Cloud Data Encryption and Authentication Based on Enhanced Merkle Hash Tree Method
2022-08-24StanlyJayaprakashKishoreBalasubramanianRossilawatiSulaimanMohammadKamrulHasanParameshachariandCelestineIwendi
J.Stanly Jayaprakash, Kishore Balasubramanian, Rossilawati Sulaiman,Mohammad Kamrul Hasan,*, B.D.Parameshachariand Celestine Iwendi
1Department of CSE, Mahendra Institute of Technology, Namakkal, 637503, India
2Department of EEE, Dr.Mahalingam College of Engineering and Technology, Pollachi, 642003, India
3Center for Cyber Security, Faculty of Information Science and Technology, Universiti Kebangsaan Malaysia (UKM),43600, Bangi, Malaysia
4Department of Telecommunication Engineering, GSSS Institute of Engineering and Technology for Women,Mysuru, India
5School of Creative Technologies, University of Bolton, Deane Road, Bolton, United Kingdom
Abstract: Many organizations apply cloud computing to store and effectively process data for various applications.The user uploads the data in the cloud has less security due to the unreliable verification process of data integrity.In this research, an enhanced Merkle hash tree method of effective authentication model is proposed in the multi-owner cloud to increase the security of the cloud data.Merkle Hash tree applies the leaf nodes with a hash tag and the non-leaf node contains the table of hash information of child to encrypt the large data.Merkle Hash tree provides the efficient mapping of data and easily identifies the changes made in the data due to proper structure.The developed model supports privacy-preserving public auditing to provide a secure cloud storage system.The data owners upload the data in the cloud and edit the data using the private key.An enhanced Merkle hash tree method stores the data in the cloud server and splits it into batches.The data files requested by the data owner are audit by a third-party auditor and the multiowner authentication method is applied during the modification process to authenticate the user.The result shows that the proposed method reduces the encryption and decryption time for cloud data storage by 2-167 ms when compared to the existing Advanced Encryption Standard and Blowfish.
Keywords: Cloud computing; cloud data storage; cloud service provider;merkle hash tree; multi-owner authentication; third-party auditor
1 Introduction
Cloud computing has been adopted in many organizations to store and process data in an efficientmanner and any organizations prefer cloud computing due to its advantages of scalability, flexibility and reliability.Cloud services are the best option for companies for the quick response and the best flexibility[1,2].User outsources the data in the cloud to store and process the data due to its scalability and flexibility.Cloud Service Provider (CSP) has to preserve the privacy of the sensitive data and the user has the option of encrypting the data before uploading in the cloud [3,4].Cloud computing provides virtual computing services to extensive, medium, and little industries and services for example Software as a service(SaaS),Platform as a Service(PaaS),and Infrastructure as a Services(IaaS)[5,6].The improved accessibility and technical advancements are extensively favorable for the deployment of cloud servers for storage and computation.Quality of Services, low cost and stability make a cloud a typical choice for computing-intensive tasks [7,8].Security is amajor problem for the cloud computing system and significant revision of the existing security choices leads to develop modern techniques.Guarantee cloud data security and users access control are the current security issues in the cloud[9,10].A trusted Third-Party Auditor (TPA) is applied to verify the cloud data to reduce the burden on users, this is called public auditing.However, the TPA may have unnecessary access to private information in the auditing process [11,12].
The receiver node is verified by the sender node in the authentication process.The sender independently generates the encrypted messages in basic authentication and the symmetric key is used in the receiver to match the key [13].Some of the research involves in apply the complex cryptosystem for authentication in a cloud [14].OTP-based authentication [15], authentication mechanism and cryptography algorithm [16-20], Multiple factor-based authentication, anonymous node ID assignment are some types of methods in cloud authentication.Security is the important aspect of cloud services and attacks in the cloud tend to lose of personal information of the users and profit to the company.Data integrity is the way to track the data in the cloud and retrieve the old version to retrieve the affected data easily.Searching is another important aspect of encrypted data and the Cloud needs to support the search process in encrypted data to retrieve the user data securely.Therefore, an efficient method is needed in the cloud to manage security, integrity and search on encrypted data.In this research,the enhanced Merkle hash tree method with multi-owner authentication is proposed to secure data in cloud storage.The enhanced Merkle hash tree method is applied to perform a significant data integrity check in cloud storage.Every node in the Merkle hash tree contains the information of position relative to its parent node.The user obtains a public key from the TPA using an authentication request to download the encrypted data.If the user is authorized, the data owner gives the decryption key to the user to decrypt the encrypted data.
This research paper is organized as follows: Section 2 surveys several existing research papers on cloud data storage authentication with problem statements.In Section 3, an effective method called the enhanced Merkle hash tree is presented with a multi-owner authentication technique for cloud data storage authentication.Section 4 explains the performance of the proposed method.The conclusion of this research paper is given in Section 5.
2 Literature Review
This section reviews recent and significant research approaches suggested by researchers in cloud data storage authentication.A brief evaluation of the essential contributions and main gaps in the existing literature are presented to support the presented proposal.
Shajina et al.[21] proposed a dual authentication protocol with two level of authentication with the list of precedence-based access control to improve the security and scalability of the cloud.The triple-DES algorithm with the identity of the user was applied as an extra attribute to improve the security in the cloud.The anonymous of the user was protected in this method to improve the security and the proposed method for the multi-owner cloud was verified in multiple scenarios.The verification shows that the proposed method has a lower average network time and high security in the cloud.The developed methodology achieves secure and effective data sharing in dynamic cloud storage.However, the developed methodology provides insecure data sharing as a one-to-one solution and lower efficiency in large datasets.
Anand et al.[22] proposed Elliptic Curve Digital Signature Algorithm (ECDSA) and Enhanced Elliptic Curve Diffie-Hellman (EECDH) method for mutual authentication in the multi-owner in the cloud.The proposed EECDH method was applied to exchange the secure key to the owners and eliminatethe Man-In-The-Middle(MITM)attack.The proposed method protects the data integrity in the cloud.The identity and attribute-based access policy increases the robustness of the method.The developed cloud computing system still has vulnerabilities, specifically in networks that have several third-party platforms and complex infrastructures.
Deep et al.[23] applied blockchain technology for secure authentication in the cloud to increases security.Blockchain technology makes it easy for an insider to change the login credential details for the authentication process.The correctness and applicability of the method were tested on the cloud.The Scyther formal system was used to test the proposed method against no reply attack, offline guessing,impersonation and denial of services.The result shows that the proposed method was robust in secure the user information in the cloud.The developed authentication scheme was an open cloud computing system that frequently encountered social engineering and phishing attacks.The integrity check in the model was poor due to the unstructured encryption process in the data.
Badr et al.[24] proposed an Attribute-based encryption method that considers authority, cloud servers, data users and data owners to secure the data in the cloud.The decryption process was delegated by the data owner to reduce the computational complexity.The MAC encryption text associated with the data stored in the cloud was generated after encryption.The attribute property was applied for the encryption and decryption was based on verification.The various attacks have been applied to test the performance of the developed method.If the number of authentication samples is low, the authentication rate will be reduced.The Attribute-based encryption has a higher overhead for the large database and has lower performance in integrity check.
Ge et al.[25] developed Accumulative Authentication Tag (AAT) using symmetric key cryptography for the authentication of keywords.The authentication tag was updated based on dynamic operations in the cloud.The secure index consists of a search table based on the orthogonal list and verification list containing AAT.The method updates are based on connectivity and flexibility.The AAT method has lower overhead and lowers computation time during a keyword search than a secure conjunctive keyword search.An analysis showed that the developed method was secure and efficient and the memory usage of the method needs to be reduced for the authentication process to be effective.The AAT methods store the tag method for the encrypted data for integrity and memory usage for the tag is high for the large dataset.
Zhong et al.[26] developed a mutual authentication and key agreement scheme based on elliptic curve cryptography for the peer-to-peer cloud.The elliptic curve certificate-free cryptography method was used for key generation.This method eliminates the trusted authority and simplifies mathematical operations to increase security.The security correctness of the method was analyzed, and it showed that the method was secure.This proposed method reduces computational and communication costs compared with existing methods.Further development is required to support multi-user access to cloud data securely.
The existing methods have considerable performance in the encryption of data in the cloud for multi-cloud support.TheDES algorithm [21]method provides the supportmulti-cloud with improved security and has lower efficiency in large datasets.The EECDH [22]method provides the data integrity in the cloud and this method fails to perform in the large dataset due to the attribute-based method.Blockchain technology [23] provides higher security in data transmission and this is not suitable for cloud-stored data.Attribute-basedmethods [24-26] was suitable for cloud storage and lower efficiency in large dataset.Commonly, existing methods have limitations of doesn’t support data integrity or lower efficiency in large datasets.
3 Problem Statement
This section describes the problem statement for the Merkle hash tree in cloud data storage authentication and explains how the proposed methodology provides a solution to the described problems.The concerns about the Merkle hash tree approach are detailed as follows:
Searching theithleaf node in data integrity auditing is computationally complex in the Merkle hash tree approach.If the storage structure is continuous, the number of operations like insertion and deletion are quite high.After performing the deletion and insertion operations, the sequence number of the nodes is likely to be modified, and the height of the tree may become imbalanced [27].
The Merkle hash tree approach has no function to manage data integrity auditing, which is called empty proof [28].Also, it does not provide any integrity guarantee for the data, because integrity assures that outsourced data is intact.The traditional Merkle hash tree uses either a message digest(MD) or a Secure Hash Algorithm (SHA) as the hash function.Most of the time, these functions do not indicate tree depth, which leads to second preimage attacks.
Solution: To overcome the above-mentioned drawbacks, an enhanced Merkle hash tree is implemented with a multi-owner authentication methodology to improve the performance of cloud data storage authentication.Here, a new hash function of the tiger tree hash function is replaced with an MD or SHA hash function in the Merkle hash tree.The tiger tree hash method is a truncated version with a specific hash size, so there is no need to distinguish the defined values.It contains a total of 24 rounds, with digest sizes of 128, 160, and 192.The tiger hash function uses 244compression functions in the16thround to avoid equivalent time complexity and uses 248compression functions in the19thround to secure the stored data from a collision attack.A detailed description of multi-owner authentication and an enhanced Merkle hash tree is given in Section 4.
4 Proposed Methodology
The proposed methodology is used for data integrity, load balancing, and multi-owner authentication in the cloud environment.A publicly verifiable methodology of enhanced Merkle hash tree with multi-owner authentication is used to protect the integrity of the cloud data and also to support dynamic maintenance.
4.1 Multi-Owner Authentication
In this method, a highly securemulti-owner authentication methodology is implemented to secure the cloud server database.Initially, the data are uploaded to the cloud server by the data owner in an encrypted format using an enhanced Merkle hash tree approach.
The user is provided with a public key for viewing and downloading the data, and the data owner verifies the user (authorized or unauthorized) using the public key.If the user is authorized, then a decryption key is provided by the data owner to the user for decrypting the data.A load balancing concept is also implemented for processing the user-requested job.Finally, the user request is passed to the cloud server.If the user is authenticated, the cloud server replies to the user query.The general design of the cloud data storage is denoted in Fig.1.A brief evaluation of the proposed technique is determined as follows:
4.2 System Model for Cloud Data Storage
This sub-section describes the systemmodel shown in Fig.1.Generally, the integrity of cloud dataarchitecture involves the following parties [29-31].
Data owner
First, the data owner needs to register on the cloud service provider’s server.After registration,the cloud service provider generates private and public keys and sends the keys to the data owner.The respective data are encrypted based on the Enhanced Merkle Hash tree method and uploaded to the cloud server.The sender encrypts the data using a public key, and only the holder has a private key to decrypt the respective data.
User
To access the network, the user needs to initially create an account.After creating the account,the user logs into the account and requests auditing from the cloud service provider.Based on the user request, the cloud service provider will process the task.The network uses programming languages like .NET or Java for communicating with the cloud server.The user can access the requested data by sending a request to the cloud service provider.The enhanced Merkle Hash tree given private key is used by the user to access the cloud data.
Cloud Service Provider
TThe cloud service provider makes a combination of hardware and software resources available and delivers flexible online data storage and computing.The cloud service provider stores a large amount of data and alsomanages the authentication of the data owner and users.To process the user-requested job, the cloud server redirects the job to any queue.In the queue, virtual machines are utilized to process user requests.
Third-Party Auditor
The TPA is performed on the encrypted cloud data to check the integrity of the data stored in the cloud.Based on the data owner’s request, the TPA audits the data, which are uploaded by the data owner.The TPA needs to register with the cloud server to audit user-requested data.The TPA sends a request to cloud storage to audit the data present in the cloud.The cloud performs a bilinear mapping on the user data and sends the proof to the TPA.The TPA performs a comparison between the user-provided data and the cloud-provided data.The encrypted data is used to protect the privacy of the file.
Bilinear Mapping
The bilinear mapping is the preliminary step of encryption to represent the data in mapping form.The cyclic groupGof the data is given as input andeis the bilinear mapped output.Consider a groupGas a gap Diffie-Hellman group with prime orderp.A bilinear map is developed ase:G×G→GT,whereGTis a prime order, multiplicative cyclic group.A usefulehas the following properties:
Bilinearity-∀m,n∈G⇒e(ma,nb) =e(m,n)ab;
Non-degeneracy—∀m∈G,m0⇒e(m,m)≠ 1;
Computability—eshould be efficiently computable.
Bilinearity is the property of representing the data with a two-dimensional vector, non-degeneracy is the property of data that is degenerated to the original data, and computability is the ability to solve a problem in an effective manner whereaandbare real random numbers.
4.3 Merkle Hash Tree Approach for Key Generation
The Merkle Hash tree method is applied to encrypt the data before uploading to the cloud and the Merkle Hash tree method generated private is used to decrypt the data in the cloud.Merkle Hash Tree method stores the table of hash values from the encrypted data in the non-leaf node and leaf node consists of encrypted data with a labeled hash value.This structure of encryption helps to identify the changes in the data related to the leaf node that helps to increases the integrity.Merkle Hash tree method stores the hash value instead of duplicate the whole data in the leaf node and this helps to encrypt the large dataset with less memory.The Merkle hash tree method is a binary tree data structure with leaf nodes integrated at each node.The Merkle hash tree root node is present as the top node, and the leaf nodes consist of data hashes.Root node authentication provides access to the leaf nodes’integrity declaration.A Merkle hash tree with eight leaf nodes is shown in Fig.2 [28].Bilinearly mapped cloud data is used for encryption based on the Merkle hash tree method.The advantage of using the Merkle Hash tree is that it effectively verifies the data in the distributed system using hash values.In the Merkle Hash tree, a node is denoted,Ni,jwereiandjare theithlevel andjthlevel of the node.The cryptographic variableHi,jstores nodeNi,j, and the nodes at level 0 are called“leaves.”The leaves describe the data stored in the tree.In the case of revocation, the leaves that have been revoked are represented by a certificate set Φ that has been revoked, as shown in Eq.(1).
where,cjis the data stored in leafN0,jandH0,jis computed as in Eq.(2).

where,his a one-way hash function.
To build the Merkle hash tree, adjacent nodes settat a given leveli(Ni,j,Ni,j+1,...,Ni,j+t-1) are combined into one node at the upper level that is denoted byNi+Ni+1,k.Then,Hi+1,kiis measured by applyinghto the concatenation of thetcryptographic variables, as in Eq.(3).


Figure 2: Eight leaf nodes Merkel hash tree
At the top level, one node is present and is denoted as “root”;Hroota digest for all the data storedin the Merkle hash tree.
For a file blockmi, a leaf node is used to computehi=H(mi), and a parent node ofN1andN2is constructed asNp= {H(h1||h2)}.A leaf node ofAuxiliary Authentication Information (AAI)Ωiis a set of hash values selected from each of its upper levels so that the root valueRcan be computed{mi,Ωi}.
For example, the data owner asks the auditor for data integrity verification at one position.The auxiliary informationAI(d[1]):{(HD,R),H(d[1]),(H(d[2]),R),(HB,R)} is provided by the data owner to the auditor.Then, the rootHRis generated by the auditor as follows,
MeasureHD←(H(d[1])||H(d[2]));
MeasureHA←(HC||HD);
Determine the rootHRoot←(HA||HB).
The root node authenticity is verified to automatically authenticate all the blocks.Each node consists of two pieces of information, such as the hash value and the relative index.The Merkle hash tree method consists of three stages, namely the set-up stage, challenge-prove stage, and update stage.An explanation of each stage is given as follows:
Set-up Stage
The set-up stage involves system initialization at the client end.This stage consists of three functions.
Key generation (1key): The probabilistic key generation method {skey,pkey} is used and the input is thekeysecurity parameter.The input is the private keyskey, and the output is the public keypkey.The public keypkeyis published by the data owner and the private keyskeyis kept safe for decrypting the respective data.
Tag generationskey,pkey,m→meta data: The client document input metadata is,skey,pkey,mand the client stores locally the output metadata tags δ.The client remotely stores the respective documentsmand tag δ at the server end.
Block-sig-generation: Once the tag documents δ are generated, the data owner uses the cryptographic hash function to generate signatures for each data block.Generally, either MD or SHA is used as the hash function.
Challenge-Prove Stage
The challenge-prove stage is an interaction between client and server.The client identifies the problem and sends challenges to the server.The server analyzes the respective issues and sends output to the client.The challenge-prove stage involves three processes.
Gen-challenge(C)→{chal}: The input for this process is the client’s private parameterc, and the output is challengechalfor future queries.
Gen-proof ((ps,m,δ,chal)→{G}: The input is a documentm, metadata δ, public parametersps,and challengechal, and the outputGis given to the user for server verification.
Check-proof (pkey,chal,meta,data,G)→ {“reject”,“accept”}: This process is used for target document server possession check.The input is the user public keypkey, metadata δ, challengechal,and evidenceG.The evidenceGis analyzed, and the function returns“accept”or“reject.”
Updated stage
In the Merkle hash tree, the update stage is a verification process for supporting dynamic data operations.The function of this stage is explained as follows:
Perform-update (pkey,m,δ,update)→{m′,δ′,Gupdate}: After the server receives theupdaterequirementfrom the client, this operation is performed.The input for this process is a documentm,metadata δ, public keypkey, and the update.The output for future checking consists of a new tag δ′, updated documentm′, and updated evidenceGupdate.
Verify-update (pkey,update,metadata,Gupdate)→ {(metadata′,“accept”),“reject”}: This process checks the correctness of the dynamic operation at the server end, and verifies the client.The update triggers the verification function, and the input is metadata δ, public keypkey, andGupdate.If the update evaluates correctly, it returns“accept”and retains the metadata locally, or the process returns“reject.”The Merkle hash tree protocol supports the data dynamic process and the public auditing of data.Still, a few major flaws in the Merkle hash tree protocol are detailed in Section 3.To overcome these issues, an enhanced Merkle hash tree approach is developed in this research study.
4.4 Enhanced Merkle Hash Tree Approach
This sub-section describes the enhanced Merkle hash tree approach.In this proposed technique,a new hash function (tiger tree hash function) is used in a Merkle hash tree instead of the MD or SHA hash function.In the tiger hash function, the one-way compression function operates on 64-bit words,where it processes 8 words of data and maintains 3 words of state.In total, the tiger hash function includes 24 rounds, using a combination of operations like S-box lookups, rotate, and XOR (addition and subtraction).An effective, intricate scheduling key technique is used to derive keys in 24 rounds from the 8 input words.This operation makes the implementation easy in a microcontroller and other hardware.A sample binary tiger hash tree is shown in Fig.3.
Finally, the TPA audits the data requested by the data owner using the enhanced Merkle hash tree approach.The TPA updates the auditing information at a certain time, so the security of the data is ensured.Also, the auditor updates the data owner if any change occurs while the data are being audited.

Figure 3: Sample binary tiger hash tree structure
5 Experimental Result and Discussion
This section provides a detailed description of the experimental set-up of the proposed method,and a measure of its performance.The performance is analyzed with comparative and qualitative analyses.
5.1 Experimental Set-Up
The proposed approach was experimentally tested usingNet-Beans (version 8.2) with 4GB RAMa 3.0 GHz Intel i3 processor, a 500 GB hard disc, and MY-SQL server as a cloud service provider.To estimate the effectiveness of the proposed methodology, the proposed approach of enhanced Merkle hash tree with multi-owner authentication performance was compared with several existing approaches: Advanced Encryption Standard (AES) and Blowfish [6].In this study, the performance of the proposed approach was compared in terms of encryption time, memory usage, and decryption time.
5.2 Discussion
This section discusses the comparison between the proposed approach and other key assignment approaches in terms of a few characteristics, and it details the compression ratio for dissimilar tree heights and delegation ratios.Tab.1 presents a comparison of five key assignment approaches with different properties such as decryption key size, cipher-text size, encryption type, and file classification relationship.Tab.1 shows that most of the encryption types of the existing methods are based on the public key, decryption key size is constant, cipher size is constant and irrelevant to the data.Constant cipher size is vulnerable to attacks and data is easily accessed with common attacks.Encryption of the existing methods is irrelevant to the File classification and integrity check for the data is difficult.Therefore, the proposed Merkle Hash tree method cipher size is inconstant to make it difficult for attacks and integrity check is carried out easily due to the encryption is based on File classification.
Generally, the communication overhead and information leakage risk increase with a greater number of delegation decryption keys.In existing key assignment schemes (symmetric-key encryption,key-aggregate encryption [26], etc.), the decryption key generation depends on previous classification files.When a new file class is uploaded to the cloud server, the whole classification structure must be changed in these methods.The proposed method generates an inconstant ciphertext size and a constant decryption key size.This is relevant to file classification and supports the incessant updating of files.
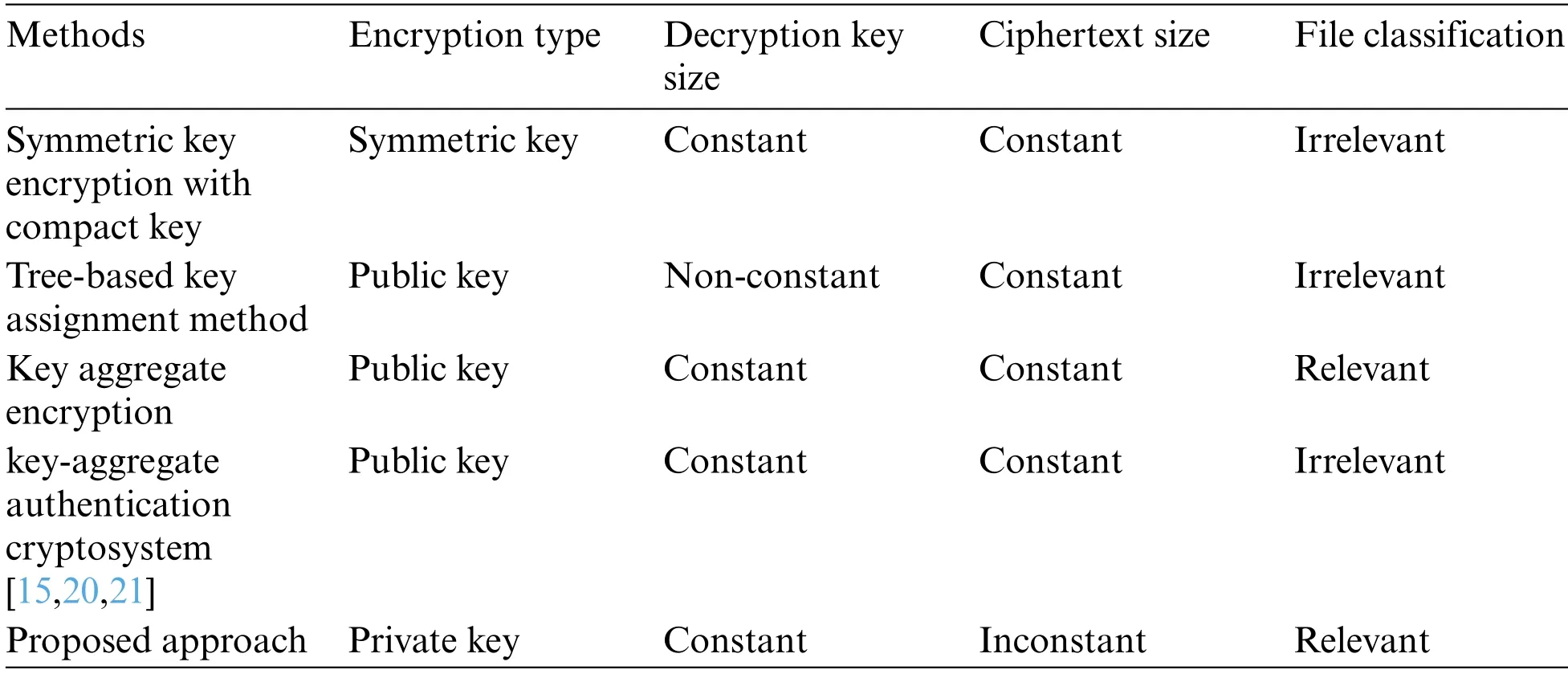
Table 1: Characteristics of a proposed and existing method
The proposed method is evaluated with dissimilar key sizes and the delegation ratio in Tab.2 and it clearly shows that the delegation keyDkeyincreases with the increase in the delegation ratio.

Table 2: Delegation ratio and dissimilar tree height comparison
5.3 Encryption and Decryption Time Analysis
The encryption and decryption of the proposed method are analyzed in this section.For experimental analysis, ten different file sizes are considered, such as 83.3KB, 108KB, 249KB, 333KB,416 KB, 1370 KB, 2740 KB, 5480 KB, 10003 KB, and 15483 KB.The existing methods carried out the encryption to encrypt the data with tags in the unstructured format that reduces the capacity to handle the large data.The Merkle has a tree encryption process involves in creating the hash for the data,store the hash value in the table and apply labels to encrypted data.This structured process decreases the encryption time of the Merkle Hash Tree method and the hash value in the table reduces the decryption time in a large dataset.The encryption and decryption times of the proposed and existing methods are shown in Tab.4.The average encryption time of the proposed method (enhanced Merkle hash tree with multi-owner authentication) is 132.9 msec.The existing methodologies (AES and Blowfish [6]) achieved average encryption times of 300.4 msec and 215.4 msec.The graphical comparison of encryption time is shown in Fig.4.
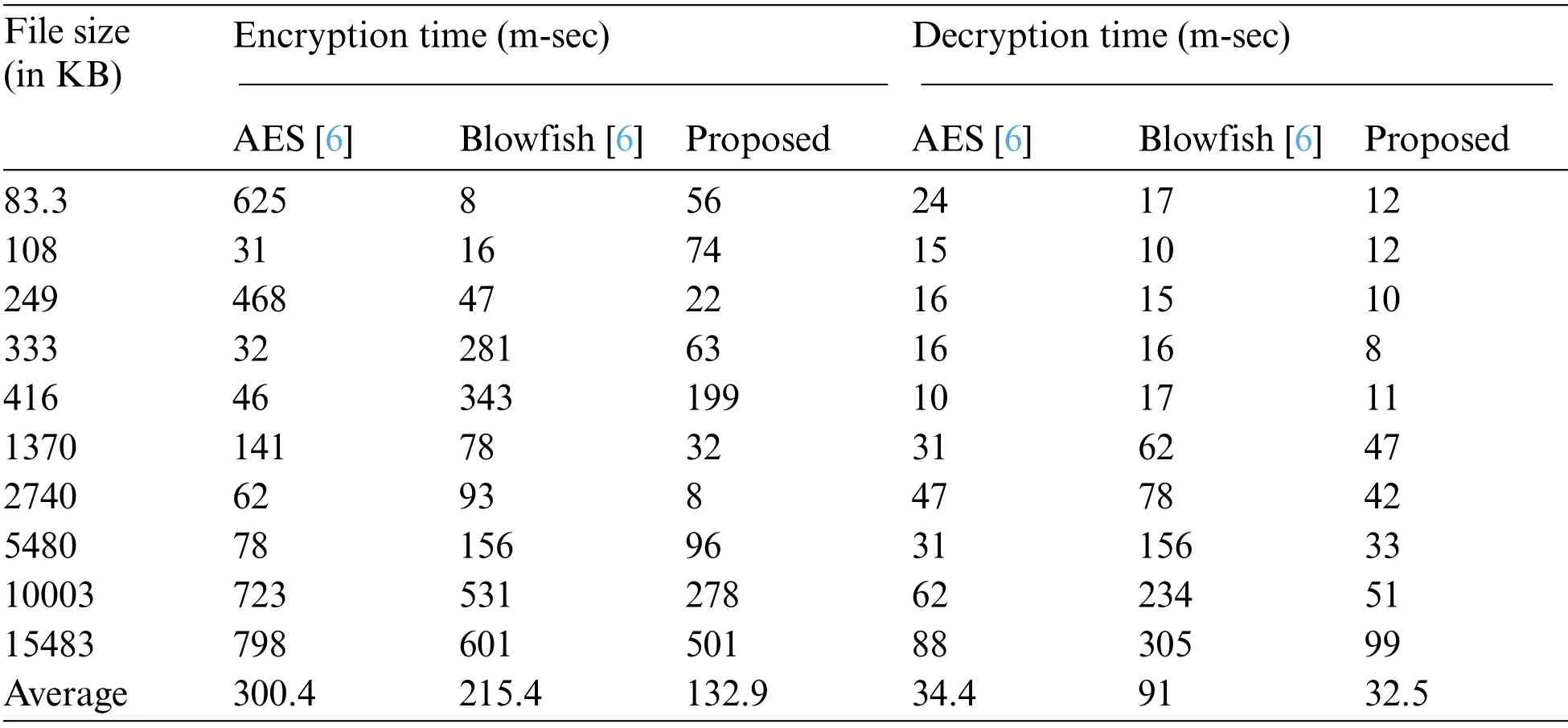
Table 3: Proposed approach evaluation using encryption and decryption time

Table 4: Proposed method memory usage analysis
Correspondingly, the average decryption time of the proposed methodology is 32.5 msec; for the existing methodologies, the average encryption times are 34.4 msec and 91 msec.The comparison of decryption time is shown in Fig.5 and the performance analysis of the proposed and existing methods is shown in Tab.3.The encryption and decryption time show that the proposed method achieves higher performance for cloud data storage authentication than previous methods.

Figure 4: Encryption time of the proposed method

Figure 5: Graphical representation of decryption time comparison
AES [32] is a symmetric Feistel block cipher protocol that utilizes a similar key for both the decryption and encryption processes.This protocol contains fourteen rounds and only accepts a block size of 128 bits.By choice, it contains another two keys with a length of 192 and 256 bits and variable rounds of 10 and 12, respectively.
Blowfish [33] is another Feistel symmetric structure algorithm that consists of a 64-bit block size,which varies from 32 to 448 bits with 16 rounds.Also, the Blowfish algorithm contains a large keydependent box for encryption, and it uses 4 S-boxes for decryption.In this algorithm, the level of security depends on the size of the key.The Blowfish algorithm is easily affected by the different key attacks because several rounds are used as a masker key that makes the algorithm infeasible [34,35].
5.4 Quantitative Analysis for Memory Usage
The memory usage of the proposed and existing methods is analyzed in this section.In Tab.4,the proposed approach (enhanced Merkle hash tree with multi-owner authentication) outperforms existing methods with an average memory usage of 7,107,722.6 KB.The existing methods duplicate the encrypted data with the tag that increases the computation time and memory of the cloud.The proposed Merkle Hash Tree method stores the hash value in the data for the search process and encrypted data is applied with a label.The hash value and label require less memory than unstructured encrypted data.The memory usage averages of the existing methods AES and Blowfish [6] are 54,573,308.1 KB and 28,185,164.8 KB.Tab.4 shows that the proposed enhanced Merkle hash tree with multi-owner authentication method performed effectively compared with the existing methods.The memory usage graphical comparison is represented in Fig.6.

Figure 6: Graphical representation of memory usage comparison
After inspecting Tabs.3 and 4, it was determined that the tiger hash function-based Merkle hash tree approach shows better performance in terms of memory usage, encryption time, and decryption time, whereas Blowfish is the second-best algorithm for cloud data storage authentication.
The running times of the proposed and existing methods [25,26] are shown in Fig.7.The AAT[25] requires more computational time than the enhanced Merkle hash tree with a multi-owner authentication method due to the generation of tags in the method, and the elliptic curve cryptography method [26] requires a greater computational time.The proposed method requires less computation due to the tiger hash method.

Figure 7: The user side running time of the proposed method
The server-side runtime of the enhanced Merkle hash tree is compared with the existing methods,as shown in Fig.8.The AAT [25] requires greater computational time on the server-side to analyze the tags,and the elliptic curve cryptography method [26] requires more time for the decryption process.The tiger hash tree in the Merkle method reduces the decryption process on the server-side.The proposed enhanced Merkle hash tree method has a server-side runtime of 8.14 ms, and the AAT [26] method requires 10.88 ms of runtime.This shows that the proposed enhanced Merkle hash tree method has a lower computation time than the existing methods.
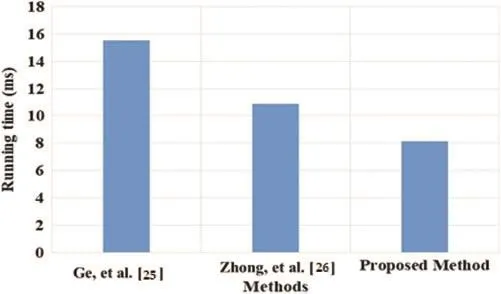
Figure 8: The server-side runtime of the proposed Method
6 Conclusion
In the current decade, the cloud computing paradigm has become standard for computer services due to its flexible computational abilities and high storage capacity.In this article, a new authentication methodology is presented to further ensure the security of cloud data storage.An enhanced Merkle hash tree with a multi-owner authentication technique is used for cloud data security.The enhanced Merkle hash tree approach algorithm encrypts user data and stores it in the cloud.The stored data is retrieved using a decryption function based on a user query.The proposed multi-owner cloud authentication method delivers an effective performance compared with other approaches for cloud data storage authentication.The experimental analysis shows that the proposed enhanced Merkle hash tree method has lower memory usage and lower encryption and decryption times.The proposed methodology saves between 2 and 167 msec of encryption and decryption time over existing methods(AES and Blowfish).In future work, a secure relevant data retrieval approach based on elliptic curve cryptography is incorporated in the cloud data storage application to increase the resilience against various attacks.
Author Contributions:The paper investigation, resources, data curation, writing—original draft preparation, writing—review and editing, and visualization were done by J.S.and K.B.The paper conceptualization, software, validation, and formal analysis were done by C.I., S.C.N, R.S, M.K.H.Methodology, supervision, project administration, and final approval of the version to be published were conducted by A.S.C:I and B.D.P.All authors have read and agreed to the published version of the manuscript.
Funding Statement:The Universiti Kebangsaan Malaysia (UKM) Research Grant Scheme FRGS/1/2020/ICT03/UKM/02/6 and GGPM-2020-028 funded this research.
Conflicts of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.
杂志排行
Computers Materials&Continua的其它文章
- Constructing Collective Signature Schemes Using Problem of Finding Roots Modulo
- Modeling and Simulation of Two Axes Gimbal Using Fuzzy Control
- Artificial Monitoring of Eccentric Synchronous Reluctance Motors Using Neural Networks
- An Optimal Scheme for WSN Based on Compressed Sensing
- Triple-Band Metamaterial Inspired Antenna for Future Terahertz (THz)Applications
- Adaptive Multi-Cost Routing Protocol to Enhance Lifetime for Wireless Body Area Network
