Automatic Search of Impossible Differentials and Zero-Correlation Linear Hulls for ARX Ciphers
2018-03-13KaiZhangJieGuanBinHu
Kai Zhang, Jie Guan, Bin Hu
Zhengzhou Information Science and Technology Institute, Zhengzhou 450000, China
I. INTRODUCTION
For the recent 20 years, large numbers of cryptographic primitives using only addition, rotation and XOR have been proposed. They are called ARX algorithms. As these operations can be implemented efficiently in software and hardware, the ARX ciphers usually have good software and hardware performance.Thus ARX algorithms are usually lightweight primitives, which is suitable for low resource devices such as sensor nodes and RFID tags.ARX ciphers have penetrated into every aspect of symmetric primitives, there are lots of famous ARX ciphers such as HIGHT[11],Threefish[12], SPECK[13], TEA family ciphers[23-25], Salsa20[16], BLAKE[18],BLAKE2[19], Skein[12] and so on.
Although more and more ARX ciphers have appeared, compared with other ciphers,the cryptanalysis of them seems to lag behind.Among these methods, impossible differential cryptanalysis and zero-correlation linear cryptanalysis are two important and effective cryptanalytic methods to analyze ARX ciphers.
Impossible differential cryptanalysis was independently proposed by Knudsen to attack the DEAL cipher[5] and further by Biham et al. against Skipjack[6]. The basic idea of impossible differential cryptanalysis is using the impossible differential character to retrieve the secrete key. Impossible differential cryptanalysis has proven to be very effective against a wide variety of ciphers[7-9]. The core of impossible differential cryptanalysis is the existence of impossible differential character.The longer an impossible differential character exists, the longer rounds of the cipher we may attack. So it is very meaningful to find long impossible differential characters of a cipher.
For automatic search of impossible differentials, in Indocrypt 2003, Kim et al. proposed the u-method[28] to search the impossible differentials for block cipher structures with bijective round functions. In 2009, Luo et al. improved the u-method and proposed UID-method[29], which has fewer limitations and can collect more information to build impossible differentials. In Indocrypt 2012, Wu et al. proposed a more general automated tool for finding truncated impossible differentials for word-oriented block ciphers with bijective S-boxes[30]. However, all these automatic search methods are designed for S-box based block ciphers, for the brand new ARX ciphers,they are not applicable.
Zero-correlation linear cryptanalysis was proposed by Andrey Bogdanov and Vincent Rijmen in 2011[1]. It is based on linear approximation whose correlation value is exactly zero. This new and novel cryptanalytic method has proven to be effective against AES,CLEFIA[1,2], TEA and XTEA[4]. The core of zero-correlation linear cryptanalysis is the existence of zero-correlation linear hull. The longer a zero-correlation linear hull exists, the longer rounds of the cipher we may attack. So finding longer zero-correlation linear hulls of a cipher is also meaningful.
In [30], the automatic search of zero-correlation linear hulls was also introduced. Unfortunately, the new method is also designed for S-box based block ciphers, which can not be applied to ARX ciphers either.
Our contributions
The main purpose of this paper is to introduce an automatic search tool to explore new and longer impossible differentials and zero-correlation linear hulls for ARX ciphers.Firstly, we propose an automatic search method to explore impossible differentials and zero-correlation linear hulls whose weights of the input/output differentials (or linear masks) are low. Secondly, we introduce some techniques on extending the low weight distinguishers to high weight distinguishers, thus more and longer impossible differential distinguishers and zero-correlation linear distinguishers can be derived. Thirdly, we apply this automatic search method to three typical ARX ciphers HIGHT, LEA and SPECK to prove the high efficiency of our automatic search method in finding impossible differentials and zero-correlation linear hulls. The summary of new IDs and ZCLHs for these ciphers is concluded in the two tables below.
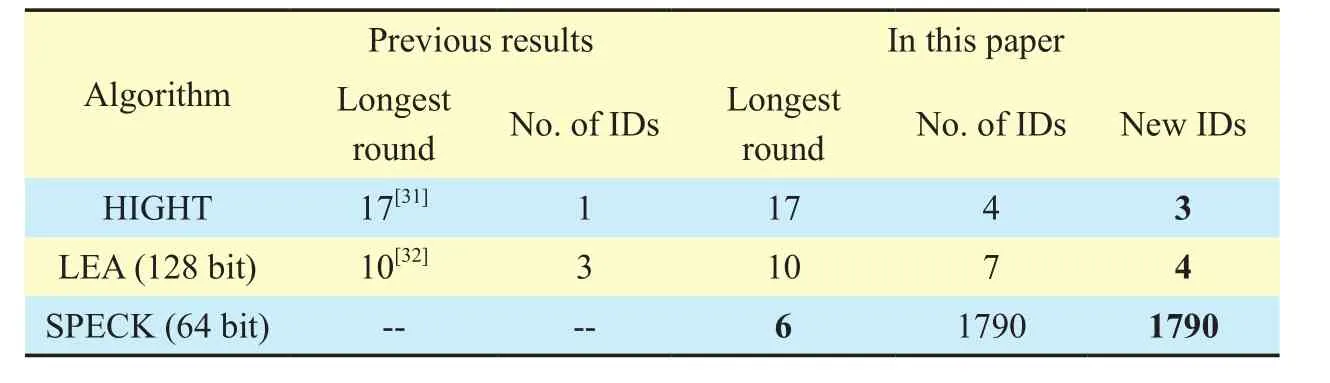
Table I. Summary of new impossible differentials for some typical ARX ciphers.

Table II. Summary of new zero-correlation linear hulls for some typical ARX ciphers.
This paper is organized as follows. Impos-sible differential cryptanalysis and zero-correlation linear cryptanalysis are briefly introduced in section 2. Section 3 proposes two automatic search methods, which are designed for finding impossible differentials and zero-correlation linear hulls for ARX ciphers. To get longer distinguishers, the extensions of the automatic search method are also proposed.Using the method introduced in section 3, section 4 illustrates impossible differentials and zero-correlation linear hulls for three typical ARX ciphers HIGHT, LEA and SPECK. Section 5 concludes the paper.

Fig. 1. Sketch of impossible differential cryptanalysis.

Fig. 2. Sketch of zero-correlation linear cryptanalysis.
II. BRIEF INTRODUCTION ON IMPOSSIBLE DIFFERENTIAL CRYPTANALYSIS AND ZEROCORRELATION LINEAR CRYPTANALYSIS
The impossible differential cryptanalysis can be simply concluded as “use the differential path of probability zero to eliminate the wrong key candidates”. For an impossible differential path, if we partially encrypt the plaintext and decrypt the ciphertext with the right key,the differential of the impossible differential path will never occur. So when we use some guessed key bits to partially encrypt the plaintext and partially decrypt the ciphertext, if the impossible differential path occurs, the guessed key bits must be wrong, so it is possible to eliminate the wrong key candidates from the right one.
There are mainly two steps for impossible differential cryptanalysis. One is constructing impossible differentials, the other is recovering the key. The basic skill used in constructing impossible differentials is miss-in-themiddle technique, which usually combines two differential paths of probability one to make a contradiction in the middle. The basic skill used in recovering the key is key sieving technique. When we use guessed key bits to realize partial encryption and partial decryption, all the guesses which satisfy the impossible differential character are wrong, then we can eliminate these wrong key candidates to reduce the candidate key space. By combining other techniques such as exhaustive search we can recover the correct key.
The procedure of zero-correlation linear cryptanalysis can be simply concluded as“use linear approximation of probability 1/2 to eliminate the wrong key candidates”. Usually, the propagation of linear mask has some fixed modes in specific cipher components. In reference [1,2], Bogdanov and Rijmen illustrated how to construct linear approximation of probability 1/2 for block ciphers, which is zero-correlation linear approximation actually.Based on these zero-correlation linear approximations, we can distinguish the cipher from random permutation, which makes key recovery attack possible. To reduce the data complexity of zero-correlation linear cryptanalysis,multiple zero-correlation linear cryptanalysis and multidimensional zero-correlation linear cryptanalysis are proposed successively.
The procedures of zero-correlation linear cryptanalysis also conclude the process of constructing zero-correlation linear hulls and the process of key recovering. The basic idea is using the guessed key bits to partially encrypt the plaintext and partially decrypt the cipher,if the zero-correlation linear approximation appears, the guess is wrong. We can use this thought to eliminate the wrong key candidates.
III. AUTOMATIC ID AND ZCLH SEARCHING METHODS FOR ARX CIPHERS
3.1 Modes operation
During the process of encryption and decryption, each unit (bit or word) of the internal states has some properties such as the property of differential character, the property of linear mask character, XOR-balanced, ADD-balanced(i.e. balance over module addition), constant and so on. If some properties or abstracted properties can be passed down, it is possible to build some distinguishers according to these property deductions. In this section, we
will propose a new definition “Modes Operation”, which can conclude all these properties.However, first of all, we want to illustrate
three key problems for this new definition.
• Why we propose this new definition -Modes Operation?
• What is the relationship between Modes Operation and some earlier proposed methods such as u-method, UID method and tuple cryptanalysis?
• Why our method is more effective than other works for ARX ciphers?
During our study on finding impossible differentials and zero-correlation linear hulls on ARX ciphers, we found that the earlier proposed methods are all ineffective for this kind of ciphers. For ARX ciphers, some earlier proposed impossible differentials or zero-correlation linear hulls are usually built by hand using some properties of addition, rotation and XOR operations. The efficiency of this old method is rather low and the effectiveness highly relies on the expertise of the cryptographers. And sometimes, it is impossible to test all the combinations of the input and output,even for those input/output differentials (linear masks) of some specific pattern. So we want to propose a new tool to solve this problem and realize automatic search for these two kinds of distinguishers on ARX ciphers.
On the other hand, during our research, it is found that some earlier proposed methods such as u-method, UID method and tuple cryptanalysis are all symbolic operations. For u-method and UID method, they use matrix as a carrier to realize symbolic operation. And for tuple cryptanalysis, it just redefines the relationship for these symbols to accord with different arithmetic operations. So on a higher level, we conclude all these symbolic operations in a more general way and thus propose our automatic search method for ARX ciphers.
Then, we will propose this new definition which we call it “Modes Operation”.
Definition 1:If a cipher hasnbasic units for each internal state, which is denoted as (X1,X2,…,Xn). Each unit of the internal state has some specific modes such as differential, linear mask, xor balance etc. If the properties of a unit are abstracted or constructed properly,when given the modes of the internal state at timet(Mt(X1),Mt(X2),…,Mt(Xn)) and the structure of the round function, the modes of the internal state at timet+1(Mt+1(X1),Mt+1(X2),…,Mt+1(Xn)) can be deducted through simple op-erations with probability one, we call this kind of operationModes Operation.
The modes of the internal states reflect some properties of the internal states, we can build distinguishers according to these modes.There are two items we should pay attention to when we construct modes operations. On one hand, we should choose the “mode”. This item decides the basic computing rules when passing through each component of the cipher.On the other hand, we should construct the property set (denoted as Ω) and assign specific meaning to each element of the set. The constructed property set may influence the length of the distinguisher directly, so how to build an appropriate property set is an open problem.
Here we want to note that u-method,UID method and tuple cryptanalysis can all be viewed as a specific modes operation. For modes operation, it can be seen as an open source definition, we can construct specific modes operation according to our need. Next,we will give two kinds of specific modes operations on ARX ciphers to realize automatic search of impossible differentials and zero-correlation linear hulls.
For ARX ciphers, the basic unit for modes operation is on bit level, not on word level.For the rest of the paper, we just focus on the modes operation for ARX ciphers.
For impossible differential cryptanalysis,the mode of an internal state bit represents some property of a differential bit. For zero-correlation linear cryptanalysis, the mode of an internal state bit represents some property of a linear mask bit.
For impossible differential cryptanalysis,the modes represent some differential properties. For an internal state bit, the property setΩ includes three elements {“0”, “1” and “U”}.“0” represents the differential of an internal state bit is 0 for sure, “1” represents the differential of an internal state bit is 1 for sure and“U” represents the differential of an internal state bit is uncertain.
For zero-correlation linear cryptanalysis,the modes represent some properties of linear mask. For an internal state bit, the property setΩ also includes three elements {“0”, “1” and“U”}. However, these three elements represent different meanings. Here, “0” represents the linear mask of an internal state bit is 0 for sure, “1” represents the linear mask of an internal state bit is 1 for sure and “U” represents the linear mask of an internal state bit is uncertain.
Before taking examples to illustrate the modes operation, we introduce two basic properties on modular addition, which establish the foundations of our search method. Property 1[3] is the basic to construct the impossible differentials and property 2[4] is the basic to construct the zero-correlation linear approximations. These two properties introduced differential property and linear approximation property of module 2nrespectively.
Property 1[3](Differential Property for Module 2n): Givenx,x’,y,y’ ben-bit values,andz=(x+y) mod 2n,z’=(x’+y’) mod 2n. If thei-th (counting from 1) toj-th bits ofx,x’,y,y’ and thei-th carryci,ci' ofx+y,x’+y’ are known, then thei-th toj-th (i<j≤n) bits of Δzcan be obtained, regardless of the values of least significanti-1 bits ofx(orx’),y(ory’).Note that if there are no differences in the least significanti-1 bits ofx+yandx’+y’, thenci=ci'.
Property 2[4](Linear Approximation Property for Module 2n): In any linear approximationof the modular addition with a non-zero-correlation, the most significant non-zero mask bit for Γx,Γyand Γzis the same.
Next, let us take some examples to show howModes Operationmanipulates when confronting with certain cipher components.
As addition, XOR, rotation and branching are basic operations for ARX ciphers, we take these operations as examples to illustrate howModes Operationoperates.
First of all, let us take a look at how the modes of the output bits are calculated when confronting with rotation, addition, branching and XOR if we consider the differential mode.For simplicity, all the input and output of these operations aren-bit word.
For simplicity, we denote this operation as
For simplicity, we denote this operation as
For simplicity, we denote this operation asmore, the truth table of “⊕ ” operation used in the computation is a natural expansion of bitwise-XOR operation to fit modes operation. Actually, ifMa,Mb∈{“0”, “1”},Ma⊕Mbis just bitwise-XOR operation. If at least one of theMaorMbequals toU,which means the differential of this internal state bit is uncertain, the differential for the output of “⊕ ” is uncertain for sure, so the result is defined asUin the truth table. This supplement for the truth table makes sure the automatic search method works when confronting with all the modes situations.For simplicity, we denote this operation as
So with the help of these operation rules in differential modes, we can get the modes of the internal states round by round.
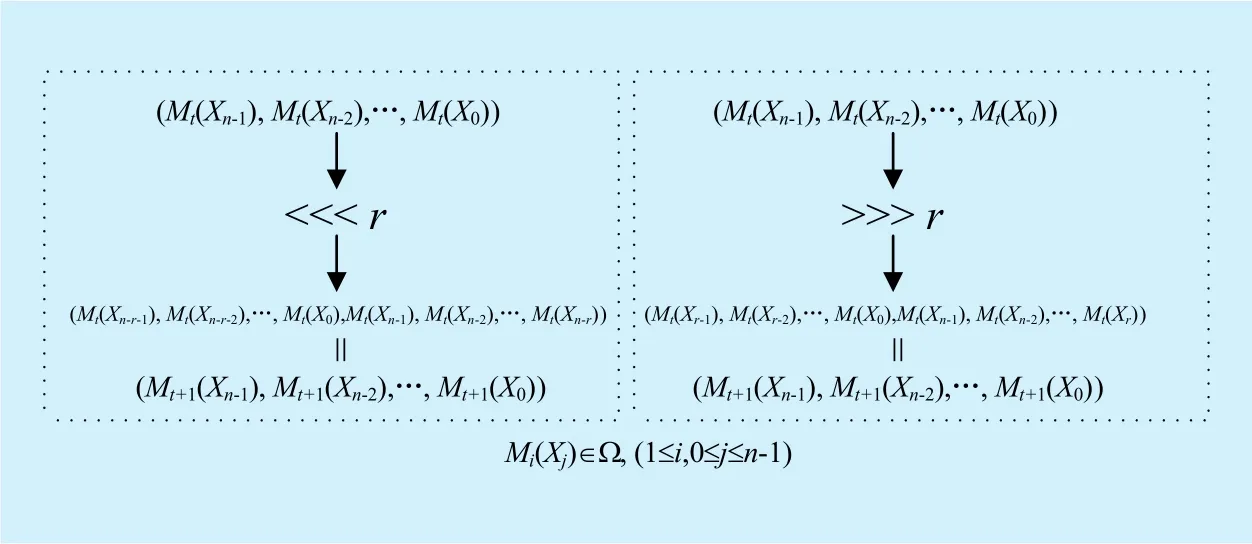
Fig. 3. Modes operation for rotation operation in differential mode.

Fig. 4. Modes operation for addition operation in differential mode.
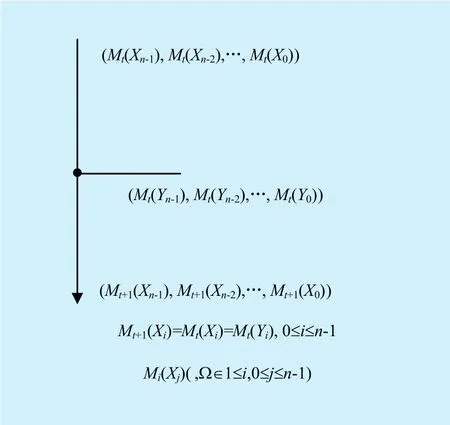
Fig. 5. Modes operation for branching operation in differential mode.
Next, what if the mode represents the linear mask? Similarly, we consider this problem with the same four operations – rotation, addition, branching and XOR. Also, all the input and output of these operations aren-bit word.
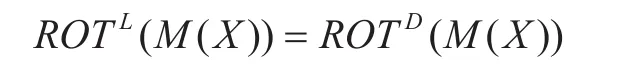
For simplicity, we denote this operation as
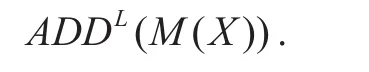
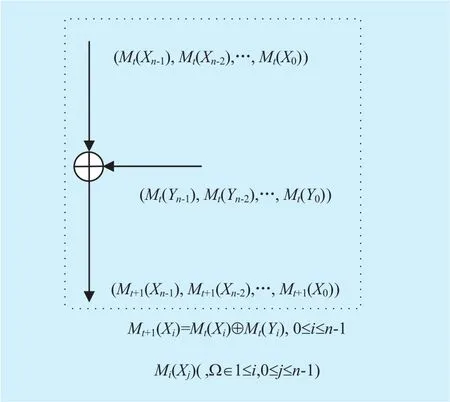
Fig. 6. Modes operation for XOR operation in differential mode.
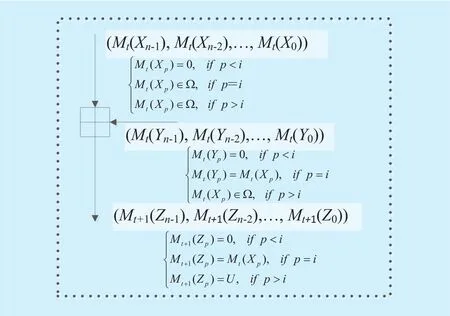
Fig. 7. Modes operation for addition operation in linear mask mode.
For simplicity, we denote this operation as
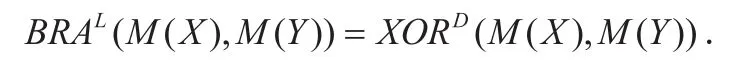
So with the help of these operation rules in linear mask modes, we can get the modes of the internal states round by round.
3.2 How to construct IDs and ZCLHs using modes operation?
Modes operation reveals some properties of the internal states, the differential mode reveals the differential status of the internal states and the linear mask mode reveals the linear mask status of the states for non-zero correlations. Given the mode of the plaintext and the mode of the ciphertext, we can use modes operation to deduce the modes of the internal states round by round in two directions. That is to say, start from the mode of the plaintext, round by round, we can get the modes of the internal states for the first few rounds. Start from the mode of the ciphertext,use the decryption algorithm, round by round,we can get the modes of the internal states for the last few rounds. If a mode contradiction appears in the middle of the internal states, an ID or a ZCLH is found. A mode contradiction means that at the same round same bit of the internal states, when we deduce the state mode from the two directions, the mode of this bit is“0” and “1” (or “1” and “0”) at the same time,which makes a contradiction.
In this paper, we only consider the differential mode and linear mask mode for ARX ciphers. When in the differential mode, through deduction, we can get lots of truncated differential paths of probability one. When we deduce the differential modes in two directions,if a “0” mode (which means the differential of this bit is 0 for sure) meets with a “1” mode(which means the differential of this bit is 1 for sure) at the same round same bit of the internal states, a contradiction occurs thus an ID is constructed. While in the linear mask mode,the process is similar. Through deduction, we can get the linear mask modes of the internal states which have non-zero correlations. When we deduce the linear mask modes in two directions, if a “0” mode (which means the linear mask of this bit is 0 for sure) meets with a “1” mode (which means the linear mask of this bit is 1 for sure) at the same round same bit of the internal states, a contradiction occurs thus a ZCLH is constructed.
3.3 Automatic ID and ZCLH
searching method for ARX ciphers
Complexity analysis
The complexity of algorithm 1 highly relies on the number of active modes (i.e. non-zero modes).
• Usually, if the number of active modes for input and output are both 1, the complexity for algorithm 1 isO(n2).
• If we want to go through all the modes of the input and output, the computational complexity of the algorithm 1 isO(32n).For each bit, there are three choices –{0,1,U}, despite all zero cases, there are altogether (3n-1) cases for the input and the output, so the computational complexity
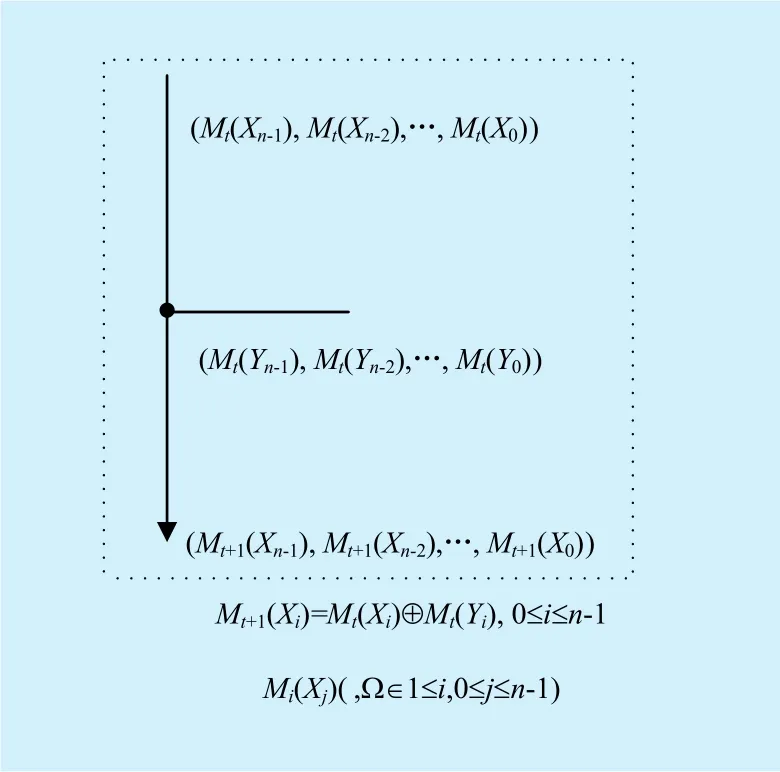
Fig. 8. Modes operation for branching operation in linear mask mode.

Fig. 9. Modes operation for XOR operation in linear mask mode.

• If the number of active modes for input and output arek1andk2respectively, the computational complexity is
As for each bit, there are three cases, “0”,
“1” and “U”.
During our research, we just search for the single bit modes rather than all the possible input and output modes, which means the computational complexity of our algorithm isO(n2). There are two main reasons for this.Firstly, the scale of the internal states is usually very large, which makes searching the entire input and output modes impossible. Secondly,through calculating, the instance that higher weight input modes or output modes which has longer IDs (or ZCLHs) is usually based on some single-bit input and output modes, and the high weight input modes or output modes can be deduced easily using the encryption and decryption algorithm.
In phase 1, we should adjust the thresholdNall the time. IfNis too large, there will be no output. IfNis too small, the outputs will be too many.
In the next section 3.4, we will propose some methods to derive high weight IDs and ZCLHs which can make us get longer and more of these two kinds of distinguishers.

Algorithm 1. Automatic ID/ZCLH searching method for ARX ciphers Input: Threshold N, modes of the input and output.Output: Longest length of the distinguisher and corresponding modes of the input and output.// Preprocessing Stage 1 M(P) and M(C) represents the modes of the plaintext and ciphertext respectively.Suppose there are totally R rounds for the target cipher and the block size is n,M(Xi) (0≤i≤R) represents the mode of the internal state at the ith round,P=X0 and C=XR.2 Set constraint on the modes of the plaintext and ciphertext. In this stage, we will dene the number of active modes. Usually, the number of active modes for the plaintext and ciphertext are both chosen to be 1.3 Substitute the operations of the round function (denoted as “RF”, the round function of the decryption algorithm is denoted as RF-1) with corresponding modes operation proposed in section 3.1. If we substitute the operations with corresponding operations in differential mode, the round function is denoted as RFD, and if we substitute the operations with corresponding operations in linear mask mode, the round function is denoted as RFL. The variants of round functions are used to calculate the modes of the internal states, thus we can calculate the modes of the internal states round by round.4 Longest Round←0// Search the longest ID and ZCLH 1 for i←1 to n do 2 set M(P):MP ji MP()1 if() 0 else j j===3 for p←1 to n do 4 set M(C):MC qp MC( )1 if( ) 0 else q q===5 for r←1 to R do 6 MPMX MX MC MX MX() ( ) ( );() ( ') ( ' ).= →= →0RF RF D L /r RRF RF D L - -1 1/Rr -7 for u, v←1 to R do 8 if there exist at least one parameter t, which makes MX MX⊕ - =9 if (u+v)>N Return {i, p, u+v}.10 then Longest Round←u+v 11 end 12 end 13 end 14 Return Longest Round.( ) ( )1 uRv tt
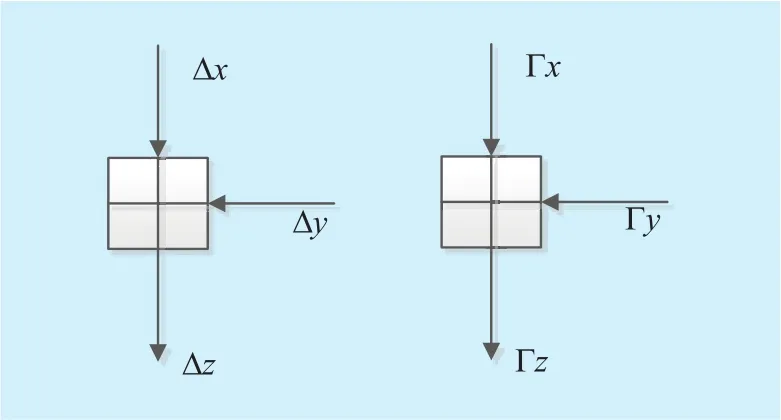
Fig. 10. Modular addition in differential mode and linear mask mode.
3.4 How to stretch IDs and ZCLHs?
In this section, we will propose two methods –“Deduction Method” and “Verifying Method”to get more and longer impossible differentials and zero-correlation linear hulls.
3.4.1 Deduction method
Ifα→βis an impossible differential (zero-correlation linear hull),By using the decryption algorithm and start withα, if the modes for the following severalNrounds are all “0” or “1” modes, that is to say,without occurrence of “U” mode, we can get a high weight input differential (linear mask) and stretch the ID or ZCLH forNrounds.
Similarly, by using the encryption algorithm and start withβ, if the modes for the follow severalMrounds are all “0” or “1”modes, that is to say, without occurrence of“U” mode, we can get a high weight output differential (linear mask) and stretch the ID(ZCLH) forMrounds.
As the addition operation is usually the only non-linear component of an ARX cipher, some differentials or linear masks which can be passed down through addition operation with probability one may be critical in the stretching of the distinguishers. When we consider the differential of module addition, if the differential mode ofxandyare (a,0,0,…,0,0) and(b,0,0,…,0) respectively,aandbrepresent “0”mode or “1” mode. The mode ofzis (a⊕b,0,0,…,0). When we consider the linear mask of module addition, if the linear mask mode ofxis (0,0,…,0,0,1), the modes ofyandzare both(0,0,…,0,0,1). Although these observations are evident, they are useful when we stretch the impossible differentials and zero-correlation linear hulls.
For example, for SPECK-32 algorithm,using the automatic search method, we find 5 round low weight impossible differential(To simplify the expression, we useabto representbconsecutivea). When extend the distinguisher in the encryption direction by one round, we can get 6 round high weight impossible differential
3.4.2 Verifying method
For differential mode, given a low weight impossible differential, if the single bit differential does not appear at the most significant bit, the bits within this word, those positions higher than the position of the single bit differential,can all be defined as “U” modes. For most cases, this method is usually applicable. However,it doesn’t always work. So when using this method, we should verify the impossible differential path to make sure the contradiction occur,so we call this method “Verifying Method”.
For linear mask mode, given a low weight zero-correlation linear hull, if the single bit linear mask does not appear at the least significant bit, the bits within the word, those positions lower than the position of the single bit linear mask, can all be defined as “U” modes.To be sure, it needs verification too.
For example, we find one 17 round zero-correlation linear hull for HIGHT: (e0,e1,6,7,the Verifying Method, we prove that all the 128 zero-correlation linear hulls of the form(e0,e1,6,7, 0, 0, 0, 0, 0, 0)(1U7, 0, 0, 0, 0, 0,0, 0) are all 17 round distinguishers.
We want to note that, usually, by using the Verifying Method, we can get massive new IDs or ZCLHs from a single ID or ZCLH,which can offer more distinguishers for cryptanalysis.
IV. SOME APPLICATIONS USING AUTOMATIC SEARCH METHOD
4.1 Brief description on block cipher HIGHT, LEA and SPECK
HIGHT is a lightweight block cipher proposed in CHES 2006, and then it was adopted as an ISO standard block cipher. It was designed by the Korea Information Security Agency.HIGHT has 32 rounds, with 64-bit block and 128-bit key. Its structure is a generalized Feistel network. For more details on HIGHT,we refer readers to reference [11].
LEA is proposed by Electronics and Telecommunications Research Institute of Korea in 2013. It provides a high-speed software encryption on general-purpose processors. LEA has 128-bit block size and 128, 192, or 256-bit key size. For more details on LEA, we refer readers to reference [32].
SPECK is an ultra-lightweight block cipher which was proposed by the U.S. National Security Agency in June 2013. SPECK family is a simple ARX-based Feistel network, which processes the input as two words. For more details on SPECK, we refer readers to reference [13].
4.2 IDs and ZCLHs on HIGHT, LEA and SPECK
Using the automatic search method on these ciphers, we can derive some long IDs and ZCLHs. Part of the best results are as follows.
V. CONCLUSION
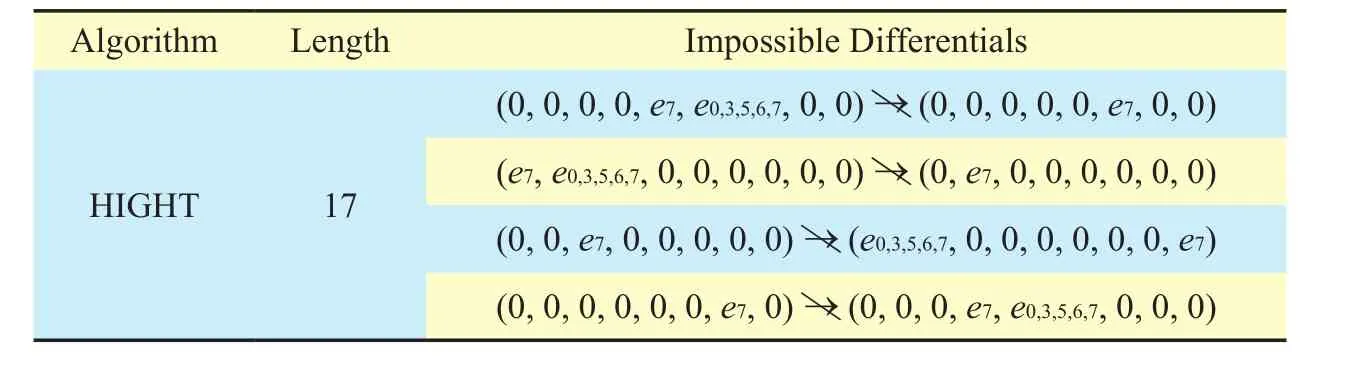
Table IV. Impossible differentials for HIGHT.
Impossible differential cryptanalysis and zero-correlation linear cryptanalysis are two important and effective cryptanalytic techniques nowadays. Although the impossible differential cryptanalysis and zero-correlation linear cryptanalysis for some ARX ciphers have been proposed, the findings of impossible differentials and zero-correlation linear hulls for ARX ciphers are usually manual work, which has become an obstacle in improving these two attacks. In this paper, automatic impossible differential and zero-correlation linear hull searching method has been proposed for ARX ciphers. The new searching method shows high efficiency in finding longer and more IDs and ZCLHs for ARX ciphers. In this paper, we propose a new concept calledModes Operation, which makes automatic search of IDs and ZCLHs for ARX ciphers possible.However, the automatic search method in this paper just uses two special cases of “Modes Operation”. Whether the “Modes Operation”can be extended to more circumstances is further to be studied. We expect the automatic search tool proposed in this article, especially the idea of modes operation, is not only helpful for evaluating the security of ARX ciphers against impossible differential cryptanalysis and zero-correlation linear cryptanalysis, but also useful in other cryptanalysis and other ciphers.
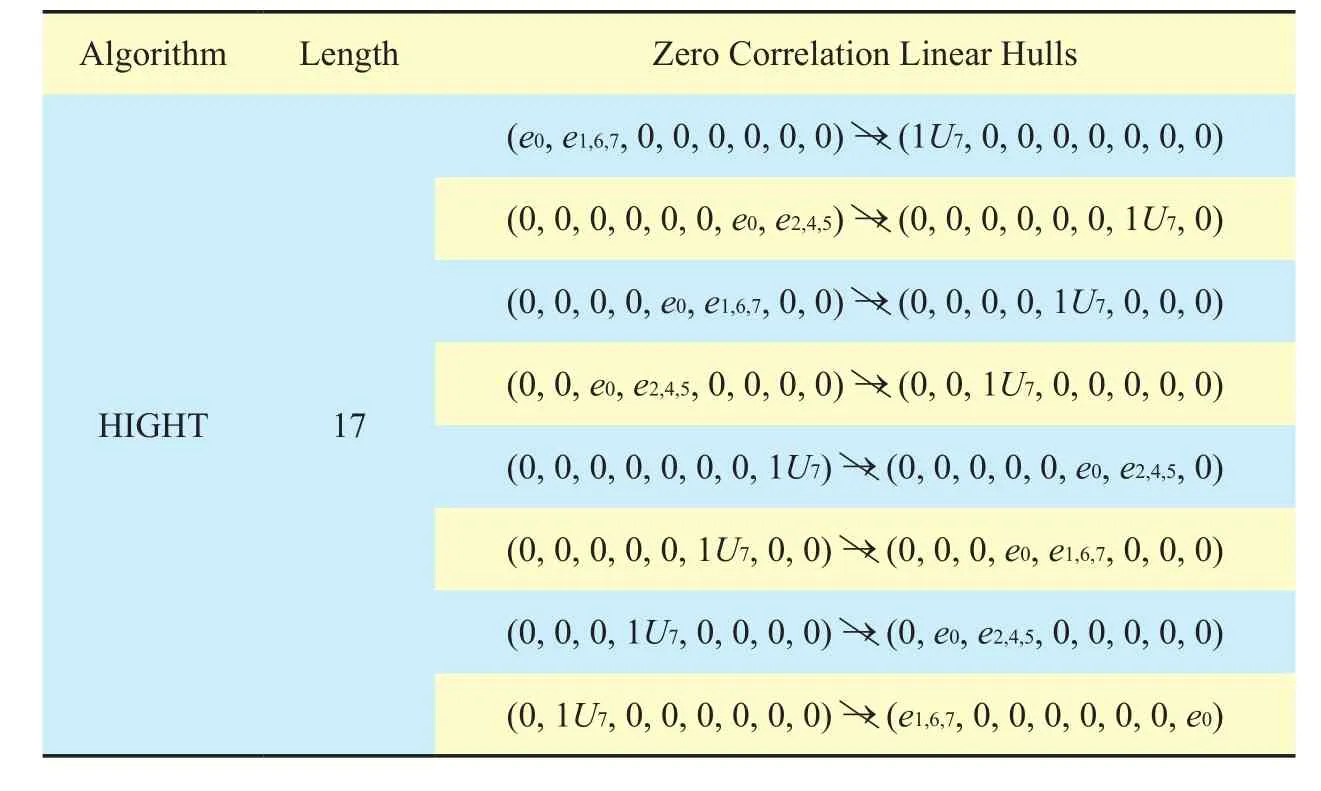
Table V. Zero correlation linear hulls for HIGHT.
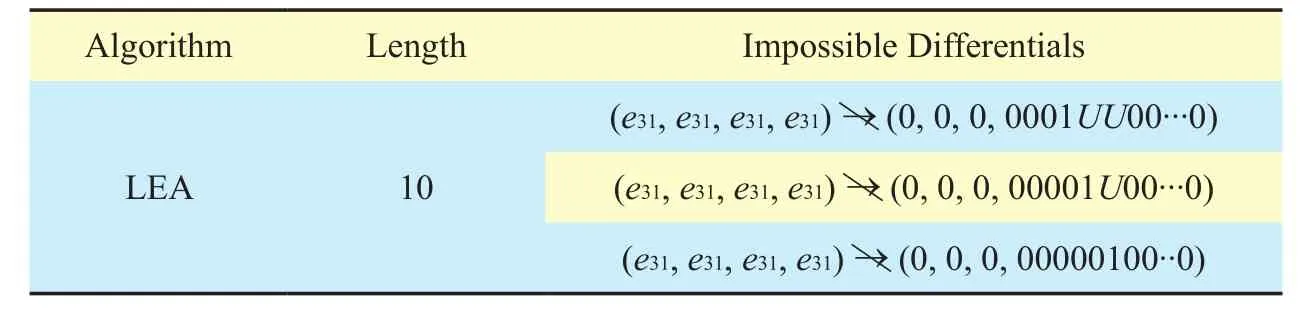
Table VI. Impossible differentials for LEA.
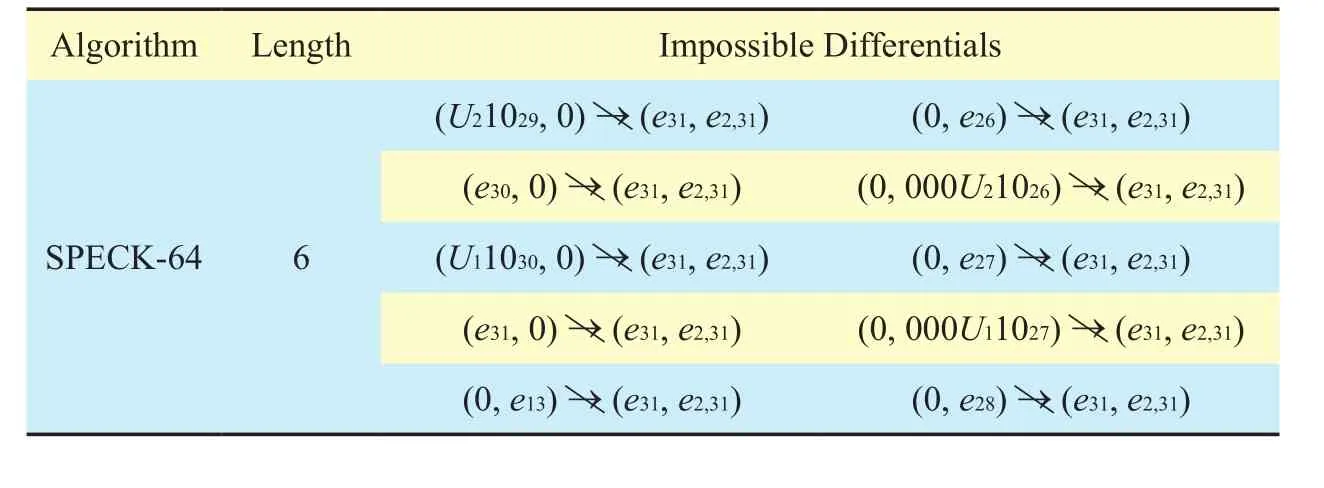
Table VIII. Impossible differentials for SPECK-64.
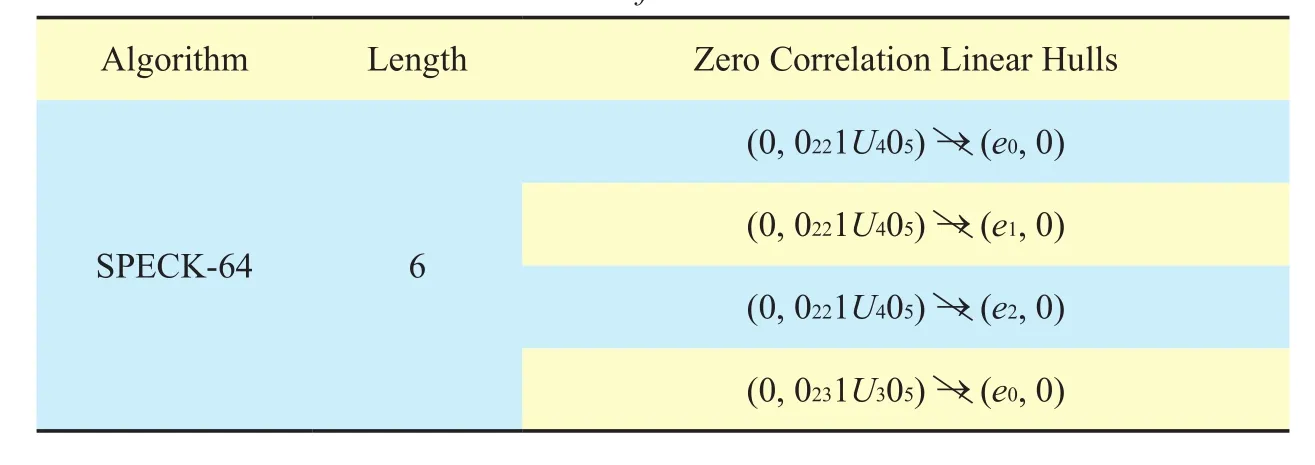
Table IX. Zero correlation linear hulls for SPECK-64.
ACKNOWLEDGEMENTS
The authors would like to thank the anonymous reviewers for their helpful comments.This work was supported by the National Natural Science Foundation of China under Grant No. 61572516, 61402523, 61202491,61272041 and 61272488.
[1] A. Bogdanov, V. Rijmen, “Zero correlation Linear Cryptanalysis of Block Ciphers,”IACR Eprint Archive Report 2011/123, March 2011.
[2] A. Bogdanov, V. Rijmen, “Linear hulls with correlation zero and linear cryptanalysis of block ciphers,”Designs, Codes and Cryptography, vol.70, no. 3, 2014, pp. 369-383.
[3] J. Chen, M. Wang, B. Preneel, “Impossible Differential Cryptanalysis of the Lightweight Block Ciphers TEA, XTEA and HIGHT,”Proc. AFRICACRYPT 2012, vol. 7374, 2012, pp. 117-137.
[4] A. Bogdanov, M. Wang, “Zero correlation Linear Cryptanalysis with Reduced Data Complexity,”Proc. Fast Software Encryption-FSE 2012, vol.7549, 2012, pp. 29-48.
[5] L. Knudsen, “DEAL – A 128-bit Block Cipher,” In:NIST AES Proposal, 1998.
[6] E. Biham, A. Biryukov, A. Shamir, “Cryptanalysis of Skipjack Reduced to 31 Rounds Using Impossible Differentials,”Proc. EUROCRYPT 1999,vol. 1592, 1999, pp. 12-23.
[7] E. Biham, O. Dunkelman, N. Keller, “Related-Key Impossible Differential Attacks on 8-round AES-192,”Proc. CT-RSA 2006, vol. 3860, 2006, pp.21-33.
[8] O. Dunkelman, N. Keller, “An Improved Impossible Differential Attack on MISTY1,”Proc. ASIACRYPTA 2008, vol. 5350, 2008, pp. 441-454.
[9] Y. Tsunoo, E. Tsujihara, M. Shigeri, T. Saito, T.Suzaki, H. Kubo, “Impossible Differential Cryptanalysis on CLEFIA,”Proc. Fast Software Encryption-FSE 2008, vol. 5086, 2008, pp. 398-411.
[10] A. Shimizu, S. Miyaguchi, “Fast data encipherment algorithm FEAL,”Proc. EUROCRYPT 1987,1998, pp. 267-278 (1988).
[11] D. Hong, J. Sung, S. Hong, et al, “HIGHT: A new block cipher suitable for low-resource device,”Proc. Cryptographic Hardware and Embedded Systems-CHES 2006, 2006, pp. 46-59.
[12] N. Ferguson, S. Lucks, B. Schneier, D. Whiting,M. Bellare, T. Kohno, J. Callas, J. Walker, “The Skein Hash Function Family,” Submission to NIST, 2008.
[13] R. Beaulieu, D. Shors, J. Smith, et al, “The SIMON and SPECK Families of Lightweight Block Ciphers,” Cryptology ePrint Archive, Report 2013/404, 2013.
[14] N. Ferguson, D. Whiting, B. Schneier, et al, “Helix:Fast encryption and authentication in a single cryptographic primitive,”Proc.Fast Software Encryption-FSE 2003, 2003, pp. 330-346.
[15] D. Whiting, B. Schneier, S. Lucks, et al, “Phelix:Fast encryption and authentication in a single cryptographic primitive,” ECRYPT Stream Cipher Project Report, 2005, 27(200): 5.
[16] D.J. Bernstein, “The Salsa20 family of stream cipher,” New stream cipher designs, 2008, pp. 84-97.
[17] D.J. Bernstein, “ChaCha, a variant of Salsa20,”Workshop Record of SASC, 2008.
[18] J.P. Aumasson, L. Henzen, W. Meier, et al, “Sha-3 proposal blake,” Submission to NIST, 2008.
[19] J.P. Aumasson, S. Neves, Z. Wilcox-O’Hearn, et al, “BLAKE2: simpler, smaller, fast as MD5,”Proc.Applied Cryptography and Network Security,2013, pp. 119-135.
[20] D. Gligoroski, V. Klıma, S.J. Knapskog, et al,“Cryptographic hash function BLUE MIDNIGHT WISH,” Submission to NIST, 2009.
[21] D.J. Bernstein, “CubeHash specification (2. B. 1) ,”Submission to NIST, 2008.
[22] D. Gligoroski, R.S. Ødegard, M. Mihova, et al,“Cryptographic hash function Edon-R’,”Proc.Security and Communication Networks-IWSCN 2009, 2009, pp. 1-9.
[23] D.J. Wheeler, R.M. Needham, “TEA, a tiny encryption algorithm,”Proc.Fast Software Encryption-FSE 1995, 1995, pp. 363-366.
[24] R. Needham, D. Wheeler, “eXtended Tiny Encryption Algorithm”, October 1997.
[25] D. Wheeler, R. Needham, “XXTEA: Correction to XTEA,” Technical report, Computer Laboratory,University of Cambridge, 1998.
[26] H. Wu, “The stream cipher HC-128,” New Stream Cipher Designs, 2008, pp. 39-47.
[27] S. O’Neil, K. Nohl, L. Henzen, “Enrupt hash function specification,” Submission to the NIST SHA-3 competition, 2008.
[28] J. Kim, S. Hong, J. Sung, C. Lee, S. Lee, “Impossible differential cryptanalysis for block cipher structures,”Proc.INDOCRYPT 2003, vol. 2904,2003, pp. 82-96.
[29] Y. Luo, X. Lai, Z. Wu, et al, “A unified method for finding impossible differentials of block cipher structures,” Information Sciences, 2014, vol. 263,pp. 211-220.
[30] S. Wu, M. Wang, “Automatic search of truncated impossible differentials for word-oriented block ciphers,”Proc.INDOCRYPT 2012, vol. 7668,2012, pp. 283-302.
[31] C. Tezcan, “Impossible Differential Cryptanalysis of Reduced Round HIGHT,” M.Sc. Thesis. Institute of Applied Mathematics, Middle East Technical University, Ankara, TURKEY, July 2009.D
[32] D. Hong, J.K. Lee, D.C. Kim, D. Kwon, K.H. Ryu,and D.G. Lee, “LEA: A 128-bit block cipher for fast encryption on common processors,”Proc.The 14th International Workshop Information Security Applications (WISA), 2013, pp.3–27.
[33] L. Wen, M. Wang, A. Bogdanov, and H. Chen,“Multidimensional zero-correlation attacks on lightweight block cipher HIGHT: Improved cryptanalysis of an ISO standard,”Information Processing Letters, vol. 114, no. 6, 2014, pp. 322-330.
杂志排行
China Communications的其它文章
- CYBERSPACE SECURITY: FOR A BETTER LIFE AND WORK
- A Cloud-Assisted Malware Detection and Suppression Framework for Wireless Multimedia System in IoT Based on Dynamic Differential Game
- An Integration Testing Framework and Evaluation Metric for Vulnerability Mining Methods
- Powermitter: Data Exfiltration from Air-Gapped Computer through Switching Power Supply
- CAPT: Context-Aware Provenance Tracing for Attack Investigation
- Decentralized Attribute-Based Encryption and Data Sharing Scheme in Cloud Storage
