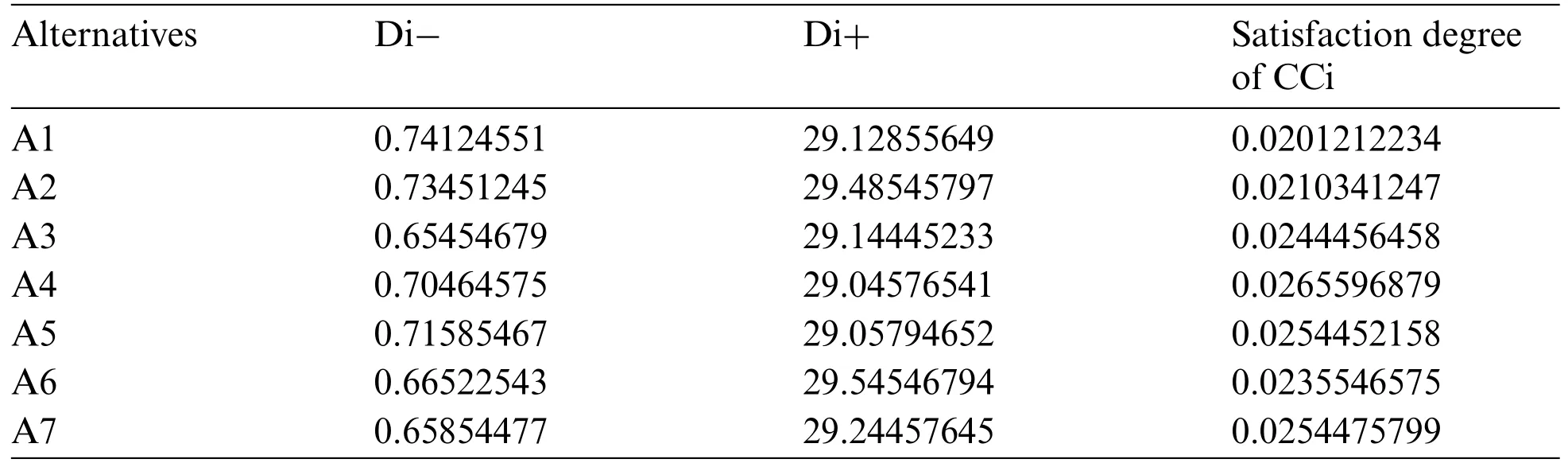
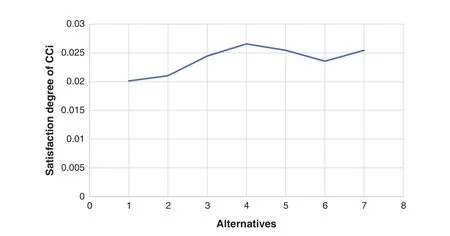
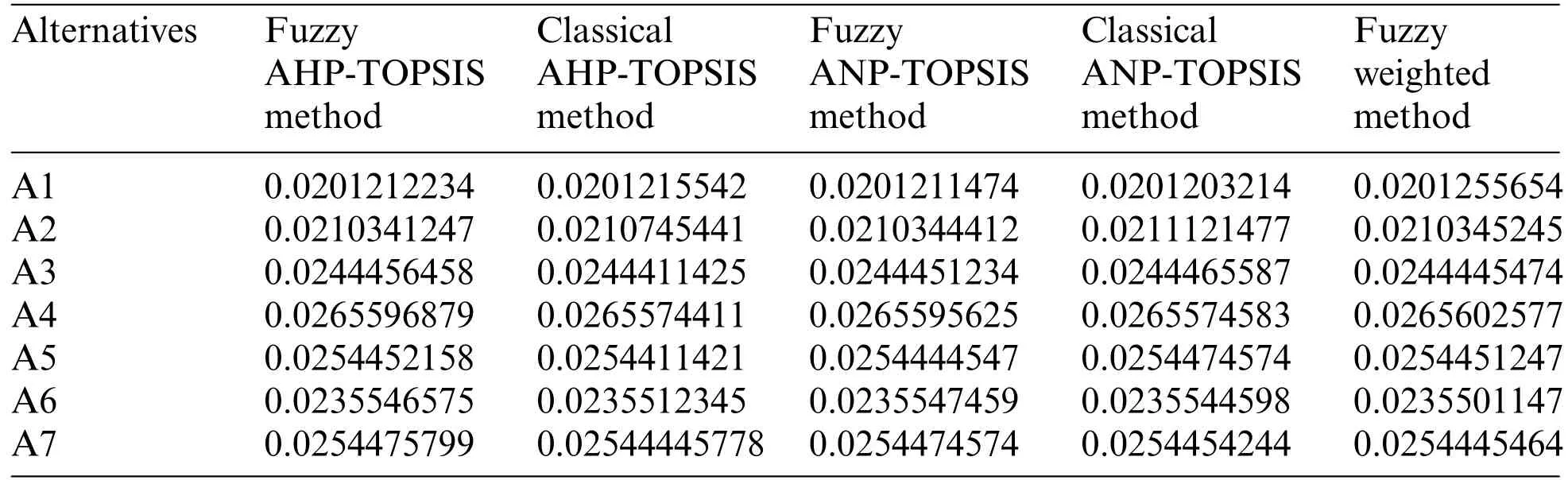
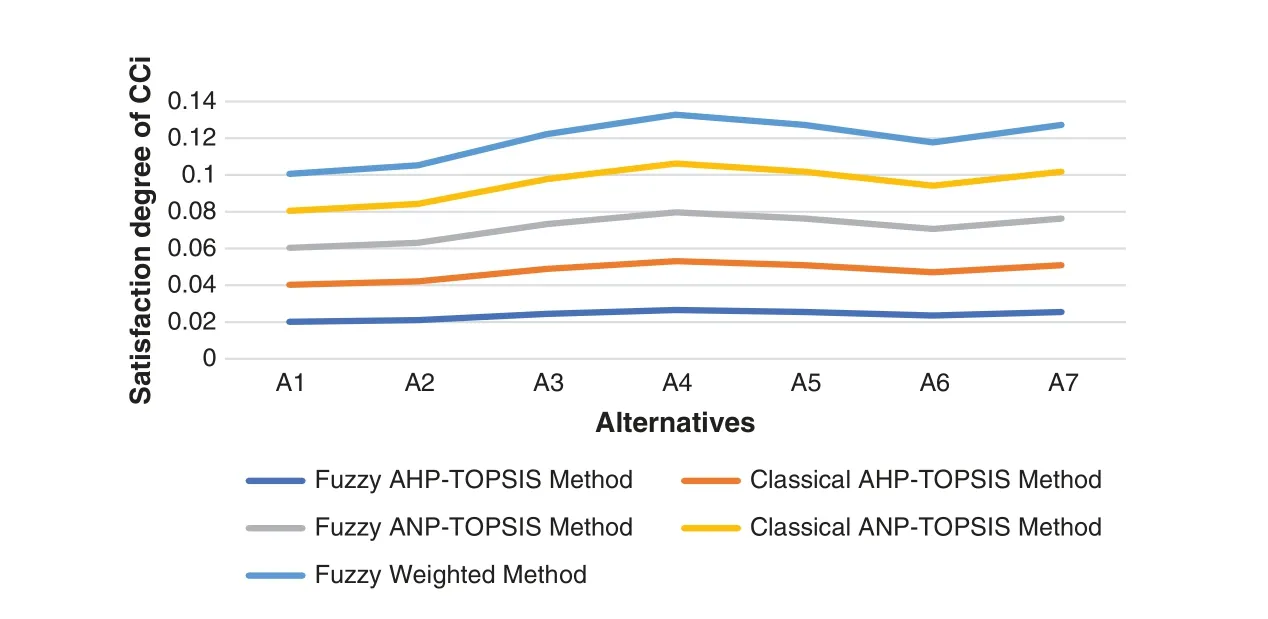
Step 1: Triangular Fuzzy Number (TFN) is architecturally a triplet (f1,f2,f3) wherein f1 As per the triangular membership function,Eq.(1),mi and u represent the lower,middle,and upper limit for triangular membership numbers. Figure 2:TFN After that,a fuzzy transformation is completed on these numeric statistics.To transform the numeric data into TFNs,Eqs.(3)–(6) are employed as well as represented as (f1ij,f2ij,f3ij),where f1ij grants low importance,f2ij grants middle importance,and f3ij grants upper importance(Table 2).Additional TFN[ij]is distinct,such as: Table 2: TFN scale Jijk denotes the degree of importance of attributes among some of the two factors using professional opinion as well as the expressions presented above.I and j are the element pairs that are evaluated and symbolized.Furthermore,the processes on the two TFNs are carried out with the assistance of Eqs.(7)–(9).Supposing T1 and T2 are two TFNs,T1=(f11,f21,f31)and T2=(f12,f22,f32).At that moment,the functioning rules for them would be: By using Eq.(12),the authors integrate the experts’opinions into the mathematical function and try to elaborate on them in it. The following Eqs.(13)–(16)are used by the authors to normalize the value and find the geometric mean of functions. Now,after conducting all these steps and solving the equations,the BNP value is determined by using Eq.(17). This completes the process for the fuzzy-AHP methodology.After this,the TOPSIS part begins.The TOPSIS methodology is adopted by the authors to test the ranking and effectiveness of the evaluated outcomes in a simulation scenario to validate the outcomes.The descriptive steps that were followed during this methodology are discussed below. By using Table 3 and Eq.(18),we prepared the correlation between the previously evaluated data and the tested alternatives. Table 3: Ranking scale Table 4: Integrated fuzzy-based comparison matrix at level 1 Table 6: Integrated fuzzy-based comparison matrix for F2 at level 2 Table 7: Integrated fuzzy-based comparison matrix for F3 at level 2 Table 8: Integrated fuzzy-based comparison matrix for F4 at level 2 Table 9: Integrated fuzzy-based comparison matrix for F5 at level 2 Table 10: Integrated comparison matrix and local weights at level 1 Table 11: Integrated comparison matrix and local weights for F1 at level 2 Table 12: Integrated comparison matrix and local weights for F2 at level 2 Table 13: Integrated comparison matrix and local weights for F3 at level 2 Table 14: Integrated comparison matrix and local weights for F4 at level 2 Table 15: Integrated comparison matrix and local weights for F5 at level 2 To make the standard of the function,Eq.(19)is used,and after that,to create the grid,Eq.(20)is utilized. After identifying all these attributes and equations,the next step is to evaluate the gap degree by the following Eq.(21). After evaluating all these equations and formulae,we found the whole simulated scenario of security tactics.This computational methodology is most effective in the current situation of its realworld application capability.The authors attempted a simulator approach to test the efficacy of the above technique. To apply the above-discussed technique in a real-world scenario,the authors prepared a security tactic based on the tree structure that has already been discussed in Fig.1.The authors applied the adopted approach of fuzzy-AHP-TOPSIS to the stated readings in Fig.1 and evaluated the results in a computational manner that would facilitate the industry’s development.Moreover,the designed tree structure has seven security domains or tactics available that will enhance the design of software and help the developers manage software security effectively. Using the method described in the previous section,the authors did the computational analysis to come up with Table 2 and Eqs.(1)–(17).Further,from Tables 4 to 9,we are showing the integrated fuzzy-based comparison matrices as per Fig.1.In addition,Tables 10 to 15 show the defuzzified values for various groups,and Table 16 represents the final weights of the attributes. Table 17: Subjective cognition results Table 18: Weighted normalized fuzzy-decision matrix After analyzing the fuzzy AHP technique and its priority list,the authors evaluated the overall impact by adopting the TOPSIS approach.To perform this approach,we took fifteen real-time projects from Babasaheb Bhimrao Ambedkar University,Lucknow,Uttar Pradesh,India.These projects’data comprised a repository of the results of quiz competitions and entrance tests held at the university over a two-to five-year period.The selected projects were taken as the alternatives in this study.The sensitivity of these selected alternatives was very high.Tables 17 and 18 demonstrate the use of the fuzzy TOPSIS method(Table 3 and Eqs.(18)–(21))to evaluate the results. For calculating the normalized values and various other computational outcomes,the authors performed the gap degree analysis of evaluated numerical values to test which alternative’s performance was the highest and which one’s was the lowest.The assessed outcomes are discussed in the following Table 19 and Fig.3.The evaluated results from the fuzzy TOPSIS approach corroborate that the results are totally verified and fairly accurate. Table 19: Closeness coefficients of the selected alternative Establishing the validity of the results is always a key point in any type of computational approach[32–36].For affirming the accuracy and reliability of any methodology,comparison analysis is the most apt methodology.In this study,the comparison was performed with four other similar techniques that are described below in Table 20 and Fig.4.All these approaches are similar to the selected one and were performed on the same alternatives for better understanding.The coefficient gap value in all these techniques is 0.7681.After a thorough analysis of the evaluated comparison analysis result,it is clear that the adopted methodology has a more effective outcome than the other selected approaches.The performance of the alternatives in the selected approach is better than the other techniques. Figure 3:Graphical representation of the satisfaction degrees Table 20: Comparison analysis Figure 4:Graphical representation of the comparative results The concept of structural security management was first developed in 2017 [11].However,even after many years of this concept,the challenges and issues of creating design-based security are still the same and even more complex due to the software’s large-scale production and application [37–42].The application of AHP and TOPSIS in the proposed scheme has significant implications beyond this research.Many authors have applied these methodologies in the context of Software Defined Networks (SDN) [43–45] and various related areas.Securing the data in the software and ensuring that the application is always sustainable continue to be formidable challenges for developers.In such a scenario,the best recourse is the suggested mechanism in this study for producing effective solutions.Several obstacles in achieving quantum-level security for IoT were identified in our research.Because quantum hardware is continually changing,one major problem is integrating quantum innovations with existing IoT infrastructures.To solve this,we concentrated on developing adaptive security frameworks that can handle evolving quantum technology.Another issue is the possible overhead of quantum encryption and computation.We overcame this by investigating hybrid techniques that efficiently exploit classical and quantum resources.Furthermore,quantum-resistant algorithms are still being developed,and the switch to these algorithms can be difficult.To ensure a gradual transition,our research suggests a staged method that incorporates both current and quantumresistant technology.These solutions allow us to address the issues posed by quantum computing while also capitalizing on its tremendous potential for improving IoT security.The proposed study adopted a computational mechanism for assessing possible significant tactics that can make any software secure.These tactics and their evaluation through the adopted computational methodology will help the developers understand and use the evaluated results as an example.Moreover,the proposed mechanism would prove to be one of the essential practices for achieving the desired level of security in a quantum computing system.The significant contributions of this study can be thusly summarized as follows: • It is always more effective to perform a numerical analysis of any situation instead of understanding it through a theoretical background. • The proposed study undertook a unique and effective quantitative analysis of security tactics through a computational approach that was developed by the quantum computing technique. • The domains or tactics selected in this study are effective and would be useful for secure web application development. • The systematic pathway proposed in the study can be employed by the developers to produce effective security in web applications. • The results of this study show that confidentiality is one of the most effective security tactics among all the ones selected. The pros and cons of this study may be listed as: Using security tactics for security management by associating a computational approach is a highly feasible,economically viable,and workable methodology for security designers working at any stage of security design.The prioritized scheme of security tactics in this study is an effective example to be alluded to during development. There is a need to focus on more security tactics.Further,the source of information used in this study is limited;there is scope for accessing different resources related to information about security tactics. Proactive strategies are required to ensure the long-term security and robustness of IoT ecosystems against quantum-level threats.To begin,ongoing collaboration among quantum researchers,IoT practitioners,as well as regulators is required to develop and update security standards that include quantum-resistant solutions.Furthermore,investment in post-quantum cryptographic algorithm advancement and research should be prioritized to effectively defeat emerging quantum threats.Furthermore,hybrid security systems that include classical and quantum algorithms can achieve a balance between IoT device security and resource constraints.Putting in place real-time monitoring as well as anomaly detection techniques can help discover quantum-based threats quickly.Also,training IoT stakeholders about quantum hazards and responses can help to create a more secure environment.Finally,incorporating quantum-safe hardware components can improve IoT devices’inherent resistance to quantum attacks.By implementing these recommendations,the IoT ecosystem will be able to navigate the quantum terrain while maintaining security and resilience when confronted with growing problems. Security management is a challenging context that demands structural security.To address this query,the authors categorized various tactics related to security and then assessed their efficiency at the quantum level by review analysis and tree structure creation.The study also performed a computational and quantitative analysis of security tactic mechanisms.The MCDM approach named fuzzy-AHP-TOPSIS was adopted for this intent.The evaluated results were tested and established as effective.Moreover,the study undertook a comparative analysis and proved that the selected approach in this study was the most effective one.For future investigations in the same league,the authors propose elaborating on the security tactics more deeply and selecting the second-level security tactics for more affirmative outcomes.We recognize that future advances in quantum technology will have a substantial influence on the security environment of IoT systems.Quantum computers have the capability of breaking traditional encryption systems,rendering present security measures obsolete.Our proposed security methods,on the other hand,may adapt dynamically.We advocate for the development of quantum-resistant algorithms capable of withstanding attacks from powerful quantum computers.Our hierarchical model and MCDM-fuzzy technique are also adaptable to developing quantum technologies.We can ensure that our security procedures stay successful in the face of shifting threats by continuously upgrading the model with the most recent quantum capabilities and weaknesses.Thus,our research presents a flexible framework that may expand in tandem with quantum advancements,ensuring the security and privacy of IoT devices.The finding provides the foundation for several intriguing potential fields of research in the field of quantum-level security for IoT.The incorporation of quantum security measures into current IoT systems could be the subject of research to promote seamless compatibility.Exploring machine learning as well as AI-driven techniques to anticipate and stop quantum-based attacks has possibilities.Strong quantum security regulations and standards can be developed through cooperative efforts involving academia,industry,as well as policymakers.The future scope intends to secure the robustness and dependability of IoT systems against the changing landscape of quantum risks by pursuing research in these domains. Acknowledgement:None. Funding Statement:The author received no specific funding for this study. Author Contributions:Study conception and design: H.Alhakami;data collection: H.Alhakami;analysis and interpretation of results: H.Alhakami;draft manuscript preparation: H.Alhakami.Author reviewed the results and approved the final version of the manuscript. Availability of Data and Materials:The author confirms that the data supporting the findings of this study are available within the article. Conflicts of Interest:The author declares that he has no conflicts of interest to report regarding the present study.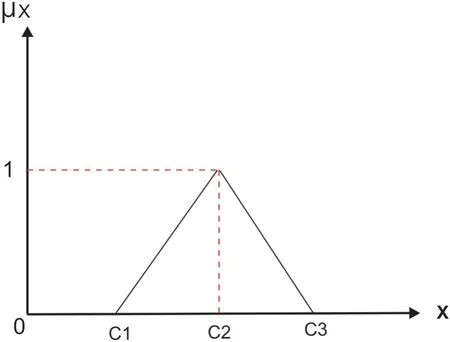




4 Data Analysis and Results
4.1 Statistical Findings

4.2 Comparison with the Classical Approach
5 Discussion
5.1 Pros
5.2 Cons
6 Conclusions
杂志排行
Computers Materials&Continua的其它文章
- Fuzzing:Progress,Challenges,and Perspectives
- A Review of Lightweight Security and Privacy for Resource-Constrained IoT Devices
- Software Defect Prediction Method Based on Stable Learning
- Multi-Stream Temporally Enhanced Network for Video Salient Object Detection
- Facial Image-Based Autism Detection:A Comparative Study of Deep Neural Network Classifiers
- Deep Learning Approach for Hand Gesture Recognition:Applications in Deaf Communication and Healthcare
