一种基于云模型的网络态势综合评估方法*
2017-01-03夏靖波张晓燕董淑福
付 凯,夏靖波,张晓燕,董淑福
(1.空军工程大学 信息与导航学院,西安 710077;2.厦门大学 嘉庚学院,福建 漳州 363105)
一种基于云模型的网络态势综合评估方法*
付 凯**1,夏靖波2,张晓燕1,董淑福1
(1.空军工程大学 信息与导航学院,西安 710077;2.厦门大学 嘉庚学院,福建 漳州 363105)
针对网络态势评估中存在的模糊性、随机性和指标量化不统一等问题,提出了一种基于云模型的网络态势综合评估方法。综合考虑实数型、区间型和模糊型指标并统一用云模型量化表示,采用主观与客观相结合的赋权方式,并利用云相似性理论进行网络态势综合评估。对通信网络态势评估的实例分析表明,该方法能够合理地实现网络态势的定性及定量评估,并且保留了评估过程中的不确定性。
通信网;网络态势评估;云模型;云相似性理论
1 引 言
随着信息栅格[1]、云计算、虚拟化[2]等信息技术的发展,通信网络已成为一个多网系交织、多业务承载的复杂系统,呈现出固定与移动网系相互融合、有线与无线手段综合运用等特点,这给通信网络管理与评估带来巨大挑战。网络态势感知是网络管理的发展方向,是指对网络中各类设备运行状况、各类网络及用户行为所构成的整个网络的当前状态进行分析评估并预测其发展趋势[3-4]。网络态势评估是网络态势感知的核心环节,借助数学工具对当前网络状态进行合理评价。目前,网络态势评估的研究大多面向单一类型网络(如Internet)并集中于网络安全态势领域,评估方法主要包括基于数学模型[5]、基于知识推理[6]和基于模式识别[7]等3类。基于数学模型的方法通过权重分析、集对分析等建立明确的数学表达式,模型易于理解,但参数选择易受主观因素影响。基于知识推理的方法是在先验知识的基础上,采用D-S证据理论、贝叶斯网络、模糊推理等智能理论进行推理得到对当前态势的评价,但推理规则维护及开销是需要考虑的问题。基于模式识别的方法在对态势空间进行划分的基础上,利用粗集、神经网络、灰关联分析等理论进行模式匹配,引入机器学习机制使得评估结果更加准确,但也带来计算量大等问题。随着通信网络建设规模和业务范围的不断扩大,其复杂性和不确定性也随之增加。在面向多网系多指标复杂系统的网络态势综合评估中,由于测量环境及工具各异、专家知识及经验不同等原因,存在指标测量结果随机性大、专家主观判断模糊性大等问题,并且不同类型指标的量化标准也不同。云模型[8]作为一种定性定量转换模型,将概念的模糊性和随机性有机结合起来,在系统评估[9]、智能预测等方面具有广泛的应用。文献[10-11]提出了基于云模型的网络安全态势评估方法,有效处理了态势评估中的不确定性问题,使评估结果更加合理。
基于此,本文提出一种基于云模型的网络态势综合评估方法,综合考虑多种类型指标并统一用云模型量化表示,采用主客观相结合的赋权方法,并基于云相似性理论实现网络态势的定性及定量评估,最后通过实例分析证明了该方法的合理性。
2 云模型基础理论
2.1 云的定义及数字特征[12]
设U是一个用精确数值表示的定量论域,C是U上的一个定性概念,若定量值x∈U,且x是定性概念C的一次随机实现,x对C的确定度μ(x)∈[0,1]是具有稳定倾向的随机数,则x在论域U上的分布称为云,每一个x称为一个云滴。
云模型用期望Ex、熵En和超熵He等3个数字特征来表征一个定性概念C的整体定量特性。其中,期望Ex是定性概念基本确定性的度量,反映了论域空间中最能代表定性概念的点;熵En是定性概念的不确定性度量,体现定性概念的随机性和模糊性之间的关联;超熵He是熵的不确定度量,反映了在论域空间中代表该定性概念所有点的不确定度的凝聚性。
2.2 云的期望曲线及“3En”规则
由于正态分布的普适性,正态云是云模型中应用最广泛的一种。对于云滴变量x,若满足x~N(Ex,En′),其中En′~N(En,He),En≠0,则把曲线
y(x)=exp[-(x-Ex)2/2En2]
(1)称为正态云的期望曲线,能够直观地描绘出云的基本几何形态(如图1所示)。在云模型中,不同云滴群对概念的贡献是不同的。对概念有贡献的云滴主要落在区间[Ex-3En,Ex+3En]中,称为“3En”规则。
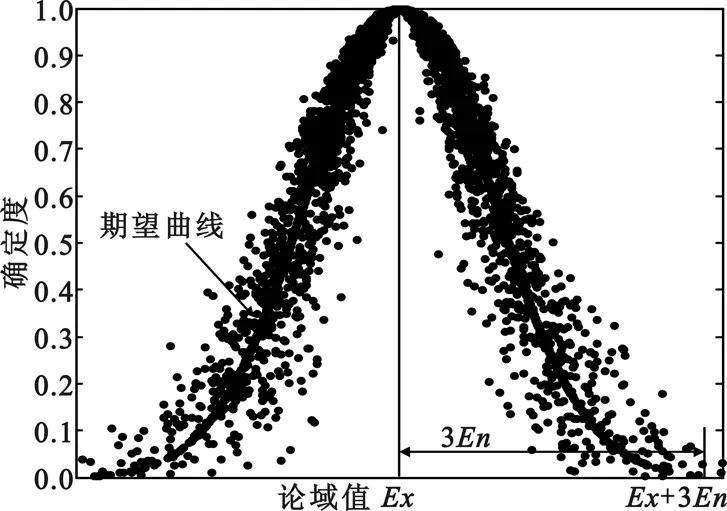
图1 云模型示意图
Fig.1 Sketch map of cloud model
2.3 云相似性理论
相似性度量是一个常见的数学问题,广泛应用于数据挖掘、图像处理等领域。云模型之间的相似性度量主要应用于基于云模型的评估决策中,通过寻找待评对象云与评价等级云的最大相似度实现定性评价,其度量方法主要分为基于云滴距离、基于数字特征和基于相交面积等3类。文献[13]首次提出了相似云理论,并基于云滴距离计算云模型之间的相似度,但大量云滴计算带来时间复杂度高、结果不稳定等问题。文献[14]利用云模型的数字特征计算云模型之间的相似性,但忽略了云模型的不确定性,并且存在数字特征向量的部分分量过度占优问题。文献[15-16]基于云期望曲线的相交面积衡量云模型之间的相似性,计算复杂度较低且结果稳定。
3 网络态势综合评估方法
3.1 基本原理
本文提出的基于云模型的网络态势综合评估方法,综合考虑实数型、区间型和模糊型等多种态势指标进行归一化及云化处理,采用主观与客观相结合的赋权方法,利用云模型的计算规则生成待评对象云并建立评价等级云,最后采用基于隶属度的云相似性度量方法进行网络态势的定性评估,并基于云模型相似度实现由定性评估到定量评估值的转换。网络态势评估流程如图2所示。
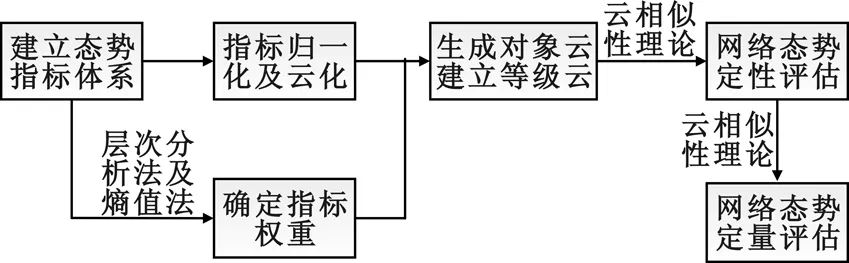
图2 基于云模型的网络态势评估流程
Fig.2 Process of network situation assessment based on cloud model
3.2 实施步骤
(1)网络态势指标归一化处理

对于效益型指标,做归一化处理如下:
(2)
对于成本型指标,做归一化处理如下:
(3)

对于模糊型指标,将其归一化与后面的云化处理同步完成。
(2)指标云化处理
指标云化主要是将各类型指标转换为云模型Ci(Ex,En,He)表示,以应用于后续基于云模型的评估中。

对于模糊型指标,采用“优、良、中、差、特差”5个等级的模糊评价值,其对应的云模型如表1所示。其中,“极差”属于半降云,“优”属于半升云,其他等级对应完整的云[16]。
表1 模糊评价值及对应云模型
Tab.1 Fuzzy assessment value and corresponding cloud model

模糊评价值云模型极差C(0.00,0.05,0.02)差C(0.30,0.07,0.02)中C(0.50,0.08,0.02)良C(0.70,0.07,0.02)优C(1.00,0.05,0.02)
(3)确定指标权重
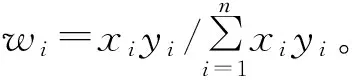
(4)生成待评对象云
对各指标云进行一维线性加权,得到待评对象云
式中:wi可以表示为C(wi,0,0)。按照云模型之间的运算规则,对于两个云C1(Ex1,En1,He1)和C2(Ex2,En2,He2),则有
(4)
(5)
(5)建立评价等级云
最终的网络态势分为“优、良、中、差、特差”5个等级,各等级对应的云模型仍采用表1中的表示方式。
(6)网络态势定性评估
网络态势定性评估主要依据待评对象云和评价等级云的相似度,找出与待评对象云相似度最大的等级云作为定性评价结果。文献[15]提出了一种新的一维正态云概念隶属度判定算法,综合考虑云模型公共面积和云滴所占比例两方面因素,并利用向量进行合成得到最终的隶属度,但此方法存在云滴计算复杂度高、向量部分分量过度占优等问题。该文献指出,云模型之间的隶属度不仅取决于其相交面积,而且取决于对象云落入概念云的云滴数量。考虑将这两方面均有所体现又要避免上述问题,本文以相交面积与自身面积之比定义云模型之间的隶属度,进而以相互隶属度衡量云模型之间的相似度。其基本思想是如果云C1对云C2的隶属度较高,且云C2对云C1的隶属度也较高,则云C1和C2的相似度较高。定义云C1对云C2的隶属度为
B(C1,C2)=Sc/S1。
(6)
式中:S1为云C1的面积;S2为云C2的面积;Sc为云C1和云C2的相交面积。对于采用云期望曲线计算各云模型自身面积及相交面积的方法见文献[15],此处不再赘述。同理,云C2对云C1的隶属度为B(C2,C1)=Sc/S2。进而定义云模型之间的相似度为
D(C1,C2)=(B(C1,C2)+B(C2,C1))/2。
(7)
本文将云模型之间的相似度定义为两个云模型相互隶属度的均值,如果两个云的相互隶属度较高,则它们的相似度也较高,并且当相互隶属度都为1时两个云的相似度为1。此方法本质上属于基于相交面积的云相似度量方法,同样具有计算复杂度低、结果稳定等优点。
按照式(7)计算待评对象云与各评价等级云的相似度Di(i=1,2,…,5),取maxDi所对应的等级云代表的评语为网络态势定性评估结果。
(7)网络态势定量评估
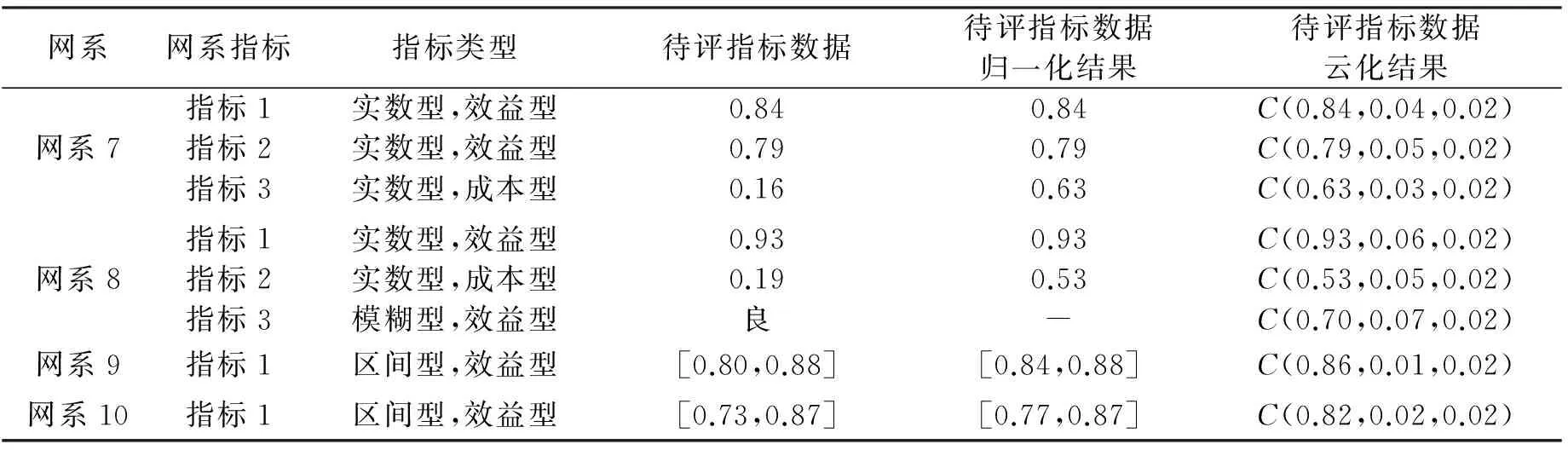
定性评估能够直观地反映网络态势的总体情况,而定量评估主要用于获得精确的网络态势值,便于对比分析。考虑态势评估中的不确定性问题,本文基于云模型相似度提出一种由定性评估到定量评估值的转换方式,以实现网络态势的定量评估。在定性评估中找出与待评对象云相似度最大与次大的两个等级云C1和C2(暂不考虑存在相似度相同的情况,并假设Ex1 T=(T1+T2)/2。 (8) 上述转换方式主要依据云模型之间的相似度并结合“3En”规则进行计算,即待评对象云与某评价等级云的相似度越高,则定量评价值与该等级云的期望Ex越接近。与直接采用待评对象云的期望Ex作为定量评估值相比,本文方法保留了态势评估中的不确定性,而且采用与待评对象云最相似的两个等级云计算均值的方式可以减小误差。 表2 通信网络指标类型及数据 Tab.2 Index type and data of a communication network 网系网系指标指标类型待评指标数据待评指标数据归一化结果待评指标数据云化结果网系1指标1实数型,效益型0.820.82C(0.82,0.07,0.02)指标2区间型,效益型[0.61,0.89][0.64,0.89]C(0.76,0.04,0.02)指标3模糊型,效益型优-C(1.00,0.05,0.02)网系2指标1实数型,效益型0.750.75C(0.75,0.05,0.02)指标2实数型,效益型0.920.92C(0.92,0.06,0.02)指标3模糊型,效益型良-C(0.70,0.07,0.02)网系3指标1区间型,效益型[0.68,0.95][0.71,0.95]C(0.83,0.06,0.02)网系4指标1区间型,效益型[0.59,0.83][0.62,0.83]C(0.72,0.03,0.02)网系5指标1实数型,效益型0.730.73C(0.73,0.03,0.02)指标2实数型,效益型0.950.95C(0.95,0.04,0.02)指标3实数型,效益型0.920.92C(0.92,0.04,0.02)指标4实数型,效益型0.820.82C(0.82,0.05,0.02)指标5模糊型,效益型优-C(1.00,0.05,0.02)网系6指标1实数型,效益型0.740.74C(0.74,0.05,0.02)指标2实数型,效益型0.890.89C(0.89,0.06,0.02)指标3实数型,效益型0.940.94C(0.94,0.04,0.02)指标4实数型,效益型0.590.59C(0.59,0.07,0.02)指标5实数型,效益型0.680.68C(0.68,0.03,0.02)指标6模糊型,效益型良-C(0.70,0.07,0.02) 续表2 利用层次分析法得到表2中各指标的主观权重为xi=(0.385 0,0.190 6,0.021 4,0.080 8,0.040 1,0.007 8,0.047 0,0.029 9,0.017 3,0.011 5,0.011 5,0.011 5,0.003 6,0.014 9,0.014 9,0.014 9,0.011 3,0.011 3,0.005 2,0.007 1,0.005 4,0.005 4,0.011 6,0.009 2,0.002 1,0.012 0,0.016 3)。利用熵值法得到指标客观权重为yi=(0.054 3,0.031 0,0.038 8,0.038 8,0.046 5,0.054 3,0.046 5,0.023 3,0.023 3,0.031 0,0.031 0,0.038 8,0.038 8,0.038 8,0.046 5,0.031 0,0.054 3,0.023 3,0.054 3,0.031 0,0.038 8,0.023 3,0.046 5,0.038 8,0.054 3,0.007 8,0.015 5)。通过乘法集成得到指标最终权重为wi=(0.492 2,0.139 2,0.019 5,0.073 8,0.044 0,0.010 0,0.051 5,0.016 4,0.009 5,0.008 4,0.008 4,0.010 5,0.003 3,0.013 6,0.016 4,0.010 9,0.014 4,0.006 2,0.006 7,0.005 2,0.004 9,0.002 9,0.012 7,0.008 4,0.002 7,0.002 2,0.006 0)。 计算待评对象云为Cz(0.808 2,0.035 4,0.010 5),利用正向云发生器[12]生成待评对象云和各评价等级云,从而得到网络态势图,如图3所示。 图3 基于云模型的网络态势图 Fig.3 Network situation chart based on cloud model 计算待评对象云与各评价等级云的相似度,并与数字特征法[14]、期望曲线法[15]作对比,如表3所示。其中,期望曲线法是指利用式(1)计算待评对象云的期望值(本文中Ex=0.808 2)对各评价等级云的隶属度。 表3 待评对象云与评价等级云的相似度 Tab.3 Similarity between target cloud and ranking cloud 方法相似度极差差中良优数字特征法0.050.980.990.991.00期望曲线法0.000.000.000.290.00本文方法0.000.000.010.340.05 由表3可知,数字特征法计算的各相似度区分度不大,与实际不符;期望曲线法和本文方法取最大相似度后得到的定性评估结果均为良。由态势图可以看出评估结果比较合理,且本文方法判定对象云与“优”、“中”代表的等级云也有较小的相似度,体现了态势评估中的不确定性。 根据表3得到D1=0.34和D2=0.05,计算可得T1=0.838 6,T2=0.857 5,则网络态势定量评价值为T=(T1+T2)/2=0.848。 本文针对网络态势评估中存在模糊性、随机性和指标量化不统一等问题,提出了一种基于云模型的网络态势综合评估方法,在各类指标云化的基础上利用云相似性理论进行网络态势评估。实例分析表明,该方法能够综合考虑多种类型指标,合理地实现网络态势的定性及定量评估,并且保留评估过程中的不确定性。本文在云模型生成方法上进行了简化处理,对于不同指标的量化标准还需要做进一步的研究。 [1] HUNG B,DEFRANCESCO D,CHENG B N,et al. An evaluation of IP header compression on the GIG joint IP modem system[C]//Proceedings of 2014 IEEE Military Communications Conference.Baltimore,USA:IEEE,2014:1484-1490. [2] 贾伟,夏靖波.一种生存性军事虚拟网络映射新方法[J]. 电讯技术,2015,55(5):545-551. JIA Wei,XIA Jingbo. A new approach for survivable military virtual network mapping[J]. Telecommunication Engineering,2015,55(5):545-551.(in Chinese) [3] BASS T. Intrusion systems and multisensor data fusion[J]. Communications of the ACM,2000,43(4):99-105. [4] 柏骏,夏靖波,钟贇,等. 网络运行态势感知技术及其模型[J]. 解放军理工大学学报(自然科学版),2015,16(1):16-22. BAI Jun,XIA Jingbo,ZHONG Yun,et al. Network running situation awareness technology and its model[J]. Journal of PLA University of Science and Technology(Natural Science Edition),2015,16(1):16-22. (in Chinese) [5] 吴琨,白中英. 集对分析的可信网络安全态势评估与预测[J].哈尔滨工业大学学报,2012,44(3):112-118. WU Kun,BAI Zhongying. Trusted network security situational awareness and forecast based on SPA[J]. Journal of Harbin Institute of Technology,2012,44(3):112-118.(in Chinese) [6] ZHAO J H,ZHOU Y,SHUO L X. A situation awareness model of system survivability based on variable Fuzzy set[J]. Telkomnika,2012,10(8):2239-2246. [7] 谢丽霞,王亚超,于巾博. 基于神经网络的网络安全态势感知[J].清华大学学报(自然科学版),2013,53(12):1750-1760. XIE Lixia,WANG Yachao,YU Jinbo. Network security situation awareness based on neural networks[J]. Journal of Tsinghua University(Science and Technology),2013,53(12):1750-1760.(in Chinese) [8] 李德毅,孟海军,史雪梅.隶属云和隶属云发生器[J].计算机研究与发展,1995,32(6):15-20. LI Deyi,MENG Haijun,SHI Xuemei. Membership clouds and membership cloud generators[J]. Journal of Computer Research and Development,1995,32(6):15-20.(in Chinese) [9] ZHANG L M,WU X G,DING L Y,et al. A novel model for risk assessment of adjacent buildings in tunneling environments[J]. Building and Environment,2013,65(7):185-194. [10] 杨宏宇,褚润林,李东博. 一种新的网络安全态势评估方法[J].微电子学与计算机,2015,32(1):29-34. YANG Hongyu,CHU Runlin,LI Dongbo. A new method for network security situation assessment[J]. Microelectronics & Computer,2015,32(1):29-34.(in Chinese) [11] 张拥军,唐俊. 基于云模型的网络安全态势分析与评估[J].计算机工程与科学,2014,36(1):63-67. ZHANG Yongjun,TANG Jun. Analysis and assessment of network security situation based on cloud model[J]. Computer Engineering & Science,2014,36(1):63-67.(in Chinese) [12] 李德毅,杜鹢. 不确定性人工智能 [M]. 2版.北京:国防工业出版社,2014:44-65. LI Deyi,DU Yi. Artificial intelligence with uncertainty [M]. 2nd ed.Beijing:National Defense Industry Press,2014:44-65. (in Chinese) [13] 张勇,赵东宁,李德毅. 相似云及其度量分析方法[J].信息与控制,2004,33(2):129-132. ZHANG Yong,ZHAO Dongning,LI Deyi. The similar cloud and the measurement method[J]. Information and Control,2004,33(2):129-132. (in Chinese) [14] 张光卫,李德毅,李鹏. 基于云模型协同过滤推荐算法[J].软件学报,2007,18(10):2403-2411. ZHANG Guangwei,LI Deyi,LI Peng,et al. A collaborative filtering recommendation algorithm based on cloud model[J]. Journal of Software,2007,18(10):2403-2411. (in Chinese) [15] 李海林,郭崇慧,邱望仁. 正态云模型相似度计算方法[J].电子学报,2011,39(11):2561-2567. LI Hailin,GUO Chonghui,QIU Wangren. Similarity measurement between normal cloud models[J]. Acta Electronica Sinica,2011,39(11):2561-2567. (in Chinese) [16] 查翔,倪世宏,谢川,等. 云相似度的概念跃升间接计算方法[J].系统工程与电子技术,2015,37(7):1676-1682. ZHA Xiang,NI Shihong,XIE Chuan,et al. Indirect computation approach of cloud model similarity based on conception skipping[J]. Systems Engineering and Electronics,2015,37(7):1676-1682. (in Chinese) [17] SAATY T L. Decision making-the analytic hierarchy and network processes(AHP/ANP)[J]. Journal of Systems Science and Systems Engineering,2004,13(1):1-35. [18] 周华仁,张晟,穆松,等. 综合评价方法及其军事应用[M].北京:清华大学出版社,2015:18-19. ZHOU Huaren,ZHANG Sheng,MU Song,et al. Comprehensive evaluation method and its military application[M]. Beijing:Tsinghua University Press,2015:18-19.(in Chinese) FU Kai was born in Jining,Shandong Province,in 1987. He received the M.S. degree in 2012.He is currently working toward the Ph.D. degree. His research concerns network management and safety. Email:fukaia3@163.com 夏靖波(1963—),男,河北秦皇岛人,教授,主要研究方向为网络管理与安全; XIA Jingbo was born in Qinhuangdao,Hebei Province,in 1963. He is now a professor.His research concerns network management and safety. Email:jbxiad@sina.com 张晓燕(1970—),女,陕西西安人,副教授,主要研究方向为图像处理; ZHANG Xiaoyan was born in Xi′an,Shaanxi Province,in 1970. She is now an associate professor. Her research concerns image processing. Email:zxyxjwxxj@163.com 董淑福(1970—),男,山东青岛人,教授,主要研究方向为通信网络技术、无人机信息系统。 DONG Shufu was born in Qingdao,Shandong Province,in 1970.He is now a professor.His research concerns communication network technology and UAV information system. Email:shufudong@163.com A Network Situation Integrated Assessment Method Based on Cloud Model FU Kai1,XIA Jingbo2,ZHANG Xiaoyan1,DONG Shufu1 (1.School of Information and Navigation,Air Force Engineering University,Xi′an 710077,China;2.Tan Kah Kee College,Xiamen University,Zhangzhou 363105,China) In order to solve the problem of fuzziness,randomness and different standards of index quantification in network situation assessment,an integrated method for assessing network situation based on cloud model is proposed. Real number,interval number and fuzzy number are all expressed by cloud model,and similar cloud theory is utilized in network situation integrated assessment with integrating subjective and objective weights. Example analysis for communication networks shows that the proposed method can achieve rational network situation assessment qualitatively and quantitatively,and retain the uncertainty in the process of situation assessment. communication network;network situation assessment;cloud model;similar cloud theory 10.3969/j.issn.1001-893x.2016.12.008 付凯,夏靖波,张晓燕,等.一种基于云模型的网络态势综合评估方法[J].电讯技术,2016,56(12):1346-1351.[FU Kai,XIA Jingbo,ZHANG Xiaoyan,et al.A network situation integrated assessment method based on cloud model[J].Telecommunication Engineering,2016,56(12):1346-1351.] 2016-03-11; 2016-06-22 Received date:2016-03-11;Revised date:2016-06-22 航空科学基金项目(20141996018);陕西省自然科学基础研究计划项目(2012JZ8005) Foundation Item:The Aeronautical Science Foundation of China(20141996018);The Natural Science Fundamental Research Planned Project of Shaanxi Province(2012JZ8005) TN915 A 1001-893X(2016)12-1346-06 付 凯(1987—),男,山东济宁人,2012年获硕士学位,现为博士研究生,主要研究方向为网络管理与安全; **通信作者:fukaia3@163.com Corresponding author:fukaia3@163.com4 实例分析




5 结 论

