A Quantum Authorization Management Protocol Based on EPRPairs
2019-06-12YanChangShibinZhangLiliYanGuihuaHanHaiquanSongYanZhangXueyangLiandQirunWang
Yan Chang ,Shibin ZhangLili YanGuihua HanHaiquan SongYan ZhangXueyang Li and Qirun Wang
Abstract:Quantum authorization management (QAM)is the quantum scheme for privilege management infrastructure (PMI)problem.Privilege management (authorization management)includes authentication and authorization.Authentication is to verify a user’s identity.Authorization is the process of verifying that a authenticated user has the authority to perform a operation,which is more fine-grained.In most classical schemes,the authority management center (AMC)manages the resources permissions for all network nodes within the jurisdiction.However,the existence of AMC may be the weakest link of the whole scheme.In this paper,a protocol for QAM without AMC is proposed based on entanglement swapping.In this protocol,Bob (the owner of resources)authenticates the legality of Alice (the user)and then shares the right key for the resources with Alice.Compared with the other existed QAM protocols,this protocol not only implements authentication,but also authorizes the user permissions to access certain resources or carry out certain actions.The authority division is extended to fin-grained rights division.The security is analyzed from the four aspects:the outsider’s attack,the user’s attack,authentication and comparison with the other two QAM protocols.
Keywords:Quantum authorization management,entanglement swapping,fin-grained rights division.
1 Introduction
Now,data and communications are omnipresent.The problems of security have come to assume an unprecedented importance.Cryptography is the approach to protect data secrecy in public environment.Both classical cryptosystems and quantum cryptography can solve the problems of security.However,the latter has shown the advantage of higher security because of the strong security basis assured by physical principles.Therefore,quantum cryptography has attracted a great deal of attention now.
Quantum cryptography,such as quantum key distribution (QKD)[Bennett and Brassard (1984)],quantum secure direct communication (QSDC)[Long and Liu (2002)],quantum identity authentication (QIA)[Dusek,Haderka,Hendrych et al.(1999)],quantum secret sharing (QSS)[Hillery,Buzek and Berthiaume (1999)],quantum signature (QS)[Yang,Lei and Liu (2016)],quantum private query (QPQ)[Gao,Qin,Huang et al.(2019);Wei,Cai,Liu et al.(2018);Gao,Liu,Huang et al.(2015)] provide unconditional security in theory,since the security is assured by the quantum mechanics principles rather than difficulty of computation.Entanglement swapping is a special property of entanglement states,which entangles two quantum systems that originate from independent source and do not share any common past.Entanglement swapping as an important characteristic of entangled particles has been widely used in constructing quantum repeaters and many other -quantum cryptographic protocols.By using EPR pairs and entanglement swapping,[Zhang and Man (2004)] presented DQSDC schema.Later,Wang et al.[Wang,Zhang and Tang (2007)] put forward QSDC schema and multiparty QSS protocol also by using EPR pairs and entanglement swapping.Alexander et al.[Alexander,Claudia and Zhang (2008)] proposed multistage entanglement swapping,which was used as quantum repeater,improved the distance of quantum transmission.
Privilege management infrastructure (PMI)is an application to provide authorization service management.In classical network,authorization is the act of verifying that a user is allowed to access a resource,which confirms that a user has a permission to carry out an action,such as to gain access to a specific online resource.In fact,privilege management (authorization management)includes authentication and authorization.Authentication is to verify a user’s identity.Authorization is the process of verifying that an authenticated user has the authority to perform an operation,it is more fine-grained [Mark (2005)].In most classical schemes,the authority management center (AMC)manages the resources permissions for all network nodes within the jurisdiction.If the user Alice wants to access the resources of the owner node Bob,Alice must issue a request to the AMC.The AMC will confirm the identity of Alice,then with the help of AMC,Bob and Alice share a key for accessing resources.However,the existence of AMC may likely be the weakest link of the whole scheme.
Quantum authorization management (QAM)is the quantum scheme for PMI problem.At present,the relevant reports are very few.Zhang et al.[Zhang,Xu,Tang et al.(2007)] proposed a simple quantum authorization scheme,which is a quantum scheme of password passing in basic digest authorization scheme.In Zhang’s scheme,the user either can access all the resources of the owner,or they can access none.This is a coarser-grained rights division.They do not divide the rights further.Akshata et al.[Akshata,Srikanth and Srinivas (2014)] put forward a multipartite protocol in a counterfactual paradigm,which is essentially a quantum scheme of certificate authorization (CA)in e-commerce.In Akshata’s protocol a semi-honest third party is introduced.Alice issues certificates in the form of digital signatures and public-private keys.
In our protocol,we propose a quantum authorization management (QAM)scheme based on entanglement swapping.Bob (the owner of resources)authenticates the legality of Alice (the user)and then shares the right key for the resources with Alice.Compared with the other two QAM protocols [Zhang,Xu,Tang et al.(2007);Akshata,Srikanth and Srinivas (2014)],our protocol not only implements authentication,but also authorizes the user permissions to access certain resources or carry out certain actions.Our authority division is more detailed (fine-grained rights division).We analyze our security from the four aspects:the outsider’s attack,the user’s attack,authentication and comparison with the other two QAM protocols.
2 The description of the protocol
On assumption that,Mresources are included in Bob’s site,each resource can be denoted as binary stringXiL={x1,x2,...,xL} with lengthL,wherexL∈{0,1},i={1,2,...,M};Bob maintains a list of resource access rights for each user,while Bob has the identity information of each user.Alice is one of the user with identity information IDA(a binary string),she can access the resourcesand.Our idea is to help Bob confirm the identity of Alice and distribute a pair of secret key between Alice and Bob which is known completely to Bob and partly to Alice.Here we define Bob’s key asKM={K1L,,...,},where={k1,k2,...,kL},kL∈{0,1}.Then Alice’s key should beKiLand.The scheme is to help them to complete the task safely.
To start with,we describe entanglement swapping of EPR pairs simply.Suppose that |0> and |1> are the horizontal and vertical polarization states of a photon,respectively.Four Bell states are represented as

Suppose that photon pairs 1 and 2,3 and 4 are instates.The following equation holds:
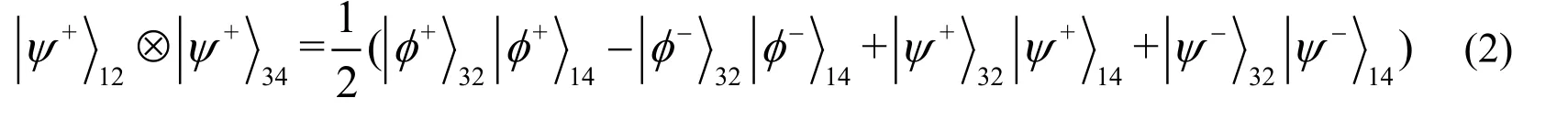
If we perform Bell basis measurements on the photon pair 2 and 3,photon pair 1 and 4 entangles.For example,if the measurement result isthe state of photon pair 1 and 4 isThe entanglement swapping characteristic is also workable for multi-EPR-pairs.
Step 1.Bob prepares a series of Bell statesandAll particle 1 (particle 2)instates compose particle 1 (particle 2)sequence.All particle 3 (particle 4)instates compose particle 3 (particle 4)sequence.Then Bob sends particle 1 sequence to Alice,and retains particles 2,3 and 4 sequence in his own hand.
Step 2.Bob measures all particle pairs 2 and 3 with Bell basis,and records the measurement results.By doing so,all particle pairs 1 and 4 entangle.
Step3.Bob chooses a random subset4BTUof particle 4 sequence and tells Alice the positions.Particles 1 at the corresponding positions form subset1ATU.Particles inUBT4andUAT1compose a random subsetUTof EPR pairs.These EPR pairs are used to detect the entanglement of EPR pairs that Alice and Bob share.Bob measures particles inUBT4withB0=σZorB1=σXbasis randomly.Alice measures particles inUAT1withbasis randomly.Alice and Bob announce their basis/measurement-result pairs inTU.We define {0,1}x=as binary input of Alice’s device,where 0x=and 1x=denote the measurement basis0Aand1Arespectively;y={0,1} is defined as binary input of Bob’s device,wherey=0andy=1denote the measurement basis0Band1Brespectively.We define {0,1}a=and {0,1}b=as the binary outputs of Alice and Bob respectively.Bob calculates the CHSH polynomialWhere the 〈axby〉 is defined asP(a=b|xy)-if the joint state of particles 2 and 3 isAs analyzed in [Pironio,Acin,Brunner et al.(2009)],the qubit measurementsZσ,andXσmaximize the CHSH polynomial for Bell states.Therefore,if the results violate the CHSH inequality (S≤2),Bob thinks that they share the correct entangled states,Bob continues to implement the protocol.These particles for eavesdropping detection inUTand the corresponding particles 2 and 3 are discarded.Otherwise,it is indicated that the particle pairs are not correct entangled pairs,so Bob terminates the protocol.
By detecting in this step,even if the source and measuring equipment are completely controlled by Eve or provided by Eve,we can find whether the particles 1 and 4 that Alice and Bob share are in the correct entangled states.Then,in the following steps,because of monogamy of non-local correlations,Bob can confirm the identity of Alice correctly and a pair of keys used for accessing resources with correct right can be distributed between Alice and Bob securely.
Step 4.Bob verify the identity of Alice by means of quantum teleportation.The detailed procedure is as follows:
(1)Alice prepares a single photon sequence SIDAaccording to IDA(identity information of Alice),the rule is:if theith bit of IDAis 0,Alice prepares |0> state,otherwise Alice prepares |1> state.
(2)Alice chooses some particles from particle 1 sequence randomly,and performs Bell basis measurement on particles in SIDAand particles she chooses from particle 1 sequence.(3)Alice publishes the positions she chooses and the corresponding measurement results.Then Bob can recover SIDAon particle 4 sequence by performing unitary operations on particles 4 according to Alice’s measurement results.For example,if theith measurement result of Alice isBob performs unitary operationon theith particle 4,by doing so Bob teleports the state of theith particle in SIDAon theith particle 4.
(4)Bob measures SIDA(he recovered in (3))in Z basis and converts it to binary sequence ID’A,the rule is:If the Bell basis measurement result of particle 2 and 3 in step 2 isBob uses |0> to denote 0,and|1> to denote 1;otherwise,he uses |0> to denote 1,and |1> to denote 0.
(5)By comparing ID’Aand IDA,Bob can know Alice is legitimate or not.
If Alice is legitimate,Alice and Bob discard the EPR pairs they used to verify the identity of Alice,and the protocol continues.
Step 5.Alice and Bob randomly select Z-basis or X-basis to measure particles 4 and 1 respectively.Alice and Bob publish their measurement basis one particle by one particle,until they have 2Lpairs of particles with the same basis,then Alice and Bob stop publishing the measurement basis.Alice and Bob record the measurement basis and measurement results of the 2Lpairs respectively.
Step 6.Alice and Bob drop the EPR pairs that have been measured.Then Alice and Bob convert the 2Lmeasurement result pairs to binary string keysand,whereKiL={k1,k2,...,kL},kL∈{0,1}.The detailed process is as follows:
According to the Bell basis measurement results of particles 2 and 3 at the 2Lpositions which are obtained in Step 2,Bob can infer each other’s measurement results.For example,if the state of 2-3 pair isBob infers that the state of 1-4 pair isthen Bob knows that his measurement result is the same with Alice’s result,thus he records his result aski,i∈{1,...2L},ki∈{0,1} (the rule:|0> or |+> denote 0,|1> or |-> denote 1);otherwise Bob knows that his measurement result is contrary to Alice’s result,thus he records his result as.
According to the rule:|0> or |+> denote 0,|1> or |-> denote 1,Alice also records her results aski,i∈{1,...2L},ki∈{0,1}.By doing so,Alice and Bob share a raw key {k1,k2,...,k2L} with length 2L.Bob and Alice divide the raw key {k1,k2,...,k2L} into two parts,each with lengthL.Then,Alice and Bob know={k1,k2,...,kL} and={k1+L,k2+L,...,k2L},ki∈{0,1}.
Step 7.Bob divides his remaining measurement results intoM-2 parts,each part hasLresults.According to the rule:|0> or |+> denote 0,|1> or |-> denote 1,Bob converts theM-2 parts intoM-2 binary string keyseach key with lengthL.Then Bob insertsandin front of theith andjth key inKM-2respectively.So far,Alice and Bob have shared a set of keysKM={K1L,K2L,...,},which is known completely to Bob and only theith andjth keys to Alice.Then Bob encrypts his resources with the secret keysK1L,K2L,...,KMLin order,Alice can only access theith andjth resources.
3 Security analysis
3.1 The outsider's attack
First of all,the outsider eavesdropper Eve cannot attack successfully by providing not perfect quantum carriers (EPR pair)[Wang,Yang and Mousoli (2018)] when she provides or controlling the equipment.The reason lies in:If Eve provides not perfect EPR pairs,Alice and Bob will find her behavior by checking the violation of CHSH inequality in Step 3.
Secondly,in our protocol,the illegal user Eve cannot pass the identity authentication in Step 4,therefore the protocol will not distribute right key for him.
Thirdly,the identity of Alice is passed to Bob by means of quantum teleportation,which ensures the validity of authentication and absolute security of the identity,therefore the identity can be reused securely.
3.2 Alice's attack
In a secure quantum authorization management protocol,Alice is not wanted to access additional resources outside of her rights.Then the purpose of Alice’s attack is to try to access additional resources.
If Alice is untrustworthy,she can collaborate with Eve,or they are the same person.In this case,Alice will provide untrustworthy devices and try to trick Bob by sending him pure states.However,if Alice sends Bob pure states,the CHSH inequality violation check of Bob in Step 3 will fail,then Alice’s behavior is found by Bob,which leads to a termination of the protocol.Furthermore,Alice cannot publish unreal inputs and outputs in Step 3 to escape the CHSH check of Bob,because the Bell basis measurement in Step 2 will lead to four stateswith equal probability 1/4,Alice does not know the state of each new EPR pair after entanglement swapping.That is to say,Alice does not know the relationship between particle 1 and 4.Therefore,wrong publishing of inputs and outputs of Alice will lead to failure of CHSH inequality violation check of Bob,which also results in a termination of the protocol.
To know more keys inKM-2,Alice may perform individual attack.For example,in Step 5 Alice measures particles dishonestly inbasis.Here,

By doing so,Alice can bias the measurement result of Bob.After Alice’s dishonest measurement,Bob’s corresponding particles collapse into stateorFor each particle,the probabilities that Bob obtains results+orare (1 sin 2 )2θ+or (1 sin 2 )2θ- respectively;the probabilities that Bob obtains resultsare cos2θor sin2θrespectively.Because in Step 5,Bob does not publish the measurement basis of the remaining (M-2)Lparticles,Alice guesses right the basis of each particle with probability 1/2.Alice will record the state with larger probability as Bob’s measurement result.For example,if Alice guesses the measurement basis of Bob is X-basis,and (1+sin 2θ)2>(1-sin 2θ)2is satisfied,Alice will recordas Bob’s measurement result.However,because Alice does not know the relationship between particle 1 and 4,she cannot infer Bob’s key.Therefore,if Alice guesses the measurement basis of Bob is X-basis,the probability that Alice knows one bit ofisp=(1+sin 2θ)4when (1+sin 2θ)2>(1-sin 2θ)2 is satisfied;and isp=(1-sin 2θ)4when (1-sin 2θ)2>(1+sin 2θ)2is satisfied;if Alice guesses the measurement basis of Bob is Z-basis,the probability that Alice knows one bit ofisp=cos2θ2when cos2θ> sin2θis satisfied;and isp=sin2θ2when sin2θ> cos2θis satisfied.Obviously the four probabilityp=(1+sin 2θ)4,p=(1-sin 2θ)4,p=cos2θ2 andp=sin2θ2 are all less than 1/2.Therefore,the probability that Alice obtains the keyKiLis less thanThat is to say,through this attack,Alice cannot get a better result than guess.The probability that the eavesdropper guesses right the keyis.WhenL=4,=0.0625,that is to say,whenL≥ 4,the probability that the eavesdropper guesses right the keyKiLis close to zero.
Furthermore,this attack will lead to error bits which contribute a key for Alice,and thus Alice’s key is inconsistent with Bob,which will cause Alice fails to access resourcesXiLand.Therefore,we think that the user Alice will not cheat to access extra resources at the cost of getting failed access of resourcesand.
3.3 The analysis of authentication
Bob kept the binary identity information of Alice (IDA)in advance.When Bob authenticates the identity of Alice,the identity information is converted to single phone sequence and passed to Bob by means of quantum teleportation,which ensures the validity of authentication and absolute security of the identity information,so that the identity information can be reused securely.
3.4 Comparison with the other two QAM protocols
In Tab.1,we compare our protocol with the other two QAM protocols [Zhang,Xu,Tang et al.(2007);Akshata,Srikanth and Srinivas (2014)].
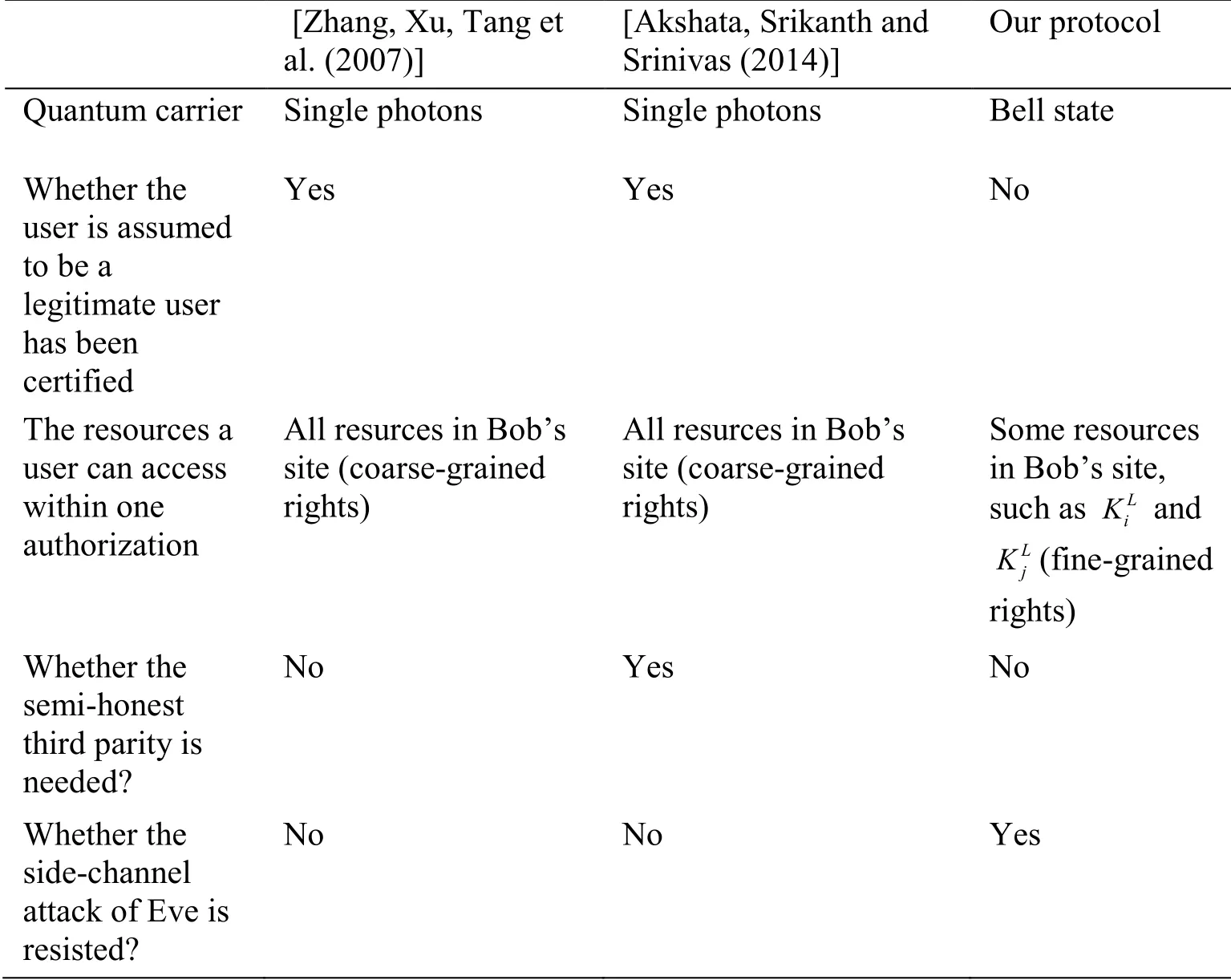
Table 1:The comparison of our protocol with the other two QAM protocols
In Zhang et al.[Zhang,Xu,Tang et al.(2007)],Alice is an authenticated user of a server Bob.Alice is supposed to have shared a key with Bob previously.Bob does the authorization checking.Once Alice passes Bob’s authorization checking,she can access all resouces at Bob’s site.It is a coarse-grained rights division.Zhang et al.[Zhang,Xu,Tang et al.(2007)] can implement authorization checking without the help of the semihonest third party.However,if Eve controls or provides the source and equipment,the side-channel attack of Eve cannot be resisted.
In Akshata et al.[Akshata,Srikanth and Srinivas (2014)],Alice is supposed to be an authenticated user in advance.With the help of the semi-honest third party,Alice and Bob share a key.Therefore,Akshata et al.[Akshata,Srikanth and Srinivas (2014)] is a quantum key distribution scheme in essence.If Eve controls or provides the source and equipment,the side-channel attack of Eve also cannot be resisted.
In our protocol,Alice is not supposed to be an authenticated user in advance.Bob does the authentication checking firstly.Then Alice and Bob share a pair of secret keys which is known completely to Bob but partly to Alice.Our protocol can implement authentication and fin-grained rights division without the help of the semi-honest third party.Furthermore,because of the checking of CHSH’s inequality violation,even if Eve controls or provides the source and equipment,the side-channel attack of Eve can be resisted.
4 Conclusion
Here,the protocol has extended the authority division to fin-grained rights division.The protocol not only implements authentication,but also authorizes the user permission to access certain resources.Security of the protocol have been analyzed against the user’s attack and outsider’s attack.
Acknowledgments:This work is supported by NSFC (Grant Nos.61572086,61402058),the Application Foundation Project of Sichuan Province of China (Grant No.2017JY0168),the National Key Research and Development Program (No.2017YFB0802302),Sichuan innovation team of quantum security communication (No.17TD0009),Sichuan academic and technical leaders training funding support projects (No.2016120080102643),the Fund for Middle and Young Academic Leaders of CUIT (Grant No.J201511).
杂志排行
Computers Materials&Continua的其它文章
- Development of Cloud Based Air Pollution Information System Using Visualization
- A Learning Based Brain Tumor Detection System
- Shape,Color and Texture Based CBIR System Using Fuzzy Logic Classifier
- LRV:A Tool for Academic Text Visualization to Support the Literature Review Process
- Application of Image Compression to Multiple-Shot Pictures Using Similarity Norms With Three Level Blurring
- On Harmonic and Ev-Degree Molecular Topological Properties of DOX,RTOX and DSL Networks
