Privacy Protection Based Access Control Scheme in Cloud-Based Services
2017-05-08KaiFanQiongTianJunxiongWangHuiLiYintangYang
Kai Fan, Qiong Tian, Junxiong Wang, Hui Li, Yintang Yang
1 State Key Laboratory of Integrated Service Networks, Xidian University, Xi’an, 710071, China
2 Key Lab.of the Minist.of Educ.for Wide Band-Gap Semiconductor Materials and Devices, Xidian University, Xi’an, 710071, China
* The corresponding author, email: kfan@mail.xidian.edu.cn
I.INTRODUCTION
With the rapid development of cloud computing, big data and public cloud services have been widely used.Users can store their data in the cloud service and rely on the cloud service provider to give data access to other users.However, the cloud service provider can no longer be fully trusted.Because it may give data access to some illegal users or attackers for profit gain.For users, it is necessary to take full advantage of cloud storage service,and also to ensure data privacy.Therefore,the study of access control scheme to protect users’ privacy in cloud environment is of great significance.Since traditional access control strategy [1] cannot effectively solve the security problems that exist in data sharing, various schemes to achieve encryption and decryption of data sharing have been proposed.In 2007, Bethencourt et al.[2] first proposed the ciphertext policy attribute-based encryption(CP-ABE).However, this scheme does not consider the revocation of access permissions.Attrapadung et al.[3, 4] came up with two user-revocable ABE scheme.However, they are not applicable in the outsourcing environment.In 2011, Hur et al.[5] put forward a finegrained revocation scheme, but it can easily cause key escrow issue.Lewko et al.[6] used multi-authority ABE (MA-ABE) to solve key escrow issue.But the access policy is not flexible.Later, Li et al.[7] presented a data sharing scheme based on systemic attribute encryption,which endows different access permissions to different users.However, it lacks of efficiency.Xie et al.[8] presented a revocable CPABE scheme.Compared with Hur’s scheme,in the key update phase, the computation load of the data service manager will be reduced by half.Liang et al.[9] proposed a CP-ABE proxy encryption scheme which supports any monotonic access structures.However, their construction which is built in the composite order bilinear group cannot be converted to the prime order bilinear group.In 2014, Chu et al.[10] proposed Key-Aggregate Encryption algorithm, which effectively shortens the length of the ciphertext and the key, but only for the situation where the data owner knows user’s identity.The above schemes only focus on one aspect of the research, and do not have a strict uniform standard either.In this paper,we present a more systematic, flexible and efficient access control scheme.To this end, we make the following main contributions:
1) We propose a novel access control system called PS-ACS, which is privilege separation based on privacy protection.To achieve read access permission, in PRD, the Key-Aggregate Encryption (KAE) scheme which greatly improves access efficiency is adopted.And in PUD, we construct a new multi-authority ciphertext policy attribute-based encryption(CP-ABE) scheme with efficient decryption to avoid the issues of single point of failure and complicated key distribution, and design an efficient attribute revocation method for it.
2) Compared with the MAH-ABE scheme which does not refer to the write access control, we exploit an Improved Attribute-based Signature (IABS) [11-13] scheme to enforce write access control in PRD.In this way, the user can pass the cloud server’s signature verification without disclosing the identity, and successfully modify the file.
3) We provide security and performance analysis of our proposed PS-ACS scheme.The functionality and simulation results provide data security in acceptable performance impact, and prove the feasibility of the scheme.
The remaining of this paper is organized as follows.We first provide some preliminaries in Section 2.In Section 3, we give the definition of the system model.Then, we present the access control scheme in PRD in Section 4 and the access control scheme in PUD in Section 5.Section 6 gives the security and the performance analysis of our scheme.Finally,the conclusion is given in Section 7.
In this paper, the authors proposed an access control system(PS-ACS), which is privilege separation based on privacy protection.
I.PRELIMINARIES
In this section, we briefly describe some fundamental backgrounds used in this paper,including bilinear maps, access structure and linear secret sharing schemes (LSSS).
2.1 Bilinear maps
Definition 1 (Bilinear Maps)Letbe three cyclic groups of prime orderp.A bilinear map is a mapwith the following properties:
2) Non-degeneracy: there existssuch that
3) Computability: there is an efficient algorithm to computefor anyand
2.2 Access structure
Definition 2 (Access Structure [14])Letbe a set of parties.A collectionis monotone ififandthenAn access structure(respectively, monotone access structure) is a collection (respectively, monotone collection)of non-empty subsets ofThe sets inare called the authorized sets, and the sets not inare called the unauthorized sets.
2.3 Linear secret sharing schemes
Definition 3 (Linear Secret-Sharing Schemes (LSSS) [14])Letbe a secret sharing scheme over a set of partieswith realizing an access structure.We say thatis a linear secret sharing scheme overif:
1) the piece of each party is a vector over
2) during the generation of the pieces, the dealer chooses independent random variables, denoted, each one distributed uniformly overEach coordinate of the piece of every party is a linear combination ofand the secrets.That is, letMdenotes a matrix withlrows andncolumns.For the vectorand any authorized set, there exist constantssuch that, ifare valid shares of any secretsaccording to, thenwhere

Table I Notations
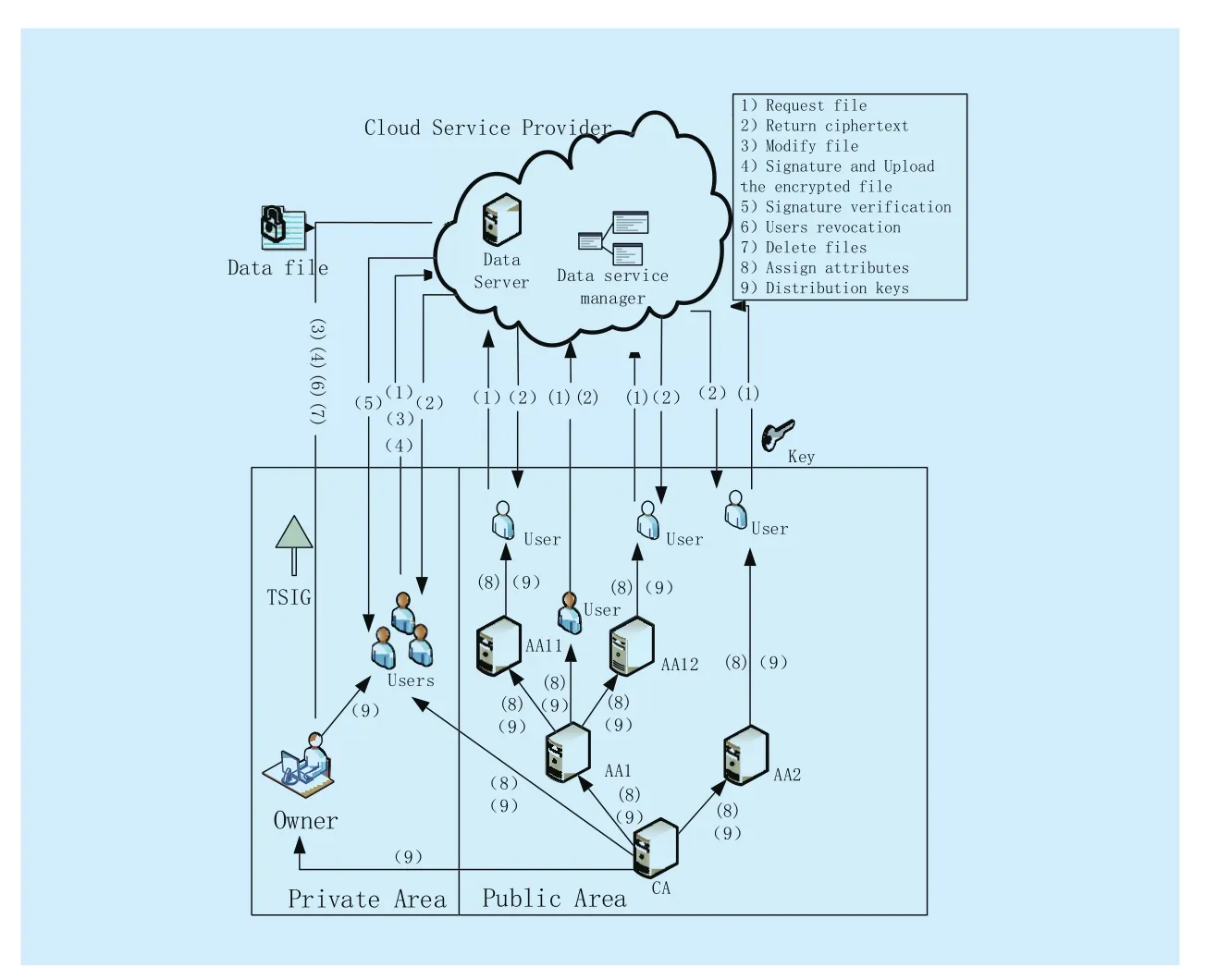
Fig.1 System framework
III.SYSTEM MODEL
As shown in Fig.1, our system model consists of Data owners, users in PRD, and users in PUD, a global certificate authority (CA), attribute authorities (AA) and the cloud service provider, which are defined as follows.
1) The cloud service provider consists of two parts: data storage server and data service management.Data storage server is responsible for storing confidential data files, and data service management is in charge of controlling external users’ access to secret data and returning the corresponding ciphertext.
2) In the actual cloud environment, CA manages multiple AAs, and each AA manages attributes in their own field.The attributes owned by the user are issued by different authorities.
3) Users in private domain (PRD) have special privileges, such as family, personal assistant, close friends and partners.This domain has a small number of users and small scale attributes, and the data owner knows users’identities, which is easy to manage.
4) In public domain (PUD), there exist a huge number of users with unknown identities and a lot of attributes owned by the user.
5) Data Owner can develop different access control strategies based on the characteristics of users in public and personal domain, encrypt uploaded files using the corresponding encryption method and then send them to the cloud server.
IV.ACCESS CONTROL SCHEME IN PRD
Before introducing our proposed secure authentication protocol, we first make a statement for the notations used in the later, all of which are listed in Table 1.
4.1 Read access control
The PRD has a small number of users, and their identities are known to the owner.In general,the data owner only wants the users to access or modify parts of data files, and different users can access and modify different parts of the data.For example, the blogger can allow his friend to browse part of his private photos;enterprises can also authorize employees to access or modify part of sensitive data.This requires the data owner to grant users read or write access permission to some data.In Chen’s[15] MAH-ABE scheme, the CP-ABE is used to achieve the read access permission, but there are some defects to be considered.Firstly, since in PRD, each user has a close relationship with the owner and the number is small, there is no need to use the CP-ABE which is applicable to the scenario which has a lot of users, and their identities are unknown to the owner, while the KAE scheme is set for the small users with certain identities.Besides, the distribution and management of keys and attributes, encryption and decryption process of CP-ABE are much more complex compared with the KAE scheme.Therefore, the KAE scheme is adopted to achieve the read access permission which improves the access efficiency.
Based on the above analysis, the paper uses the Key-Aggregate Encryption scheme to encrypt the data files to achieve different read access control.The specific application process of the KAE algorithm is as follows.
1) System setup and file encryption.The system first runsSetupof KAE to establish the public system parameter and master key.Each owner classified the file by its data attribute, such as “photo files”, “blog files” and “game files”.Fig.2 shows the way to classify the files.Choose and label the files, denoted bynote that a file class i cannot be the subset of another file classThen the owner’s client application runs Encrypt of KAE using the public key and the number of classification file to encrypt the PHR files and sends them to the cloud.
2) Access and key distribution.When the user sends access request to the cloud server,and his file index number is i , then the cloud server returns the corresponding encrypted classification file to the user.The owner authorized users access permission with the file index number denoted by j and sent the collection S of all the index number j to CA, CA generate an aggregate decryption key for a set of ciphertext classes via Extract of KAE and sent it to the corresponding user, Finally, any user with an aggregate key can decrypt any ciphertext whose class is contained in the aggregate key via Decrypt of KAE.
Setup().The Setup algorithm takes as input a security parameterand the number of ciphertext typesn.The CA first chooses a random numberand forit computesThen it publishesas the public parameters.Each type of ciphertext is expressed with an index numberi, where
KeyGen.The authority first randomly selects a numberand then outputs the public key asand keepsits master secret key.
EncryptOn input the public parameterPP, the public keyPK, the file index numberi, the data filemand a random numberthe data owner computes the ciphertext as and then sends the ciphertext to the cloud server.
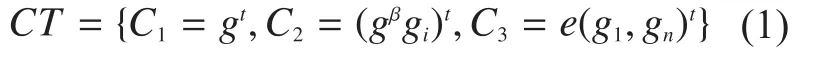
Extract().The Extract algorithm is executed by the authority.On input the mastersecret keyMSKand a collectionSof the file index number which are authorized the access permission by the data owner.It outputs the aggregate key as
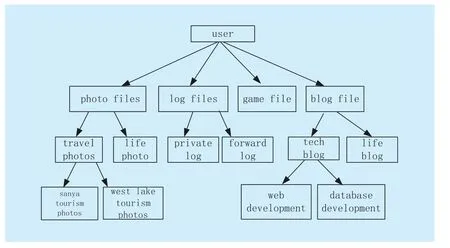
Fig.2 Data file classification
DecryptThe decryption algorithm takes as input the aggregate keythe setS, the file index numberiand the ciphertextCT.It recoversmas
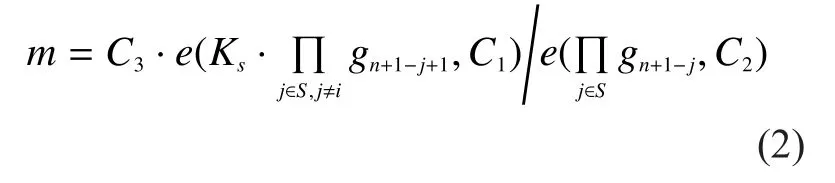
4.2 Write access control
As Chen’s MAH-ABE scheme does not refer to the write access control, and in PRD some cases exist, for example, the owner needs his friends to modify his file after he read it.So we proposed the write access permission in PRD.For the user, the public key and file class label are all known, he can use the algorithm to encrypt the files after he modified, and then upload them to the cloud.But whether the cloud server saves the modified file is decided by the write access control policy.On the one hand, in the complex cloud environment, if a user’s modification operations are very frequent, maybe he is very important to the user,so that the user may be stricken from outside attacks.Therefore, the user worries the leak of identity after the signature.On the other hand, in the data sharing scheme, the separate access of read and write to the file is extremely important.In PRD, not all users who have read permissions also have write permissions to the files.Whether the user has write permissions to the file is decided by the data owner.Therefore, this paper selects the improved attribute-based signature (IABS) to determine the user’s write permission.
The main structure of the scheme includes five parts: an authentication center (CA), the data owner, users, mediator and cloud servers.The CA is responsible for generating master key which is sent to the owner and system parameters which are shared for all users.The mediator holds part components of the signature keys and is responsible for the validity check of attributes and users.The data owner produces the signature tree and sends it directly to the cloud server.The user encrypts the modified files and signs them using the attribute-based signature, then uploads them to the cloud server.The cloud server verifies the attribute-based signature, if the authentication is successful, the user has permission to modify files and the cloud server stores the file.Own to the limited space we will omit the specific description of the IABS scheme in PRD.
V.ACCESS CONTROL SCHEME IN PUD
5.1 Overview
The PUD is characterized by a huge number of users, a lot of attributes owned by the user,complexity management, and indefinite users’identity.In view of the above characteristics,the user can only have the read access permission.Although the attribute-based encryption scheme (CP-ABE) can achieve access control,it cannot meet the needs of complex cloud environment.In traditional CP-ABE scheme, there is only one attribute authority responsible for the management of attributes and distribution of keys.The authority may be a university registrar’s office, the company’s HR department or government educational organizations and so on.The data owner defines access policies and encrypts the data files in accordance with this policy.Each user is distributed a key related to his attribute.As long as the user’s attributes meet the access policy he can decrypt the file.However, if there is only one authority in the system and all public and private keys are issued by the authority.Two problems will appear in the practical application:
1) In the practical cloud environment, there are a lot of authorities and each authority in their own field manages part of users’ attributes.The attributes owned by the user are issued from different authorities.For example,a data owner may want to share his medical data with a user who owns the doctor attribute issued by medical institutions and the medical researcher attribute by the clinic practice man-agement.Therefore, exploiting multi authority is more realistic in the practical scenarios.
2) If there is only one authority, all the distribution of the keys are handed over by one trusted authority.The frequent interaction between the user and trust authority will not only bring bottlenecks for the system load capacity,but also increase the potential security risks.Therefore, multi authority ABE (MA-ABE) is used in this paper.
To reduce the computation overhead of users in PUD, we propose an outsourcing decryption MA-ABE scheme.Firstly the data owner uploads the attribute-based encrypted data files to the cloud server.When a user requests the encrypted data from the cloud server, the cloud server will first check his transformation key.Only if the corresponding attributes satisfy the access structure, will the cloud server output a partially decrypted ciphertext and then sends it to the user.Finally,upon receiving the partially decrypted ciphertext, the user can use his private key to recover the message.The framework of this area is shown in Fig.3.
5.2 Our construction
Global SetupThe Global Setup algorithm takes as inputs a security parameterand a universe descriptionU.Letandbe the multiplicative groups with the same prime orderp, andbe the bilinear map.Letbe the generator ofandbe the generator ofLetbe a hash function such that the security will be modeled in the random oracle.The CA chooses a random numberand publishes the public parameters as
Authority Setup(PP).EachAAfirst chooses two random exponentsthen publishes its public key asand keepsas its master secret key.Letdenote the set of all attributes managed byAA.For each attributechooses anIDnumberand then generates the public attribute keys as
EncryptThe encryption algorithm takes as inputs the public parametersPP, the public keyPK, the relevant public attribute keysthe messagemand an LSSS access structureover all the selected attributes from the involved authorities.The encrypt algorithm first chooses a random encryption exponentand a random vectorwithsas its first entry, whereare used to share the encryption exponents.For, it computeswhereis the vector corresponding to thei-th row ofM.Then it randomly choosesand computes the ciphertext as
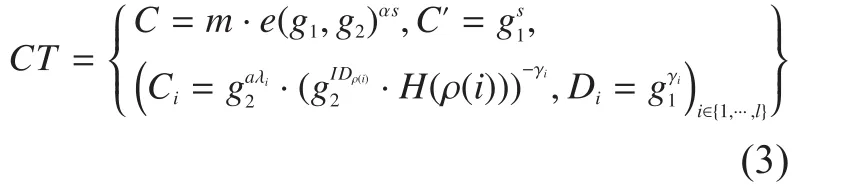
KeyGenEach authority runs the key generation algorithm.On input the public parameterPP, the relevant public attribute keysthe master secret keyMSKand a set of attributes managed by the authorityS, it outputs the transformation keys as
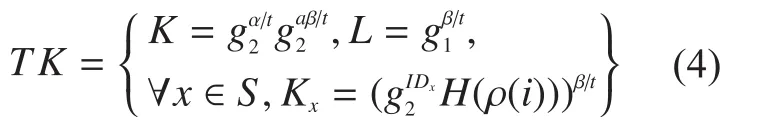
Transform.The transformation algorithm takes as input the transformation keyTKand a ciphertextCT.IfSdoes not satisfy the access structure, it outputs.Oth-erwise it chooses a set of constantssuch that ifare valid shares of the secretsaccording toM, thenwhereThen the cloud server computes
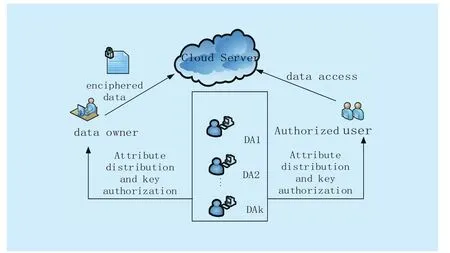
Fig.3 Access control framework of PUD

and sends the partially decrypted ciphertextto the corresponding user.
本次比赛得到了各参赛馆的高度重视,中共上海市委党校图书馆馆长唐月娥和副馆长李敏、上海财经大学图书馆书记戴洪霞、上海对外经贸大学图书馆馆长王群、上海中医药大学图书馆党总支书记兼副馆长石德响、复旦大学图书馆副书记史卫华、同济大学图书馆副书记危红、华东师范大学图书馆副馆长周健、华东政法大学图书馆副馆长吴志鸿、上海师范大学图书馆副馆长庄雷、上海工程技术大学图书馆副馆长盛芳和王镇、上海健康医学院图书馆副馆长柳丽花、奉贤区图书馆副馆长浦飒、松江区图书馆副馆长奚建治等出席并担任各奖项颁奖嘉宾。
DecryptThe decryption algorithm takes as input the partially decrypted ciphertextand a user private keySK.It computes
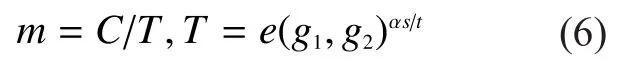
Notice that since the ciphertext is already partially decrypted by the cloud server, the user only needs one exponentiation operation to recover the message.
RekeyUpdateThe involved authority first generates a newIDnumberIt then computes the public attribute update key asAfter that, it appliesto compute the transformation update key asfor each non-revokeduser who has the attributeand the ciphertext update key asThen the authority updates the public attribute key of the revoked attribute asand broadcast a message for all data owners such that they can get the updated public attribute key of the revoked attribute.Thenandare sent to the cloud server to updateTKandCT.
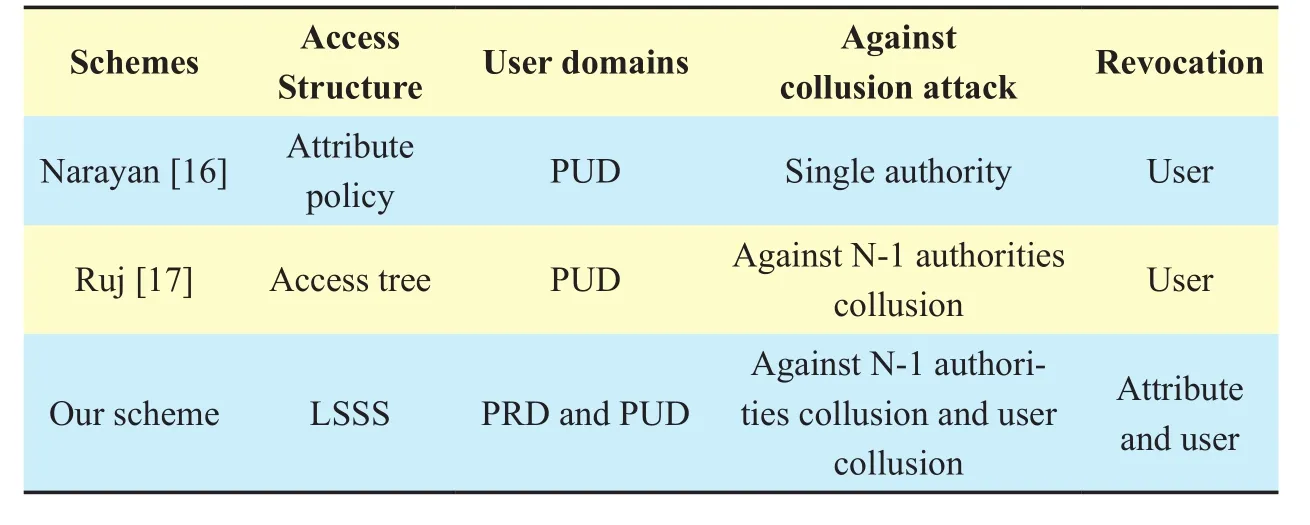
Table II Comparison of security
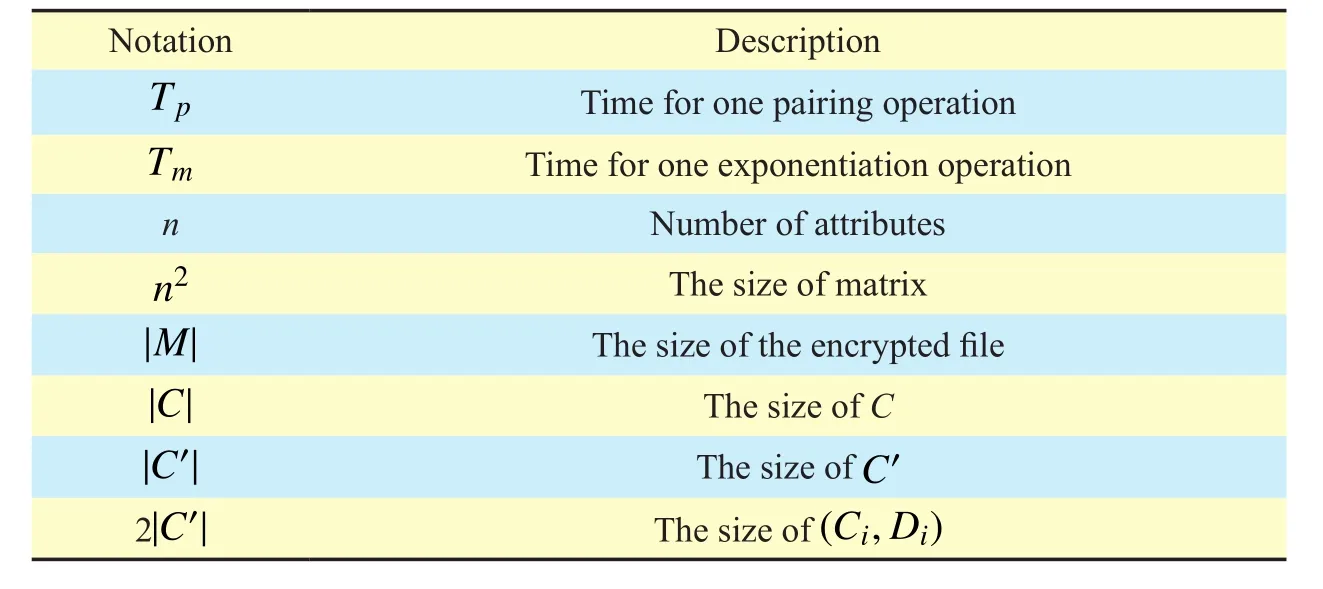
Table III Notations for performance analysis
TKUpdate.Upon receiving the transformation update keythe cloud server runs the transformation key update algorithm to update the corresponding transformation keys asfor each non-revoked user who has the attribute
Thus the transformation keyTKcan be updated as
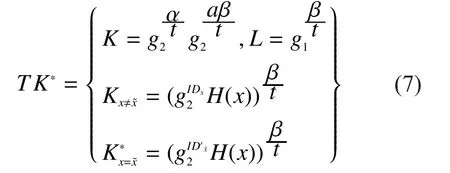
ReEnc.Upon receiving the ciphertext update keythe cloud server runs the ciphertext re-encryption algorithm to update the corresponding ciphertext as
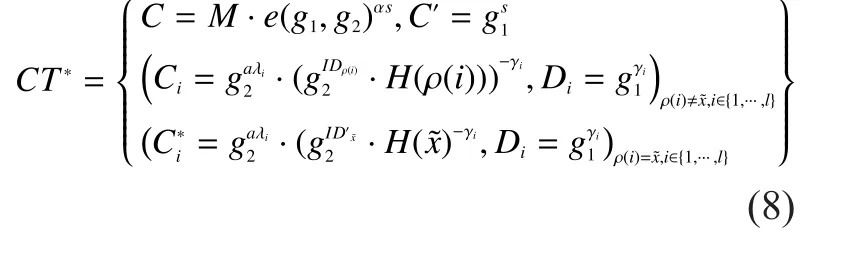
VI.ANALYSIS OF OUR SCHEME
In this section, we present the security analysis and performance analysis of our access control system (PS-ACS).
6.1 Security analysis
In PRD, users can only decrypt the files corresponding to the received aggregate keys and do not have access to other files, thus the data owner controls the users’ access permissions.When the data file is modified, although CA is trusted, the system parameters and revocation instructions are generated by the CA.The signature policy is formulated by the data owner and is sent directly to the cloud server.The CA does not know the signature policy.Assuming that CA cannot give itself authorization, as long as the attributes of CA cannot satisfy the access policy, it is not valid to modify the file.Thus, the write access permissions still belong to the data owner.In the process of the users’signature, the signature key is only related to the users’ attributes, so the user’s identity is secure.On the whole, the IABS scheme can protect users’ identity privacy.
In addition, our scheme also achieves forward and backward security.When a user is revoked, his transformation keys will be deleted by the cloud server.Thus, he can no longer receive the partially decrypted ciphertext and cannot recover the original message.On the other hand, when a new user joins to share the outsourced data, the ciphertext will be re-encrypt by the cloud server so that he can also decrypt the cipthertext.Therefore, the forward and backward security of the outsourced data can be guaranteed.
We compare our scheme with several existing multi-authority CP-ABE schemes in Table 2 in terms of the access structure type, user domains, the security against collusion attack and the support of revocation.
From Table 2, we can conclude that our scheme achieves high efficiency of privacy protection.Compared with other schemes, we adopt outsourcing decryption method to reduce the overhead in user decryption phase.In our system, the transformation keys are stored on the cloud server, the collusion among users and between users and authorities both need to be considered.In our scheme, eachTKcontains a unique parameterzwhich is bind with the user.As eachzis different and it is kept secret to other users, different users cannot share theirTKsto make collusion attack.Thus, our scheme can prevent users’ collusion attack.On the other hand, although the cloud server transforms the ciphertext into an El-Gamal-style ciphertext, as the ciphertext is associated withzwhich he does not know, he still learns nothing about the original message.Therefore, our scheme can prevent the server attack.On the whole, our scheme can achieve privacy protection in PUD.
6.2 Performance analysis
We first make a statement for the notations used in the performance analysis, which are listed in Table 3.
In our KAE scheme in the PRD, the system parameters are generated by the trusted authority, which is not within our consideration.Moreover,can be calculated in the system setup phase.In addition, the aggregate key only needs one pairing operation, and to calculate a pairing operation is very fast, the specific comparison can be seen in Fig.4.
In Fig.4, the attribute-based encryption algorithm of the MAH-ABE scheme spent much more time than the KAE algorithm used in our scheme.If the attribute revocation occurs,the ABE algorithm will be more time-consuming.More importantly, the growth rate of time spent with the number of file attributes is much higher than KAE algorithm.The simu-lation results show the high efficiency of our scheme.
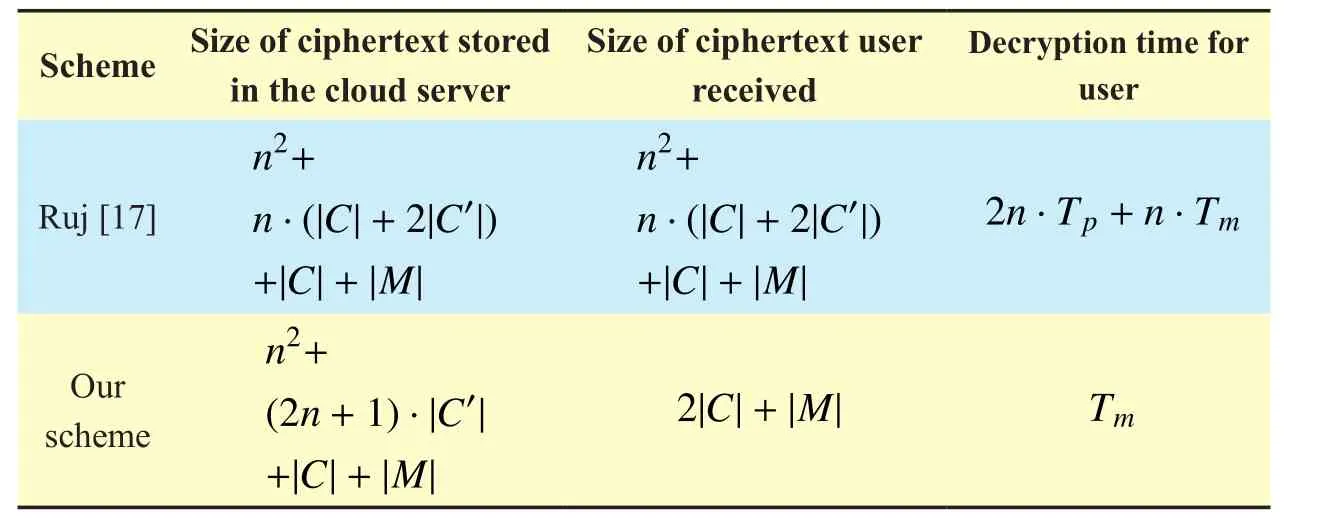
Table IV Comparison of communication cost and computing time
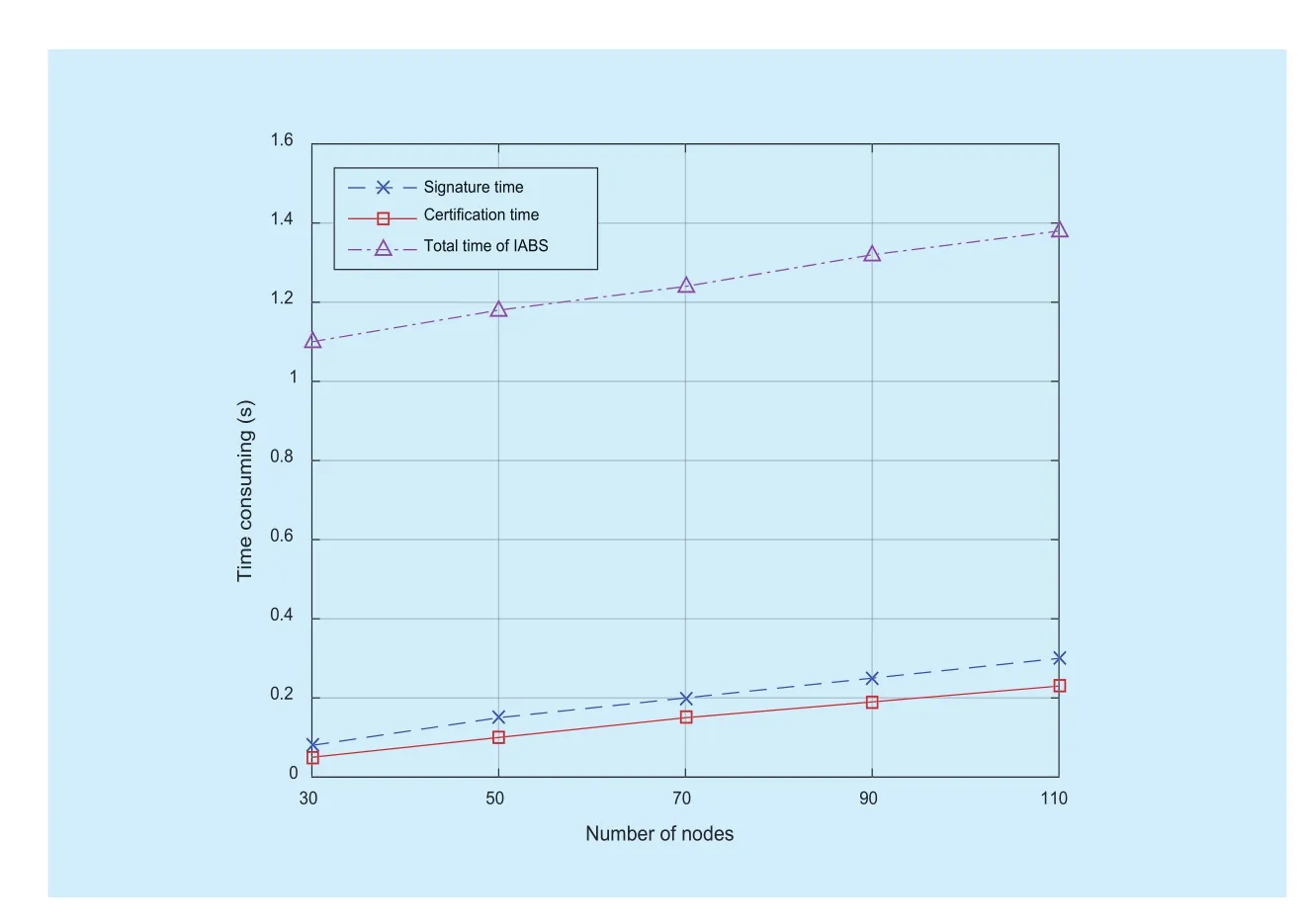
Fig.5 The signature and authenticationtime of IABS
In Fig.5, the user only needs a very short time to sign the modified files.While, the authentication time only makes up a small part,so the process of signature and authentication consume a very small time.Therefore, from the client’s perspective, the program is efficient.
In PUD, we adopt outsourcing decryption method.We compare our scheme with Ruj’s scheme, and the results are shown in Table 4.Combined with Table 4, the performance analysis is given in the following aspects.
• Since the cloud server uses a set of transformation keys to transform the ABE ciphertext into a constant-size ElGamal-style ciphertext which is much smaller and easier to decrypt than an ABE ciphertext, the user only needs one exponential operation to recover the message.From Table 4, it is obvious that the method can greatly reduce the overhead of users.
• Our scheme supports efficient user and attribute revocation without updating users’ private keys.For user revocation, we do not need to re-encrypt the ciphertext and update all non-revoked users’ private keys.Instead, we only need to delete the user’s transformation keys.Without the transformation key, he can no longer decrypt the ciphertext.On the other hand, when attribute revocation occurs, private keys of all non-revoked users will not be updated, only the transformation keys which are stored in the cloud server and the involved ciphertext need to be updated.Thus, the effi-ciency of revocation can be greatly improved.
We implemented our construction in Charm[18], a framework developed to facilitate the rapid prototyping of cryptographic schemes and protocols.It is based on the Python language which allows the programmer to write code similar to the theoretical implementations.However, the routines that implement the dominant group operations use the PBC library [19](written natively in C) and the time overhead imposed by the use of Python is usually less than 1%.Charm also provides routines for applying and using LSSS schemes needed for Attribute-Based systems.For more information on Charm we refer the reader to [18, 20].All our implementations are executed on an Intel®Pentium® CPU G630@270GHz with 4.00GB RAM running Ubuntu14.04 and Python2.7.
We compared the computing time incurred in encryption and decryption.In Fig.6, the number of authorities is set to 10.It is obvious that our scheme requires less time for encryption and decryption than Ruj’s scheme, especially for decryption.Since in the decryption phase,major computation overhead is delegated to the cloud, user only needs one exponentiation operation to recover the original message.
Therefore, the decryption time for users can be greatly reduced.Computing cost for transformation is shown in Fig.7.On the whole, it can be concluded that our scheme’s computation efficiency is much better than Ruj’s scheme.
VII.CONCLUSION
In this paper, we proposed an access control system (PS-ACS), which is privilege separation based on privacy protection.Through the analysis of cloud environment and the characteristics of the user, we divide users into personal domain (PRD) and public domain(PUD) logically.In PRD, we set read and write access permissions for users respectively.To achieve read access permission, the KAE scheme which can improve the access efficiency is adopted.A high degree of patient privacy is guaranteed simultaneously by using IABS scheme which can determine users’write access permission.For users in PUD, we constructed a new multi-authority ciphertext policy attribute-based encryption (CP-ABE)scheme with efficient decryption to avoid the issues of single point of failure and complicated key distribution, and design an efficient attribute revocation method for it.The analysis and the simulation result show that the PSACS scheme is feasible and superior to protect the privacy of data in cloud-based services.
ACKNOWLEDGEMENT
This work has been financially supported by the National Natural Science Foundation of China (No.61303216, No.61272457, No.U1401251, and No.61373172), the National High Technology Research and Development Program of China (863 Program) (No.2012AA013102), and National 111 Program of China B16037 and B08038.

Fig.6 Comparison of Encryption and Decryption Time

Fig.7 Computing cost for transformation
Reference
[1] YU SH, WANG C, REN K, “Achieving Secure,Scalable, and Fine-Grained Data Access Control in Cloud Computing”,Proceedings of IEEE Con-ference on Information Communications 2010,pp.1-9, 2010.
[2] BETHENCOURT J, SAHAI A, WATERS B, “Ciphertext-Policy Attribute-based Encryption”,IEEE Symposium on Security and Privacy, vol.2008,no.4, pp.321-334, 2007.
[3] ATTRAPADUNG N, IMAI H, “Conjunctive Broadcast and Attribute-Based Encryption”,Proceedings of Pairing-based Cryptography - Pairing 2009, vol.5671, pp.248-265, 2009.
[4] ATTRAPADUNG N, IMAI H, “Attribute-Based Encryption Supporting Direct/Indirect Revocation Modes”,Proceedings of Cryptography and Coding 2009, pp.278-300, 2009.
[5] HUR J, NOH D K, “Attribute-based Access Control with Efficient Revocation in Data Outsourcing Systems”,IEEE Transactions on Parallel and Distributed Systems, vol.22, no.7, pp.1214-1221, 2011.
[6] LEWKO A, WATERS B, “Decentralizing Attribute-based Encryption”,Proceedings of Advances in Cryptology-EUROCRYPT 2011 - 30th Annual International Conference on the Theory and Applications of Cryptographic Techniques,pp.568-588, 2011.
[7] LI M, YU SH, ZHENG Y, “Scalable and Secure Sharing of Personal Health Records in Cloud Computing Using Attribute-based Encryption”,IEEE Transactions on Parallel and Distributed System, vol.24, no.1, pp.131-143, 2013.
[8] XIE X, MA H, LI J, et al, “New Ciphertext-Policy Attribute-based Access Control with Efficient Revocation”,Proceedings ofInformation and Communication Technology 2013, pp.373-382,2013.
[9] LIANG K, MAN H A, SUSILO W, et al, “An Adaptively CCA-Secure Ciphertext-Policy Attribute-Based Proxy Re-Encryption for Cloud Data Sharing”,Information Security Practice and Experience, pp.448-461, 2014.
[10] CHU C K, CHOW S S M, TZENG W G, “Key-Aggregate Cryptosystem for Scalable Data Sharing in Cloud Storage”,IEEE Transactions on Parallel and Distributed Systems, vol.25, no.2, pp.468-477, 2014.
[11] LI J, KIM K, “Hidden Attribute-based Signatures without Anonymity Revocation”,Information Sciences, vol.180, no.9, pp.1681-1689, 2010.
[12] MAJI H K, PRABHAKARAN M, ROSULEK M, “Attribute-based Signatures”,Proceedings of RSA Conference 2011, pp.376-392, 2011.
[13] KUMAR S, AGRAWAL S, BALARAMAN S, et al, “Attribute based Signatures for Bounded Multi-level Threshold Circuits”,Proceedings of Public Key Infrastructures, Services and Applications-European Workshop, Europki 2010, pp.141-154, 2010.
[14] BEIMEL A, “Secure Schemes for Secret Sharing and Key Distribution”,International Journal ofPure & Applied Mathematics, Research Thesis,1996.
[15] CHEN D, SHAO J, FAN X, “MAH-ABE based Privacy Access Control in Cloud Computing”,Chinese Journal of Electronics, vol.42, no.4, pp.821-827, 2014.
[16] NARAYAN S, GAGNÉ M, SAFAVI-NAINI R,“Privacy Preserving EHR System Using Attribute-based Infrastructure”,Proceedings of ACM Cloud Computing Security Workshop 2010, pp.47-52, 2010.
[17] RUJ S, NAYAK A, STOJMENOVIC I, “DACC: Distributed Access Control in Clouds”,Proceedings of Trust, Security and Privacy in Computing and Communications 2011, pp.91-98, 2011.
[18] AKINYELE J A, GREEN M, RUBIN A D, “Charm: A Framework for Rapidly Prototyping Cryptosystems”,Journal of Cryptographic Engineering, vol.3, no.2, pp.111-128, 2011.
[19] LYNN B, “The Stanford Pairing based Crypto Library”, http://crypto.stanford.edu/pbc.
[20] Charm, http://www.charm-crypto.com.
猜你喜欢
杂志排行
China Communications的其它文章
- Offline Urdu Nastaleeq Optical Character Recognition Based on Stacked Denoising Autoencoder
- Toward a Scalable SDN Control Mechanism via Switch Migration
- Reputation-Based Cooperative Spectrum Sensing Algorithm for Mobile Cognitive Radio Networks
- Identifying the Unknown Tags in a Large RFID System
- Dynamic Weapon Target Assignment Based on Intuitionistic Fuzzy Entropy of Discrete Particle Swarm
- A Non-Cooperative Differential Game-Based Security Model in Fog Computing
