Toward Cloud-Based Parking Facility Management System: A Preliminary Study
2013-07-14ChungYangChenWenLungTsaiandTzuYinChen
Chung-Yang Chen, Wen-Lung Tsai, and Tzu-Yin Chen
1. Introduction
The motive of this paper is based on the everything-as-a-service (XaaS)[1]that has received more attention and popularity at home and abroad—the matured development and successful application of e-tags. As a matter of fact, the e-tag is found as the same as radio frequency identification (RFID), for it is non-reproducible,resistant to disturbance as well as stroke, fast identification,and intelligent discrimination[2]. Without doubt, it should offer to the management of various kinds of parking facilities with a brand new of solution, which is the motive of study for this paper. In recent years, RFID has already been one of the most important technology items, since it is taken as a novel technology that can change ways of human consumption so that it is considered as the major progress of technological advance by humans. The non-contact RFID card has successfully resolved the power problem as well as non-contact application, being one of the major breakthroughs in terms of electronic application. Therefore,we would like to make use of the e-tag stuck onto the vehicle so that information of the e-tag can be read through the cloud-based environment, then one can learn that if the vehicle has rented any space at the park lot to determine whether the vehicle is allowed to pass. Thus, it can save time, and also achieve nice management. As for the previous RFID parking permit, there was a problem that two or more individuals used the same permit for the park,and we should like to make use of e-tags and with the feature that it cannot be detached and attached repeatedly to avoid the occurrence of similar scenarios.
For the time being, certain parking facilities have resorted to the management with access by RFID, but it still can not avoid the problem of several individuals using the same card. Therefore, the use of e-tag can help resolve the problem. It can not only save time, but also resolve the situation of queuing congestion for driving into the parking facility. For the previous RFID card, it will only respond within the distance of 5 cm to the sensor, whereas the e-tag can have detected vehicles within the range of 25 cm, so that vehicles can access more efficiently. In addition, before reaching the parking facility one can use the cell phone application (APP) to check the amount of the remaining number of parking spaces. Actually, the nature of the e-tag is of the passive tag in RFID, and if it is used in the management system of parking facilities, many of its functions in the system will be the same as those of RFID.It is why we have exploited the cloud-based construction as the foundation to develop a parking facility system, based on the reuse feature of its components to, one by one,model out the development system that we need and install the management system for the parking facility making use of e-tags, acting as the precursor for other campus or parking spaces systems. In Section 2, the operating principle of e-tags, review of related literature of cloud computing, and object-orientation of e-tags are described.Section 3 and Section 4 present the process of system development and methodology, and the systematic achievement and constraints, respectively. The conclusions and future approach are given in the final section.
2. Literature Review
2.1 RFID Technology
RFID is a kind of identification management technology, and it is mainly composed of a reader and tag as shown in Fig 1. In more simple terms, the system makes use of radio frequency (RF) signals which are transmitted and received through wireless for data. At the same time, it also provides all of the power for circuit operations at the tag.
At present, a great deal of the systems has made use of RFID applications, such as the easy-card, and the frequency used by RFID will determine the distance of transmission as well as related applications for possible undertaking,such as low-frequency RFID which can only be read within 10 cm by readers. For a high-frequency reader, it can read information in the range of 30 cm to 1 m.
2.2 Application and Trend of RFID
At the moment, there is the trend of increasing use of RFID, such as the easy-card, student card, and parking permit. Besides, many more items have close contacted their daily life with RFID, its application, and services that now are inseparable from our life so that our life becomes more convenient.
In terms of parking, though there are related studies[3],[4]about making use of the RFID technology on the management of parking facilities, it would still need to take out of the RFID card and bring it closer to 5 cm distance to the sensor. Such an act is what we need to make an improvement. In fact, if we use the new function of the sensor chip with an e-tag, the sensor can detect the card in the distance of 25 cm so that one does not have to extend their hand near by the sensor before the vehicle can enter the parking facility. And since directly getting close to the sensor is not necessary, the flow of the crowd lining up for parking can be reduced.
Furthermore, the application benefits of RFID are shown in Fig. 2, so that we can know that the development trend will be gradually turned from active tags to passive ones. And the application would also embrace the aspect of service management.
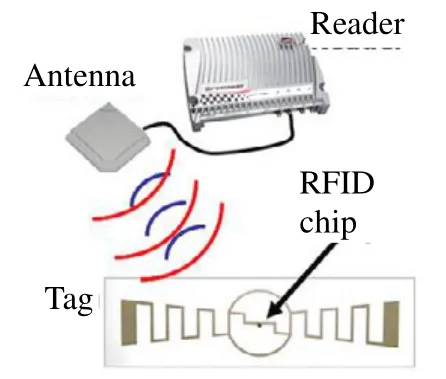
Fig. 1. RFID reader & tag[5].
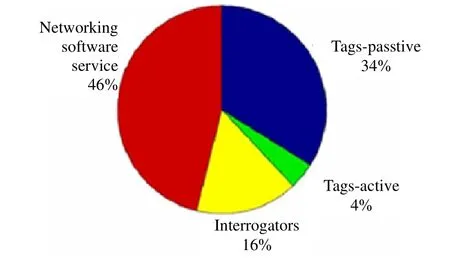
Fig. 2. Revenue ratio for RFID component types[6].
Hence, this paper would hope to make use of the identification (ID) card rather than making contact with the reader that can read, write, and identify the data stored in the card, and conduct transmission, identification, and exchange of information. It will be convenient for users to,at any time, learn about the amount of empty spaces at the parking facility, and users will not then be disappointed by learning that there is no more empty space when reaching the parking facility. The user can avoid wasting time and save gas. As the e-tag is being combined, when one reaches the parking facility during a rainy day or peak-hour, users do not have to seek for their parking permits, and it makes parking be smoother and save a lot of time. For a manager of a parking facility, since this system has e-tags, it will carry out control and management of the access of every vehicle, so that the parking permit of user will not be stolen or cheated by other people, which compromises the management mechanism and interest of the parking facility.
2.3 Cloud Computing Construction
This section simplistically presents the general construction of cloud computing[7]. Software-as-a-service(SaaS), platform-as-a-service (PaaS), and infrastructureas-a-service (IaaS) are three typical service delivery models.These services are usually delivered through industry standard interfaces, such as Web services.
SaaS is sometimes referred to as application-as-a-service. It offers a multi-tenant platform where common resources and a single instance of both the object code of an application and the underlying database are used to support multiple customers simultaneously.
PaaS provides developers with a platform, which includs all the systems and environments comprising the lifecycle of development, testing, validation, and hosting of sophisticated web applications, as a service delivered by a cloud-based platform. PaaS may offer a number of services readily, which means that PaaS can support multiple applications on the same platform.
IaaS is sometimes called hardware-as-a-service. It is extremely useful for enterprise users as it eliminates the need of investing in building and managing their own information technologies (IT) systems. Another important advantage is the ability of having access to, or using, the latest technology as it emerges.
2.4 . Object Oriented Mechanism
A major benefit of adopting the object-oriented mechanism in a software development project is real reusability: reusability of code, program portions, analyses,and designs. Now, researchers and practitioners focus their efforts on reuse of the standard and general components or structures[8],[9]. The object-oriented reuse has been discussed in terms of the building of libraries of standard object classes, as well as cataloging of the design patterns[6]-[10]and frameworks. During achieving the campus parking facility system using object-oriented approach, we realize that the functions of the system,especially that coded by the existing reusable ones, are very useful for developing a new system in the similar domain.The merits of utilizing the pre-built system functions are shown as follows.
· Lessons learned. All functions of a system provide a complete instance.
· Develop a family of system products in the similar domain.
· Reuse in all stages of the software life cycle,including analysis reuse, which is not considered in the general asset-centered reuse.
· Get more domain specifics and design context information which is needed to guide the reuse.
The previous reuse approaches tend to record down only the general or relatively stable properties of classes.For example, in the class library only the inheritance relationship is kept. Context information, which is not used as reusable assets, may help to understand and guide the reuse.
3. Methodology
This paper would hope to develop a parking system that combines e-tags into the cloud computing environment, so it would employ the development model of information system in software engineering as the methodology for implementation. Furthermore, since the e-tag is of the passive tag, whose application mechanism is similar to that of RFID, even some functional components can be reused.Also, in the context of restricted time, the purposed system in this paper could not be built by iterative and incremental development. Thus, based on the reuse characteristic of object-oriented development, we build the cloud-based parking facility management system. On the other hand, the conditions of scenarios should include teaching faculty,staff, and students; nonetheless, for the limited budget, this paper is a preliminary study. We make interviews to collect and analyze information for the system design, and focus on the needs of key men (i.e. teacher).
3.1 . Collection of User Needs
· Explanation of user requirements
The following is the content brief on the interview of key men for their needs, “⋅⋅ in view of the increasing trend for RFID, individuals have more than one card, such as the Easy-card, students card, parking permit, and more and more things would then be combined with RFID. It would then render convenience to users, but for the most part of parking, one would still have to extend hands and press the button, or bring the RFID card out and reach the range of 5 cm to the sensor. For this, we can now make an improvement. The new function of the sensor chip in the e-tag can be detected within the distance of 25 m. And one can be spared from extending their hands to get close to the sensor before entering the parking facility. Since one can get detected directly, it would help reduce the crowd lining up into the parking facility, for everyone is spared from the act of finding card, cutting down the congestions. …”
· System range
a) User: the motorcyclist can save the action of taking out of the RFID card, and access the parking directly by his e-tag. Thus, it is most convenient and saves time, and it will not result in jam caused by lining up.
b) Manager: when vehicles enter and exit, it will discriminate whether the user is in this parking facility, and show the remaining amount of parking spaces so that it can facilitate the inquiry of the user.
· System functions table is shown in Table 1.
· Consideration of other needs for management of the e-tag parking facility.
Consideration of key functions for other requirements regarding the management of e-tag parking is that: “It must include the concerns of saving manpower, lowering cost,increase of efficiency, and marginal effect.”
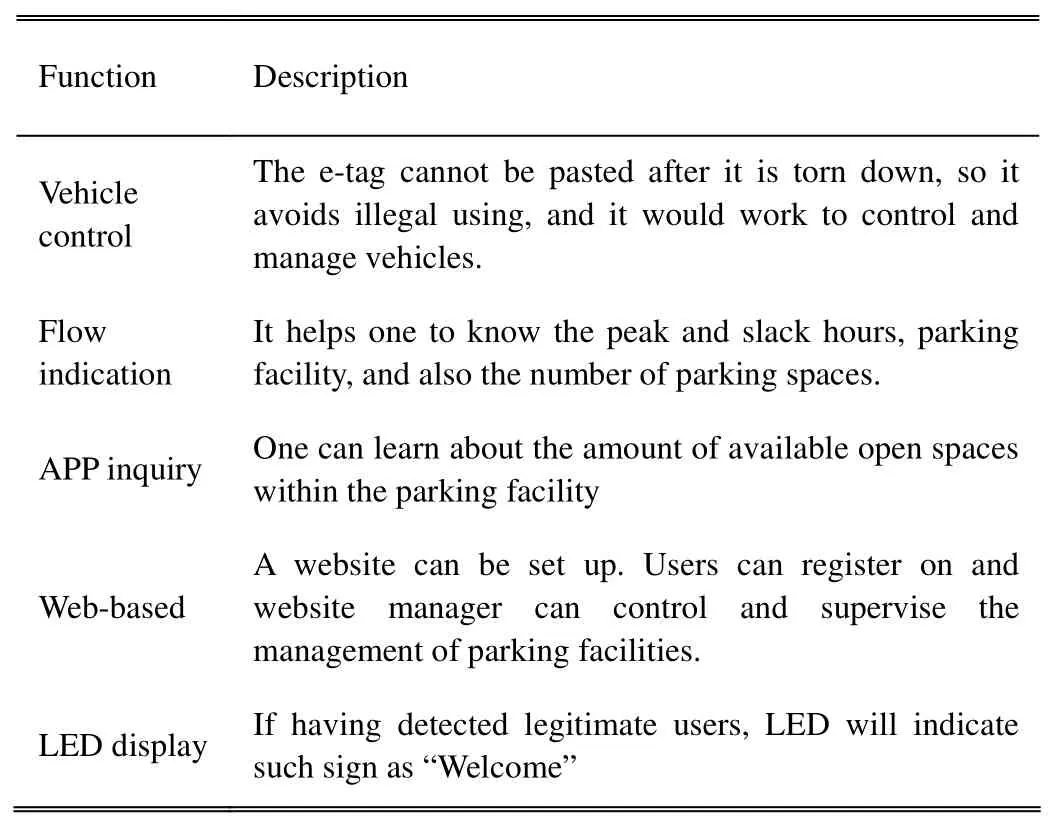
Table 1: System functions table
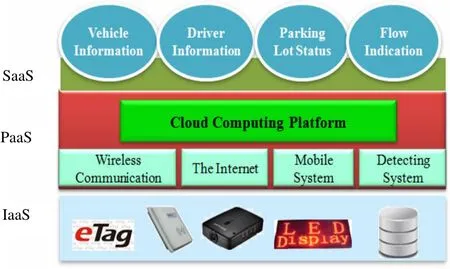
Fig. 3. System construction of campus parking facility management system.
3.2 System Construction
According to the system range and function, the construction of the cloud-based campus parking facility management system can be divided into the IaaS, PaaS, and SaaS layers, as shown in Fig. 3.
· IaaS layer: The main function in IaaS layer is using RFID tags, readers, all kinds of sensors, video cameras, etc.to collect the data and a great deal of information for the vehicle management system (e.g. vehicle information).
· PaaS layer: PaaS layer is a system platform. In this paper, it means that the cloud computing platform includes four modules: wireless communication, the Internet, the mobile system, and the detecting system.
· SaaS layer: SaaS layer is responsible for the communication between people and machines, such as all kinds of car terminal, on-board computer, etc. Through the detecting system and wireless communication network,detailed driver and vehicle information are provided.
3.3 Installation of System Development Environment
Based on the management of campus parking facility,this paper construes a specialized parking facility management system and simulates the front-end user.Through the reader that reads e-tags for information and combines the management system of rear-end database, it would achieve the objective of exactly mastering the access permission by vehicles. During the process of practice, we will use Tibbo which is a dialect of the BASIC programming language, designed for programmable logic controllers to compose the system and read and write the e-tag functions as well as the specifications for the control and supervision file of data information when we install the database management system. The requirements of the system environment include the hardware equipment,software items, and tools of the development program.
3.4 System Analysis
Use Case
Once users’ needs have been analyzed and concluded,the use case of unified modeling language (UML) will be used to demonstrate the functions of parking facility management required for e-tags, and they are organized as follows.
· In Fig 4, a user needs to have ID and authority limit so that the manager can control the access of vehicles.
· Through the flow that communicates with the manager, the user can know how many spaces are left within the parking facility at that time.
· User through the cell phone App to know how many spaces is left available.
· As shown in Fig. 5, from the webpage, the users can learn about information conveniently from the webpage and the manager can easily run the parking facility.
· When the reader has read the e-tag as the legally detected and authorized, the LED shows access is granted.If it does not detect or sensed the authorized e-tag, it will show denial for access.
Sequence Diagram
Fig. 5 explains that if the manager is to access the management interface he must first verify the account number and access code. When such information has been confirmed, then the manager can change the content of the database.
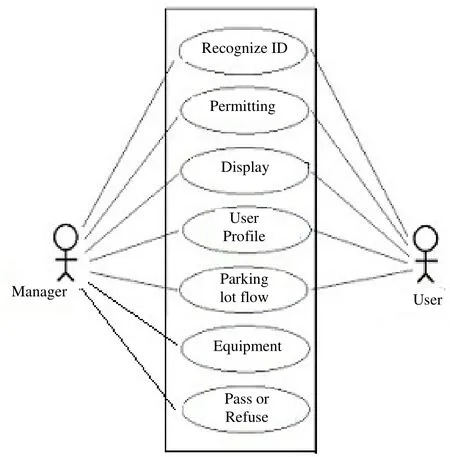
Fig. 4. Use case.
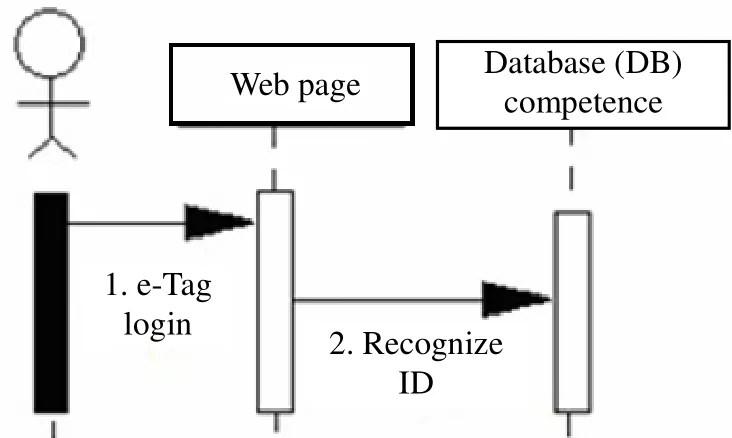
Fig. 5. Management sequence diagram.
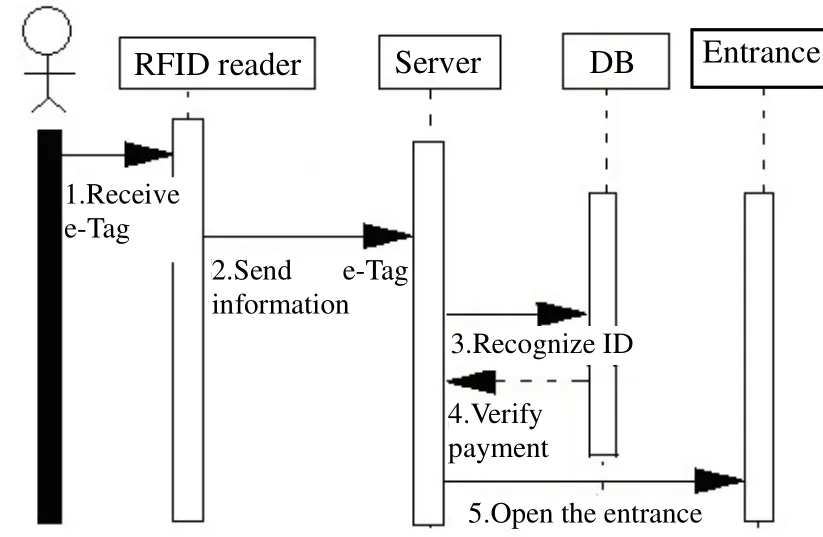
Fig. 6. System sequence diagram.
In Fig. 6, it explains that the system will first detect the e-tag on the user’s. Initially, the reader will check if there is any e-tag. If no e-tag has been detected, it will directly refuse to pass; if there is, it will detect the serial number of the e-tag and send related information to the server for verification to see if the e-tag is legal. If the e-tag is not legal, it will deny the pass; if it is, it will next send information back to the database to check the validity of ID,and if the ID cannot be confirmed, it will deny, too. If ID has been confirmed, it will, afterwards, verify if the user has paid the toll; if the user has not, pass will also be refused; if the user has already paid the toll, the system will,at the end, conduct the last step and send the command back to the server and be instructed for the entrance.
Activity Diagram
Fig. 7 (a) is about the process of using an e-tag for entrance. First, if the RFID reader has detected an e-tag and conduct ID confirmation, and if it finds that the e-tag has paid the toll, the railing will be lifted up. If not, the railing will not be lifted, so that user cannot pass through.
Fig. 7 (b) explains that when the manager is to access into the management interface of the webpage they must first conduct ID verification. Only when the account number and access code are accurate, they can then access into the monument system, and carry out the action of supervision and management.
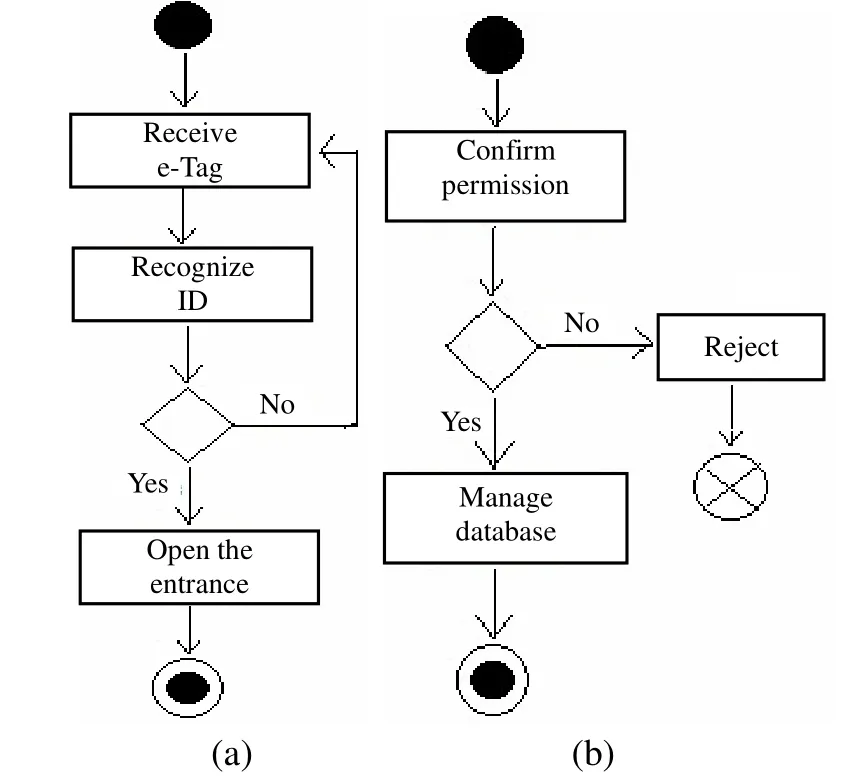
Fig. 7. Activity diagram: (a) system and (b) management.
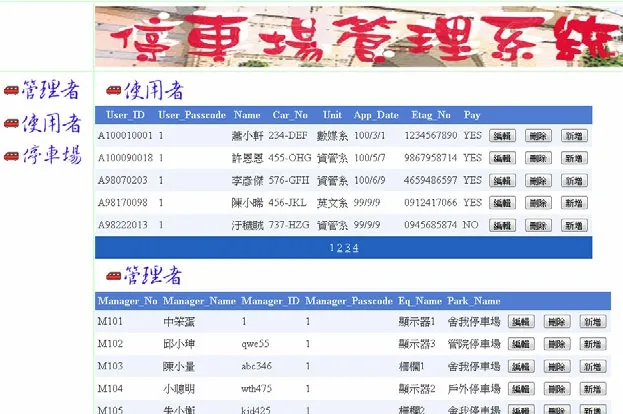
Fig. 8. Screenshot of webpage.
4. Results and Constraints
4.1 Results
Fig. 8 shows the screenshot after the manager has accessed with the accurate account number and access code,the manager can, according to the authority of the manager,directly add, delete, and modify content in the database on the web page.
4.2 Constraints
Since the time of development is limited, it has merely developed a prototype. But it can be a reference for subsequent development, or be the blueprint and commissioned to the third party. The comprehensive e-tag is of the recent application product of RFID, but we are still unable to have fully mastered its technique. The module of e-tag components can not be all reused, and it is why the front-end and backstage in the prototype as well as the control component of the panel have been developed on its own rather than reused.
The primary contribution of this paper is that it can conduct through UML, blending the object-oriented mechanism to develop the cloud-based campus parking facility system, and it is considered as the innovative development method for system application. However,since the budget is limited, there can hardly be effect of practicality and substantiation. If the budget is sufficient and there is the support of technologies from working manufacturers, it can render all functions of the system perfectly and implement the professional campus parking facility management system.
5. Conclusions
The cloud-based parking facility management system proposed in this paper is mainly based on the concept of cloud computing in a general construction and related e-tag applications of the RFID wireless ID system, meanwhile the object-orient method is used for development. In addition, it has worked with the webpage software language to design the interactive web page and combined with the management system blended with the database, so that the system can cooperate with the webpage, database, and function of remote access. The system has been considered as a structured query language (SQL) server for it can conduct access with massive amount of database, and the development environment is also given with open source components ASP.NET, so it will not have to pay for the extra expenses of the utility. As such, it has lowered the cost of development, and drastically improved the quality of automatic parking.
With the merits of lower installation cost and power-consumption, using e-tags for realization and application is considered as the latest concept and technology for the management of parking, and it can replace campus parking with a previous RFID sensor card.In such a way, it can not only effectively eliminate the scenario of several individuals using one card, but also reduce the crowd lining up during the rush hours of getting in and out of the parking facility. Through the APP function of a cell phone, the system can help users to quickly obtain the parking status of vehicles in and out as well as the parking facility, thus enhancing service quality and parking efficiency. In addition, the system can also effectively make use of resources, and accommodate the mutual needs of drivers (such as teachers, staff, and students) and the school management of parking facilities. As a recapitulation, the system has combined the technology of RFID and the database of a cloud-based construction to enhance the function of the present automation system, so that the parking spaces can be efficiently utilized. It makes use of application programming of e-tags to clearly provide optimized parking facility management with reference of needs, and it can then increase the overall benefit of the cloud-based system development that after this.
Reference
[1] P. Banerjee, R. Friedrich, C. Bash, P. Goldsack, B.Huberman, J. Manley, C. Patel, P. Ranganathan, and A.Veitch, “Everything as a service: powering the new information economy,” Computer, vol. 44, no. 3, pp. 36–43,2011.
[2] K. Finkenzeller and D. Muller, “Differentiation features of RFID systems,” in RFID Handbook: Fundamentals and Applications in Contactless Smart Cards, Radio Frequency Identification and Near-Field Communication, 3rd ed. K.Finkenzeller, Ed. London: John Wiley & Sons, Ltd. Press,2010, pp. 11–28.
[3] Y.-R. Huang, “A study on the application of radio frequency identification (RFID) in the curb parking,” M.S. thesis, Dept.of Transportation & Communication Management Science,National Cheng Kung University, Tainan, 2009.
[4] T.-M. Lin, “RFID technology applies to park the planning of management,” M.S. thesis, Dept. of Communication Engineering, National Central University, Taoyuan, 2007.
[5] RFID is wandering between the privacy and security.[Online]. Available: http://youhuizi. wordpress.com/2010/04/13/rfid-security-and-privacy/
[6] P. Harrop and R. Das. (2012). RFID Forecasts, Players &Opportunities 2012-2021. [Online]. Available: http://www.IDTechEx.com/forecasts
[7] B. P. Rimal, A. Jukan, D. Katsaros, and Y. Goeleven,“Architectural requirements for cloud computing systems:an enterprise cloud approach,” Journal of Grid Computing,vol. 9, no. 1, pp. 3–26, 2011.
[8] R. Gelbard, D. Te'eni, and M. Sade, “Object-oriented analysis: is it just theory?” IEEE Software, vol. 27, no. 1, pp.64–71, 2010.
[9] B. S. Lerner, S. Christov, L. J. Osterweil, R. Bendraou, U.Kannengiesser, and A. Wise, “Exception handling patterns for process modeling,” IEEE Trans. on Software Engineering, vol. 36, no. 2, pp. 162–183, 2010.
[10] S. Konrad, B. H. C. Cheng, and L. A. Campbell, “Object analysis patterns for embedded systems,” IEEE Trans. on Software Engineering, vol. 30, no. 12, pp. 970–992, 2004.
杂志排行
Journal of Electronic Science and Technology的其它文章
- Call for Papers Journal of Electronic Science and Technology Special Section on Terahertz Technology and Application
- JEST COPYRIGHT FORM
- ID-Based User Authentication Scheme for Cloud Computing
- Interpurchase Time of Customer Behavior in Cloud Computing
- A Genetic Algorithm Based Approach for Campus Equipment Management System in Cloud Server
- A Distribution Management System for Relational Databases in Cloud Environments
