A Survey on Smart Agriculture: Development Modes, Technologies, and Security and Privacy Challenges
2021-04-22XingYangStudentMemberIEEELeiShuSeniorMemberIEEEJianingChenMohamedAmineFerragJunWuMemberIEEEEdmondNurellariMemberIEEEandKaiHuang
Xing Yang, Student Member, IEEE, Lei Shu, Senior Member, IEEE, Jianing Chen, Mohamed Amine Ferrag,Jun Wu, Member, IEEE, Edmond Nurellari, Member, IEEE, and Kai Huang
Abstract—With the deep combination of both modern information technology and traditional agriculture, the era of agriculture 4.0, which takes the form of smart agriculture,has come. Smart agriculture provides solutions for agricultural intelligence and automation.However,information security issues cannot be ignored with the development of agriculture brought by modern information technology. In this paper, three typical development modes of smart agriculture (precision agriculture,facility agriculture, and order agriculture) are presented. Then,7 key technologies and 11 key applications are derived from the above modes.Based on the above technologies and applications,6 security and privacy countermeasures (authentication and access control, privacy-preserving, blockchain-based solutions for data integrity, cryptography and key management, physical countermeasures, and intrusion detection systems) are summarized and discussed. Moreover, the security challenges of smart agriculture are analyzed and organized into two aspects: 1) agricultural production,and 2)information technology.Most current research projects have not taken agricultural equipment as potential security threats. Therefore, we did some additional experiments based on solar insecticidal lamps Internet of Things, and the results indicate that agricultural equipment has an impact on agricultural security. Finally, more technologies (5 G communication, fog computing, Internet of Everything, renewable energy management system, software defined network, virtual reality, augmented reality, and cyber security datasets for smart agriculture) are described as the future research directions of smart agriculture.
I. INTRODUCTION
AGRICULTURE is the primary industry in the world,and it plays an important role in social stability and economic development [1]. Overcoming the contradiction between the population explosion and the limited grain yield is a challenge that motivates an increasing number of studies on smart agriculture. The development of agriculture is based on both the improvement in productivity and the restrictions of the era, and the progress of science and technology drives the revolution of agriculture [2]. Fig.1 is used to help readers understand the characteristics and confronted issues of agriculture development(from Agriculture 1.0 to Agriculture 4.0).
• Agriculture 1.0: the traditional agricultural era (between 1784 and around 1870) dominated by human and animal resources, the main issue of agriculture was the low efficiency of operation.
• Agriculture 2.0: the era of mechanized agriculture (in the 20th century), the main issue was the inefficient use of resources.
• Agriculture 3.0: the era of high-speed development of automatic agriculture (between 1992 to 2017), the main issue was the low level of intelligence.
• Agriculture 4.0: the era of smart agriculture (which is characterized by unmanned operations, begin at 2017) is mainly marked by the use of modern information technology to both serve agriculture and develop it intelligently.
Smart agriculture is a new agricultural production mode,that contributes to agricultural information perception,quantitative decision-making, intelligent control, precise investment, and personalized service through the deep integration of modern information technologies, e.g.,the internet, Internet of Things (IoT), big data, cloud computing, and Artificial Intelligence (AI) with agriculture.In short, the new mode is a smart agricultural solution that combines agriculture with modern information technology. Although modern information technology brings new opportunities to the development of agricultural production, it also creates great demands and challenges to security and privacy in the field of smart agriculture. For instance, both intellectual and unmanned operations are the development goals of smart agriculture, whose characteristics not only increase productivity but also increase the security risks of equipment and data.

Fig.1. Characteristics and confronted issues of agriculture development (from Agriculture 1.0 to Agriculture 4.0).
A. Motivation for the Article
This article has three motivational factors:
1) Smart agriculture is an emerging paradigm that extends information technology to traditional agriculture, and it has the potential as the development trend of agriculture due to the limited productivity of traditional agriculture and the wide application of information technology. Therefore, it is very important to summarize the existing production mode and specific researches.
2) Although smart agriculture has been extensively studied,little work has been done on the analysis of security challenges compared with industrial security solutions.
3) There is a great difference between urban (industry)conditions and rural(agriculture)conditions,as shown in Table I. It indicates that security countermeasures based on urban conditions may not suitable for rural conditions. Therefore, it is critical to analyze the characteristics of security issues under the smart agriculture scenarios.
For the above factors, this article aims to present a survey of the security topics that arise from smart agriculture, which naturally leads to a large number of open research issues.
B. Related Works
1) Works related to smart agriculture: Some of the articles related to smart agriculture and its security issues are listed in Table III. In [3], typical applications of cloud computing technology in agricultural IoT were discussed, and a simple IoT agriculture model was addressed with a wireless network.Gondchawar et al. sought to make agriculture smart by using automation and IoT technology,e.g.,smart GPS-based remotecontrolled robot, smart irrigation with decision-making system, and smart warehouse management [4]. Antonacci et al.discussed the application of nanostructured sensors to support farmers in accessing fast and accurate analyses [5]. In [6],IoT deployment challenges and specific issues were discussed.In addition, the wireless communication technologies that are associated with agricultural applications were analyzed.Elijah et al. depicted the applications of IoT and data analytics in agriculture and analyzed the benefits of these applications[7]. Khanna et al. highlighted the applications of IoT in precision agriculture [8]. In [9], the research initiatives and scientific literature of smart agriculture were discussed in detail. The applications of big data in smart agriculture were discussed in[10],especially in terms of the food supply chain.In addition, the study mentioned that ensuring privacy and security is one of the greatest challenges of big data. Bacco et al. presented ground and aerial vehicles, along with the vision systems of UAVs in smart agriculture scenarios [11].To identify the differences between UAV missions, the study also proposed a simple taxonomy. In [12] and [13], climatesmart agriculture was mainly used in precision agriculture by monitoring and predicting meteorological factors and environmental conditions. Various applications, services, and sensors based on IoT devices and communications techniques in smart agriculture were introduced in [14]. In [3]−[10], these studies also mentioned security issues without further discussion.
2) Works related to security issues in smart agriculture:Security issues in smart agriculture have been studied in[15]−[20], among them privacy-oriented blockchain-based solutions were introduced in [15], [16] proposed a holistic study on security and privacy in a smart agriculture ecosystem,and [17] studied the cyber security in smart agriculture. A prediction model framework for cyber-attacks in precision agriculture was presented in [18], and it is suggested that anomaly detection is needed to eliminate false alarms.Furthermore, Haseeb et al. proposed a security mechanism based on symmetric data encryption in agricultural sensors and a robust transmission strategy for IoT-based smart agriculture applications [19]. Moreover, Farooq et al. made a brief overview of security requirements, security challenges,stack challenges, thread model, and attack taxonomy on smart agriculture without further discussion about them [20].Although the above surveys reviewed various smart agriculture applications and described security issues from the aspect of various information technologies, there is little discussion about security challenges in agricultural production.

TABLE I COMPARISON OF SECURITY ISSUES BETWEEN URBAN(INDUSTRY) AND RURAL(AGRICULTURE)
C. Contributions
The contributions of this paper are listed as follows.
1) The development status of smart agriculture is summarized and classified into three typical development modes:precision agriculture,facility agriculture,and order agriculture.Furthermore, 7 key technologies and 11 key applications are discussed.
2)Security and privacy countermeasures are summarized as(1) authentication and access control, (2) privacy-preserving,(3) blockchain-based solutions for data integrity, (4) cryptography and key management,(5)physical countermeasures,and(6) intrusion detection systems.
3) Potential security challenges of smart agriculture are highlighted and divided into two aspects: (1) agricultural production and (2) information technology.
4)Agricultural equipment will also affect the security strategy. For instance, it is suggested that high voltage discharge interference of Solar Insecticidal Lamps Internet of Things(SIL-IoT) should be considered as attacks or have an impact on security strategy. In [25], [26], we did some experiments and the results indicate that the interference of high voltage discharge affects data transmission. Then, we found that the interference has an impact on data acquisition from the results of our additional experiments in this paper. Furthermore, the electromagnetic interference of photovoltaic power generation may also be potential attacks in photovoltaic agricultural Internet of Things.
The remaining part of this paper is structured as Fig.2:Section II describes the development modes of smart agriculture. Section III lists some key technologies and applications in smart agriculture. Section IV summaries the security and privacy countermeasures for smart agriculture. Section V discusses the security challenges of smart agriculture. Section VI summarizes the future trends and opportunities of smart agriculture and Section VII concludes the article. To help readers understand this paper, acronyms found in this paper are shown in Table II.
II. DEVELOPMENT MODES OF SMART AGRICULTURE
At present, smart agriculture is the common goal of agricultural development in all countries worldwide. The world’s typical smart agriculture development modes are divided into three types, as shown in Table IV. Considering the characteristics of the vast territory and uneven population distribution in China, the development modes need to be modified before they are applied to the different regions of China.These modes have a strong impact on promoting production management,industrial operation, and unmanned development of agriculture. Fig.3 shows three types of development modes and their characteristics in smart agriculture.
A. Precision Agriculture
According to the environmental conditions of each operation unit in the field and the temporal-spatial differences of crop yield, various agronomic measures should be carefully and accurately applied to optimize the quantity,quality and timing of water, fertilizer, seeds, pesticides, etc., so as to obtain the highest yield and maximum economic benefits, and protect the agricultural ecological environment and protect the agricultural natural resources.Precision agriculture is an advanced technology to improve crop yields, in which Wireless Sensor Networks (WSNs) is the main developmental driving force[30].The combination of WSNs and agriculture can effectively reduce the potential risks of the production process and help farmers make favorable decisions by deploying a large number of low-power,multi-function,wireless communication sensors on farmland to collect relevant data throughout the agricultural production process(e.g.,environmental data,crop growth data,and livestock health data) [31].

Fig.2. Organization of this paper. Development modes, 7 key technologies, and 11 applications of smart agriculture are summarized in Section II and III,which contribute to discuss security issues in Section IV, V and VI.
The modern information technology used in precision agriculture is mainly “3S”, which includes remote sensing technology (RS), geographic information system (GIS), and global positioning system (GPS) [15]. Various types of data(e.g., GPS data, GIS data, RS data), as well as AI methods,are used in precision agriculture to deduce the crop growth process and propose crop production management in an expert decision system, which is different from the traditional agricultural production management methods based on subjective experience. The functions of precision agriculture include:
• Reducing environmental pollution by reasonably controlling the pesticide dosage;
• Reducing the waste of resources by improving the efficiency of agricultural irrigation;
• Enhancing the land utilization by improving the ecological environment of farmland;
• Improving the yield and quality of agricultural products by analyzing the law of crop growth and thereby maintaining the best crop growth conditions.
The main security threats in precision agriculture are:
• Sensors being vulnerable to eavesdrop, steal and inject malicious data due to signal loss from their long-distance of deployment strategy and harsh environment;
• Location tampering of outdoor sensors and actors resulting in agricultural facilities failure and abnormal operation.
B. Facility Agriculture
Facility agriculture has the goal of good quality and high yield,and this agricultural production mode is in the industrial style. This type of agriculture is a remarkable sign in the development of modern agriculture, and it is characterized by high demand for capital, technology, and labor. Using engineering technology,facility agriculture can provide man-made conditions suitable for crop growth, and facility protection; it can also remove the environmental restrictions on agricultural production and improve the efficiency of automatic production.Compared with traditional agriculture,facility agriculture can meet the multi-level consumption demands derived from societal development without the constraints of the natural environment and seasonal agricultural products [32].
Moreover, facility agriculture, facility horticulture, and facility breeding share a similar mode of production, and all of them are outfitted with the technologies,i.e.,biotechnology,engineering technology,meteorology technology,IoT technology, and computer technology. The cores of the above three production modes consist of prediction models and decisionmaking management systems that are based on historical data,e.g.,environmental data,crop growth data under different conditions,and crop growth data with different types of genes.Considering the different environmental requirements of crops,elements in the facility(e.g.,temperature,air pressure,relative humidity, light intensity, and fertilizer application rate) are monitored and controlled in real time to ensure crops grow in the most favorable conditions.The most typical example is the intelligent greenhouse. The differences between specific studies(i.e.,greenhouse,aquaculture,plant factory and poultry and livestock breeding) include different environmental elements,different sensor devices, and specific computer-controlled programs. The functions of facility agriculture include:

TABLE II ACRONYMS FOUND IN THIS PAPER
• Ensuring sustainable and efficient production within a completely closed environment with the function of intelligent control;
• Ensuring agricultural production against the restriction of geographical conditions;
• Shortening the production cycle of agricultural products;
• Improving the quality and yield of products.
As a combination of both agriculture and industry, facility agriculture, will be the development trend of agriculture, and it has become a pillar industry in developed countries e.g.,the U.S., the Netherlands, and Japan. Due to the characteristics of centralized administration and automatic management, facility agriculture is vulnerable to control system intrusion and unauthorized access.
C. Order Agriculture
With the advancement of urbanization in China, urban development is rapid, while rural development is slow. There are three main problems that hamper rural development:
• A weak agricultural foundation,
• Hidden dangers in the quality and security of agricultural products,
• Information island transactions within agricultural products [33].
It implies that on its own, advanced agricultural production technologies are not sufficient,and it helps to create value only when it meets an enabling market opportunity[34].Therefore,order agriculture has achieved an effective business model by outsourcing the production demand for agricultural products in advance,which can reduce the planting and breeding risks,and avoid blind production [29]. Besides, to ensure food security and manage agricultural products, a traceability system which makes consumers obtain the appropriate information agricultural productions is applied to agricultural product supply chain. Furthermore, agricultural product supply chain plays a vital role in the market supervision of agricultural products trade. The functions of agricultural product supply chain include:
• Improving the transparency of agricultural product information by modern e-commerce and blockchain technology;
• Eliminating the information island of an agricultural product transaction [35];
• Reducing the information asymmetry between farmers and suppliers;
• Reducing the imbalance between the supply of and demand for agricultural products.
For instance,Leng et al.[36]proposed a public agricultural supply chain system based on double chain architecture to provide a security guarantee mechanism for the public platform and improve the utilization of business resources.In[37],an agricultural provenance system based on blockchain was presented to solve the trust crisis in product supply chain.
D. Summary
Precision agriculture, facility agriculture, and order agriculture are the main development modes of smart agriculture,which combine traditional agricultural forms (outdoor),emerging agricultural forms(indoor),and agricultural products industry chain with emerging technologies. Various applications of smart agriculture based on the above developmentmodes contribute to the improvement of grain products and the quality of agricultural products, the reduction of agricultural production costs,and the transparency of agricultural products trading.
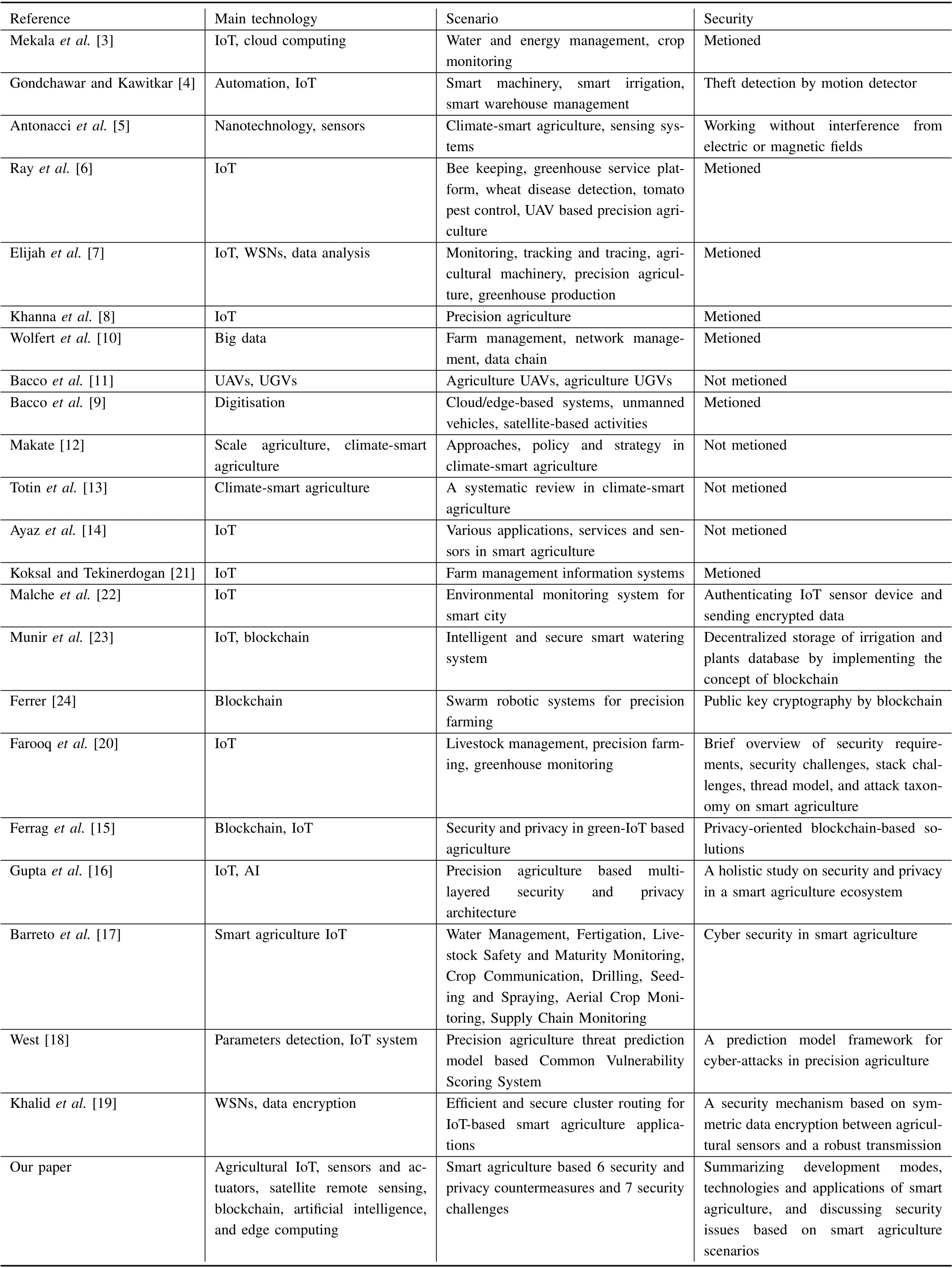
TABLE III RELATED WORKS

Fig.3. Research fields of smart agriculture based on 1) precision agriculture, 2) facility agriculture, and 3) order agriculture.

TABLE IV THREE TYPICAL DEVELOPMENT MODES OF SMART AGRICULTURE
III. KEY TECHNOLOGIES AND APPLICATIONS IN SMART AGRICULTURE
In this section, 7 key technologies and 11 key applications in smart agriculture based on the three development modes mentioned in Section II are introduced. The arrangement of this section is shown in Fig.2. Agricultural IoT (key technology, introduced in Subsection A) is the information carrier of the other technologies and applications in smart agriculture. Seven Typical applications of it (introduced in Subsection B) are: 1) IoT in field agriculture, 2) IoT in aquaculture,3)IoT in poultry and livestock breeding,4)IoT in greenhouse, 5) plant factory, 6) photovoltaic agricultural IoT,and 7) SIL-IoT. Besides, agricultural IoT has the functions of data acquisition, data transmission, data storage, and data analysis.According to the four functions,six key technologies are:1)sensors and actuators,and 2)agriculture satellite remote sensing (data acquisition technologies, introduced in Subsection C); 3) various data transmission technologies (listed in Table V); 4) agriculture blockchain (data storage technology,introduced in Subsection E); 5) agriculture AI and 6) agriculture edge computing(data analysis technologies,introduced in Subsection F). And four key applications are: 1) agriculture crowd sensing, and 2) plant phenotype information system(data acquisition applications, introduced in Subsection D);3) agriculture UAV, and 4) driverless tractor (data analysis applications, introduced in Subsection G).
A. Agricultural Internet of Things Technology
Agricultural IoT is a key technology in smart agriculture which makes it possible to quantify the environmental factors,crop growth, and process of agricultural production by automatic processing, analysis, and access [38]. According to the definition of IoT, IoT architecture can be divided intoperception layer, transmission layer, and application layer, as shown in Fig.4.

TABLE V COMPARISON OF THE EXISTING WIRELESS COMMUNICATION TECHNOLOGIES
In the perception layer, various types of sensors are used to collect both field environment information and crop growth information, and these sensors are also used to describe the state of the environment [39].
The transmission layer includes all types of network communication protocols in which the data collected by the perception layer can be transmitted to the application layer based on these protocols. Various wireless communication technologies and their parameters are listed in Table V (adapted from [6], [7], [38], [40], [41], and Wikipedia). Due to the characteristics of the large-scale and outdoor environment in precision agriculture, technologies with low transmission range (e.g., WiFi and Thread) and high energy consumption(e.g., WiFi) cannot apply to precision agriculture. In addition,low data rate technologies (e.g., 2 G(GSM), Z-Wave, LoRa)are not applicable for some technologies with high throughput data transmission (e.g., plant phenotype information system).
The application layer plays a vital role in agriculture, and it can be the cloud-based (i.e., multiple servers) and localbased (i.e., edge computing based on the gateway) system.The application layer consists of the following functions:
• Data storage, e.g., cloud-based platform and Hadoop distributed file system for quick and safe accessing to data [42];
• Data management, e.g., Supervisory Control And Data Acquisition(SCADA)for monitoring real-time data[18];
• Data analytics,e.g.,decision-making system,yield models and plant instructions for automatic control in agricultural production [43];
• Data marketing, e.g., data visualization, traceability system of agricultural products for ownership, privacy,new business models [44].

Fig.4. Various technologies and applications based on IoT architecture.
B. Agricultural Internet of Things Application
1) Internet of Things in field agriculture: Field crops mainly refer to such products as wheat, rice, and corn, which are of great significance to ensuring grain security [45].In field agriculture, the main research topics include field resource management and agricultural condition monitoring,and IoT plays an important role in both of these areas. Based on the characteristics of various regions in field agriculture,it is difficult to apply wired transmission in that setting.Therefore, WSNs technology is mainly used instead of wired transmission in field agriculture [46]. After analyzing the data transmitted by the transmission layer,the application layer can be expanded into a variety of digital tools that benefit the agricultural production e.g., decision support systems, expert systems, and cloud data storage.
Although IoT technology improves the efficiency and quality of field agricultural production,it also entails some security problems (e.g., agricultural facility damage).
2) Internet of Things in aquaculture: China has become the largest aquaculture country with aquaculture production that accounts for approximately two-thirds of the world’s production[47].Currently,aquaculture is transferred from traditional extensive aquaculture to industrialized and precise aquaculture.IoT in aquaculture is a symbol of the transformation of aquaculture,it is an intelligent aquaculture system based on WSNs that collects environmental data for real-time monitoring,early warning analysis, and auxiliary decision-making [48]. Special facilities, e.g., water quality parameter sensors, underwater robots, underwater cameras, and meteorological stations, are applied to monitor environment elements such as the water temperature,dissolved oxygen,pH value,salinity,and chloride in real time. In addition, actuators are used to adjust the water quality of the culture pond to ensure the most suitable environmental conditions for the growth of aquatic organisms[49].
The differences between IoT in aquaculture and IoT in field agriculture include not only the monitoring objects but also the complex aquaculture environment and various influencing factors during the growth of aquatic organisms. Thus, it is difficult to implement accurate and effective monitoring,detection, and optimization management [50].
3) Internet of Things in poultry and livestock breeding:Compared with the other forms of agricultural production,poultry and livestock breeding have higher production scales and requirements in terms of the technology,facility,and funds[51]. IoT in poultry and livestock breeding is based on both indoor conditions and outdoor environment,as shown in Fig.5.Indoor conditions include facilities e.g., environmental control equipment (to ensure environmental stability), automatic feeding equipment(to ensure forage supply),video monitoring equipment (to monitor animal behavior). In addition, to track the growth status of each animal under indoor conditions and outdoor environment and increase the traceability of meat products, Radio Frequency Identification (RFID) technology is generally used to set the electronic identification, assign a serial number to each animal, and simplify data storage and tracing [52]. Hence, the advantages of monitoring, identification, and positioning of animals through RFID technology are:
• Effectively strengthening the detection of the breeding environment;
• Preventing the spread of various epidemic diseases among animals;
• Ensuring the price stability of meat products [53].
For instance, the recent sharp rise in the price of pork in China, which resulted from African swine fever in 2019,will not happen again if IoT technology is well applied in poultry and livestock breeding.Currently,important studies of IoT in poultry and livestock breeding include the electronic identification of animals, database management of animal information, the quality control and safety traceability of product, and auxiliary disease diagnosis using AI technology[54].Due to the high production value of poultry and livestock breeding, high data sensitivity is required for the decisionmaking system.Failures in sensors,links,and decision-making systems may lead to irreparable economic losses to farmers.

Fig.5. Indoor conditions and outdoor environment of poultry and livestock breeding,e.g.,(a)indoor conditions for chicken farm,(b)outdoor environment for sheep breeding, (c) indoor conditions for hog farm, and (d) outdoor environment for cattle breeding.
4) Internet of Things in greenhouse: Through the environmental control system, IoT in a greenhouse provides a closed growing environment to ensure the healthy growth of crops without the restrictions of an external environment,which helps improve the yield and quality of crops [55] .Agriculture production of IoT in greenhouse can be divided into the following steps:
• Collecting the environmental data through sensors, including the temperature, relative humidity, carbon dioxide concentration, light intensity, soil temperature, soil humidity, and pH value;
• Uploading the collected data to the control system through signal transmission facilities;
• Modeling and analyzing the heterogeneous data through the prediction model in the control system [56].
Through the above three steps,the facilities in a greenhouse,e.g.,the sprinkler irrigation facility,drip irrigation facility,and temperature regulation facility, can execute commands intelligently and automatically to maintain steady environmental conditions.
5) Plant factory: Due to the growing scarcity of both arable land and water sources, a type of low-consumption,environmental-protection, high-yield, and safe agricultural production mode has emerged as the most suitable mode for agriculture. The plant factory is one of the representative technologies, which is a reflection of the transformation from traditional agriculture to modern industry [57]. The plant factory’s characteristics include:
• No limitation due to the environmental conditions;
• Less pollution;
• Less waste of resources;
• A controllable production cycle,these features ensure the agriculture production even with a deterioration of the ecological environment [58].
Similar to the production mode of IoT in a greenhouse, a plant factory cultivates crops under the controlled conditions of factors such as the temperature, humidity, carbon dioxide concentration, and light intensity. The differences are that the plant factory has:
• Higher mechanization;
• Higher automation;
• More hydroponics;
• A higher space utilization rate;
• Proximity to a city;
• A closed and clean environment.
At present,plant factories are mainly distributed among East Asia, Europe, and the U.S., and artificial light plant factories are being developed rapidly in Japan. Due to the reduction of arable land, frequent natural disasters, and the shortage of rural labor, agriculture is also trending to plant factories in China [59]. The key technologies of the plant factory are as follows:
• Three-dimensional and multi-layer soilless cultivation technology;
• Artificial lighting luminous technology;
• Intelligent environment control technology;
• Automatic control technology of the plant production space.
The above technologies are associated with the production efficiency and production cost of a plant factory [60]. A plant factory is confronted with the following issues:
• The high cost of the initial construction and maintenance;
• Limited types of crop cultivation;
• A low level of intelligent production;
• Low security and privacy [60].
Because the above issues hinder the development of plant factories, they should gain more attention and emphasis.
6) Photovoltaic agricultural Internet of Things: With the reduction of natural resources and the aggravation of environmental pollution, clean and renewable energy plays an indispensable role in the energy transformation of the world [61]In China,photovoltaic power generation occupies a significant position in new energy power generation, and there is vast potential for its development [62]. In addition, photovoltaic power generation has the advantages of low operation cost,no greenhouse gas emissions, and a low maintenance cost [63].However, the development of photovoltaic power generation is limited by the low energy conversion efficiency, the high correlation with meteorological factors, and the waste of residual power after the grid connection [64], [65]. With the combination of photovoltaic power generation and agricultural IoT, the residual power can be utilized effectively.
Generally, if the actual generation exceeds the demand of the grid,power will be limited to protect the grid,which leads to energy waste. With the application of residual power for agricultural IoT facilities through battery storage, the wasted power and farm operation costs can be effectively reduced.For example,photovoltaic energy was used for the irrigation of farmland,and SolarCoin(similar to Bitcoin)was proposed for energy and water trading[66].In addition,because a large area of land is required for both field agricultural production and photovoltaic power generation, deploying photovoltaic panels over farmland can optimize land usage[67].Moreover,sensors for monitoring field crops can acquire power from a photovoltaic system and monitor photovoltaic power generation facilities [68]. However, this technology also brings some security challenges. For instance, photovoltaic power generation may have a great impact on information transmission and further increase the risk of receiving malicious data.
7) Solar insecticidal lamps Internet of Things: Solar insecticidal lamps (SIL) kill migratory pests by releasing a high voltage pulse current, which contributes to reducing the usage of pesticides [69]. At present, SIL are widely applied in China, for instance, 20000 SIL have been deployed for pest control in Xinyu City, Jiangxi Province, China. With a low level of intelligence, most of the traditional SIL are deployed only for killing pests among the fields. However,pest information cannot be obtained to make forecasts of pests and adjust the work time of insecticidal lamps adaptively.Therefore, the application situation of SIL was investigated and the structure diagram of SIL-IoT node was introduced in [69]. It has been found that the effective killing distance of SIL (SIL deployment radius ≤110 m) [70] is in the valid communication radius of wireless sensor nodes (e.g.,ZigBee, LoRa), as shown in Fig.6. Due to the advantages of SIL-IoT (i.e., pollution-free, high insecticidal efficiency,and easy for scheduling), SIL-IoT will be applied widely for pest prevention and control, as well as the data acquisition of field agriculture. Recently, Yang et al. [70] proposed a node deployment strategy based on partition structure for SILIoT. The node deployment problem is transformed into a secondary allocation problem by using the natural partition structure of farmland, and the problem is solved by genetic algorithm. Under the constraint of ensuring full coverage, this strategy significantly reduces the number of SIL-IoT nodes.In addition, Huang et al. [25], [26] found that high voltage pulse discharge released by SIL has been as an interference to ZigBee-based device in SIL-IoT. It is mentioned that the device in [25], [26] can be used as a method to attack WSNs,leading to the abnormal working state,and it is suggested that the installing space between SIL and ZigBee-based device is at least 25 cm. Moreover, Yang et al. [71] mentioned that the interference will affect fault diagnosis of SIL-IoT and thereby affect the reliability of SIL-IoT.In[71],the characteristics and challenges of fault diagnosis in SIL-IoT are analyzed and it is highlighted that security attacks will lead to the failure of fault diagnosis.

Fig.6. SIL-IoT component and communication diagram. The insecticidal range is smaller than the communication range, which ensures that the SILIoT nodes deployed in the field meet the communication requirements.
Although the application of IoT technology expands the functions of insecticidal lamps and improves their utilization rate, it entails some new security challenges. For example,signal interference is serious when the insecticidal lamp is discharged, and traditional signal transmission security methods may not suitable for this situation.
C. Data Acquisition Technology
Data acquisition is an interface that uses a device to collect data from the outside of the system and input them into the internal system. Data acquisition technology mainly includes:
• RS232,RS485 serial ports for connecting multiple detection instruments to implement automatic data acquisition;
• USB interface for outputting data;
• The wireless communication module for transmit data;
• Various sensors for collecting data and various actuators for maintaining the controlled variable;
• Satellite for obtaining, measuring and processing the related data through the interaction between electromagnetic wave and object.
These technologies can be applied to agriculture crowd sensing and plant phenotype information system,which obtain data from perception module of mobile devices, camera,spectrometer, various weather sensors, etc..
1) Sensors and actuators: Agricultural sensors are mainly used to collect both environmental conditions and crop growth information [39] and then transmit the data to the cloud [38].Various sensors in smart agriculture can be classified into location sensors, photoelectric sensors, mechanical sensors,electrochemical sensors, airflow sensors, and optical sensors,as shown in Table VI (adapted from [5], [7], [72]). These sensors are applied to collect meteorological information(e.g.,temperature, humidity, carbon dioxide concentration), crop information (e.g., crop growth conditions, crop disease), soil information (e.g., tensiometers, soil type, and moisture level of the soil), location information (e.g., precision location of crops), etc..
Then, these information are transmitted to the cloud. If the data collected by the sensor meet certain judgment conditions,actuators will activate or deactivate agricultural equipment.The main actuators in facility agriculture are:
• Irrigation equipment to ensure the sufficient moisture for crop growth;
• Lighting control equipment to ensure the suitable lighting conditions for crop growth;
• Air circulation to ensure the carbon dioxide concentration in closed growth conditions;
• Crop disease control to ensure the healthy growth of the crop.

TABLE VI SENSORS IN SMART AGRICULTURE
2) Agricultural satellite remote sensing: Agricultural satellite remote sensing is a technology that monitors:
• Various types of agricultural systems e.g., field planting and aquaculture;
• The process of agricultural production;
• Multiple elements of agriculture i.e.,production,environment, and ecology information [73].
It is mainly applied to the following fields: area estimation,crop growth monitoring, pest information monitoring, yield prediction, grassland vegetation monitoring, and agricultural resources mapping [74]. Moreover, the trends of agricultural satellite remote sensing development in the world include both joint observation and high spatial-temporal resolution monitoring.
In China, the demand for sky-air-ground-integration in agriculture was proposed in the “Outline of the National Rural Development Plan of Sky-air-ground Digital Agriculture(2018-2025)”. The requirements also include realizing (1) the digitalization of all factors and all production processes, and(2) intelligent dynamic monitoring in field planting, animal husbandry, and related areas [75]. To implement sky-airground-integration, several problems must be solved, e.g.,we need both cooperative observation among satellites, and massive data fusion among satellites, aircraft, UAVs, and surface stations, as shown in Fig.7.

Fig.7. Massive data fusion among satellites, aircraft, UAVs, and surface stations.
D. Data Acquisition Application
1) Agricultural crowd sensing: Crowd sensing employs the functions of perception computing, common measurement,and information sharing by a large number of personal mobile devices (e.g., smartphones and wearable devices) to complete large-scale and complex perception tasks[76].Mobile terminal equipment is used as the basic sensing unit to complete the collection of sensing data through the wireless network.Furthermore,with the combination of the ideas of both mobile perception and crowdsourcing, crowd sensing has the advantages of low cost, strong scalability, and strong mobility. The emphases of crowd sensing are:
• The data processing technology;
• The incentive mechanism;
• The crowd sensing software platform.
To date, crowd sensing has been widely used in intelligent transportation, public security, environmental monitoring, and other applications.It is mainly applied in urban environments,and there have been few applications in rural ones. Due to the increasing proportion of farmers with smartphones and the demands of collecting agricultural data,agricultural crowd sensing has huge potential for data acquisition [77]. For instance,Ginige et al.[78]proposed a mobile-based information system which consists of a smart computing framework, and was studied for farmers to report pest and disease outbreak events. As a new IoT sensing technology, agriculture crowd sensing will inevitably entail a variety of security challenges[79]. For example, a SmartfLAIr system was proposed for an increased resolution of leaf area index and a perturbation based privacy mechanism with Trusted Third Party (TTP)architecture was designed to ensure user privacy [80].
2) Plant phenotype information system: The plant phenotype information system is a technology that quantitatively analyses the interaction effect of both the genotype and the environment on crop products’ quality and other traits. It has the following functions:
• Monitoring the growth of crops by deploying various types of sensors and measuring instruments under Specified conditions [81];
• Analyzing the data from both UAVs and satellite remote sensing to quantify the growth state and yield of crops under different genes and environmental factors;
• Selecting stable and high-yield crop genes and their suitable growth environment.
All the functions are based on abundant plant phenotype information, which is mainly composed of massive images,videos, and text data. To make the data suitable for analytics,the main studies of plant phenotypic information systems are:
• Massive data annotation [82], management [83] and integration [84] (i.e., data annotation, data association and data storage by knowledge graph technology);
• Massive image data analysis [85], [86] (e.g., machine learning, and deep learning algorithms).
Due to the characteristics of interdisciplinary fusion, multiteam cooperation is required for a plant phenotype information system. Hence, Ubbens et al. [87] proposed a deep p
lant phenomics system,which was an easy platform by providing a pre-trained model for plant scientists.In addition,a plant phenotype information system involves various technologies,e.g.,sensor facility,network communication,big data platform,and data processing method, which entails many security issues.
E. Data Storage Technology
Data storage objects include temporary files generated by data stream or information that needs to be searched in the process of processing. At present, the main data storage methods include:
• Direct Attached Storage (DAS), a storage device directly connected to the host system without centralized management solution;
• Network Attached Storage (NAS), a device with data storage function connected to the network;
• Storage Area Network (SAN), a network in which storage devices are connected to each other and connected to a server or group of servers.
Moreover,database is the most commonly used data storage software, which consists of:
• Relational database,the relational model is used to organize data in database, e.g., Oracle, SQLServer, MySQL;
• Non-relational database, removing the relational characteristics of relational database to ensure the scalability of data, e.g., Redis, MongoDB, Neo4J).
From the aspects of storage mode, traditional databases mostly adopts centralized storage mode, which are confronted with capacity bottleneck issue.Therefore,distributed database is presented, which provides scalable service capacity and storage capacity by the way of sub database and sub table,and provides transparent data access and smooth capacity expansion and reduction by database agent. Similar to the characteristics of distributed database, blockchain is a decentralized distributed database, which collectively maintains a reliable database by decentralizing and trusting mechanisms.
1) Agriculture blockchain: Blockchain technology was proposed by scholars with the pseudonym of“Satoshi Nakamoto”in 2008. It is a point-to-point distributed data-storagearchitecture scheme, and it uses a variety of consensus mechanisms to achieve collaborative trust among multiple participants [88]. Furthermore, the application of cryptographic methods ensures the security of data transmission. At present,the intelligent operation of node data can be implemented by deploying smart contracts(a kind of script code)on distributed nodes [89]. Blockchain supplies a reliable technical guarantee for both the integrity and immutability of information, and it is widely used in product information traceability [90].
In agriculture, blockchain has the following functions: 1)establishing the backtracking mechanism of agricultural products.Reliable and safe information about agricultural products including their planting,processing,and selling are provided to improve information transparency. In addition, the distributed information storage method based on digital encryption and verification technology ensures the information security of agricultural products [91]; 2) establishing a new agricultural product trading market. The distributed storage technology of blockchain is used to digitize the upstream and downstream information of agricultural products. Moreover, the information is shared across the entire agricultural blockchain alliance[92].Although blockchain can be used as an information security solution, it is essentially data storage and releases technology.Because blockchain technology is still in the exploration stage in agriculture, the security challenges of blockchain remain to be explored.
F. Data Analysis Technology
Data analysis is a process of detailed research and summary of data to extract useful information, which uses appropriate methods (e.g., statistical analysis method, machine learning method) to analyze the large amount of data. Artificial intelligence is an emerging technology which contributes to the accuracy of data analysis. In addition, edge computing technology greatly reduces the traffic amount and delay by deploying artificial intelligence algorithms on the device rather than cloud server.
1) Agricultural artificial intelligence: With the development of IoT technology, the amount of agricultural data has increased dramatically. AI technology can provide an expert system to analyze agricultural big data, select valuable information,and increase agricultural productivity finally[93],[94]. At present, there are many studies and applications in agriculture AI [95], [96]. The main studies of agriculture AI include:
• Intelligent robots based on pre-set machine learning models and computer vision technology that complete basic agricultural tasks much more quickly than manpower and traditional robots, e.g., intelligent seeding robot and intelligent harvesting robots;
• Crop and soil monitoring, which have applied both computer vision technology and deep learning algorithms to analyze the crop growth data and soil health data;
• Predictive analysis,which forecasts the impact of weather changes on crop harvests by training machine learning model [97].
Based on the above studies, manual operations are being replaced by intelligent machines and decision-making systems,which contribute to the development of smart agriculture[10].However, AI technology will result in huge losses (e.g., a wrong decision for the irrigation system and plant factory environment control) if it suffers from attacks.
2) Agricultural edge computing: Cloud computing provides scalable, on-demand, and virtualized resources for users[98]. Therefore, cloud computing has been widely applied in planting, aquaculture, poultry and livestock breeding, plant factories, and related applications [54]. However, it is difficult to use the centralized data processing method of cloud computing to meet the growing amount of data, which stem from the explosive growth of agricultural data.Although cloud computing has the advantages of both strong computing power and fast processing speed,the demands of data analysis cannot be fully met by it due to its disadvantages(e.g.,high cost,high delay, and low capacity of protecting the privacy of users).
Thus, edge computing is applied in agriculture to solve these problems, as shown in Fig.8. The “edge” refers to any network and computing resources between the data source(e.g., sensors) and the cloud data center [99]. For instance,the smartphone is the edge between the user and the cloud.By transmitting sensor data to edge devices for calculation,communication delay can be reduced effectively[100].Therefore, edge computing is suitable for tasks with both low computational cost and high timeliness requirements [101].
In the area of SIL-IoT, if insect pest location data are transmitted to the cloud for decision-making and then returned to an actuator, the pest outbreak area may be transferred before the implementation of relevant measures. However, if the data are transmitted to the edge nodes and then returned to the actuator, the delay caused by the data transmission will be greatly reduced. Therefore, it is important to promote agricultural edge computing and find its potential security problems [102].
G. Data Analysis Application
1) Agricultural unmanned aerial vehicle: With the development of “3S” technology, UAVs have become widely used in agriculture, industry, and commerce. Furthermore, the UAVs’ characteristics of labor-saving and high efficiency are consistent with the development goal of smart agriculture. At present,the studies of agricultural UAVs mainly focus on plant protection operations, forestry monitoring, crop pollination,and herd positioning [103].
Due to the advantages of high operating efficiency, low pollution, and no poisoning risks for farmers in agricultural applications, the development of agricultural UAVs has been rapidly growing in some countries e.g.,the U.S.,Russia,South Korea, and especially Japan. With more than 2400 registered agricultural UAVs and more than 14 000 operators, Japan has become the country that has the largest number of agricultural UAVs [104]. Compared with the above countries in the fields of UAVs, the development of Chinese UAVs has lagged, but the investment in agricultural UAVs has increased in recent years.

Fig.8. Comparison of edge computing and cloud computing.The advantages of edge computing are low cost and low delay, which benefit to high time efficiency tasks, e.g., SIL-IoT, agricultural UVAs, driverless tractors.
There are various types of agricultural UAVs on the market,as shown in Fig.9.For instance,UAVs can be divided into both hydraulic UAVs and electric UAVs according to the dynamic system. Furthermore, UAVs can be divided into fixed-wing UAVs, single-rotor UAVs, and multi-rotor UAVs according to the model structure. Currently, electric multi-rotor UAVs have a major market share due to their low cost, low failure rate,simple operation, and environmental protection. Besides, the plant protection UAV is one of the most common applications of agricultural UAVs,based on high operating efficiency,good spraying effect, low pollution level, and operation without limitations due to the crop height. The technology gaps in the production areas where plant protection cannot be carried out manually are addressed by agricultural UAVs [103].
2) Driverless tractor: The traditional tractor is indispensable power machinery in field agriculture, as it provides traction for cultivating machines, traction seeders, a machine that spray insecticide, harvesters, etc. [105]. The driverless tractor is a combination of the traditional tractor and modern driverless technology. The advantages of driverless tractors include both optimal operation path planning by the map transmission system and dynamic obstacle avoidance by lidar,which contribute to improving the quality and efficiency of operations, and maximizing the utilization rates of land, seed and fertilizer [106], [107].
Currently, the applications of the global navigation satellite system (GNSS) and laser system in driverless tractors have been generalized in Europe, so as to avoid obstacles and operate in the appointed paths effectively [108]. In [109],further studies have been conducted in North America on the key components of automatic navigation,including navigation sensors, vehicle motion models, navigation plan devices, and steering controllers. Liu et al. [110] proposed an artificial vehicle powertrain system to build a general framework for data-driven intelligent control, which can be applied to the driverless tractor.

Fig.9. (a) Fixed-wing UAV, (b) single-rotor hydraulic UAV, and (c) multirotor electric UAV. Currently, electric multi-rotor UAVs have a major market share due to their low cost, low failure rate, simple operation, and environmental protection.
Furthermore,China has begun to develop driverless tractors in recent years. For instance, the major research program“Cognitive Computing of Audio-visual Information” of the National Natural Science Fund of China (NSFC) was established in 2008, and it has provided finance and policy support for driverless driving.
H. Summary
In this section, we described 7 key technologies and 11 key applications in smart agriculture based on IoT architecture (perception layer for data acquisition, transmission layer for data transmission, and application layer for data storage and data analysis). Some applications of agricultural IoT are introduced: IoT in field agriculture, IoT in aquaculture, IoT in poultry and livestock breeding, IoT in greenhouse, plant factory,photovoltaic agricultural IoT,and SIL-IoT,which have unique characteristics in specific agricultural scenarios and are confronted with various security threats (e.g., agricultural facility damage for IoT in field agriculture,failures in sensors for IoT in poultry and livestock breeding,control system intrusion for IoT in greenhouse and plant factory,malicious data attacks for photovoltaic agricultural IoT, and signal interference for SIL-IoT).
In addition, sensors and actuators, and agriculture satellite remote sensing are introduced as data acquisition technologies, which contribute to the applications of data acquisition(agriculture crowd sensing, and plant phenotype information system). There are some security threats for data acquisition technologies and applications, e.g., facility damage and interception of node communication for sensors and actuators,unauthorized access for agriculture satellite remote sensing,privacy leaks for agriculture crowd sensing,and control system intrusion for plant phenotype information system.
Agriculture blockchain is described as a distributed data storage technology to ensure data storage security, which is also confronted with security threats (e.g., access control failure, unsafe consensus agreement).
Moreover, agriculture artificial intelligence and agriculture edge computing are introduced as data analysis technologies.They are confronted with various security threats e.g., malicious data attacks, unauthorized access, and control system intrusion. The above data analysis technologies are applied in agriculture UAV and driverless tractor for path planning,automatic operation, local information processing, etc.. There are some security threats for agriculture UAV and driverless tractor, e.g., false location information by malicious data attacks, facility damage by control system intrusion, data interception by interception of node communication.
Therefore, effective security and privacy countermeasures play a vital role in ensuring security of smart agriculture.
IV. SECURITY AND PRIVACY COUNTERMEASURES
The summary of existing security and privacy countermeasures which are suitable for smart agriculture are presented in Table VII.The relationship between some key technologies and applications in smart agriculture and security and privacy countermeasures are shown in Fig.10.
A. Authentication and Access Control
To enhance the security and privacy of smart agriculture,user authentication systems should ensure the following security and performance requirements: resilience to various attacks, device anonymity, session key agreement, mutual authentication, and unlinkability. Lee et al. [111] proposed a three-factor anonymous user authentication scheme, which can be applied in a network model composed of three types of nodes, namely, a mobile node, a sensor node, and a gateway.Based on the bio-hash function, Lee et al.’s scheme can satisfy user anonymity, users untraceability, and resists stolen mobile device attacks.For achieving cross-domain permission delegation and access control, Gauhar et al. [112] proposed a decentralized blockchain-based framework, named xDBAuth,which the blockchain technology is used for providing transparent to all the users in the IoT network. The xDBAuth framework considers a network model composed of five main elements, including, smart contract, IoT devices, blockchain manager, overlay network, and underlay network. Based on the two algorithms, namely, cross-domain resource access algorithm and proof-of-authenticity/integrity algorithm, the xDBAuth framework can provide authentication/authorization,availability, integrity, and non-repudiation.
In addition, Shin et al. [113] designed a privacy-preserving authentication scheme for wireless sensor networks in 5 Gintegrated IoT, which the IoT architecture is based on a wireless sensor network,gateways,cloud computing,and with three types of layers, including, network layer, application layer, and support layer. The Shin et al.’s scheme uses elliptic curve cryptography to guarantees gateway anonymity, user anonymity with untraceability, and resistant to four types of attacks, including, offline password guessing attacks, mobile device loss attacks, stolen verifier attacks, and user impersonation attacks.
B. Privacy-preserving

Fig.10. Different security and privacy countermeasures for 7 key technologies and 11 key applications in smart agriculture.

TABLE VII SUMMARY OF SECURITY AND PRIVACY COUNTERMEASURES FOR SMART AGRICULTURE
For achieving privacy-preserving, Wang et al. [114]proposed a privacy-preserving spectrum sharing framework for the IoT network, which can be applied for smart agriculture by considering at the same time the spatial spectrum reuse and truthfulness. Specifically, the proposed framework considers three units, including, a cryptographic authority,multiple bidders, and an auctioneer. Based on the Elgamal encryption scheme, the proposed framework can keep the bidders’bids confidential and achieving user satisfaction ratio.Therefore, in order to enable offline/online computation and support IoT devices with various cryptographic settings, Wei et al. [115] designed privacy-preserving message authentication scheme, named SAMA, for IoT networks, which can be applied for smart agriculture. The SAMA scheme uses various systems such as RSA-type and ElGamal-type for preserving the location and identity privacy of a data source as well as message authenticity and integrity. Zhang et al.[116] proposed a privacy-preserving data aggregation scheme,named LVPDA,which can be applied for the edge-computingenabled smart agriculture. During the data aggregation process,the LVPDA scheme combines an online/offline signature technique and Paillier homomorphic encryption method for privacy-preserving and integrity verification. Based on the q-strong Diffie-Hellman (q-SDH) assumptions, the LVPDA scheme is proven unforgeable under the chosen message attack.
C. Blockchain-based Solutions for Data Integrity
The blockchain technology is used as a security solution to provide data integrity in smart agriculture. To provide automated data processing in fish farming, Hang et al. [118]designed a blockchain-based fish farm platform, which is based on smart contracts. The proposed platform uses four main components, including, end-user, blockchain network,fish farm, and data storage. Based on the blockchain network,the proposed platform can provide reliable and secure storage. Therefore, to provide traceability and trust in the agrifood supply chain, Shahid et al. [119] proposed a security solution deployed over the Ethereum blockchain network.The proposed solution considers an agri-food supply chain with a layered architecture and is categorized into three layers,including, data layer, blockchain layer, and storage layer. To achieve accountability and authenticity, the proposed solution uses an interplanetary file storage system that receives the data and returns a hash of these data to the blockchain network.
D. Cryptography and Key Management
The symmetric encryption/decryption along with the cryptographic hash function are used by Wazid et al. [125] for designing a secure user authenticated key management protocol,which can be applied in smart agriculture.The network model used by the proposed protocol is composed of three different nodes, including, the sensing nodes, the gateway node, and cluster head nodes. To verify the biometric authentication,the proposed protocol uses the fuzzy extractor technique.To ensure confidentiality with end-to-end security guarantees,Esposito et al. [123] proposed a clustered and distributed key management framework, which is based on the group-based keys. Specifically, the proposed framework uses a network model composed of group nodes with the cluster head and the border nodes. In addition, within the proposed protocol,the key to be shared, is divided into encoded parts, and only a part of the received parts is transmitted by the cluster head to its neighboring nodes.
E. Physical Countermeasures
Both cyber and physical attacks are in high demand in smart agriculture.Li et al.[121]proposed an auditing and analyticsbased IoT monitoring mechanism. The proposed mechanism uses disaggregation-aggregation architecture using the evaluation of the power usage of the system’s sub-components.Therefore, the proposed mechanism adopts two deep learning models, including, the aggregation model and disaggregation model. Therefore, to provide a comprehensive view of the security status of smart homes in smart agriculture, Ali and Awad [124] proposed the operationally critical threat, asset,and vulnerability evaluation methodology, named OCTAVE,which focuses on information assets. The OCTAVE method is applied in the network model composed of three parts,including, IoT devices, a gateway, and a web server. In addition,the OCTAVE method uses four main phases to allow comprehensive risk assessment, including: 1) establish drivers phase,2)profile assets phase,3)identify threats phase,and 4)risk mitigation phase.
F. Intrusion Detection Systems
Cyber-attacks for smart agriculture infrastructures are emerging as an increasingly important concern for both organizations and nations. To detect these cyber-attacks in smart agriculture, security researchers have proposed intrusion detection systems based on machine learning and data mining algorithms. Ferrag et al. [117] and Maglaras et al. [127]designed a hybrid intrusion detection system,named RDTIDS,for internet-of-things networks,which can be applied for smart agriculture. Specifically, the RDTIDS system uses decision tree and rules-based concepts to classify the network traffic as attack/benign.The experimental results on the BoT-IoT dataset and the CICIDS2017 dataset shows that the RDTIDS system achieves the highest accuracy with 96.995% and 96.665%,respectively.
In addition, Anthi et al. [120] designed a three-layer intrusion detection system for detecting a series of cyber-attacks on IoT networks, which can be applied for smart agriculture.The proposed system uses a supervised approach to classifies attacks such as replay attack, reconnaissance attack, man-inthe-middle attack,spoofing attack,and denial of service attack.The experimental results on cyber attacks dataset show that the proposed system achieves an F-measure of: 1) 96.2%,2) 90.0%, and 3) 98.0%. Sforzin et al. [126] proposed an intrusion detection architecture for the IoT network, named RPiDS,which can be applied for smart agriculture.The RPiDS architecture uses a small, portable device, pre-packaged with an intrusion detection system for detecting an active attack and or suspicious network-related activity. The experimental results on Raspberry Pi equipped with Snort show that RPiDS architecture is adapted to conduct intrusion detection in an IoT framework.Ahmim et al.[122]designed an intrusion detection system that can be applied for smart agriculture. Specifically,the proposed system can be installed at the fog computing layer for detecting cyber-attack using the combination of the probability predictions of a tree of classifiers. The experimental results on KDD’99 and NSL c○datasets show that the proposed system achieves the highest accuracy with 96.27%and 89.75%, respectively.
V. SECURITY CHALLENGES OF SMART AGRICULTURE
Most of the existing security and privacy countermeasures are based on industrial scenarios or only based on simulation performance, without considering the actual application scenarios.Therefore,it is necessary to analyze security challenges based on smart agriculture, which contributes to applying the above security and privacy countermeasures to various smart agriculture scenarios.
A. Security Challenges in Agricultural Production
1) Harsh environment: The modes of agricultural production mainly include large-scale field farming, small-scale greenhouse farming, aquaculture, and poultry and livestock breeding. However, the maintenance problems of sensors and farm implements by the above modes cannot be ignored. The primary maintenance problems include hardware protection for the facilities and the energy consumption design of the facilities. Due to the characteristics of sparse deployment and the absence of supervision in agricultural IoT facilities,sensor nodes may be stolen and used by malicious users,which would lead to serious security problems (e.g., data leakage and network paralysis). In addition, agricultural IoT facilities are required to have reliable long-distance signal transmissions,and they must reduce their energy consumption to ensure their long-term stable operation.Therefore,a balance between energy consumption and the reliability of the signal transmission is critical for agricultural IoT facilities.
2) Threats from agricultural equipment: Except for the harsh environment, the security issues caused by the working characteristics of agricultural equipment cannot be ignored.For instance, SIL release high voltage (~2150 V to ~6000 V)pulse discharge while migratory insects with phototaxis feature contact with the metal mesh, which has a great impact on ZigBee [25]. In [25], [26], we did some experiments and the results indicate that the interference of high voltage discharge affects data transmission. In this paper, we did the following experiments under the same experimental devices[26] (parameter, evaluating indicator, purpose, and device are shown in Table VIII). The first experiment (only indicating that the interference affects sending node) has been done in[26] before, we did that again with three evaluating indicators and extended it to two additional experiments, which are used to verify whether the interference has an impact on receiving node and sensors.
• Observing the interference of high voltage pulse discharge for sending node under the distances of 10, 15,20, and 25 cm. Table IX illustrates that the interference is stronger to ZigBee with the closer distance between SIL and sending node (there is a positive correlation between FET and interference intensity). It is mentioned in [26] that the interference (quantified by FET times)has an impact on the ZigBee-based device. However, the influences of the interference on data transmission and data acquisition are not mentioned.Therefore,we did the next two experiments.
• Observing the interference of high voltage pulse discharge for receiving node under the distances of 0, 5,and 10 cm. The results are depicted in Fig.11, and communication duration is the time difference between node receiving data normally and not receiving data normally.It is observed from the results that the communication duration has a positive correlation with the distance between SIL and receiving node. Moreover, when the distance between SIL and receiving node is more than 10 cm, the interference is not obvious under the existing experimental equipment and conditions. The distance may increase with the increase of the interference intensity generated by the equipment.

Fig.11. Interference on different distances between SIL and receiving node.Average communication duration values of 0 cm, 5 cm, and 10 cm are 45.6 s,116.5 s, and 765.9 s. Maximum values of 0 cm, 5 cm, and 10 cm are 151 s,422 s, and 1970 s. Minimum values of 0 cm, 5 cm, and 10 cm are 4 s, 4 s, and 45 s.
• Observing the interference of high voltage pulse discharge for sensors under the distances of 0 and 5 cm.The sensors with ID 1 and 2 were used for the experiment(distances between them and SIL are 0 and 5 cm),and the sensor with ID 3 was used as the control group (distance between it and SIL is 1m). As shown in Fig.12, when we turn on the discharge module at 15:34:30, the data acquisition is abnormal and the device reset after a few seconds.The proportion of abnormal data(the proportion of abnormal data to all data in a certain period) and the proportion of device reset are shown in Table X. When the distance is 0cm, sensors with ID 1 and 2 can hardly collect data normally. The interference is not obvious when the distance between SIL and sensors is more than 5cm. However, in the case of a harsh environment and aging equipment, the effective range and extent of injury of interference may be unpredictable.
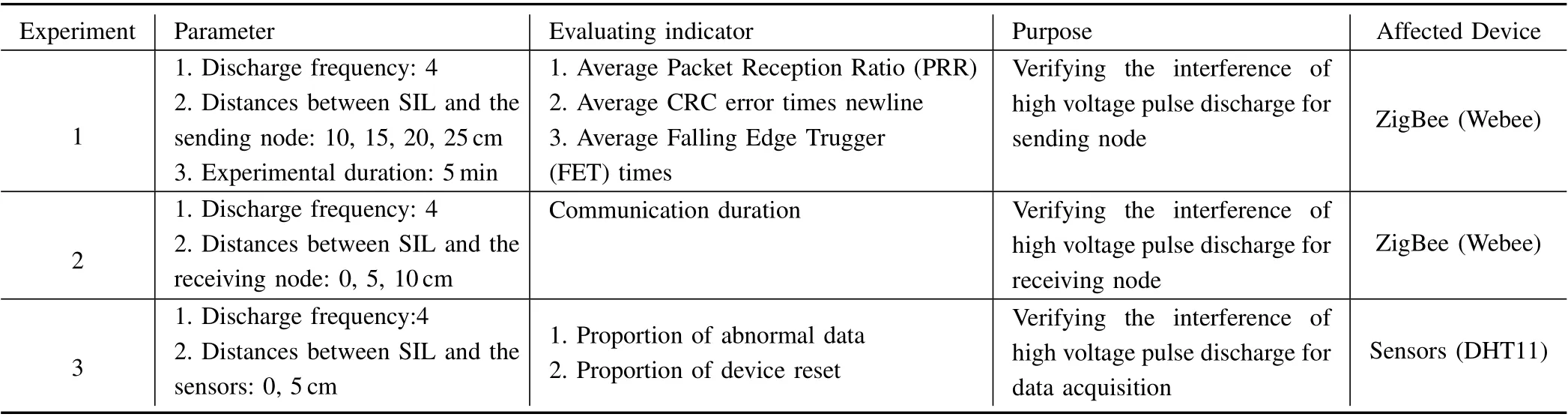
TABLE VIII INTERFERENCE EXPERIMENTS FOR DIFFERENT DEVICES

Fig.12. Data acquisition under interference. For the first line, “2020-07-08-15-15:34:32” is time format, “02” is sensor ID in red dotted box, “26.6” is temperature (◦C) in yellow dotted box, and “72” is relative humidity (%) in green dotted box. Besides, data in blue dotted box are normal data, data in violet dotted box are abnormal data, and data in grey dotted box are device reset information.

TABLE IX INTERFERENCE ON DIFFERENT DISTANCES BETWEEN SIL AND SENDING NODE
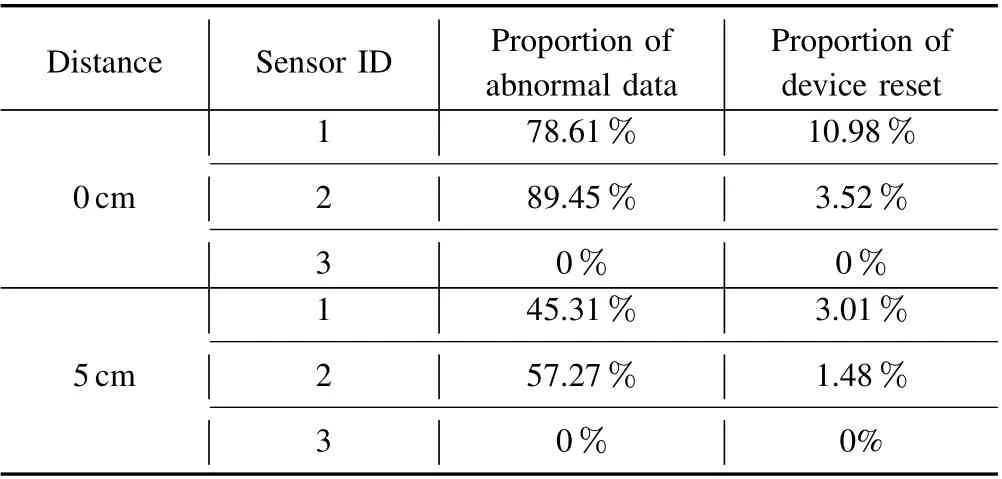
TABLE X INTERFERENCE ON DIFFERENT DISTANCES BETWEEN SIL AND SENSORS
The above experiments indicate that the interference of high voltage pulse discharge has an impact on data transmission and data acquisition. The interference is a kind of security threat and may mislead the execution of security strategy. For instance, if the receiving node cannot receive data normally due to interference, the security strategy may classify it as a DDoS attack.
B. Security Challenges in Information Technology
1) Unauthorized access: Unauthorized access refers to unauthorized use of system resources and unauthorized access to a database, which results in serious network security challenges. To access data and control agricultural IoT facilities beyond the limit of users’ authority, hackers attack the access control mechanism of the system by forging a counterfeit identity [128]. The main reasons for unauthorized access are:
• Rapid change of accessing the particular user account from the unrecognized location;
• Accessing the user account with an unrecognized device;
• Sudden IP, server domain and gateway change [128].
Identity authentication, which identifies legal users by their passwords and biometrics, is applied to prevent unauthorized access [129]. Furthermore, access control strategies should be set up to manage user rights, and to ensure the security of various resources in the system. As shown in Fig.13, hackers can illegally access edge nodes and cloud databases to obtain crop growth data and modify control system information,which would have an impact on crop growth and data quality.

Fig.13. When a variety of data is transmitted to the cloud or edge node,hackers access the database through unauthorized access.
2) Interception of node communication: Wireless communication technology is widely applied in various agricultural IoT facilities. Unfortunately, the information transmitted by wireless communication is easily copied and stolen [130].The information usually contains both environmental data collected by sensors and facility control signals in agricultural production. Data tampering and interception by hackers may have serious consequences [131]. To ensure the security of wireless communication, appropriate encryption strategies for wireless devices are required to encrypt data [132]. Simultaneously, various wireless sensors may not be able to support complex encryption algorithms for communication security.Therefore, a balance between the encryption strength and the facility capacity must be sought. As presented in Fig.14, data collected by sensors can be sent to a gateway through the communication terminal. Hackers steal data by invading wireless communications, which results in serious consequences.

Fig.14. In the process of node communication, hackers intercept data by invading receiving nodes.
3) Facility damage: Due to the complex conditions in an agricultural production environment, facilities that are deployed in an agricultural environment may send incorrect data, be damaged, or lose the capacity to collect data. Facility damage may result in data distorted and missing,which would affect the data analysis and the decision-making system[133].Therefore, it is necessary to establish a facility detection mechanism. If the facility stops working or the data collected by the sensors deviate from the normal range, faults should be detected and related measures should be implemented promptly by the neighboring nodes or diagnosis nodes.Fig.15 shows various faults that result from facility damage, which have negative impacts on the daily operation of agricultural UAVs.
4) Malicious data attacks: AI technology can be applied with its ability to analyze massive data and sensory data is the main factor in any decision-making process[134].In addition,a pre-trained model with optimal environmental parameter settings contributes to improving the yield and quality of agricultural products. However, by inserting malicious data into the database,the model training process is affected,which would cause a deviation in the model results. The primary solutions include the privacy protection of agricultural IoT facilities [135], and online and real-time monitoring system[136]. As presented in Fig.16, due to malicious data attacks,the solar insecticidal lamps in an actual pest outbreak area are sleeping, which leads to crops damage. Simultaneously, we have a waste of energy caused by incorrect responses of the solar insecticidal lamps that are in the false pest outbreak area.

Fig.15. System fault,link fault,sensor fault,and other factors lead to uneven spraying of pesticides.

Fig.16. Due to malicious data attacks, the solar insecticidal lamps in an actual pest outbreak area are sleeping, which leads to crops damage.Simultaneously, we have a waste of energy caused by incorrect responses of the solar insecticidal lamps that are in the false pest outbreak area.
5) Control system intrusion: After the data collection and analysis,the control system sends commands to the machinery to complete the corresponding production operation. Therefore, the security of the control system plays a vital role in agricultural production. Control system intrusion may lead to no response from the production machinery [137], which would have a strong impact on agricultural production.Therefore, protecting the decision-making system from intrusion,and protecting the control signals from interference has a great impact on the performance of agricultural production. Fig.17 illustrates a driverless tractor operating on the wrong route after a control system intrusion.
C. Summary
Due to the harsh environment and threats from agricultural equipment, the protection measures and anti-interference design of the agricultural equipment are very important. Furthermore, severe weather prediction and interference filtering at the software layer contribute to the security of agricultural production.However,ensuring the security of agricultural production is a very complex task, mainly because of changeable climatic conditions, large-scale and harsh environments, and various agricultural equipment with different standards.

Fig.17. A driverless tractor operating on the wrong route after a control system intrusion.
In addition, recent works related to information security are shown in Table XI. Key distribution and authentication mechanisms are a major research direction of unauthorized access, and among these works, machine learning algorithms have been used to improve the accuracy of the classifications[138]. Furthermore, hypothesis testing is a method that can estimate false alarm rate and false negative rate(i.e.,5%false rejection rate with four PCA dimensions [129]).
Recent studies of the interception of node communication focus on the decode-and-forward protocol, and the affected layer is typically the cyber-physical layer. Intercept probability is mainly used to estimate the performance of model,increasing power-splitting factor signal power,and the number of relays may improve the security of wireless transmission[130], [132], [139]. In addition, Zou and Wang [131] demonstrated that sensor scheduling method contributes to against eavesdropping attack.
The perception layer is the main affected layer in facility damage. Various methods are used to protect sensors and actuators, and the effective ones include node privacy and source encryption methods [140].
Malicious data attacks mainly happen in smart grids and position systems, and statistical methods and deep learning algorithms have primarily been applied to mitigate this problem [136]. In [141], an analytical method based on no previous knowledge of attack was adapted to multiple and simultaneous cyber-attacks. Alromih et al. [134] proposed a randomized watermarking filtering method to ensure data security in transmission layer and save as up to 85% more energy than Cui et al. [142]. In addition, an online robust PCA-based algorithm was proposed to reconstruct the original data when the corruption rate is no more than 20% [136].
Industrial control systems (ICS) are the major attack target of control system intrusions, which have strong impacts on these systems’ transmission layer and application layer. Modbus/TCP oriented attack is a major type of control system intrusion.Ndona and Sadre[143]proposed a two-level intrusion detection system to efficient against Modbus/TCP oriented attacks with a small impact on communication latency. In[144], a new intrusion detection algorithm based on oneclass SVM was presented with advantages of fast and strong generalization ability, less support vector, simple mode, and great practical value. Moreover, A stereo depth intrusion detection system with a low rate of false positive (not exceed 0.045%) was proposed [145]. With the development of smart agriculture, agricultural production will be the novel attack target,and above intrusion detection algorithms will contribute to the security of the agricultural control system.
In summary, analyzing types of attacks for different smart agriculture researches and security strategies suitable for various agricultural scenarios is critical to ensuring the security of smart agriculture.
VI. FUTURE TRENDS AND SECURITY ISSUES
The following issues may be the future research trends of smart agriculture, and they may result in novel security challenges. We briefly describe the concepts below.
A. Fifth Generation Communication (5 G)
5 G is the next generation wireless communication technology with characteristics of high-frequency electromagnetic wave and low latency. Compared with the existing wireless communication technology, 5 G provides faster data transmission speed and larger data throughput, which support the device communication, AI algorithm deployed in user end, distributed fault diagnosis method, and complex security strategy. However, 5 G is also vulnerable to security threats,e.g., interception of node communication. In addition, the security defined in the 3rd Generation Partnership Project(3GPP) focuses on resistance to network attacks, authenticity, integrity, and confidentiality. However, some emerging cryptographic techniques, e.g., public key infrastructure,anonymization,security mechanisms of IPsec,and differential privacy, etc., can be considered for achieving security and privacy requirements. To design efficient and secure privacypreserving schemes using these techniques for 5 G-enabled smart agriculture networks, the following critical challenges need to be solved:
• How to protect the confidentiality of transmitted data between network entities?
• How to authenticate the source of the received data?
• How to protect the integrity of transmitted data between different network entities?
• How to detect and prevent attacks (e.g., falsification of multiple identities and replays data between network entities)?
A possible research direction in this topic could be related to developing an efficient secure and privacy-preserving scheme for 5 G-enabled smart agriculture networks. For instance, the physical-layer threats in UAVs’ communication based on 5 G was discussed in [148].
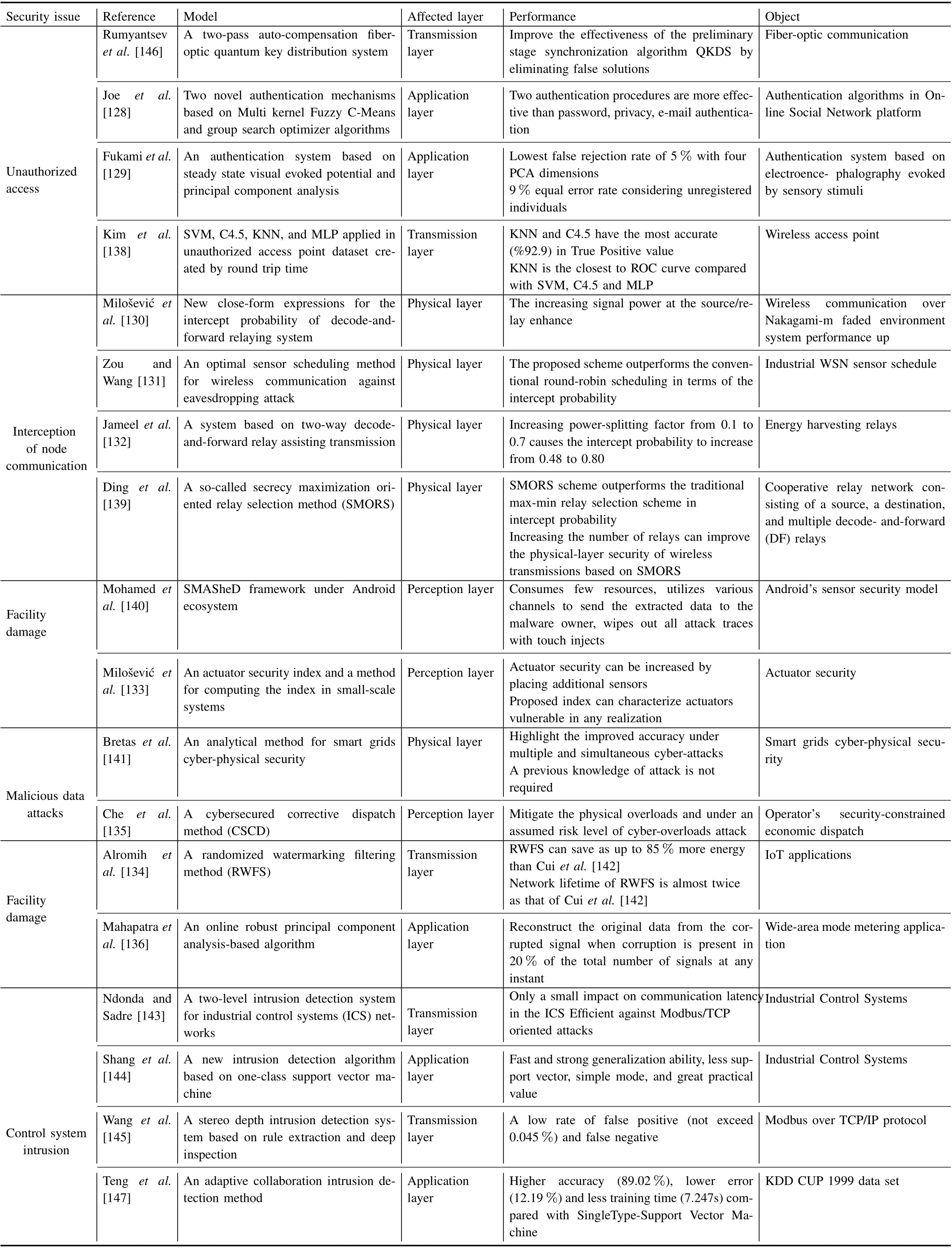
TABLE XI SUMMARY OF RECENT WORKS RELATED TO INFORMATION SECURITY
B. Fog Computing (FC) and Internet of Everything (IoE)
FC is a computing paradigm that reduces communication delays by moving the cloud computing facilities and services to the access network. Since the FC is designed upon traditional networking components, it is highly vulnerable to security attacks (e.g., wiretapping, tampering, loss of information,and Trojan horses) [149]. IoT mainly focuses on machine-tomachine sensor-based smart facility communication, as well as IoE aims at providing services to people by IoT. Due to the resource-limited sensors and bandwidth-limited wireless communication,the Fog of Everything(FoE)was proposed in[150] to set up a complexity system. It will contribute to SILIoT and photovoltaic agricultural IoT which have multi-tasking requirements (i.e., operating, monitoring, and scheduling).
In addition, data of farmers, consumers and sensors are fused by FoE, and part of processing modules of agricultural information, agricultural products trading and other data can be deployed in the local network layer, as shown in Fig.18.With the application of new generation of communication technology, e.g., 5 G, FoE can meet more intelligent agricultural production demands,and improve the security of existing smart agriculture applications. Simultaneously, in the process of data fusion,transmission,storage and analysis,new security issues will inevitably arise due to the application of novel computing paradigm and information carrier, especially cyber security at the edge.

Fig.18. The novel mode of agricultural production by FoE architecture.
C. Renewable Energy Management System (Renewable EMS)
With the aggravation of the global energy crisis, considerable attention has been paid to the study of integrating and using high penetration of renewable energy in past decades[151]. Renewable energy has been widely applied in various domains, and agriculture is one of the most potential application scenarios. Energy management plays a vital role in smart multi-microgrids for agriculture (e.g., energy management of photovoltaic agricultural IoT), and it can ensure the energy supply of sensors deployed outdoors with the combination of wireless charging technology.
At present, the security scheme of renewable EMS usually includes fault self-diagnosis of hardware and software,identity authentication, data encryption, intrusion detection, and data backup,as shown in Fig.19.Because agricultural facilities are mainly deployed in outdoor environment, fault self-diagnosis of hardware and software is very important to ensure the security scheme.In addition,blockchain technology may contribute to the security of renewable energy management system.
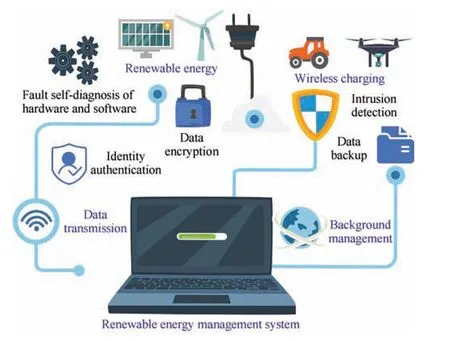
Fig.19. The security scheme of renewable EMS, including 1) fault selfdiagnosis of hardware and software in agricultural facilities and renewable energy equipment, 2) identity authentication and data encryption in data transmission layer, 3) intrusion detection and data backup in background management.
D. Software Defined Network (SDN)
Software defined network is characterized as a centrallycontrol network.With user-defined virtualization and programming, the relaying and controlling are performed separately,which can provide flexibility and reliability to the network management [152]. In recent years, SDN has been a hot subject,especially multi-domain SDN that controls large-scale networks, i.e., precision agriculture [153]. Moreover, It can effectively simplify the network, and manage heterogeneous network equipment. The SDN controller can monitor the security situation of whole network in real-time.
However, centralizing the network control plane and enabling network programmability are the emphases of hacking,and may lead to new security challenges, controllers’ safety from applications, controller’s scalability and availability, resilience and placement,etc.[154].For instance,a plant phenotype information system integrates multiple data sources, and SDN architecture can improve its performance and security,but new security threats are an urgent problem. As shown in Fig.20, if hackers attack the SDN controller, it will transmit wrong control instructions,which results in abnormal data flow and affects the trust between the SDN controller and the plant phenotype information system applications.
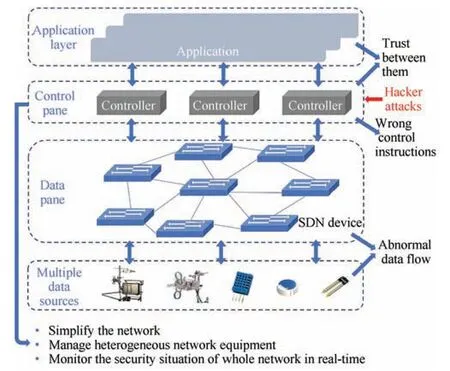
Fig.20. A plant phenotype information system based on SDN architecture(including multiple data sources, control pane, data pane, and application layer) and security issues (trust between applications and controller, wrong control instructions, and abnormal data flow) result from hacker attacks.
E. Virtual Reality (VR) and Augmented Reality (AR)
VR is a simulated experience that can be similar to or completely different from the real world.AR is the technology of superimposing virtual objects upon the real world[155].Although VR has been widely applied as an educational method in industry,there are a few researches about VR in agriculture domain. For instance, Kim et al. developed an educational simulator by VR technology for a better farmer education compared with two-dimensional screens [156]. Besides, a VR simulator that contributes to technical training of maintenance of agricultural machinery was developed [157]. Huuskonen et al. designed a wearable AR equipment to aid and guide the farmer to collect soil samples [158]. Both VR and AR technologies contribute to the automation and intelligence of agriculture. For instance, farmers can remotely and precisely control agricultural robots through VR and AR equipment in the control center. In addition, farmers can study the fault diagnosis and security countermeasures by VR educational simulator, which contribute to the improvement of securityconscious and prevention skills of farmers.
However, both VR and AR technologies are vulnerable to various types of attacks, which have an impact on reliability of systems as they are designed to replace our perception of the physical world (e.g., tracking attacks) [159].
F. Cyber Security Datasets for Smart Agriculture
When proposing intrusion detection systems,it is struggling to find comprehensive and valid cyber security datasets to test and evaluate the performance of cyber security intrusion detection.The study in[160]reviewed the most cyber security datasets used in deep learning approaches for cyber security intrusion detection such as NSL-KDD dataset, KDD Cup 1999 dataset, and UNSW-NB15 dataset. These datasets are not simulated for smart agriculture environments. Therefore,the development of a new dataset to build a network intrusion detector under a smart agriculture environment is one of the significant research challenges. In addition, we believe that a comparative study of machine learning approaches for cyber security intrusion detection is needed for smart agriculture environments.
G. Summary
The integration of the above issues and agriculture provides the opportunity to promote intelligent and automatic agriculture. In addition, faster data transmission speed (5 G),lower communication cost and latency (FC), lower energy consumption(renewable energy management system),separate relaying and controlling (SDN), simulation environment (VR and AR), and datasets for evaluating model (Cyber security datasets for smart agriculture) contribute to the development of smart agriculture, as shown in Fig.21. However, the above issues are confronted with more severe security challenges because security threats of them have not been fully explored.When the above issues are widely used in smart agriculture,there will be a quantity of security problems. And these problems may lead to serious consequences, e.g., tracking attacks to VR equipment will result in improper positioning and harm to users.
Therefore, secure and privacy-preserving schemes play a vital role in reliability of smart agriculture. Researches on the existing security and privacy countermeasures in the above issues can prevent security threats of them in smart agriculture.For instance,the authentication and access control and privacypreserving scheme for 5 G-enabled smart agriculture networks is required with the rapid development of smart agriculture.To ensure the security of 5 G in agriculture, the researches on existing security and privacy countermeasures,and specific strategies will become hot issues in this field and promote the development of smart agriculture.
From the above sections, it is suggested that:
• Expanding and improving the existing security and privacy countermeasures in smart agriculture (most of them are in the theoretical stage, and few actual cases).
• Analyzing the characteristics and challenges of security issues in smart agriculture scenarios, and applying the existing security and privacy countermeasures mainly for industrial scenarios to smart agriculture scenarios (industrial scenarios are widely used, but the characteristics of agricultural production are not taken into consideration).
• Following the development of novel technologies, applying them to smart agriculture scenarios, and highlighting the new security issues brought by them simultaneously.
VII. CONCLUSION
Fig.21. Future research trends, security challenges, and lessons learned about smart agriculture.
With rapidly advancing modern technology, smart agriculture, which is a combination of agriculture and information technology, is becoming a trend of agricultural development.However, information technology also entails various security challenges. This paper surveys the state-of-the-art works related to smart agriculture and discusses the security challenges of smart agriculture. We introduce three smart agriculture development modes(precision agriculture,facility agriculture,and order agriculture), and investigate 7 key technologies and 11 key applications of smart agriculture. It is followed by a summary of security and privacy countermeasures for smart agriculture. Authentication and access control, privacypreserving,blockchain-based solutions for data integrity,cryptography and key management,physical countermeasures,and intrusion detection systems are introduced and discussed in detail.Then,we discuss the security challenges in agricultural production and information technology. In addition, we did some experiments based on SIL-IoT, and the results indicate that the interference of high voltage pulse discharge has an impact on data transmission and data acquisition. Moreover,we present six issues which may be the future research trends of smart agriculture and introduce the novel security challenges.
杂志排行
IEEE/CAA Journal of Automatica Sinica的其它文章
- Digital Twin for Human-Robot Interactive Welding and Welder Behavior Analysis
- Dependent Randomization in Parallel Binary Decision Fusion
- Visual Object Tracking and Servoing Control of a Nano-Scale Quadrotor: System, Algorithms,and Experiments
- Physical Safety and Cyber Security Analysis of Multi-Agent Systems:A Survey of Recent Advances
- A Survey of Evolutionary Algorithms for Multi-Objective Optimization Problems With Irregular Pareto Fronts
- Multiagent Reinforcement Learning:Rollout and Policy Iteration
