Throughput Analysis of Dynamic Spectrum Anti-Jamming Multiple-Access in HF Communication Systems
2018-09-06YichaoZhuChaoGuoXiaoxueWang
Yichao Zhu*, Chao Guo, Xiaoxue Wang
China Ship Research and Development Academy, Beijing 100101, China
Abstract: A multiple-access networking scheme based on the new dynamic spectrum anti-jamming system is proposed in this paper.The network consists of a center node and multiple user nodes. The center node detects spectrum holes in the operation band periodically according to the user performance target.Detected spectrum holes are allocated to users who request communication. Throughput of this networking scheme is analyzed over a high-frequency (HF) interference channel.The effect of error correction coding and spectrum hole information transmission error is discussed. Throughput of this scheme and conventional frequency-hopping multiple-access (FHMA) scheme are compared. Results show that user performance increase leads to throughput decrease, which can be offset by error correction coding. If spectrum hole information transmission is in error, the throughput is not affected much as long as the bit error rate is below 10-2. Furthermore, throughput of this scheme is obviously superior to the throughput of FHMA scheme.
Keywords: dynamic spectrum anti-jamming;multiple-access communication; throughput;spectrum hole
I. INTRODUCTION
The material in this paper was presented in part at the National Electromagnetic Security and Control Conference, Beijing, China,June 2017.
Dynamic spectrum anti-jamming (DSAJ) is a new anti-jamming communication technique based on the idea of opportunistic spectrum access in cognitive radio [1-4]. Within the operation band of a DSAJ system, portions where there is no jamming or the power of jamming is below a particular threshold are considered as spectrum holes. DSAJ minimizes the detriment of jamming by transmitting information in spectrum holes and adjusting communication parameters according to the variation of jamming adaptively. Current researches on DSAJ are mainly focused on the point-to-point case. Performance of point-topoint DSAJ communications has been studied.Capacity, bit error rate (BER) and processing gain are theoretically analyzed over different channel conditions in [5-7]. Nevertheless, the DSAJ multiple-access problem has not been considered much. Few open literatures on this issue are found. Therefore, a new DSAJ multiple-access networking scheme is proposed in this paper. Throughput of this scheme and the influencing factors of the throughput are studied. Furthermore, throughput performance of this scheme and frequency-hopping multiple-access (FHMA) are compared, which shows the superiority of DSAJ.
A multiple-access networking scheme based on the new dynamic spectrum anti-jamming system is proposed in this paper.
This operation is suboptimal and only for the sake of analytical convenience. But despite its suboptimum,it does not change the superiority of DSAJ networking.
II. NETWORKING SCHEME
The DSAJ network consists of a center node and multiple user nodes. The networking scheme assumes that the distance between each two nodes is small so that the local electromagnetic environment of each node is similar. All nodes work in the same operation band, which is to be partitioned before communication starts. The band partition schematic is shown in figure 1. De fine Wssas the total bandwidth and Rcas the information rate. The whole operation band is divided into Nt=Wss/Rcadjacent and non-overlapping channels. The bandwidth of each channel is Rcand the center frequency of each channel forms the available frequencies of the system. If M-ary MFSK modulation is used, the system combines each adjacent M channels to obtain N1=Nt/M M-ary channels. All the N1M-ary channels are further divided into two parts. Each part is a subband called Gn, which consists of N=N1/2 M-ary channels1. The center node determines spectrum hole detection threshold according to the user performance target. All M-ary channels in the current Gn with jamming power below the threshold are selected as spectrum holes.Since the local electromagnetic environment is similar for all nodes, spectrum holes selected by the center node are also valid in the local area of each user node. Due to the time-variance characteristic of the wireless channel, Gn switch and spectrum hole detection must be performed periodically.
A schematic diagram of DSAJ network operation is shown in figure 2. In figure 2, node 0 is the center node, node 1 is the calling user and node 2 is the called user. Each node in the network has a signaling frequency outside the operation band (in the figure, fi(i=0,1,2)is node i’s signaling frequency). When node 1 is to initiate a call, it sends channel request information (including information of the called user) to node 0 at frequency f0(step 1) in a CSMA mode. Once the request is received, node 0 checks the spectrum hole allocation status. If there are non-allocated spectrum holes, channel number (shown in figure 2 as the frequency fa) corresponding to one of them is sent back to both the calling and called users (step 2), otherwise, node 0 rejects the request. If node 1 does not receive any response or is rejected, it can make channel request again after a random delay. Once the channel number is received, node 1 starts communication process in the allocated M-ary channel (Step 3). If communication process is over, an END message is sent from node 2 to node 0 and the channel is released (Step 4).After Gn is switched and spectrum holes are updated, node 0 re-allocates channels to users in communication first. If the number of users in communication is larger than the number of detected spectrum holes, communication is paused for all the users without allocating an updated channel. Their communications restart if there are channels being released and re-allocated to them.

Fig. 1. Band partition schematic of DSAJ multiple-access network.
III. CHANNEL MODEL
The channel model considered in this paper is the high-frequency (HF) interference channel. HF interference characterizes the severe background interference to communication process produced by many users in the HF channel [8]. By using the congestion measurements of 95 1KHz channels in the HF band,HF interference is modeled as Gaussian noise with randomly varying average power [9]. The probability density function (PDF) of the average interference power is

where the unit of interference power x is dBm.α and B are parameters fitted to the congestion measurements. For different HF channels, α has different values typically ranging from -16 to -9. The value of B is approximately -0.1.The expectation of average interference power E[I](dBm)=- α/B.
The above HF interference model is to be applied in the following analysis, where PDF of the average interference power within each M-ary channel is assumed to be given by (1).In fact, the HF interference model can be considered as a kind of unintentional nonuniform jamming [12]. DSAJ networks alleviate jamming effect by real-time sensing and allocating M-ary channels with average interference power below some predetermined threshold.In order to simplify the analysis, parameter α in (1) for all the M-ary channels is assumed to be the same1.
If α’s in (1) for each M-ary channel are assumed to be different, the throughput performance derived in the following chapters should be averaged by α. But a probability distribution of α is not available.
IV. THROUGHPUT ANALYSIS

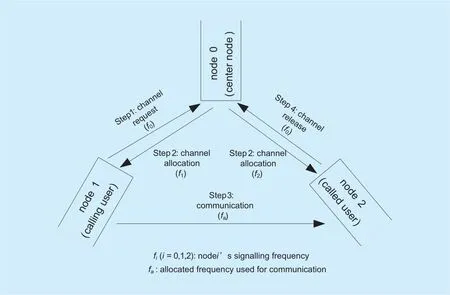
Fig. 2. schematic diagram of DSAJ networking.
According to the networking scheme, the maximum number of users is equal to the number of detected spectrum holes. Hence, if there are m spectrum holes, the normalized throughput of the DSAJ multiple-access system is [10]where N1=Nt/M and Pcis the probability of correct transmission for each information bit when communicating in a spectrum hole,i.e., the user performance target. Although signaling information transmission actually reduces the throughput, it can be neglected if the amount of user information transmission is large.
From (2), the normalized average throughput
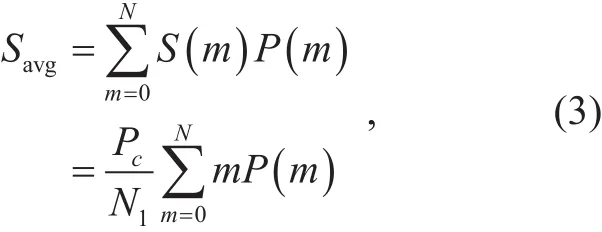
where N=Nt/(2M) and P(m) is the probability of detecting m spectrum holes in the current Gn. Let PSPHbe the probability of an M-ary channel being the spectrum hole, then

Substituting (4) into (3),

Let τ be the threshold of spectrum hole detection, then

From (1) and (6), the PDF of average interference power in spectrum holes is

Here the division of PSPHin (7) is for normalization, which makes the integration of PY(y) be equal to 1.
Assume noncoherent demodulation is used.Since HF interference is Gaussian noise given power x, the symbol error rate (SER) of each user [11]
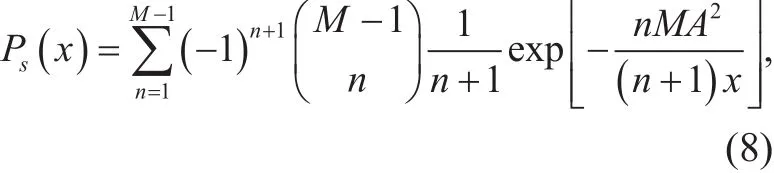
where A2is the signal power. SER of communication in spectrum holes is derived by averaging (8) with (7). Since the unit of parameter x in (8) is Watt, it must be transformed to dBm before averaging. Let t be the dBm form of x,then t=30+10log10x according to the dBm de finition. Combining this with (7) and (8),

Using the parameter transformation of y=(t-30)/10, and using the relationship of BER and SER, i.e., Pb=MPs/(2(M-1)), we get
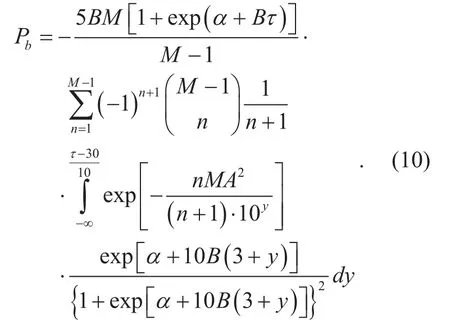
Hence

Let Ebbe the information bit energy andbe the average single-sided interference power spectrum density, then the average signal-to-interference ratio (SIR)= MA2/(E[I]log2M). Since E[I](dBm) = - α/B, the relation between(dB) and parameter A, α, B is
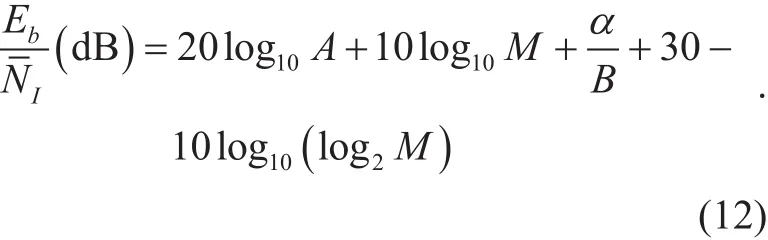
The throughput computation process begins with the user performance target (i.e., Pcor Pb)determination. The next step is to derive the spectrum hole detection threshold τ using (10).With this value of τ, PSPHis derived using (6).Finally, the throughput can be computed by(5).
V. INFLUENCE OF CODING
Coding influences the throughput of DSAJ multiple-access systems in two ways. First,given a fixed user performance target, coding can reduce the coded symbol error rate requirement, thus more M-ary channels in a Gn can be detected as spectrum holes and the maximum number of users in the network increases. On the other hand, coding usually lowers the information rate, which leads to throughput decrease. The overall influence of coding is decided by analysis. Two types of codes are considered. One is the capacityachieving codes and the other is practical codes.
When capacity-achieving codes are used,information transmission is error-free. The code rate is the channel capacity. If hard- decision decoding is used and channel state information is unavailable, the capacity [11]

where the unit of capacity C is M-ary information symbol/ M-ary coded symbol. The coded symbol error rate is Ps=2(M-1)Pb/M, where the expression of Pbis given by (10). When coding is used, (12) becomes

where R is the code rate. For capacity- achieving codes, R=C. Since information transmission is error-free, the normalized throughput

For the second case, we consider RS codes.The codeword length n=Q-1, where Q is the coded symbol alphabet size. The minimum hamming distance d=n-k+1, where k is the number of information symbol in a codeword.The code can correct up to t0=(n-k)/2 errors.The relation between information BER Pband Q-ary coded symbol error rate PQis [12]
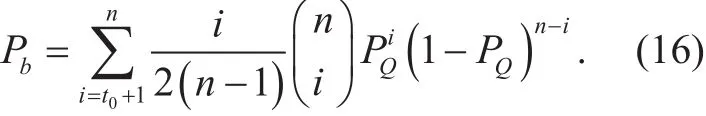
If transmit symbol alphabet M<Q, the log2(Q) bits of each coded symbol are divided into L= log2(Q)/log2(M) groups, with log2(M)bits in each group. Hence, each coded symbol transmits L times by using M-ary symbol. The relation between M-ary symbol error rate Psand PQis

When RS codes are used, the normalized throughput is

VI. INFLUENCE OF SPECTRUM HOLE INFORMATION TRANSMISSION ERROR
From the networking scheme, it is easily seen that the transmission of the spectrum hole information plays an important role in guaranteeing the user performance. For one user,errors in the transmission may result in communications outside the spectrum holes, or even collisions with other users. Both of these two cases degrade its performance and the overall throughput significantly. The in fluence of spectrum hole information transmission error is analyzed here. In order to simplify the analysis, other types of signaling information errors are not considered. It is obvious that the transmission BER depends on the waveform used by the center node. In order for the analysis not dependent on specific waveforms, we assume the transmission BER is a fixed value (say, P0) for all SIR. Hence, for a specific waveform which reaches P0at some SIR threshold, the actual throughput is lower-bounded by the theoretical result when SIR is beyond the threshold.
Consider the event that m spectrum holes are obtained in one spectrum hole detection process. Its probability P(m) is given by (4).The probability that n out of m spectrum holes are correctly received is
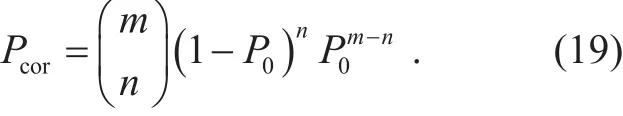
For each user, there exist four possible cases according to whether the spectrum hole information is correctly received. They are 1) the user is hit; 2) the user is not hit and the spectrum hole information is correctly received; 3) the user is not hit and the spectrum hole information is erroneously received which makes the user operate in another spectrum hole; 4) the user is not hit and the spectrum hole information is erroneously received which makes the user operate outside any spectrum holes. Let 1, 2, 3, 4 denote the four cases respectively. The joint probability that n spectrum holes are correctly received and case 2 occurs is

The other three joint probabilities are computed as
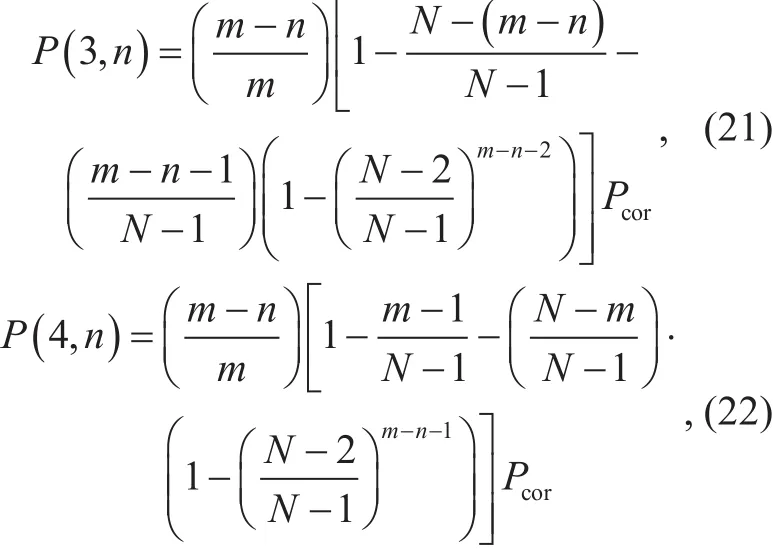

In case 4, the user operates outside the spectrum holes. Similar to (7), the PDF of average interference power outside spectrum holes is
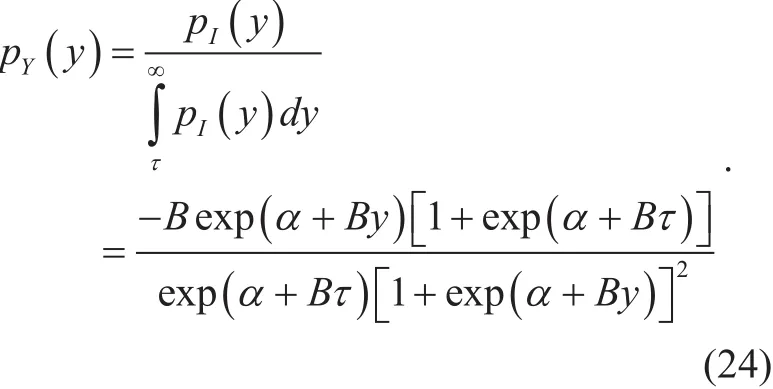
BER of communicating outside spectrum holes is derived by averaging (8) with (24),that is

The normalized throughput of a single user when the BER of spectrum hole information transmission is not zero is

where the BER of communication when the user is hit is set to be 0.5.
VII. COMPARISON WITH FHMA
In DSAJ multiple-access and FHMA networks,user frequencies vary with time. The difference is that frequencies in FHMA networks are preset and only used to distinguish users,while frequencies in DSAJ multiple-access networks are determined during the communication process and not only used to distinguish users but also guarantee the user performance.The throughput performance of these two networks are compared. We assume the user information of DSAJ network is uncoded and all the signaling information is error-free. We also assume modulation and demodulation method of the two networks is the same.
In FHMA networks, all the M-ary channels are used in designing FH patterns. Any channel can be used at any time. Hence, larger channel occupancy gives FHMA networks an advantage over DSAJ networks in throughput performance. However, since FHMA networks are usually asynchronous, collisions are inevitable among user transmissions. High BER caused by collision gives FHMA networks disadvantage over DSAJ networks in throughput performance. Assume exact channel state information is available for FHMA users,then error correction coding along with error-and-erasure decoding can be introduced to mitigate the detriment of frequency collisions[13]. Throughput of these two networks are compared on the premise of the same user performance target. The normalized throughput of FHMA networks is computed as

where K is the number of users, Pbis the information BER, R is the code rate and q is the number of M-ary channels.
Consider that the optimum convolutional code based on 4-ary signal set is used by FHMA users. Its code rate R=1. The upperbound of Pbis [12]
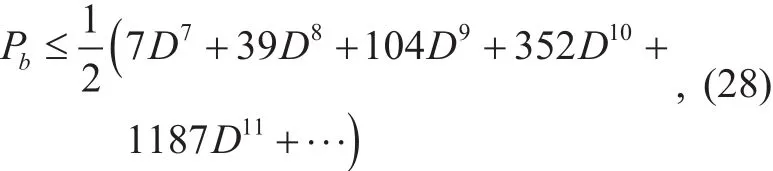
where D is the Chernoff parameter. For errorand-erasure decoding, D is computed as [13]

where Phis the probability of frequency collision. For asynchronous FHMA networks with one symbol per hop [14]

Ps1is the error rate of coded symbols without any collisions. Similar to (9), Ps1can be derived by (1) and (8)

where the relation between signal power A2and average SIR(dB) is

VIII. NUMERICAL RESULTS
Figures of DSAJ multiple-access network performance are given in this section. For all the figures, it is assumed that the number of M-ary channels N1=100, the HF interference channel parameter α=-10, B=-0.1, and M=4. For FHMA network, assume the number of frequencies q=64.
The normalized throughput of DSAJ multiple-access networks is shown in figure 3 for user performance target Pb=10-3, 10-4and 10-5.It can be seen that since only half of the M-ary channels are used in one spectrum hole detection process, upper limit of the normalized throughput is 0.5. It also can be seen that the throughput decreases as the user performance requirement upgrades. This is because the increase of user performance means the enhancement of spectrum hole quality. But as the spectrum hole quality gets better, the spectrum hole, i.e., the user number gets smaller. This effect offsets the user performance increase and leads to the overall throughput decrease.Therefore, it can be said that user performance increase is achieved at the cost of throughput decrease.
The influence of capacity-achieving codes on network throughput is illustrated in figure 4. It can be seen that throughput increases as capacity increases. The reason is as follows.According to (13), larger capacity means smaller Psand higher spectrum hole quality,which lowers the spectrum hole detection threshold and detection probability PSPH. However, capacity (i.e., code rate) increase has larger effect on throughput than PSPHdecrease,thus the overall throughput still increases. By comparing throughput of coded case with uncoded case, we can see that although coding lowers the spectrum hole quality requirement and increases the user numbers, cost of information transmission rate decrease has to be paid. Therefore, coding does not necessarily lead to the overall throughput increase.
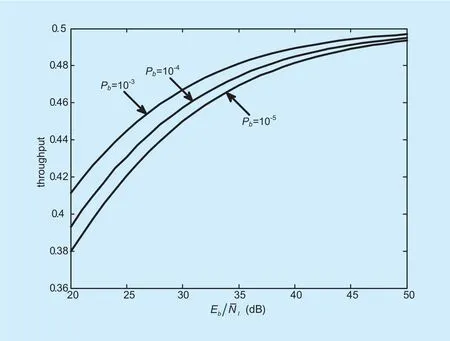
Fig. 3. Normalized throughput for different user performance target.

Fig. 4. In fluence of capacity-achieving codes.
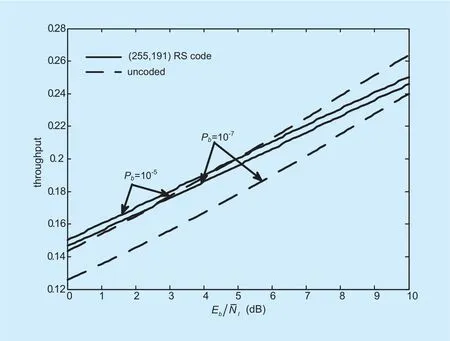
Fig. 5. In fluence of RS codes.

Fig. 6. In fluence of spectrum hole information transmission error.
The in fluence of practical codes on network throughput is illustrated in figure 5. The code considered is (255,191) RS code. From figure 4 and figure 5, it can be seen that no matter what type of codes are used, throughput curves of coded case intersect curves of uncoded case.Coding increases throughput only at low SIR.The reason is that when SIR is small, there are not many spectrum holes in Gn. By the use of coding, the number of spectrum holes (i.e.,access users) increases. When SIR is large,however, the number of spectrum holes is also large, thus code rate becomes the main in fluencing factor in throughput. It also can be seen from figure 4 that throughput improvement by coding becomes significant at low SIR as the user performance target upgrades, which indicates that in view of throughput optimization,coding is applicable to the case that low BER is required at low SIR.
The in fluence of spectrum hole information transmission error is illustrated in figure 6. It is seen that throughput obviously decreases at the spectrum hole information transmission BER of 10-1. However, the decrease is not obvious for BER of 10-2or less. Note that it does not mean that the transmission error is not important. When the error occurs, user performance is significantly degraded and the performance target can not be achieved. But since this event occurs with probability equal to the transmission BER, which is usually far less than 1 especially for large SIR, it does not deteriorate the overall throughput too much.Despite this fact, spectrum hole information transmission waveform must be carefully designed to avoid transmission error as much as possible, in order to guarantee the user performance target.
Throughput comparison of DSAJ multiple-access networks and FHMA networks is illustrated in figure 7. User information of DSAJ multiple-access networks is assumed to be uncoded, while user information of FHMA networks is assumed to be coded by the optimum convolutional code described in Section 7. Error-and-erasure decoding is considered.User performance target of both networks is 10-3. It is seen that although collisions in FHMA networks can be eliminated via error-and-erasure decoding, and information rate is lossless with code rate equal to 1, throughput of FHMA networks is still far smaller than DSAJ multiple-access networks. Hence, it can be concluded that although the channel utilization level of DSAJ multiple- access networks is low, high throughput is also achieved since collision and interference are avoided by virtue of good channel selection.

Fig. 7. Throughput comparison of DSAJ multiple-access and FHMA networks.
IX. CONCLUSIONS
Throughput performance is theoretically analyzed for a simple DSAJ multiple-access networking scheme. The main idea of this scheme is to provide users spectrum holes for communication. By doing this, the detriment of strong background interference and collisions are avoided simultaneously. Results show that the increase of user communication performance is at the cost of throughput decrease, but it can be improved by coding at low SIR. DSAJ networking scheme adopts fundamental idea of cognitive radio. Its throughput performance is superior to FHMA which has no ability of cognition.
ACKNOWLEDGEMENT
The authors would like to thank the anonymous reviewers for their valuable comments,which have been extremely helpful in improving the quality of the manuscript.
杂志排行
China Communications的其它文章
- DNN-Based Speech Enhancement Using Soft Audible Noise Masking for Wind Noise Reduction
- HF Communications: Past, Present, and Future
- A Spectrum Prediction-Based Frequency Band Pre-Selection over Deteriorating HF Electromagnetic Environment
- Deep Spectrum Prediction in High Frequency Communication Based on Temporal-Spectral Residual Network
- Digital Channelization Technology for HF Communication Base on Fast Filter Bank
- High Frequency Communication Network with Diversity: System Structure and Key Enabling Techniques
