Design and implementation of Internet application security protection
2020-12-09WangYaoweiWeiYushuaiGuoQuanchengFengBinLiGang
Wang Yao-wei, Wei Yu-shuai, Guo Quan-cheng, Feng Bin, Li Gang
Information Network Management Office, Weifang People’s Hospital, Weifang 261000, Shandong Province, China
Abstract On the premise of ensuring the data security, medical staff can access the business system anytime and anywhere, acquire patient’s information in time, deal with emergencies, and even assist remote diagnosis. Through exploration and research, it is found that by using deep encryption tunnel technology and virtual isolation space, business applications and general applications can be separated in field of transmission and storage, used business information can be cleared,unauthorized terminal connection and access to the system can be prohibited, so as to ensure that data will not be processed and stored on mobile terminals and prevent all kinds of known and unknown Trojan Horse Virus from spreading to and destroying the system, rapid tracing and tracking can be performed through visualization audit mechanism, to control the violations and illegal operations. Through the above means, the transmission security on the data link is ensured, also the security requirements without leakage are achieved. Finally, regardless of internal or external network environments, an effective management, security protection and use can be performed.
Key words: Internet+ Health; information security; mobile health; data protection; tunnel technology;virtual isolation space
Background
With the continuous popularization of various mobile Internet products, various mobile Internet application software and office systems are constantly emerging in daily life and work. At present, more than half of Chinese population are using mobile devices to access the Internet. With such a huge base, the use of mobile medical systems based on the Internet and mobile networks can achieve the acquisition of medical and health education knowledge, simultaneously, an increasing requirement is provided from the vast majority of medical staff who are calling for understanding changes in patients’ conditions anytime and anywhere by using mobile products. In order to improve the efficiency of diagnosis and treatment of clinical medical staff, mobile health, as a new diagnosis and treatment model, has become an indispensable part in the business development of Hospital Information System,and it also serves as the development trend of future diagnosis and treatment models.
Status Analysis
“Internet+ Health” will promote a comprehensive integration of medicine and public health with the Internet, Internet of Things, big data, cloud computing and other fields, and bring major innovations to the medicine and public health industry. It has become the focus and hot spot in the current medical field. Medical institutions at all levels have also been continuously involved in the practice of Internet Comprehensive Health,Comprehensive Healthcare, Comprehensive Services, and they actively explore the network applications of medical health service (such as computerized physician order entry system and electronic prescription system) and medical development models on the basis of the above concept,allowing hospitals to update from traditional fixed workstations to mobile wireless multifunctional vehicle,and to the current mobile PDA/PAD and smart phones,enabling the medical staff’s working mode to extend from fixed workstations, wards, patients to outside hospitals and even community clinics.
In the process of providing affordable and convenient medical treatment, the sensitive data of patients are required to be disclosed. Although data disclosure will bring a series of benefits to the majority of patients and make the originally mysterious and unpredictable medical service industry more transparent, it is undeniable that data disclosure is a double-edged sword. Without good protection of patient’s privacy upon disclosure, the harm caused by information leakage is also obvious.
While mobile health brings convenience, it is also prone to be cracked due to the openness of mobile medical equipment. Various information security problems are emerging, and will affect normal business development of the hospitals, even induce medical disputes at a serious problem level, when these security problems cannot be solved in a timely and effective manner. Then, how to solve the problems of terminal security, data protection,application distribution, and secure transmission in the era of mobile Internet, how to protect patient’s privacy and ensure no leakage or stealing of various sensitive hospital data, have brought new problems and topics to information security management at this stage, and are also first key issues that must be resolved in the promotion of mobile medical applications.
System Architecture Design
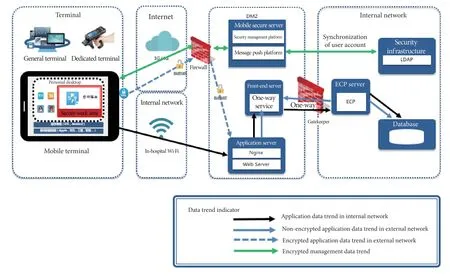
In order to construct a secure mobile medical system,a mobile medical security system architecture based on mobile security management platform is deployed in the demilitarized zone (DMZ) of the hospital’s external network. The security system architecture is centered on the mobile security platform, comprising four layers of security defense. The first layer is the one-way network security isolation (gatekeeper) between the internal network and the DMZ zone; the second layer is the system perimeter security defense (internal and external network firewalls) set up in the external network and the DMZ zone; the third layer is mainly based on the mobile security management platform, all data and access are communicated through application access control(authorization system); and the fourth layer is the mobile terminal security system (APP) of security terminal equipment.
System Implementation
Information security refers to ensuring the integrity,availability, confidentiality, reliability, and controllability of information. Its essence is to ensure that both information system and information resources in the system (including hardware, software, data, personnel, physical environment and their infrastructure) shall not be destroyed, altered,leaked or illegally occupied due to natural or manmade factors. The opening of the mobile Internet era contributes to convenient and efficient works. The design and implementation of the protocol should include the following considerations: how to ensure the security of its access environment, how to confirm the access identity,and how to ensure the safety and reliability of access information.
Mobile security management platform
The mobile security management platform is the core area of the entire security system. It encrypts, decrypts, and analyzes the data transmitted from the system perimeter security defense and network security isolation, and then conducts a second security audit on the data through the access control system. The application data of internal and external networks are distinguished and assigned to different directions, thus achieving the security of data interaction.
Deep tunnel
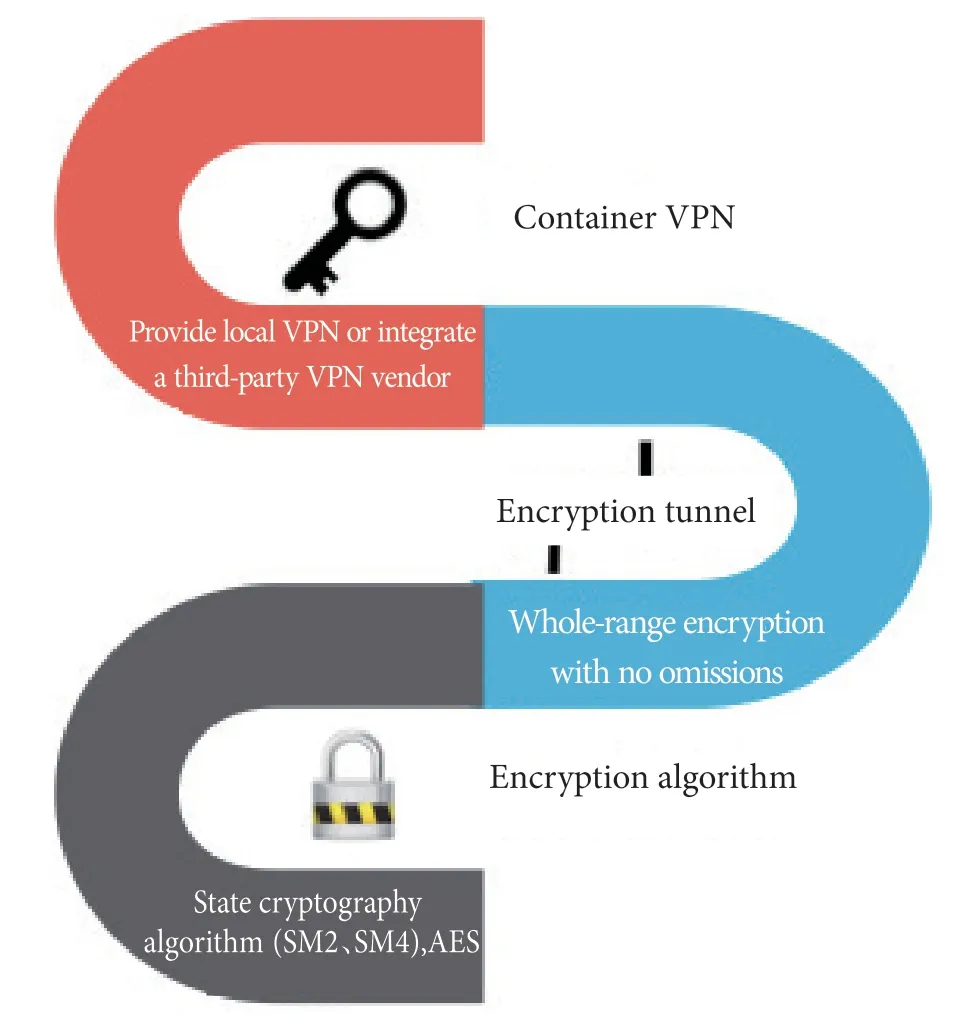
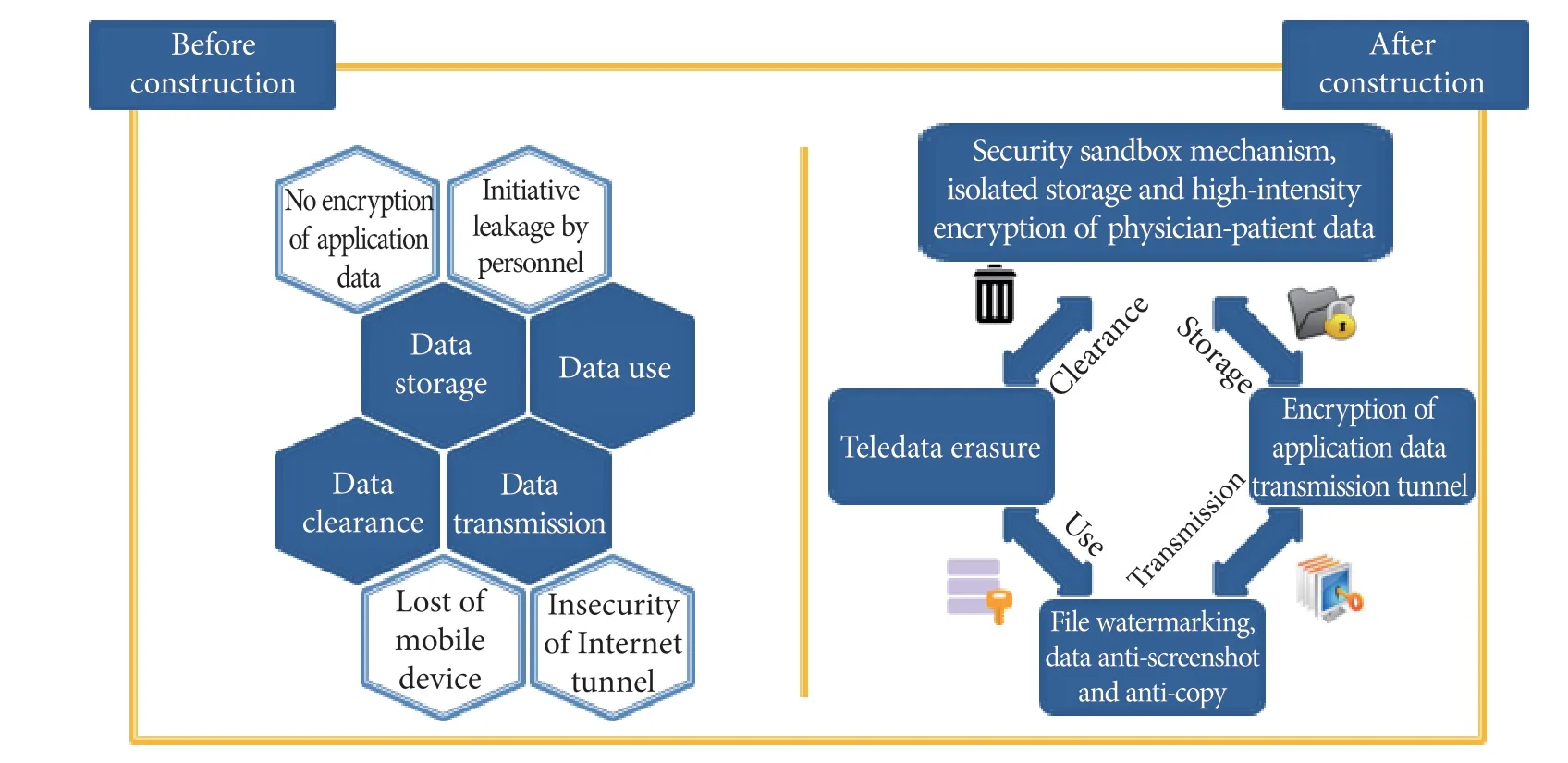
The deep encrypted VPN tunnel technology is not only supportive of state cryptography algorithm/AES-256 highintensity encryption algorithm, also fully compatible with mainstream third-party VPN solutions. Then, a secure transmission link different from the traditional VPN tunnel is opened, which solves the high-cost problem and complicated client configuration caused by the use of privacy lines, serving as a best-of-both-worlds approach.This link becomes a secure tunnel for medical staff working inside and outside the hospital to connect to the office system and business system of internal network,ensures that information of both physicians and patients cannot be stolen and used during transmission.
Virtual isolation space
Using virtual isolation space technology, a virtual work area is established in the mobile terminal equipment to achieve a complete isolation between the personal area and the work area, and information of physicians and patients in the secure area are subject to high-intensity encryption,including the application information, files, and phonebooks. Only authorized applications can decrypt the information to prevent the entry of risks outside the space and the exit of doctor-patient information in the space.
Information security application
The information application process not only adopts a series of functions such as intelligent file watermarking,data anti-copy, anti-paste and anti-screenshot, but also erases the information data temporarily stored in each terminal after the information data application is completed, to ensure that the physician-patient information in the terminal is not leaked.
Summary
The use of mobile medical technology in the construction of hospital informatization not only facilitates timely medical treatment for patients and shortens the time for medical treatment. At the same time, it is also beneficial to the hospitals, making the hospital’s diagnosis and treatment in more ordered manner, and reducing the workload of physicians and related medical personnel.At the same time, through the mobile security management protection platform, using deep encryption tunnel and virtual isolation space technologies, the security and timeliness of internal application distribution under the control of dedicated terminal, the cumbersome multi-application login, and the security of information access from out-of-hospital to in-hospital are effectively solved. It is not only convenient and safe for medical staffwho use the terminals, but also achieves the purposes of releasing management difficulty, elevating security level,enhancing operation and maintenance efficiency, and improving terminal experience. It has good practicality and promotion value for the security protection of medical staff applications in Internet mobile medical system.
杂志排行
Global Smart Medicine的其它文章
- SWOT analysis of static data backup media
- Research and application of information extraction technology in clinical medical records
- Application based on integration platform and big data center
- Instructions for Authors Journal of Global Smart Medicine
- Practical exploration of artificial intelligence in the field of medical nursing care
- Discussion on Internet of Things communication technology and its general development trend
