Improved Channel Reciprocity for Secure Communication in Next Generation Wireless Systems
2021-12-16ImtisalQadeerandMuhammadKhurramEhsan
Imtisal Qadeer and Muhammad Khurram Ehsan
1Ind.Reseacher,Neckarstraße 244,PLZ:70190,Stuttgart,Germany
2Zelle Solutions,Office#FF-37,Saima Square,Gulshan-e-Iqbal,Block-10A,Karachi,Pakistan
3Faculty of Engineering,Bahria University,Lahore Campus,Lahore,Pakistan
Abstract:To secure the wireless connection between devices with low computational power has been a challenging problem due to heterogeneity in operating devices,device to device communication in Internet of Things(IoTs)and 5G wireless systems.Physical layer key generation (PLKG) tackles this secrecy problem by introducing private keys among two connecting devices through wireless medium.In this paper,relative calibration is used as a method to enhance channel reciprocity which in turn increases the performance of the key generation process.Channel reciprocity based key generation is emerged as better PLKG methodology to obtain secure wireless connection in IoTs and 5G systems.Circulant deconvolution is proposed as a promising technique for relative calibration to ensure channel reciprocity in comparison to existing techniques Total Least Square (TLS)and Structured Total Least Square(STLS).The proposed deconvolution technique replicates the performance of the STLS by exploiting the possibilityof higher informationreuse and its lesser computational complexity leads to less processing time in comparison to the STLS.The presented idea is validatedby observing the relation between signalto-noise ratio (SNR) and the correlation coefficient of the corresponding channel measurements between communicating parties.
Keywords:Channel measurements;physical layer key generation;channel reciprocity;Internet of things;deconvolution
1 Introduction
Next generation of wireless systems specifically 5G,introduces a platform for better exploitation of Internet of Things (IoTs).IoTs do not only require the heterogeneity of the operating devices [1,2],better energy consumption [3]and secure communication are also the major concerns in such wireless systems [4-6].According to some statistical studies such as [7],there will be more than 30 billion devices wirelessly connected to Internet and also with each other too.This colossal network of devices will evidently require some efficient wireless security measures.One of the promising methods for such wireless security is called Physical Layer Key Generation(PLKG) [8-10].The Wire-tap channel model is the first method to prove that secrecy can be obtained by exploiting physical layer properties [11].This method overcomes the discrepancies in initial cryptographic methods such as,exponential operations and computationally bounded security [12].This approach is then used by the authors in [13,14]to design PLKG technique.One of the key benefits of PLKG is to use information theoretic-security for creating cryptographic keys [15,16].The principle model of PLKG includes two legitimate nodes Alice and Bob which need to communicate privately and a third node,Eve,who wants to eavesdrop the communication between Alice and Bob.The legitimate nodes send probe signals to each other in order to learn the channel properties.The data in these signals is known beforehand to both nodes and the variation in the data due to channel profile is learned by exchanging such signals.These channel measurements are used to generate a private key.The intrinsic part of this model is to hide these measurements from Eve.The working of PLKG model is based on following fundamental properties i.e.,channel reciprocity [17,18],temporal and spatial variation.PLKG assumes a reciprocal channel between Alice and Bob which makes it highly probable that the private key generated at both ends will be similar.The temporal channel variation means that the changes in the channel properties (due to change in ambient temperature,objects in line-of-sight (LOS),noise and interference etc.) can be exploited to ensure the randomness of the private key.This means that each newly generated private key,between Alice and Bob,would be random and different [19].The spatial variation makes sure Eve should be at safe distance from either of Alice or Bob.If position of Eve is not close to Alice and Bob,it would experience a different channel and the measurements will be different as well.The required distance is estimated by Jake’s model asλ/2,whereλis the transmission wavelength.Typically,there is no hard bound for the safe distance and it can vary from case to case [20].
The architecture of PLKG is divided into different blocks which collectively work to produce a private key as shown in Fig.1,a detailed description about this architecture is provided in [21].At first,Alice and Bob send pilot signals to each other.These signals are used to acquire channel state information (CSI) or receive signal strength (RSS) of the channel within channel measurement block.Pre-processing block deals with enhancing the reciprocity between Alice and Bob and de-correlating their respective measurement sequences.The processed signal is then passed to quantization block and converted from signal to binary digits,often the resulting binary stream is referred to as pre-key.Afterwards,information reconciliation block is used to reconcile the pre-key among Alice and Bob by using the cascade protocol or the LDPC codes.Privacy amplification block increases the diversity of the reconciled key and it is carried out by using hash functions [22,23].The focus of this work is on the pre-processing block.Previously,methods like Savitsky Golay filtering along with Walsh,Haar or other similar transform were used for pre-processing [24].However,these methods lack in certain aspects.The first drawback was the overhead computation required to compensate increased redundancy while enhancing the reciprocity (in the form of de-correlation).Secondly,the recursive nature of reciprocity enhancement,as each measurement has to be processed individually.Thirdly,it fails to address hardware differences such as,front-end attenuation,antenna gain mismatch etc.The incapability of previous reciprocity enhancement model (pre-processing) to cater hardware differences,leads to the further investigation for improving reciprocity.Assuming that the front-end hardware brings imperfection [25],we consider the channel between communicating parties as the effective channel comprising of two parts.First is the true channel which remains same because of being reciprocal.Whereas second is the filter imperfections which vary along the nature of filters.
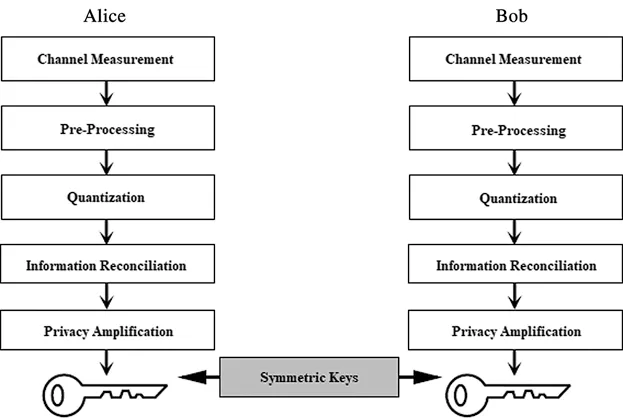
Figure 1:PLKG architecture
According to [26],relative calibration can be used to nullify the effect of filter imperfections.There are several advantages of using relative calibration,e.g.,the calibration is executed by signal processing measures and takes place entirely in signal space.Moreover,the relative calibration is easy to be implemented and flexible to be used as it does not require any specific hardware arrangements,especially for dissimilar front-ends of the communicating stations.This is really beneficial when dissimilar front ends are used for the communicating stations.
The researchers have implemented relative calibration in terms of channel coefficients which are obtained in both time and frequency domains.From literature we have discovered that schemes like Channel Gain Compliment (CGC) [27]with focus on frequency response of channel coefficients and exploit the randomness between adjacent frequency sub-carriers at each time instant.The non-reciprocity element in the calibration process is also computed.Furthermore,the hardware differences can be compensated by complementing this non-reciprocity element in each frequency sub-carrier.An extension to CGC is devised in [28]which is referred as a novel transform to mitigate hardware-differences namely,log-domain differential (LDD) transform.The authors claimed that it is a real-time transform which does not require the learning of channel imperfections.In this paper,time domain relative calibration is performed using deconvolution based on Toeplitz and circulant structures.
The contributions of this paper are included as following:
• In order to ensure channel reciprocity,the relative calibration is implemented using state of art deconvolution techniques including the Total Least Square (TLS) and the Structured Total Least Square (STLS).
• Circulant deconvolution technique is proposed as an alternative to the existing techniques and is hypothesized as better performing than the TLS and the STLS.
• The proposed deconvolution technique replicates the performance of the STLS by exploiting the possibility of higher information reuse and its lesser computational complexity leads to less processing time in comparison to the STLS.
• The simulation results of the proposed method also validate that secure communication is possible by adapting the circulant deconvolution within wireless systems having ultra-low latency including 5G and IoTs systems due to its less computational cost.
The paper is organized as follows.Section 2 discusses the system model in hand.Section 3 describes the method of performing the relative calibration.The deconvolution using circulant structure has been introduced in Section 4.Section 5 provides the simulation results.Finally,conclusions are discussed in Section 6.Vectors and matrices are denoted using boldfaced characters.In this paper,andare the error and the estimated values of x,respectively.The ‘*’represents the convolution.Parameters indexed by roman characters A and B are associated with the communicating nodes Alice and Bob,respectively.
2 System Model
It is assumed that two nodes A and B referring to Alice and Bob,respectively,need to communicate over a wireless Time Division Duplex (TDD) channel within time duration shorter than channel coherence time.The system model is shown in Fig.2 which is comprised of cascaded linear filters for both the paths A to B and B to A.The linear filters are consisted oftA,tB,rAandrBas output and input filters respectively,whereas C represents the true channel.The input and output filters are introduced to model as front-end hardware differences [26]which results in the non-reciprocity i.e.,tA/=tBandrA/=rB.WhilenAandnBare assumed to be Additive White Gaussian Noise (AWGN) whereas G and H represent the forward and reverse effective channels including the imperfections introduced by the front-end filters,respectively.In the system model,tA,tB,rAandrBare considered time-invariant filters.The reason is that the front-ends vary slower than the channel as discussed in [26].The forward and reverse chains of the system in Fig.2 can be expressed as convolution of cascaded linear filters

where G(t,τ) is the forward and H(t,τ) is the reverse effective channel.The relation between these cascaded chains has been derived in [26]and expressed as

where P(τ) is the non-reciprocity element and is modeled as the filter imperfections,which of course is the function of delay only.However,in reality,the filter imperfections are produced by the finite length filters,which can be modeled asτ.If we assume that only one-time instant is considered,then the Eq.(2) can be simplified as

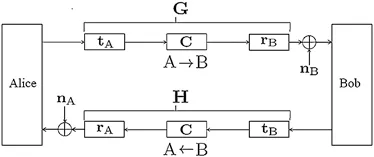
Figure 2:System model
where,g represents vector that contains channel coefficients from forward effective channel,H represents a square matrix of a specific structure covering the channel coefficients of the reverse effective channel and p is a vector that represents the calibration metric.p contains the nonreciprocity part of the channel and that is why it is first learned and then used to rectify erroneous channel measurements as shown in Fig.3.
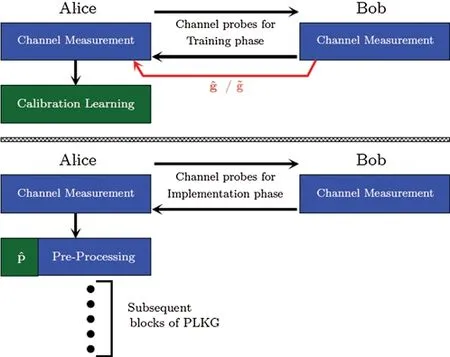
Figure 3:Relative calibration phases.(a) Training phase which uses calibration learning algorithms to obtain (b) implementation phase which uses for compensating the imperfections
3 Relative Calibration through Deconvolution Techniques
To compensate the time-invariant filter imperfection,relative calibration can be performed using the deconvolution techniques.In this section,the deconvolution is performed using the TLS and the STLS as discussed in Subsection 3.1 and Subsection 3.2.
3.1 Deconvolution by TLS
Let us assume that the forward and reverse channel coefficients at kth channel measurement are real,finite-valued and defined asandwherehki∈RL′,and j ∈{1,...,L}.Here L′,L are the filter lengths and to ensure that the Toeplitz matrix is a square matrix,L′has to have an odd value.Thus,a relation between L and L′can be formulated as L=(L′+1)/2.The calibration vector is defined asp≜[pl,...,pL]T∈RL.The matrix H in (3) is a square matrix of the Toeplitz structure [26].The kth measurement is represented asHk.
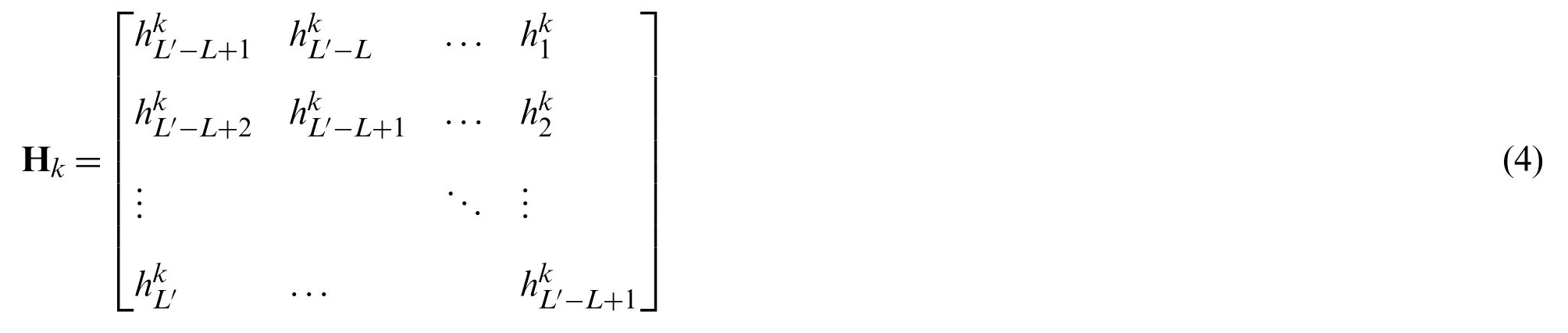
It is assumed thathkandgkare affected only by the estimation errors,where the estimated calibration vector p can be obtained using singular value decomposition (SVD) method [29].
3.2 Deconvolution by STLS
For a more realistic approach to address the problem of deconvolution,we assume that both gkand hkare noisy (denoted with a tilde).This modifies the problem given in Eq.(3) as:

Eq.(5) includesαkandβkare the error correction terms forandrespectively.The error correction terms are also structured in the case of STLS which is not the case with TLS and it improves the optimization process.To maintain the symmetry of the equation,αkis transformed into the Toeplitz matrix as well which is denoted asEk.
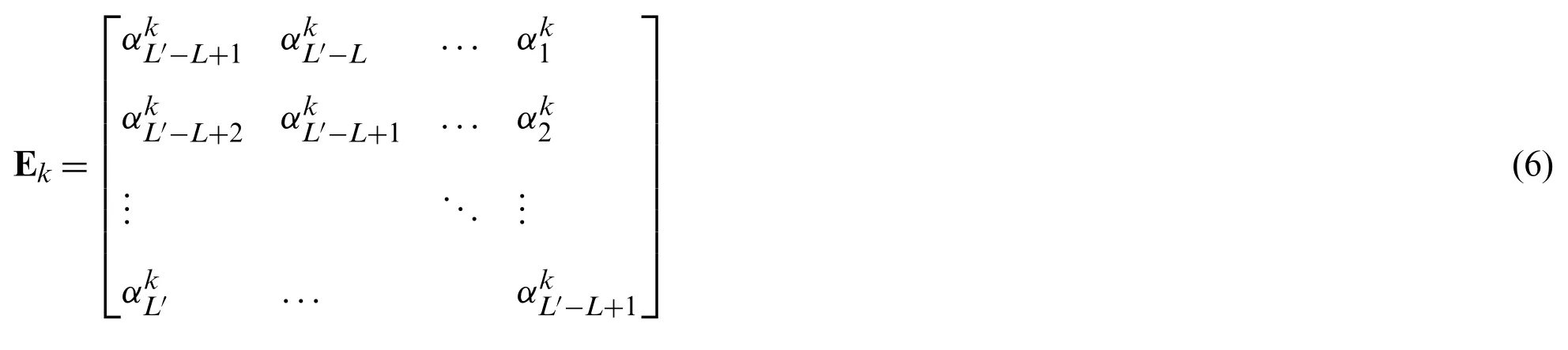
As the noise is Gaussian i.i.d (independent and identically distributed),Eq.(5) can be solved by using Maximum Likelihood (ML) method [30].The Gauss-Newton method [31]is chosen for the ML implementation.In addition,ML optimizes the parameter vector p by minimizing the vector (αTk αk+βTk βk) in an iterative process.The process of ML is an exhaustive search as it requires much more time than TLS method which is an oversimplified approach.Although STLS is a slower process than TLS,the quality of the p from STLS is far better than TLS,which in turn gives improved calibration.Until now,we have considered a single channel measurement.The assumption can be extended to multiple channel measurements by concatenating successive kth measurements ofandrespectively.A comprehensive equation considering all channel measurements can be given as:

andk=1,...,Kdenotes the number of training probes.Ecandmatrices have dimensions[(L′−L+ 1)×K(L′−L+ 1)].Again,Ecis a Toeplitz matrix ofαwhich is given byα≜[26].Similarly,is a single vector that denotes the error correction terms for concatenated[26].Eq.(7) is subjected to the input of the constraint optimization algorithm and an optimizedis estimated.The matrix or vector with subscript “c” is generated within the algorithm.
Relative calibration is performed in two step fashion as depicted in Fig.3.The details of which are given as following:
3.2.1 Training Phase
In this phase,Alice and Bob learn the channel imperfections by sending pilot signals to each other.The channel coefficients from Alice to Bob and Bob to Alice are storedin and,respectively,depending upon the coefficients’nature.Since calibration is performed on Alice side in our case,has been sent from Bob to Alice.By doing so,the method of deconvolution can be applied to estimateusing any of the above-mentioned methods.
3.2.2 Implementation Phase
In this phase,Eq.(3) is then used to obtain estimated forward channel measurementsby convolving the estimatedwith H.
4 Deconvolution Using Circulant Structure
The limitations of TLS and STLS depend mainly on the structure of H which is Toeplitz,as shown in Eq.(3).However,we can manipulate the performance by using different structure for H.The circulant matrix can be an effective candidate instead Toeplitz matrix.The circulant matrix is defined as a modified Toeplitz matrix which is created by rotating each column or row by one element relative to preceding row or column.In our case,we have rotated a column vector to generate the circulant matrix.The comparison between the circulant matrix and Toeplitz matrix is as following:
4.1 Advantages of Circulant over Toeplitz
In the case of Eq.(3),the number of elements in the matrix H is of great importance.We have to infer the calibration vector p by using channel coefficients from g and H.For calculating more accurate value of p,the number of channel coefficients should be higher in number.Since the circulant matrix is created by using only one vector,a large matrix can be created by using same number of channel coefficients compared to the Toeplitz matrix.Generally,a Toeplitz is defined by two vectors one for row and one for column,the channel coefficient vector h has to split in two further in order to fulfill the condition of being a Toeplitz matrix.
Let us assume we have a vector s=[a,b,c,d,e]and this has to be transformed into both Toeplitz and circulant matrices.
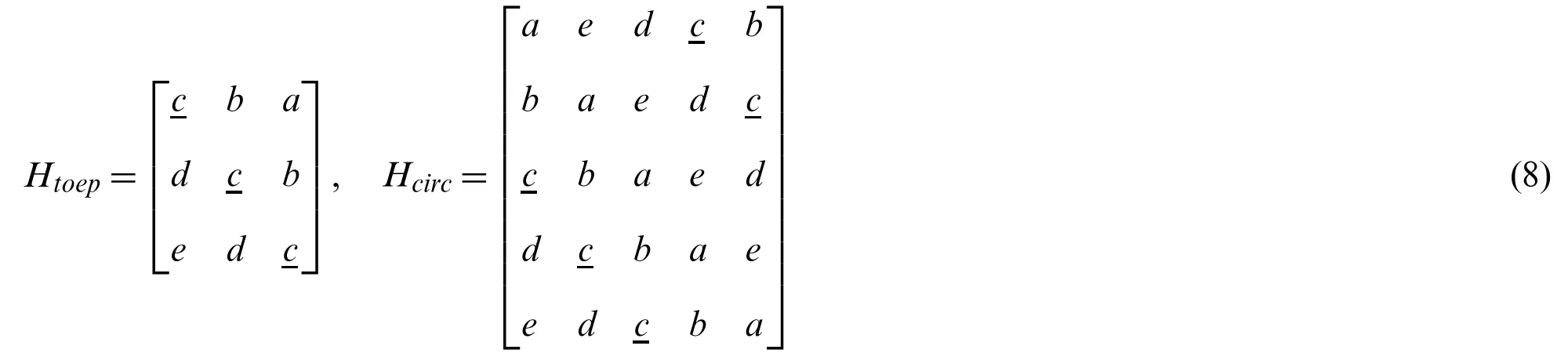
The vectors results in 3×3 and 5×5 matrices as shown in Eq.(8).If every element of this vector is considered as one unit of information then Fig.4 illustrates how many times an information can be re-used in both types.It clearly shows us that maximum information of circulant is nearly double of what the Toeplitz can achieve (For example displayed in Eq.(8) as the recurring underlined “c”).This gives an edge to circulant over Toeplitz structure.A redundant matrix can increase complexity for circulant structure compared to Toeplitz structure.This happens only if we use SVD for the deconvolution of both,however the results would definitely be better in circulant because of the higher information-reuse.Instead,if Toeplitz structure is used in STLS deconvolution,its complexity also increases because of exhaustive iterations required for MLE execution.Thus,a comparison between the circulant structure using SVD for deconvolution and Toeplitz structure using STLS for deconvolution can be considered fair for the same vector s.
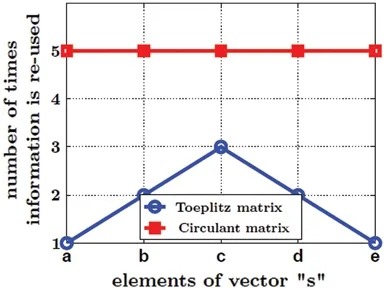
Figure 4:Comparison of the Toeplitz and the circulant matrices’re-use factor
4.2 Deconvolution
Recalling Eq.(3) for the deconvolution through circulant,the forward and reverse channel coefficients can now be given asandwhereas the calibration vector is defined asp≜[p1,...,pL]T∈RL.Note that contrary to Toeplitz,all vectors here are equal in length.This provides the basis for more information re-use.The circulant matrix created byhkwould then be:

While using circulant transformation for H in Eq.(3),the calibration vector p can be easily estimated by using SVD and referred as.This makes it very efficient and less complex to implement.In simple words,circulant deconvolution can be deemed as a scheme that is as efficient as STLS and as simple as TLS.It breaks the trade-off need between STLS and TLS.
5 Simulation
The linear model in Fig.2 is simulated in this section and results are presented for the validation.The simulation environment used here is devised by characterizing the theoretical equations and system model in MATLAB.Fig.5 shows a prototypical model which is used for simulation purpose.The motivation behind using this is to simplify our original model given the fact that filter imperfections can also be monitored by using single filter per chain.
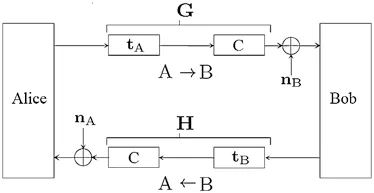
Figure 5:The simplified model for simulation environment
The parameters used for the simulation are shown in Tab.1.Given the maximum length of the filter is N=30,where N=L 0 in the case of Toeplitz (STLS) and N=L in the case of circulant.
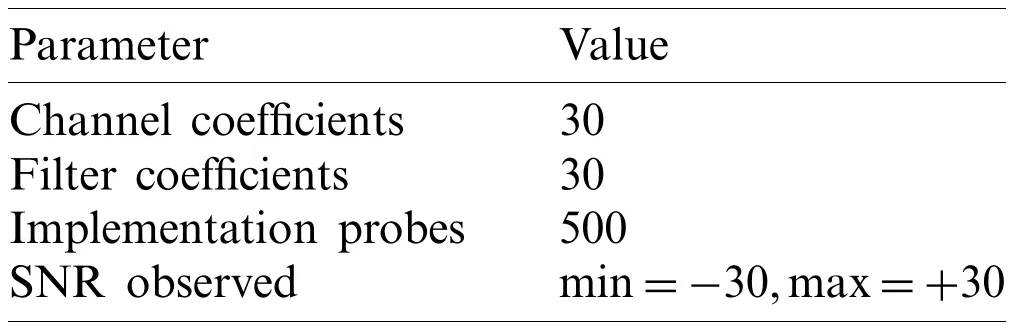
Table 1:The simulation parameters
In general,the filter responses can be complicated but to keep our assumption simple,tAandtBare modeled as sin(θ) and sin(2θ) respectively,whereθ∈[0,2π].The channel C is modeled as Rayleigh distributed fading channel.Contrary to [26],only absolute value of channel coefficients is utilized.The performance of the system is evaluated by comparing the correlation between H and g relative to H and.Each simulation has been run for 100 observations and averaged out for a steady response.Fig.6a shows the SNR versus correlation graph which contrasts the correlation of channel estimates before calibration and after calibration over a wide-range of SNR.Negligible correlation exists in extremely low SNR regions showing the limitation of relative calibration schemes.The reason for this limitation is the noise dominance in the channel coefficient values which does not allow calibration to work properly.However,after a certain SNR,the correlation between channel coefficients of either station becomes visible and it keeps improving from then on.This improvement is visualized in Fig.6b for STLS and circulant deconvolution schemes.Fig.6b is a measure of percentage improvement in correlation at any given SNR value.
It can be observed that the circulant performs slightly better in low SNR regions and achieves maximum at 0 dB.The decrease in percentage for both methods in Fig.6b attributes to the improvement of uncalibrated curve in the positive SNR regions,shown in Fig.6a.Since there is slight chance for an enhancement,the relative percentage in Fig.6b decreases and saturates to a single value.The saturation at 10% shows the maximum possible increment which is clearly visible in Fig.6a.We can observe that the correlation is increasing from 0.88 to 0.98 on 30 dB SNR which translates to 10% increment.Another difference between the two methods is their execution time in terms of the training phase of calibration.The time of training phase is imperceivable to the user or the system in general.Less time it takes to determine the calibration,better would be the system performance.That is why it is an important factor for Physical Security (PHYSEC) systems.Although the execution time of any method greatly depends upon the processing speed of the system and chosen simulation parameters,the comparison between STLS and circulant deconvolution methods is performed by keeping all those factors constant.Fig.7 depicts such a contrast and is a rather logical comparison then an exact relation between the two methods.As mentioned earlier,an average of 100 observations are taken for each method and their execution times in seconds are recorded by means of MATLAB’s clock command.It is evident that the circulant deconvolution utilizes nearly quarter of the time to provide almost same level of performance as STLS deconvolution,hence it can be regarded as more efficient scheme in terms of relative calibration.
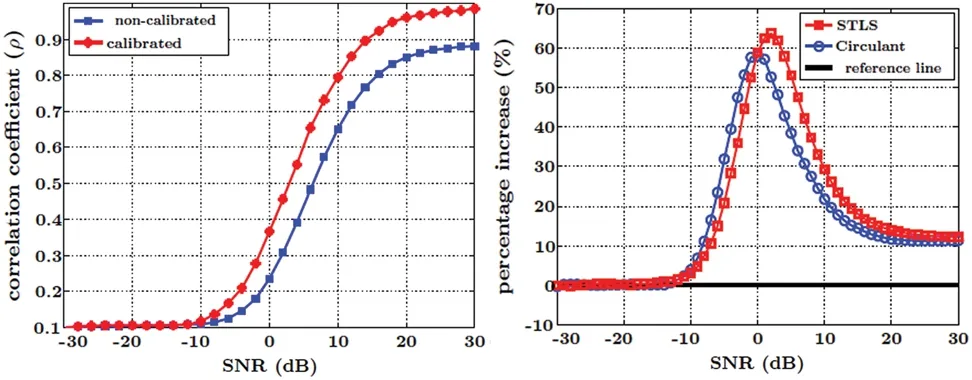
Figure 6:Comparison of STLS and Circulant (a) SNR vs. correlation coefficient graph which shows the effect of calibration on the system (b) shows the percentage improvement in the system performance at different SNR
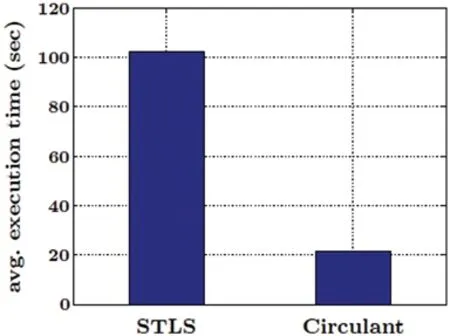
Figure 7:A comparison of average execution time of deconvolution through STLS and Circulant methods
6 Conclusion
The deployment of relative calibration has introduced as an enhancement in terms of reciprocity in the PLKG architecture which has a major influence in securing communication between nodes.The deconvolution method is proposed in order to implement the relative calibration with less computational cost in comparison to the state-of-the-art methods.Existing deconvolution methods like TLS and STLS are implemented and discussed for comparative purpose.STLS being more efficient than TLS in terms of quality,is used to perform deconvolution however due to its higher computational cost as a trade-off to quality,the circulant deconvolution is proposed as an alternate solution.In this context,a comprehensive comparison between the two methods is also presented,highlighting the reasons and motivation to use circulant deconvolution.It is to be concluded that the circulant deconvolution replicates the performance of STLS even with less computational cost.The simulation results of the proposed method also validate that secure communication is possible by adapting the circulant deconvolution within wireless systems having ultra-low latency including 5G and IoTs systems due to its less computational cost.The proposed circulant deconvolution is recommended as a better scheme in comparison to the state-of-the-art techniques and this is clearly validated by the simulation results.As an immediate succession,the relative calibration is to be implemented over complete PLKG chain and its effect on the created keys should be observed in real time scenarios.
Funding Statement:The authors received no specific funding for this study.
Conflicts of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.Although APC is to be funded by author’s institute under predefined standard policy.
杂志排行
Computers Materials&Continua的其它文章
- Recognition and Detection of Diabetic Retinopathy Using Densenet-65 Based Faster-RCNN
- Adaptation of Vehicular Ad hoc Network Clustering Protocol for Smart Transportation
- Computational Microfluidic Channel for Separation of Escherichia coli from Blood-Cells
- A Fractal-Fractional Model for the MHD Flow of Casson Fluid in a Channel
- Simulation,Modeling,and Optimization of Intelligent Kidney Disease Predication Empowered with Computational Intelligence Approaches
- Prediction of Time Series Empowered with a Novel SREKRLS Algorithm
