Architecture of Ubiquitous Mobile Internet
2010-09-08
(National Engineering Laboratory for Next Generation Internet Interconnection Devices,Beijing Jiaotong University,Beijing 100044,P.R.China)
Due to technological advances,the amount of information available within societies is ever increasing.The Internet has become a strong driving force of economic and social development,and such development requires the Internet to provide pervasive services anywhere,anytime,and in numerous ways.However,defects in the Internet’s original design hamper it from fulfilling these requirements.First,by employing fixed and wired connections,the Internet cannot meet user demands in a wireless mobile environment[1](let alone provide network services for users anywhere,anytime,and in numerous ways).Next,the Internet was originally designed for data services,and is not satisfactory for voice and image transmission.It is insufficient for diverse networks,and cannot support diverse and pervasive services.Finally,as a scale-free network with a power-law structural topology[2],the Internet is poorly secured,and quite vulnerable to attack or deception.In sum,the existing Internet is not only incapable of satisfying current application demands for ubiquity and mobility,but is also hindering the further development of information networks.A new network architecture with breakthrough design is needed to solve the Internet’s serious shortcomings.
In recent years,many countries have begun to carry out research into new Internet architecture.The US National Science Foundation(NSF)launched a 100x100 Clean Slate Project[3]in 2003,and in August 2005,sponsored the well-known Global Environment for Network Innovations(GENI)project[4].Later in December 2005,the NSF also proposed the Future Internet Design(FIND)program[5].In 2004,British Telecom announced their 21st Century Network(21CN)project[6],and in 2007,the European Union approved the Seventh Framework Programme for Research and Technological Development(FP7).This programme attracted 930 million euros for research into information and communication technologies;in particular,the design of future network and service architecture.It aimed to spark a revolution in the information industry by creating a new architecture.Also in 2007,the EU established a next generation network research group and started the Future Internet Research and Experimentation(FIRE)Initiative[7].Forty million euros were invested into this initiative.Meanwhile,countries such as Japan and South Korea also began researching theories of future Internet architecture.By redesigning a next generation information network,these abovementioned projects,especially GENI and FIND,have attempted to remedy serious defects in Internet mobility,security,sensing,and support for pervasive services.However,projects such as GENI are still in their infancy and are at the stage of planning the research of next generation information networks.They have yet to work out clear schemes for theoretical research.Other projects have studied only a single or several aspects of future Internet but lack a comprehensive and systematic approach to new network architecture,its key theories and technologies.

Figure 1.Model of ubiquitous mobile Internet architecture.
The National Engineering Laboratory for Next Generation Internet Interconnection Devices(Beijing Jiaotong University)has used the"Fundamental Research on the Architecture of Universal Trustable Network and Pervasive Services"project of the National Basic Research Program of China("973"Program)as a platform for actively exploring new architectures.It has produced a series of research results[8-10].Drawing on these results,this paper proposes an architecture for ubiquitous mobile Internet,enabling the Internet to provide pervasive services at any place,at any time,and by any means.
1 The Overall Architecture of Ubiquitous Mobile Internet
Reference[8]proposes an overall universal network architecture and defines a number of basic concepts,such as parsing and mapping of access identifier,parsing and mapping of service identifier,and parsing and mapping of connection identifier,that are used herein.This paper introduces an Internet architecture based on that architecture,and which encompasses the demands and features of ubiquitous mobile Internet.
As shown in Figure 1,the overall architecture of ubiquitous mobile Internet can be divided into two layers:infrastructure layer and pervasive service layer.
The functions of the infrastructure layer include providing unified network access for ubiquitous wireless and mobile terminals,implementing mobility management of ubiquitous mobile Internet,and performing data switching and routing.In the infrastructure layer,a virtual access module,virtual backbone module,and parsing and mapping of access identifier are introduced.Using access identifiers,the virtual access module supports identification and access of ubiquitous mobile terminals.The virtual backbone module provides switching-routing identifiers for various types of access;these indicate the locations of ubiquitous mobile terminals and are used in switching and routing in the core network.The parsing and mapping function of an access identifier maps an access identifier onto a switching-routing identifier,thus enabling user identities to be separated from and combined with their locations.
To control and manage diverse services,the pervasive service layer uses concepts such as virtual service module,virtual connection module,parsing and mapping of service identifier,and parsing and mapping of connection identifier.The virtual service module uses a service identifier to describe and represent various services;the virtual connection module provides several connections for each service;the parsing and mapping of the service identifier maps a service object onto several service connections(to support diverse services);while the parsing and mapping of the connection identifier maps a service connection onto several connections in the infrastructure layer.This embodies the idea that one service can correspond to several connections and paths,thus making service more reliable.
2 Architecture and Theory of the Infrastructure Layer
Unified network access is necessary for various types of mobile terminals in the ubiquitous mobile Internet(as shown in Figure 2).The terminal can be a specific type—for instance,a Wireless Local Area Network(WLAN)terminal that accesses the core network via a corresponding access network—or it can be a reconfigurable terminal that uses Software-Defined Radio(SDR)technology to dynamically and intelligently select an access network before accessing the core network.
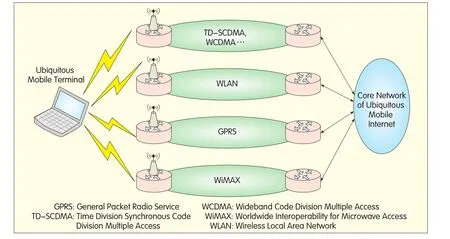
Figure 2.Ubiquitous mobile access.
To enable unified access of ubiquitous mobile terminals,the virtual access module introduces an access identifier mechanism.The module not only allows users to enjoy optimal access and communication anytime,any place,and with widely pervasive services,but also ensures interconnection and close cooperation among heterogeneous networks.The module enables coordinated configuration of services and resources via the core network;that is,traffic sharing among networks and spectral resource sharing.To facilitate route selection of the core network,the virtual backbone module employs a switching-routing identifier for generalized switching and routing in the core network.
As shown in Figure 1,a core function of the infrastructure layer is parsing and mapping of the access identifier.The parsing and mapping function of the access identifier is responsible for mapping an access identifier into a switching-routing identifier,achieving separation of user identifier from its location.Specifically,its main functions include:
(1)Ensuring the mobility of various access networks and users.When one access network relocates,only its switching-routing identifier and the mapping relation between the switching-routing and access identifiers(representing user identities),needs to change.The access identifiers need not change.In this way,a user can enjoy various services without experiencing an interrupted connection.
(2)Enabling unified access of ubiquitous mobile networks and terminals,such as WLAN,Code Division Multiple Access(CDMA),Worldwide Interoperability for Microwave Access(WiMAX)and sensor networks,in the infrastructure layer.This expands the range of network services.
(3)Guaranteeing user security and privacy.The access identifier is the identity of the whole network,whereas the switching-routing identifier is only used for switching and routing in the core network.When separated from the switching-routing identifier,the access identifier will not be broadcast in the core network.Other users cannot therefore intercept user information for malicious purposes because such information is effectively secured.Nor can they intercept core network information for the purpose of analyzing another user’s identity.User privacy is protected.
(4)Allowing the network to be controllable and manageable.When a ubiquitous mobile access network applies for its access identifier,the network administrator must execute access control by giving authentication according to subscription information.Based on the authentication result,the administrator decides whether to accept a connection request,and determines the Quality of Serivce(QoS)class to be provided.
In short,the infrastructure layer offers sound,network-level support to the ubiquitous mobile Internet.
3 Architecture and Theory of the Pervasive Service Layer
The goal of the pervasive service layer is to provide diversified,pervasive services for the ubiquitous mobile Internet.To this end,the pervasive service layer employs a virtual service module,a virtual connection module,parsing and mapping of service identifier,and parsing and mapping of connection identifier.
The virtual service module is the basis for delivering pervasive services.It is used to describe various services in a unified way,and to control and manage these services.It uses a service identifier to uniformly distinguish and describe diversified services,conveying the idea of pervasive services.The parsing and mapping done by the service identifier associates the virtual service module with the virtual connection module,thereby mapping the service identifier into the connection identifier and setting up connections for various services.
The virtual connection module employs a connection identifier for identifying a service connection and a user.It offers mobility and security to a connection and guarantees a certain QoS class.The parsing and mapping done by the connection identifier,maps a connection identifier into an access identifier of the infrastructure layer.
Here,the primary focus of explanation lies on the mapping mechanism from a connection identifier into an access identifier—as this is central to ubiquitous mobile support.
Traditional network design does not take into account the coexistence of multiple accesses,and in most cases communication parties can only use one path for data transmission.When the path fails or performs poorly,the sender can do nothing but wait.With the continuous development of wireless technology,an increasing number of network access technologies have been put into commercial use.As a result,it is now possible for the communication parties to establish active and standby paths for data transmission.When one path fails or does not perform well,the sender can use the other to transmit data.Moreover,the introduction of multiple access modes creates conditions for concurrent transmission via multiple paths.Concurrent transmission implies the simultaneous transmission of data via multiple paths.A transmission method of this kind can improve both reliability and security of data transmission.Where one path only is involved,an eavesdropper can easily intercept the communication by monitoring the path.Multipath concurrent transmission,however,prevents this from happening because an eavesdropper is unlikely to attempt monitoring data packets on multiple paths at the same time.A higher level of data transmission security is therefore realized.
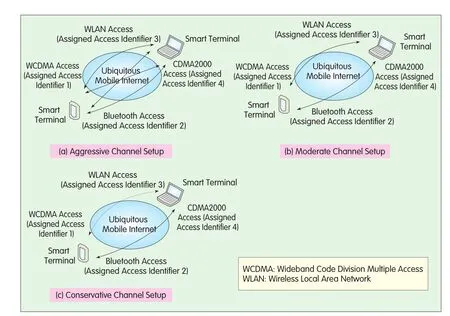
Figure 3.Three channel setup methods.
In the ubiquitous mobile Internet,multipath concurrent transmission is closely related to the mapping from the connection identifier to the access identifier.After a connection identifier has been generated,the question of setting up a corresponding data transmission channel must be addressed.This setup process entails the mapping from the connection identifier to the access identifier.Upon generating a connection identifier,the two communication parties should establish a suitable path according to the requirements of services they wish to obtain.When they procure these services,they may adjust the path based on the network status(as the Internet is time variant).Therefore,the mapping process should be dynamic and in real-time.
A simple example can explain the process of dynamically selecting a suitable channel setup.Suppose both A and B can access the Internet via two modes:WLAN and 3G.They can establish an aggressive channel setup method(four data transmission channels),a moderate setup(two transmission channels),or a conservative setup(only one transmission channel).These three methods are shown in Figure 3.The channel should be specifically set up according to each connection identifier.
4 Mobility Management Mechanism
In the ubiquitous mobile Internet with access identifiers and switching-routing identifiers,the two communication parties use an access identifier to initiate communication.Because the access identifier visible to users does not include location information such as network prefix,the two parties do not know the location of each other until the communication has been set up.Therefore,a complete location management scheme is necessary to enable the router accessed by the user to obtain the location of the other user according to the access identifier.Otherwise,the communication cannot be set up.This paper proposes a location management system to facilitate this connection.A location management system stores the access identifiers of various terminals in the local network,and also the mapping relations of current switching-routing identifiers.It accepts queries for switching-routing identifiers to match access identifiers.When the location of a terminal changes,its information in the system is updated to avoid any communication failure due to location information error.
For effective management of identities and terminal location information,two functional entities are needed:access switching router and mapping server.The access switching router assigns access identifiers and switching-routing identifiers for users.During communication,it replaces the user’s data packet identifiers,enabling the packets to be transmitted between the core network and access network.This router stores the location information of the local access terminal as well as that of the opposite terminal.A local buffer approach enhances efficiency in querying.When an identifier cannot be found in the router’s storage table,the query then turns to the mapping server.For the most part,this server maintains the mapping relations between access identifiers and switching-routing identifiers in the network,and provides a query service for access switching routers and other mapping servers.It is the most important storage component in the whole location management system.In designing the storage system for a mapping server,a centralized storage approach by region can be adopted.
Mobility management predominately involves mobility detection,location registration,and location update.
(1)Mobility Detection
Mobility detection combines active and passive detection methods.In passive mobility detection,a mobile node passively monitors the access router notifications or messages broadcast or multicast on the links after the link layer has been switched over.According to the contents of these notifications or messages,the node judges whether movement has taken place.In active mobility detection,a mobile terminal actively scans surrounding networks when the quality of the radio link(e.g.signal strength)of the local network cannot meet normal communication requirements.The mobile terminal determines whether there is any access switching router that can meet the communication requirements.On detecting such a router,the terminal initiates authentication and access to that router.
(2)Location Registration
Location registration is the basis of terminal management in the network.It is implemented by the access switching router and mapping server,and is designed to create storage units within the mapping server for the terminals(which are used for query during communication setup).
When a user accesses the network via an access switching router,the router takes an idle switching-routing identifier from the local identifier pool,assigns it to the user,and initiates the location registration process for the user terminal.If the terminal moves to a new region,the location registration process is also performed and the location update function triggered.
When a new terminal appears,the access switching router checks the local switching-routing identifier pool.If there are idle identifiers,the router assigns one switching-routing identifier to the terminal.Upon assignment,the router sets up a new storage unit in the local user mapping table,records the access identifier/switching-routing identifier mapping pair of the terminal,and sets a related timer for this storage unit.Then the router reports the mapping relation to the local mapping server as the terminal cannot initiate communication until it is registered with the local mapping server.
After the mapping server processes the reported mapping relation,it returns a response message to the access switching router,where the registration result is included.If the registration fails,the router can obtain related error information from the response message and re-initiate the location registration following error correction.If the registration is successful,the location registration process ends.
The location registration process described above begins with the assignment of a switching-routing identifier by the access switching router and ends with a successful registration message returned by the mapping server.This process is designed to set up a storage unit for a new terminal(or a terminal arriving from elsewhere)in both the access switching router and mapping server.If the terminal’s storage units already exist,the location information will be updated.
(3)Location Update
The number and types of mobile terminals in the network are continuously increasing,and new services are demanding more in terms of mobility support.One critical issue in mobility management is the timely update of mobile terminal locations.During communication,a terminal may frequently change its access points.At each change,the location management system needs to update the terminal’s location information to ensure uninterrupted communication.
In a local network,access for all types of terminals is unified and the locations of all terminals are centrally managed by region.The location update process is as follows:when a terminal changes location,all entities holding the old mapping information are informed by the network of the terminal’s new switching-routing identifier.Upon receiving the new identifier,all entities update their mapping information or delete the old storage unit of the terminal.The update process is performed via message interaction between mapping servers and access switching routers.The goal of location update is to ensure all entities holding location information can update or delete old information in a timely manner in order to avoid errors when setting up a new communication.
5 Conclusions
To remedy serious defects in the Internet,this paper proposes a new architecture for ubiquitous mobile Internet and discusses the models and theories of its two layers:the infrastructure layer,and the pervasive service layer.The former allows users to access the Internet at any place,at any time and by any means;and the latter can support pervasive services.
Although some encouraging advances have been made,the architecture presented in this paper is still in the conceptual design stage.Deeper research needs to be undertaken into the theories and key technologies.
[1]张宏科.移动互联网络技术的现状与未来[J].电信科学,2004,20(10):5-7.ZHANG Hongke.Mobile IP Technology:Present and Future Directions[J].Telecommunications Science,2004,20(10):5-7.
[2]WATTS D J,STROGATZ S H.Collective Dynamics of Small-world Networks[J].Nature,1998,393(6684):440-442.
[3]100x100 Clean Slate Project[EB/OL].[2009-08-19].http://100x100network.org/.
[4]DEMPSEY H P.GENI:Global Environment for Network Innovations[EB/OL].[2006-11-15].http://www.geni.net.
[5]FIND:Future Internet Network Design[EB/OL].[2008-08-19].http://find.isi.edu.
[6]21CN Project[EB/OL].[2008-07-17].http://www.btglobalservices.com/business/global/news/2005/edition_1/21CN.html.
[7]FIRE:Future Internet Research and Experimentation[EB/OL].[2008-08-20].http://cordis.europa.eu/fp7/ict/fire/.
[8]张宏科,苏伟.新网络体系基础研究——一体化网络与普适服务[J].电子学报,2007,35(4):593-598.
ZHANG Hongke,SU Wei.Fundamental Research on the Architecture of New Network—Universal Network and Pervasive Services[J].Chinese Journal of Electronics,2007,35(4):593-598.
[9]董平,秦雅娟,张宏科.支持普适服务的一体化网络研究[J],电子学报.2007,35(4):599-606.
DONG Ping,QING Yajuan,ZHANG Hongke.Research on Universal Network Supporting Pervasive Services[J].Chinese Journal of Electronics,2007,35(4):599-606.
[10]杨冬,周华春,张宏科.基于一体化网络的普适服务研究.电子学报[J].2007,35(4):607-613.
YANG Dong,ZHOU Huachun,ZHANG Hongke.Research on Pervasive Services Based on Universal Network[J].Chinese Journal of Electronics,2007,35(4):607-613.
