Active resilient defense control against false data injection attacks in smart grids
2023-12-01XiaoyuanLuoLingjieHouXinyuWangRuiyangGaoShuzhengWangXinpingGuan
Xiaoyuan Luo·Lingjie Hou·Xinyu Wang,·Ruiyang Gao·Shuzheng Wang·Xinping Guan
Abstract The emerging of false data injection attacks(FDIAs)can fool the traditional detection methods by injecting false data,which has brought huge risks to the security of smart grids.For this reason,a resilient active defense control scheme based on interval observer detection is proposed in this paper to protect smart grids.The proposed active defense highlights the integration of detection and defense against FDIAs in smart girds.First, a dynamic physical grid model under FDIAs is modeled, in which model uncertainty and parameter uncertainty are taken into account.Then,an interval observer-based detection method against FDIAs is proposed,where a detection criteria using interval residual is put forward.Corresponding to the detection results,the resilient defense controller is triggered to defense the FDIAs if the system states are affected by FDIAs.Linear matrix inequality (LMI) approach is applied to design the resilient controller with H∞performance.The system with the resilient defense controller can be robust to FDIAs and the gain of the resilient controller has a certain gain margin.Our active resilient defense approach can be built in real time and show accurate and quick respond to the injected FDIAs.The effectiveness of the proposed defense scheme is verified by the simulation results on an IEEE 30-bus grid system.
Keywords Active resilient defense·Attack detection·Cyber attacks·Cyber-attack detection·Cyber grid elements·Cyber threat·False data injection attack·Smart grids security·Interval observer
List of symbols

1 Introduction
With the fully integration of information and communication technologies,smart grid has replaced traditional power system [1].Using modern information technology, smart grids can realize two-way flow of information and electricity[2].However,the high reliance on computation technology makes smart grid more vulnerable to malicious attack [3].For example, three regional grid distribution companies in Ukraine in December 2015,were successively threatened by the advanced persistent threat of malicious code"BlackEnergy"within 30min[4,5].Therefore,studying the security against attacks in smart grids is of great significance to us.
Recent researches have shown that malicious attacks can pose serious threat to the security of smart grid.In [6], the machine learning methods against different malicious attacks were discussed for the detection in IoT networks.Additionally, Ashraf et al.[7] presented a network model that has been subjected to various DoS attacks to demonstrate cyber security aspect.Different from the Denial of Service attacks,FDIAs against state estimation in smart grids was first studied in[8].Subsequently,the features of FDIAs were presented in many studies[9–11].The harm of FDIAs could be reflected in the electricity market,the attacker manipulated the price of the power market to get huge financial benefits without being detected[9].As described in[10],FDIAs could damage smart grid operations by leading to load shedding for a period of time while the power grid has no effective and immediate action.In[11],FDIAs could bypass the BDD and attack the system multiple times by injecting the false data into the estimated states.These researches have shown that FDIAs can cause unexpected damage to the system quickly and repeatedly due to its concealment characteristic.Therefore,the effective real-time defense scheme is urgent.
Up to date, researches on the defense control of cyber attacks can be roughly divided into passive defense control and active defense control.Some scholars aim at passive defense control of cyber attacks, a defense mechanism was proposed by finding protected meters based on graph-theoretical method in [12].As presented in [13], a Bayesian-based approximated filter was proposed to improve the immunity of the monitoring applications against data injection attacks.In[14],a variation of the receding-horizon control law was proposed to deal with replay attacks, but the interrelated characteristic of network systems was not considered.Passive defense technology plays an important role in the security of smart grids,it can be robust to attack.However, passive defense is limited to defense ability and it depends too much on system configuration.If the attacker adopts a more effective strategy,passive defense control cannot protect the smart grids against cyber attacks.Therefore,active defense control has received more widespread attention.Some scholars focus on the active defense control of cyber attacks but the research results are not much at present.Active defense schemes co-design detection and defense of cyber attacks to protect smart grids.In [15], an Euclidean detection method using Kalman filter was proposed to detect FDIAs.In[16],an inoculated subobserver-based fusion filter was proposed to improve the resilience against malicious attacks.As shown in[17],a resilient linear quadratic Gaussian controller was proposed to recover system behavior subject to zero dynamic attacks by updating the information from Kalman filter.However,Kalman filter is extremely susceptible to external disturbance and the influence of noise may make the error of the estimated results lager.In [18],a multisensor temporal prediction scheme was proposed to enhance the resilience of wide-area control systems against malicious attacks.As described in [19], the authors proposed a defense scheme against DoS attacks using a switched methodology.Compared with the passive defense methods,the above active defense methods can improve the defense performance against FDIAs in smart grids.However, there still exist some problems for active defense methods to be solved as follows: (1) How to solve the impact of current attack detector on defense performance;(2)How to design a robust controller to respond to injection attacks quickly.
To address the shortcomings of the above approaches,an active defense scheme consisting of interval observer-based detection and resilient defense control against FDIAs is proposed in smart grids.First,an interval observer is designed to estimate the physical states of smart grids.Instead of calculating the threshold,the interval residual detection standard is proposed to detect FDIAs quickly and effectively.Then a resilient defense controller is triggered after the FDIA is detected.The defense controller is designed by solving LMI.The advantage of our active defense scheme is that the resilient defense controller can be triggered as long as the FDIAs are detected,which makes the smart grids return stable rapidly before FDIAs cause huge damage.The effectiveness and performance of the proposed active defense scheme are illustrated by simulations.The main contributions of this work are given as follows:
1.An interval residual-based detection is introduced.Compared with the works in [15], the proposed method can detect FDIAs quickly and cut down the impact of current attack detector on defense performance.
2.A resilient defense control method is developed.Compared with the main-stream works in [20] and [31], the proposed active defense scheme can respond to injection attacks quickly and ensure the smart grids stable operation.
The rest of this paper is organized as follows:In Sect.2,the system model and the problems are described.In Sect.3,the active defense scheme is presented.In Sect.4, a numerical example of the power system and its simulation results are shown.Finally,some conclusions are given in Sect.5.
2 Preliminaries and problem formulation
In this section, the physical dynamic grid model is established.Then,the feature of FDIAs is shown and the problem of active resilient defense control against FDIAs are formulated,respectively.
2.1 Grid model
Some notations are given firstly in the nomenclature.
A smart grid system which containsngenerators interconnected with transmission busses and load busses is considered in this paper,the dynamic physical model of theith generator is presented[20].
where
Letxi(t) = [δi ωi Pmi Xei]T,i= 1,...,n, then the model can be written as follows
whereϱi jBi j0 0T,uiis the control input of theith generator, the matricesAi,Biare given as follows:

Fig.1 A block diagram of smart grids under FDIAs
Letyi=Ci xi(t),then the system can be rewritten as
wherexi(t) ∈ Rni,ui(t) ∈ Rmiandyi(t) ∈ RPiare the state space vector, the control input and control output,respectively,Ai,BiandCiare known constant matrices,respectively.
2.2 The description of false data injection attacks
2.2.1 False data injection attacks
As a typical cyber–physical system,the normal operation of smart grid relies on the tight integration of cyber layer and physical layer.As shown in Fig.1 smart grids can use the information interaction between the network and physical system to realize control purposes.Sensors and smart meters send measurement data to control center,such as phase angle and relative speed.Then the designed detector will detect whether the data has been tampered or hacked by attacks.If the attack is detected, a well-designed controller acts on defending against the attack and reducing the impact on smart grids.Then, the control command is sent to the actuator to ensure the normal operation of the system.However, as a stealthy cyber attack,FDIAs can bypass bad data detection technique to achieve the goal of electricity theft[21].
2.2.2 Traditional bad data detection technique
For a smart grid system withnbusses andmmeters(m>n),the attack model can be described as[22]
Based on the WLS method,the above model can be solved by optimizing the following equation as
Assumption 1 The attacker has full knowledge of the network topology.
Then,the attacker can inject a bank of false attack vector into the smart grid as
wherea=[a1,a2,...,am]T.
Then,we can obtain
The expression of detection residualrunder FDIAs can be obtained as follows:
Remark 1Eq.(12) indicates that if the detection residual exceeds the predetermined threshold,an alarm is triggered.However,the attacker can obtain the knowledge of topology and parameters of the entire smart grid system.Attackers can launch covert FDIAs on smart grids to steal electricity without being detected.
Based on Eq.(12),the detection residualrunder FDIAs can be obtained as
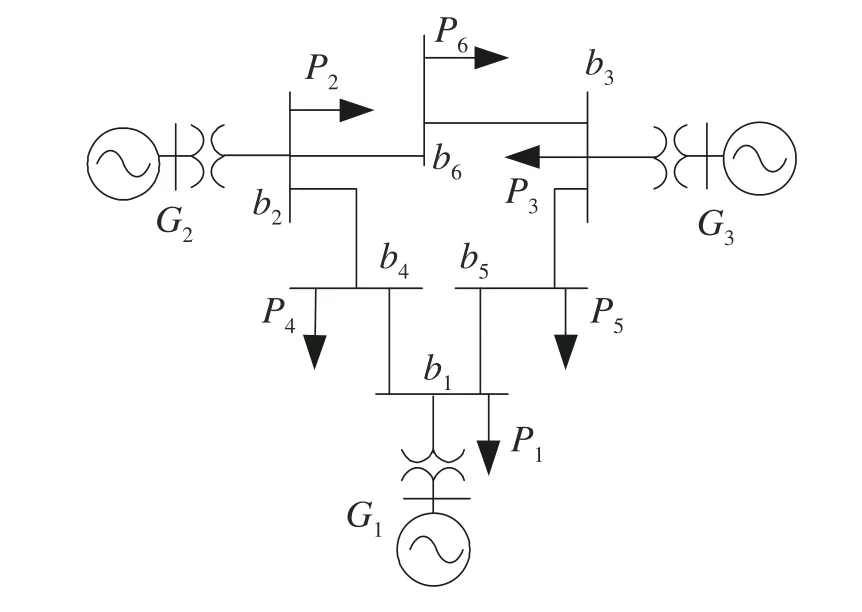
Fig.2 The IEEE 6-bus smart grid system
Ifa=Hc,whereais a linear combination of the column vectorH,then
the residualris smaller than the threshold.In the following,the attacker can launch an attack successfully with no alarm triggered.Then,an example is given to illustrate the stealth characteristic of designed FDIAs on IEEE 6-bus grid system shown in Fig.2.
Example 1It is assumed that one FDIA is injected att=60ms on generator 1, and the attack sequence is given as[23]
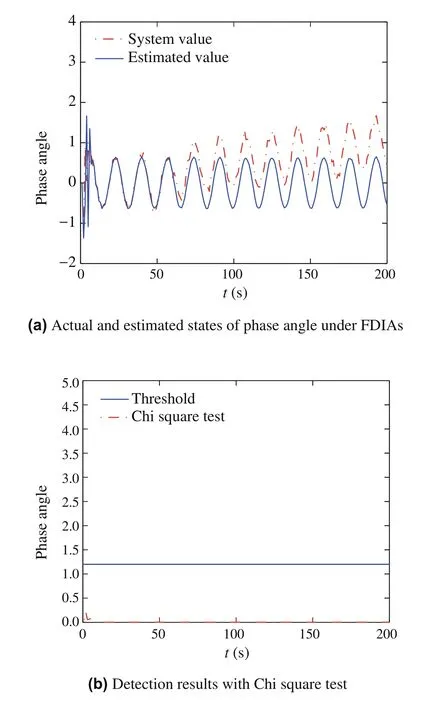
Fig.3 Simulation results of example 1 under FDIAs
wherenis the dimension of state space,a∗=Cς,ςis eigenvector ofA,ra(κ)-r(κ).Figure3(a)indicates the attacker has launched an attack successfully from the comparison between the real state value and the estimated value.However,the detection residual does not exceeded the predetermined threshold in Fig.3(b).
The simulations in Example 1 show that the FDIAs without being detected can cause huge risk to the security of smart grid.In order to solve this problem,an active defense scheme to detect and defend against FDIAs is proposed.Our active defense strategy can effectively detect and defense against covert FDIAs in real time before it causes huge damage to smart grid.
2.3 Problem formulation
Based on the sparsity of the smart grid,the large-scale grid system can be divided intoNsubareas[24].Then,the grid
model under FDIAs can be rewritten as follows:
The objective of this paper is to design a protection scheme that integrates detection and defense of FDIAs.
To ensure the achievement of our proposed defense scheme,some assumptions are given.
Assumption 2 [25]Theparameterun-certaintyΔAkisnormbounded,that is
whereEk,Nkare known constant matrices of appropriate dimensions and(t)is the unknown time-varying matrix satisfying
whereIis the identity matrix of appropriate dimension.
Assumption 3 [26]For system(14),there exist two constant matrices with appropriate dimensionsandsatisfying
Remark 2In this paper,the parameter uncertainty and interconnection uncertainty of the system are fully considered.In the previous study,Assumptions 2–3 are normal and necessary.In the following work,a resilient defense controller based on interval detection is designed to assure the safety of smart grid system.
3 Active defense scheme against FDIAs
In this section, an active defense scheme against FDIAs is proposed.Our active defense scheme consists of two parts,attack detection and attack defense.In the detection part, a detector based on interval observer and the corresponding interval residual detection criteria are given.Relevant work has proved the validity of interval observer to detect attacks[27,28].Then,thedefensecontroller canbetriggeredtowork based on detection results the detector.The LMI approach is used to design the defense controller.A feasible solution of the resilient controller with the H∞performance is given in the presence of FDIAs.With the proposed strategy,the damage caused by FDIAs can be mitigated timely.The concrete work are presented as follows.
3.1 Interval observer-based detection of FDIAs
In this section, the interval observer-based detection of FDIAs is proposed in the following:
The interval observer of thekth area can be designed as
where(Ck)+=max{0,Ck}and(Ck)-=(Ck)+-Ck.
To assure the validity of our designed interval observer,the following conclusion is given.
Theorem 1For the system(18),under Assumptions 2–3,if there exists ∊>0,Wk>0,such that
then the designed interval observer is stable,where
ProofThe interval errors are defined asand, then if there does not exist attack one can obtain
Consider the Lyapunov function as
Then,we can obtain
From Assumption 2,the following inequality is obtained
and

where
where
Pre-and post-multiplying both sides of(26)by
one can obtain
where
LetWk=(P-1)k,we can obtain Eq.(19).■
Then,the residuals for the proposed interval observers are defined as
Basedontheaboverelationshipofupperandlowerbounds of residuals, it can be obtained that if the upper and lower bounds of residuals contain zero value all the time,the system runs normally and no attack occurs;otherwise,attack occurs.The corresponding residual detection criteria is given as follows:
Letαkact as an identification factor of detection results
The detection process based on interval observer mainly consists of four steps.First,interval observer is established based on the physical dynamic model.Then,the corresponding interval residuals are calculated.Subsequently,we detect whether there exists an attack according to the judgment criteria.Finally, we getαkbased on the detection results and decide whether to trigger resilient defense controller to work.The details are shown in steps 1–2 in Algorithm 1 in the next section.
3.2 Resilient defense controller design
In this section, we design the resilient defense controller against FDIAs.The designed controller needs to reduce the damagecausedbyFDIAsandkeepthesystemasymptotically stable.The gain value of the designed defense controller has a certain resilient margin so that it can realize resilient defense against FDIAs.
For the grid model in Eq.(14),the following defense controller can be designed as
whereis the normal controller of the system andΔKkrepresents the structured resilient of the gainKksatisfying the following condition as
whereΥkandWkare known constant matrices with appropriate dimensions.
Substituting Eqs.(32)–(33) into Eq.(14), we can get the following closed-loop system:
When an attack occurs, we can obtainαk= 1 based on the detection result, then the resilient defense controller is triggered.To ensure the stability of the designed non-fragile defense controller and obtain the gain value,a conclusion is given as follows:
Theorem 2ConsiderthesysteminEq.(14)withAssumptions 1–2,if there exist γk> 0,εk1> 0,εk2> 0,εk3> 0and matrices Xk,Yk andℜk with appropriate dimension,such that
then
the system is stable with anH∞norm bound γk under controller in Eq.(33)where
ProofThe following Lyapunov function candidate is chosen as
Substituting Eq.(35)into Eq.(38),one can obtain
Then,the following inequality can be written as
Equation(40)can be rewritten as
and
For the closed-loop system in Eq.(35), the performance indexJkis defined as

where
According to Lemma 1 in[29],the inequality can be converted into
where
Pre-and post-multiplying both sides of Eq.(47)by
Then,we can obtain the following matrix inequality as
where
Then,we can get the matrix inequality Eq.(36).■
Based on the active resilient defense scheme, an active defense algorithm against FDIAs is summarized as follows:
Step 1:The interval observer of thekth area is designed to estimate the states.
Step 2:The residual of each area is calculated.
Step 3: A judgment criteria based on interval residual is given to detect which area is attacked.
Step 4:If FDIAs are detected in thekth area,thenαk=1.The resilient defense controller is triggered to work.
The more detailed process can be seen in Algorithm 1.
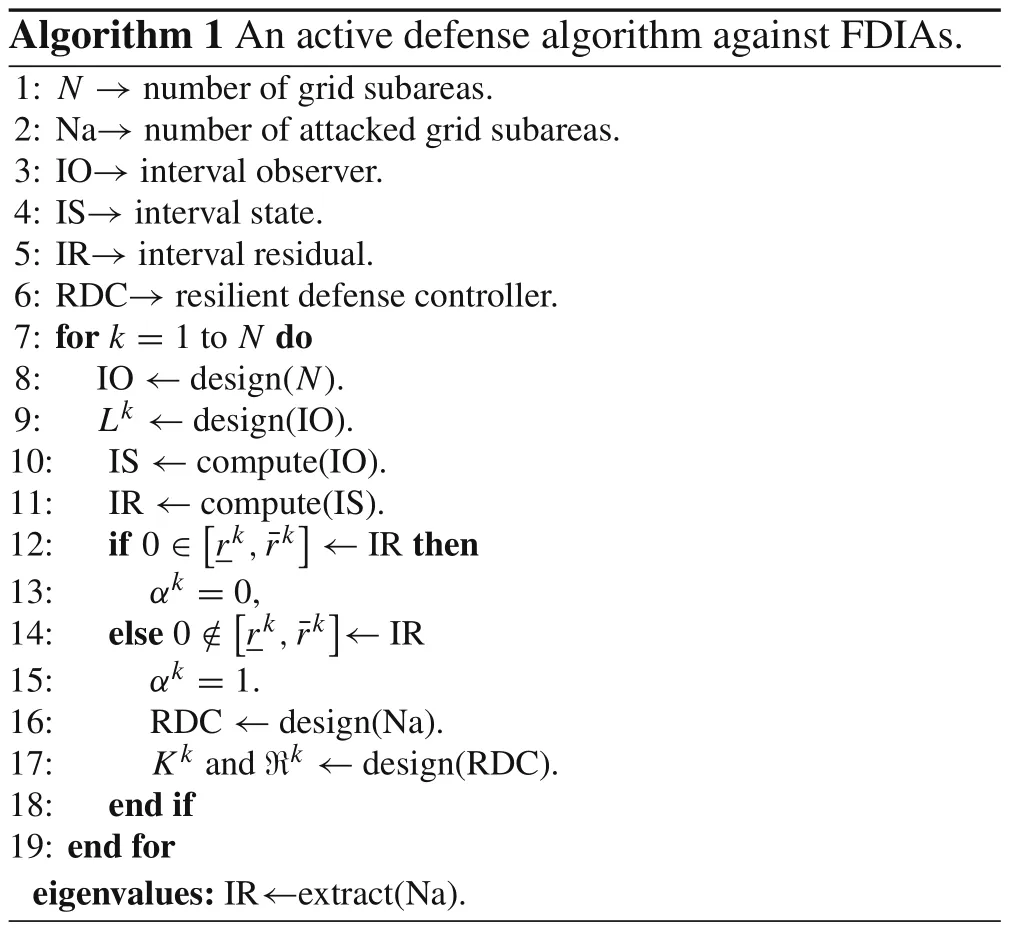
Algorithm 1 An active defense algorithm against FDIAs.1: N →number of grid subareas.2: Na→number of attacked grid subareas.3: IO→interval observer.4: IS→interval state.5: IR→interval residual.6: RDC→resilient defense controller.7: for k =1 to N do 8: IO ←design(N).9: Lk ←design(IO).10: IS ←compute(IO).11: IR ←compute(IS).12: if 0 ∈images/BZ_37_406_2477_420_2512.pngr k,¯rkimages/BZ_37_502_2477_515_2512.png←IR then 13: αk =0,14: else 0 /∈images/BZ_37_436_2566_450_2601.pngr k,¯rkimages/BZ_37_532_2566_546_2601.png←IR 15: αk =1.16: RDC ←design(Na).17: Kk and ℜk ←design(RDC).18: end if 19: end for eigenvalues:IR←extract(Na).
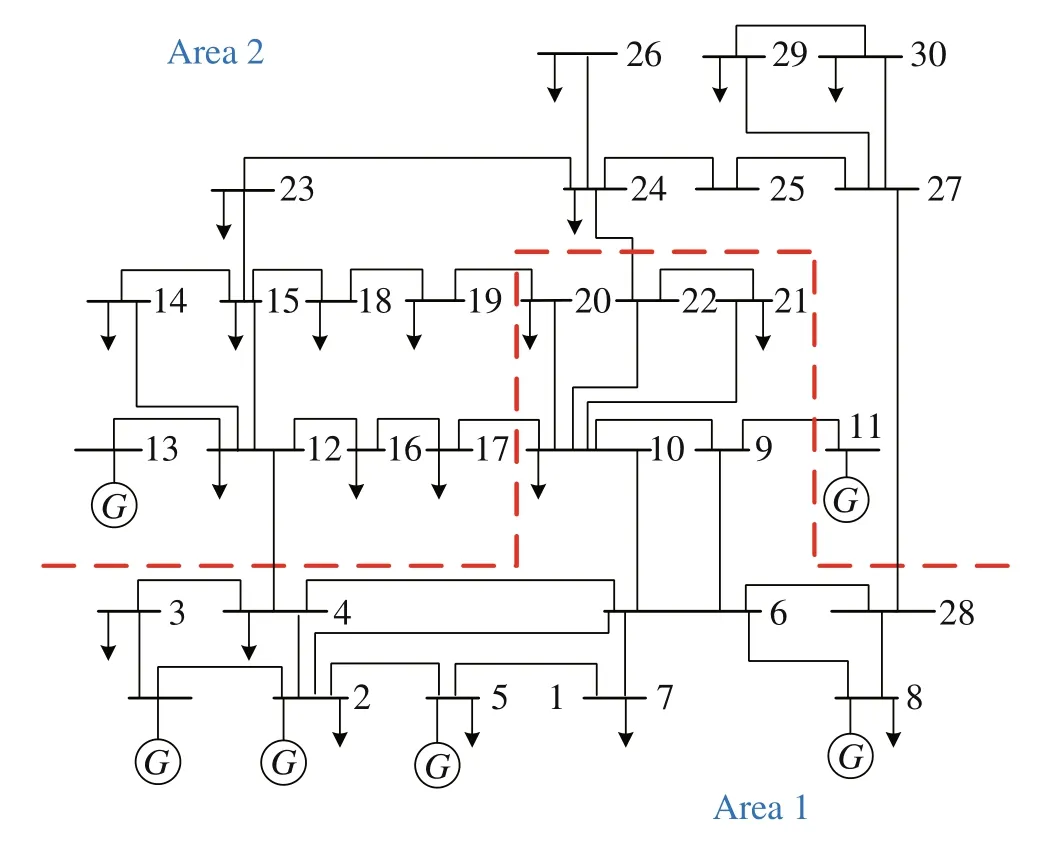
Fig.4 The IEEE 30-bus smart grid system
4 Simulation studies
In this section, simulation studies are developed to illustrate the effectiveness of the proposed active resilient defense scheme against FDIA on the IEEE 30-bus grid system.Considering the sparsity of grid system, the IEEE 30-bus grid system can be divided into two areas shown in Fig.4.The related area division technique is shown in our previous work[24].Comparison results with current mainstream technologies in [15, 20, 31] are provided to demonstrate the performance of the proposed method.The continuous intermittent FDIAs are considered and attack sequence is given in Eq.(13).The first attack is launched to test the system’s defense ability, if it is found to be insufficient, the more intense attack is launched again to achieve the purpose of power theft.The performance analysis of the proposed active defense scheme will be presented as follows.Furthermore,related simulation parameters are given as follows:
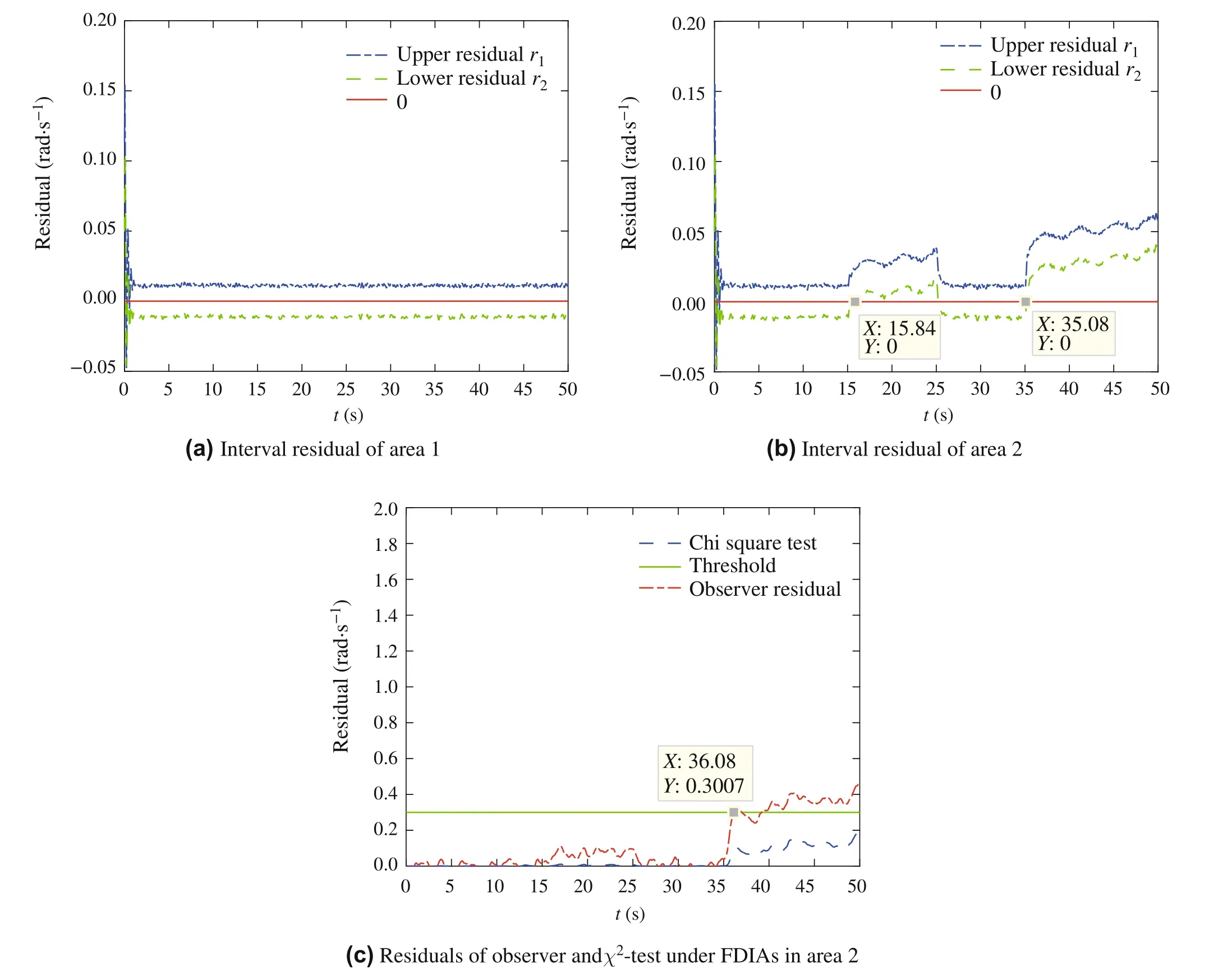
Fig.5 Detection results under FDIAs
4.1 Effectiveness analysis of the proposed active defense scheme
It is supposed that the system is attacked by continuous intermittent FDIAs.The first attack occurs in 15s, and lasts for 10s.And the second attack occurs after 35s.The simulation results of detection and defense of FDIAs are shown in Figs.5 and 6.
Based on Algorithm 1, we first design the interval observers to obtain interval estimation of the states in each area.Then, the interval residual of each area can be computed.The detection results are shown in Fig.5.Based on residual detection criteria,we can detect that there does not exist FDIAs in area 1.Detection result of area 1 is shown in Fig.5(a),one can findIn Fig.5(b),it is shown that the first attack is detected around at 15.84s and lasts about10s.Thesecondattackisdetectedaroundat35.08sand lasts about 15s again.Therefore,the continuous intermittent FDIAs can be detected at 15.84s and 35.08s.The detection results based on the traditional threshold detection method are shown in Fig.5(c).The criterion of traditional threshold detection method is whether the residual value exceeds the threshold.Based on this,we can find thatχ2-test detection can not detect stealth FDIAs because its residual does not exceed the threshold.We can also find that the residual detector based on traditional observer can only detect the FDIA at 36.08s, and it can not detect the first FDIA.Therefore, we can get that the traditional threshold detection method can not detect stealthy FDIAs successfully and accurately.
Based on detection results, we can getα2= 1 and the defense controller is triggered twice.The simulation results of passive defense controller in[31],normal controller in[20]and resilient defense controller are shown in Fig.6 respectively.Defense result based on passive defense controller is shown in Fig.6(a),one can find that the passive defense controller can not defend against continuous intermittent FDIAs successfully.
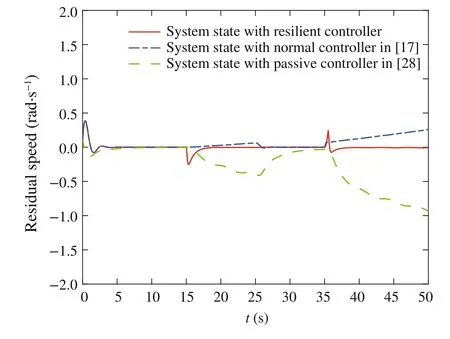
Fig.7 The comparison of system states with different defense controllers in area 2
Because the passive defense controller is always working in the system,it is difficult for the passive defense controller to defend against FDIAs if the attacker grasps the defense ability of the system and then changes the attack strategy.In Fig.6(b), the defense result of the normal controller based on the detection result is shown.One can find that the normal defense controller cannot eliminate the impact caused by stealth FDIAs,especially after the second FDIA.As presented in Fig.6(c),we can find that the impact of the FDIAs can be almost eliminated by the defense controller after each attack.Figure6(c) shows that 0 is between the upper and lower bounds of the residual after each FDIA with the proposed defense controller.The variation of residual in area 2 shows that the designed controller can effectively defend against FDIAs in smart grids.
4.2 Performance analysis of the proposed active defense scheme
Thestatesofthesystembasedonthreedefensecontrollersare shown in the Fig.7.The comparison highlights that the proposed resilient defense controller based on interval observer detection can better protect the smart grid from FDIAs.Compared with the other two defense controllers,the system with our designed controller can return to be stable quickly and maintain the good performance of the system after being attacked.
5 Discussion
The proposed detection and defense method is limited to the accuracy of the power grid model.In addition,the parameter selection of interval observer and elastic controller is also important to the performance of the method.In a sum,future work needs to consider designing observers or controls from the perspective of data-driven to solve the problem of model constraints; Intelligent algorithm is introduced to improve the parameter optimization ability of observer or elastic controller.
6 Conclusion
In this paper, an active resilient defense scheme against stealthy FDIAs in smart grids is proposed.The defense scheme consists of two parts:interval observer-based detection scheme and resilient controller-based defense scheme.The designed interval observer estimates the internal physical states of the system accurately,and the proposed interval residual detection method breaks through the limitation of using fixed threshold in the normal detection techniques.The resilient defense controller designed by LMI has a certain gain margin compared with general controllers.By solving linear matrix inequalities, a feasible solution is obtained to keep the system stable after being attacked.The effectiveness of the proposed method is verified on the IEEE 30-bus grid system.
Declarations
Conflict of interest The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
杂志排行
Control Theory and Technology的其它文章
- Consensus control of second-order stochastic discrete-time multi-agent systems without velocity transmission
- Robust non-aggressive three-axis attitude control of spacecraft:dynamic sliding mode approach
- Algebraic form and analysis of SIR epidemic dynamics over probabilistic dynamic networks
- Erratum to:Modular supervisory control for multi-floor manufacturing processes
- Adaptive feedback control for nonlinear triangular systems subject to uncertain asymmetric dead-zone input
- Sailboat navigation control system based on spiking neural networks
