For Mega-Constellations: Edge Computing and Safety Management Based on Blockchain Technology
2024-03-11ZhenZhangBingGuoChengjieLi
Zhen Zhang ,Bing Guo,* ,Chengjie Li
1 College of Computer Science,Sichuan University,Chengdu 610064,China
2 The Key Laboratory for Computer Systems of State Ethnic Affairs Commission,School of Computer Science and Technology,Southwest Minzu University,Chengdu 610225,China
3 National Key Laboratory of Science and Technology on Communications,University of Electronic Science and Technology of China,Chengdu 611731,China
Abstract: In mega-constellation Communication Systems,efficient routing algorithms and data transmission technologies are employed to ensure fast and reliable data transfer.However,the limited computational resources of satellites necessitate the use of edge computing to enhance secure communication.While edge computing reduces the burden on cloud computing,it introduces security and reliability challenges in open satellite communication channels.To address these challenges,we propose a blockchain architecture specifically designed for edge computing in mega-constellation communication systems.This architecture narrows down the consensus scope of the blockchain to meet the requirements of edge computing while ensuring comprehensive log storage across the network.Additionally,we introduce a reputation management mechanism for nodes within the blockchain,evaluating their trustworthiness,workload,and efficiency.Nodes with higher reputation scores are selected to participate in tasks and are appropriately incentivized.Simulation results demonstrate that our approach achieves a task result reliability of 95%while improving computational speed.
Keywords: blockchain;consensus mechanism;edge computing;mega-constellation;reputation management
I.INTRODUCTION
With the rapid development of satellite internet,researchers have paid significant attention to the wide coverage,flexibility,scalability,and diverse applications of mega-constellation communication systems.In a mega-Constellation Communication System (MCCS),it comprises a large number of lowcost and low-performance satellites,but a highperformance network architecture is a prerequisite for the normal operation of the system.Cloud computing,due to its advantages of low cost,high flexibility,scalability,reliability,and strong fault tolerance capabilities,is the preferred computing technology for mega-constellation communication systems.To better support high-density,large bandwidth,and low delay business scenarios,a more effective way is to build a business platform (edge data center) at the edge of the network close to the task provider (TP).In this way,some critical business applications are sunk to the edge of the network to reduce the loss of bandwidth and delay caused by network transmission and multi-level forwarding.However,due to the wide distribution of edge nodes and the vulnerable network environment,it is not easy to evaluate the reliability of their transmitted data.Therefore,how to ensure the reliability of the computing results is a scientific problem worthy of discussion.
In edge computing research,there are two common assumptions:one is that the computing nodes are honest and can provide reliable computing results for TPs[1,2].WNs in the public network can freely join or exit,and unreliable workers in the network may deliberately or unintentionally perform unwelcome behaviors to mislead the task results [3,4],so how to select WNs in the untrusted network environment is of great importance.Second,researchers assume that all devices unconditionally contribute their resources[5].Since computing brings energy consumption,the assumption of selfless dedication is unrealistic in the real world[5].Therefore,it is necessary to design an effective incentive mechanism to motivate end devices to become the WNs of edge computing tasks.
This paper aims to get efficient and reliable results in an untrusted environment in the MCCS so as to provide security (i.e.,the reliability of the computing results)and efficiency,the incentive framework for federated learning in multi-tp scenarios in MCCS is shown in Figure 1.A fair index is needed to evaluate the quality of WNs.Current researchers judge reputation as a measurement to assess the reliability or credibility of an entity due to its past behavior [6,7].However,when the number of tasks in the network is large,the workload of WNs with high reputation is significant,resulting in long task delays.
For the MCCS,this paper designs an extensible task allocation mechanism based on the above reputation management methods and redundancy computing methods.This allocation mechanism evaluates the busy situation of computing devices in the network,gives honest and efficient reputation evaluation to WNs on the premise of ensuring efficient and reliable computing results,and provides work opportunities to WNs that do not have high reputation evaluation,for the time being,the task throughput of the whole network is improved.To ensure safe reputation management and reliable reputation calculation,we do not adopt the traditional centralized management structure but manage reputation in a decentralized manner through the blockchain with openness and tamper-proof characteristics.A public blockchain is a trusted technology,which can widely combine computing devices in the network to realize computing services,but the popular public blockchain technology has shortcomings in efficiency.Innovative blockchain technology can provide efficient computing services and quickly reach a consensus on computing results[8-10].
To encourage employees to join the blockchain and share their resources,TPs use the blockchain to record the working status of WNs and design an incentive mechanism to reward WNs.The more tasks they complete,the higher the reputation of WNs and the more rewards they receive from TPs.More reliable and efficient task execution can improve TPs’and WNs’profits.To address the heterogeneity and multilevel nature of MCCS,the main contributions of this article are listed as follows.
This paper uses the task records on the blockchain and subjective logic model to manage and evaluate the reputation of WNs in a decentralized and efficient manner and evaluate WN’s efficiency and workload according to the public information in the blockchain.
This paper uses a novel blockchain technology to ensure the efficiency and reliability of edge computing results and significantly improve the parallel processing efficiency of distributed tasks in the network by using multiple low-reputation WNs to work together in a high-load and untrusted environment.
This paper designs an effective arithmetic auction algorithm,which has feasibility and individual rationality,can maintain the interests of WNs and TP,stimulate honest and efficient behavior,and resist malicious attacks.
Experiments proves that when the malicious nodes are less than half and the workload is small,the throughput of the network is slightly affected by the malicious WNs on the premise of ensuring the network security,and with the increase of the malicious WNs,the WNs are more willing to maintain honesty.
The rest of this article is organized as follows.We present the related work in Section II.Section III outlines the architecture of edge computing system,introduces the task-oriented blockchain consensus and describes the WNs selection scheme based on reputation,workload and efficiency-evaluation,then an incentive mechanism based on auction model for highreputation WNs selection is proposed.The perfor-mance evaluation in Section IV.Finally,we summarize this article in Section V.
II.RELATED WORK AND SYSTEM ARCHITECTURE
In MCCS,to improve computing efficiency and reduce energy consumption,a strategy is proposed to offload the tasks to the computing device nearby.[11]proposes a lightweight offload framework to support offloading computing-intensive tasks,deploy servers efficiently,and optimize overall execution time and energy consumption.[12] establishes a hybrid offload model and proposes a distributed deep learning driven task offload (DDTO) algorithm to generate near-optimal offload decisions on MDS,edge ECs and central ECs.[13] proposes an online incentivedriven task allocation scheme to maximize system utility,promote faster computing speed,and stimulate collaborative computing.
2.1 Related Work
As a distributed computing architecture,the computing resources of edge computing can be managed by companies or individuals,which brings security problems to distributed edge computing service providers.Many works of literature introduced blockchain to provide trust,security,and privacy support for edge computing.[14] proposes a blockchain framework to provide a trusted collaboration mechanism among edge servers in a work node environment.[15]offers a computing offload method named BENG based on blockchain.[16]uses Hyperledger’s blockchain architecture,a safe and reliable federal learning platform to build crossed data and then record them on the distributed ledger.[17]proposes a blockchain-based federated learning model designed for edge computing deployment against poisoning attacks.
In edge computing,efficient and honest computing devices should get computing tasks as much as possible,so reputation management is proposed.WNs can also improve their reputation by completing tasks honestly and efficiently.TPs can choose WNs with high reputations for completing tasks.Accordingly,if a WN provides wrong results or computing results over time,it causes reputation damage.[18]proposes a process to support smart contracts and automated reputation management through incentive design to reduce malicious behavior.[19] measures the reputation of WNs from the accuracy,integrity,efficiency,and historical data of results,an incentive mechanism is proposed to stimulate WNs to provide efficient and accurate computing results and eliminate malicious nodes.[20]proposes a reputation evaluation system based on blockchain.[13] proposes the cooperation mode of WNs.
Traditional reputation management is a centralized platform of third-party[21].The centralized platform is easy to be attacked by hackers,resulting in errors in reputation data.In addition,third-party platforms may snoop on data,leading to user information disclosure.Contrary to centralization,distributed reputation management system.Due to the distributed management of data,it cannot be easily tampered with,so it can provide trusted data.Because distributed devices redundantly back up the reputation data,TPs can access the nearest device to obtain reputation data efficiently.
2.2 System Architecture
The system architecture is shown in Figure 2,where a TP (Task Provider) submits a task to an Oracle node,and the Oracle node sends the task to the public blockchain.After the blockchain completes the task through one or several smart contracts,the result is sent to the Oracle node,which then provide the feedback to TP.The Oracle node is also called a MN(master node)and nodes in blockchain are called WNs(worker nodes).We assume that the MNs are trusted[22,23].In the public blockchain,the WNs are divided into several groups based on their proximity to the MNs.Within a group,all WNs redundantly complete a task delegated by the MN and vote on the task results.The blockchain considers the result with more support as trustworthy.WNs that provide trustworthy result are rewarded,and logs and rewards of all tasks are backed up on all WNs in the blockchain.
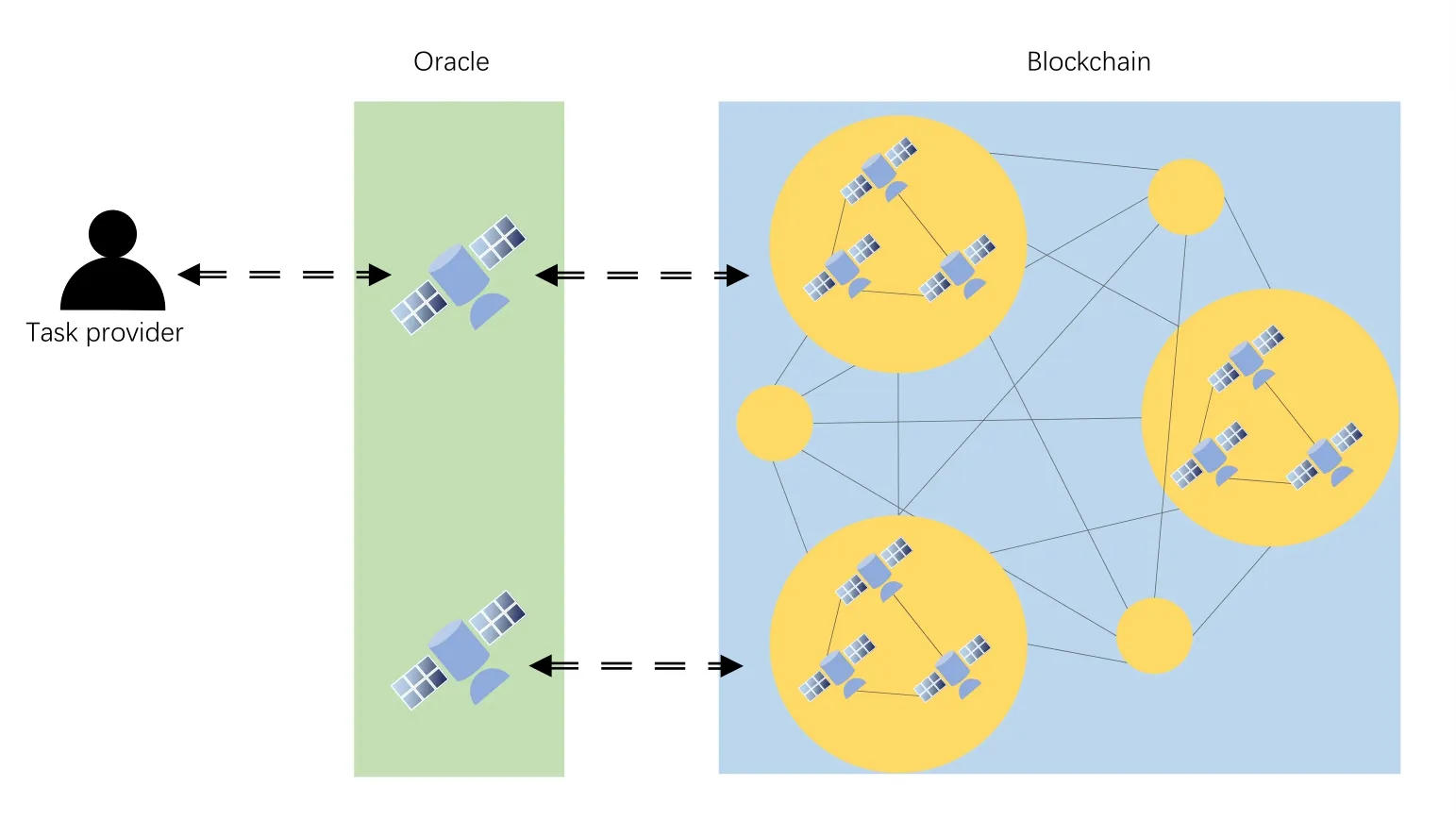
Figure 2.High-level architecture of the proposed system.
The closer a TP is to a group of WNs,the smaller the network delay caused by transferring data.The task should ideally be assigned to the nearest group of WNs.However,these WNs may have insufficient resources and take too long to complete the task.In such cases,the MN delegates the task to a nearby group of WNs.Since these WNs are part of the public network,there is a risk of malicious behavior where incorrect results are provided to deceive rewards.To address this,a task allocation mode is required to evaluate and manage the reputation value of WNs in the public network.This mode should mobilize nearby WNs to assist in completing the task based on their credibility,capability,network conditions,and workload.Furthermore,it should incentivize honest behavior among the WNs.
2.3 Novel Consensus Mechanism
The objective of applying blockchain to edge computing is to ensure the speed and reliability of task execution.To achieve this,we utilize the blockchain consensus mechanism described in [10].Unlike traditional block-based systems,this blockchain directly publishes transactions without packaging them into blocks.The consensus mechanism is depicted in Figure 3.The Oracle contract selects an appropriate group and publish a new task transaction,which is represented by the white square.These transactions contain task information and allocation details.
The WNs participating in the task complete the smart contract and receive the encrypted computing results from other WN in same group,which are represented by the colored squares.The transactions related to the same task are linked to the task’s genesis point,denoted by the white square.These linked squares of different colors form a task chain,as illustrated by the black arrows in Figure 3.Furthermore,the tasks completed by a specific worker WN are linked back and forth,forming a chain of WNs represented by the blue arrows [10,24].The combined chains of tasks and WNs create a network structure.

Figure 3.Novel consensus mechanism.
Through the use of hash encryption,data tampering is prevented,ensuring the integrity of reputation information.This means that reputation information cannot be altered without detection.
In contrast to traditional blockchains,each WN in blockchain publishes a single transaction that contains the result of a task.As there are multiple tasks being processed concurrently in the network,there exist multiple task chains simultaneously.When multiple WNs provide the same feedback for a particular task,their transactions are linked together.The task chain with the highest number of supporters becomes the main chain,while the chains outside the main chain are referred to as parasitic chains[9].
Within the main chain,the credibility of a WN is determined by the height of its transaction.WNs with lower transaction heights have higher credibility.However,it is important to note that transactions at the tip of the chain are not yet confirmed,which means that the corresponding WNs do not receive any credibility or rewards until the confirmation takes place.
III.REPUTATION AND AUCTION MODEL
Reliability and efficiency is key to computing QoS,to provide high-level computing service,a reputation management and auction model is needed.
3.1 Multi-Factor Evaluation on a WN
WNs have the freedom to join and exit the public network at will.However,the trustworthiness of the computing results provided by these WNs cannot be guaranteed.In the context of distributed computing,the speed and accuracy of results are of utmost importance.Therefore,it is crucial to identify and prioritize WNs with high credibility and efficiency in order to enhance the performance of distributed computing in an untrusted environment.To rate a WN,we consider factors such as its historical track record and workload[20].
3.1.1 Reputation of a WN
Taskxis assigned to a group of WNs to collaborate on its completion.The possible outcomes for taskxare represented by the sample spaceU={u1,···,un,null},a specific WN namedUAcan be in one of two states when working on taskxmay be in one of the two states: Working or Done.WhenUAis in the Working state for taskx,the corresponding result isnull,indicating that the task is still in progress.On the other hand,whenUAis in the Done state for taskx,it provides a resultui,whereui ∈U,representing the outcome it has produced for the task.
Definition: Letnidenote the number of WNs that provide a computing resultui.If for anyi=j,there is nonisuch thatni ≥nj+nnull,it indicates that there is no reliable result for taskx.However,if∃ni ≥nj+nnull,∀j=i,uiis considered the reliable result for taskx,and∀uj ∈{U-ui-null}are regarded as unreliable results[25].
The status of results provided byUAis defined as:
which corresponds toUAproviding a reliable result(positive),an unreliable result (negative),no reliable result(uncertainty),no results respectively.
A TP namedUBdelegatesktasks toUA,The status ofUAforUB’s tasks is denoted as:
1.Credibility evaluation
UA’s credibility is expressed by a tuple vector
2.Time effect on accuracy The reputation of WNs is dynamic and can change over time.WNs cannot be considered trustworthy at all times.The accuracy evaluation of WNs is crucial for recent tasks,and to account for this,a fading parameterf(0<f <1)is introduced.The accuracy value is affected bynow-tm(x),wheretm(x)represents the generation time ofx,i.e.,the creation time ofx’s genesis.The accuracy evaluation ofUAis influenced by time according to the Equation(6):
Considering above,credibility ofUAforUBis expressed as follows:
whereηpv,ηnv,ηucandηnoneindicate the influence weights of the states pv,nv,uc and none.
3.1.2 Workload of WNs
Given the transparent nature of the blockchain,all transactions are publicly accessible.The MN can assess the workloads of WNs by examining the task chains,specifically by tracing the tasks from the genesis block to the latest transaction in each task chain.This allows the MN to identify which WNs have not yet completed their tasks.By analyzing all the task chains,the overall workloads of WNs in the network can be determined.When there is a backlog of pending tasks,it is important to consider the efficiency of WNs and avoid assigning new tasks to already busy WNs.The workload ofUAis illustrated as follows:
In the case of tasks that were delegated a long time ago,the work WN might have abandoned the task and is available to accept new tasks.As time passes,the likelihood of task abandonment increases,thus diminishing the negative impact of the workload.Consequently,the workload variation over time can be expressed as in Equation(10):
3.1.3 Efficiency Evaluation
Honest and efficient work history serves as a reference for the MNs.In order to evaluate the work efficiency of WNs,we avoid relying on transmission time due to its uncertainty in the network.Instead,we utilize the height of transactions in the task chains as a measure.A lower transaction height indicates a higher level of responsiveness from the WN,which could be attributed to either superior performance or fast network transmission speed.The efficiency evaluation of a WN is as follows:
whereHx(UA)indicates the height of transactionUApublishes in task chain ofx.Hxindicates the height of the longest chain ofx.
Considering time,the efficiency evaluation ofUAforUBis as below:
3.1.4 Dynamic Task Allocation Mechanism
In an untrusted environment,both honest WNs and malicious WNs coexist and have the freedom to join or exit the network.While it is assumed that the majority of WNs are honest [26],low-reputation WNs can still participate in voting to contribute their results and obtain reliable outcomes.Alternatively,a highreputation WN can independently complete the task.Drawing inspiration from the consensus mechanisms employed in existing public blockchains,we propose the following methods to ensure the attainment of reliable results:
1.The most secure approach is to involve a large number of WNs in the computation and determine the results based on the majority through voting.This method is similar to the Proof of Work(PoW)consensus used in Bitcoin.However,it comes with the drawback of consuming significant energy,resulting in low overall network task execution efficiency.
2.An improved approach is to select one or several highly reputable WNs to participate in the computation.This method shares similarities with the Proof of Stake(PoS)or Delegated Proof of Stake(DPoS) consensus in blockchain.It enhances task execution efficiency and reduces computation costs.However,the drawback is that highly reputable WNs in the network are often occupied,making it difficult for newly joined WNs to obtain task opportunities.Moreover,task delegation to a limited number of WNs reduces security and hampers overall network task throughput improvement as task volume increases.
3.A further enhancement involves dynamically selecting a few WNs,based on their reputation values and task requirements,to participate in the task.WNs with high reputation values are assigned the task individually,while WNs with lower reputation values collaborate as a group.This approach ensures the reliability of computing results while minimally impacting efficiency[10].
A TP sends a task to the MN with a desired reliability level ofq.To achieve this reliability,the MN has two options: it can select a single WN with a reputation valuer ≥q,or it can choose multiple WNs withr <q.Among all the WNs that are available to work forUBi.e.i ∈available(UB),the selection process follows a specific priority.The selection of WNs continues until the following condition is met.
WNs with high reliability tend to receive a large number of tasks,resulting in heavy workloads.Therefore,the MNs needs to strike a balance between the efficiency and workload of the WNs.The efficiency and workload of a WN should meet the following condition:
ζandϑare the predefined weights of efficiency and workload,respectively.ϵis a threshold.When the difference between efficiency and workload is greater thanϵ,the MN considersUAa candidate WN.
3.2 Auction Model
After a TP submits a task to a MN,the MN selects one or several WNs to complete it.This process can be treated as an auction.The TP is the buyer,the WNs are the sellers,and the blockchain is the auctioneer.In the auction process,the auctioneer needs to maximize the buyer’s interests through the reputation information on the blockchain.
First,a TP sends bidding informationB={x,t0,τ,v,N,q},xis the task,t0isx’s arrival time,τis the maximum tolerance time ofx,vis the reward of a WN for completingx,Nis the maximum number of WNs for completingx,the TP paysNvto WNs at most forx,qis requiring reliability ofx.
Second,after receiving bidding information,the MN tends to delegate tasks to honest,efficient WNs.Wx={w1,w2,···,wn}is the set of employed WNs that work forx.
Third,afterWxis determined,the MN transfer data and deploys the task to the WNs.
Fourth,the WNs complete the task,encrypt the results,then publish transactions containing the results to the blockchain.The transactions can be mutually verified by WNs and form a chain,and the chain with most transactions is the main chain.If a WN does not complete the task after maximum tolerance time,the WNs lose the opportunity to get paid.
3.2.1 Information Exchange Model
The task is defined asx={s,ω},srepresentsx’s size,ωis the required computing resources.
xis delegated by a MN namedUB,UA∈Wx,the transmission time is:
wherer(UB→UA)=B×ln(1+P×g/σ2)represent the transmission rate,Bis the transmission bandwidth,Pis the transmission power,gis the channel gain between WNs and the TP,σ2is the power of additive Gaussian white noise.
The computing time ofUAforxis:
wherefUAis the computing resourceUAcontributes,i.e.the CPU frequency.
So the timeUAspends forxis:
wherecisUA’s unit energy value.δis the effective capacitance parameter ofUA’s computing chipset.Similarly,the total cost in terms of time and energy of the execution mode is:
whereϕis the energy consumption coefficient.
Several WNs work onxand the execution time ofxistx=min(Done_time(Wx),τ),where Done_time(Wx) represents the time to get a reliable result.In the most optimistic case,all WNs publishes transactions with the same results and transactions are linked in the main chain.In this case,when half of the WN inWxcomplete the task,the task is completed.In the most pessimistic case,all the transactions are not linked to each other,the reliable result is confirmed till all of the WN inWxcomplete the task.In the most pessimistic case,
wheretpending(wi) is the time required for previous tasks that have not been completed by thiswi.For the convenience of the following calculations,we settpending(wi)=0.
3.2.2 Utility Function
TP’s utility function isUTP=ϵ(τ-tx)-nv,whereϵ >0 is the satisfaction parameter of the task publisher.In order to maximize the profits of TP,the auction must meet the following constraints: 1.the results meet the reliability criteriaq;2.rationalization of WNs;3.maximization of TP’s expected benefits.
For constraint 1,it is discussed in subsection Dynamic task allocation mechanism in this section.
For constraint 2,Honest WNwiget rewardvby completing the task.The utility function of honest WN is:
whereµis the predefined weight parameter of energy consumption.
If the resources of the WNs are insufficient to complete the task,i.e.,the WNs reject to work on this task.
For constraint 3,as a TP,UBwants to maximize the benefits.
whichtx(wi) decreases,UBincreases or does not change.
The higher the reputation of each WN,the fewer WNs are required,and the greater the UBis.In order to maximize the utility function,TP preferentially selects WNs with high reputation and a large amount of idle computing resources to work on the task.
Requirements of algorithm:
1.In order to maximize the benefits of TP,the working time of the WNs should be as short as possible.
2.In order to ensure the reliability of the results,the high-reputation WNs are preferred according to the reputation ranking of available WNs.
3.The MN should judge whether the task can be accepted according to the estimated utility function of the WNs.
4.The MN should judge whether the task can be completed before theτaccording to the available resources of the WNs.In the whole system,we assume that the MN is completely trusted,but the TPs and the WNs are free devices in the public network.Therefore,we only consider the malicious behaviors of TPs and WNs for benefits.
Proposition 1.WNs will not misreport their available resource.
Proof.The WNs will not publish false network information or available resources because:
1.The rewardsvhas no direct relationship to the network environment nor available resourcesf;
2.If the WNUAfalsely publishes higher available resources or a better network environment than actual on the blockchain,all the MNs in the network can see this new information,andUAwill receive inappropriate tasks and miss appropriate tasks.AfterUAreceives taskx,and fails to completexinτ,UA’s reputation will be lost,and the possibility of obtaining other tasks will be lost;Even ifUAis lucky to complete the task in time,it will obtain extremely low rewards due to its transaction is near the tip or even no rewards if its transaction is the tip.
Proposition 2.TP will not misreport their resource demand.
Proof.The TPs will not publish false resource demand because:(1) If the demand resource is reported high,the selection range of WNs will become smaller.In order to make the reliability of the computing result reachq,more WNs will be required to work,resulting in a larger compensationnv;(2) If the required resource is reported low,the WN may not be able to complete the task inτ,and the results are of low reliability.
Proposition 3.The WNs will keep honest on results.
Proof.In pursuit of rewards,self-interested and illintentioned WNs might engage in the subsequent behaviors:
1.They may abstain from computation altogether,opting to fabricate inaccurate outcomes directly.Additionally,they could collaborate with other malicious WNs to disseminate misleading results;
2.They could furnish outcomes identical to credible results,even without conducting any actual computation.
For Proposition 1,reputations are essential to WNs.The WNs with high reputations have an excellent working history and are unlikely to collude;When high reputation WNs are busy,many low reputation WNs are selected.Based on the assumption that most WNs are honest,false results may have a dominant position at the beginning of the task handling and will eventually be surpassed by reliable results.
For Proposition 2,since a WN can only publish one result for one task,this selfish and lazy WN needs to know the results provided by other WNs,then publish its transaction behind.The WN needs a long time to find out the main chain,so the transaction published by this WN is high in the chain.The selfish WN will not be rewarded if there are no transactions behind this transaction.In addition,the result in the transaction is an encryption result(for example,asymmetric encryption is realized by using the WNs’IDs).The selfish result cannot get the actual results,so the transaction is even less likely to be verified by other WNs.This situation is the same as in Proposition 1.In addition,as the number of malicious WNs gets more and more,and the malicious WNs are less than the honest ones,the honest WNs get more and more tasks and earn more,so honest WNs are more willing to keep honest.
IV.SIMULATION AND EVALUATION
4.1 Simulation Models and Settings
This paper uses C++and socket technology to simulate a blockchain model and the simulation experiments conducted are grounded in the parameter settings of the Hongyan LEO satellite system,which operates at an orbital altitude of roughly 1100 kilometers.This blockchain consists of twenty-two WNs,two MNs,and two TPs.The initial reputation value of each WN is 0.49.Each WN in the blockchain can be directly or indirectly connected,and TPs are directly connected to the corresponding MNs.In MCCS,the server virtualization platform serves as the test environment,and the hardware configuration of the virtual environment is specified as follows.Apart from configuring the parameters at the physical layer,the wireless signal transmission network incorporates the parameters listed in Table 1.
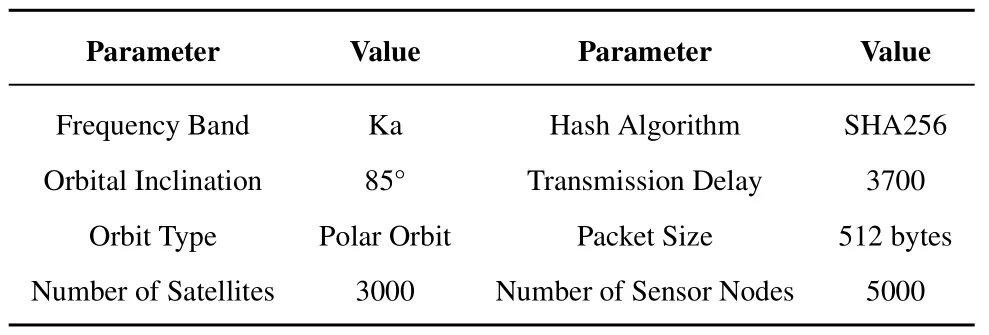
Table 1.Experimental parameters.
Because the blockchain in this paper is used to solve real-time computing tasks,the amount of information in the network is greatly increased compared with the traditional blockchain,which causes a tremendous burden on the network.This paper adopts two methods to solve the problem of network burden:
1.Reduce the amount of data transmitted.The realtime data transmission(i.e.transaction)only occurs among the WNs employed to the task.After the reliable results are determined,all the data containing the results are packaged into a data package and distributed to all WNs in the network.
2.Reduce the amount of data sent by a WN.Referring to the gossip protocol,we design that WNs can only send data to adjacent WNs.In this way,the whole network will receive the data several forwarding times.
Due to the network transmission delay,the same computing results may not be connected in a chain.In this case,our simulation sets a super WN to connect transactions with the same task results into a chain[9].When the TP submit a task to the MN,the results’reliability is required.If there is no WN with a reputation that meets this requirement,the computing results proposed by multiple decentralized WNs have higher credibility than that of a single WN[25].According to the records on the blockchain,the MN analyzes the reputation,workload,and network transmission time of the WNs,then selects the appropriate WNs and publishes a new task to the blockchain as a transaction.The WNs start to work after receiving this transaction.
4.2 Performance Evaluation
Referring to the work on the mobile/IOT blockchain[27-29],we assume that the task interval time is exponentially distributed with the average value of 30 seconds,i.e.the expected arrival interval time of the tasks(equal to the average task interval time) is Δt=30 seconds.
Our goal is to use a consensus mechanism,reputation evaluation,and incentive mechanism to encourage honest WNs to provide TPs with secure(i.e.,the reliability of the computing results)and efficient computing results so as to improve the system’s security(i.e.the number of malicious WNs that the system can tolerate)and throughput(i.e.the number of transactions verified per time unit).When all WNs in the network are trusted,the required reliability is 0.8,0.9,and 0.95,respectively.The consensus mechanism adopted in this paper compared with POW and POS(with four accounting WNs)consensus can 1)significantly shorten the processing time of each task,as shown in Figure 4;2)reduce the number of WNs occupied by the task,as shown in Figure 5;3)improve the utility of TP,as shown in Figure 6.
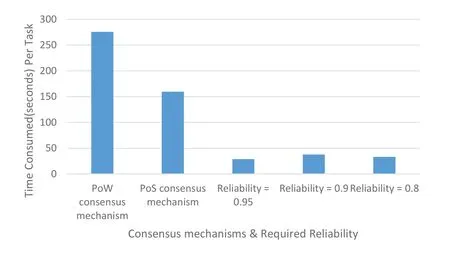
Figure 4.Time consumptions for consensus mechanisms and required reliabilities.

Figure 5.WNs occupied by tasks for consensus mechanisms and required reliabilities.
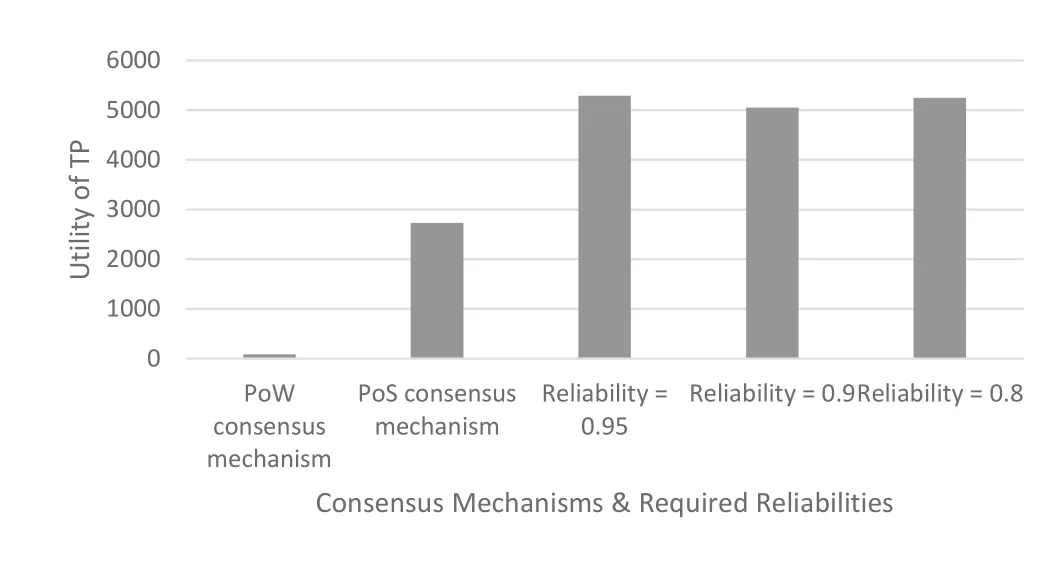
Figure 6.Utilities of the TP for consensus mechanisms and required reliabilities.
From Figure 5 we can see,the idle rate of WNs is high due to the influence of gossip protocol.The transmission time of WNs far from the TP is affected,and these WNs are not delegated with tasks.In a distributed network,decentralized task sources can improve the utilization rate of WNs,and improve the network throughput and the income of WNs per unit of time.
Since the WNs close to the TP do not need much time for transmission when processing tasks,the efficiency for processing tasks is higher,thus obtaining a higher reputation than those far from the TP.The high reputation of the WNs makes the TP reduces the number of WNs required for the task.Efficient completion of tasks and a small number of WNs for the task improve the utility of TP.Therefore,the method used in this paper significantly improves the utility of TP compared with PoW and PoS consensus as shown in Figure 6.
Next,when there are malicious WNs in the network,the task needs to be delegated to honest WNs.In our simulation,when the reliability requirement is low,the system selects only a few WNs during initialization,which is not conducive to evaluating the reliability.Therefore,in this simulation,it is appropriate to set the reliability of the task to 0.95.In the network,malicious WNs are evenly distributed.With the increase of malicious WNs in the network,honest WNs with a dominant number can still get tasks,while malicious WNs cannot get tasks gradually.The time consumption per task of the network is shown in Figure 7.
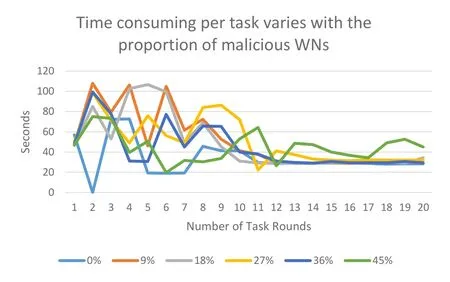
Figure 7.Influence of malicious WNs proportion on time consumption per task.
As in Figure 7,with the increase of malicious WNs,the fluctuation time of the broken line becomes more extended,and the TP needs more time to evaluate their reputations.Finally,the processing time of each task is shortened to about 30s,which is the shortest time among the WNs to process tasks.As in Figure 8,when the proportion of malicious WNs is less than 45%,the network’s throughput does not change much.It is because when the number of tasks in the network is small and there are enough idle WNs,the honest idle WNs near the TP can take the malicious WNs’place in the tasks.When the number of malicious WNs reaches 45%,the network needs more time to find honest WNs so that the throughput is affected.
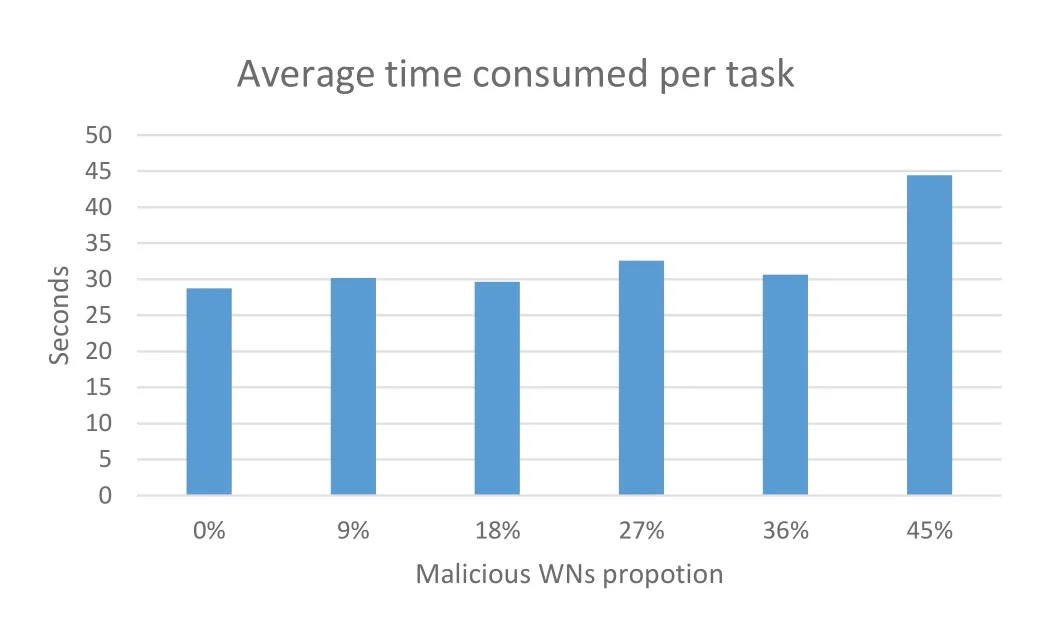
Figure 8.Influence of malicious WNs proportion on average time consumption.
As in Figure 9,the fluctuation of TP’s utility wave line extends with the increase of the proportion of malicious WNs.It is due to the consumption brought by the establishment of WNs’reputation.The higher the proportion of malicious nodes,the more rounds of trust evaluation are required to stabilize the utility of the TP in each task.This is because the larger the proportion of malicious nodes,the more challenging the reputation evaluation becomes,requiring more rounds of computation for reputation assessment.Although,different proportions of malicious nodes have little impact on the utility per task of the TP after stabilization as shown in Figure 9,total utilities of the TP in several rounds of tasks are decreasing along with the increase of malicious WNs as shown in Figure 10.
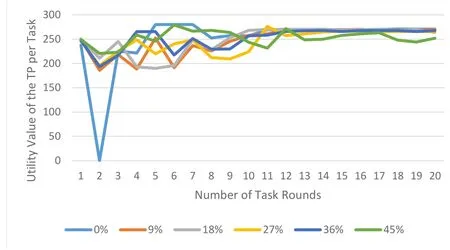
Figure 9.Influence of malicious WNs’proportion on TP’s utility per task.

Figure 10.Influence of malicious WNs’proportion on TP’s average utility.
The average profit of honest WNs is shown in Figure 11.As the proportion of malicious nodes increases,the profit of each honest node increases.This is because the number of malicious WNs increases,resulting in the decrease of honest WNs,and thus the workload of each honest WNs increases,so the profit increases.
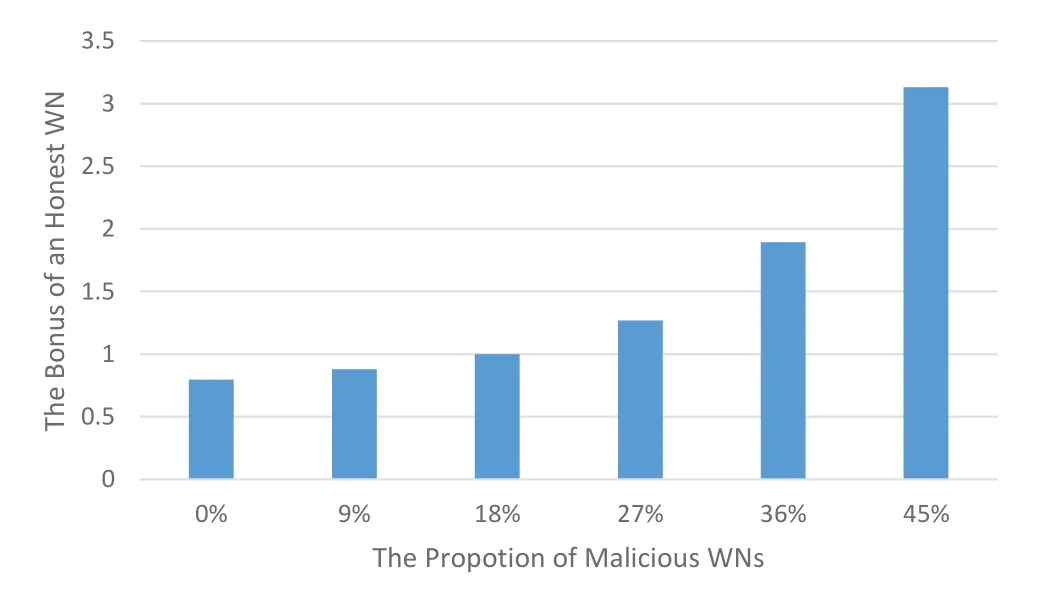
Figure 11.Influence of malicious WNs’ proportion on rewards of honest WNs.
V.CONCLUSION
For MCCS,this paper designs a multi-factor reputation management and evaluation,a dynamic task allocation mechanism and an incentive mechanism based on blockchain for edge computing.This incentive mechanism combines the consensus mechanism that can quickly process computing tasks and can provide distributed computing services for TPs,achieving the goal of improving network throughput and security.Advantages of these in MCCS are as follows.(1)Reduced network latency: Edge computing enables placing computing tasks and data processing functions on edge devices closer to the users,avoiding the latency of transmitting data to remote cloud centers for processing.(2)Reduced data transmission: Massive constellation communication systems involve large-scale data transmission,and transmitting all the data to the cloud for processing would consume significant bandwidth resources.By leveraging edge computing,local processing and data filtering can be performed on edge devices,reducing the amount of data transferred to the cloud and thereby lowering the risk of network congestion and operational costs.(3) Enhanced data privacy and security:Edge computing enables processing sensitive data on local devices instead of transmitting it to the cloud,thereby enhancing data privacy and security.(4)Improved system reliability: Satellite WNs in massive constellation communication systems face various environmental and failure risks.By performing local computing on edge devices,dependence on the central cloud is reduced,enhancing the overall system’s robustness and reliability.At last,we show the results of the algorithm through several experiments.
ACKNOWLEDGEMENT
This work was supported in part by the National Natural Science Foundation of China under Grant No.U2268204,62172061 and 61 871422;National Key R&D Program of China under Grant No.2020YFB1711800 and 2020YFB1 707900;the Science and Technology Project of Sichuan Province under Grant No.2023ZHCG0014,2023ZHCG0011,2022YFG0155,2022YFG0157,2021GFW019,2021YFG0152,2021YFG0025,2020YFG0322;Central Universities of Southwest Minzu University under Grant No.ZYN2022032,2023NYXXS034 and the State Scholarship Fund of the China Scholarship Council under Grant No.202008510081.
杂志排行
China Communications的其它文章
- An Efficient Approach to Escalate the Speed of Training Convolution Neural Networks
- Reliability Assessment of a New General Matching Composed Network
- Cooperative User-Scheduling and Resource Allocation Optimization for Intelligent Reflecting Surface Enhanced LEO Satellite Communication
- Flight Time Minimization of UAV for Cooperative Data Collection in Probabilistic LoS Channel
- Joint Optimization of Resource Allocation and Trajectory Based on User Trajectory for UAV-Assisted Backscatter Communication System
- Cooperative Anti-Jamming and Interference Mitigation for UAV Networks: A Local Altruistic Game Approach
