Technical Analysis of Security Management in Terms of Crowd Energy and Smart Living
2018-12-26MDShahrukhAdnanKhanMuhammadAhadRahmanMiahShaikhRashedurRahmanMirzaMursalinlqbalAseeflqbalAravindCVChuaKeinHuat
MD Shahrukh Adnan Khan* | Muhammad Ahad Rahman Miah | Shaikh Rashedur Rahman | Mirza Mursalin lqbal | Aseef lqbal | Aravind CV | Chua Kein Huat
Abstract—In this paper, a technical and statistical analysis of security system and security management is provided for crowd energy and smart living.At the same time, a clear understanding is made for crowd energy concept and next generation smart living.Various case examples have been studied and a brief summary has been provided.Furthermore, a statistical analysis has been provided in terms of security management in smart living where it is found that young technocrats give the highest importance to security management in smart living.Last but not the least, current limitation, constraints, and future scope of security implementation have been discussed in terms of crowd energy clustered with next generation smart living.
1. lntroduction
The industrial development of the world has raised the prosperity of life of at the cost of exhausting limited natural resources and damaging the environment.The consumption of fossil fuels, on which the industrial development has been largely based, has been recognized as a major cause of climate change.The impacts on the global ecosystem resulting from climate change are in turn expected to lead to substantial economic losses.Moreover, the global pollution due to traditional sources of energy moves scientists to search for other sources of green energy and to create a common platform for both energy producer and consumer.Our nation’s electric power infrastructure known as “the grid” is rapidly reaching to its limit.We may get the electricity supply but the risks associated with that depending on the traditional structure are increased with the rising demand of the grid.So it is very essential to decentralize the entire power system to make it more secure and sustainable.
Smart living is altogether a new concept where technology adopts into day-to-day life to provide a comfortable,safer, convenient, and sustainable environment.Gradually, many countries around the world are trying to adopt the concept of smart living and related technology.Basically smart living is an idea which integrates technology with humanity.Smart living brings technology to all phases of human life necessity like food, housing, health,medication, education, transportation, and entertainment.The smart technology allows people to achieve smart living into all sectors of daily life and therefore a better world for upcoming generations.This paper brings out the new concept of crowd energy clustered into next generation smart living.This has been a complete new theory which is still under observation and indeed a very promising and emerging concept.But a very little study has been conducted in this short period of time.This paper finds the gap and tries to give a clear understanding of what crowd energy and smart living are as well as provides an analytical discussion on security management for both the emerging concepts.
2. Crowd Energy
Crowd energy is the combined effort of individuals or profit or non-profit organizations, or both, pooling their resources through online information and communications technology applications (ICT-applications) to help to implement the energy turnaround.It holds the concept of decentralization (production, storage, and consumption of renewable electricity) and a considerable change in society, economy, and politics[1].According to [2], ICT will play an essential role in future power grids.
In addition to the crowd energy concept, the bidirectional flow of power between the grid and other consumers through a reliable and well-secured communications network is essential.A system controller will ensure a bidirectional interaction (cyber and physical) between the utility-side and the customer-side.This unit should be distributed, overseeing the local dispatch of energy in a way to optimize system reliability, quality, and the real-time trading of electricity.Moreover, a consumer can be turned into a producer whenever he supplies the electric energy produced in excess to his requirement.Intelligent generation storage load (iGSL) cells are the primary elements of the crowd energy concept.Introducing many cells in a network, connecting them by bidirectional communications lines, and finally processing the information in a crowd management system, yield to iGSL cells crowd.One issue is that the structure of the crowd does not have to be fixed.It is rather can be stated that the iGSL cells can and should vary over time.
Crowd energy system should be a socio-technological system.The mutual dependency between grid development and changing roles of end users must be considered.The iGSL cells make an energy consumer to become an energy producer.On the other hand, the prosumer is a new player in the energy (electricity) market and the prosumer is one of the important factors within the crowd energy concept helping to implement the energy turnaround.Fig.1 shows a connection between traditional generation units with the prosumers.Now it is necessary to focus on the socio-psychological part of the crowd energy management side.When “the end points of consumption of electricity” (the electricity consumers) get incorporated to produce and store energy(electricity), they should have share their own electricity to the others after fulfilling their own demand.But why should they share? Motivations are required for the consumer to becoming a producer to share his own electric energy.The fields of human motivations are categorized into intrinsic and extrinsic ones.As Fig.2 shows[3], the set of measures is directed to influence the intrinsic and extrinsic motivations of consumers to deploy renewables and smart grid technology (SGTs), participate in crowd energy, improve efficiency and reliability in an energy system, as well as increase public awareness and positive feedback[4],[5].At the same time the policy maker decision in the favor of crowd energy is necessary[6].
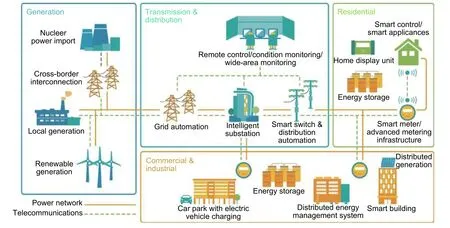
Fig.1.Traditional generation unit and the prosumers are connected with a bidirectional communications line in the concept of crowd energy.
3. Security Management in Crowd Energy
The generation, transmission, and distribution of energy are among the most vital prerequisites for the functioning of modern societies[7].ICTs are used to monitor, control, and operate power generation plants and power distribution within electric power supply system[8].Process control systems, e.g., supervisory control and data acquisition systems (SCADA systems), and other ICT systems used within electric power supply systems, are vulnerable to a multitude of physical, electromagnetic, and logical threats, both natural and man-made[9].The recent trends are towards more general purpose software solutions; and towards the use of the Internet for communications related to operations and management of remote processes and production systems.The security issue should be maintained in crowd energy conception.A power system with crowd energy conception is a very complex network which contains millions of devices and whole components are connected with each other.So the security issue is a big concern for this huge network.
Crowd energy provides electricity demand from the centralized and distributed generation stations to the customers through transmission and distribution systems.The grid is operated, controlled, and monitored by using ICTs.These technologies deliver the power in an efficient way to the customers at a reduced cost.Crowd energy conception is based on two-way communications between prosumers and electric power generation and distribution companies.The two-way digital communications ensure the proper electricity consumption.Security system should be much reliable so that the communications channel works properly.Three main security objectives must be considered in the crowd energy system: 1) availability of uninterrupted power supply according to user demands, 2) integrity of communicated information between the prosumers and entity, and 3) confidentiality of user’s data and the assurance of system safety.
Crowd energy network is a complex formation of different types of equipment which makes the system more vulnerable compared to the conventional power system network.These vulnerabilities might allow attackers to access the network, break the confidentiality and integrity of the transmitted data, and make the service unavailable.The following two vulnerabilities are the most serious in the crowd energy network:
■ Unorganized and weak communications between utility and prosumers might cause a lot of bad decisions,which creates too much vulnerability.
■ Having many stakeholders might give rise to a very dangerous kind of insider attacks which can create major damages.
And the followings are the recommendations to the vulnerabilities[10],[11]:
■ Ensure prosumers security when they are not in home.
■ Provide the security of several intelligent devices which are involved in managing both the electricity supply and network demand.
■ Physical security is needed for many components which are out of the utility’s premises.
The attackers can cause a wide variety of attacks, which can be classified into three main categories[12],[13]:Component-wise, protocol-wise, and topology-wise.These three attacks can be further divided into different categories[14]-[17], such as:
1) Malware spreading;
2) Access through database links;
3) Compromising communications equipment;
4) Injecting false information;
5) Network unavailability;
6) Modbus security issue.
To prevent the attackers attack and to ensure the crowd energy network security, the following steps may be taken into consideration[18],[19]:
1) Strong authentication;
2) Mechanisms should be used to verify the prosumer identity;
3) Malware protection system should be incorporated in both the producer and consumer ends;
4) Network intrusion prevention system (IPS) and network intrusion detection system (IDS) technologies should augment the host-based defenses to protect the system from outside and inside attacks;
5) To ensure the security of the system, vulnerability assessments must be performed at least one in a year;
6) Awareness programs should be incorporated to educate the network users about the security of the system for using network tools and applications;
7) Control system and IT security engineers should be equally involved in securing with the crowd energy network;
8) Security issues must be considered as a part of the crowd energy design;
9) A robust authentication protocol is needed while communicating between the prosumers.Fig.3 shows a security system model in crowd energy system.
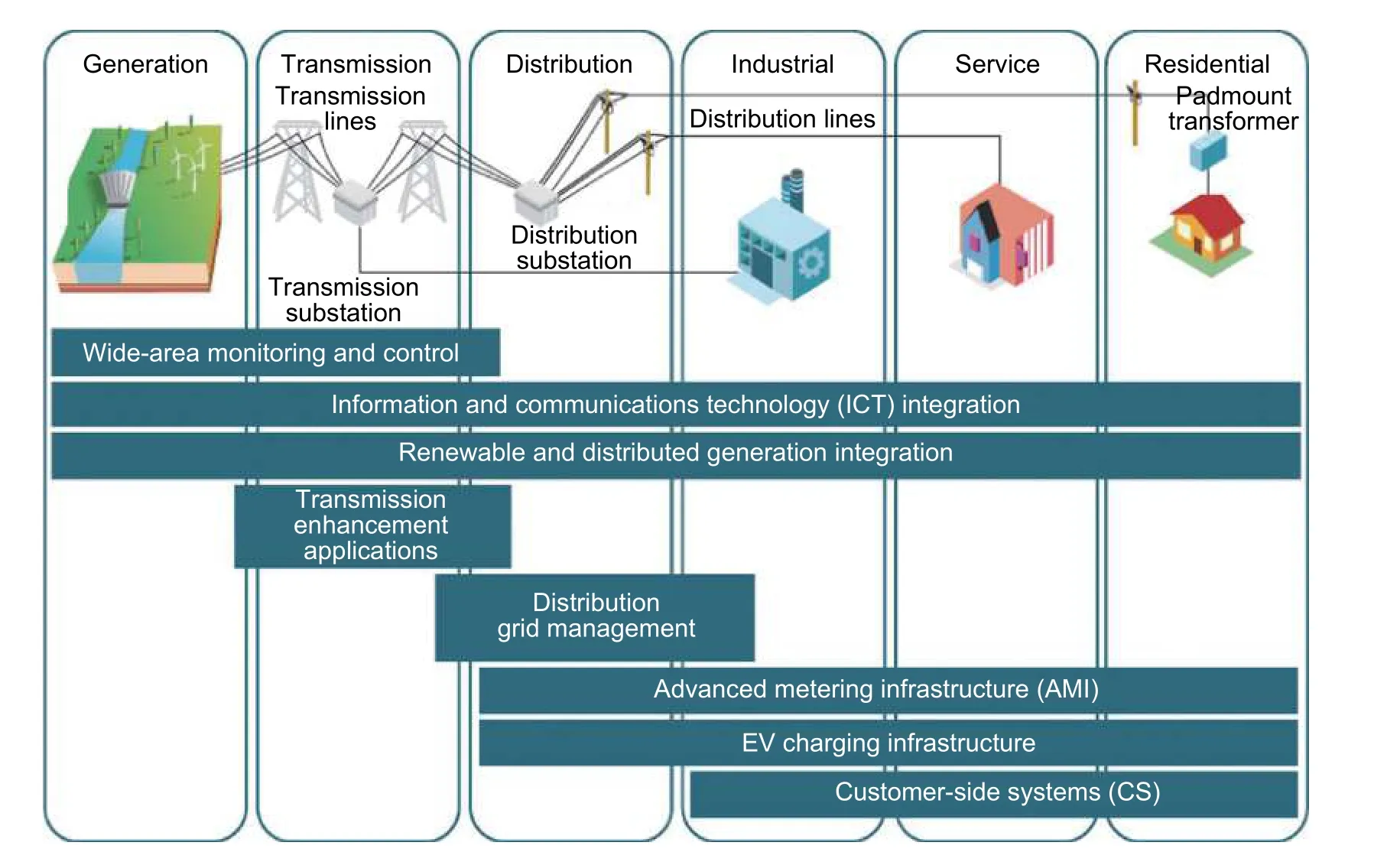
Fig.3.Model security based design for crowd energy power system.
The following Section 4 describes the existing crowd energy models/systems so that the security layout of existing smart living technology can be found out, as shown in Fig.4.
4. Case Examples of Crowd Energy
Fig.4.Proposed security management model for crowd energy system.
According to [20], S.Abolhosseini et al.proposed that improving energy efficiency is an important way to reduce energy use and thereby CO2emissions, and to overcome the climate change problem.Energy efficiency for electricity networks can be considered in different stages, such as power generation, transmission, distribution, and consumption.For this purpose, thirty different energy efficiency technologies are available, including electric vehicles, combined heat and power, virtual power plants, crowd energy, and smart grid.According to [21], R.-H.Zheng et al.considered one of the most prevalent ways to boost investment in renewable energy generation is to motivate individuals to participate into green energy investment and generation.However, not all individuals are willing or able to install on-site renewable energy generation at their homes.Therefore, a special crowd funding green energy investment has been recently introduced in the form of community shared renewable energy projects and it can be incorporated to crowd energy system.
5. Smart Living
Smart in general is a common term which refers knowledgeable, efficient, more controllable, adoptable, and sustainable.The definition of smart is different when it comes to technological advancements.J.Vasauskaite et al.precisely defined the term “smart” in [22] as according to them it mostly goes parallel to “intelligent”.In addition, they mentioned five characteristics of “smart” which are adaptable, sensing, inferring, learning, and anticipating[22].
As renewables along with distributed smart grids, real time monitoring systems are being given importance constantly, the definition of “smart living” is changing every decade to further technological enhancements.Smart living is all about smart lighting, smart water, smart traffic, smart parking, smart building, smart industry, smart environment, location/context based service, and more.Smart living integrates all stakeholders such as people, machines, devices, and environment[23]-[25].One of the major components of smart living is smart home.Smart home adapts smart designs and accommodates smart devices, intelligent technology, and sensors.But at present smart home means having efficient appliances and control devices to control lighting and temperature.Smart home design concepts also reflect the change in perception to adjust the needs of the environment and consumers, which can comprise of things such as regulations of room lighting and temperature and control of other machines and devices.The smart house would combine a number of smart communications systems which help residents to completely manage their own environment.To be precise, a smart home would be user-centric[25],[26].
In brief, smart home incorporates smart energy, smart mobility, digital healthcare, smart connectivity, smart shopping, home automation, smart comfort, and smart security.
6. Security Management in Smart Living
There is a word “stay smart, stay secure”.Security management is a big issue in implementing smart living components.All the components are connected through various hardwares and softwares.A large number of devices, transmitting huge amount of data through many different APPs, are controlled through a secured management platform.Surge in data requires a new approach for speed, agility, and security.One of the technologies is being used extensively in smart living/smart house is Internet of things (IoT).But IoT has a high security issue in terms of data handling.Moreover, the configurations of some devices (sensors) are too weak to ensure protections.The hardware side or the device connectivity is not only guilty for this, but also the shortage of recognized security standards dedicated for the system.Fig.5 shows a typical structure of security management system for smart living[27].
Security threats to smart home environments are existent and may be applicable to all devices and services.Sometimes the types of threats vary in different applications but they may cause significant damage in the overall structure and the environment may collapse.Thus, the following threats are still applicable such as physical attacks, unintentional damage, disasters/outage, damage/loss, and failure/malfunction.
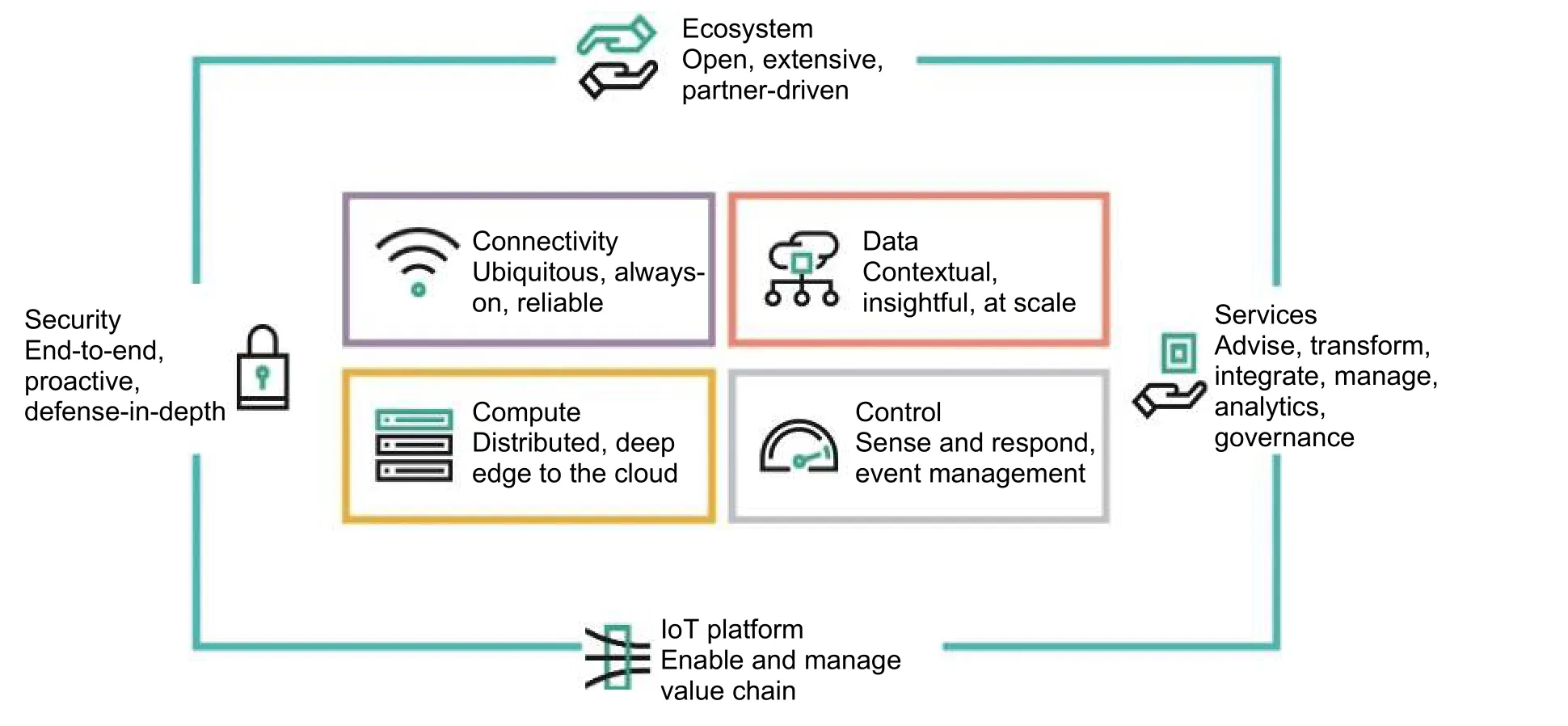
Fig.5.Smart living security management[27].
Table 1 represents the concise interpretation of security concerns and defines which scenario disrupts security goals in the smart home[27],[28].Therefore, security requirements, such as user and device authentication, monitoring the network integrity, availability, and confidentiality are desired.Fig.6 might be a pathway to implementation of smart living addressing the security concerns.First of all, a plan should be carried out as an initialization of smart living.This includes the type of target consumer, project location, the environment, and more importantly the budget.The value proposition should be accounted carefully and express the result to the target consumer.Later,the project can be built to serve the target consumers as per their requirements and needs.After installation of the project components, test run should be processed to find out if there is any bug, security issues, customer concerns, etc.Finally, after the necessary optimization, the project may continue for a longer period of time.
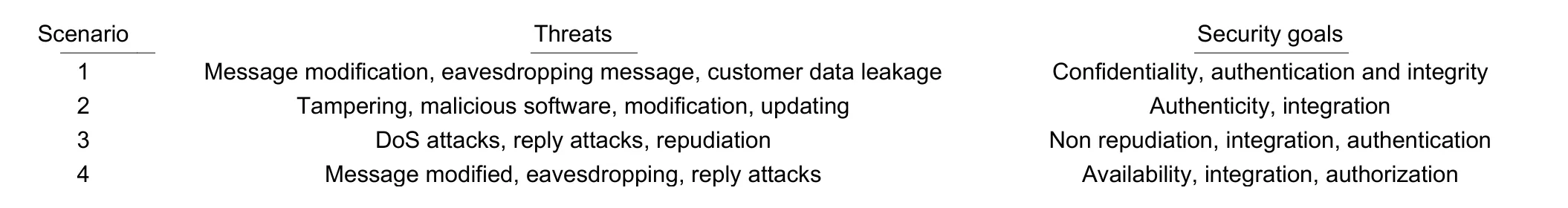
Table 1: Smart home security challenges[28]
7. Case Examples of Smart Living
Smart living technologies are still facing a chasm due to some reasons: Value propositions are not yet clear;existing solutions do not meet client needs; existing solutions lack interoperability, data security is not fixed;and there are too few live examples.There are some smart living projects ongoing around the world.T-city of Germany and Panasonic eco idea house and aware home at Georgia represent these projects.Fujisawa sustainable smart town (Tokyo, Japan) brings smart living to 1000 apartment residents[29]-[33].
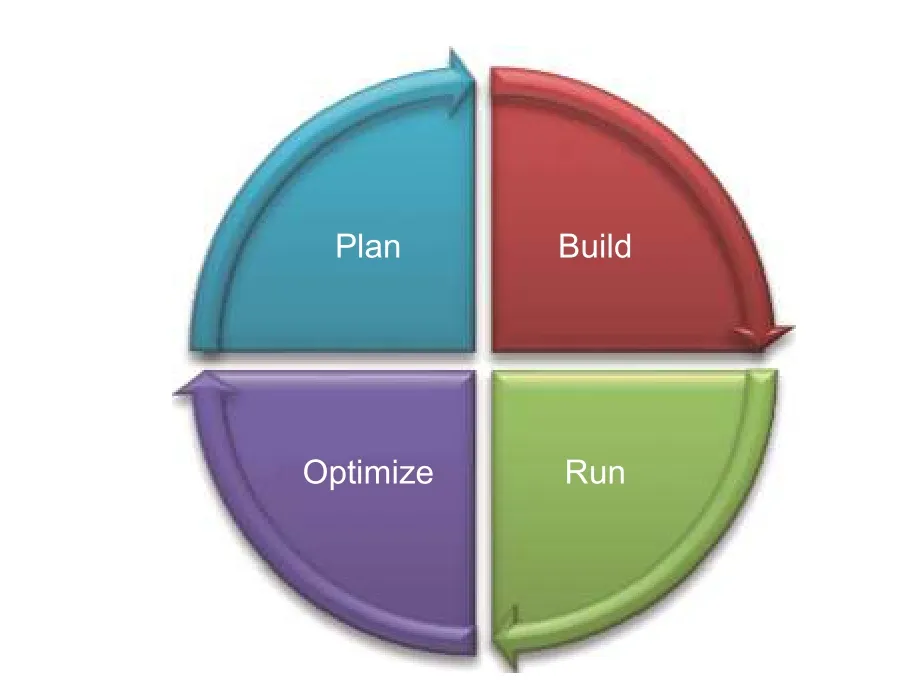
Fig.6.Pathway for a sustainable smart living.
By creating a connected, sustainable, and comfortable living with innovative technology, the smart town offers solutions to energy management, security, assisted living, and mobility.In Adlershof (Berlin, Germany), 69 apartments, 29 studios, and 10 shops are practicing smart living with vision to create a real environment of selfdetermined future living at high comfort levels for everyone, to provide a live development, testing, and presentation platform with real user data, to develop key use cases and outcome technological challenges, and to drive public acceptance of smart home technology and connected life[23].The above projections show that smart living technology concept has not merely been limited to cities (Germany), but also to schools (Georgia Tech.), and shops and enterprises (Panasonic).This shows that smart living technology is getting world’s attention[33]-[35].
8. Statistical Analysis of Technical Know-How of Security Management among Technocrats
The survey was conducted by asking over two hundred respondents of different ages of technocrats, coming from engineering background.The survey portrays the smart living importance on current generation technocrats,mostly coming from engineering background. In addition, the reflection of security importance in energy management on those technology friendly people also has been tried to find out.Fig.7 shows the age range of participants on the survey where it is clearly seen that the young generation dominates.This was made intentionally as smart living and security management in smart energy is said to be the next generation technology.
8.1. Question 1: How lmportant ls lt to Have a Secure Supply of Oil, Gas, Coal, and/or Uranium?
Securing the supply of fossil fuels is one of the most crucial components of energy security.Fig.8 reveals that this dimension is ranked at the top position by a majority of respondents.Interestingly, survey results revealed that people with different ages, gender, and levels of education prioritized the security of supply of primary energy resources.Almost 87 percent of the respondents feel it as a pure necessity.
8.2. Question 2: How lmportant ls lt to Have Small-Scale, Decentralized Energy Systems?
For next generation smart security management, decentralized energy system (DES) plays one of the most important roles.Most of the security management needs to be implemented in the next generation, such as building to grid (B2G) and vehicle to grid (V2G) technologies which are the major parts of DES.Consequently, the smart renewables, including vertical axis wind turbines for low wind speed, low cost solar panels with smart sensors, real time smart monitoring for hybrid renewable interface, supercapacitor based switched control energy harvesting, and high data through multi-channel wavelength division multuiplexing (WDM) based optical fibre, are being implemented for advanced living[36]-[39].The need of DES in smart living has been reflected in Fig.9.As a sign of favor against decentralization and towards large-scale, capital intensive infrastructure, Fig.9 shows that how this dimension differed among respondents.Although around 66 percent respondents thought that it is important to have decentralized and small scale energy systems for energy security, around 33 percent respondents opined oppositely.It reflects the growing recognition about small scale renewable systems.
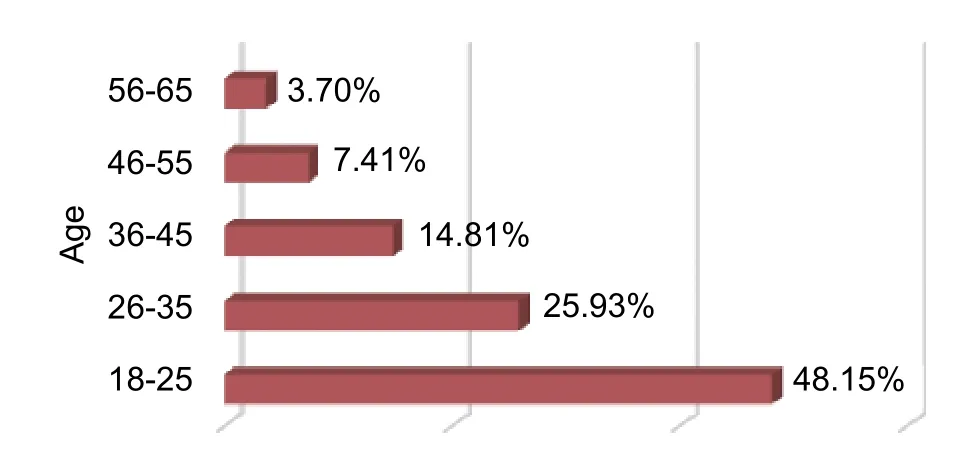
Fig.7.Age range of the technocrats participated in the survey.
8.3. How lmportant ls lt to Conduct Research and Development on New and lnnovative Energy Technologies?
Lastly, questions have been asked relating to the importance of encrypted security in smart home energy management system (SHEMS).Fig.10 illustrates that almost 85 percent of the respondents gave above average importance to security management on new and innovative energy technologies.The respondents,giving it the highest importance, were mainly the people with post-graduation degrees.
9. Conclusion: Summary,Limitation and Future Scope
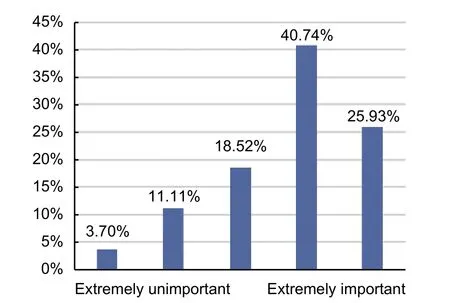
Fig. 9. Level of importance of having small-scale,decentralized energy systems.
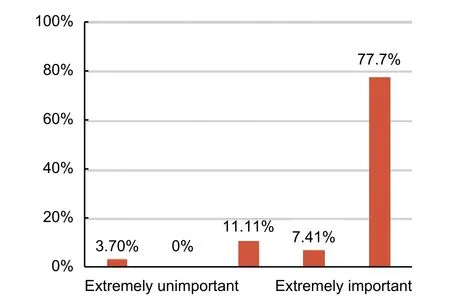
Fig.10.Level of important about encrypted security in SHEMS.
To summarize, it is not too much to say that the crowd energy concept is still a new theory and yet to be implemented in practical cases.The smart city living is surely the next generation planning and the current world is running with great pace at it.With the increase in renewables and breakdown in energy distribution, it is not too late to see a great smart-technological advance in this sector.The security management will definitely play a key-factor in the bidirectional flow of crowd energy clustered into next generation smart city living.
In conclusion, it was found that in terms of availability, the security of primary energy sources was amongst the most important dimensions.Although the rise of micro-grid and small scale renewable energy system is evident,decentralization was not as important to the respondents as security of supply.Young generation from Bangladesh with higher degrees from engineering level is giving security management to its utmost importance.
Acknowledgment
The authors would like to thank the support provided by the University of Asia Pacific and Institute for Energy,Environment, Research and Development (IEERD).
杂志排行
Journal of Electronic Science and Technology的其它文章
- Guest Editorial____________________________Special lssue on Energy-Efficient Technologies—Crowd Energy Applications
- lntegrating Smart Building Energy Data into Smart Grid Applications in the lntelligent Secondary Substations
- Energy-Efficient Operation of Water Systems through Optimization of Load Power Reduction in Electricity Markets
- Options and Opportunities for Energy Management in Malaysian Grid Systems—Putrajaya as a Case Study
- lmplementation of Efficient B2G and V2G in Practical Cases
- lnvestigating Energy Prosumer Behaviour in Crowd Energy Using an lnteractive Model/Diorama
