一种网络攻击下网联自动车的改进换道模型
2023-01-08吴新开张少伟贺晓征王斯奋
吴新开,何 山,张少伟,贺晓征,王斯奋
(1.北京航空航天大学交通科学与工程学院 北京 100191;2.Department of Civil and Environmental Engineering,Rensselaer Polytechnic Institute,Troy,NY 12180,United States)
Connected automated vehicles(CAVs),which integrate vehicle-to-vehicle(V2V)communication and autonomous vehicles(AV)technologies,are expected to greatly improve traffic safety and efficiency[1-2].Through wireless communication,CAVs can share and exchange information such as velocity,position,acceleration,and road conditions[3].However,due to open wireless communication,CAVs are vulnerable to various kinds of attacks,such asman-in-the-middle attack,impersonation attack,forging attack,replay attack,andSybil attack[4-5].These cyberattacks have shown severe risks to CAV traffic.To prevent these risks,a fundamental task is to research the impacts of cyberattacks on CAVs'driving behaviors[6-7].
Lopezet al.[8]developed attack models as functions of tampered traffic control settings(e.g.,green time raios,cycle length,retaining ratios)with outputs equivalent to mobility impacts on the traffic network.Fenget al.[9]investigated the vulnerability of traffic control systems in a connected environment and summarized four attack surfaces,including signal controllers,vehicle detectors,roadside units,and onboard units.Khanet al.[10]developed a conceptual system dynamics(SD)model to analyze cybersecurity in the complex,uncertain deployment of CAVs.The SD model consists of six critical avenues and maps their respective parameters that either trigger or mitigate cyber-attacks in the operation of CAVs using a systematic theoretical approach.Maglaraset al.[11]present main threats to critical infrastructures along with protective measures that one nation can take,and which are classified according to legal,technical,organizational,capacity building,and cooperation aspects.Donget al.[12]designed an evaluation framework for cyberattacks on CAVs,and analyzed the impact of cyberattacks on vehicles and the transportation system.Liet al.[13]investigated the influence of slight cyber-attacks on the longitudinal safety of CAVs,and considered the communicated position and speed data from preceding CAVs under attacks.Huet al.[14]proposed a method to detect cyberattacks by cross-checking Signal Phase and Timing(SPaT)information and connected vehicle trajectories data.
However,the existing work aims to investigate the impact of cyberattacks on CF behaviors.To the best of our knowledge,only a few previous studies have considered the impact of cyberattacks on LC behaviors.For instance,Khattaket al.[15]utilized an infrastructure-based communication platform consisting of cooperative adaptive cruise control and lane control to perform cyber risk assessments of CAVs.Kashyapet al.[16]found that the malicious vehicles may perform subtle speed and/or lane changes and modeled the mix of malicious and normal vehicles in the traffic system by using the Lighthill-Whitham-Richards(LWR)model.The authors aimed to use Gaussian Processes to detect the presence of such malicious vehicles in such a mixed traffic scenario.Zhaoet al.[17]used the default lanechanging algorithm in Simulation of Urban Mobility(SUMO)and presented the traffic behavior under cyberattacks.
Although these studies present the influence of cyberattacks on LC behaviors using simulation experiments,they have not developed new lanechanging model with cyberattacks.In this research,we aim to construct an improved LC model associated with cyberattacks,through which we could better understand how the cyberattacks impact the LC maneuver and how to quantify this impact.The detailed description will be presented in the following sections.
This study improves a classic LC model,i.e.,MOBIL(Minimizing Overall Braking Induced by Lane changes)model[18]to describe the lane-changing behavior.In the proposed ELC(Extended Lane Change)model,an improved IDM(Intelligent Driver Model),a most widely used CF model[19],is adopted to derive neighbor vehicles' accelerations based on their own and their nearest leaders’velocities and positions when the LC happens.Numerical simulations are conducted to verify the effectiveness of our proposed ELC models and illustrate the impact of cyberattacks including velocity,position and acceleration attacks on LC behaviors.
The main contributions are described as below.(i)Cyberattacks on vehicles are formulized and integrated into the classical LC and CF models.(ii)The extended LC model and the improved IDM are used to describe the process of LC in two lanes.(iii)Various cyberattacks are classified into three types,i.e.,velocity,position and acceleration attacks,and numerical simulations illustrate the changes of malicious attacks on vehicles'LC movements.
1 An extended lane-changing model for CAVs under cyberattacks
1.1 Lane-changing model
In general,a LC process consists of three phases,i.e.,before,during,and after the lane change[20].In the phases of before and after the lane change,vehicles follow the CF rules.A lso,before the lane change,the subject vehicle requires to consider neighbor vehicles'dynam ical parameters such as velocity,space gap,and acceleration.If the LC condition is satisfied,then the subject vehicle performs a lane change.This section presents how to derive an extended lane-changing(ELC)model w ith cyberattacks.
To describe CAVs'LC behaviors under cyberattacks,we adopt the MOBIL model,which has many advantages[21-22]compared to other LC models.The most evident one is that MOBIL uses acceleration as amodel control variable,which allows perfect integration w ith other CF models to simulate both CF and LC behaviors at a m icroscopic level.A lso,MOBIL integrates the LC demand generation and the feasibility judgment,which can better describe CAVs'LC behaviors.
In this study,the MOBIL LC model is implemented to model a two-lane highway traffic.A simple diagram of a lane change on two-lane traffic is first provided in Fig.1.As shown in the figure,the subject vehicle,indexed asm,plans to change to its neighbor lane.Before the LC,its nearest preceding and follow ing vehicles are indexed asm-1 andm+1,respectively.The neighbor vehicles on the LC target lane are indicated bynandn-1,respectively.When the LC condition is satisfied,the subject vehiclemw ill change its current lane to the neighbor target lane,as shown by the virtual vehicle in Fig.1.A fter the lane change,the subject vehiclemfollow s its new preceding vehiclen-1 based on the CF theory.M eanwhile,the new follower of the subject vehicle turns to be vehiclen.
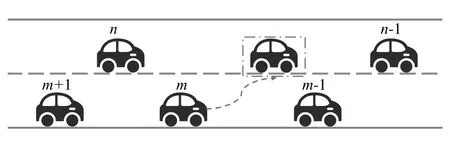
Fig.1 A typical lane-changing scene
The MOBIL model has a comprehensive consideration of both LC safety and gain.Therefore,itneeds tomeet the follow ing two essentialconditions:
(1)The safety criterion:This condition aims to ensure the safety after the LC,i.e.both the accelerations of the subject vehiclemand its new follower vehiclenneed to fit the follow ing conditions:

(2)The incentive condition:This criterion is used to decide whether a lane change improves the local traffic status.The incentive criterion is formalized asbelow:

whereamindicates the acceleration of vehiclemon the current lane,pdenotes the politeness factor,indicates the predicated acceleration of vehiclem+1 after the subject vehiclemchanges the lane,andΔathis the LC threshold.The politeness factorpcan be interpreted as the degree of altruism,which is a variable that determ ines the impact of nearby vehicles on the LC decision of the subject vehicle.It can vary fromp=0 for completely selfish lane-changers top>1 for altruistic drivers who do not change lane if LC would deteriorate the traffic situation considering these followers.Furthermore,p>0 represents considering the benefitsofother vehicles.
1.2 Car-follow ing model
There are two different car-follow ing models,linear and the other nonlinearmodel,to demonstrate the CAVs'follow ing behaviors.Car-follow ingmodels are used to formulate vehicle interactions and uncover CAV platoon dynam ics.Linear car-follow ing models include Pipes model,Helly's model,and Gazis-Herman-Rothery model.Nonlinear car-follow ing models include Newell's model,optimal velocity model,and intelligent driver model(IDM).The critical difference between these two types of carfollow ing models is that the nonlinearmodels capture a nonlinear relationship w ith deviation from the desired space gap and the relative velocity.
Compared to the linear car-follow ing model,the nonlinear car-following is more suitable for describing the real traffic flow due to its nonlinearity and sophistication in capturing complex vehicle dynamics.This research adopts the IDM due to its advantages as follows.First,the IDM is a multi-regime model,which presents a greater realism than other nonlinear models when characterizing the congested traffic flow[2].Second,the IDM ensures collision-free vehicle movements,which would not cause unrealistic acceleration/deceleration shown in some linear car following models[23].The formulation of this model is expressed as follows[19]:

whereamindicates the acceleration of vehiclem;v0indicates the desired velocity in free flow;s* indicates the desired safe gap;s0denotes the space gap in completely stopped traffic;sm=xm-1-xm-lis the space gap between the preceding vehiclem-1 and vehiclen;lis the length of vehicle;xmis the position of the vehiclem;vmis the velocity of vehiclem;and Δvm=vm-vm-1is the relative velocity between vehiclemand its preceding vehiclem-1.In addition,Tis the desired time gap between successive vehicles;andaandbindicate the vehicle's maximum acceleration and deceleration,respectively.Note if all vehicles travel uniformly,i.e.,each vehicle's acceleration is equal to zero,each vehicle keeps the same velocity and space gap between consecutive vehicles.
In a normal CAV environment,each vehicle can receive dynamic information such as velocity,position,and acceleration from the surrounding vehicles.Vehicles' information will be accurately sent to the target vehicle on time.However,when an attack happens,the information transmission between vehicles could be interrupted,delayed,lost,or even falsified.Then,the vehicle's LC and CF behaviors can also be influenced.Note that this study only the V2V communication.
1.3 Cyberattacks
Muchresearchhasdemonstratedthat cyberattacks have an impact on the effective use of vehicles[24].If without any influence of cyberattacks,vehicle dynamics information,including speed,acceleration,headway,etc.,will be accurate and timely disseminated to other vehicles.The cyberattacks can be classified into three main categories:DoS attacks,replay attacks and false data injection attacks.When an attack such as spoofing,replay,and impersonation occurs,the information transmission among vehicles could be interrupted and/or falsified.A detailed description of these attacks is listed below[25-26].
(1)Spoofing attack:An adversary can compromise a vehicle and send fake messages such as fake location,velocity,and acceleration.For instance,GPS is responsible for delivering the realtime location message to the surrounding vehicles.When the spoofing attack happens,the spoofed GPS can send a fake location to the subject vehicle by releasing a strong-power signal from the GPS satellite simulator.
(2)Replay attack:An attacker captures the packets and replays them at a later time to disguise that they were sent by the true sender.Thus,the repeated message,which is sent after a while,could be accepted as a new message.Mathematically,the position,velocity,and position of vehicle may be unchanged during the attacking period.
(3)Impersonation attacks:In vehicular networks,an attacker could impersonate a roadside infrastructure or vehicle to trick others by applying their authentication details.For example,an attacker might impersonate an emergency vehicle,which would give them a higher priority within the vehicular network and result in less congestion.The position,velocity,and position of vehicle can be altered.
The above cyberattacks could affect vehicles'behaviors in their own manners.Essentially,all these attacks can release bogus messages which falsify the vehicle's dynamic information such as velocity,position,and acceleration.Hence,for simplicity,this research considers all these attacks asbogusattacks[25].
1.4 Extended LC model with cyberattacks
To describe CAVs' dynamic traffic behaviors under cyberattack,we present the following two representative attacking cases.In the first case,we assume that the velocity and/or the position of the preceding vehiclem-1 of the subject vehiclemis attacked,and vehiclem-1 sends falsified velocity and/or position messages to the subject vehiclem.Then the subject vehicle's acceleration will be influenced.In this case,the influenced acceleration in MOBIL needs to be updated by the following extended IDM model:
whereβandγare the weight parameters to describe the impacts of cyberattacks on velocity and position of the subject vehicle’s nearest leader,respectively.Ifβ≠0 orγ≠0,Eq.(4)means that the velocity or the position of vehiclem-1 is attacked.Ifβ=γ=0,Eq.(4)is transformed to the classical IDM model.
In the second case,we assume that the acceleration of the following vehiclenafter LC of the subject vehiclemis falsified.In this situation,the weighting parametersα,δare introduced to capture the change of acceleration influenced by attacks.An improved incentive criterion in the MOBIL model under cyberattacks can be formulated below:
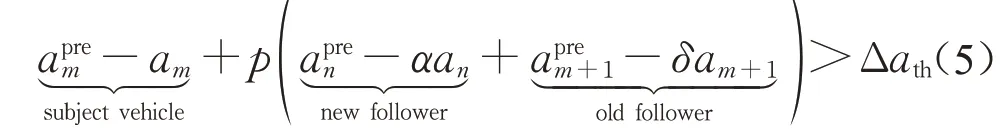
whereαandδare the weighting parameters to describe the impacts of cyberattacks on the new follower vehiclenafter LC and the old follower vehiclem+1 before LC.Here,αandδhave clear physical meanings.Ifα=δ=1,it indicates the CAV is moving without cyberattacks.Whileα≠1 and/orδ≠1,it denotes the CAV is influenced by cyberattacks.Specifically,ifα>1(δ>1),it represents that the subject vehicle receives overestimated acceleration messages of the following vehicle after(or before)LC;and ifα<1(δ<1),it represents that the subject vehicle receives an underestimated acceleration message from the following vehicle after(or before)LC.
Overall,these falsified messages could cause the vehicle to make the wrong decision,leading to potential collisions.To fully capture these impacts,based on above Eqs.(1),(4)and(5),we can derive an ELC model,i.e.,an improved MOBIL model,as described in the following equation:
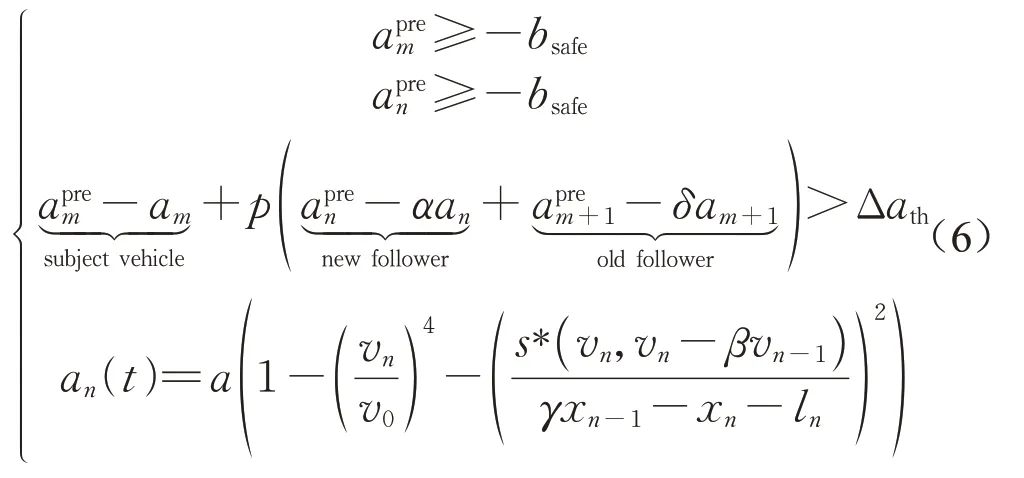
Note that Eq.(6)essentially integrates the CF IDM model and the LC MOBIL model for the CAVs under attacks.The following section will verify the effectiveness of our proposed model.
2 Numerical Simulation
This section presents a series of simulations to verify the effectiveness of the proposed ELC model and illustrate the impact of cyberattacks on vehicles'LC behaviors.In this study,we use Python to show the change in vehicles' behaviors under cyberattacks.We select a two-lane highway whose length is long enough to conduct our simulation.The total simulation time is 30 s,and each sampling time is 0.01 s.For the convenience of investigation,we put forward the following assumptions(see Fig.2):(i)12 CAVs are grouped as two platoons and are traveling on a straight two-lane highway;(ii)Without LC,each vehicle updates its dynamical parameters based on the IDM model and adopts a simple predecessor-following communication protocol,i.e.,one vehicle only receives beacon messages from its directly preceding vehicle;and(iii)The subject vehicle(3rdvehicle)changes to the neighbor lane based on the proposed ELC Eq.(6).

Fig.2 Numerical simulation scenarios
To illustrate the impact of cyberattacks on the vehicle's lateral behaviors,we design five scenarios:without attacks,velocity attack,position attack,velocity and position attacks,and acceleration attack.
In all scenarios,each vehicle's initial space headway in the platoon is 35m,and the initialvelocity is set as 14m·s-1.As shown in Fig.2,the velocity of the first vehicle(i.e.,vehicle 1)in the current lane(i.e.,lane A)remains unchanged at 14 m·s-1,and the first vehicle(i.e.,vehicle 2)in the target lane(i.e.,lane B)is 18m·s-1.Other vehicles in the platoon obey the IDM to follow their preceding vehicles.The initial values of all parameters for simulation are presented in Tab.1.

Tab.1 Simu lation parameters
(1)W ithout cyberattacks
As a reference,Fig.3 shows the changes in the dynamic parameters of the platoon w ithout cyberattacks.When the LC model does notmeet the safety constraint and the incentive condition,there isno LC.
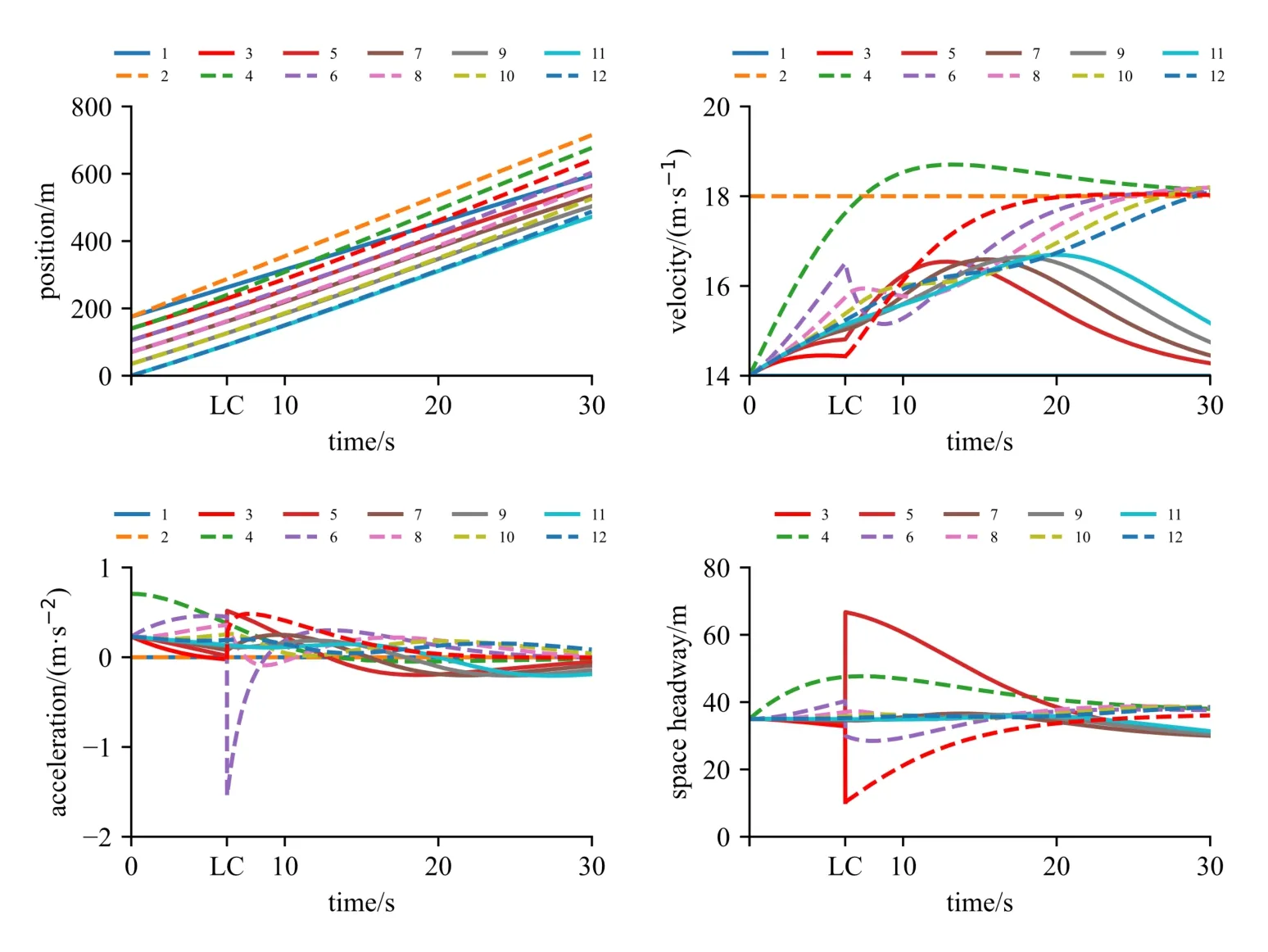
Fig.3 Plots of position,velocity,acceleration,and space headway without attacks
Before the LC,each vehicle is traveling uniform ly in the current lane.We can see that the 3rdvehicle changes its lane at 6.23 s according to the classical MOBIL model.At this time,the 3rdvehicle's velocity is 14.44 m·s-1,and the 4thvehicle's velocity is 17.63 m·s-1.As shown in this figure,after the LC,the follow ing vehicles of the 3rdvehicle in lane A(e.g.,5thand 7thvehicles)accelerates to shrink the space headway.Meanwhile,the following vehicles of the 3rdvehicle in lane B(e.g.,4thand 6thvehicles)have to decelerate to keep the safe space headway.
(2)Velocity attacks
Fig.4 and Fig.5 show the dynamic parameters of the platoon when the 1stvehicle's velocity is underestimated(β=0.9)and overestimated(β=1.1),respectively.It can be seen that the 3rdvehicle plans to change its lane at 4.87 s and 7.80 s,respectively.According to the extended IDM model Eq.(4),when the 1stvehicle's velocity is underestimated,the 3rdvehicle is forced to slow down to achieve safe space headway.Based on Eq.(2),the incentive value in the MOBIL model turns large.Hence,the subject vehicle(i.e.,3rdvehicle)will change to the neighbor lane in advance.Compared with Fig.3,under underestimated velocity attack,the LC time is advanced by 1.36 s.

Fig.4 Plots of position,velocity,acceleration,and space headway under underestimated velocity attacks when β=0.9
Fig.5 shows the impact of an overdamped velocity attack on the LC of the subject vehicle.If the released messages of the 1stvehicle's velocity are falsified and amplified,the subject vehicle(i.e.,3rdvehicle)who receives the falsified messages has to accelerate to keep the same velocity as the first vehicle.Based on Eq.(2),the incentive value in the MOBIL model turns small.In this case,the LC time is delayed by 1.57 s.It should be noted that the real velocity of the first vehicle does not change.It is not difficult to imagine that this attack could lead to a potential collision.
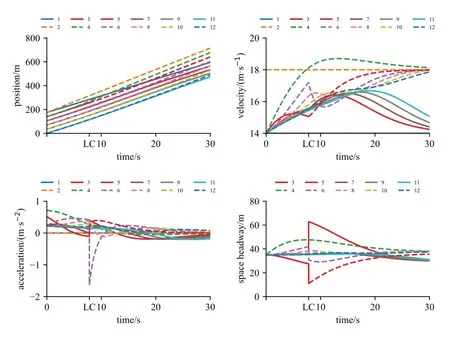
Fig.5 Plots of position,velocity,acceleration,and space headway under overestimated velocity attacks when β=1.1
(3)Position attacks
Fig.6 and Fig.7 show changes in the dynamic parameters of the platoon when the space headway between the 1stvehicle and the 3rdvehicle is underestimated and overestimated,respectively.It can be seen that the 3rdvehicle chooses to change lanes at 5.76 s and 6.67 s,respectively.Intuitively,when the space headway is underestimated,the 3rdvehicle has to decrease its velocity to keep a safe space headway.The smaller acceleration of the subject vehicle leads to a larger incentive value based on Eq.(2).Hence,based on the MOBIL model,the subject vehicle should change its lane in advance.As shown in Fig.6,the LC time is advanced by 0.47 s.By contrast,when the space headway is overestimated,the 3rdvehicle accelerates to shorten the space headway.Based on Eq.(2),the larger acceleration of the subject vehicle leads to a smaller incentive value.Hence,based on the MOBIL model,the LC time of the subject vehicle should be postponed.As shown in Fig.7,the lane-changing time is delayed by 0.44 s.

Fig.6 Plots of position,velocity,acceleration,and space headway under underestimated position attacks when γ=0.9

Fig.7 Plots of position,velocity,acceleration,and space headway under overestimated position attacks when γ=1.1
(4)Velocity and position attacks
In this case,we discuss the effects of modification of both velocity and position on LC behaviors.Fig.8 and Fig.9 show that changes in position,velocity,acceleration,and space headway of the vehicle platoon under velocity and position attacks.The 3rdvehicle changes lanes at 4.42 s and 8.20 s,respectively.It can be seen that when the velocity and headway are both underestimated by 10%,i.e.,β=γ=0.9,the LC time will be greatly advanced by 1.81 s.Underestimated velocity and space headway lead to an increase in the incentive value of lane-changing.Thus the 3rdvehicle changes its lane quickly.When the velocity and headway are both overestimated by 10%,i.e.,β=γ=1.1,the 3rdvehicle first increases its velocity to follow the 1stvehicle and reduce the space headway,resulting in a decrease in the incentive value of LC based on Eq.(2).Hence,the LC time is put off.In this case,the LC time is delayed by 1.97 s.Compared with the velocity or position attacks,the influence of both velocity and position is much severer.

Fig.8 Plots of position,velocity,acceleration,and space headway under underestimated velocity and position when β=γ=0.9

Fig.9 Plots of position,velocity,acceleration,and space headway under overestimated velocity and position when β=γ=1.1
(5)Acceleration attack
To be consistent with the proposed ELC model,we assume that the accelerations of the new follower after LC(the 6thvehicle)and the old follower before LC(the 5thvehicle)are falsified.In detail,Fig.10 and Fig.11 show the changes in the dynamics parameters of the platoon when the acceleration is underestimated(i.e.,α=δ=0.5)and overestimated(i.e.,α=δ=1.5),respectively.These figures show that the 3rdvehicle changes its lane at 6.21 s and 6.25 s,respectively.In fact,the new or old followers cannot influence the subject vehicle's longitudinal behaviors but the lateral LC behaviors based on the MOBIL model.Compared with no attack scenarios scenario,whether underestimated or overestimated acceleration attacks could result in a slight change in LC time.The reason is that the politeness factor(p=0.1)in Eq.(6)weakens the influence of the accelerations of the new and old followers.Hence,acceleration attacks only lead to slight time changes.

Fig.10 Plots of position,velocity,acceleration,and space headway under underestimated acceleration attacks when α=δ=0.5

Fig.11 Plots of position,velocity,acceleration,and space headway under overestimated acceleration attacks when α=δ=1.5
The above five simulation experiments show that falsification of acceleration,velocity,and position will cause abnormal LC behavior,such as LC time in advance or delay and vehicles' oscillation amplitudes.These results demonstrated that cyberattacks could influence traffic efficiency and cause potential rear-end collisions.
3 Conclusions
With the advent of intelligent and connected technology,the impacts of cyberattacks on vehicles have drawn many scholars' attention.This research focuses on modeling LC behaviors under cyberattacks.To this end,based on the MOBIL and IDM models,this study proposes an extended LC(ELC)model with cyberattacks to describe the LC decision-making behavior.Through the numerical simulation,we found that cyberattacks could imperil the LC maneuvers and different attacks are able to result in different consequences such as LC time in advance or delay,and even potential rear-end collisions.
By studying the lane-changing behavior of connected vehicles under cyberattacks,the impact of cyberattacks on vehicle lane-changing behaviors is revealed.Attackers can attack with different parameters on vehicles according to different attack purposes and real-time traffic conditions to accomplish specific attack goals,such as causing collisions and increasing traffic congestion.
The research in this paper allows us to have a deeper understanding of the impact mechanism of cyberattacks,so that we can actively defend against attacks.By analyzing the manifestations and results of cyberattacks,the detection and defense of cyberattacks can be completed in time,so as to avoid personal and property hazards.
In actual vehicle applications,relevant algorithms can be installed to detect the dynamic information of the own vehicle and other vehicles,so as to quickly and timely find abnormal dynamic updates and communication information.At the same time,the detection method can also be used in combination with other cyberattacks detection methods to improve the detection rate of cyberattacks,and provide response strategies in time.
Vehicles have multiple strategies to defend against cyberattacks.In addition to cryptographic methods,communication information can also be verified by methods such as multi-sensor data fusion.At this time,the attacker needs more sophisticated attack strategies,such as performing compound attacks and attacking acceleration,speed,and position information at the same time,which also puts forward higher requirements for vehicle information security protection.
There are several directions for future study.First,it is expected that this research could help counter the detrimental effects caused by cyberattacks.By understanding the impacts on traffic dynamics caused by different cyberattacks,some possible traffic control,and management strategies could be developed and applied to resolve these impacts.Second,in this study,for the convenience of analysis,we just adopt two lane framework in our simulation studies,the framework will be extended to a multi-lane with thousands of vehicles.Third,it will be interesting to explore to assess the impact on more parameters like traffic flow,safety etc.At last,security work against malicious attacks such as detection of cyberattacks,privacy-preserving scheme between V2X and human driver intervention,etc.will be investigated in nearly future.
作者贡献声明:
吴新开:构建框架,起草论文;
何山:调研文献,提出模型;
张少伟:调试参数,设计实验;
贺晓征:实验仿真,验证模型;
王斯奋:评阅论文,提供指导。
