Attack-Resilient Distributed Cooperative Control of Virtually Coupled High-Speed Trains via Topology Reconfiguration
2024-04-15ShunyuanXiaoXiaohuaGeSeniorandQingWu
Shunyuan Xiao ,,, Xiaohua Ge ,Senior,, and Qing Wu ,,
Dear Editor,
This letter addresses the resilient distributed cooperative control problem of a virtually coupled train convoy under stochastic disturbances and cyber attacks.The main purpose is to achieve distributed coordination of virtually coupled high-speed trains with the prescribed inter-train distance and same cruise velocity, while preserving driving security of the train convoy against a class of topological attacks.First, a resilient distributed cooperative control framework of the virtually coupled train convoy is established, which incorporates the longitudinal train dynamics, stochastic disturbances, and topological attacks on inter-train information flows.Building on that, a distributed cooperative control protocol and a topology reconfiguration algorithm are designed for attack-resilient train convoy tracking.Furthermore, a formal stability analysis is performed for the exponential convergence of the convoy tracking errors.Finally, a numerical case study on a 56 km-line segment of a real-world high-speed railway is carried out to validate the efficacy of our results.
In a virtually coupled train convoy, each train is equipped with onboard sensors, data processors, and transceivers, allowing for the exchange of specific train-related data (e.g., speed, position, acceleration, braking actions) with its neighboring trains in accordance with specified information flow topologies.By sharing the train information in real-time, interacted trains can make cooperative decisions and adjust their own operations accordingly to achieve a harmonized tracking objective of the train convoy [1].This therefore testifies the significant role of the inter-train information flows in the desired train convoy tracking control.However, the implementation of virtually coupled trains is prone to malicious security threats on the wireless train information flows [2]–[4].It is well-acknowledged that these malicious cyber attacks can impose significant adverse effects on the system and control performance [5]–[9].Among the various cyber attacks targeting inter-train information flows, data availability attacks, such as wireless radio jamming, routing protocol falsification, and network traffic flooding [2], aim at impeding the transmission of exchanged information to the intended recipient.
When it comes to the design of a cooperative control strategy over generic information topologies, consensus-based control has been pervasively adopted [3], [4], [10]–[13].In the context of virtual coupling control, this therefore allows flexible or varying communication topologies to be comprehensively analyzed and designed from the entire train convoy perspective.However, the majority of existing cooperative train control results rely on preconceived notions regarding the leader’s global reachability or the presence of a spanning tree with the leader train acting as its root; see, e.g., [3], [4],[11]–[13].This implies that the control strategies therein may fail to guarantee the train convoy stability once the leader’s global reachability is no longer satisfied, for example, due to malicious data availability attacks.To the best of the authors’ knowledge, there have been rare studies available on cooperative control of virtually coupled trains where data availability attacks are present to violate the global reachability assumption.
In this study, we delve into the resilient distributed cooperative control issue for multiple virtually coupled high-speed trains subject to topological attacks.To cope with such attacks, we propose an attack-resilient distributed cooperative control protocol together with an information flow repairing algorithm via topology reconfiguration.Summarized below are the main contributions of this study:1) A resilient distributed cooperative control framework of a virtually coupled train convoy is established, which incorporates the longitudinal train dynamics, stochastic disturbances, and aperiodic topological attacks; 2) A numerically tractable controller design procedure and a topology reconfiguration algorithm are presented for effective and secure cooperative train tracking control; 3) A formal stability analysis is conducted to prove the exponential convergence of relative positions and velocities to the leader.
Problem formulation: Consider a train convoy comprisingN+1 high-speed trains, where the leader train is represented as train 0 while the rest follower trains are indexed byi∈VN={1,...,N}.The longitudinal dynamics of trainican be characterized by

and implement Algorithm 1 when χ (t)=1.

Algorithm 1 Topology Reconfiguration Require: Repairing procedure activation signal χ(t)=1 χ(t)1: while do Fσ(t)=(VF σ(t),EF 2: Identify a remaining spanning tree with the maximum number of trains, where and are the train index set and information link set of Fσ(t)σ(t))ns VFσ(t)⊆VN EFσ(t)⊆Eσ(t)Fσ(t)3: if the root of is train 0 then Fσ(t) 0,1,...,ns-1 4: Renumber the trains in as such that each train’s parent node is lower numbered than itself¯ns=ns-1 5: Set 6: else 7: Renumber the trains in as such that each train’s parent node is lower numbered than itself 8: Build an information link from train 0 to the renumbered train 1¯ns=ns Fσ(t) 1,...,ns 9: Set 10: end if Υ=∅11: Define i= ¯ns:N-1 12: for do j=1:N 13: for do j ∉VFσ(t)∪Υ 14: if then 15: Identify train i’s nearest available neighbor j(j,i)∉Eσ(t)16: if & Train j is not informed by train 0 then(j,i)j ∉VFσ(t)17: Build an information link from renumbered train i to its nearest neighbor train j,VF σ(t)=VFσ(t)∪{j}18: Update EFσ(t)=EFσ(t)∪(j,i)19: Update 20: Renumber train j as in break 21: else Υ=Υ∪{j}i+1 Fσ(t)22: Update 23: end if 24: end if 25: end for 26: end for 27: end while
Stability analysis: The exponential stability analysis criterion for the train tracking error dynamics (4) is presented as below.
Theorem 1: For a virtually coupled high-speed train convoy with longitudinal dynamics (2) and compromised inter-train information flows, under the distributed cooperative control protocol (3) and repairing Algorithm 1, the tracking errors δi(t),i∈VNare exponentially stable in mean square if (5) and (6) hold.
Proof: Choose the Lyapunov function candidate as


The information flow topologies during attacking periods and repairing periods are depicted in Fig.1.It can be seen that the information links (3, 2) and (1, 3) are reconstructed after links (1, 0), (2,1), (3, 2) and (5, 0) being interrupted by Type I attacks.Together with the link reconstruction results facing Types II and III attacks, we observe that relatively few information links (less than the number of disrupted links) are built through Algorithm 1 to handle the topological attacks.
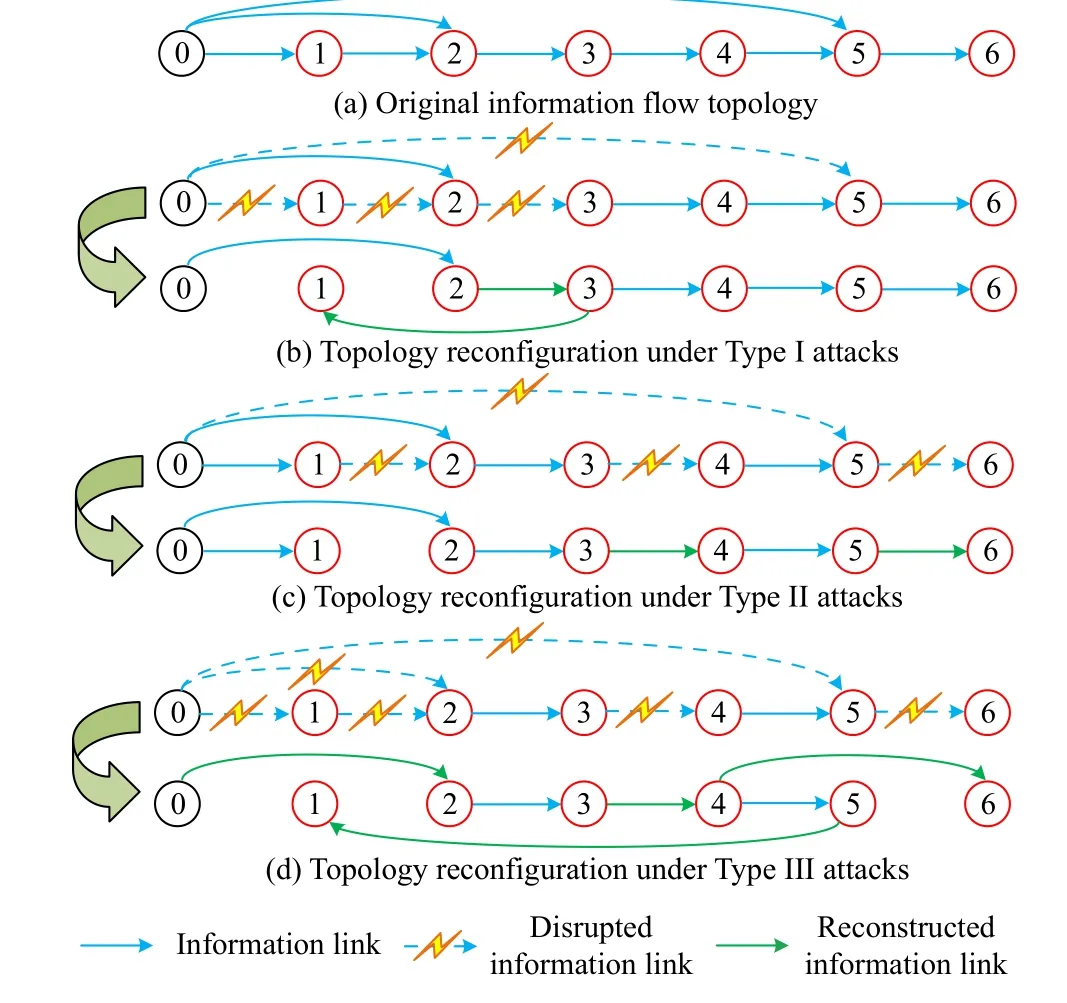
Fig.1.Information flow topologies during attacking and repairing periods under topology reconfiguration.
Applying the proposed controller design procedure, we obtain≤2.4319s, which indicates the upper bound of average implementation time of repair procedures.Following this requirement, together with the proposed Algorithm 1, the relative positions and velocities of follower trains to the leader, are depicted in Figs.2(a) and 2(b),respectively.It is seen that although the simulated topological attacks disrupt the global reachability of the leader train, the virtually coupled train convoy under our proposed secure distributed cooperative control scheme still achieves the desired train tracking performance in terms of prescribed inter-train distances (w.r.t.mass points) of 450 m and same velocities.
Conclusion: The resilient distributed control problem of virtually coupled high-speed trains encountering topological attacks is addressed in this paper.To cope with the generic inter-train information flow topologies with compromised global reachability of the leader train, a repairing algorithm based on topology reconfiguration is proposed, which, together with the derived distributed control protocol, achieves the desired secure train tracking performance.Finally,a case study is conducted for efficacy validation.

Fig.2.Relative positions and velocities of follower trains to the leader.
Acknowledgments:This work was supported in part by the National Natural Science Foundation of China (62303240), the Natural Science Foundation of Jiangsu Province of China (BK20230356),the Natural Science Research Start-Up Foundation of Recruiting Talents of Nanjing University of Posts and Telecommunications(NY222033) and the Natural Science Foundation for Colleges and Universities in Jiangsu Province (22KJB120001).
杂志排行
IEEE/CAA Journal of Automatica Sinica的其它文章
- When Does Sora Show:The Beginning of TAO to Imaginative Intelligence and Scenarios Engineering
- Goal-Oriented Control Systems (GOCS):From HOW to WHAT
- Digital CEOs in Digital Enterprises: Automating,Augmenting, and Parallel in Metaverse/CPSS/TAOs
- A Tutorial on Federated Learning from Theory to Practice: Foundations, Software Frameworks,Exemplary Use Cases, and Selected Trends
- Cybersecurity Landscape on Remote State Estimation: A Comprehensive Review
- Data-Based Filters for Non-Gaussian Dynamic Systems With Unknown Output Noise Covariance
