T-IP: A Self-Trustworthy and Secure Internet Protocol
2018-03-13XiaofengWangHuanZhouJinshuSuBaoshengWangQianqianXingPengkunLi
Xiaofeng Wang*, Huan Zhou, Jinshu Su, Baosheng Wang, Qianqian Xing, Pengkun Li
School of Computer, National University of Defense Technology, Changsha 410073, China
I. INTRODUCTION
The Internet Protocol (IP) is the principal network layer protocol in the Internet. However it does not have any security protection [1].Unlike transport or application layer security,network layer security can provide transparent protection for all applications and higher level protocols (tcp/utp/icmp). Hence, the need for network layer IP security is becoming more pressing, with the increasingly successful and popular use of IP protocol. In the new networks including IoT (Internet of things),real-time system networks and resource-constrained networks, the network layer security must provide authentication, encryption and integrity for data traffic between hosts or networks. Meanwhile, it should keep the characteristics of IP to be lightweight and stateless.Moreover, the security protocol needs to have low connection latency and packet overhead.
Currently, IPsec is the de facto standard of the network layer security protocol. However IPsec has the following problems. (1) It has high connection latency and transmission overhead, since it uses the third- party credential based authentication and application layer key negotiation [2]. (2) It changes the stateless IP with complicated security session states.While making the protocol more complex, it may also cause packets dropping when they arrive at the wrong states, which needs new security session to be negotiated. (3) It cannot guarantee the accountability of IP address,since it does not authenticate the addresses.The spoofed address is the root cause for various network attacks such as to mask botnet device locations and to stage a reflected assault in DoS attacks such as DNS amplification attacks, smurf attacks, and NTP amplification attacks), and man-in-the-middle attacks.
To address the problems of IPsec, David[1] proposed the Accountable Internet Protocol (AIP), which uses the self-certifying IP address and does not need the credential based authentication. However, AIP needs a specific flat address structure, which is not compatible to the existing TCP/IP architecture and may degrade the routing performance. In addition,AIP did not talk about the secure data transmission. Similarly, Hummen [3] proposes a new lightweight IP security protocol using self-certifying IP address. It also suffers from the compatibility problem. To achieve low connection latency and overhead, most existing work focus on the transport layer security optimization. MinimaLT [4], Tcpcrypt [5],TCP Fast Open (TFO) [6] and Stream Control Transmission Protocol (SCTP) [7] try to encrypt the session and accelerate the connection process for TCP protocol. QUICK [8] provides an efficient and secure stream transport over UDP. These mentioned transport layer security protocols can only be used in a specific TCP or UDP protocol. They cannot provide a common IP protection for all transport layer protocols such as ICMP.
In this paper, we extend our previous work[15] to propose the self-trustworthy and secure Internet protocol (T-IP) with full compliance to TCP/IP. TIP has the following main contributions: 1. We design the self-trustworthy T-IP mechanism, which can use the current IP address as its corresponding public key directly. Hence, T-IP provides the address accountability, since the attacker cannot get the private key for the spoofed address. To the extent possibility, this kind of authentication can resist the Distributed Denial of Service(DDoS) attack. 2. Since T-IP does not need credential based authentication or application layer key negotiation, it has negligible connection latency and transfer overhead. 3. T-IP can derive the symmetrical session key directly from the self-trustworthy address. Therefore, it can reserve to be stateless without needing to maintain the complicated security negotiation states. 4. The overall T-IP design is compatible with the existing network architecture, hence it is flexibly deployable. We theoretically prove our shared secret key in T-IP is adaptively secure in the random oracle model. In addition,we enhance the T-IP shared secret key calculation to achieve forward secrecy security and be resistant to the known session key attack.We analyse the possibility of the application of T-IP, including its resilience against the man-in-the-middle attack and DoS attack. The evaluation shows that TIP has a much lower transmission overhead and connection latency than IPsec. In addition, our opportunistic encryption design enables T-IP to be deployed step by step.
The rest of the paper is organised as follows. Section II introduces some related work.In Section III, we present some prerequisites about T-IP, including cryptographic background, threat model, security goals and some assumptions. In Section IV, we give the T-IP design and demonstrate its feasibility in theory. It is followed by implementation details and evaluation in Section V. Finally, we have discussion and conclusion in Section VI.
II. RELATED WORK
IPsec is the most used secure protocol in the network layer. However, IPsec relies on certificates to establish a secure session. The certificate distribution and verifying brings heavy transportation overhead and connection latency to the IP communication. Moreover,IPsec needs to maintain complicated states for each session, which changes the stateless IP and makes it vulnerable to DDoS attacks. In addition, IPsec can only authenticate the packet’s user identity. The source addresses of the packets cannot be authenticated.
AIP [1] was proposed by David to provide the source ID accountability. It takes the users’public keys to be a part of the address. Hummen [3] designed a lightweight IP security protocol for the Internet of things (IOT), and proposed three security extensions. Sumit [16]proposed a light-weight cryptographic pro-tocols, which can achieve high security with minimal processor capacity requirement. HIPDEX (Host Identity Protocol Diet Exchange)[17] is a variant of HIP Base Exchange specially designed to reduce the complexity of cryptographic computations. However, these work suffer from the compatibility problem.They are not compatible to the existing TCP/IP architecture, since they all need to change the original semantic of IP address or the protocol architecture.
To achieve low connection latency and overhead, existing work focus on the transport layer security optimization. MinimaLT [4] is a new secure protocol to provide server and user authentication. It changes the TCP process and uses a controlled TCP connection to be faster than TLS. However, it only focuses on TCP connections. Therefore, it is not suitable for UDP applications and end-to-end fast communication. TCP Fast Open (TFO) [6] improves the performance of short transfers by issuing a security cookie to forge TCP’s three-way handshake. Tcpcrypt [5] designs a ubiquitous transport-level encryption to minimize the cost of key negotiation. The DTLS (Datagram Transport Layer Security) protocol [18] has been proposed to operate over the unreliable transport protocol and provides the same high security level as TLS. QUICK [8] replaces TLS and TCP with an efficient and secure stream transport over UDP. In summary, the above mentioned transport layer security protocols can only be used in a specific TCP or UDP protocol. They cannot provide a common IP protection for all transport layer protocols such as ICMP.
III. PREREQUISITES
In this section, we present several key mechanisms on cryptographic, discuss our threat model and goals, then put forward necessary assumptions.
3.1 Cryptographic background
In this section, we provide background on the cryptographic mechanisms used in this paper:bilinear map and several related hard cryptographic problems.
Bilinear Map:We defineG1andG2.They are additive groups formed by points on different elliptic curves.GTis a multiplicative group. Their orders are allq, a very large prime number. The bilinear map is defined asIt has three properties. The most important one is as follow:
• Bilinearity:and ∀a,b∈Zq*, the followings hold.
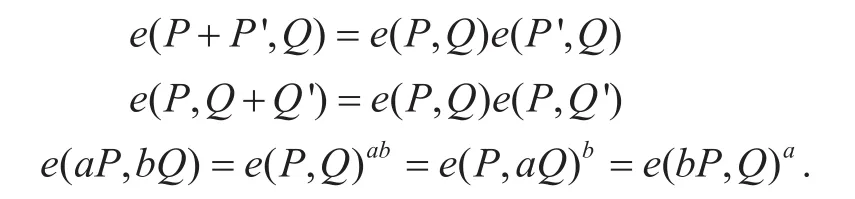
Cryptographic Problems:We discuss the cryptographic problems in the group ofG1.It stands for the group of elliptic curve. Our protocols are mainly based on CBDH hard problem.
• Computational Bilinear Diffie-Hellman Assumption (CBDH):The CBDH assumption in bilinear group systemis that for any PPT adversaryA:
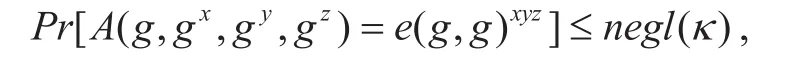
where the probability is taken over the choice of
3.2 Threat Model
We are concerned with an attacker that will try to destruct the integrity and confidentiality of network traffic. The attacker can intercept and modify arbitrary packets. This can be a man-in-the-middle attack. He uses an arbitrary IP address to communicate with others to impersonate one of the participants. In addition,we want to resist the attacks on availability,such as DoS. This attack is addressed by some malicious users with powerful machines. The attacker creates a lot of fake users with forged IP addresses. They all connect the target user at one time. To resist this attack, we need authorize the identity and address of other user and break those invalid connections.
An identity-based non-interactive session key exchange scheme consists of the following polynomial-2time algorithms:
•Setup(κ,n): on input a security parameter κ and a parameter n for the number of participants, output master public keympkand master secret keymsk. LetIbe the identity space andSHKbe the share key space.
•Extract(msk,id): on input msk and identityid∈I, output a secret keyskidfor id.
•Share(skid,IS): On input secret keyfor identity id and a listIS∈Inconsisting ofnidentities, output a shared keyshkforIS. We assume that the identities inISare always lexicographically ordered.We follow the security notions presented in
[9]. Let A be an adversary against the session key exchange scheme and define its advantage as:
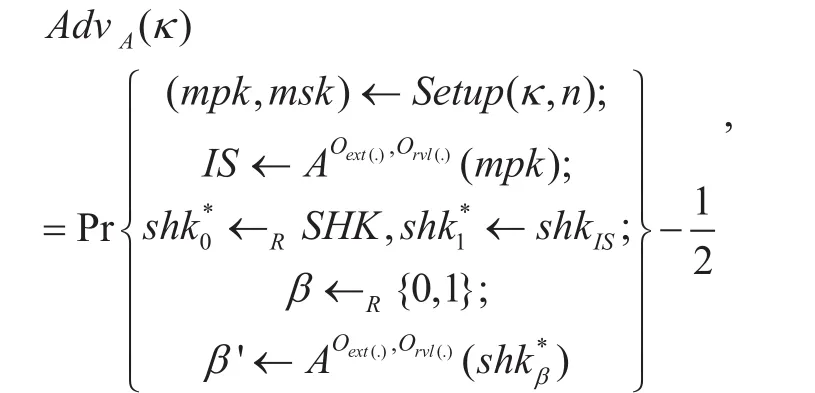
Where
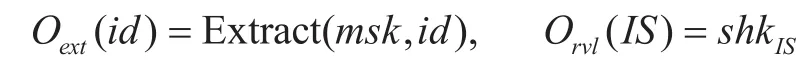
andAis not allowed to queryOext(·) for any identityid∈Iand queryOrvl(·) forIS. We say that an identity-based non-interactive session key exchange scheme is adaptively secure if no PPT adversary has non-negligible advantage in the above security experiment.The adaptive security is the strongest security notion for the identity-based non-interactive session key exchange schemes so far.
3.3 Goal
Our core goal is to make the communication between every participant as lightweight as possible. At the same time, the session should still be secure and authenticated. To enable such a usable system and maintain high security, we outline four essential properties required in T-IP:
•Secrecy:The messages transferred in the network should be in cipher text. Furthermore, the security level should be higher than the traditional RSA algorithm adopted by IPsec.
•Lightweight:The communication and computing overhead for establishing a secure session should be low.
•Authenticity:Every participant in a session should be sure that the one they are talking about is exactly the one they want to communicate with. Therefore, the source address of the packet should be authenticated.
•Easy to deploy:First, the protocol should be compatible to traditional network structure. Then, the protocol should have the property of incremental deployment. That means the host supporting T-IP still be able to communicate with the host without this protocol.
3.4 Assumption
Security does not mean absolutely secure in any circumstances. Our protocol does need to assume certain conditions to make the system execute successfully. First, we assume that the management center, namely the IP-Private Key Generator (IP-PKG), is secure. That means no attacker can compromise the master key of the IP-PKG. Because every participant’s private key is derived from this master key. Second,we assume that the whole process of private key delivering is secure. The channel used for private key delivering between the IPPKG and the participant should be protected by other security technologies. For example, it can be protected by traditional IPsec. Although this is time-consuming, the participant just makes this operation once when he gets on line. We have also proposed another efficient method[11]. But we just assume the private key cannot be compromised during delivering, as this aspect is outside the scope of this work.
IV. T-IP DESIGN
In this section, we demonstrate the process and principle of T-IP. The T-IP communication system mainly includes two parts: T-IP self-certified address management and T-IP communication protocol.
4.1 T-IP self certified address management
4.1.1 T-IP Management Framework
In T-IP communication, the IP address can serve as its public key directly, hence it is trustable. However, the communicating host needs to have the Identity Based Encryption(IBE) private key for its IP address (we call it T-IP private key for short). As shown in Figure 1, for each administration domain, we assume there is a trust administrator named the IPPKG, which is responsible for the T-IP private key management. When a host joins the system, the IP-PKG authenticates the host and generates the T-IP private key for it. The T-IP Management includes two steps: IP-PKG initialization and TIP private key management.
1) IP-PKG initialization: As the trust administrator for a domain, the IP-PKG needs to be initialized first and publish its public parameters. It selectsG,GT,P,e, whereGis an additive group formed by points on a certain elliptic curve,GTis a multiplicative group,Pis a generator element ofG, ande:G×G→GTis an admissible bilinear map ofG.
2) T-IP private key management: After being initialized, the IP-PKG needs to generate the T-IP private keys for all the participants in its domain, and be responsible for the private key update and revocation. Assume Alice requests to join the system, she authenticates herself and her IP addressIPAto the IP-PKG.
Then the IP-PKG generates the T-IP private key forIPAby using the IBE technology. However, IP-PKG does not useIPAdirectly. It usesIPAand other elements to form a new stringTIPA, called T-IP self-certified address (the formation of T-IP self-certified address will be discussed in detail later). Then it maps the string ofTIPAto a point of the elliptic curve,H1(TIPA). Then the private key ofIPAisSA=sH1(TIPA). Finally, the IP-PKG needs to distributeSAto Alice in a traditional secure way or simpler way [11].
4.1.2 T-IP Self Certified Address
In previous part, we mention about T-IP self certified address. This is a key part of T-IP private key management. Before showing the formation of T-IP address, we discuss the problems if we directly take the IP address as the T-IP address.
Firstly, the IP address is not fixed to some participant in campus network or other local area networks. When the attacker Malice is assigned “192.168.1.2” for communication,she can authenticate herself to the IP-PKG with her own identity. Then she gets the T-IP private key corresponding to the IP address.However, she does not delete this private key when she is off-line. So when Alice is assigned the IP address of “192.168.1.2”, Malice can capture the packets of Alice. She uses her previous stored private key and the destination address in the packet to generate the session key with bilinear map. In this way, Malice can compromise the Alice’s private key and impersonate her.

Fig. 1. T-IP management.
Secondly, the problem is the key revocation. In IPsec, the Certificate Revocation List(CRL) works for key revocation. Every time before communication, the participant checks the CRL to confirm whether the certificate of the opponent has been revoked. Then the corresponding private key is also revoked. However, we cannot realize the key revocation, if we just take opponent’s IP address as the T-IP address. Because if the participant gets the T-IP private key corresponding to the IP address, the private key cannot be revoked automatically. If we adopt the similar mechanism as the CRL, it will increase the complexity of T-IP.
Considering the technical features of IBE,an arbitrary string can be the public key.Therefore, we carefully design the structure of T-IP address when implementing the T-IP. As for the first problem, we add the participant’s ID into the T-IP address. This makes differences between Alice’s and Malice’s T-IP address.Hence, Malice cannot get the same T-IP private key as that of Alice and decrypt the packets of Alice. As for the second problem, we can divide the whole day into 12 parts and one part is 2 hours. When a host starts up, we add the time period according to the current time into the TIP address. Therefore, Alice can only get the T-IP private key for the current period and the private key will become expired after the specific time. Because the opponent will calculate the new session key with the new T-IP address. Hence, previous T-IP private key is revoked automatically. In a word, the T-IP address of the participant can be expressed as
Among them, “YYYY.MM.DD:HH-HH”defines the format of current time period. “Y”means year. ”M” means month. ”D” means day. ”H” means hour. ID is the identity of the participant.
For instance, Alice’s host starts up when the Greenwich Mean Time is 03/18/2015 21:10.Obviously, 21:10 belongs to the time period of 20:00 to 22:00. Therefore, theTIPAis not merely the IP address. It also needs to concatenate the identity and the time string. In this case, if the IP address of Alice is “192.168.1.2”,then

The other computing steps are the same with the procedure mentioned above. But this makes the session key is only valid in this period of time for just two hours. It is worth to mention that two hour here is just an example.The valid time duration can be set by the IPPKG. It is a trade-off between the workload of the IP-PKG and security.
4.2 T-IP communication protocol
Compared with IPsec, we design T-IP to be a lightweight secure network protocol without needing the credential based authentication or key negotiation. Based on the T-IP self-trustworthy address, the two T-IP communicating participants can calculate the symmetric session keyskeyby using its own T-IP private key and the opponent’s T-IP address (T-IP public key) directly. The IBE technology can guarantee that the session key can only be generated by the sender and receiver who have the T-IP private key for the packet’s source and destination address respectively. Therefore, T-IP can achieve an authenticated and secure data transmission directly without costing time on credential based authentication or key negotiation. In the next part, we give a simple introduction to the T-IP packet format and procedure.
4.2.1 T-IP packet format
T-IP is between the network layer and the transport layer. As shown in Figure 2, it is a part of T-IP packets. The IP header is omitted here, as it is almost the same as a normal IP packet. However, the “protocol” field of IP header should be a new protocol number to figure out the packet is in the format of T-IP.We define the protocol number of T-IP is 150.The packet format mainly contains two parts:T-IP header and T-IP tail. As T-IP is between two layers, the T-IP header is after IP header and followed by the header of original transport layer. In T-IP header, the meanings of every field are as follows:
Next Header:The length of this field is one byte. This is an integer number defining what protocol is in the following transport lay-er. When it indicates TCP or UDP, the session is in T-IP transport mode. When it indicates IP, the session is in T-IP tunnel mode. These modes are similar to the modes of IPsec.
Algorithm:The length of this field is one byte. This is an integer number defining the type of the symmetric cryptography algorithm.This field is used for packet encryption and decryption. The length of this field is only one bit. This field works as a flag bit. If the flag bit is 1, the T-IP packet includes the MAC field to verify the packet integrity.
Reserved:Currently, the length of this field is 15 bits. This is a reserved place for T-IP new functions in future.
Sequence Number:The length of this field is 4 bytes. It’s similar to the sequence number of IPsec. The receiver adds the sequence number he received by 1 and then send back to the sender. It has two functions. One is used for protecting the session from replay attack.Because the sequence number is different every time. The attacker cannot reply the packet with a specific sequence number. The other is used for authenticating the opponent’s identity.Because only the user with the right identity can send back the correct sequence number and the MAC.
Message Authentication Code(MAC):The length of this field is 20 bytes. This field is generated from some hash function and can protect the packet from malicious modification.
In T-IP tail, the meanings of every field are as follows:
Padding:The length of this field is variable. This field is used for encryption and decryption, as to satisfy the length requirement for the symmetric cryptography algorithm.
Padding Length:The length of this field is one byte. This is an integer number indicating how many bytes are padded.
In addition, Figure 3 shows the encryption and authentication scope of T-IP packet. The shadow parts of the figure indicate that these fields are included in the scope of authentication. MAC is generated from these fields.
4.2.2 T-IP protocol procedure
T-IP has two transmission modes: transport mode and tunnel mode. They have different packet construction mechanisms but the same protocol procedure. Next, we focus on the T-IP protocol procedure. Assuming Alice (with T-IP addressTIPA) is going to communicate with Bob (with T-IP addressTIPB). They have got their T-IP private keysrespectively from the IPPKG. The detailed procedure of the T-IP protocol is shown in Figure 4.
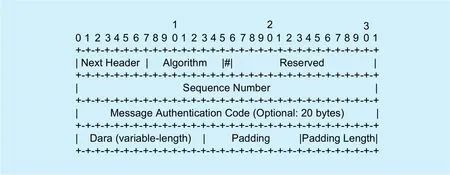
Fig. 2. T-IP protocol format.

Fig. 3. T-IP protocol format.
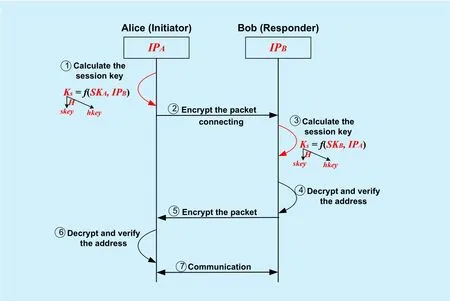
Fig. 4. T-IP protocol communication.
1. Alice uses her T-IP private key and Bob’s T-IP address to calculate the shared secret valueKAB=e(SA,H1(TIPB)). Then she concatenates the shared secret value with a specific string to generate the symmetric cipher keyskeyand MAC (Message Authentication Code) keyhkeyas follows:

2. Alice uses the cipher keyskeyto encrypt the packetM1 and gets the encrypted packetC1=Eskey[M1]. Meanwhile, she uses the MAC keyhkeyto authenticate the packet,MAC1=Hhkey[M1].MAC1 is inserted into the packet field “MAC” for the packet integrity check. Then Alice constructs the packet in the protocol format according to the transmission mode and sends it to Bob.
3. After receiving the packet from Alice, Bob uses his TIP private key and Alice’s T-IP address to calculate the shared secret valueKBA=e(H1(TIPA),SB). Then he can getskeyandhkeyas step 1.
4. Bob decrypts the packet with the keyskeyand authenticates its source address. If the source address is spoofed (Alice is impersonated), the format of the decrypted packet would be in chaos. This is because the attacker personating Alice cannot get the T-IP private key of Alice’s T-IP address,and he cannot calculate the rightskeyandhkeywith Bob. Therefore, the packets with spoofed address cannot pass the authentication test.
6. After receiving the packet from Bob, Alice decrypts the packet and authenticates the source address as Bob in step 4.
7. Finally, after the two participants have authenticated each other by verifying the addresses, they can establish a trustworthy and secure session.
We can prove that both Alice and Bob are able to calculate the same shared value. Because

4.2.3 Security analysis and attack resistance
Theorem 1.The T-IP session key exchange scheme is adaptively secure in the random oracle model assuming the CBDH assumption. Suppose H and G are random oracles,for any adversaryAbreaking this session key exchange scheme with advantageAdvA(κ) that makes at mostqeextraction queries andqrreveal queries andqgrandom oracle queries to G, there is an algorithmBthat solves the CBDH problem with advantage 4AdvA(κ)/e2(qe+qr)2qg, whereeis the natural logarithm.
Proof. Given the CBDH instance (g,g1=gx,g2=gy, g3=gz) in bilinear group system (p,G,GT, e)G(κ),Binteracts withAwith the Setup:Bsetsh=gx, then setsmpk=(g, h,H, G) andmsk=x(which is unknown to him), treats H and G as random oracles, sendsmpktoA. To process random oracle queries,Bmaintains two associated listsHandG. Each entry inHis of the form (id;mark;coin;t;pk), whereid∈I,mark,coinThe rest setting has been illustrated in [9]. Finally we have
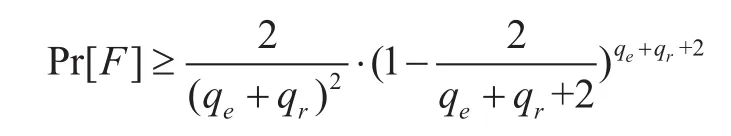
andAdvB(κ) =Pr[F]·AdvA(κ)/qg. According to the estimation that limthe maximum value of the lower bound for Pr[F]is approximate 2/e2(qe+qr)2.
Then, we figure out some of the attacks that T-IP can resist. These indicate that how T-IP can be applied in these cases.
Source Accountability:Besides the encrypted communication, T-IP has the security feature of source accountability. Source accountability means that if a host uses a source address that has been assigned to another host, this kind of malicious behaviour can be detected. A harder-todetect form of spoofing occurs when a malicious or compromised host uses a source address to impersonate other users. There are such attacks observed in the Internet and they are used to send spam [12]. However, T-IP supports the source accountability naturally. To prove this security feature, we assume the attacker Malice use IP address “192.168.1.3” of Bob impersonating him to com- municate with Alice as the assumption in section 2. Alice takes the T-IP address of the opponent as“192.168.1.3||Bob||XXXX:XX:XX”. Therefore, Mali- ce should use the private key corresponding to “192.168.1.3||Bob||XXXX-:XX:XX” to generate the session keys as T-IP procedure. Obviously, Malice cannot get that private key because she only has the private key corresponding to her own T-IP address.Hence, if two participants are able to establish connection in a session with T-IP, then the source address of the packet is accountable.
Man-in-the-middle attack:Man-in-themiddle attack refers that Malice impersonates Bob to communicate with Alice and at the same time, impersonates Alice to communicate with Bob. In this way, Malice can get the encrypted content without comprising the session key. However, we have demonstrated that T-IP has the security feature of source accountability. Then Malice cannot impersonate anyone else to communicate with T-IP. Hence,T-IP can resist man-in-middle attack.
Denial of service attack: Denial of service attack refers that Malice uses some method to make Alice not be accessed normally by Bob.One of the method is IP spoofing. That is Malice impersonates Bob and sends a RST packet to Alice, then the session between Alice and Bob will be interrupted. But with T-IP, the RST packet from Malice will be detected as invalid because of source accountability. Another method is Malice forges a lot of packets with different source IP addresses to generate a lot of sessions with Alice. Then Alice’s normal session with Bob will be affected. But with T-IP, Malice cannot obtain so many private keys corresponding to the forged IP addresses.So the forged packets cannot establish session successfully. Therefore, T-IP can resist Denial of service attack.
4.2.4 Security-enhanced procedure under Known session keys attack in T-IP protocol The symmetric cipher keyskeyand MAC(Message Authentication Code) keyhkeyin the preliminary procedure is fixed. Once an adversary who has learned the cipher key or the MAC key at some time, he could always decrypt the cipher and the encrypted packets afterward. We improve the security against this known session keys attack by employing a newly shared secret value computation method.
We change the shared secret keys of different flows. For the very flow, we add the constant information in its IP Header to the shared secret value. Without loss of generality,we hash the specific information for a flow including the version number, the service type,the protocol type and the IP-tuple <Source-IP, Dest-IP> asx. ThenAlice calculates the shared secret value asKAB=e(SA, xQB)e(QA,xQA).
Then she concatenates the shared secret value with a specific string to generate the symmetric cipher keyskeyand MAC (Message Authentication Code) keyhkeyas follows:

Alice uses the cipher keyskeyto encrypt the packetM1 and gets the encrypted packetC1=Eskey[M1]. Meanwhile, she uses the MAC keyhkeyto authenticate the packet,MAC1=Hhkey[M1].MAC1 is inserted into the packet field “MAC” for the packet integrity check. Then Alice constructs the packet in the protocol format according to the transmission mode and sends it to Bob.
After receiving the packet from Alice,Bob firstly hashes the constant information extracted from the packet asx, and calculate the shared secret valueKBA=e(xH1(TIPA),SB+QA). Then he can getskeyandhkey. After the two participants have authenticated each other by verifying the addresses, they can establish a trustworthy and secure session.
We can prove that both Alice and Bob are able to calculate the same shared value. Because

Security Analysis: If an adversary learned the cipher key or the MAC key of one flow between Alice and Bob, he is unable to calculate the keys of another flow between Alice and Bob. For the tight proof, we assume the adversary directly learned the shared secret valueKAB-x=e(SA,xQB)e(xQA,QA) and he tries to deriveKAB-y=e(SA,xQB)e(xQA,QA).Without the secret key of Alice, the adversary cannot deriveKAB-yfromKAB-x. If the adversary directly learned the shared secret valueKBA-x=e(xQA,SB+QA) and he tries to deriveKBA-y=e(yQA,SB+QA). Without the secret key of Bob, the adversary cannot deriveKBA-yfromKBA-x.
Moreover, our procedure achieves the unknown key-share attribute which means Alice cannot be coerced into sharing a key with Bob without Bob’s identity, i.e., when Alice believes the key is shared with Bob.
Additionally, forward security has been considered so long as the hash is correlated with the time. Since the clock synchronization and management is one of the other problem as the T-IP infrastructure to support T-IP protocol, we omit here and will demonstrate it in the future.
V. IMPLEMENTATION & EVALUATION
Last section, we have demonstrated the basic principles and processes of T-IP in detail. In this section, we will discuss the protocol implementation in Linux kernel. Furthermore,we put forward a method to make T-IP easier to deploy.
5.1 Technical framework
As the Linux is an open-source operating system, we choose the protocol stack in Linux to realize T-IP.
In the user mode, T-IP private key management module is responsible for achieving and storing the T-IP private key. It provides the private key for the T-IP Internet Key Calculation(T-IKC) module. Then, T-IKC module is used for calculating the shared secret value between two communicating hosts, and to generate the symmetric cipher keyskeyand MAC keyhkeyfor communicating sessions. The configuration module provides the interface for users to dynamically configure the T-IP security policies, such as which IP addresses to use, which transfer mode and encryption algorithm to use in TIP communication, etc. It communicates with the module in the kernel to change the configuration of T-IP. On the other hand, T-IP table management module and cryptographic module are implemented in the kernel mode.The former module is responsible for configuring and managing T-IP table. It provides the interfaces of managing the T-IP table for other modules. The later module consists two submodules, packets encryption and decryption. It uses the configured symmetric cryptographic algorithm and the session key stored in T-IP table to encrypt or decrypt the packets according to the security policy.
Finally, there is a T-IP table in the kernel mode. This data structure records all the related security attributes with other participants,including cache session keys.
5.2 Framework increased security implementation
Increased security means a mechanism to guarantee the usability of the new security system and its compatibility to the old system.This mechanism can enable the new system to be deployed step by step. IETF has just funded a new group of TCPINC (TCP Increased Se-curity) to make TCP satisfy increased security[13].
For network security, the increased security is mainly based on the idea of opportunistic encryption [14]. In the opportunistic encryption communication, the new deployed system tries to connect other opponents with the new encryption technology first. If the opponent does not support the new encryption technology, both of the participants fall into the old communication mechanism. We apply this idea into T-IP. The T-IP participant try to communicate with other participants by using T-IP first. If the other opponent supports T-IP, the communication will be carried out by T-IP. On the contrary, the session falls back into IPsec or unsecured communication.
As for implementation, the cryptographic modules and TIP table need to work together to realize the increase security. These modules have been introduced above. The packet encryption module is on the packet input path and the packet decryption module is on the output path. These two modules can analyse the packets and change their forwarding paths.Figure 5 illustrates the principle of this implementation.
5.3 Evaluation
In this section, we evaluate the function and performance of T-IP, especically on the packet overhead and latency. From the perspective of connection latency, we design an experiment that Alice communicates with Bob at different packet loss rate. Figure 6 shows T-IP is nearly 3s faster than IPsec at the packet loss rate of 0. Meanwhile, the connection latency of T-IP has a much slower increase speed than IPsec, when the packet loss rate rises. In particular, when the packet loss rate comes to 15%, the connection latency of IPsec becomes dozens of times longer than that of T-IP. Because there are complicated states transition in IPsec. When the packet loss rate rises, the packet arriving at a wrong state makes the process of key negotiating restart again. However,T-IP is a stateless protocol. The connection latency of it is not significantly affected by packet loss rate. Therefore, T-IP is much better for unstable network.

Fig. 5. Principle of increased security implementation.
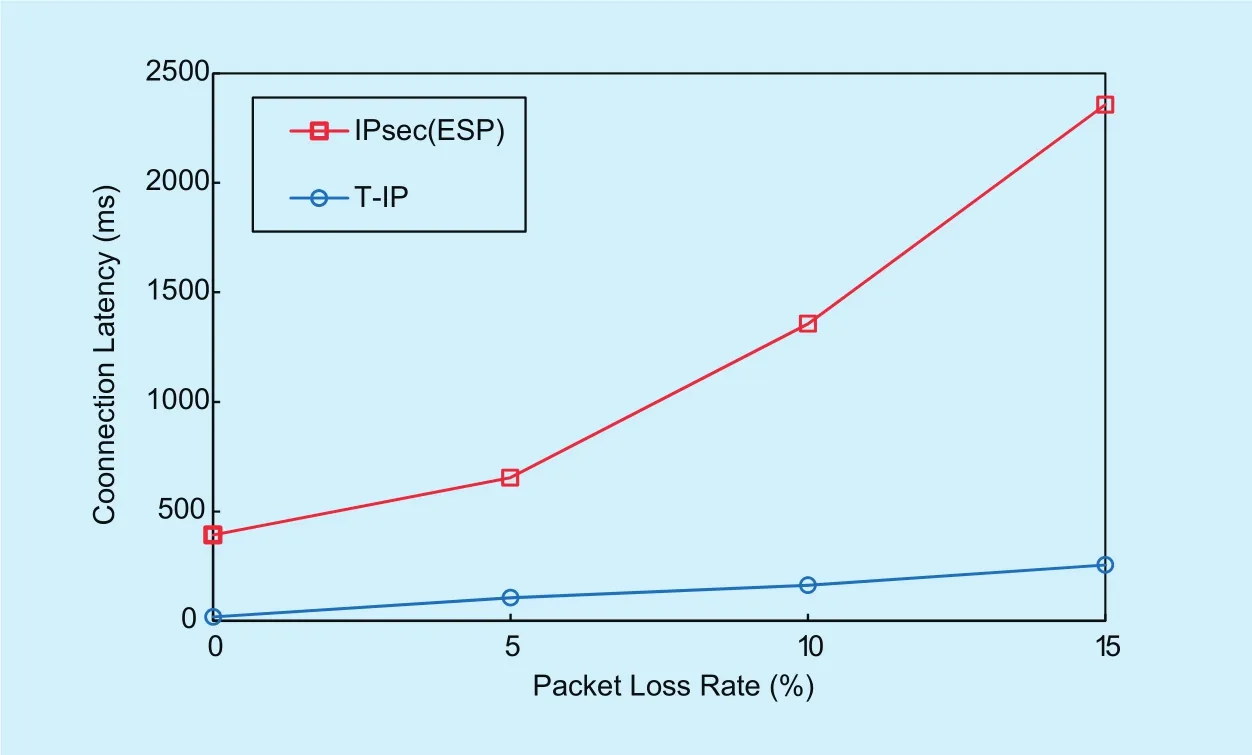
Fig. 6. Connection latency.

Fig. 7. Transmission overhead with UDP.
As for performance evaluation on transfer-ring overhead, we design two kinds of experiments to achieve the evaluation. In the first experiment, Alice chooses TCP as the transport layer protocol to send a certain amount of valid data to Bob with IPsec and T-IP. For IPsec, we choose to use Encapsulate Security Payload (ESP). Respectively, we choose T-IP with MAC. They are both in transport mode.On the other hand, Alice chooses UDP as the transport layer protocol in the second experiment. In every experiment, we use Wireshark to capture all the packets and calculate the transmission overhead.
For the purpose of visualization, Figure 7 illustrates the overhead of comparison between IPsec and T-IP. This pie figure shows the evaluation result when transferring 1 KB valid data with UDP. On this occasion, the overhead of T-IP is 74.3% lower than that of IPsec. The area of the pie represents the amount of data in both of the pie charts in Figure 7. Therefore,the areas of the white space for T-IP and IPsec are the same. Because Alice transfers the same amount of valid data with TIP and IPsec respectively. This figure obviously demonstrates that T-IP is much more lightweight than IPsec.

Fig. 8. Overhead comparison between T-IP and IPsec.
Figure 8 contains four subfigures, describing the evaluation results of both two experiments. In Figure 8(a) and 8(c), the vertical coordinates represents the percentage of the valid data in all transferring data when transferring a certain amount data. From these figures, we can prove that T-IP costs much less than IPsec when transferring small amount of data, no matter with TCP or UDP. In addition,T-IP always is more lightweight than IPsec.However, Figure 8(b) and 8(d) shows that the overhead of T-IP and IPsec come close with both TCP and UDP. Because the overhead of T-IP only consists of transmission control overhead and a little amount of padding bytes for encryption. The transmission control over-head refers to the packets for establishing and breaking connection. It also refers to the protocol headers in every packet, including IP header, T-IP header, etc. However, the overhead of IPsec not only consists these overhead of T-IP, but also includes the huge overhead for transferring certificates with either TCP or UDP. Therefore, T-IP is more lightweight. But when the amount of valid data increases to 1 MB, the overhead of TIP and IPsec nearly become same. Because the transmission control overhead is almost fixed as analyzed above.Therefore, when the total amount data transferred becomes large, the extra overhead for IPsec seems little. That means T-IP is much better for control network, in which only a few bytes of command are transferred. In addition,when transferring the same amount data, TIP with UDP is more efficient than T-IP with TCP. Because UDP do not need to establish a connection and it is just an unidirectional transferring process. This is also why the percentage of valid data for T-IP with UDP stays at 92.5%. Therefore, this means that T-IP is much better for realtime applications, because most of these applications adopt UDP for communication.
VI. CONCLUSION
The network layer security can provide transparent protection for all applications and higher level protocols. However, the existing network layer IPsec protocol is heavyweight without the address accountability guarantee.Moreover, it has a high transmission overhead and latency. Hence, we propose the self-trustworthy and secure Internet protocol (T-IP).TIP adopts the identity based encryption technology to take IP address as public key directly. This method reserves the semantics of IP address. Therefore, T-IP is compatible with the TCP/IP protocol stack. In addition, T-IP uses the non-interactive session key exchange method, which enables the protocol to be stateless and lightweight as IP. Moreover, TIP has negligible connection latency and transfer overhead. Finally, the increased security makes T-IP easy to deploy. In this paper, we demonstrate the correctness of T-IP communication, not only from the theoretical analysis but also from the practical experiments. The experiments show that T-IP has a much lower transmission overhead and connection latency than IPsec. It provides an efficient security protocol for the time-critical applications, resource-constrained and IoT networks.
ACKNOWLEDGEMENTS
The work has been supported by the national key research and development program under grant 2017YFB0802301 and Guangxi cloud computing and large data Collaborative Innovation Center Project.
[1] D G Andersen, H Balakrishnan, N Feamster,et al., “Accountable Internet Protocol (AIP)”,ACM SIGCOMM Computer Communication Review,vol. 38, no. 4, 2008, pp. 339-350.
[2] D K Smetters, G Durfee, “Domain-based administration of Identity-based cryptosystems for secure email and IPSEC”,Proc. USENIX Security Symposium, 2003.
[3] R Hummen, H Wirtz, J H Ziegeldorf,et al., “Tailoring end-to-end IP security protocols to the Internet of Things”,Proc. IEEE International Conference on Network Protocols (ICNP), 2013, pp.1-10.
[4] W M Petullo, X Zhang, J A Solworth,et al.,“Minimalt: Minimal-latency Networking through better security”,Proc. ACM SIGSAC Conference on Computer and Communications security,2013, pp. 425-438.
[5] A Bittau, M Hamburg, M Handley,et al., “The case for ubiquitous transport-level encryption”,Proc. USENIX Security Symposium, 2011, pp.403-418.
[6] Y Cheng, J Chu, S Radhakrishnan,et al., “TCP fast open”, RFC 7413, 2014.
[7] R Stewart, “Stream Control Transmission Protocol”, RFC 4960, 2007.
[8] A Langley, A Riddoch, A Wilk,et al., “The QUIC transport protocol: Design and Internet-scale Deployment”,Proc. ACM SIGCOMM, 2017, pp.183-196.
[9] Y Chen, Q Huang, Z Zhang, “Sakai–Ohgishi–Kasahara Identity-based non-interactive key exchange revisited and more”,International Journal of Information Security, vol. 15, no. 1,2016, pp. 15-33.
[10] S Blake-Wilson, D Johnson, A Menezes, “Key agreement protocols and their security analysis”,Proc. IMA International Conference on Cryptography and Coding, 1997, pp. 30-45.
[11] D Cao, X F Wang, F Wanget al., “SA-IBE: A secure and accountable identity-based encryption scheme”,Journal of Electronics and Information Technology, vol. 33, no. 12, 2011, pp. 2922-2928.
[12] A Ramachandran, N Feamster, “Understanding the network-level behavior of spammers”,ACM SIGCOMM Computer Communication Review,vol. 36, no. 4, 2006, pp 291-302.
[13] TCP increased security (TCPINC), 2014, https://datatracker.ietf.org/wg/tcpinc/documents/.
[14] C Castelluccia, G Montenegro, “Opportunistic encryption for IPv6”, Inria technical report,2002, http://www. inria. fr/rrrt/rr-4568. html.
[15] X F Wan, H Zhou, J S Su,et al., “Poster: T-IP: A self-trustworthy and secure internet protocol with full compliance to TCP/IP”,Proc. ACM SIGSAC Conference on Computer and Communications security, 2014, pp. 1520-1522.
[16] S Mishra, “Network security protocol for constrained resource devices in Internet of Things”,Proc. IEEE India Conference, 2016, pp. 1-6.
[17] S Sahraoui, A Bilami, “Efficient HIP-based approach to ensure lightweight end-to-end security in the Internet of Things”,Computer Networks, vol. 91, 2015, pp. 26-45.
[18] P. M Kumar, U. D Gandhi, “Enhanced DTLS with CoAP-based authentication scheme for the Internet of Things in healthcare application”,Journal of Supercomputing, vol. 3, 2017, pp. 1-21.
杂志排行
China Communications的其它文章
- CYBERSPACE SECURITY: FOR A BETTER LIFE AND WORK
- A Cloud-Assisted Malware Detection and Suppression Framework for Wireless Multimedia System in IoT Based on Dynamic Differential Game
- An Integration Testing Framework and Evaluation Metric for Vulnerability Mining Methods
- Powermitter: Data Exfiltration from Air-Gapped Computer through Switching Power Supply
- CAPT: Context-Aware Provenance Tracing for Attack Investigation
- Decentralized Attribute-Based Encryption and Data Sharing Scheme in Cloud Storage
