SBFT:A BFT Consensus Mechanism Based on DQN Algorithm for Industrial Internet of Thing
2023-11-06NingjieGaoRuHuoShuoWangJiangLiuTaoHuangYunjieLiu
Ningjie Gao ,Ru Huo ,Shuo Wang,3 ,Jiang Liu,3 ,Tao Huang,3 ,Yunjie Liu,2,3
1 State Key Laboratory of Networking and Switching Technology,Beijing University of Posts and Telecommunications,Beijing 100876,China
2 Faculty of Information Technology,Beijing University of Technology,Beijing 100124,China
3 Future Network Research Center,Purple Mountain Laboratories,Nanjing 211111,China
*The corresponding author,email: huoru@bjut.edu.cn
Abstract: With the development and widespread use of blockchain in recent years,many projects have introduced blockchain technology to solve the growing security issues of the Industrial Internet of Things(IIoT).However,due to the conflict between the operational performance and security of the blockchain system and the compatibility issues with a large number of IIoT devices running together,the mainstream blockchain system cannot be applied to IIoT scenarios.In order to solve these problems,this paper proposes SBFT (Speculative Byzantine Consensus Protocol),a flexible and scalable blockchain consensus mechanism for the Industrial Internet of Things.SBFT has a consensus process based on speculation,improving the throughput and consensus speed of blockchain systems and reducing communication overhead.In order to improve the compatibility and scalability of the blockchain system,we select some nodes to participate in the consensus,and these nodes have better performance in the network.Since multiple properties determine node performance,we abstract the node selection problem as a joint optimization problem and use Dueling Deep Q Learning(DQL) to solve it.Finally,we evaluate the performance of the scheme through simulation,and the simulation results prove the superiority of our scheme.
Keywords: Industrial Internet of Things;Byzantine fault tolerance;speculative consensus mechanism;Markov decision process;deep reinforcement learning
I.INTRODUCTION
With the development of the IIoT,5G,and industrial technology,a growing number of countries and regions have begun to deploy IIoT applications[1][2].IIoT has received widespread attention in industry and academia due to its rapid development.In order to meet the demands of ubiquitous network connections and industrial network stability,IIoT has introduced technologies such as Industrial Passive Optical Network(PON),Industrial Software Defined Network(SDN),edge computing,and identifier resolution.These technologies are used to realize the access and interaction of massive heterogeneous data in IIoT,and to tap the potential of industrial data.The massive amount of data has brought serious security problems when migrating[3][4].The current industrial network is far from meeting the requirements of IIoT in terms of security and scalability of deployment.
Recently,as a distributed and decentralized technology,blockchain has been used to solve the above challenges.Blockchain is a distributed and immutable data ledger,which can realize reliable transmission and circulation of data without using a centralized authority[5].In terms of security and data sharing,blockchain can achieve trustworthiness in a distributed way.
However,there are still many problems with introducing blockchain technology into IIoT systems,and we summarize two main problems: (1) The trade-off between security and device power consumption.As we all know,introducing the blockchain and consensus mechanisms into the internet can significantly improve the security of the internet.Blockchain exploits a variety of different consensus mechanisms to defend against malicious attacks.As a typical application of the consensus mechanism,the proof of work(POW)consensus mechanism forces the blockchain nodes to run a high-complexity cryptographic algorithm,proving workload and reaching consensus.However,for low-power devices in industrial scenarios,it is difficult for them to run a typical POW consensus mechanism:The Bitcoin network consumes about 20-80 Tera Watt Hour(TWh)per year,about 0.1%-0.3%of global electricity consumption[6].At the same time,choosing some lightweight consensus mechanisms will reduce the security of the system.Therefore,how to balance the device power consumption requirement and security requirements of the IIoT system is the first problem.(2)The performance of the blockchain is difficult to meet actual needs.The IIoT environment usually has many device access and high concurrent data circulation,which requires the blockchain system to have good scalability and high throughput.Unfortunately,most of the existing blockchains have poor scalability and low throughput,derived from their security consensus mechanism based on complex cryptography.For example,PBFT is simpler than POW,but the PBFT protocol generates a lot of traffic overhead due to its higher communication complexity.In addition,as the number of nodes in the network increases,the performance of PBFT will drop sharply,making it difficult to apply in IIoT networks with a large number of devices.Therefore,how to improve the throughput and scalability of the blockchain to meet the needs of high concurrent transactions in IIoT is the second problem we need to solve.
Many studies have proposed improvements to the blockchain consensus mechanism.These mechanisms have studied how to improve the scalability and throughput of the blockchain system,and reduce the communication overhead and consensus delay of the system.For example,Li[7]proposed a two-layer scalable consensus mechanism based on PBFT,which can improve the throughput of the system and reduces the communication complexity of the system by hierarchically grouping nodes into different layers and restricting the communication within the group.Sujit Biswas[8] proposed PoBT,a novel lightweight proof of block and trade consensus algorithm,which can verify the security of blocks in the transaction verification and block creation stages and reduce the cost of consensus within the network.Laphou[9]proposes G-PBFT,a novel,location-based,and scalable consensus protocol.It selects fixed devices within an IIoT network as loyal endorsers,reducing the overhead for validating and recording transactions and increasing the throughput of the network.Gao[10]proposed a novel system architecture for different IIoT devices to deploy high-performance blockchain systems in many scenarios.To improve the performance of the blockchain network,they adopt the sharding hashgraph consensus mechanism and introduce a node evaluation mechanism based on the state of the node,which is applied to divide a large number of nodes into many shards dynamically.Hong[11] proposed Pyramid,the first layered sharding blockchain system,in which some shards can store the full records of multiple shards thus the cross-shard transactions can be processed and validated in these shards internally.When committing cross-shard transactions,to achieve consistency among the related shards,a layered sharding consensus based on the collaboration among several shards is presented.Compared with complete sharding in which each cross-shard transaction is split into multiple sub-transactions and costs multiple consensus rounds to commit,the layered sharding consensus can commit cross-shard transactions in one round.These schemes usually involve the improvement of one or several aspects of the blockchain(consensus efficiency,throughput,communication overhead,scalability).But it is difficult to achieve a balance between blockchain security and overall performance.
This paper introduces SBFT,a deep reinforcement learning-based blockchain consensus mechanism for the IIoT.Specifically,we propose a relatively simple consensus mechanism to adapt to devices with limited power and computing power in the IIoT network,improve consensus efficiency,and reduce intra-network communication overhead.On the premise of ensuring the security and decentralization of the blockchain,we select some nodes in the network to participate in the consensus to further enhance the scalability and consensus performance of the system,and these nodes have better performance in the network.Since these nodes have multiple properties,we abstract the node selection problem as a joint optimization problem and use Dueling DQL to solve it.Our unique contributions to this paper are as follows.
(1)We propose a novel,speculative consensus protocol for simpler IIoT devices,improving consensus efficiency and reducing communication overhead.The detailed consensus steps and theoretical analysis are given later.
(2) There are significant differences between IIoT devices,such as device load,power,computing power,network conditions,trust characteristics,etc.In order to ensure the performance of the blockchain system,we select some nodes in the network with better comprehensive performance to participate in the consensus.Accordingly,we formulate the node selection as a joint optimization problem.We define the state space,action space,and reward function for this problem and abstract it as a Markov decision process.
(3) To verify the effectiveness of the scheme proposed in this paper,we designed a complete set of simulation experiments and compared them with other mature schemes.The simulation results prove the superiority of the scheme proposed in this paper.
The remainder of the paper is organized as follows.In Section II,we introduced some knowledge about blockchain and IIoT.In Section III,we provide a detailed introduction and analysis of the system model and consensus algorithm used in this paper.In Section IV,we discuss the performance of the consensus algorithm proposed in this paper at the theoretical level.The simulation results and discussion are introduced in section V.In Section VI,we give conclusions and future work directions.
II.RELATED WORKS
In this section,we will introduce the relevant knowledge of IIoT and blockchain.
2.1 Recent Advances on the Industrial Internet of Things
In recent years,next-generation network technologies such as big data,cloud computing,and SDN have gradually emerged,making industry and academia have great interests in IIoT.The typical system architecture of IIoT is a unified 5-level architecture[3],as shown in Figure 1[1].
The development of IIoT largely depends on various enabling technologies,such as big data,cloud computing,5G[12],SDN[13],etc.The typical technical support of IIoT is shown in Figure 2.
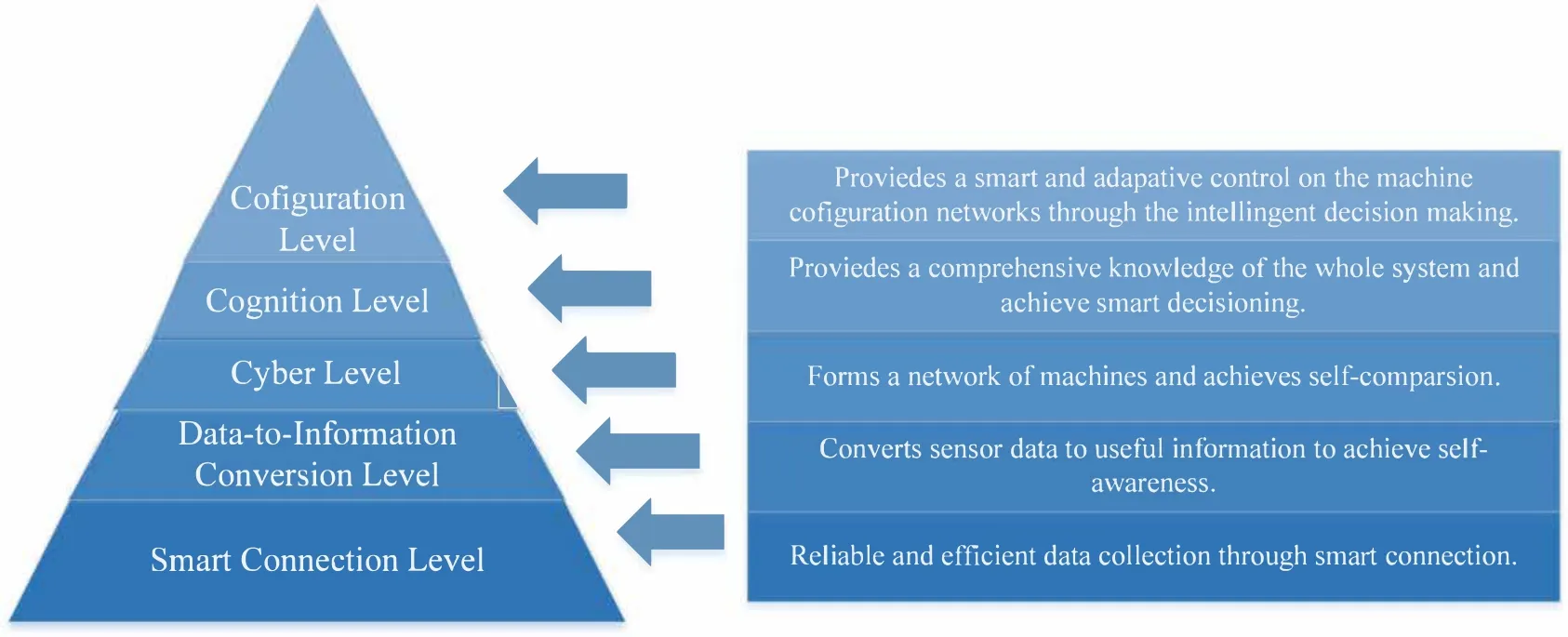
Figure 1.5C architecture of the Industrial Internet of Things.
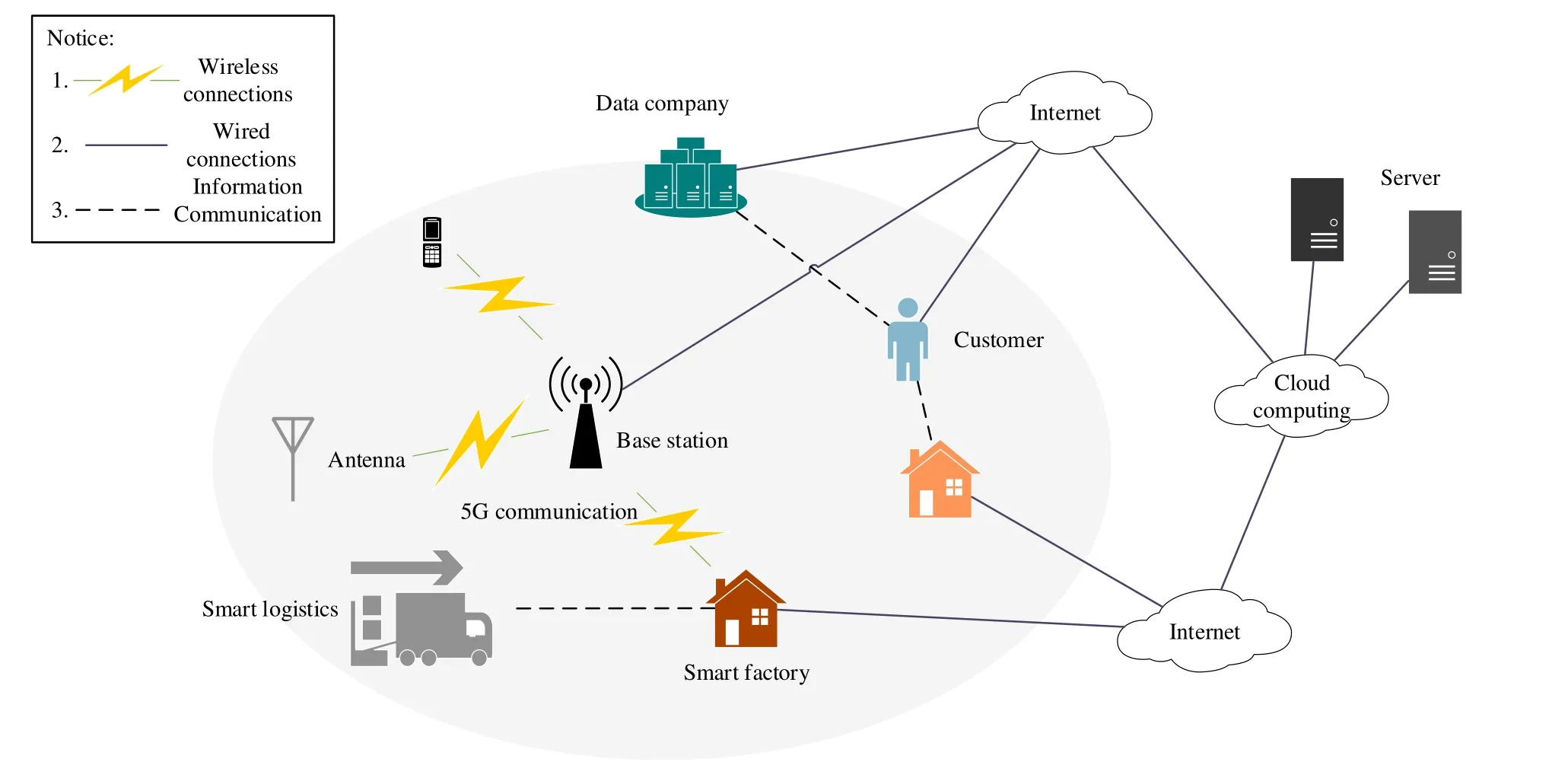
Figure 2.The typical technical support of IIoT.
These technologies are applied in many specific scenarios.For example,the smart factory collects different sensor data and uploads it to the cloud computing network to make intelligent decisions.In manufacturing,3D printing technology realizes fast and low-cost product customization functions[14].In the factory network,SDN,edge computing,and other technologies can be used to transform the internal network of the factory to observe and schedule the entire network uniformly.IIoT adopts advanced network access technology,network transmission technology,artificial intelligence,big data analysis,blockchain,and other technologies to automate production decisions,reduce enterprise costs,and free up more human resources for enterprises.Therefore,these enterprises can invest in more creative work in,reverse the “Pareto principle” of traditional industries,improve the efficiency of industrial production,dissemination and reuse,expand the digital space of the enterprise,which discovers new wealth creation models.IIoT can realize the transformation and upgrading of traditional industries such as aerospace,manufacturing,medical,oil,and natural gas,bringing profound changes[15].
Unlike the Consumption Internet,an IIoT network connects tens of thousands of industrial assets,so it places higher requirements on network security and data security in the industrial environment.
2.2 Recent Advances on the Blockchain
Blockchain is a decentralized,distributed,immutable data ledger.The ledger is stored in multiple participants in the peer-to-peer network.Participants can use cryptographic signatures to add new transactions to the existing transaction chain to form a secure,continuous,and invariant chain data structure.Due to the critical properties of blockchain,such as decentralization,persistence,anonymity,and auditability,it has been widely used in financial services[16],smart cities[17],Internet of Things[18,19]and many other fields.It is generally accepted that blockchain is a new distributed computing and storage paradigm that incorporates various existing technologies[20].
As we all know,the distributed system has the CAP theorem:In a distributed system,there are at most two of the three characteristics of Consistency,Availability,and Partition tolerance.As a distributed system,the blockchain system also has similar theorems: any blockchain system has at most three of the four characteristics of decentralization,scalability,security,and consensus efficiency.In addition,the strengthening of certain attributes must be accompanied by the weakening of certain attributes,which is the four-way tradeoff principle of the blockchain.
As one of the core technologies of the blockchain,the consensus mechanism directly determines the performance of the blockchain system.Through the research and improvement of the consensus mechanism,the blockchain can have different characteristics,such as higher scalability and consensus efficiency.As the underlying consensus mechanism of the Bitcoin project,the POW consensus mechanism has almost the highest security,decentralization,and scalability among all consensus mechanisms.Tens of thousands of nodes freely join or withdraw from the Bitcoin network every day.Relatively speaking,the consensus efficiency of the POW consensus mechanism is extremely low.The system only proposes a block and reaches a consensus every 10 minutes,which is difficult to meet the needs of IIoT applications.Compared with the POW consensus mechanism,the BFT(Byzantine Fault Tolerance) type protocol has lower algorithm complexity and higher consensus efficiency,so it is more suitable for applications in scenarios with limited network nodes,such as alliance chains,consortium chains,and IIoT.In BFT protocols,the most typical solution is PBFT.The consensus pattern of the PBFT protocol is shown in Figure 3.In order to better apply the blockchain program to the IIoT scenario,in this paper,we will design A BFT-based consensus protocol with improvements.
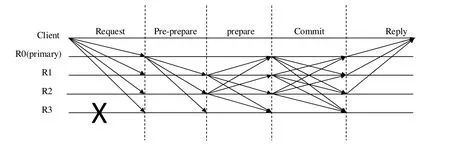
Figure 3.The consensus pattern of PBFT protocol.
III.SYSTEM MODEL AND PROTOCOL DESIGN
In this section,we describe the design of the SBFT protocol in detail.We first describe the threat model and model assumptions.Then we introduce the overview and specific implementation process of the protocol.
3.1 Threat Model
We assume that there is a set of nodes in the system,indexed byN=(R0,R1,...RN-1).All nodes run the Byzantine fault model.We assume a strong adversary in the network,which may attack the network and produce a certain number of faulty nodes,and control these faulty nodes,sending wrong information to the client or not sending information.However,they cannot destroy existing encryption technologies,such as node encryption signatures and message authentication codes (MACs)[21].In addition,the blockchain network is a fully connected distributed system,so there will be no message loss in the network.
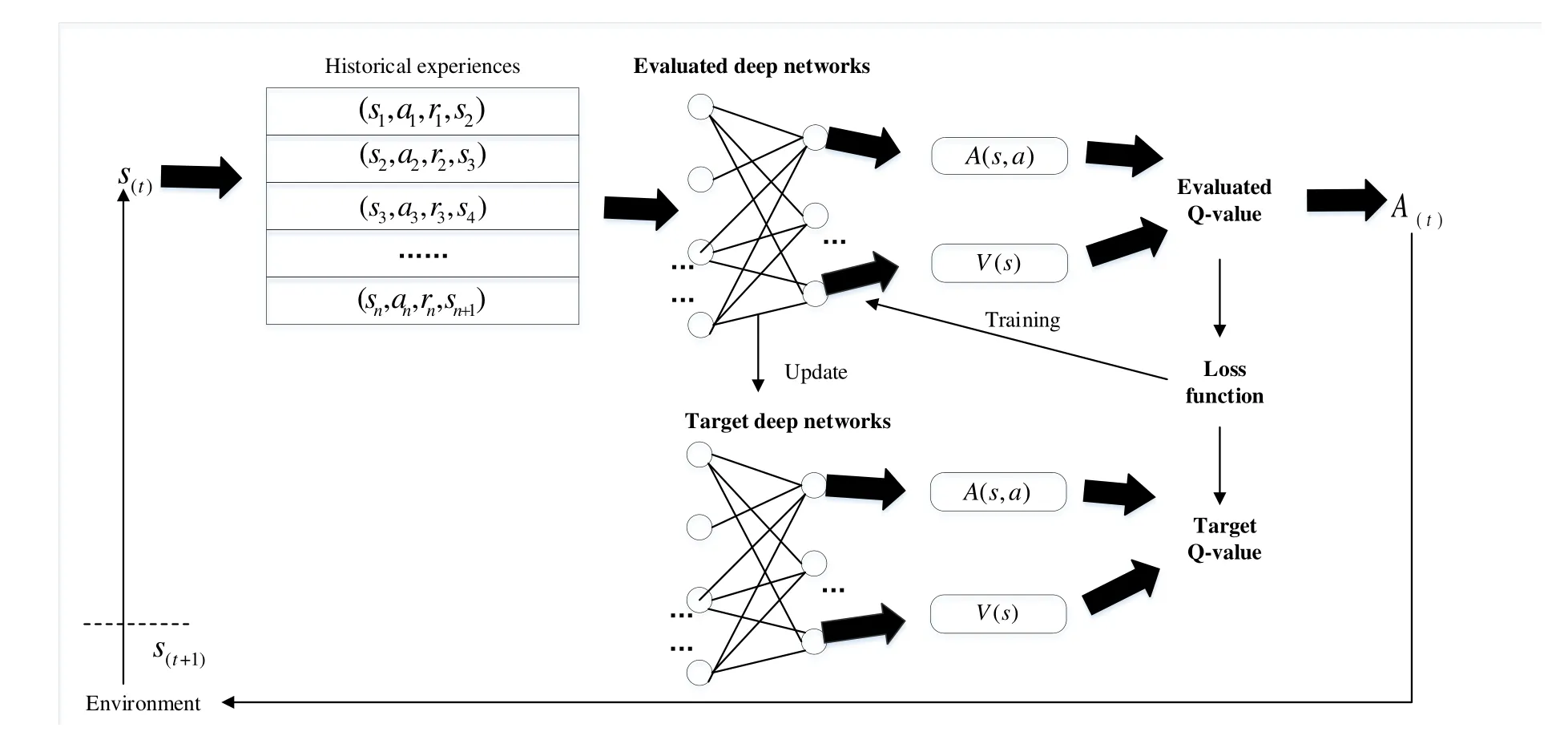
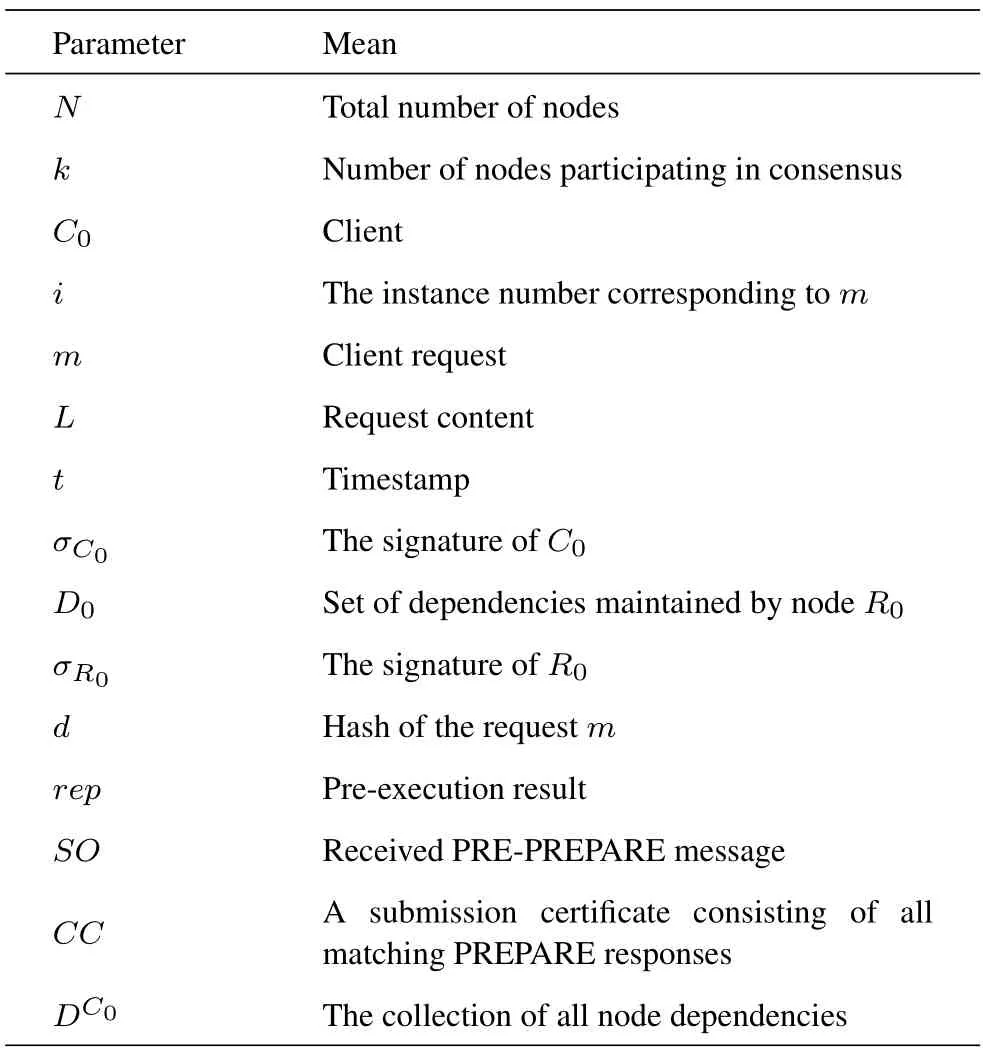
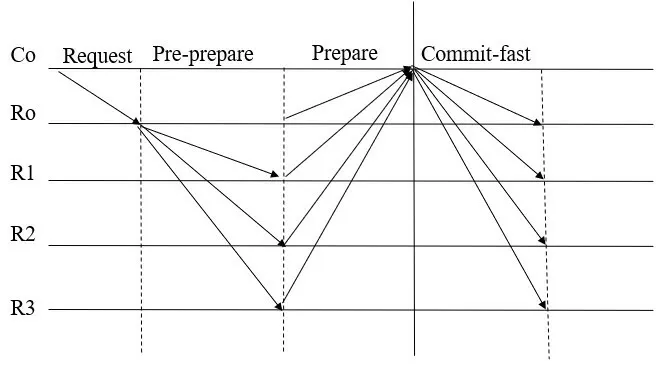
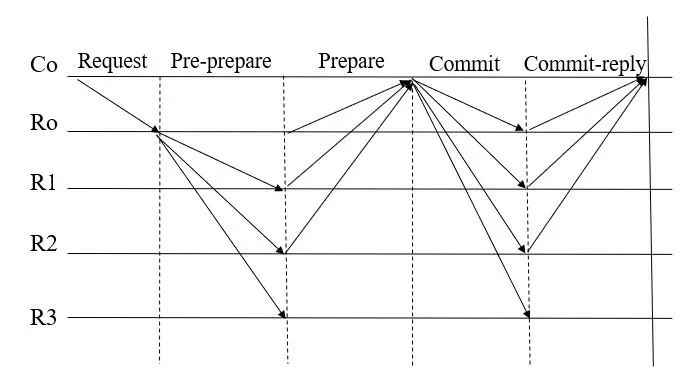
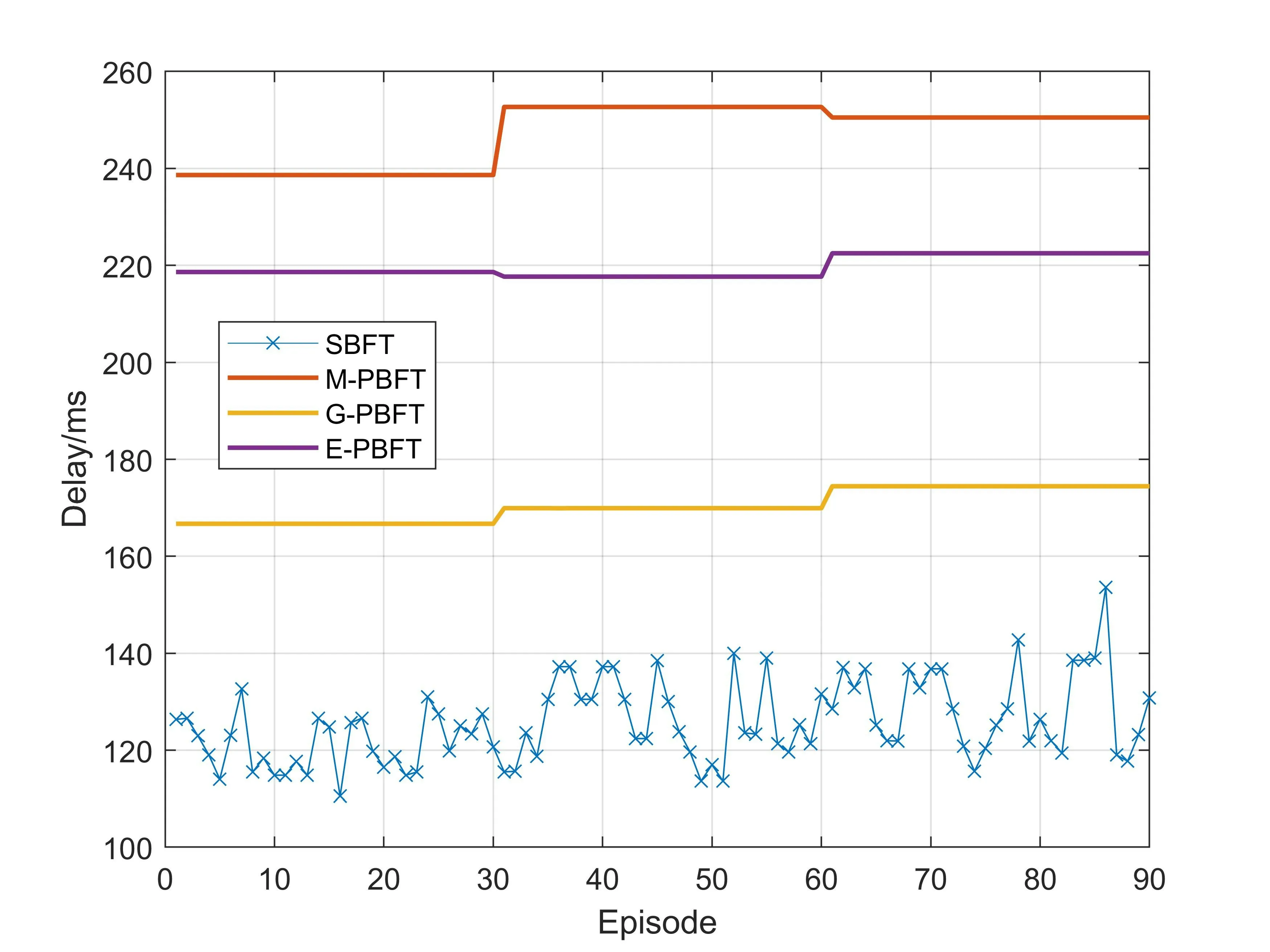
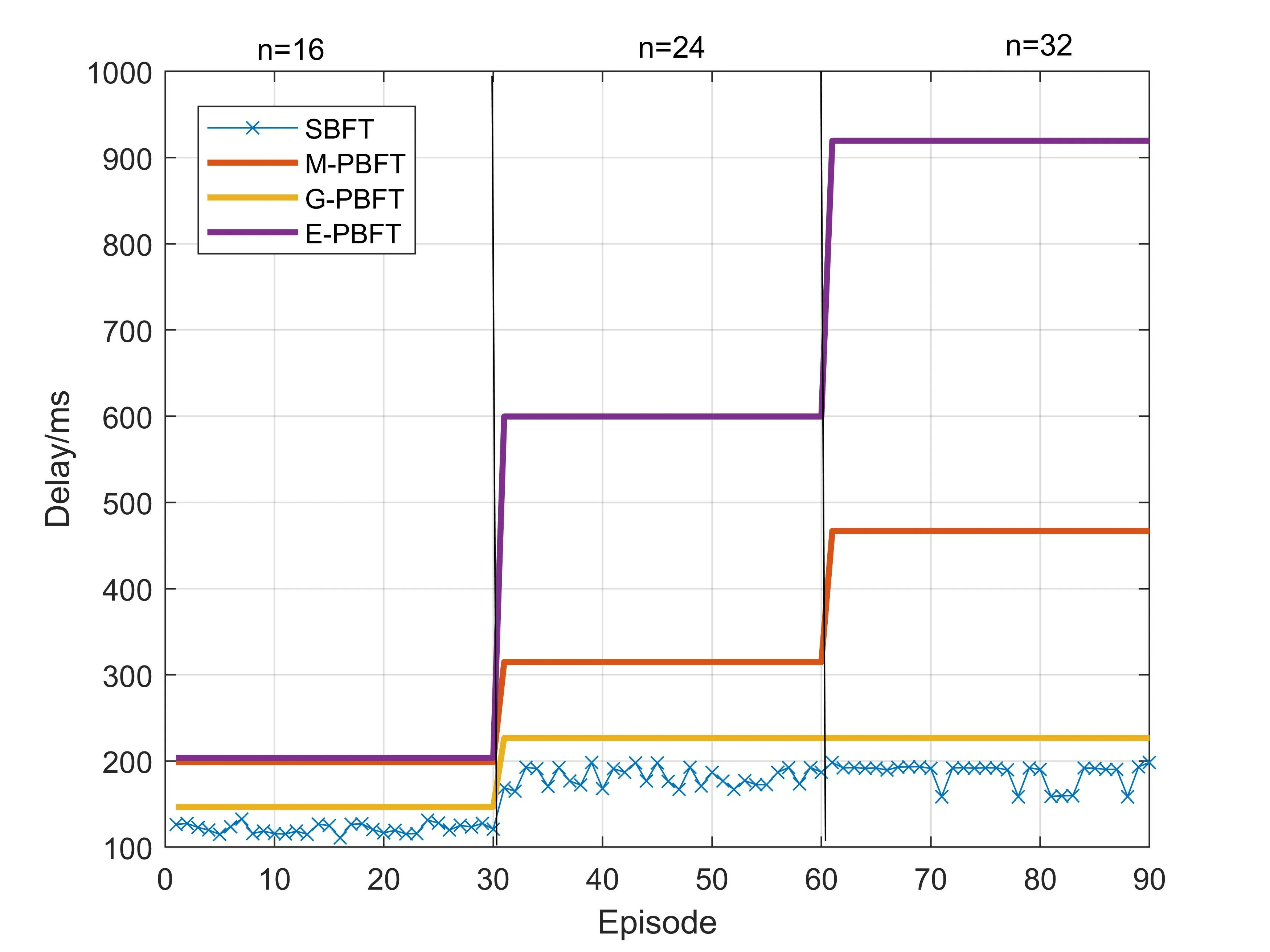
According to the BFT fault model,the numberfof faulty nodes in the network should follow the principle of 3f+1 The design of the SBFT is based on the fact that IIoT devices are differentiated.For example,a smart factory network has both sensor nodes that can only send and receive information and large server nodes that aggregate and process all information in an area.These nodes have different properties,such as communication bandwidth,computing power,power,network delay,etc.As shown in Figure 4,in order to improve the consensus efficiency and scalability of the blockchain system,we select those nodes with the best performance in the network to participate in the consensus,and the remaining nodes only serve as forwarding nodes in the network,responsible for storing and forwarding consensus results and block.The nodes participating in the consensus are rotated periodically or when consensus fails.In addition,we also propose a speculation-based consensus process,which has lower communication complexity,higher consensus efficiency and scalability.Therefore,the SBFT protocol proposed in this paper is divided into two parts,the first part is the node selection process,and the second part is the consensus process. Figure 4.Select some nodes from the network to participate in the consensus. For the proposed consensus model to work efficiently,it is necessary to decide on the selection of nodes running the consensus protocol[21].Reinforcement learning has been widely used in blockchain to optimize the performance of blockchain systems.Dai[22]integrates DRL and permission blockchains into a network of vehicles for smart and secure content caching.They first proposed a blockchain authorized distributed content caching framework,where vehicles perform content caching and base stations maintain the license blockchain.They then use advanced DRL methods to design an optimal content caching scheme that takes liquidity into account.In addition,Feng[23] develop a cooperative computation offloading and resource allocation framework for blockchainenabled MEC systems.In the framework,they design a multiobjective function to maximize the computation rate of MEC systems and the transaction throughput of blockchain systems by jointly optimizing offloading decisions,power allocation,block size,and block interval.Due to the dynamic characteristics of the wireless fading channel and the processing queues at MEC servers,the joint optimization is formulated as a Markov decision process (MDP).To tackle the dynamics and complexity of the blockchainenabled MEC system,they develop an asynchronous advantage actor-critic-based cooperation computation offloading and resource allocation algorithm to solve the MDP problem. Since nodes have multiple attributes,selecting nodes is a joint optimization problem.We use a dueling deep reinforcement learning method to solve this joint optimization problem.In this section,we formulate this problem as a Markov decision process and then define the system state space,system action space,and reward function. 3.3.1 System State Space This algorithm maintains a state space.Assuming that there areNnodes in the network,the status attributes of each node are〈Bi,Ci,Ri,Di,Fi〉,whereBimeans the communication bandwidth,Cimeans the credit score,Rimeans the computing resources that can be used for consensus algorithm execution,Dimeans the average communication delay with other nodes,Fimeans the frequency that the node was selected.Then the state space isS(N).According to the state space,we define the state of the system as a functionS(t)that changes with timet.Since the learning agent makes decisions based on the node communication bandwidth,the node credit score,the computing resources that the node can use for consensus algorithm execution,the average communication delay between the node and other nodes,and the frequency that the node was selected,so the system state can be expressed as: 3.3.2 System Action The system action can be denoted as follows:Ak(t)represents selectingknodes from all nodes as the execution nodes of the consensus protocol. 3.3.3 Reward Function Our optimization target is to maximize the client’s consensus execution speed,so we model the reciprocal of the client’s consensus delay as a reward function.The reward function is shown in Eq.(3): whereC0andF0are two constants,which are used to ensure the security and decentralization of the selected nodes.Specifically,we need to ensure that the overall credit score of the selected node group is high to ensure the security of the blockchain system.The first constraint of Eq.(3) can ensure that the average credit score of the selected node group is higher thanC0,and the overall credit level of the selected node group can be flexibly adjusted by adjusting the value ofC0.At the same time,choosing the same node too often may compromise the decentralization of the blockchain system and cause a single point of failure.can describe the average occurrence times of the selected node group.The second constraint of Eq.(3) can ensure that the same node will not appear many times in the selected node group in each consensus cycle.The degree of decentralization of the system can be flexibly adjusted by adjusting the value ofF0.Therefore,by adding constraints,the system can be guaranteed to have a certain degree of security and decentralization while maximizing the blockchain consensus rate. 3.3.4 Dueling Deep Reinforcement Learning Reinforcement learning is a type of machine learning that can help us solve some more complex decisionmaking problems,such as the Markov decision process mentioned above.In this section,we introduce the deep Q learning(DQL)method,an improved reinforcement learning algorithm.In Q Learning,there is a function calledQFunction,which is used to approximate rewards based on the state of the system.We defineQFunction asQ(s,a),whereQis a function which calculates the expected future value from statesand actiona.In DQL,we use neural networks to approximate rewards based on the state of the system.It is worth noting that in our system,system actions are only related to the current system state.Dueling DQL is more efficient than natural DQL[24].Dueling DQL method has two outputs,respectively output state valueV(s) and (state-dependent) action advantagesA(s,a).According toV(s)andA(s,a),Q(s,a)can be calculated.Figure 5[21]shows the workflow of dueling DQL. Figure 5.The workflow of dueling DQL. SBFT is a speculation-based consensus mechanism.First,we default that there are no Byzantine nodes in the group of nodes participating in consensus in the current consensus cycle.Under such a premise,there will be no disputes and errors within the network,there is no need for multiple collective signatures and broadcasts,and the system can reach consensus through a very simple process.Therefore,the perfect execution of SBFT consensus mechanism has a very high consensus rate and throughput,and we name the perfect execution process of SBFT consensus mechanism as“fast consensus process”.However,during the actual operation,there is a certain probability that there are Byzantine nodes in the system,which can destroy the perfect execution process of SBFT and prevent the system from reaching consensus.In this case,in order to reach consensus,the system will change from a perfect execution process to a general execution process by adding consensus steps to improve the security of the network.In such a case,the consensus rate of the system will be affected,and we name the general execution process of SBFT consensus mechanism as“slow consensus process”. In order to ensure consistency without a leader,each replica node needs to maintain a dependency setD[],whereD[i] represents the content of theirequest received by the node.The system parameters used in the algorithm in this section are shown in Table 1. Table 1.The algorithm parameters. (1)The Fast Consensus Process The steps of the fast consensus process are given as follows: Step 1:The clientC0sends a requestm=〈REQUEST,L,t,C0〉σC0to the closest replica nodeR0. Step 2:After the replica nodeR0receives the request,it assigns the instance numberiin the order of block generation,and assignsD0[i] asL.After the assignment is completed,R0sends〈〈PRE-PREPARE,R0,i,D0,d,C0,t〉σR0,m〉to other nodes in node groupk.After the transmission is completed,the nodeR0replies to the client with a〈〈PREPARE,R0,i,D0,d,C0,t〉σR0,rep〉message. Step 3:After receiving the PRE-PREPARE message,other nodes perform verification according to the local dependency set,and reply the result and the updated dependency set to the client.When nodeRjreceives the PRE-PREPARE message from nodeR0,it first verifies whethermis a valid REQUEST message and whetherDj[i] is empty.IfDj[i] is empty,the verification is successful.After successful verification,RjupdatesDj[i] according to its instance space and dependency set,puts the command into the execution queue to wait,and replies to the client〈〈PREPARE,R0,i,Dj,d,C0,t〉σRj,Rj,rep,SO〉. ClientC0sets a timer immediately after sending the request.When the client receives 3f+1 PREPARE messages,it performs verification.If messages from different replicas have the samei,D[i],C0,t,andrep,they are said to match.If there are 3f+1 matching commands,a〈COMMIT-FAST,C0,i,CC〉message is sent to all copies for execution,as shown in Figure 6. Figure 6.Fast byzantine consensus process. (2) The Slow Consensus ProcessIf the received matching response is less than 3f+1,it enters a slow Byzantine consensus process,as shown in Figure 7.The fourth and fifth steps of the slow consensus process are as follows: Figure 7.Slow byzantine consensus process. Step 4:If the client receives 2f+1 matching PREPARE requests when the timer expires,it will generate a newDC0(the collection of all node dependencies).C0sends〈COMMIT,C0,i,DC0,CC〉to all replicas. Step 5:After receiving the COMMIT message,the replica updates the receivedDC0into its own dependency set,deletes the previous pre-execution results,and executes again according to the new order.The final execution resultrepis returned to the client via〈COMMITREPLY,L,rep〉.The client returns the execution result to the application after receiving 2f+1 return messages,and the process is completed.Finally,if the client receives less than 2f+1 matching PREPARE requests when the timer expires,it terminates the consensus process of the current node group and re-selects a batch of node groups to perform consensus. In general,the fast Byzantine consensus process does not have disputed results in the default system operation,and the results returned by all nodes are matched,so the fast Byzantine execution process has the highest consensus rate.In practice,the fast Byzantine consensus fails or the system security is poor,the system state is unstable (network state,node access and withdrawal,etc.),the system will use the slow Byzantine consensus process to reduce the consensus rate in exchange for higher security and stability. In this section,we will analyze the performance of the SBFT algorithm from four aspects,including security,scalability,decentralization,and consensus efficiency,based on the four-way trade-off theory of blockchain. The SBFT algorithm is a consensus algorithm based on speculation.Compared with the high-complexity algorithms such as POW and PBFT,there are certain deficiencies in the security of the SBFT.In order to improve the security of the algorithm,a series of improvements have been made in this paper.The system selects a batch of nodes with the highest comprehensive scores to participate in the consensus through the node screening process and modifies the scores of these nodes in real time according to the consensus results.The reputation score of nodes occupies a great proportion of the comprehensive score.Therefore,most of the nodes participating in the consensus are nodes with a good reputation,which can improve the security of the algorithm to a certain extent.In addition,when there is a problem with the consensus process,the system will quickly switch to the slow consensus process with higher security to ensure the safe conduct of the consensus.Next,we will analyze according to the specific attack types. 4.1.1 Sybil Attack Traditional blockchains may suffer from Sybil attacks by malicious users,such as creating many Sybil nodes and manipulating the consensus process.In order to solve this problem,the system will screen the node information during the node selection process.If many nodes have similar characteristics (network bandwidth,computing resources,network delay,etc.),they will be recognized by the system and cannot become consensus nodes.In addition,if a node participates in the consensus process and destroys the consensus process,it will be recognized by the system,and its reputation score will be lowered,making it impossible to continue to destroy the consensus. 4.1.2 Byzantine Attack Most of the Byzantine series algorithms require that the Byzantine nodes in the network do not exceed 1/3.This algorithm also requires that the Byzantine nodes in the network do not exceed 1/3,and the signature of each node cannot be forged.Because the algorithm requires that the matching prepared information exceeds 2f+1 to proceed to the next consensus,the Byzantine attack will not affect the final consensus result of the algorithm. 4.1.3 Double Spend Attack Double spend attack is one of the common ways to attack the blockchain.In order to resist double spend attacks,the system sets up a dependency set for each node and unifies it globally.When the consensus node receives a PRE-PREPARE request,it first verifies whether the local dependency set is empty.If it is not empty,the consensus can continue.In addition,the client will match after receiving the PREPARE message returned by all nodes to verify whether there is a conflict in the dependency set.This method can effectively prevent double spend attacks and ensure the security of the blockchain. One of the most important reasons for the poor scalability of most consensus algorithms is their high communication overhead.For example,the communication overhead of the PBFT algorithm isO(n2),wherenis the total number of nodes in the network.Therefore,the performance of the PBFT algorithm will drop rapidly as the number of nodes increases.The SBFT algorithm reduces the communication overhead of the system from two perspectives.First,node screening is performed through DQL,andknodes are selected fromnnodes to participate in the consensus,which reduces the communication scale and thus reduces communication overhead.Second,simplify the consensus process.Since each node in the SBFT algorithm only needs to send the confirmation information to the client after receiving the PRE-PREPARE information,and does not need to send information to all other nodes in the network and receive valid information,the communication overhead of the SBFT algorithm isO(K).Therefore,asnis larger andkis smaller,the communication overhead of the SBFT algorithm is reduced more,and the scalability is improved more. Since the system will regularly filter nodes,and the resources and network bandwidth that each node can currently use for consensus have variability,the nodes selected by the node screening will not be a fixed batch of nodes.In addition,the system will ensure that the proportion of nodes that are repeatedly selected in the current cycle is maintained at a small level during each node screening process,to ensure that most nodes in the network can participate in the consensus and ensure the decentralization of the system. Compared with traditional consensus algorithms,the biggest improvement of the SBFT algorithm is the improvement of consensus efficiency.Taking PBFT as an example,assuming that there arennodes in the network,each node can processfmessages per second.Obviously,PBFT needs at least 2n/3fseconds in both the PRE-PREPARE and PREPARE stages,so the PBFT algorithm completes a consensus process at least takesO(n/f)seconds.The SBFT algorithm first reduces the number of consensus nodes tokthrough node screening,and only the PRE-PARE stage in the consensus process requires at leastk/fseconds,so the consensus delay of the SBFT algorithm isO(k/f)seconds.Therefore,the consensus efficiency of the SBFT algorithm isn/ktimes higher than that of PBFT. In this section,we build a simulation environment to verify the effectiveness of SBFT through numerical simulations and compare it with other consensus protocols.Then,we analyze and discuss the simulation results. In order to better perform the numerical analysis,we use TensorFlow 1.4.1 to build a deep neural network,use python3.6 to build a system model,and use MATLAB2019b to analyze the output results graphically. We run four consensus protocols: SBFT,G-PBFT,E-PBFT,and multi-layer PBFT(M-PBFT) in a simulated environment.The four consensus mechanisms are BFT improvement protocols for the IIoT environment. To simulate the real network,we build a simulation model for each node as follows: 1.The bandwidth of each node is a random value between 80-100Mbps and changes with time. 2.Each node has an initial credit score between 60-80,and the credit score of the node is updated according to the execution after the end of the work cycle of each consensus node.C0is 70,and the value ofC0can be changed according to the requirements for the system security. 3.The calculation speed of each node is a random value between 100-200Hz and changes with time. 4.Each node has an average communication delay between 10-20ms with other nodes,which varies with time. 5.The initialFof each node is 0.After each node is selected,itsFis increased by 1.After five rounds,theFof all nodes is cleared.F0is 2,and the value ofF0can be changed according to the requirements for the degree of decentralization of the system. It is worth noting that the SBFT solutions do not require any additional modifications to the blockchain system.The nodes in the network only need to deploy blockchain services and join the network based on node screening results.The reference [25] proposes a method to separate control and execution in the blockchain.Through this scheme,nodes can join and leave the blockchain network flexibly and dynamically. Figure 8 shows the consensus latency of the four consensus mechanisms compared in this paper.Among them,the total number of nodes in the network n is 16,SBFT and G-PBFT select 4 nodes to participate in the consensus in each cycle,and E-PBFT and MPBFT select all nodes in the network to participate in the consensus.Every 30 consensus cycles,the system will recreate the entire network.It can be seen that because the SBFT algorithm has the lowest algorithm complexity,and the network scale is reduced through node screening,the consensus delay of SBFT is greatly reduced.Although G-PBFT also reduces the size of the consensus network,the consensus nodes are still running the PBFT algorithm,so the reduction of consensus delay is limited.In contrast,the E-PBFT algorithm uses the Gossip protocol to propagate the consensus message,reducing the number of message copies and bringing more obvious communication delay.Since the multi-layer PBFT consensus mechanism divides the nodes in the network into two or more layers,each layer of nodes needs to complete the consensus,so the multi-layer PBFT has a higher consensus delay. Figure 8.Consensus delay of the four schemes. Figure 9 shows the scalability of the four consensus mechanisms compared in this paper.Among them,in the first 30 consensus cycles,the total number of nodes in the network is 16,SBFT and G-PBFT select 8 nodes to participate in the consensus in each cycle;in the 31st-60th consensus cycle,the total number of nodes in the network is 24,SBFT and G-PBFT select 8 nodes to participate in the consensus in each cycle;in the 61st-90th consensus cycle,the total number of nodes in the network is 32,and SBFT and G-PBFT select 8 nodes to participate in each cycle Consensus;in all cases,E-PBFT and M-PBFT select all nodes in the network to participate in consensus.It can be seen that with the increase in the number of nodes,the consensus delay of E-PBFT increases significantly,which reflects the poor scalability of E-PBFT.Multi-layer PBFT can flexibly allocate the number of network layers and the number of nodes in each layer according to the number of nodes,so the scalability is relatively strong.SBFT and G-PBFT effectively ensure the stability of the consensus delay by controlling the scale of the consensus node group.When the number of consensus node groups is the same,the consensus delay of the two algorithms does not increase significantly,which reflects these two algorithms are more scalable.In addition,due to the lower algorithm complexity of the SBFT algorithm,it has lower consensus delay and better scalability than G-PBFT. Figure 9.The scalability comparison of the four schemes. Figure 10 shows the throughput of the four consensus mechanisms compared in this paper.The parameters of the simulation experiment are the same as in Figure 9.It can be seen that with the increase of the number in nodes,the throughput of the worst scalable E-PBFT does not increase significantly.In contrast,the throughput of the SBFT and G-PBFT algorithms increases slowly at first.When the number of consensus nodes stops increasing,the throughput starts to increase substantially.When the number of nodes is increased,the concurrency of the four algorithms increases gradually.Because the consensus delay of EPBFT increases significantly,the transaction processing time becomes longer,and the increase in throughput is also seriously affected.Multi-layer PBFT effectively reduces the communication complexity of the system and improves the scalability of the system,but increases the consensus delay of the system,so the increase in throughput is also affected to a certain extent.The SBFT and G-PBFT algorithms have good scalability.When the concurrency increases,the throughput also increases,and because SBFT has a lower consensus delay,the throughput becomes higher. Figure 10.The throughput comparison of four schemes. Figure 11 shows the communication overhead of the four consensus mechanisms compared in this paper.The parameters of the simulation experiment are the same as those in Figure 8 and Figure 9.It can be seen that,as the number of nodes increases,the communication overhead of the SBFT algorithm and the GPBFT algorithm also increases.After the number of consensus nodes remains unchanged,the communication overhead of these two algorithms stops increasing.The communication overhead of the E-PBFT algorithm has always maintained a relatively obvious increase.Since the multi-layer PBFT can flexibly modify the network structure according to the number of nodes,after the number of nodes reaches a certain level,the increase in the communication overhead of the multi-layer PBFT is less obvious.In any case,the communication overhead of the SBFT algorithm is low.The communication complexity of the algorithm determines the communication overhead of the consensus algorithm.The communication complexity of E-PBFT algorithm isO(n2),but the E-PBFT algorithm effectively reduces the communication overhead of the algorithm by using the gossip protocol.The algorithm overhead of multi-layer PBFT is.The communication complexity of the G-PBFT algorithm isO(k2)(kis the number of nodes selected),and the communication complexity of the SBFT algorithm isO(k).The lowest communication complexity brings the lowest communication overhead to SBFT. Figure 11.The communication overhead comparison of four schemes. In this paper,we proposed SBFT,a flexible and scalable blockchain consensus mechanism for the IIoT,and a detailed consensus execution process.In order to improve the scalability and throughput of the blockchain system,we selected some nodes to participate in the blockchain consensus process which have better performance in the network.Since multiple attributes determine node performance,we formulated the node selection process as a joint optimization problem.We use the Dueling DQL method,which is more effective than natural DQL,to solve this joint optimization problem.The simulation results show that SBFT has good performance in terms of consensus efficiency,throughput and scalability. This paper only used a single consensus protocol,and we decided to propose a switching algorithm for selecting a more appropriate consensus protocol based on user characteristics in future work.3.2 Protocol Overview
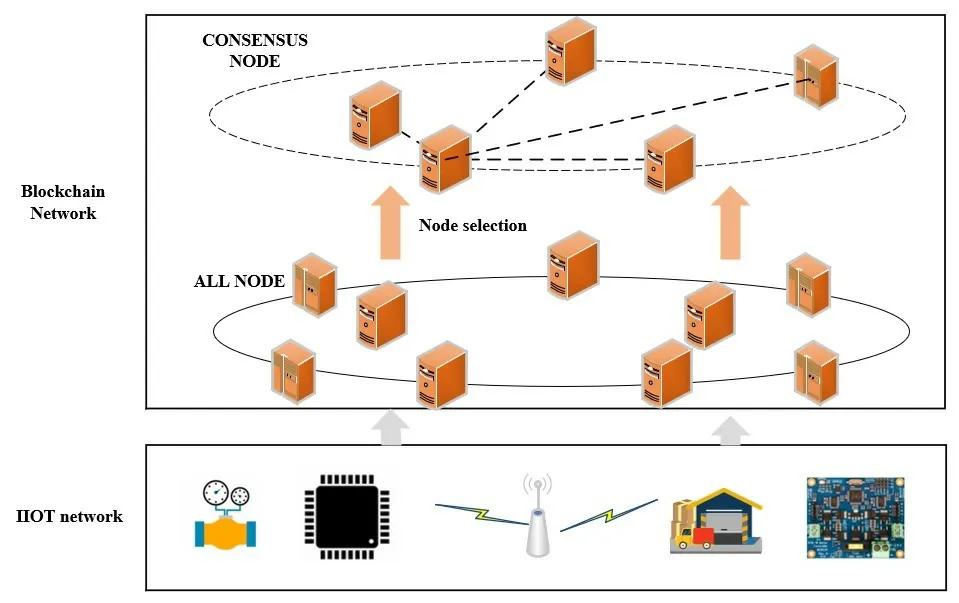
3.3 Node Selection
3.4 CONSENSUS ALGORITHM DESIGN
IV.THEORETICAL ANALYSIS
4.1 Security
4.2 Scalability
4.3 Decentralization
4.4 Consensus Efficiency
V.SIMULATION RESULTS AND DISCUSSION
5.1 Simulation Settings
5.2 Simulation Results and Discussion


VI.CONCLUSION
杂志排行
China Communications的其它文章
- SR-DCSK Cooperative Communication System with Code Index Modulation: A New Design for 6G New Radios
- Sparsity Modulation for 6G Communications
- Sparse Rev-Shift Coded Modulation with Novel Overhead Bound
- Reconfigurable Intelligent Surface-Based Hybrid Phase and Code Modulation for Symbiotic Radio
- Model-Driven Deep Learning for Massive Space-Domain Index Modulation MIMO Detection
- Modulation Recognition with Frequency Offset and Phase Offset over Multipath Channels
